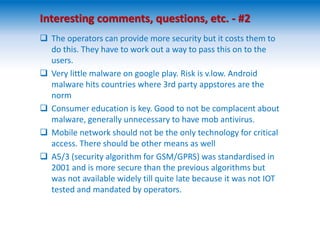
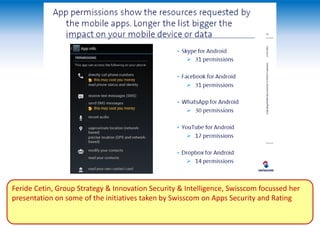
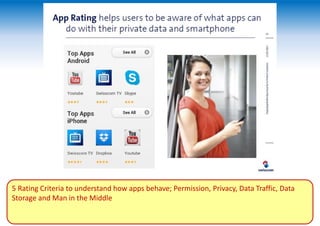
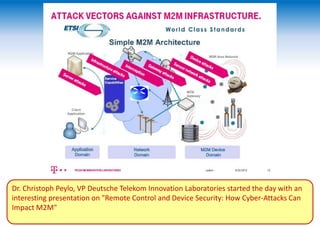
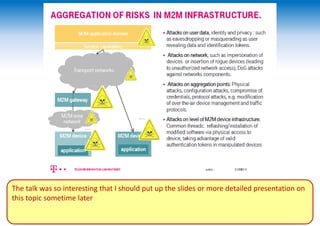
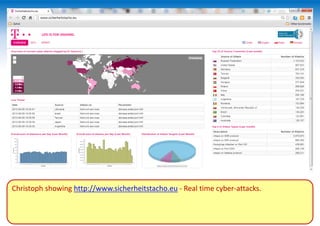
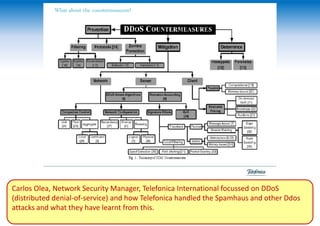
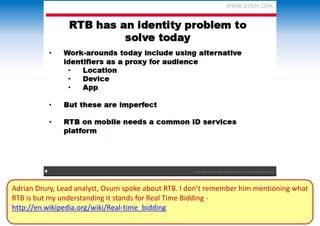
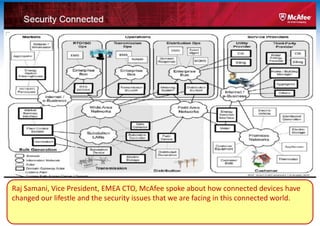
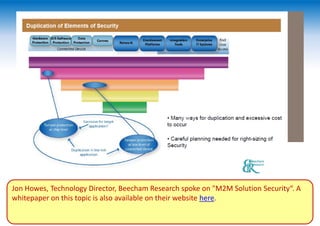
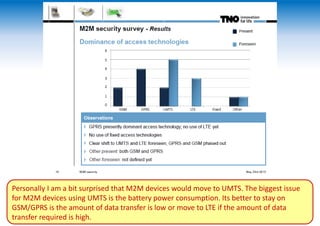
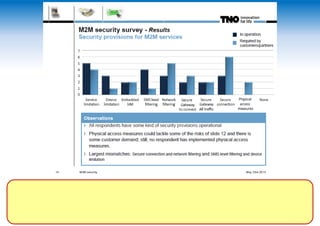
The two-day Network Security Conference in May 2013 covered several topics related to mobile network and device security. Key discussions included the importance of securing user data in the cloud rather than on devices, making users aware of background functions and security risks, and challenges for operators in providing security while controlling costs. Presentations also addressed security issues for emerging technologies like LTE, M2M/IoT, and small cells. Attendees discussed the need for continued user education on security best practices as threats evolve with new mobile applications and connectivity.