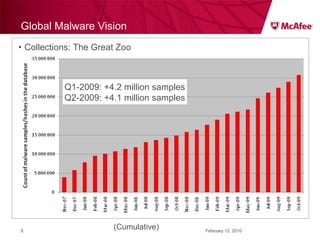
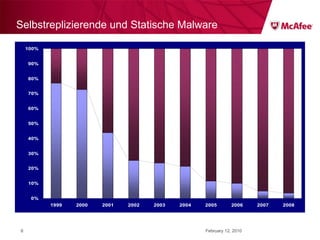
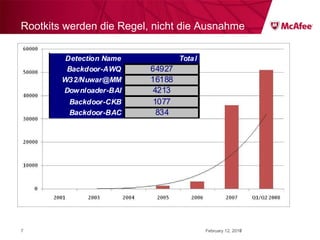
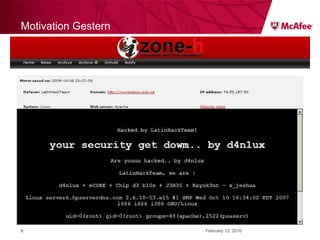
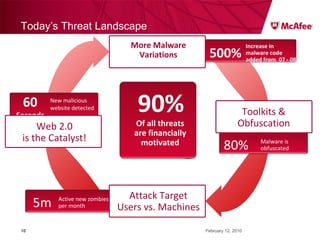
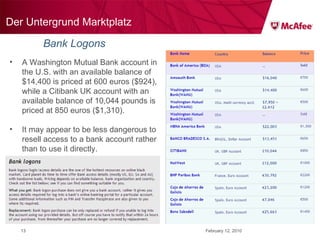
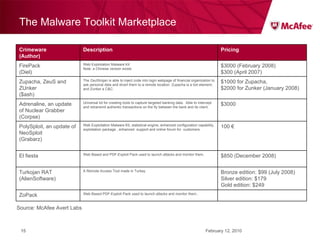
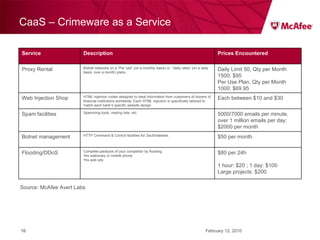
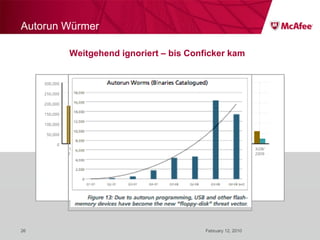
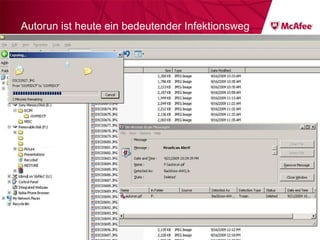
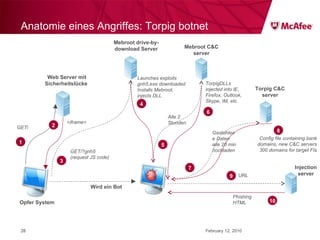
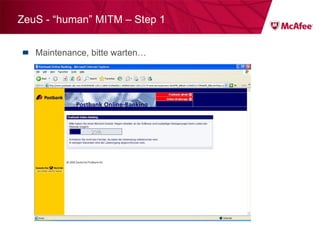
The document discusses trends in malware threats observed by McAfee Avert Labs. It notes a massive increase in the number of malware samples analyzed daily, with most being encrypted or packed to avoid detection. Banking trojans like ZeuS that perform man-in-the-middle attacks to steal login credentials are among the most prevalent threats. Criminal organizations have developed toolkits and markets to enable others to easily create and distribute their own malware.







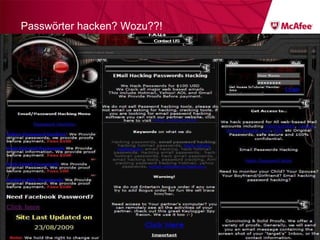
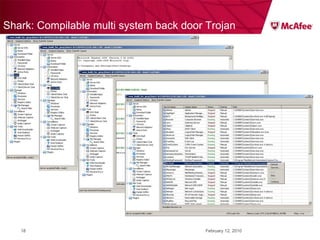
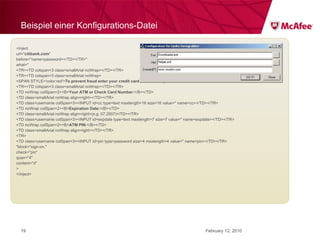
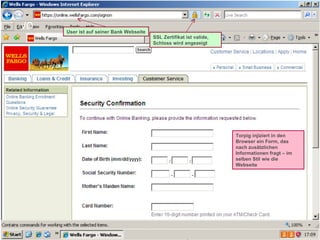

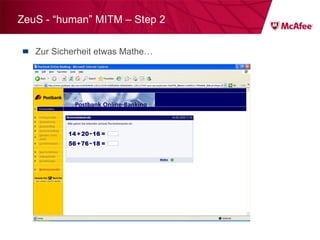
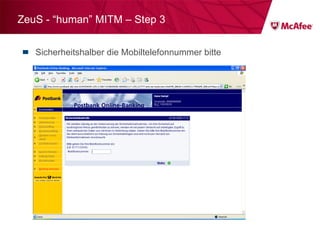
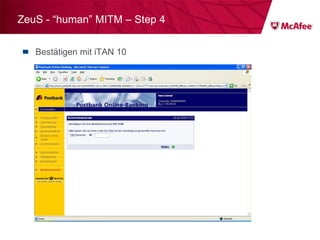
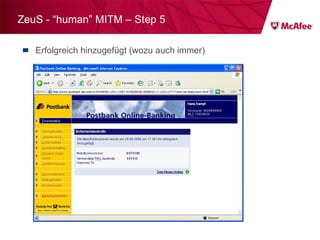
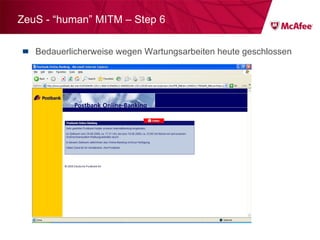
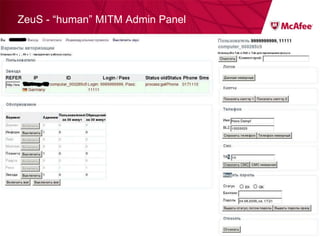
![ZeuS – mit Instant Messaging ZeuS Jabber Add-on [im] server=jabber.ru username=glom*** password=qazx***** to=thekl***@jabber.ru to1=icq12***@jabber.ru to2=tank56***@jabber.ru ; name=mask ; mask [keylist] ;key1="login=" key2="injtoken=" key3="inja1=" [list] ;test1=*onlineeast*.bankofamerica.com*](https://image.slidesharecdn.com/091209mcafeeroundtable-100212081624-phpapp01/85/091209-Mc-Afee-Roundtable-36-320.jpg)