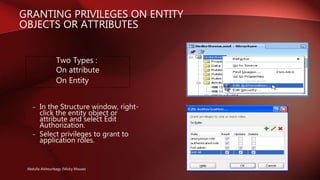
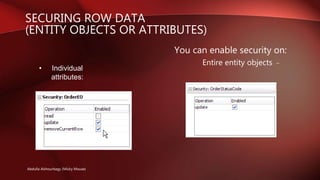
The document discusses Oracle Application Development Framework (ADF) security. It provides an overview of key aspects of ADF security, including that it:
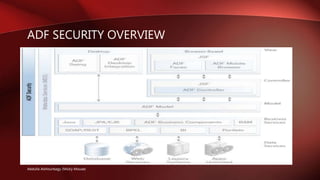
- Is built on Oracle Platform Security Services and integrated with WebLogic Server.
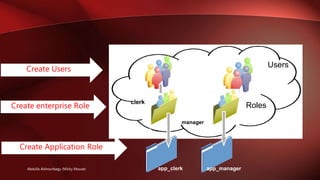
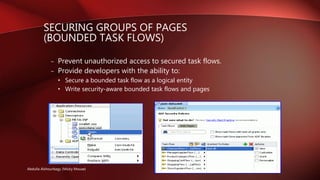
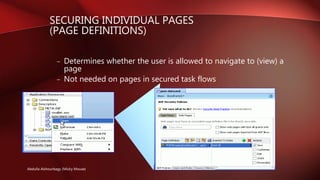
- Provides declarative, permission-based security for ADF resources like bounded task flows and entity objects.
- Implements a policy-based Java Authentication and Authorization Service (JAAS) security model.
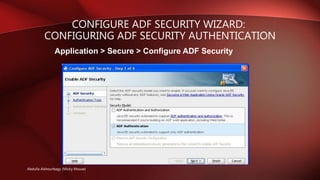
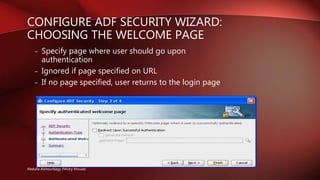
- Allows configuring authentication, roles, and permissions using the Configure ADF Security wizard.