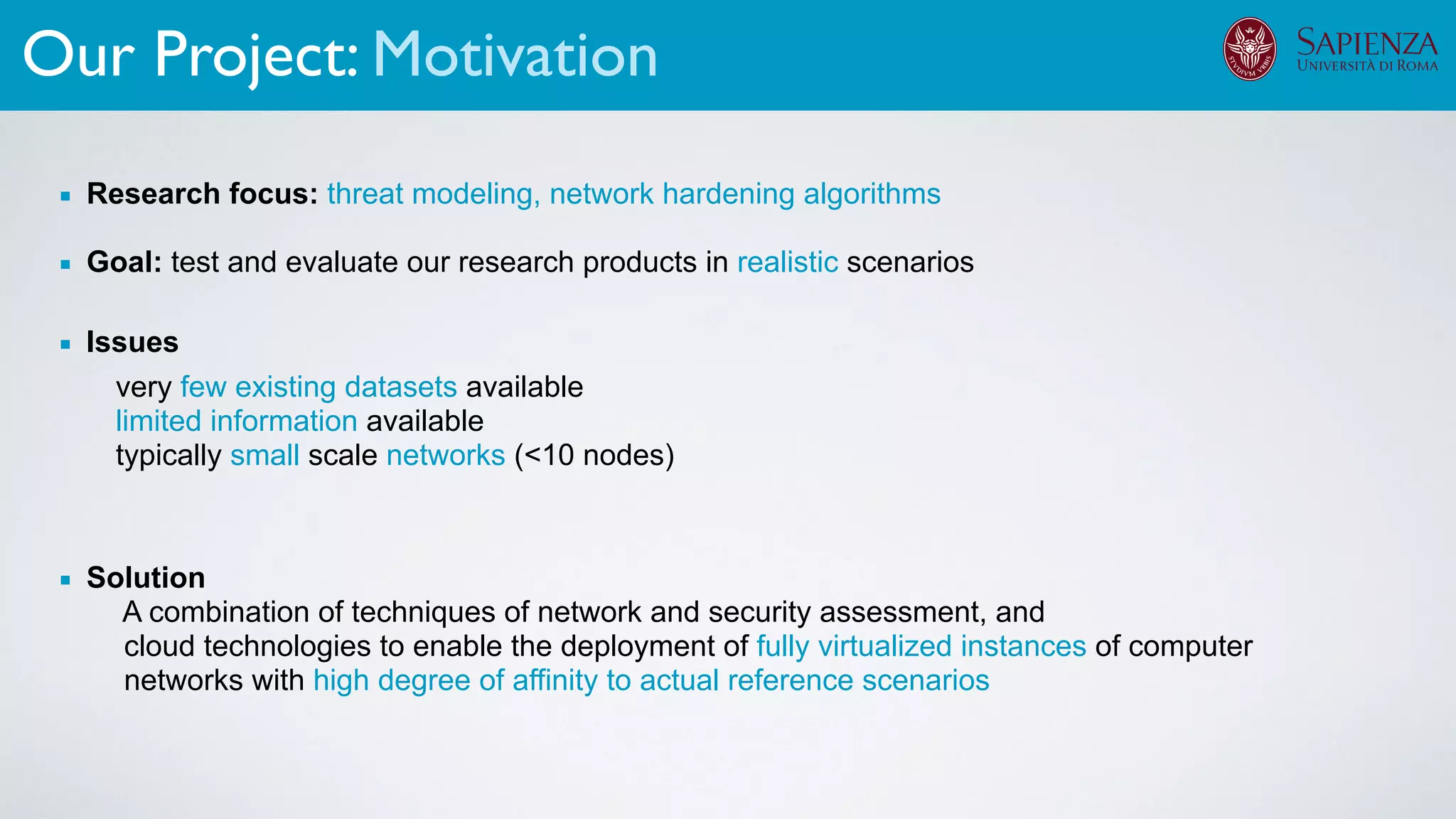
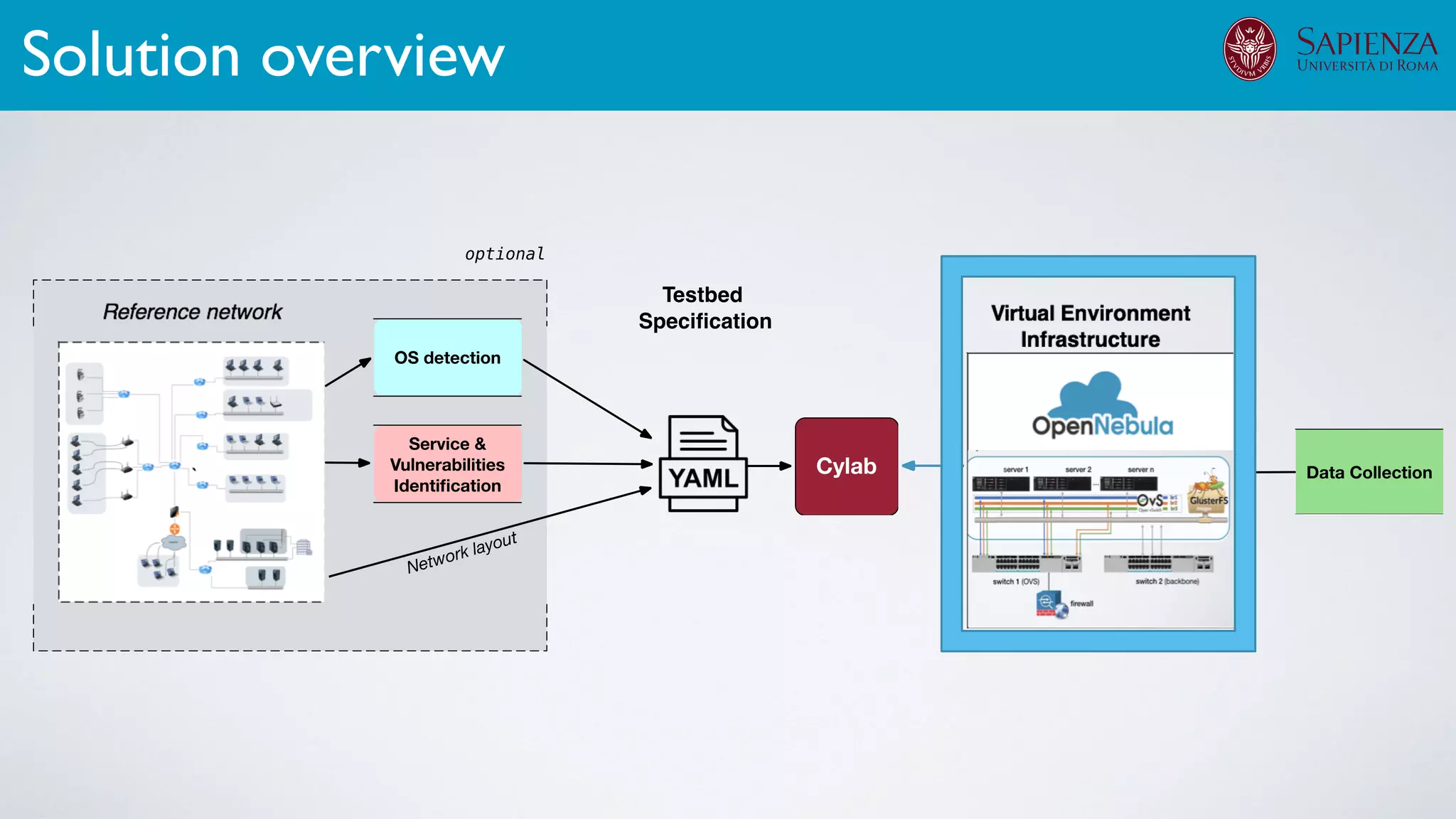
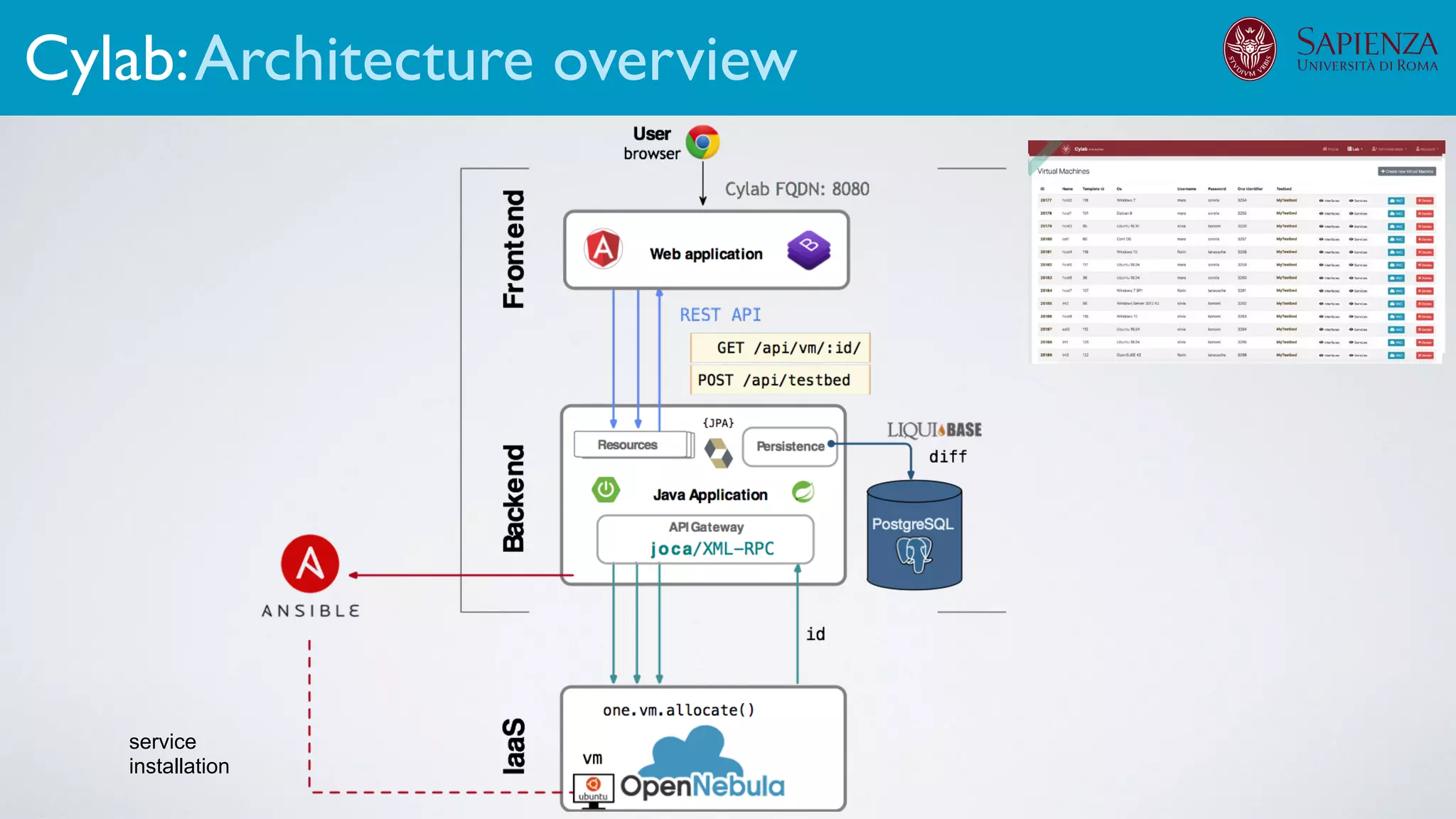
The document discusses the development of virtual environments, or cyber ranges, to analyze the security of complex networked systems amid increasingly sophisticated cyber attacks. It emphasizes the importance of realistic scenarios for security testing and personnel training, as well as the need for effective threat modeling and network hardening. The project aims to create a flexible, automated testbed utilizing cloud technologies and open-source solutions, while addressing data collection and analysis of various cyber scenarios.










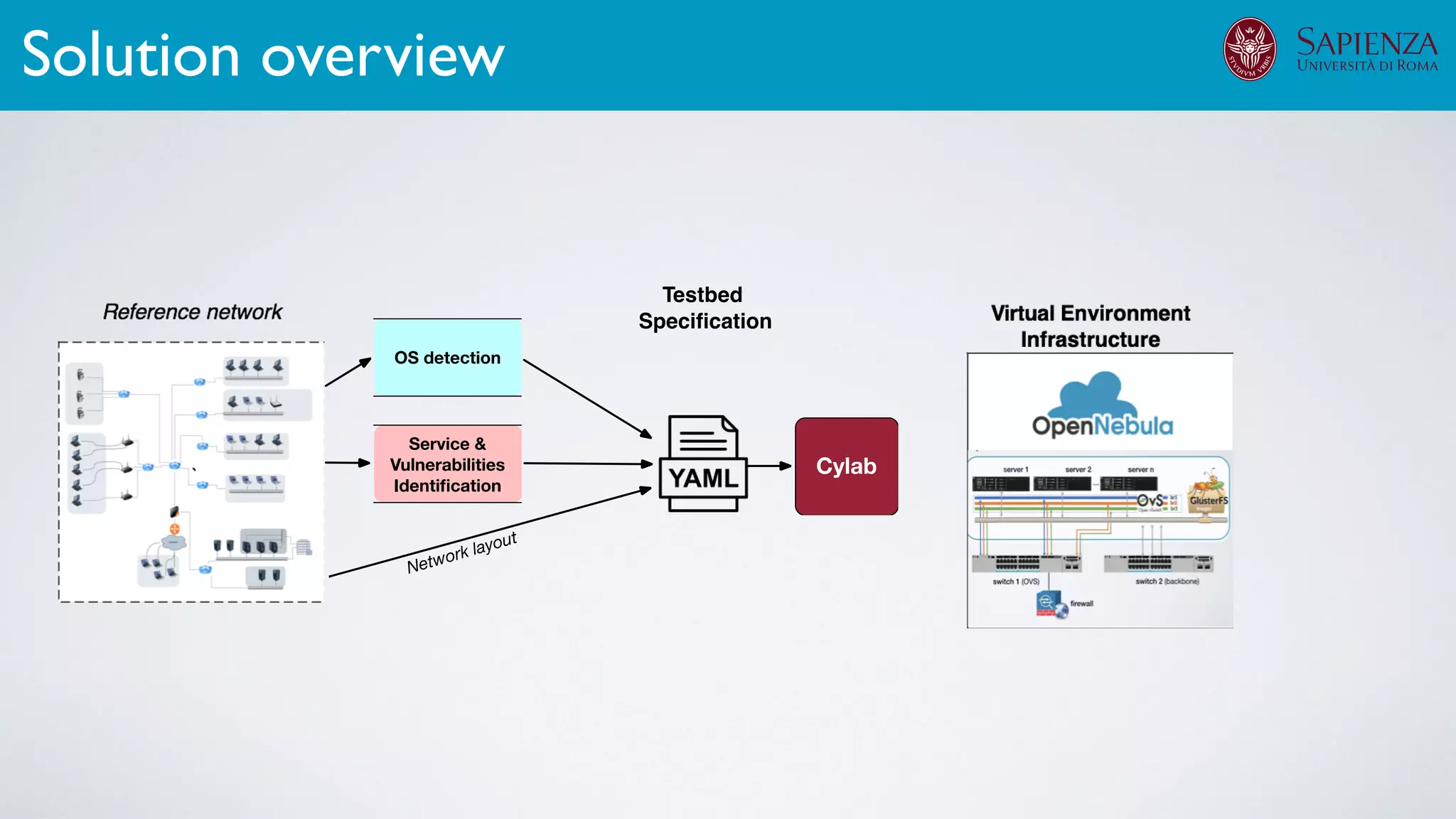


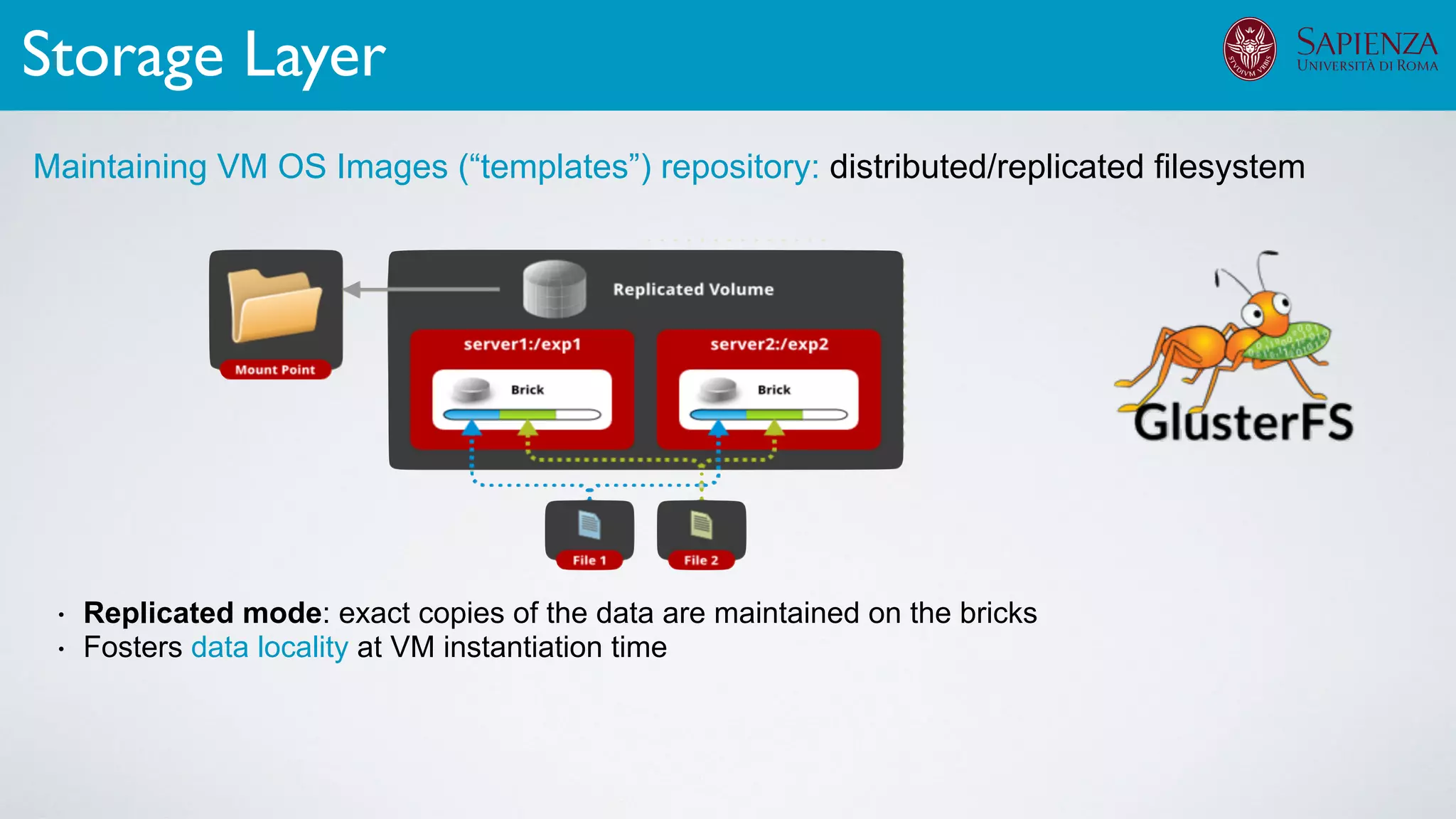


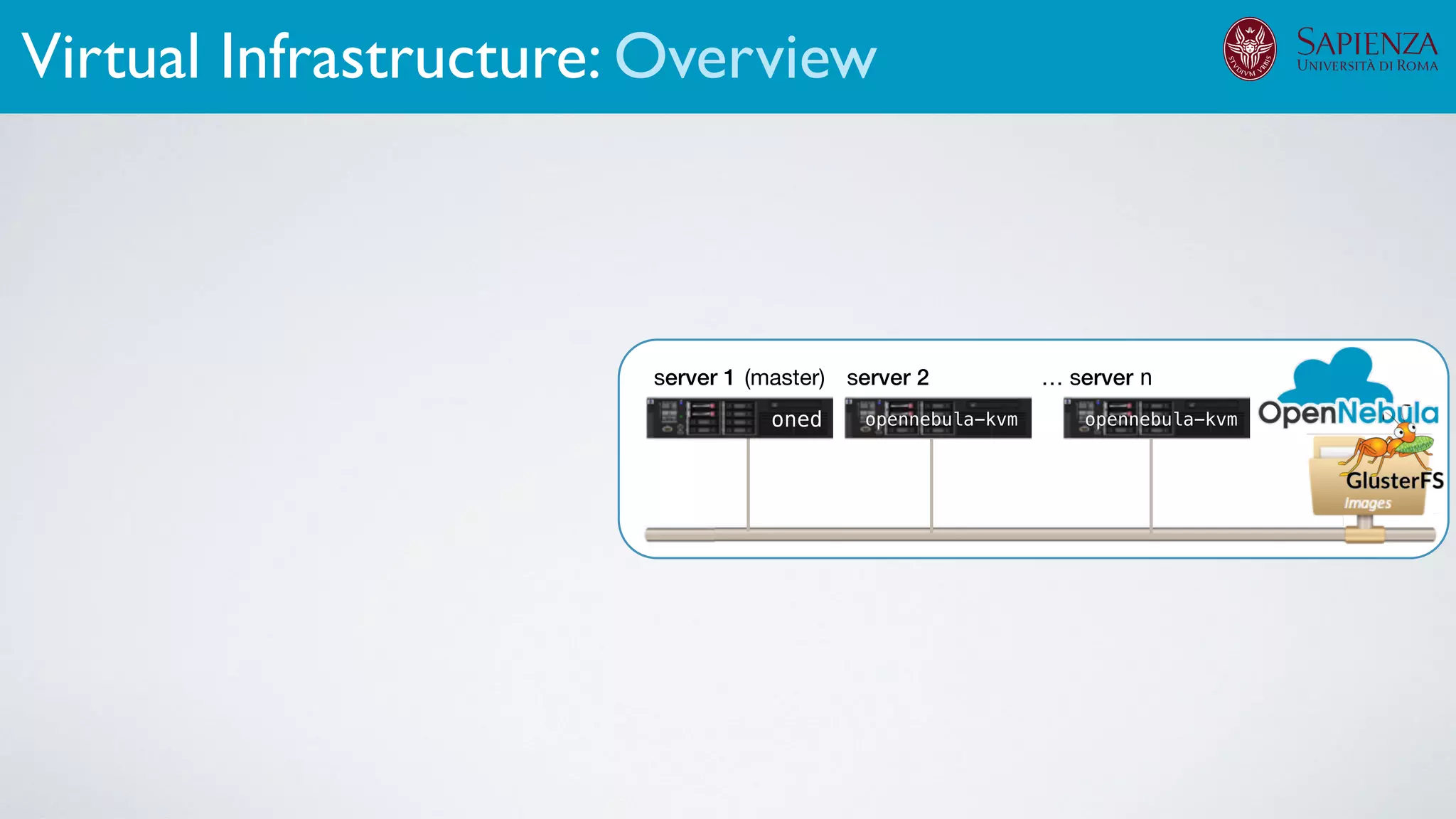
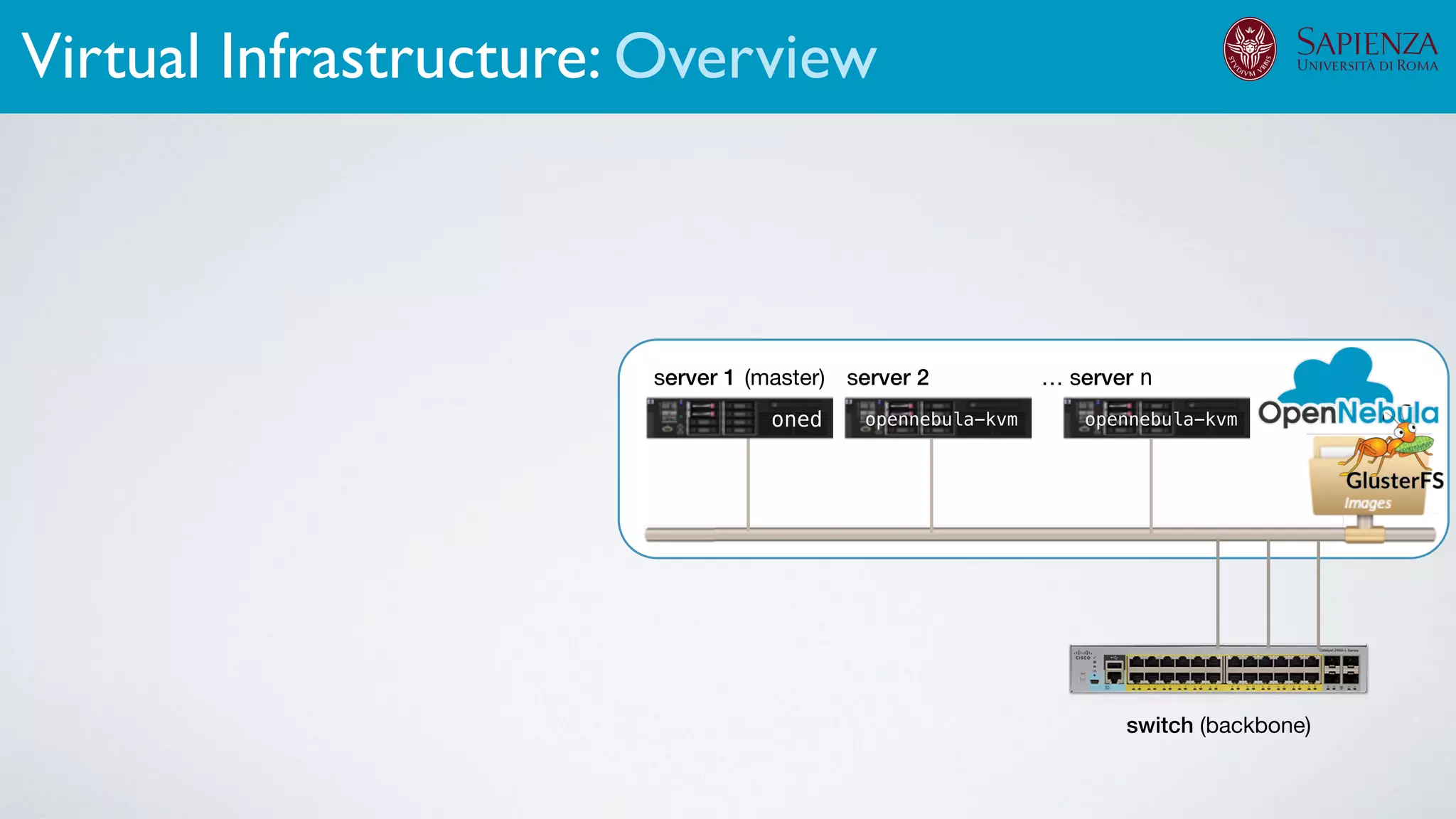
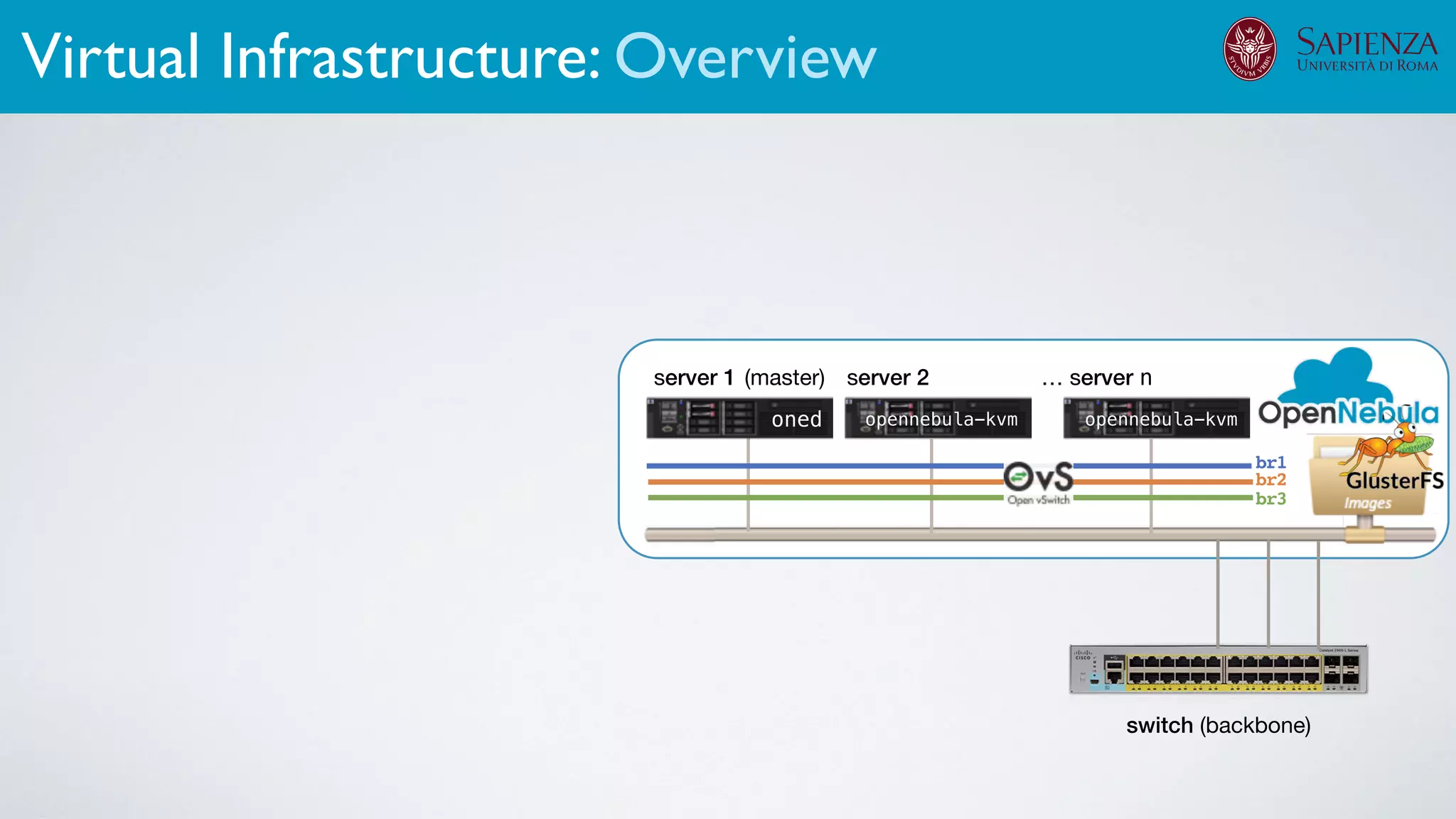
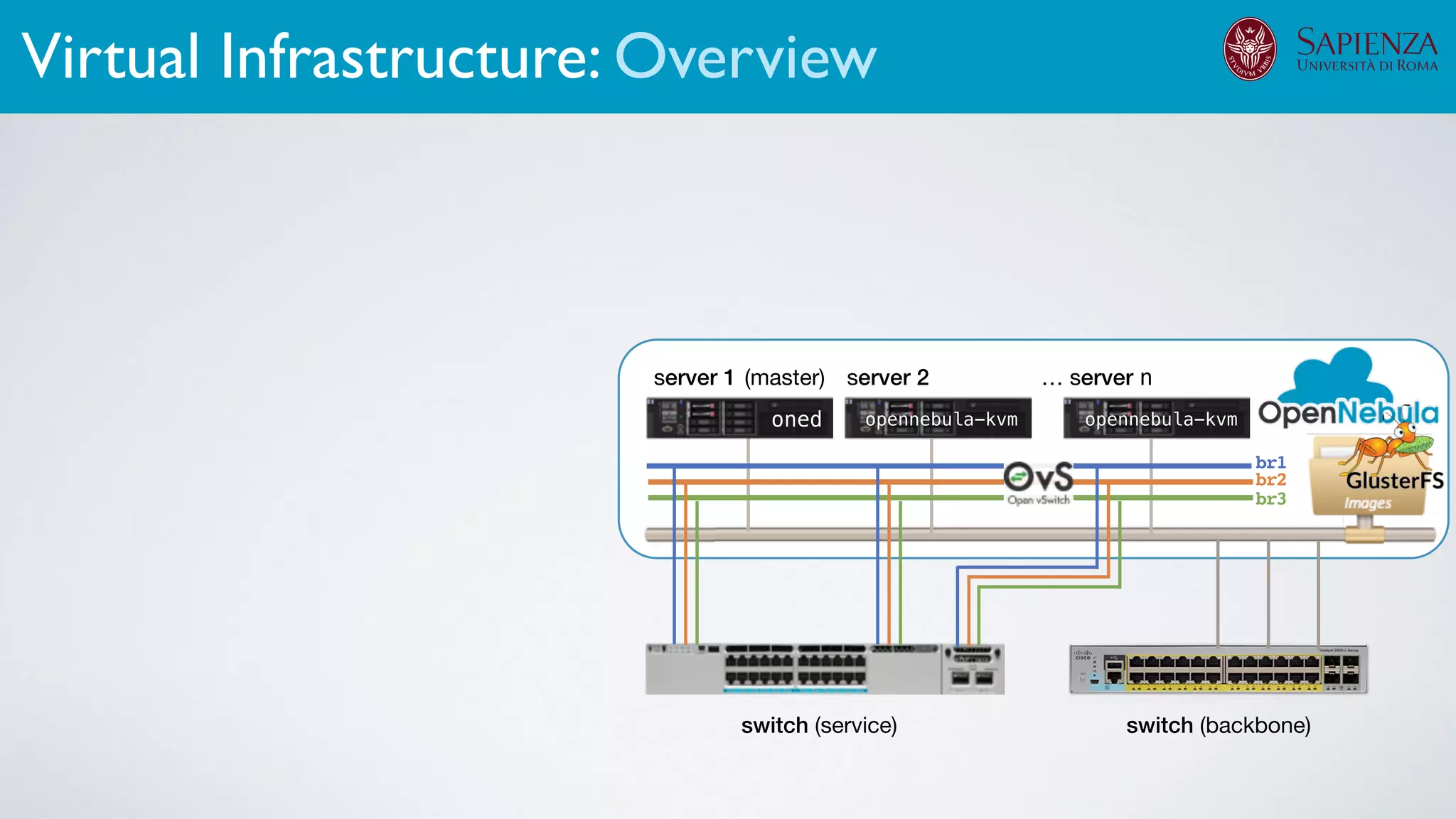
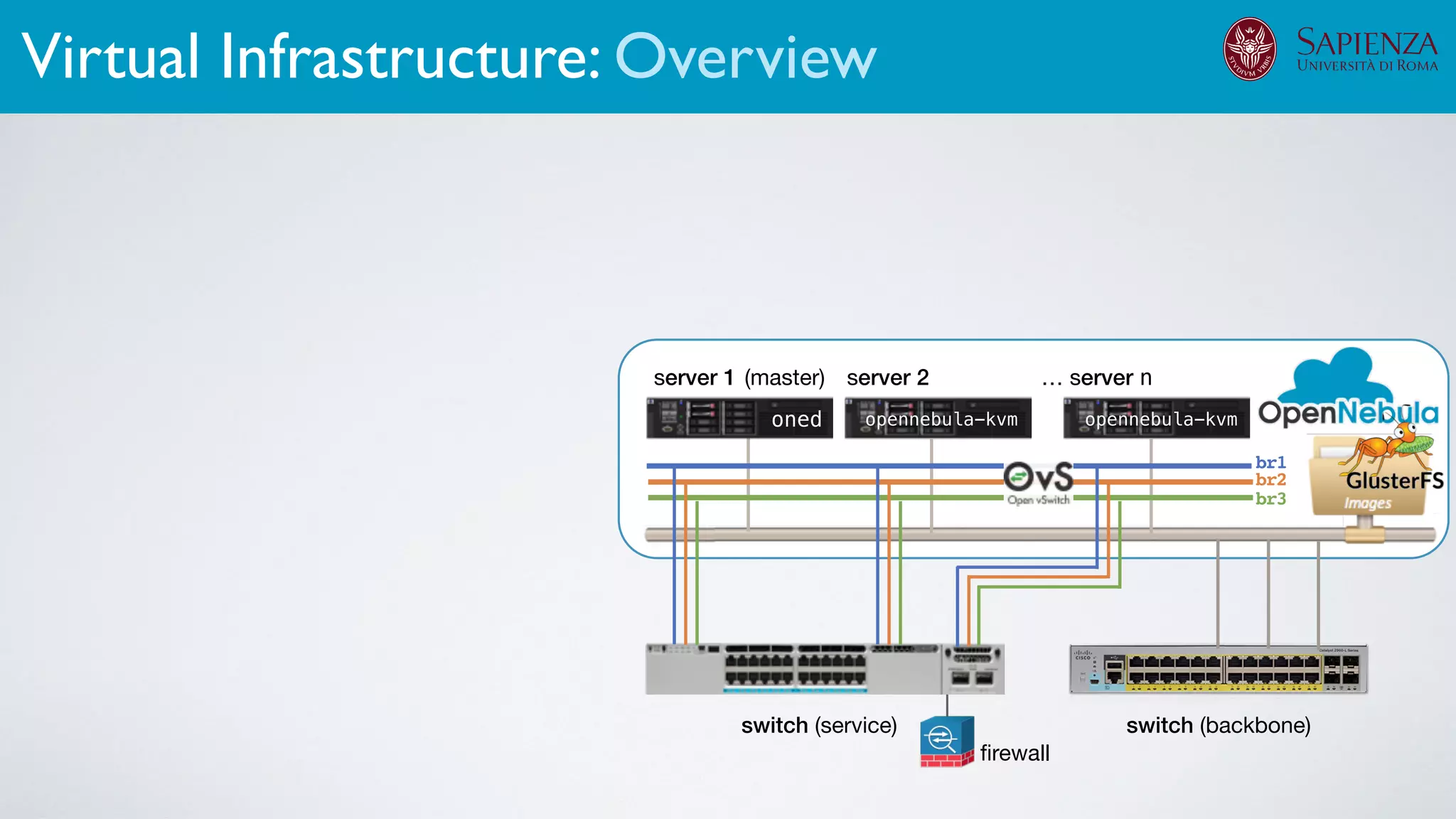
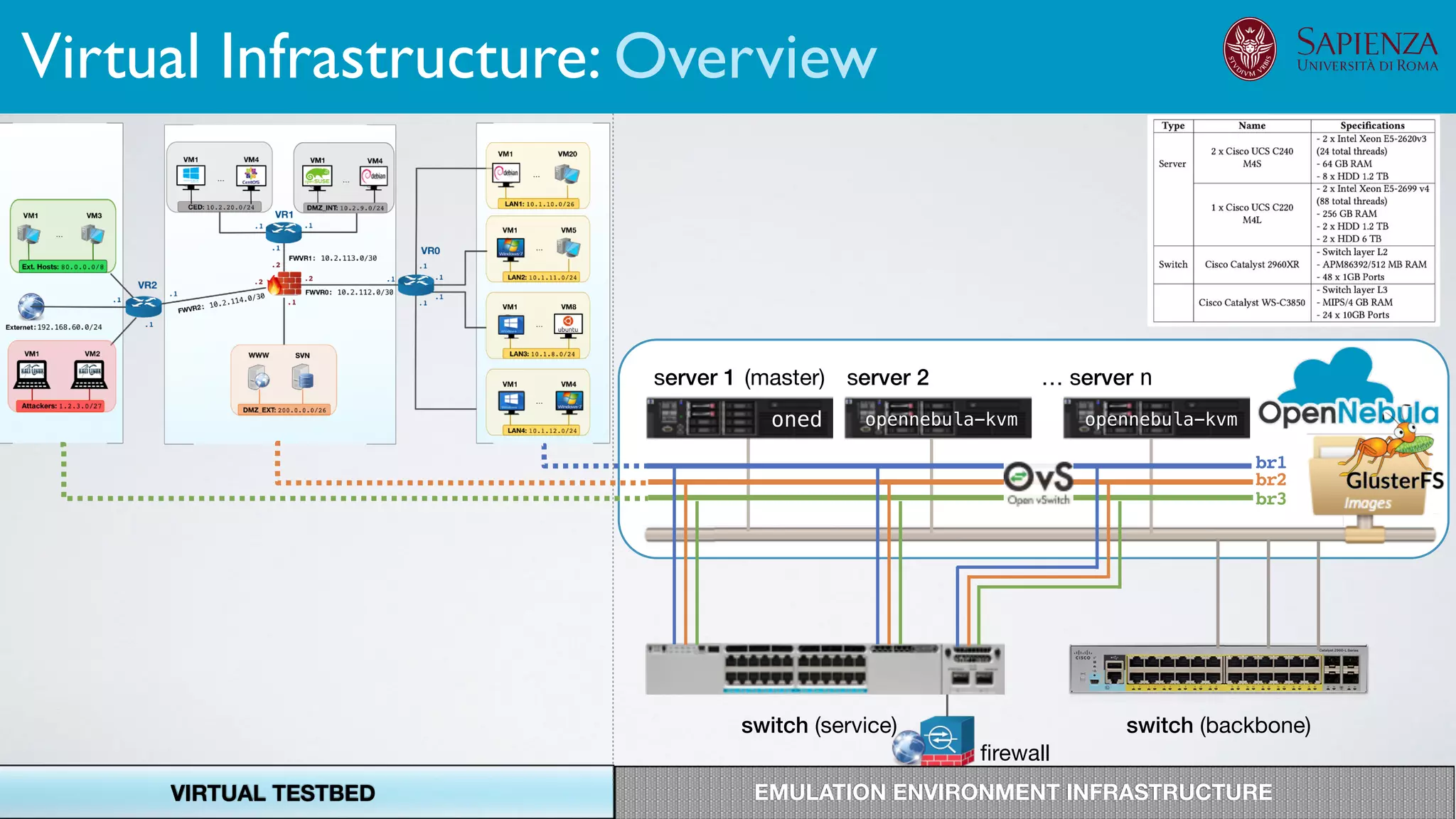

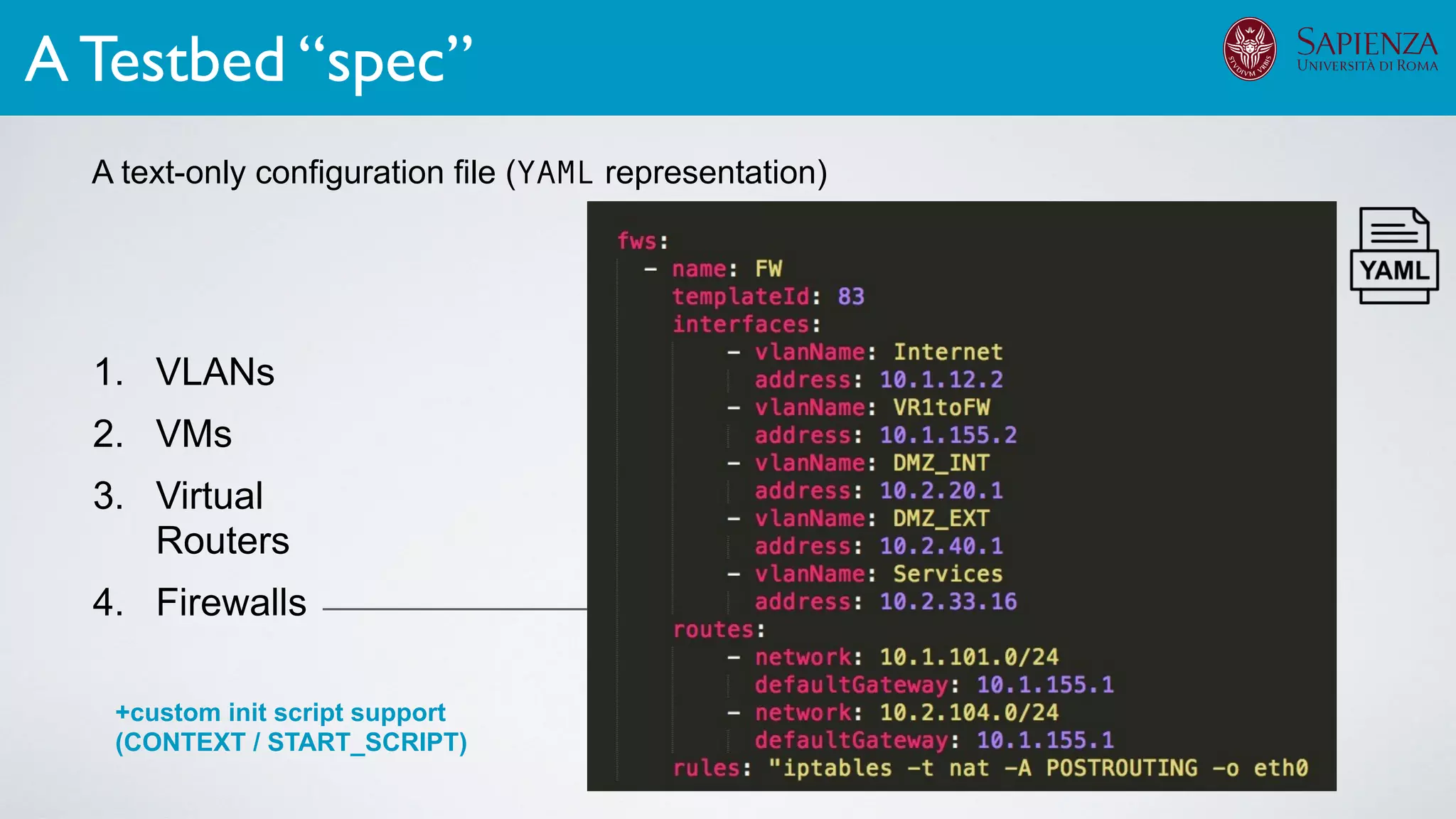
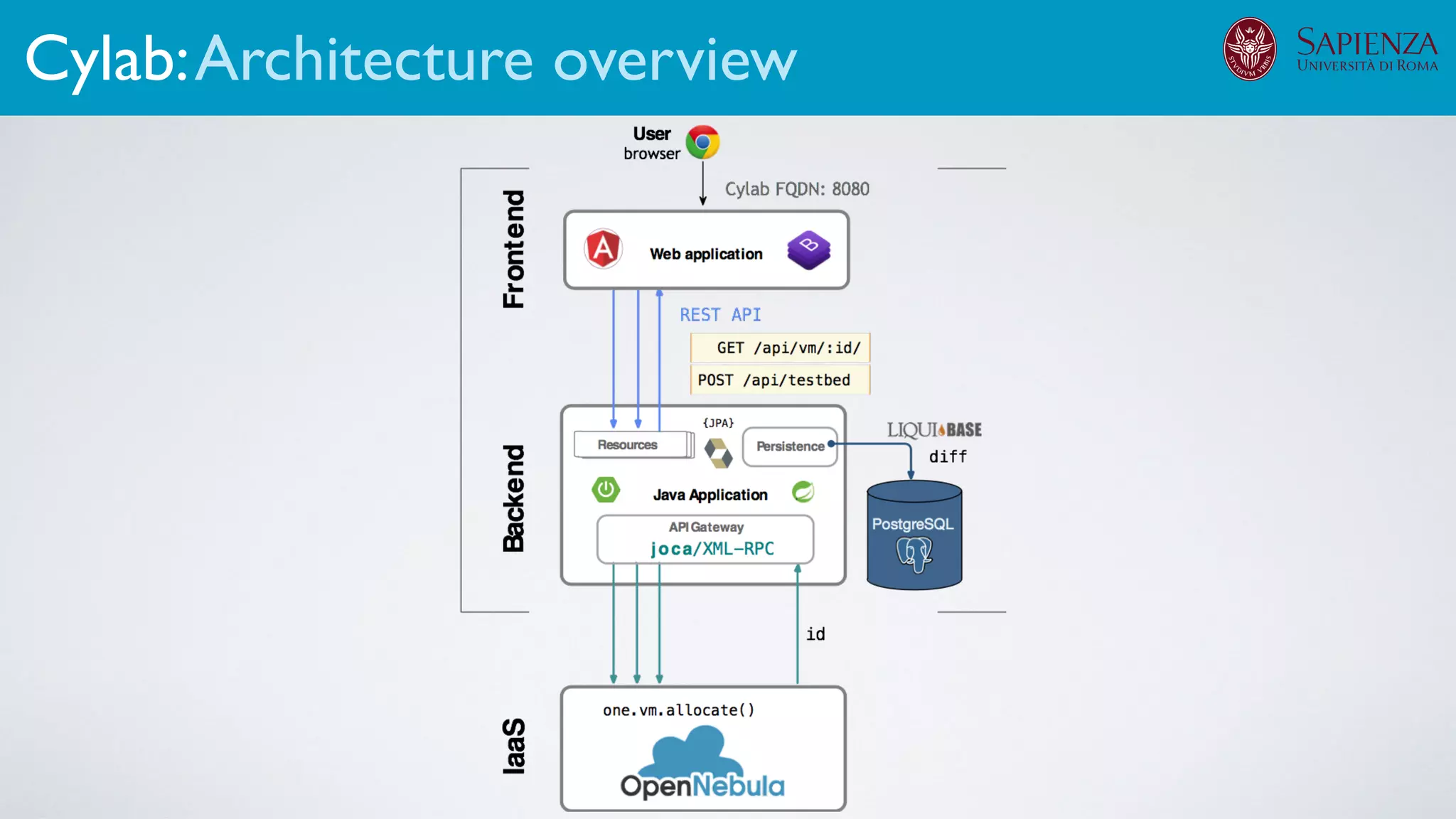
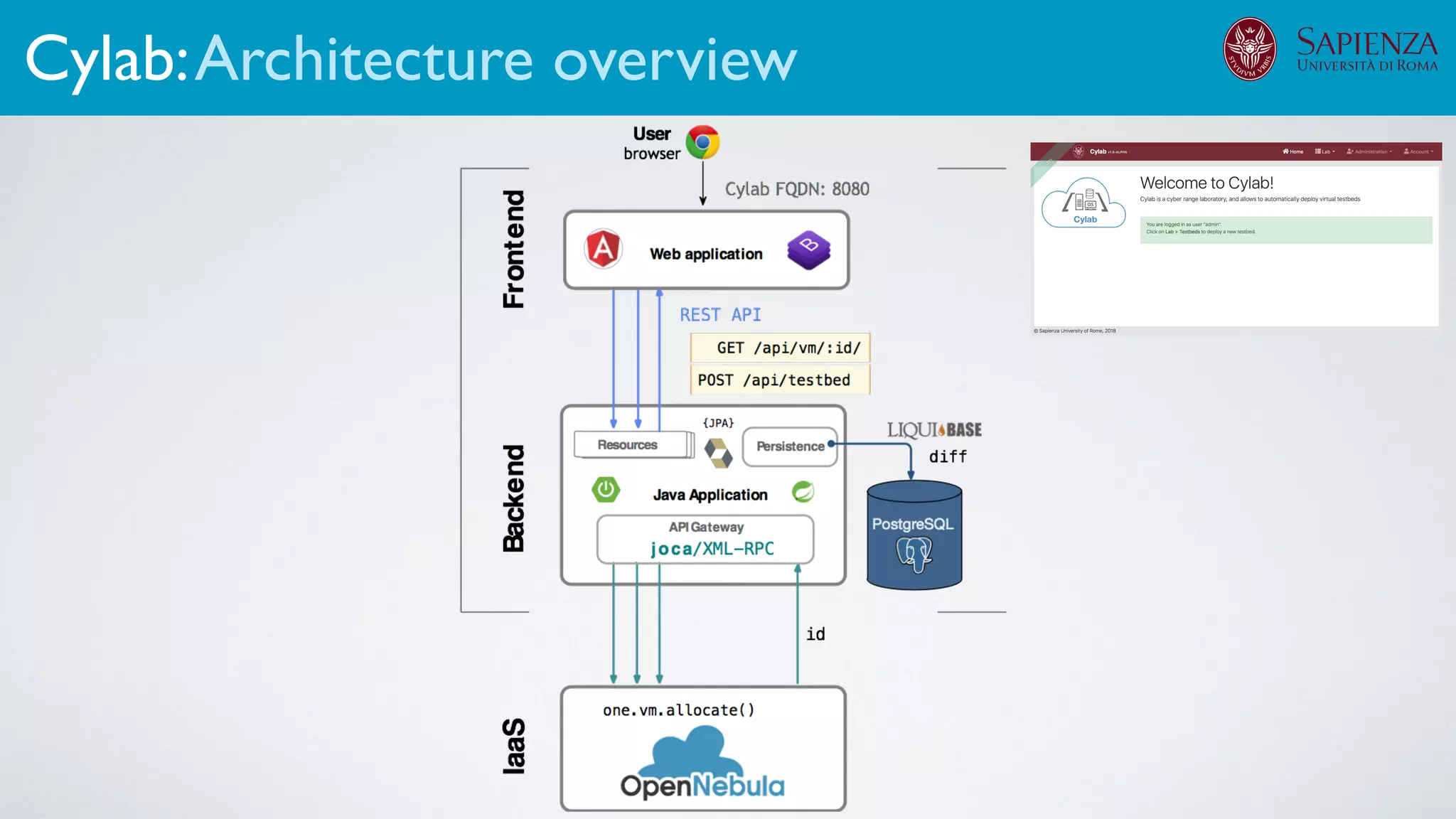
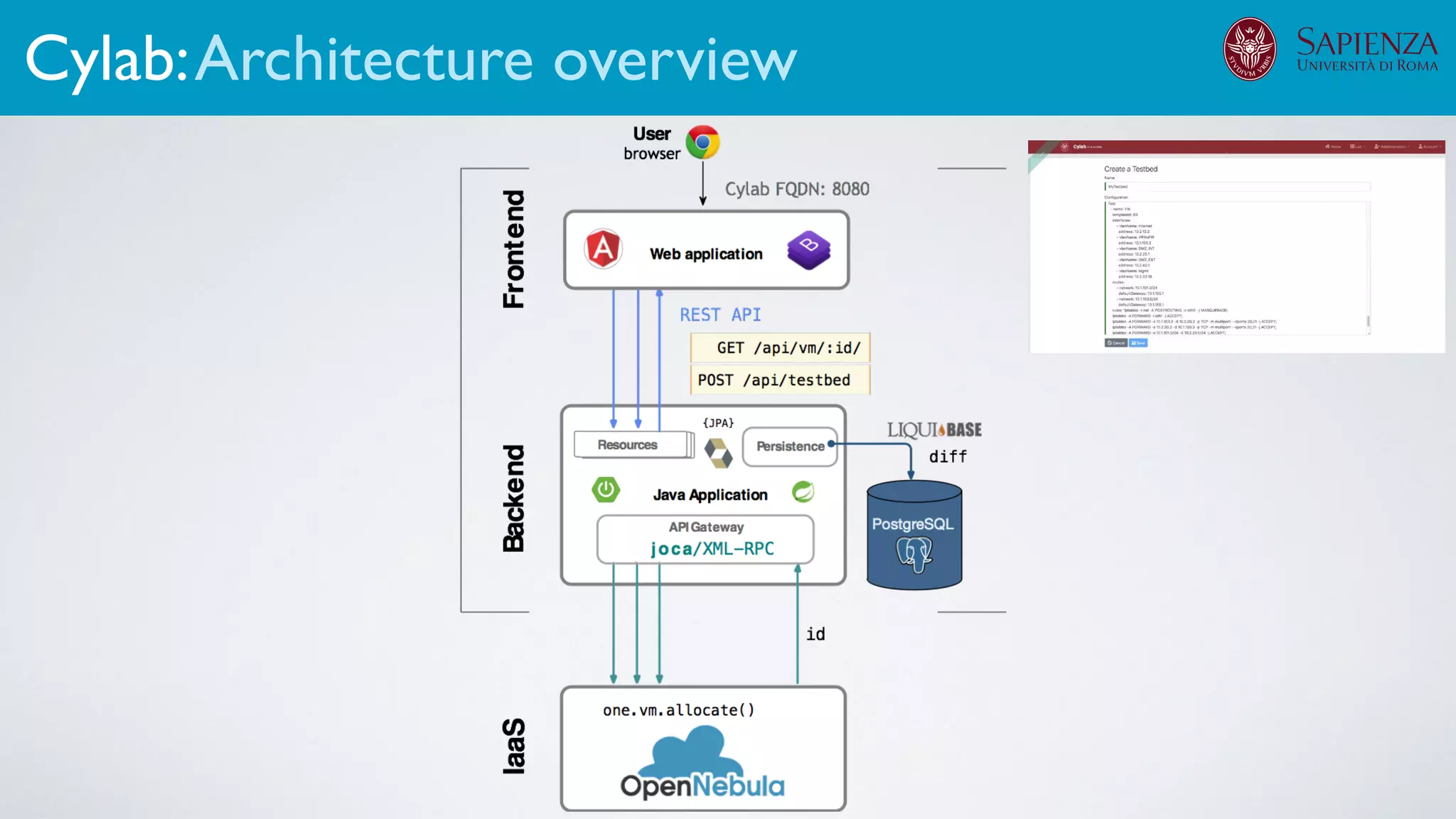

![[ICDCN ‘19] Tanasache, Sorella, Bonomi, Rapone, Meacci. Building an emulation environment for cyber security analyses of complex networked systems
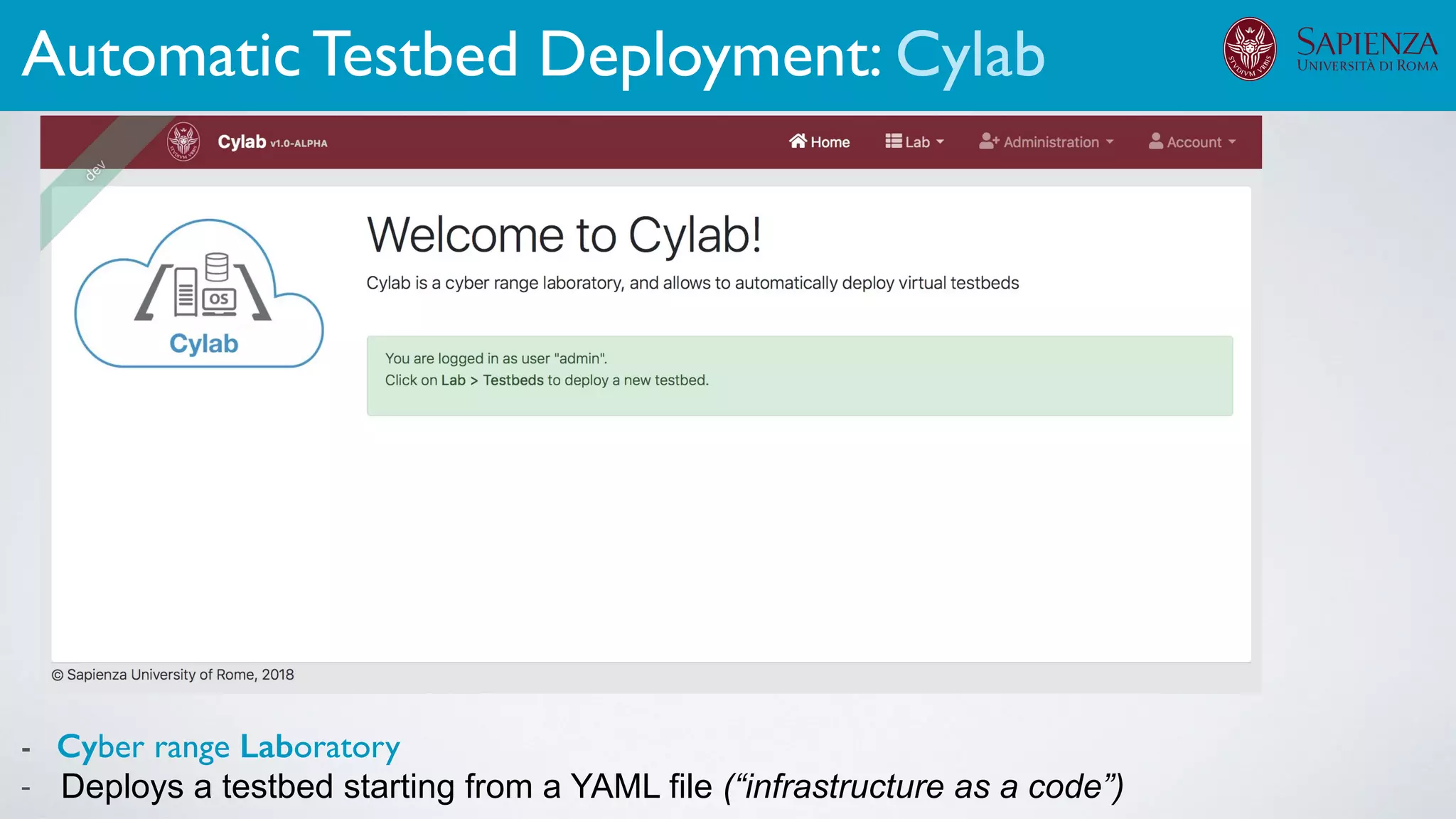
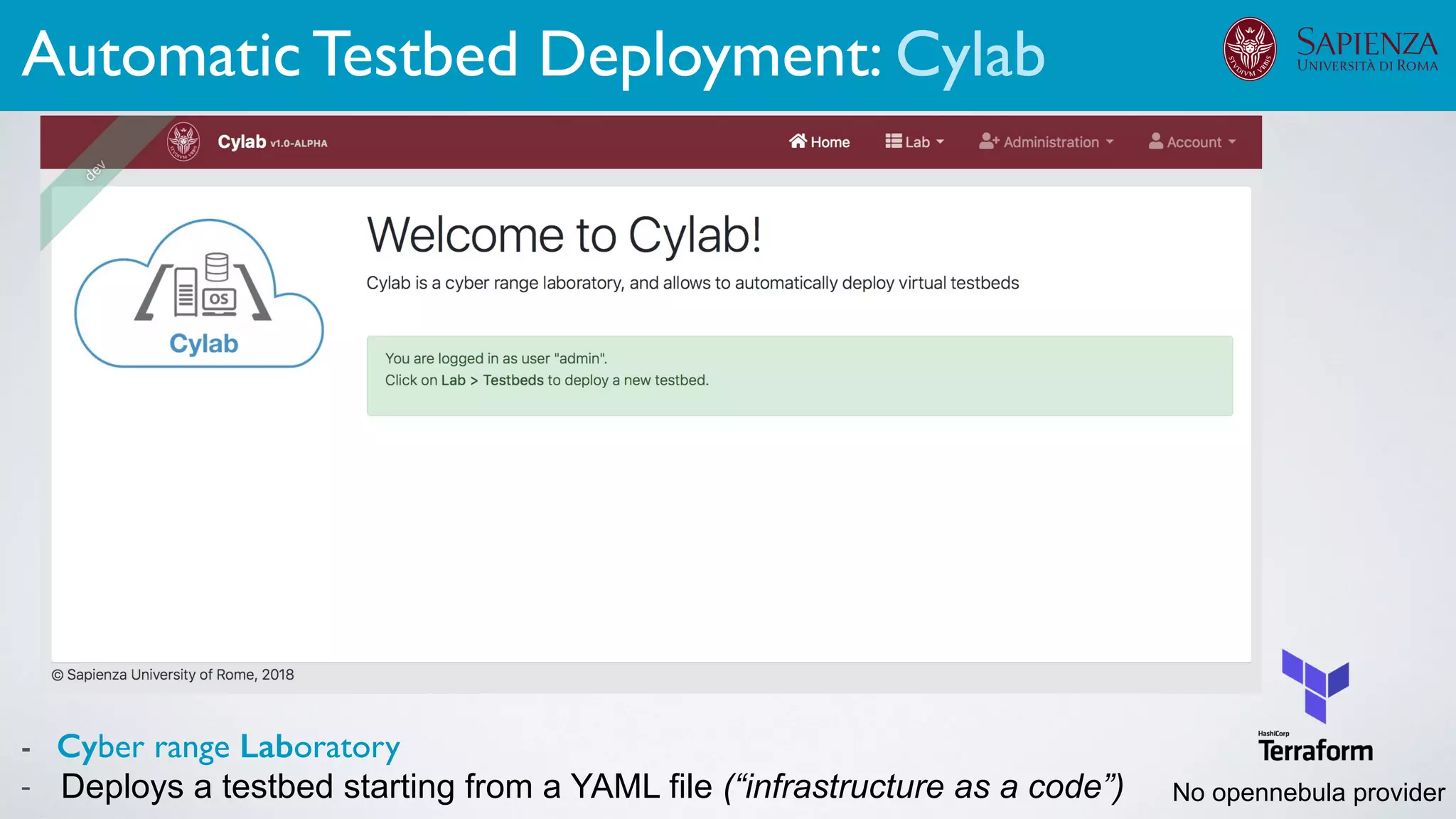
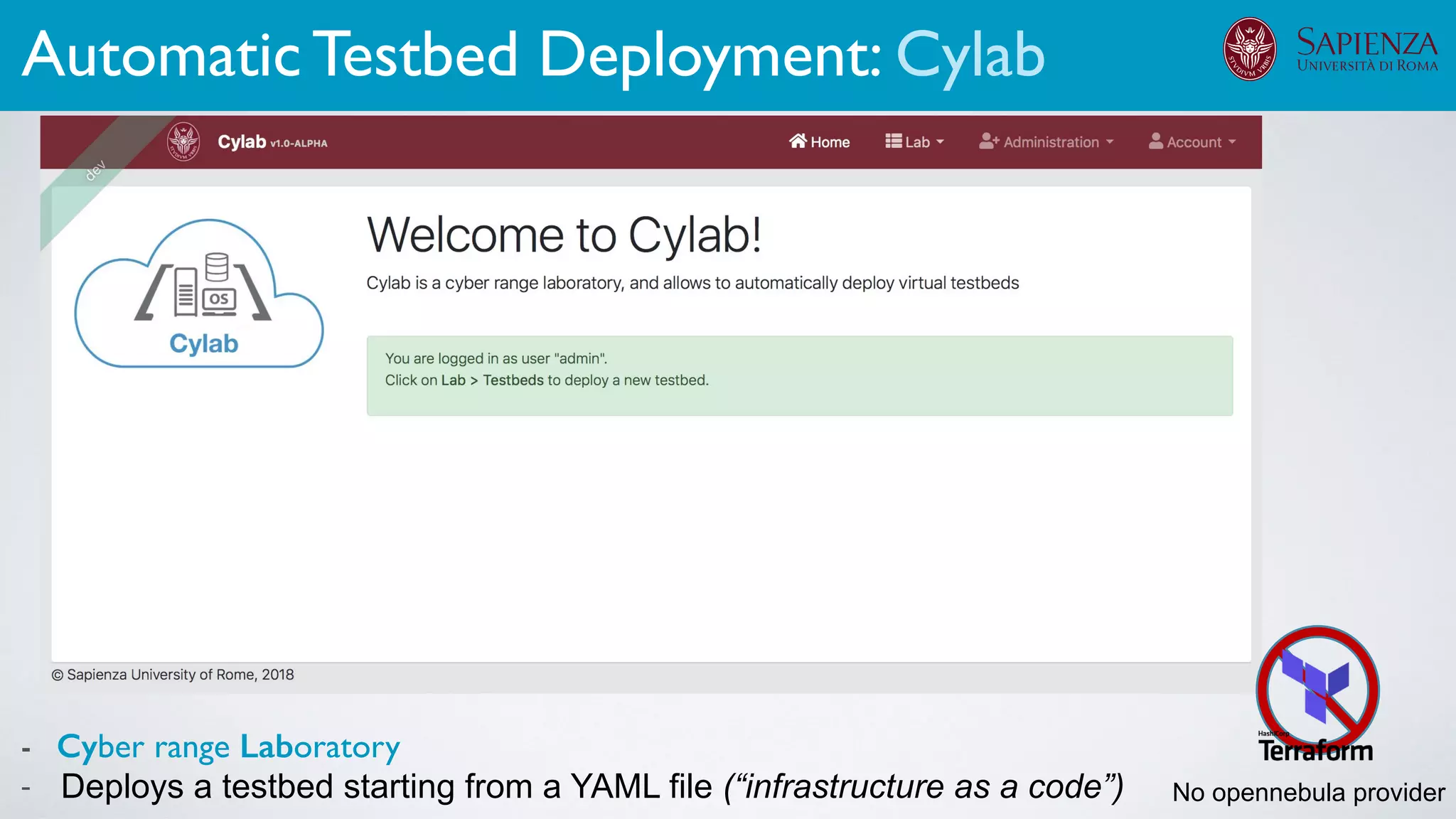
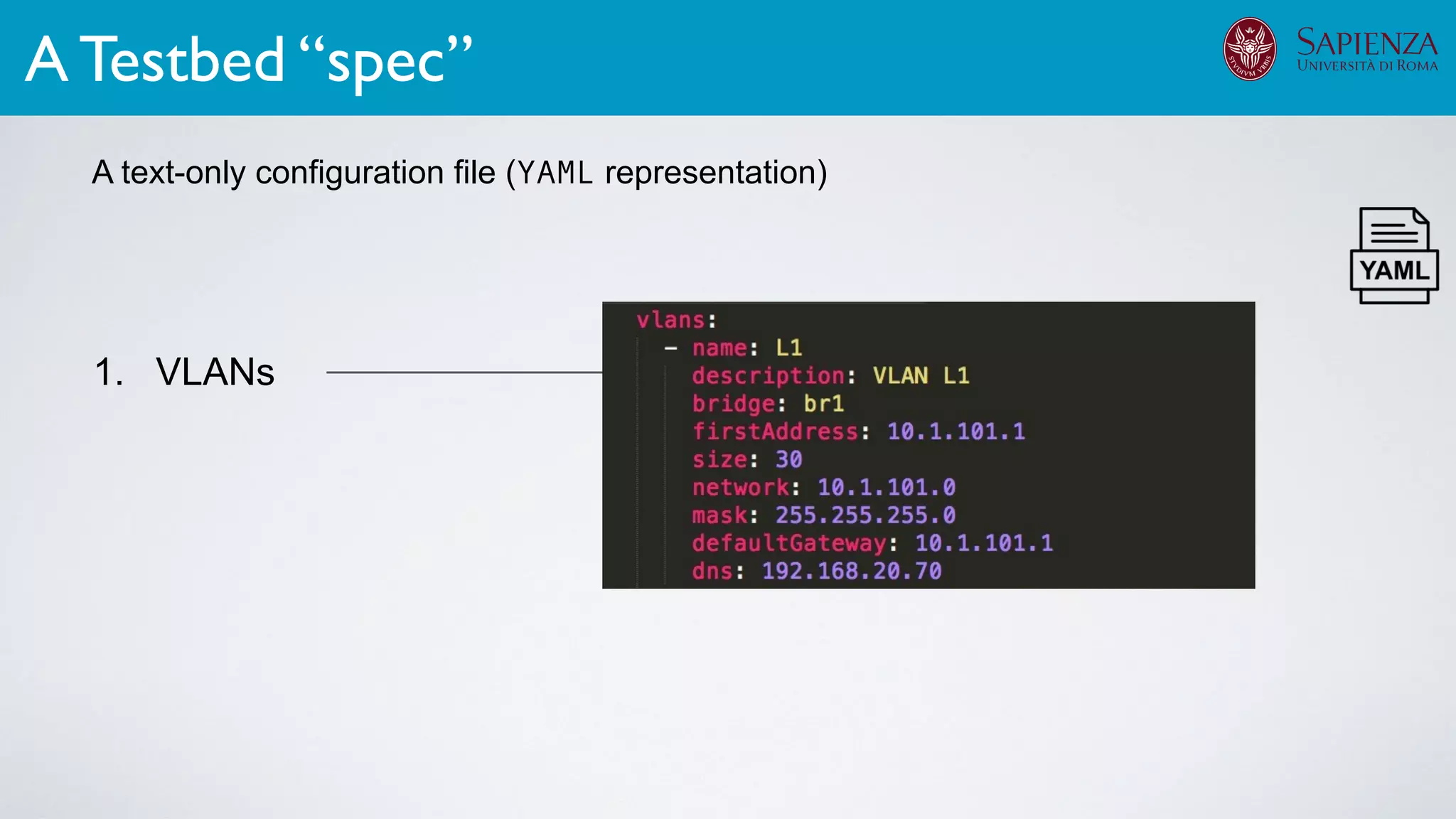
1. Cyber-range deployment for security training and testing
• cyber security scenario awareness
• incident management (detection, investigation, response)
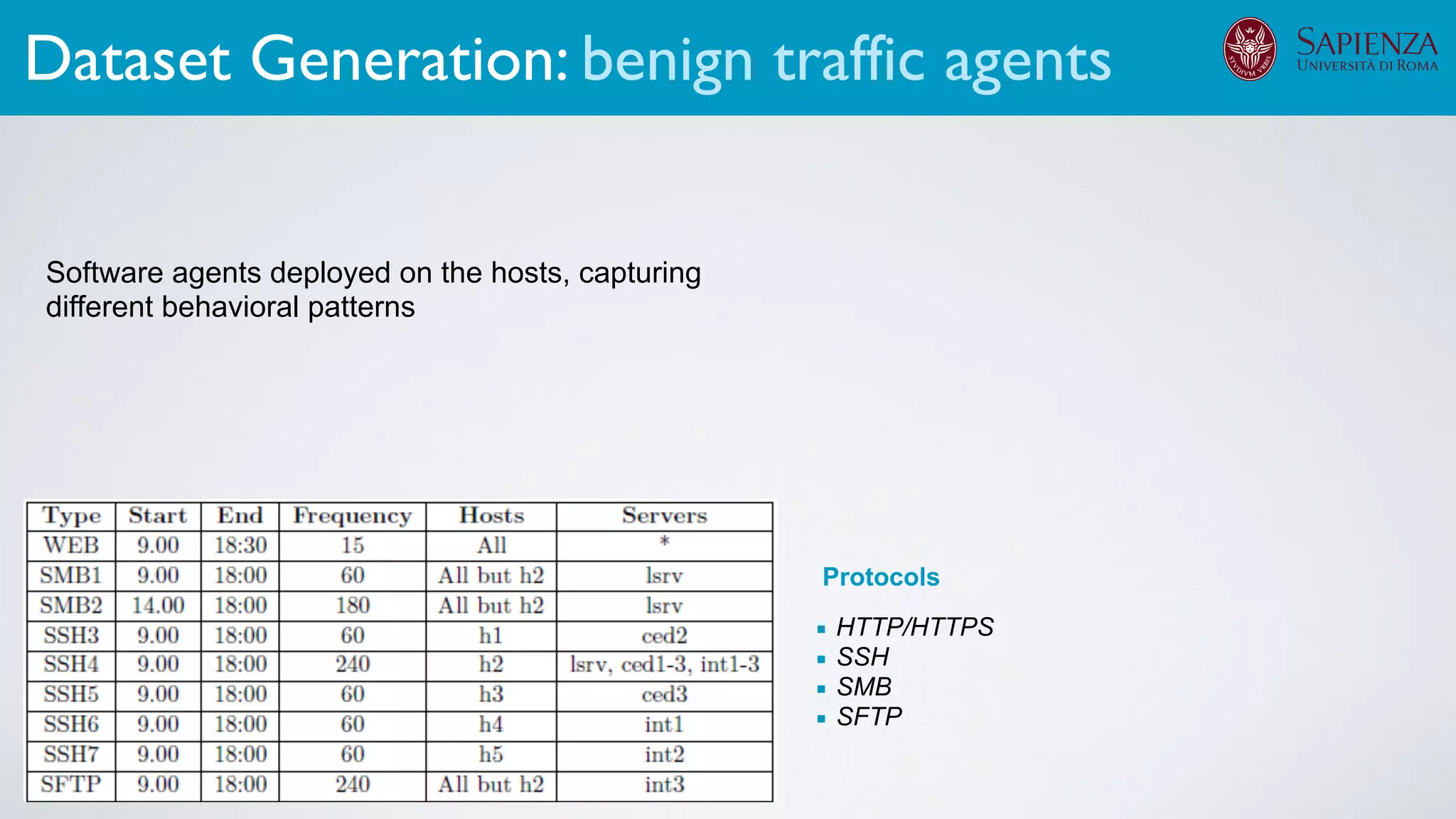
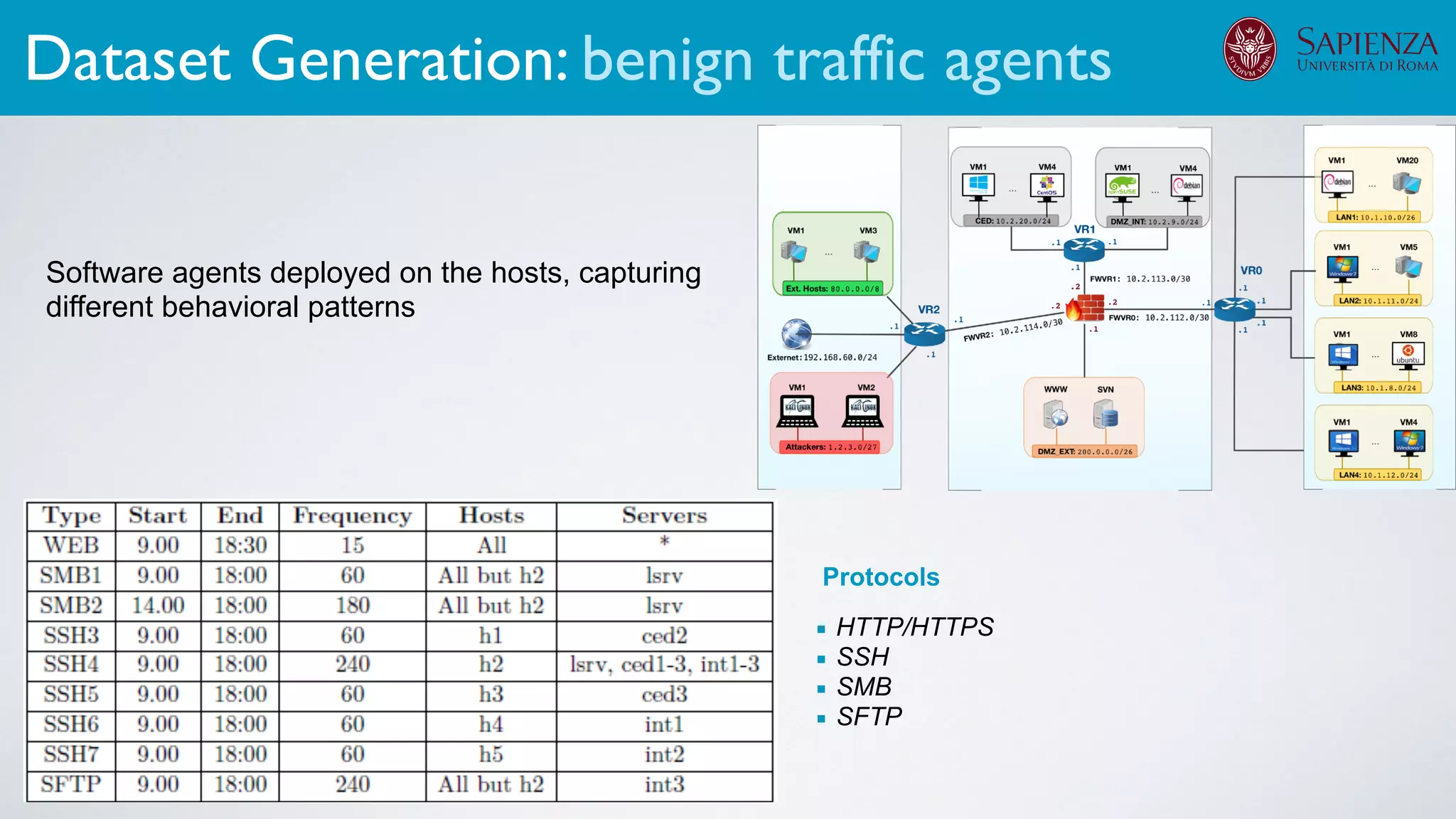
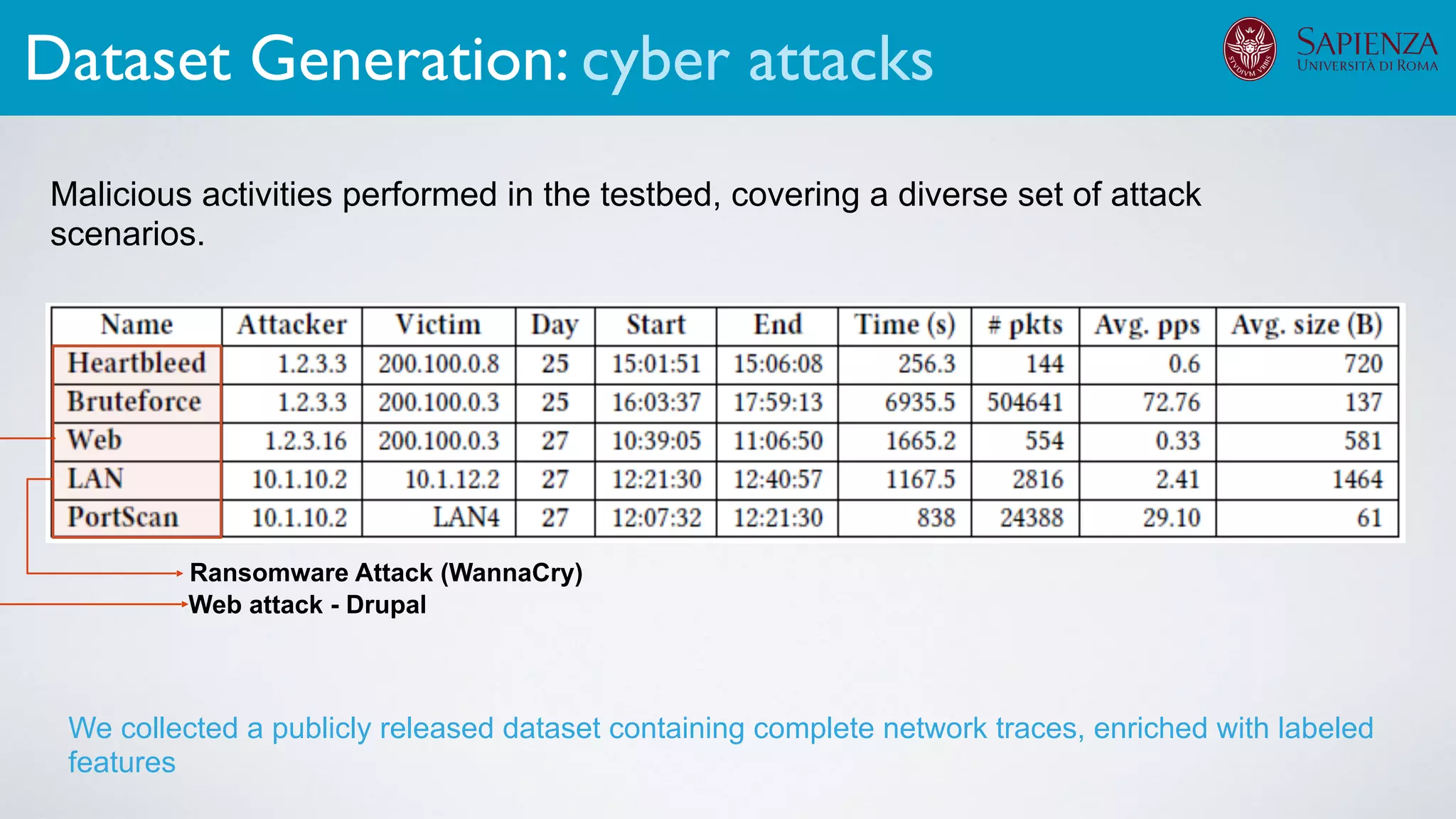
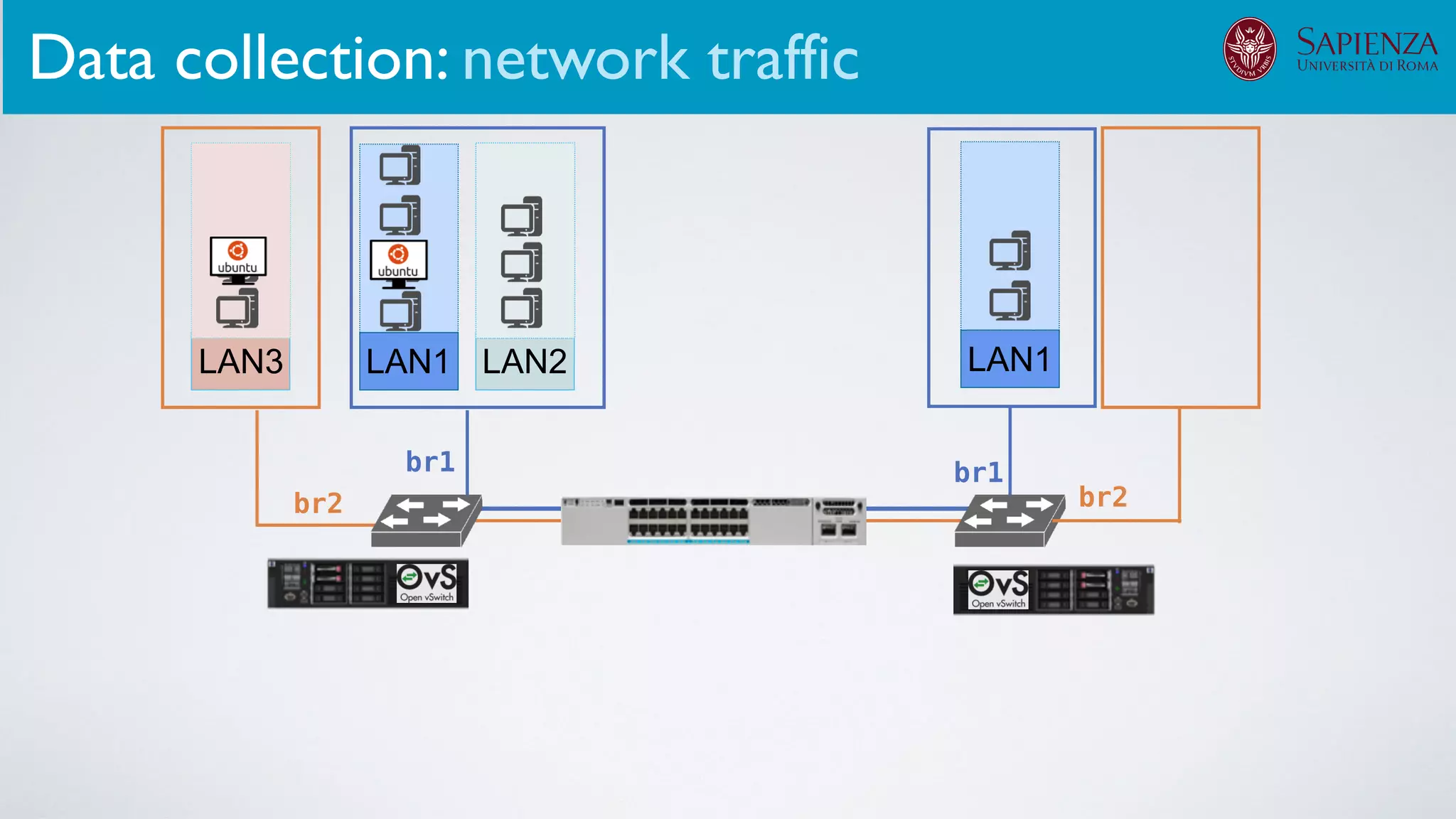
2. Dataset generation
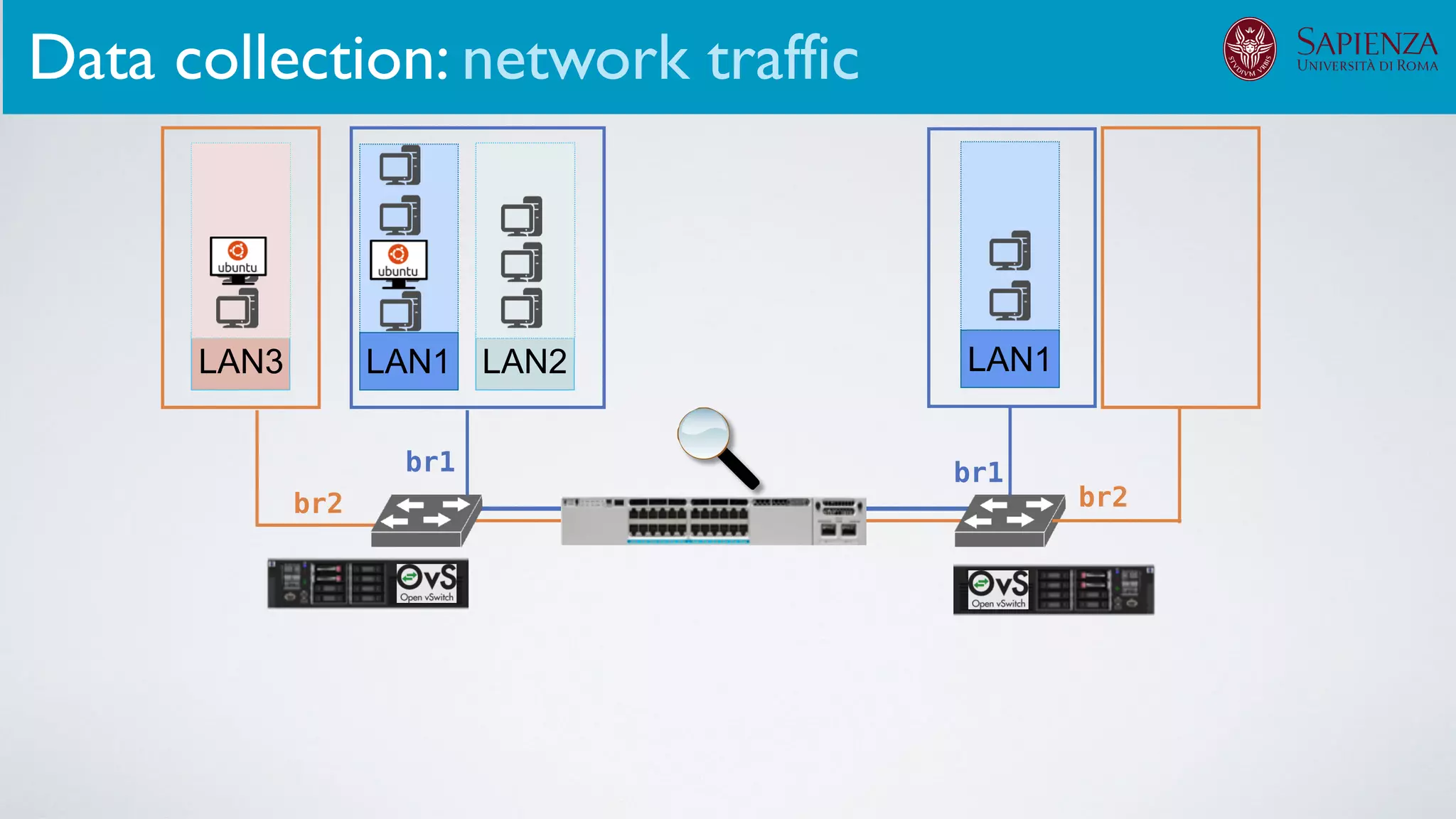
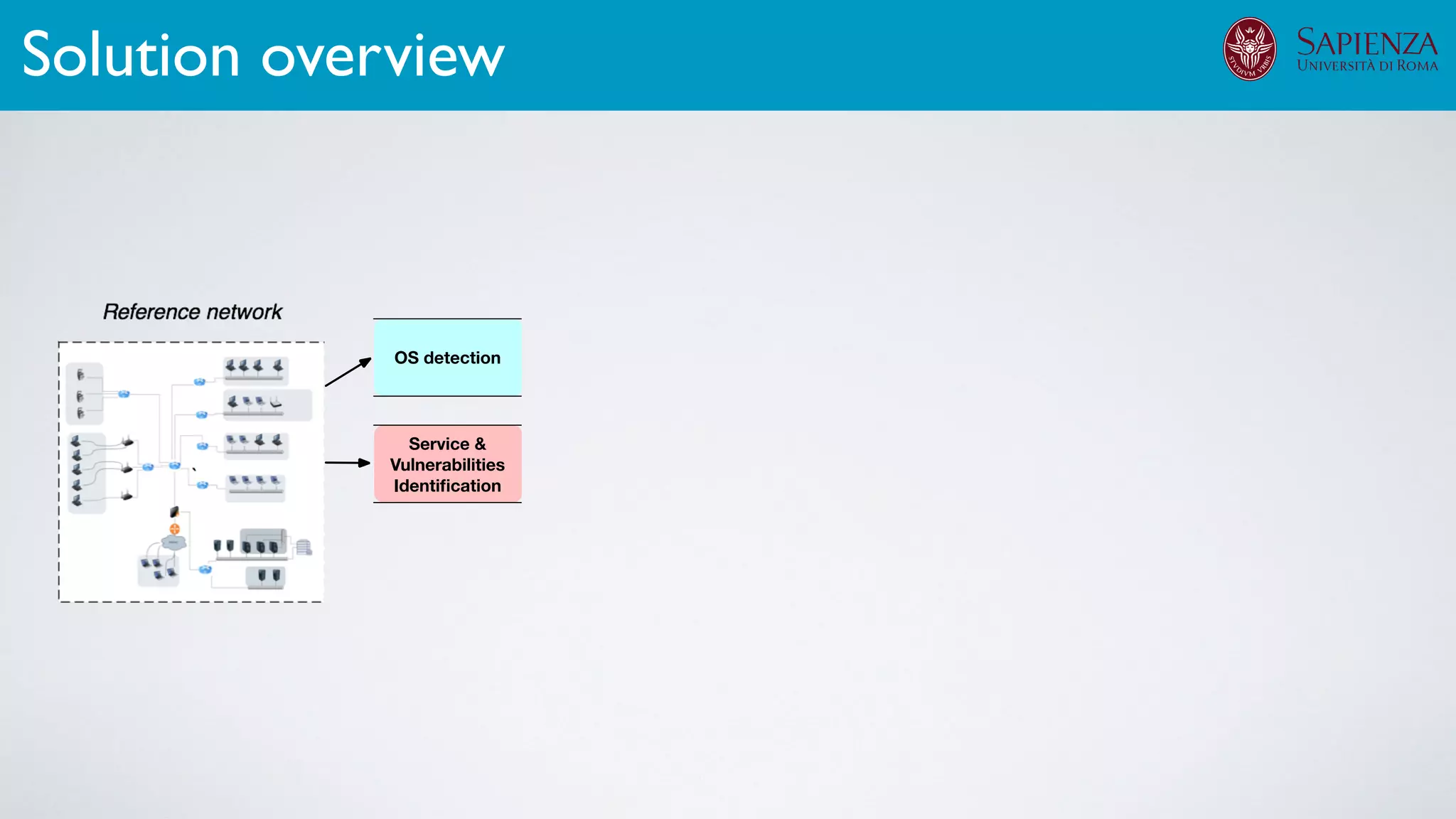
The infrastructure can support various activities
case study [ICDCN ‘19]
Applications: Overview](https://image.slidesharecdn.com/opennebulaconf2019univroma-191027214504/75/OpenNebulaConf2019-Building-Virtual-Environments-for-Security-Analyses-of-Complex-Networked-Systems-Mara-Sorella-Sapienza-Univ-of-Rome-60-2048.jpg)
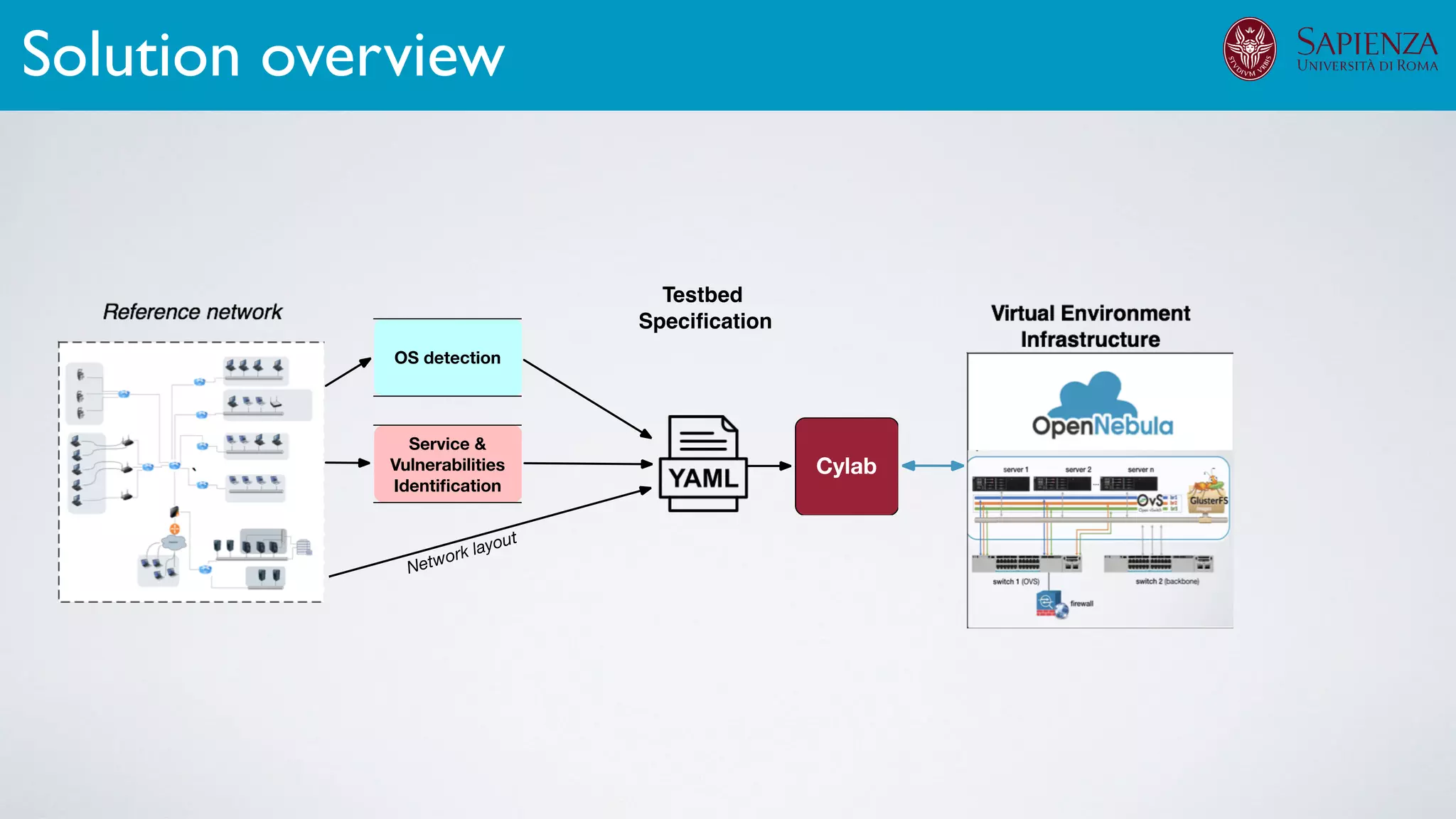
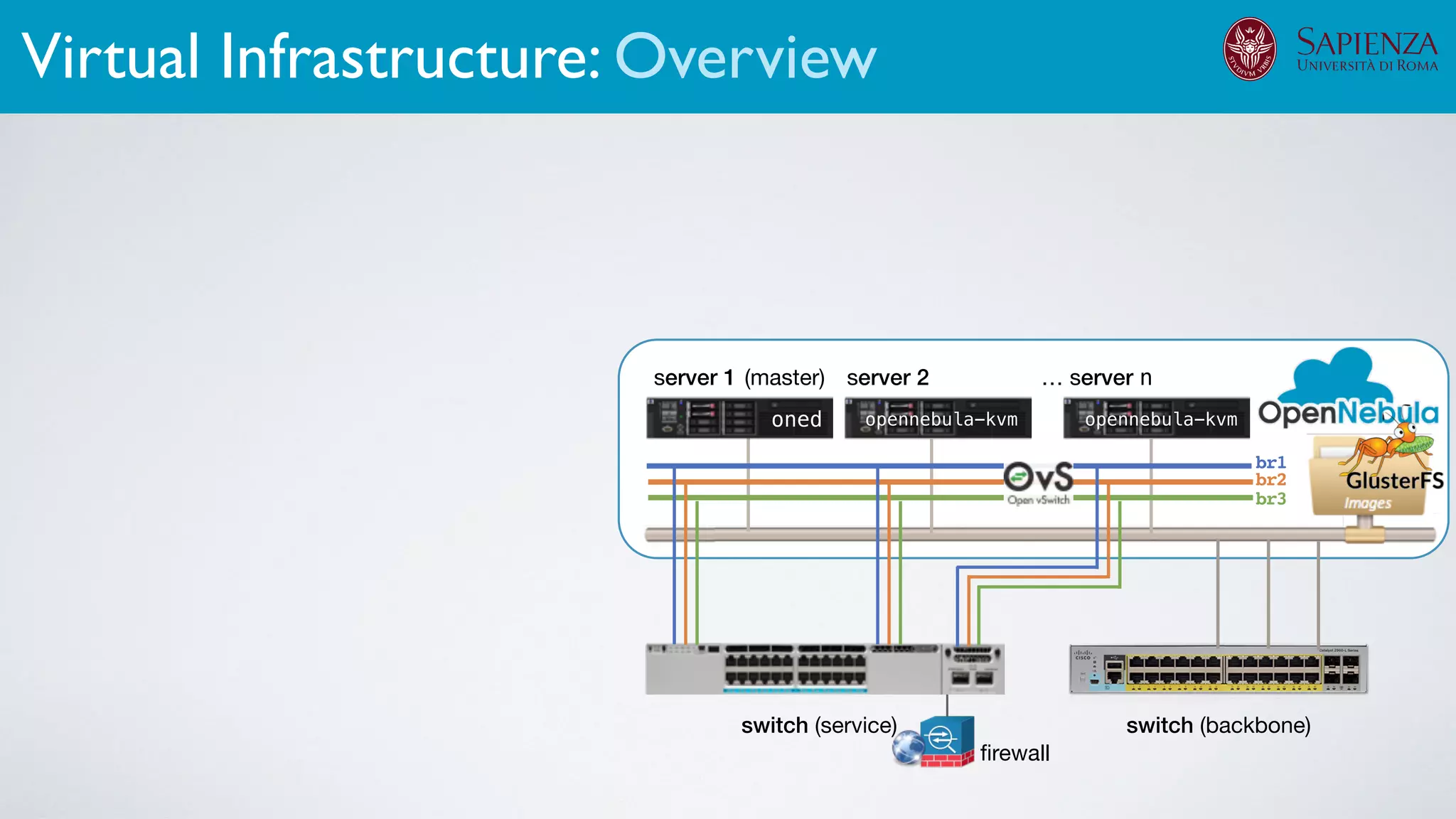
![[ICDCN ‘19] Tanasache, Sorella, Bonomi, Rapone, Meacci. Building an emulation environment for cyber security analyses of complex networked systems
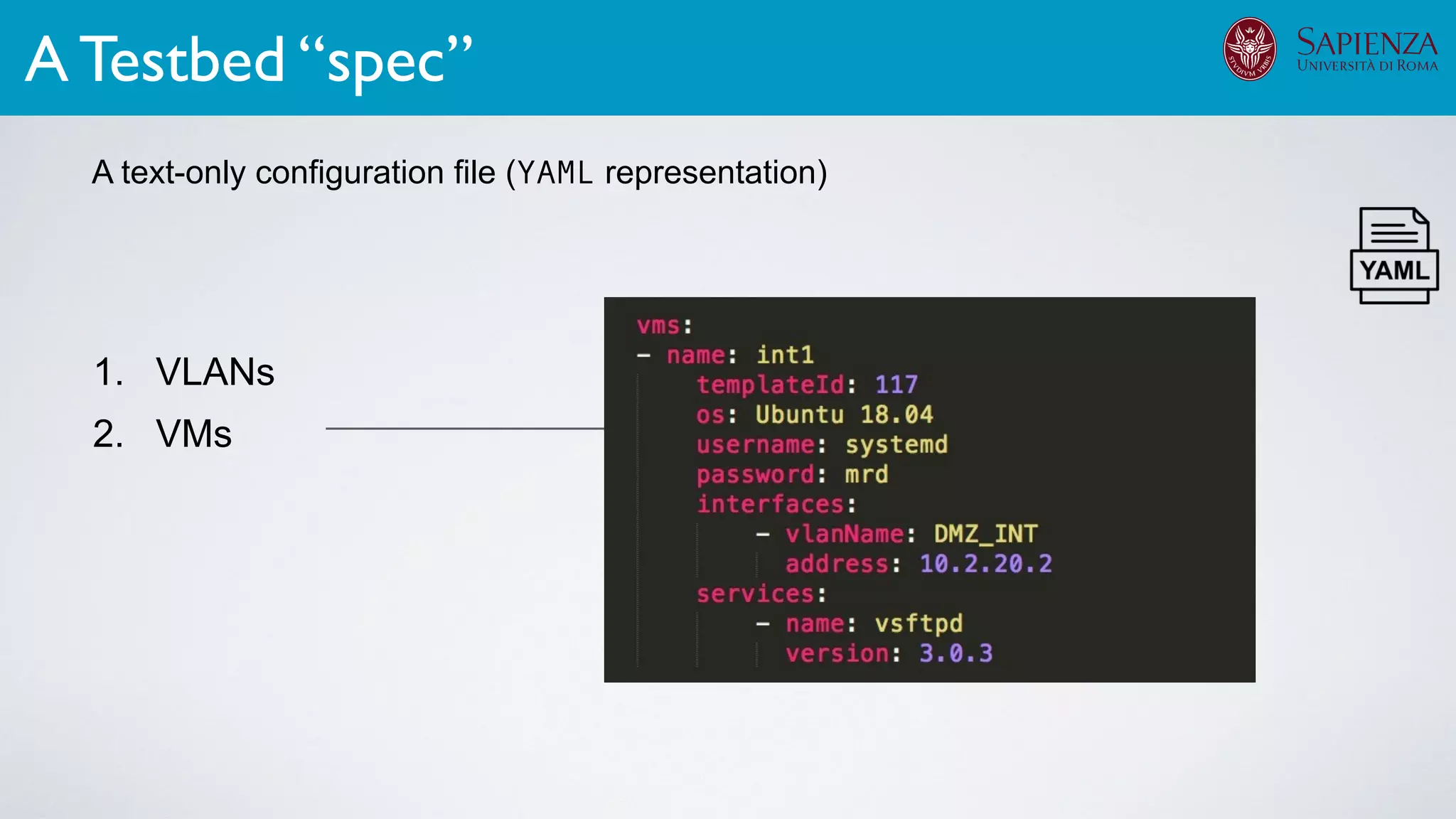
1. Cyber-range deployment for security training and testing
• cyber security scenario awareness
• incident management (detection, investigation, response)
2. Dataset generation
3. Threat modeling & risk management
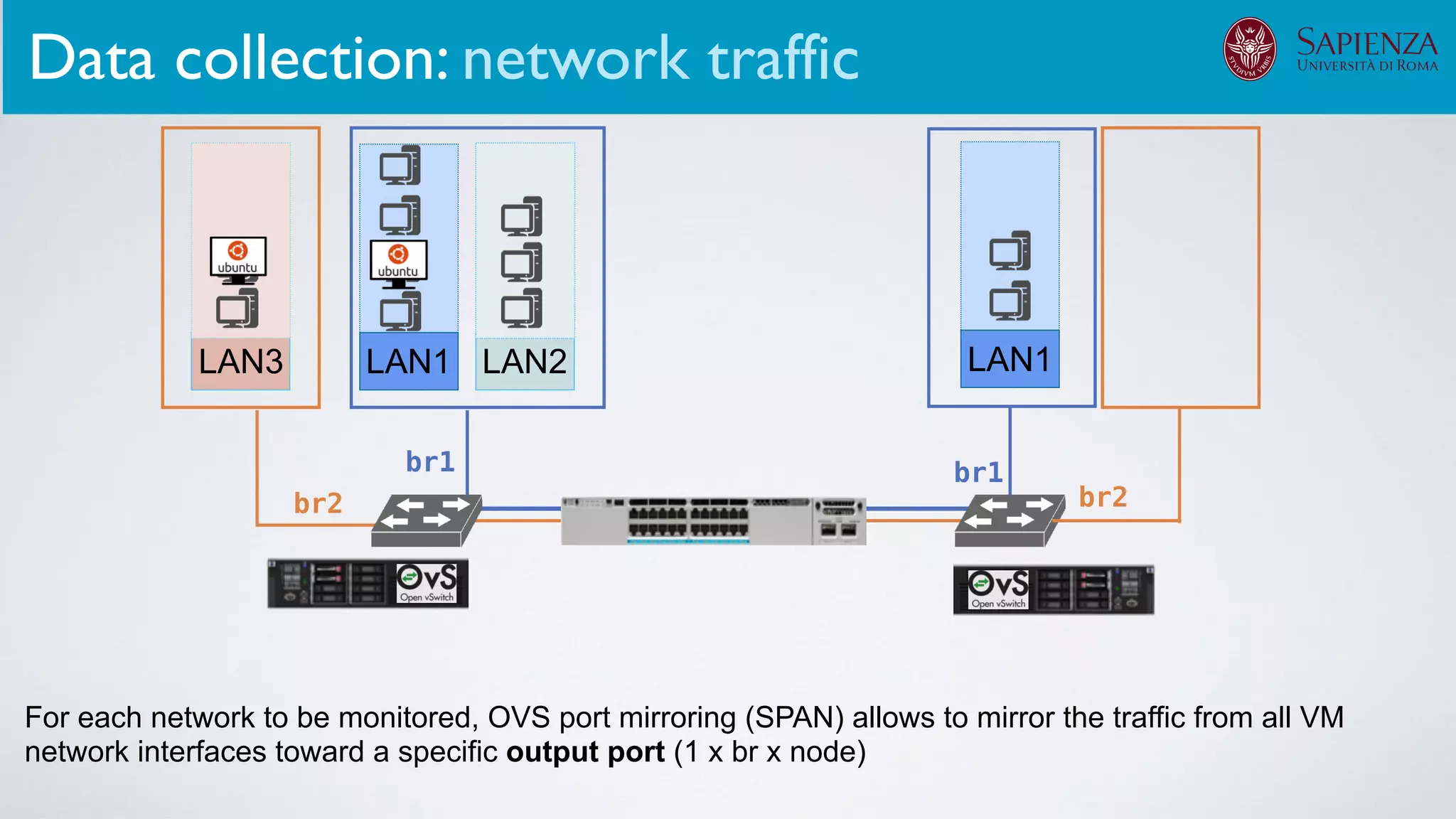
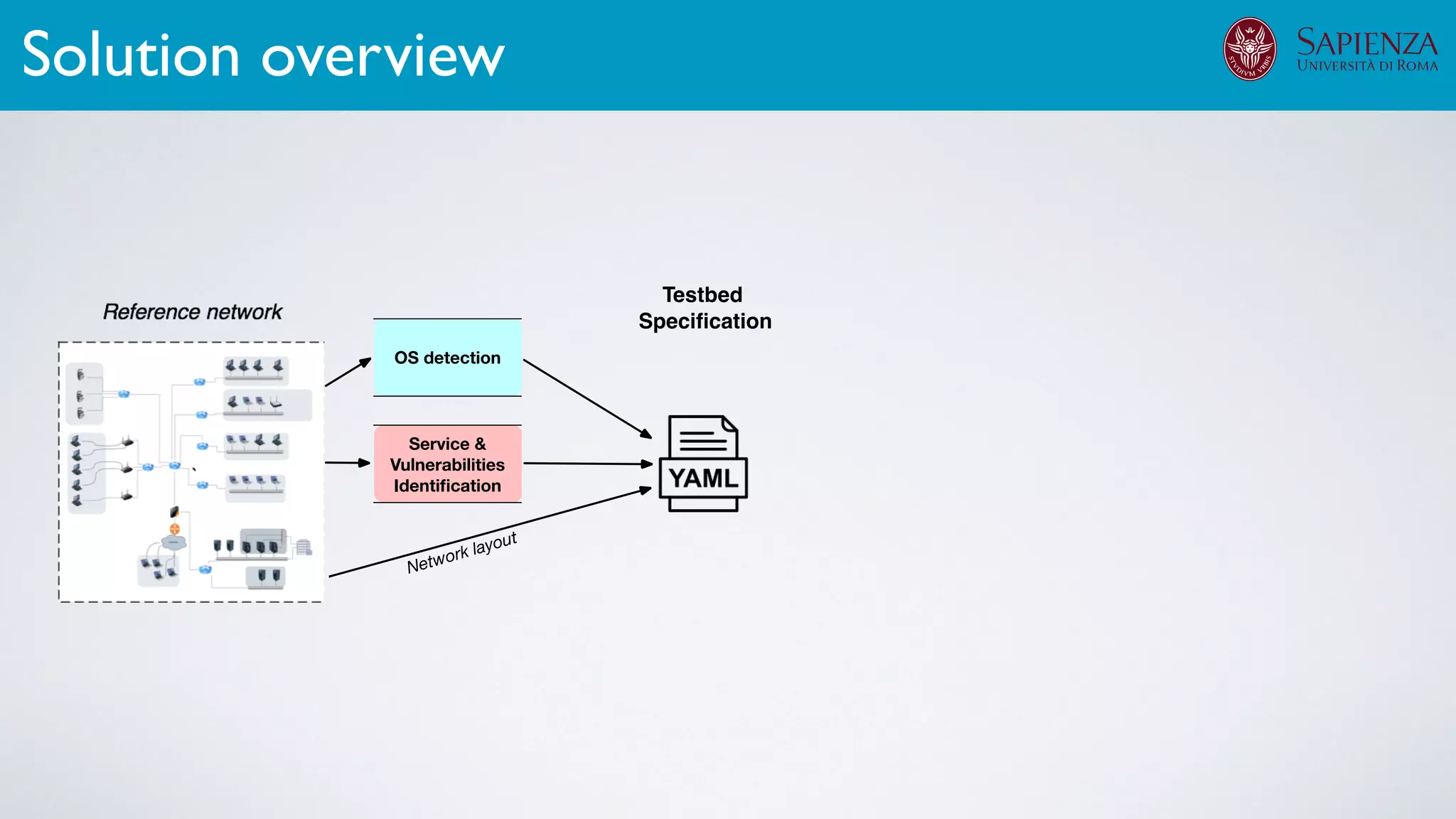
The infrastructure can support various activities
case study [ICDCN ‘19]
Applications: Overview](https://image.slidesharecdn.com/opennebulaconf2019univroma-191027214504/75/OpenNebulaConf2019-Building-Virtual-Environments-for-Security-Analyses-of-Complex-Networked-Systems-Mara-Sorella-Sapienza-Univ-of-Rome-61-2048.jpg)
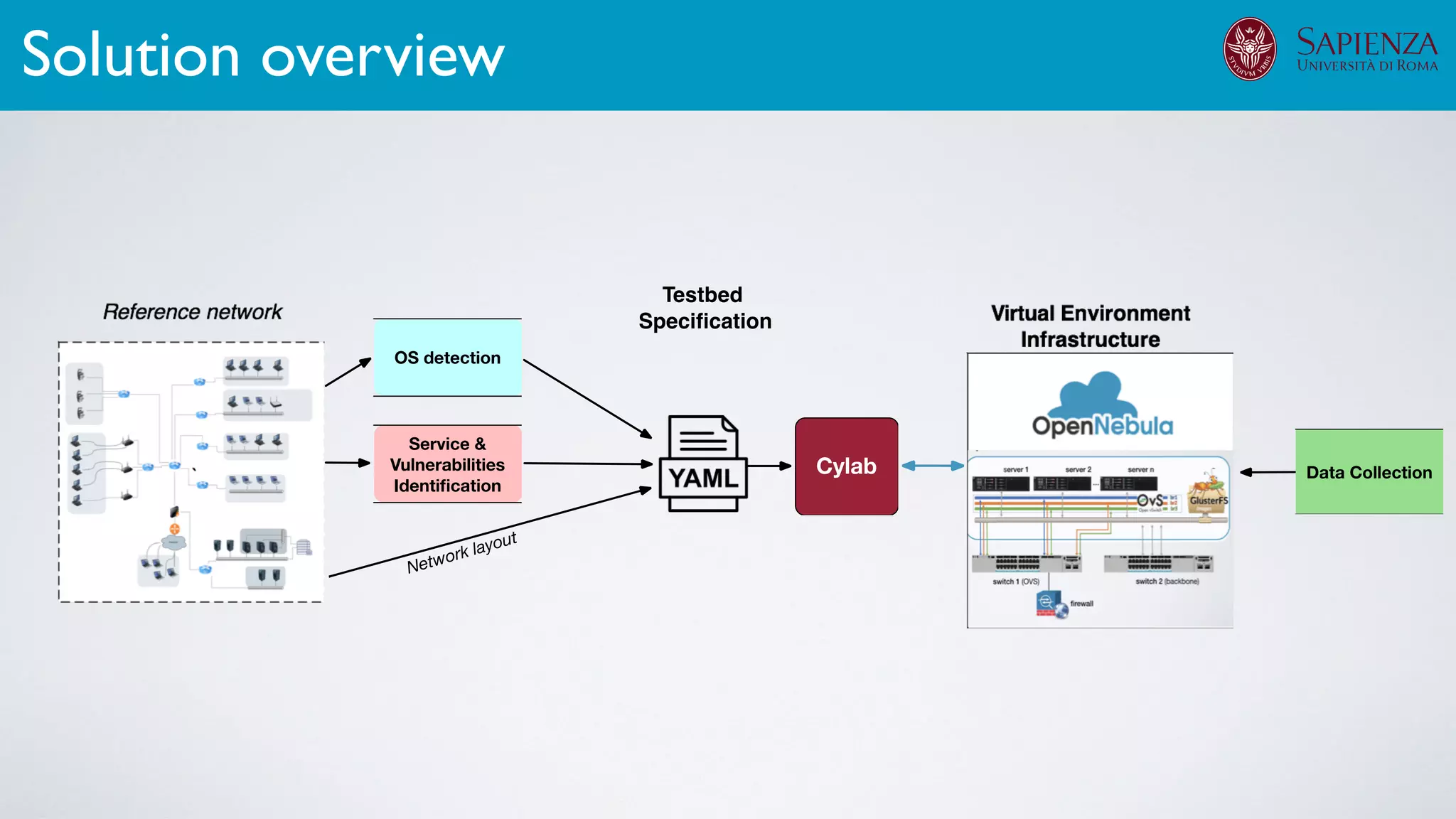
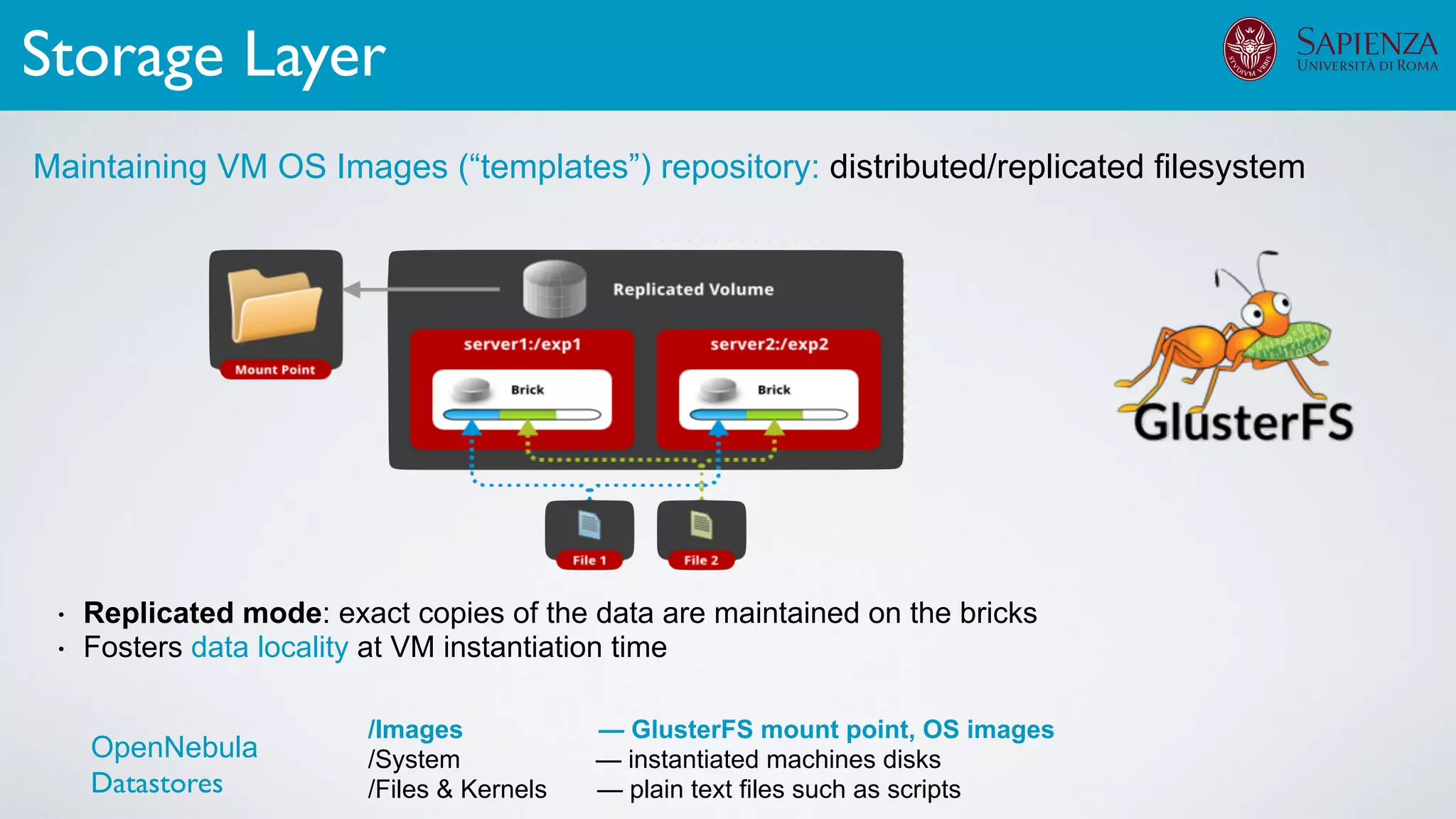
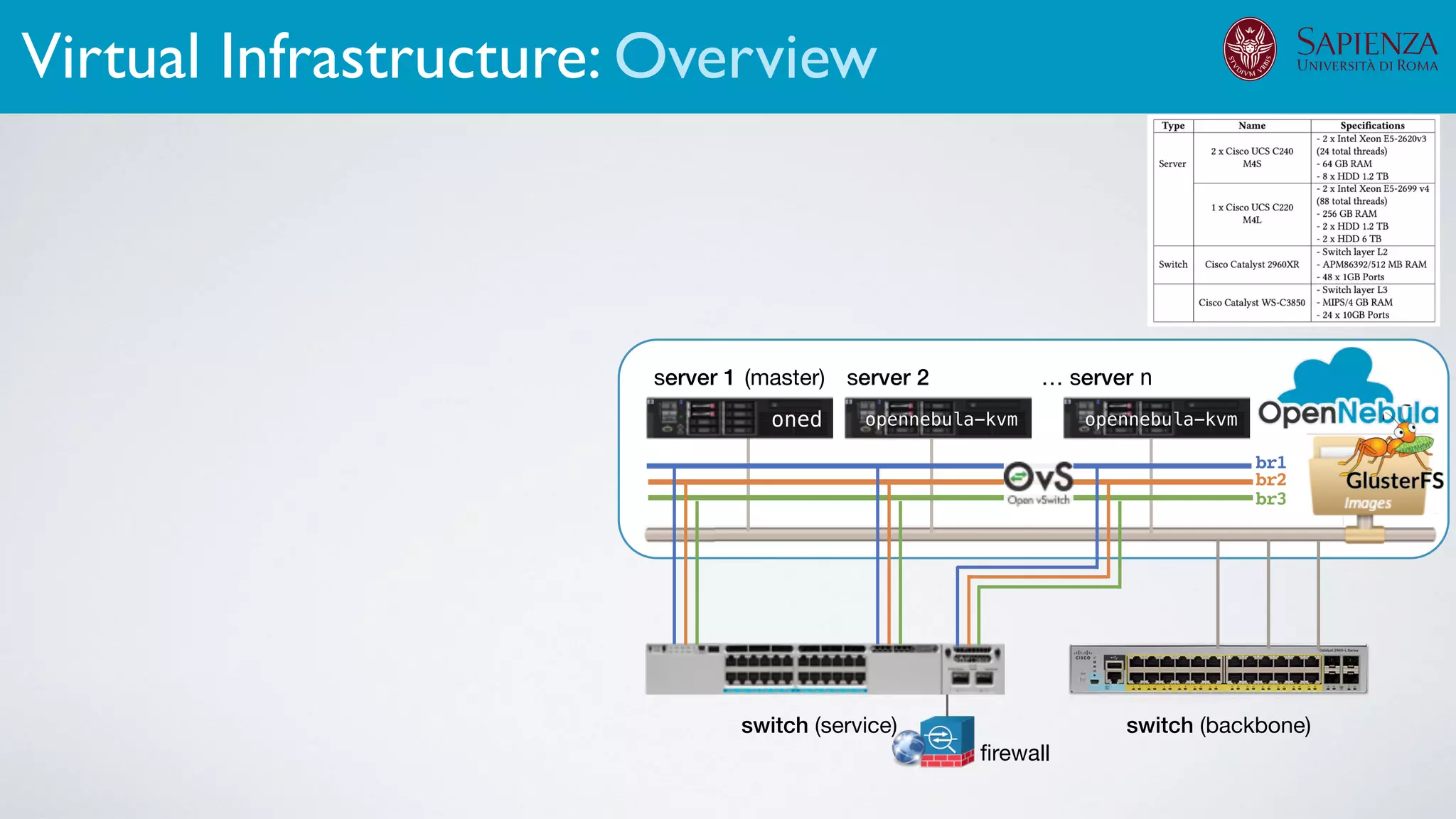
![[ICDCN ‘19] Tanasache, Sorella, Bonomi, Rapone, Meacci. Building an emulation environment for cyber security analyses of complex networked systems
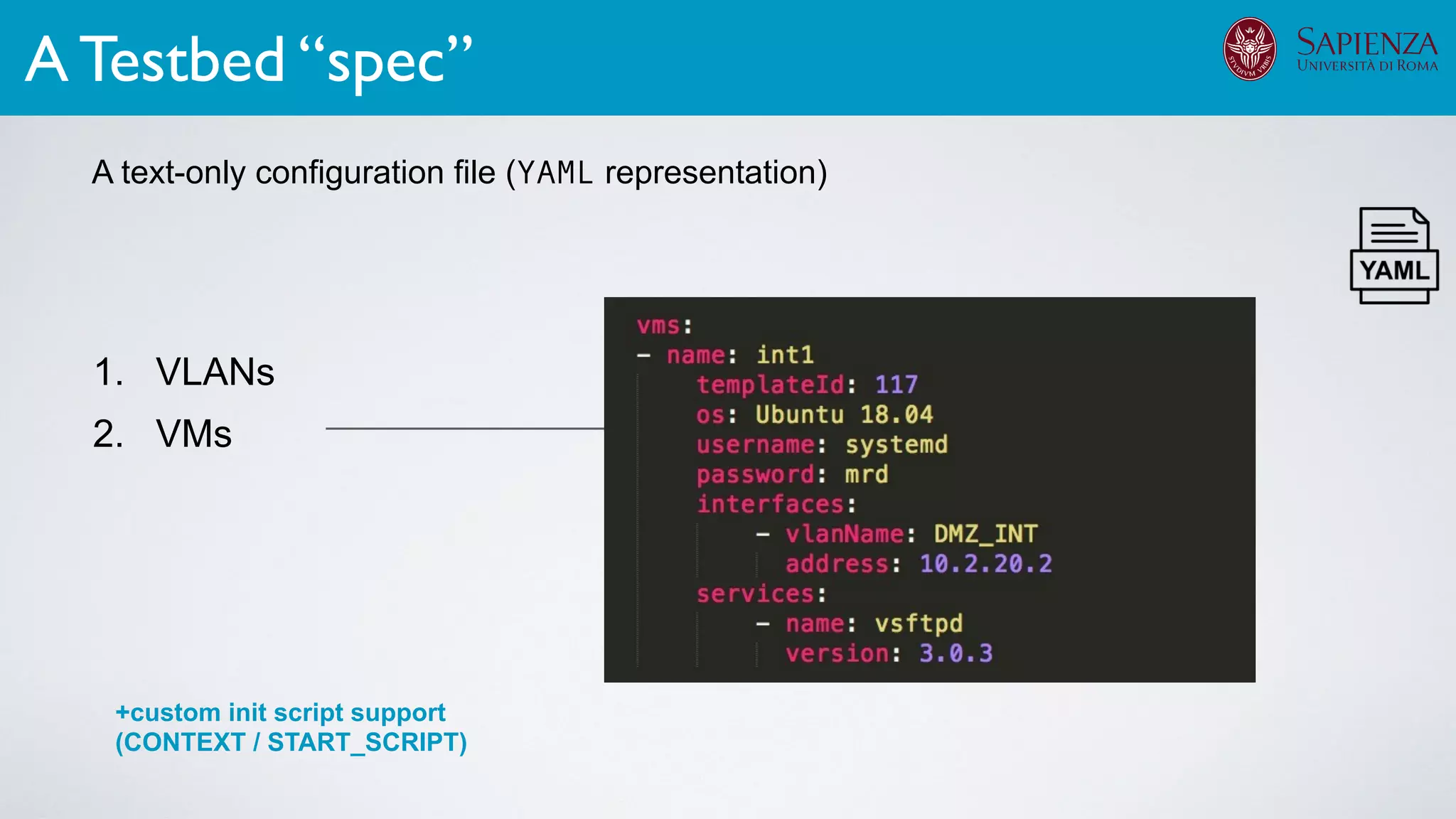
1. Cyber-range deployment for security training and testing
• cyber security scenario awareness
• incident management (detection, investigation, response)
2. Dataset generation
3. Threat modeling & risk management
• dynamic attack graph generation
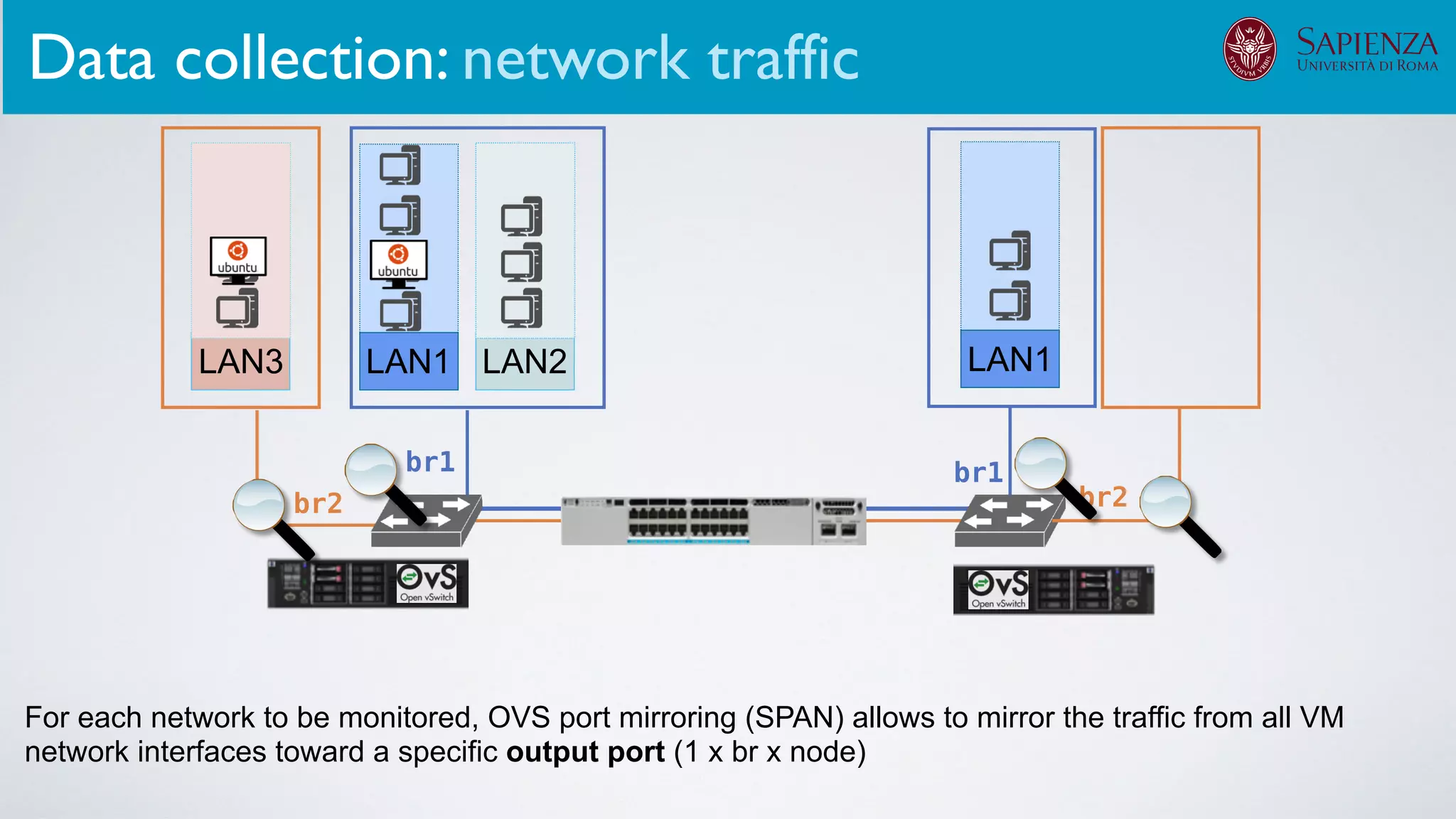
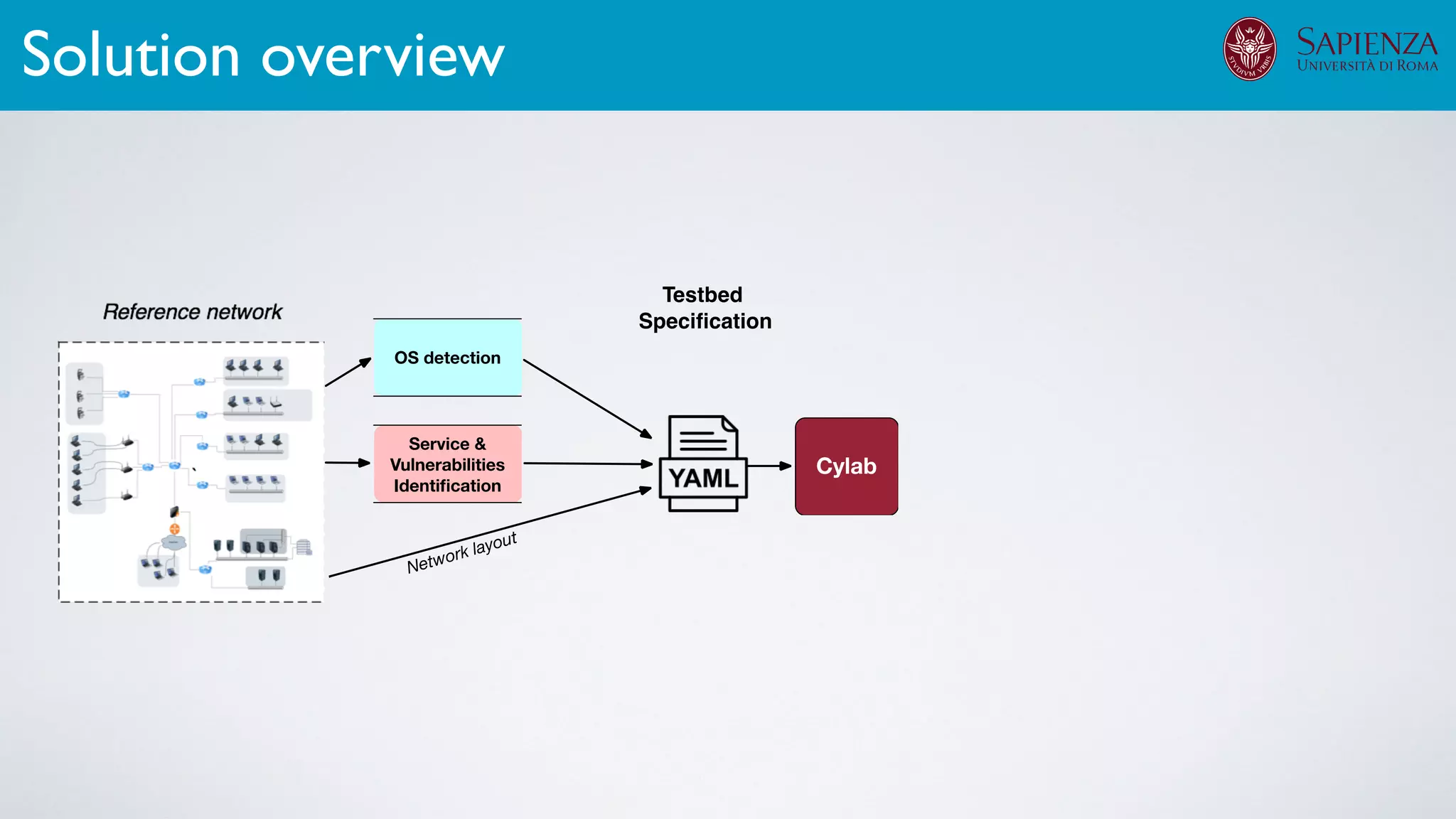
The infrastructure can support various activities
case study [ICDCN ‘19]
Applications: Overview](https://image.slidesharecdn.com/opennebulaconf2019univroma-191027214504/75/OpenNebulaConf2019-Building-Virtual-Environments-for-Security-Analyses-of-Complex-Networked-Systems-Mara-Sorella-Sapienza-Univ-of-Rome-62-2048.jpg)
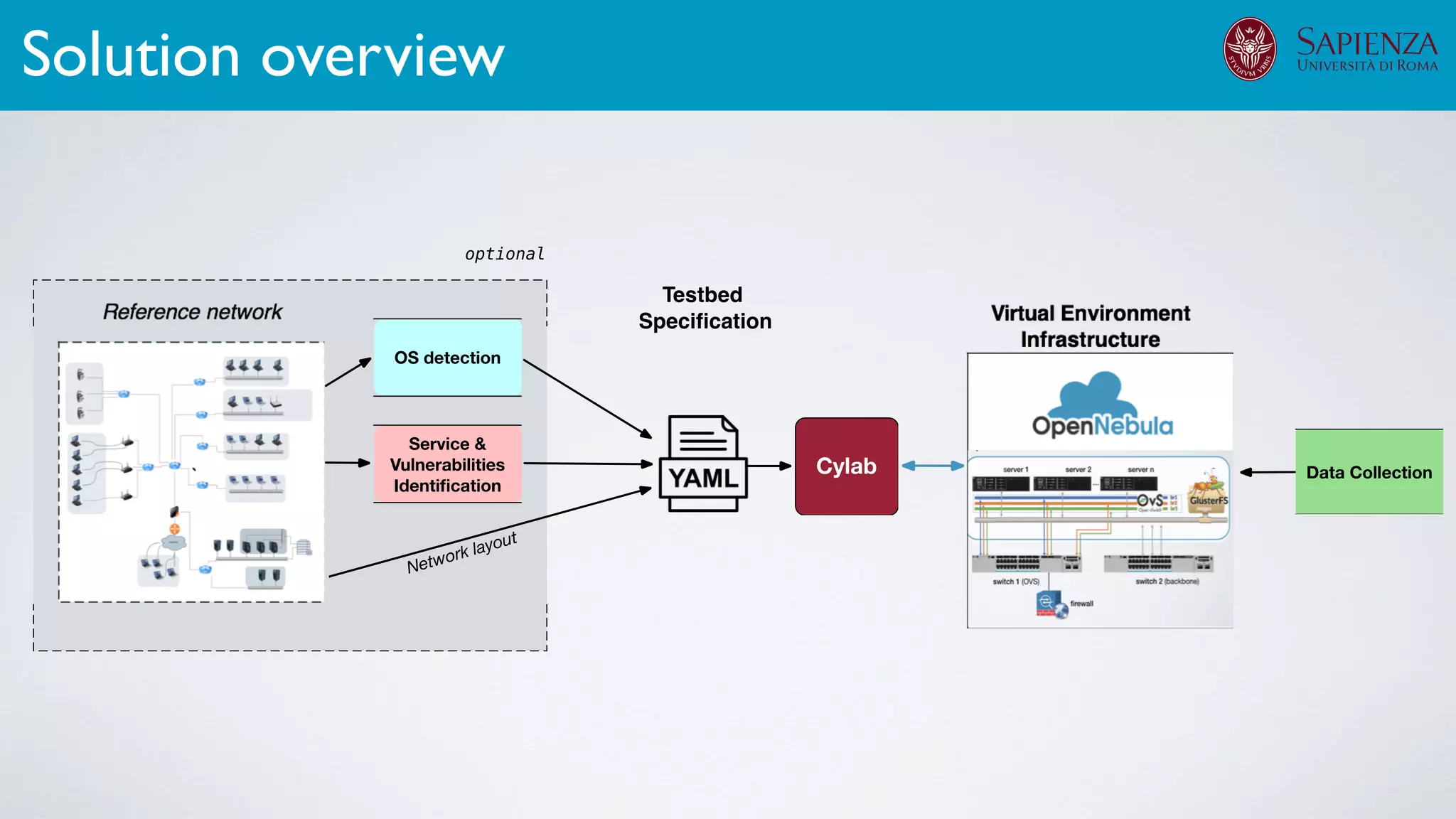
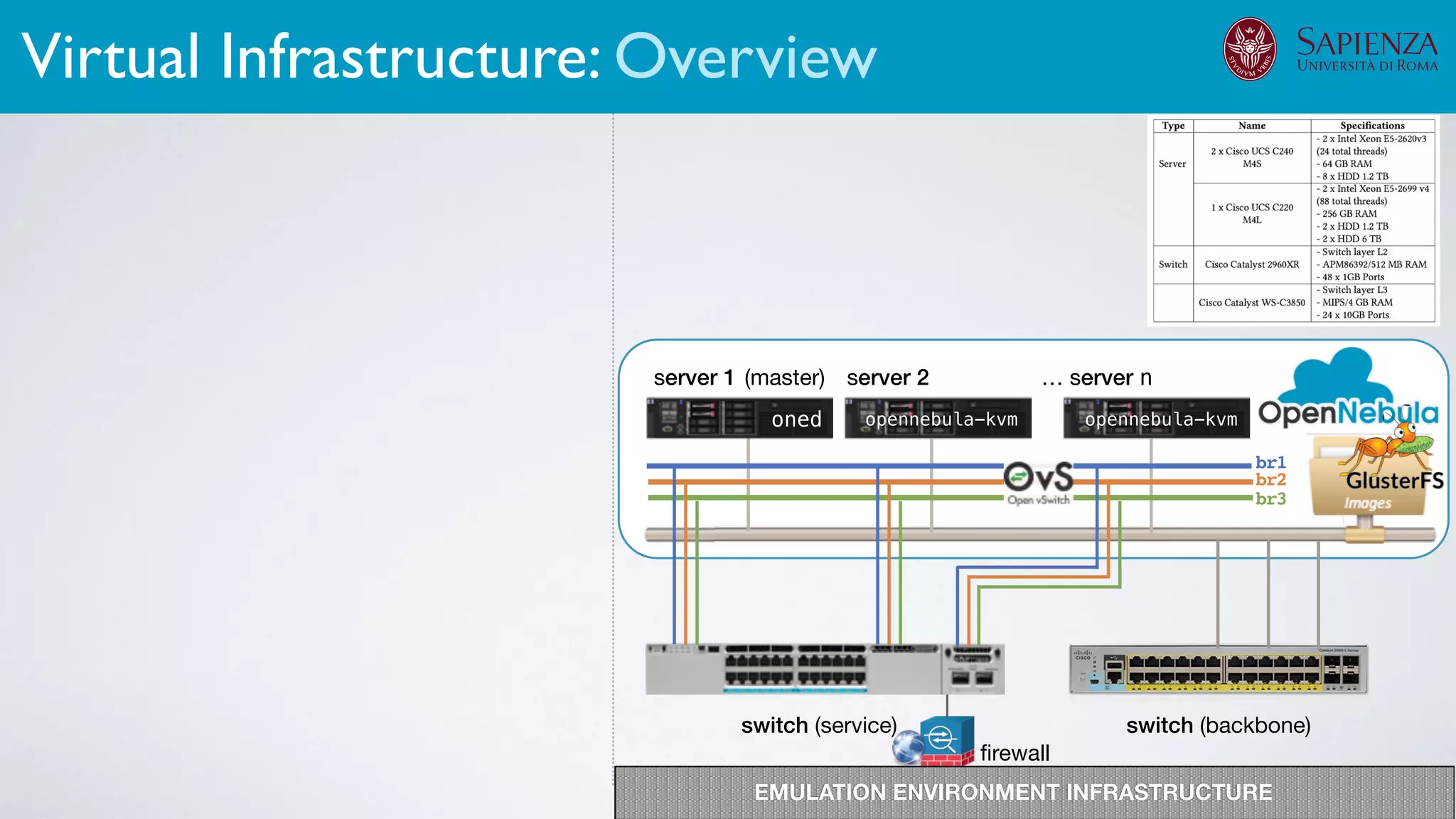
![[ICDCN ‘19] Tanasache, Sorella, Bonomi, Rapone, Meacci. Building an emulation environment for cyber security analyses of complex networked systems
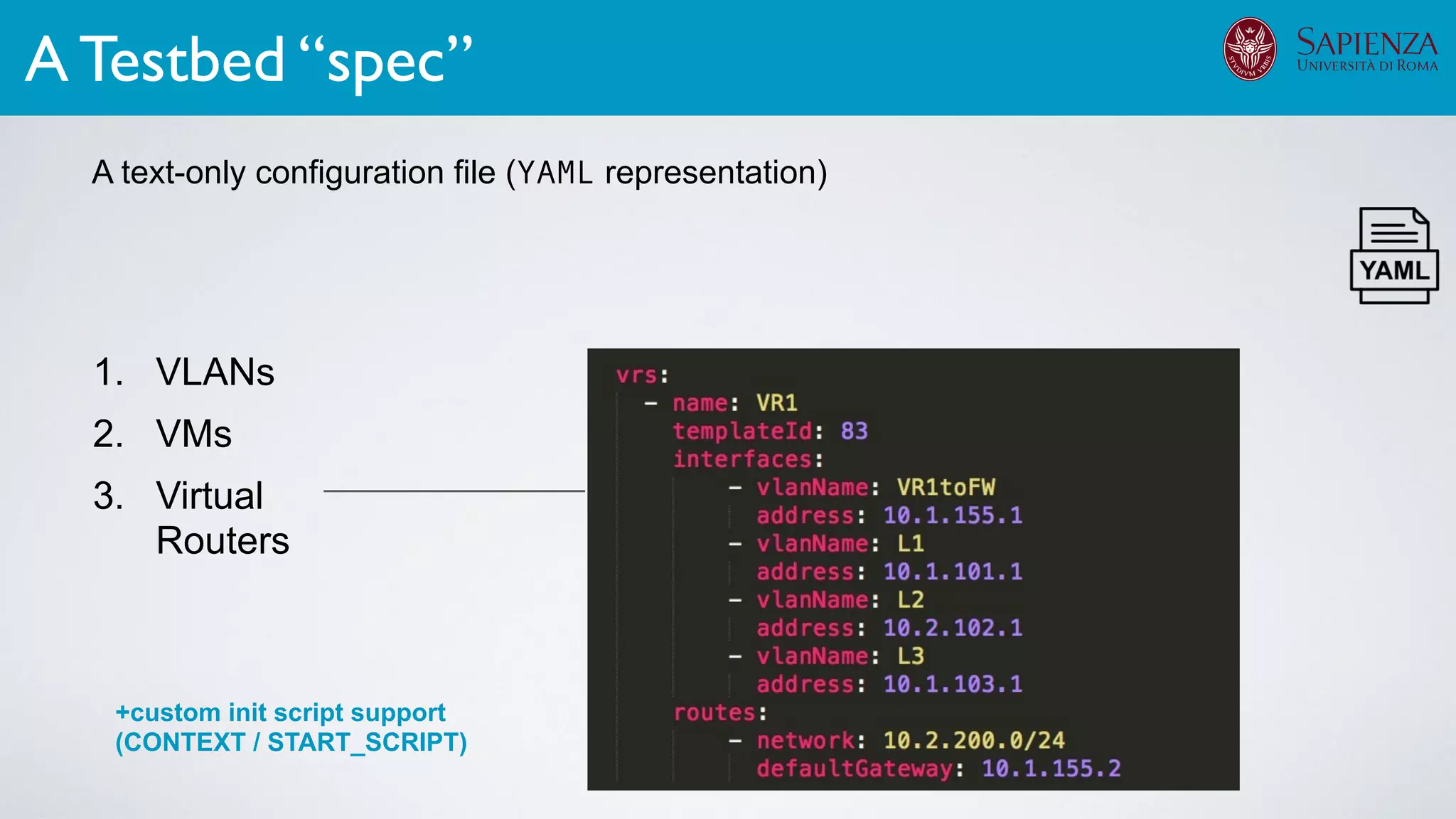
1. Cyber-range deployment for security training and testing
• cyber security scenario awareness
• incident management (detection, investigation, response)
2. Dataset generation
3. Threat modeling & risk management
• dynamic attack graph generation
The infrastructure can support various activities
case study [ICDCN ‘19]
Applications: Overview](https://image.slidesharecdn.com/opennebulaconf2019univroma-191027214504/75/OpenNebulaConf2019-Building-Virtual-Environments-for-Security-Analyses-of-Complex-Networked-Systems-Mara-Sorella-Sapienza-Univ-of-Rome-63-2048.jpg)
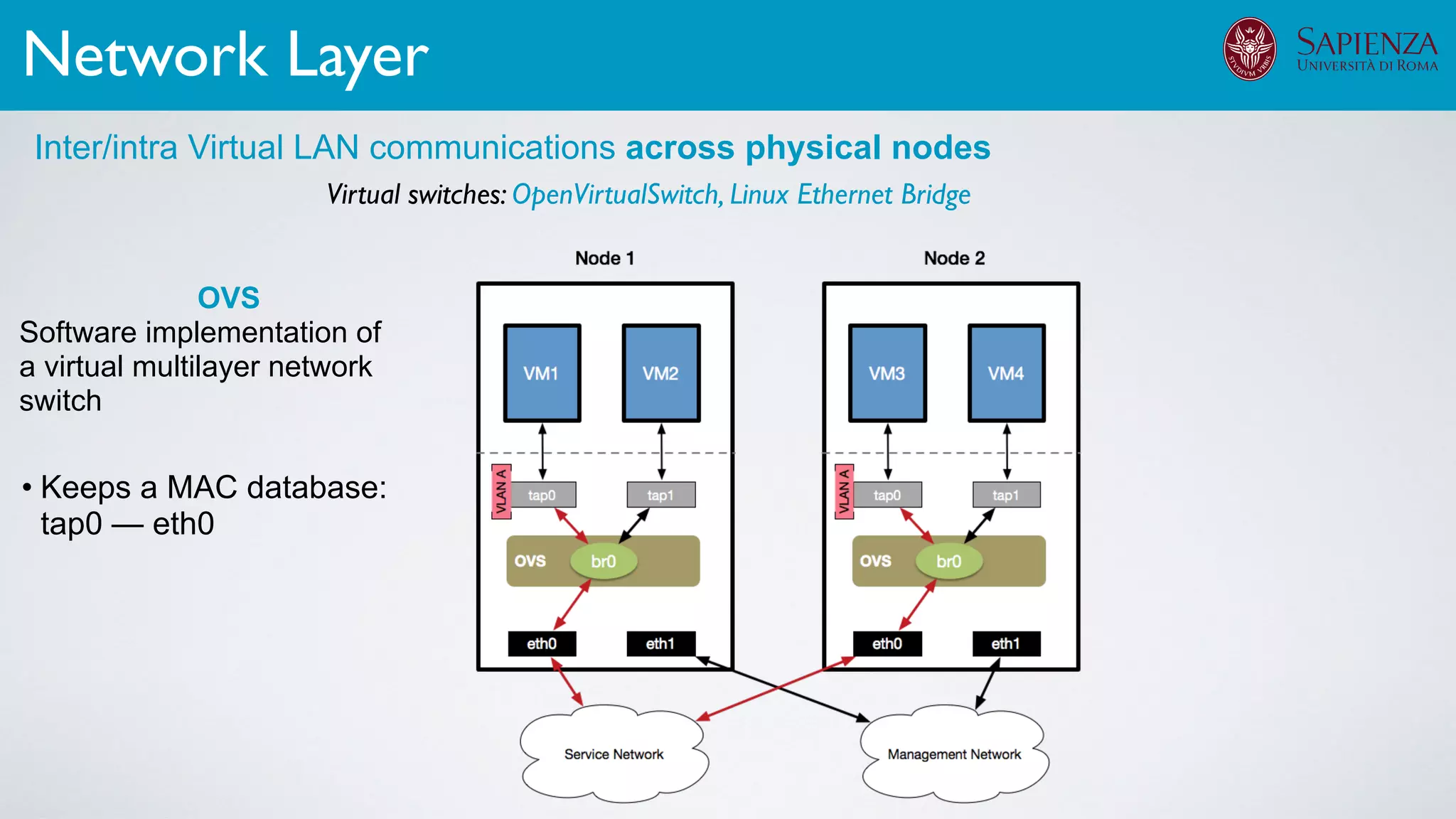
![[ICDCN ‘19] Tanasache, Sorella, Bonomi, Rapone, Meacci. Building an emulation environment for cyber security analyses of complex networked systems
1. Cyber-range deployment for security training and testing
• cyber security scenario awareness
• incident management (detection, investigation, response)
2. Dataset generation
3. Threat modeling & risk management
• dynamic attack graph generation
• network hardening
• automatic attack path instantiation
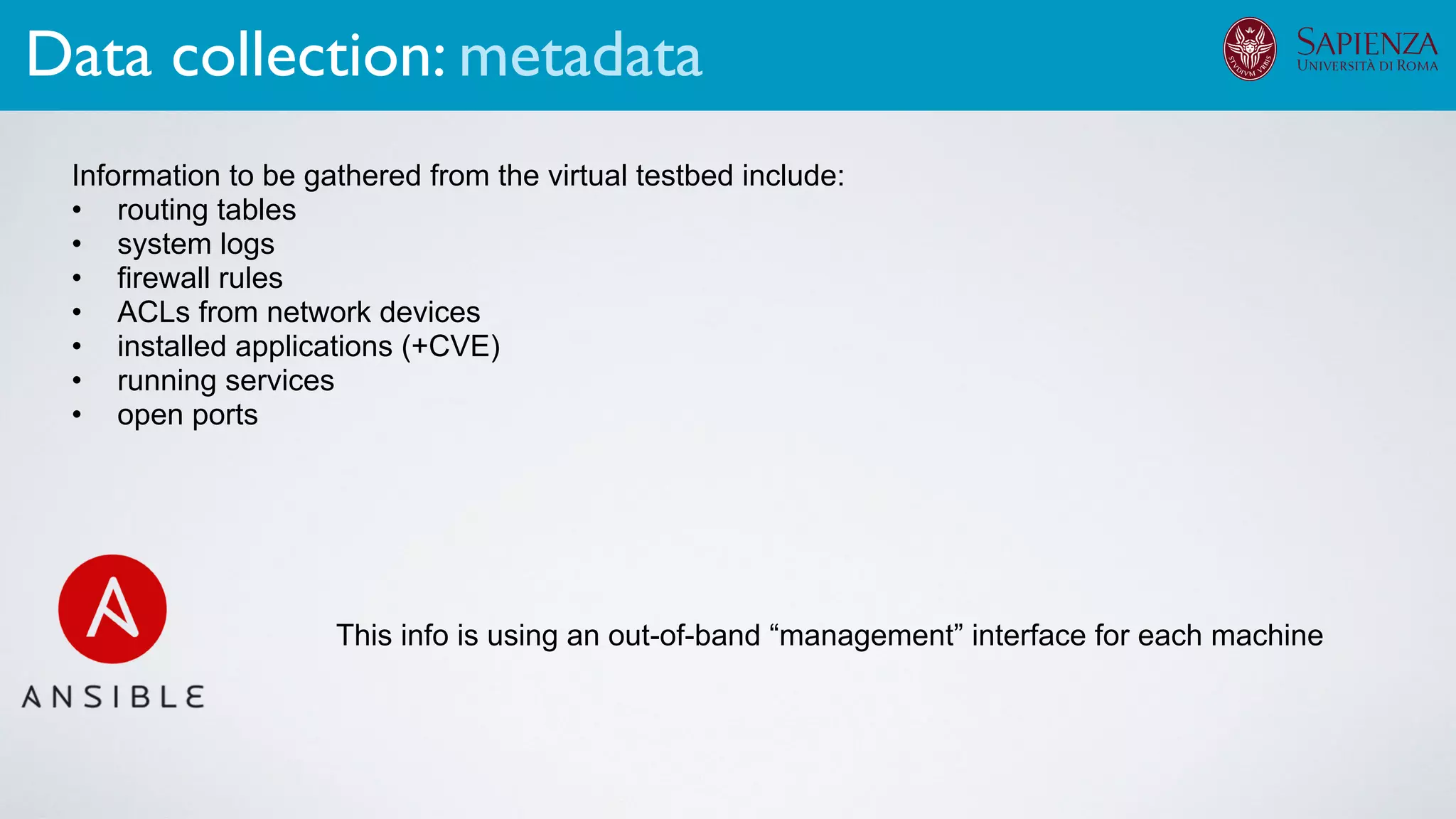
The infrastructure can support various activities
case study [ICDCN ‘19]
Applications: Overview](https://image.slidesharecdn.com/opennebulaconf2019univroma-191027214504/75/OpenNebulaConf2019-Building-Virtual-Environments-for-Security-Analyses-of-Complex-Networked-Systems-Mara-Sorella-Sapienza-Univ-of-Rome-64-2048.jpg)
![[ICDCN ‘19] Tanasache, Sorella, Bonomi, Rapone, Meacci. Building an emulation environment for cyber security analyses of complex networked systems
1. Cyber-range deployment for security training and testing
• cyber security scenario awareness
• incident management (detection, investigation, response)
2. Dataset generation
3. Threat modeling & risk management
• dynamic attack graph generation
• network hardening
• automatic attack path instantiation
The infrastructure can support various activities
case study [ICDCN ‘19]
Applications: Overview](https://image.slidesharecdn.com/opennebulaconf2019univroma-191027214504/75/OpenNebulaConf2019-Building-Virtual-Environments-for-Security-Analyses-of-Complex-Networked-Systems-Mara-Sorella-Sapienza-Univ-of-Rome-65-2048.jpg)