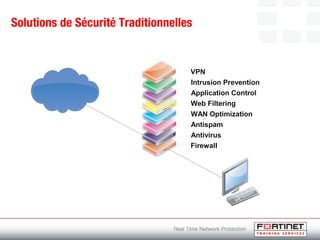
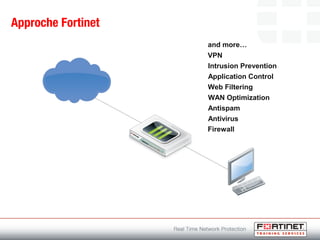
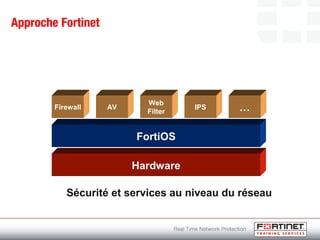
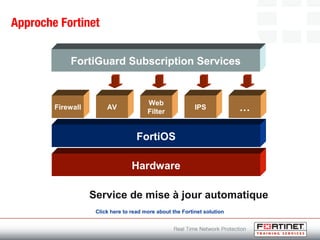
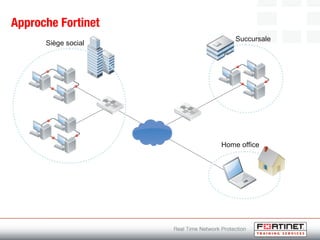
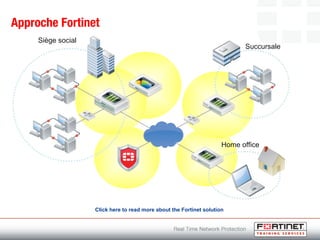
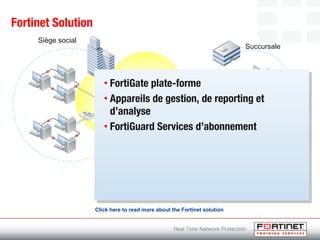
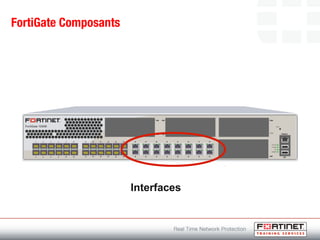
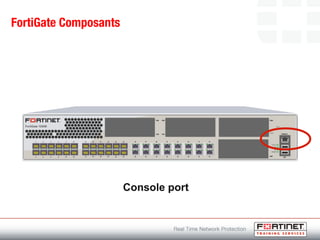
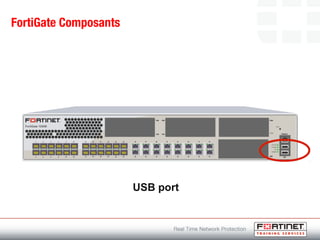
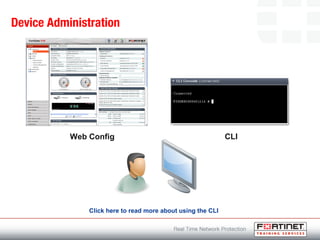
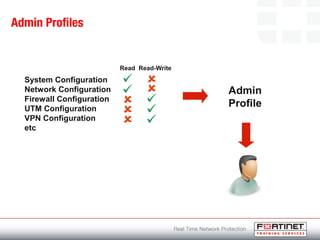
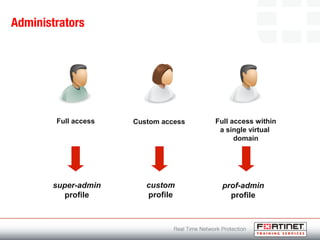
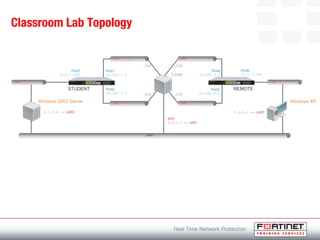
This document provides an introduction to Fortinet's Unified Threat Management solutions. It discusses how Fortinet uses a single appliance with a specialized operating system to provide comprehensive security with features like firewall, antivirus, web filtering, intrusion prevention, and more. It also touches on the FortiGate platform, management tools, subscription services, and various FortiGate components and appliances in the Fortinet product line.