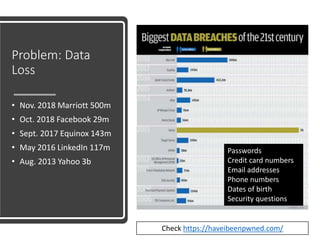
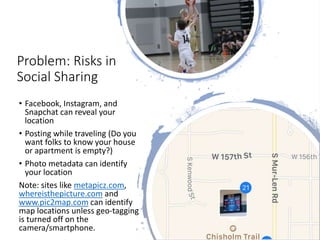
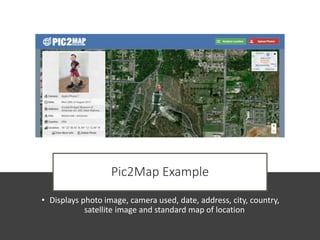
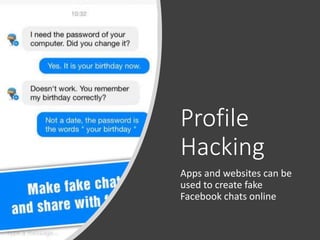
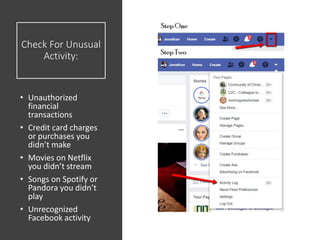
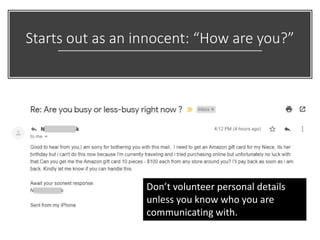
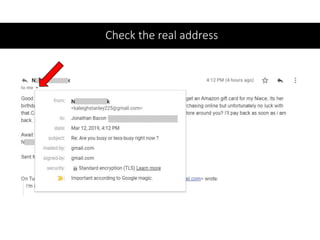
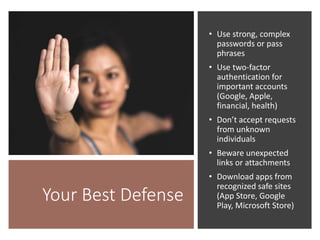
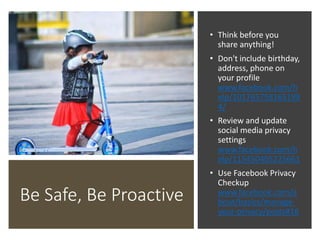
The document discusses various risks associated with social media use, including data loss, identity theft, fake requests, and profile hacking. It provides actionable advice for protecting oneself, such as using complex passwords, being cautious with friend requests, and monitoring accounts for unusual activity. Additional resources and tips for enhancing security on social media platforms are also included.