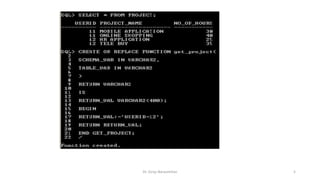
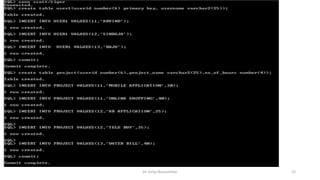
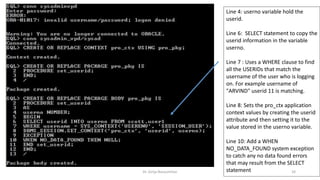
This document discusses database security using Oracle Virtual Private Database (VPD). It covers row level security (RLS) using predicates, components of a VPD policy including creating a function and policy, an example of a policy restricting user access, and dropping a function and policy. It also discusses column masking and application context, including using SYS_CONTEXT to return session information and setting an application context within a function.