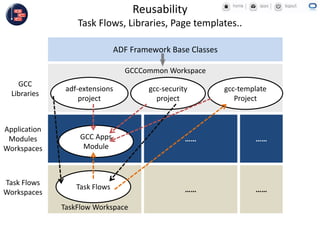
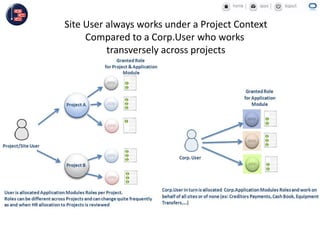
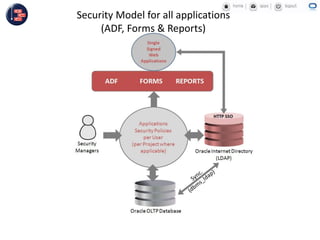
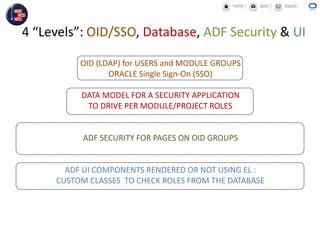
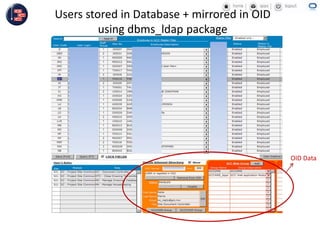
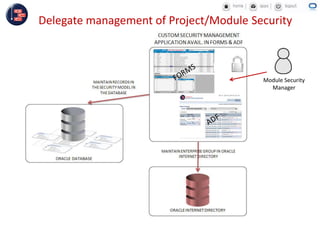
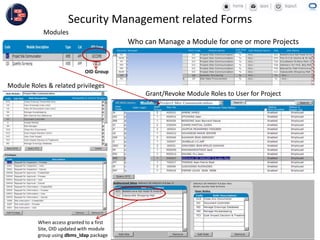
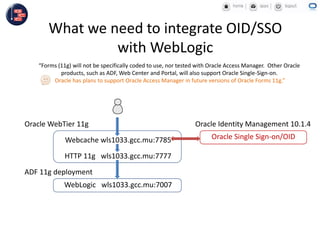
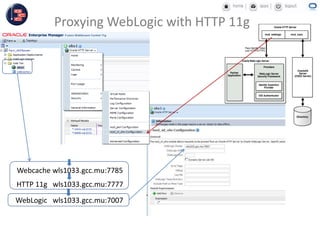
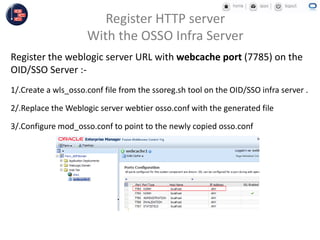
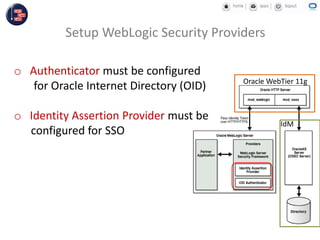
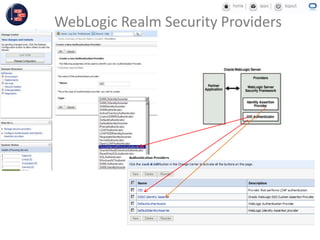
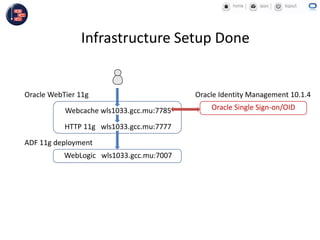
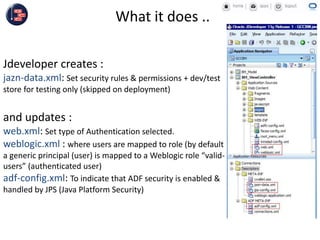
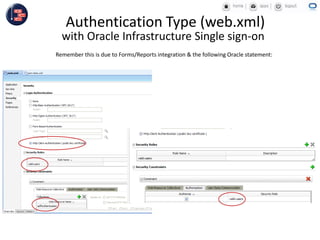
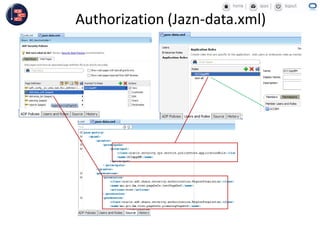
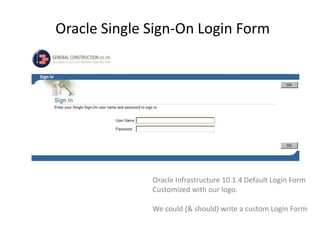
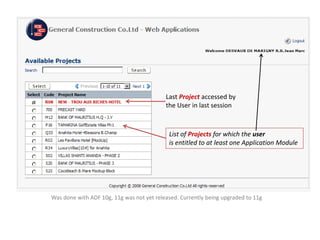
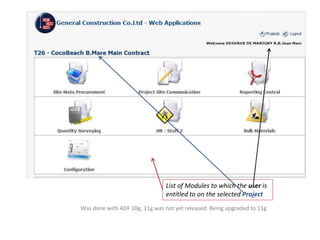
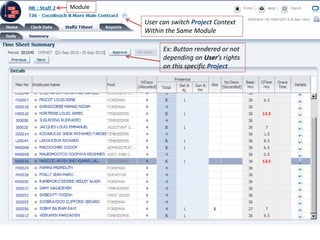
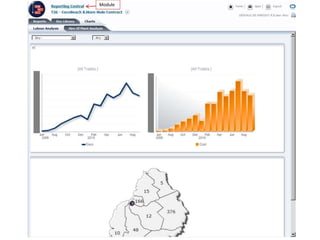
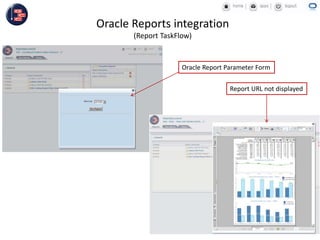
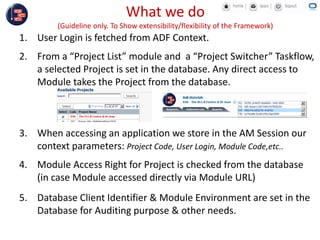
GCC implemented a project-centric security model for their ADF applications to enable their construction sites to securely access centralized systems. Users are authenticated using Oracle Single Sign-On and assigned roles and privileges at the project and module level by security managers. These privileges are checked using EL expressions to control UI rendering on a per-page and component level. The infrastructure was set up using WebLogic, HTTP Server, and Identity Management integrated with the ADF applications. Reusable task flows, libraries, and templates help manage the growing portfolio of ADF applications.












![UI components level
Rendering or not a UI component
(button, panel etc..)
JSF Expression Language (EL)
CurrentPeriod <= (le for less or equal) Period
#{securityContext.userInRole[‘rolename’]} for “static” role
We will see later how we use EL to apply per project security](https://image.slidesharecdn.com/adfsecurityinaproject-centricenvironment-101117050834-phpapp02/85/Oracle-ADF-Case-Study-36-320.jpg)


![Normal EL Expression to check from static role
#{securityContext.userInRole[‘Role Name']}
Custom EL Expression to check from Database
privileges Codes assigned to Role
#{securityScope.userInRole[‘Priv List Code']}](https://image.slidesharecdn.com/adfsecurityinaproject-centricenvironment-101117050834-phpapp02/85/Oracle-ADF-Case-Study-47-320.jpg)