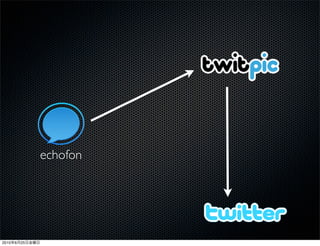
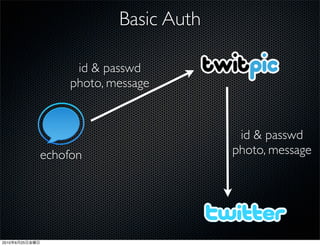
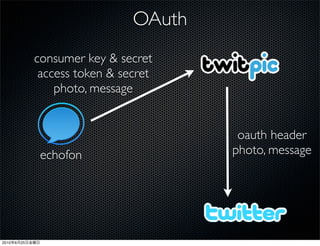
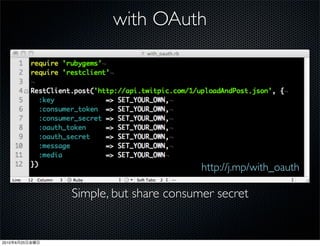
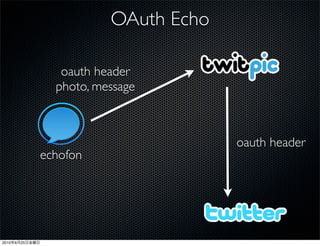
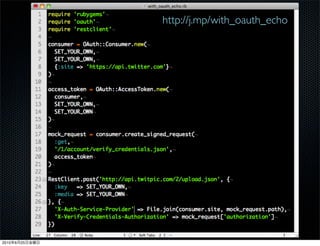
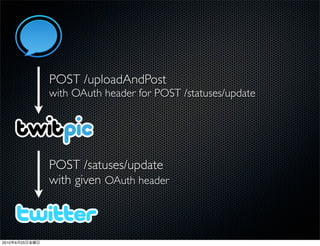
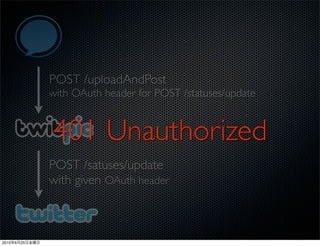
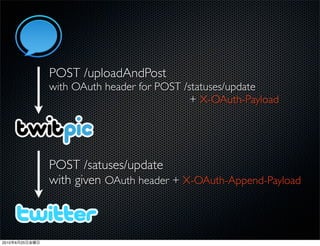
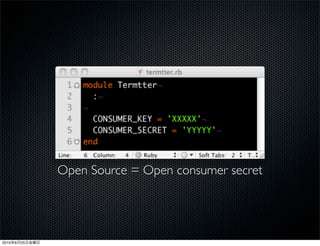
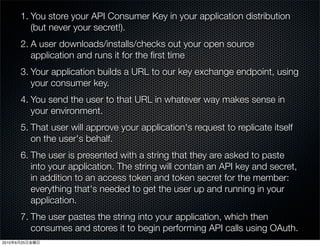
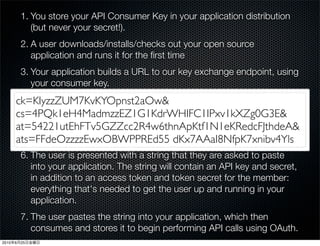
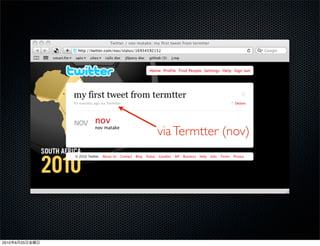
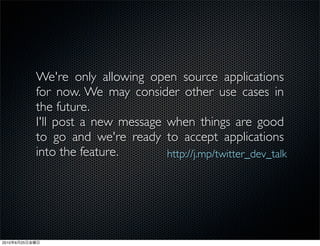
This document discusses Twitter's implementation of OAuth authentication. It describes how basic authentication worked previously with username and password, and how OAuth provides an improved authorization method using consumer keys, access tokens, and secrets. Various iterations and implementations of OAuth are presented for authenticating photo uploads, posts, and delegating identity verification between applications and Twitter's API. An upcoming solution is proposed for open source applications to utilize OAuth without hardcoding secret keys.