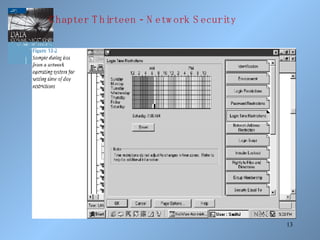
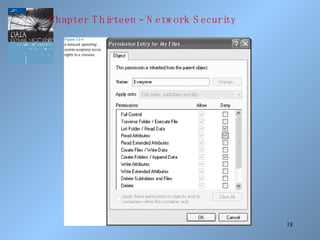
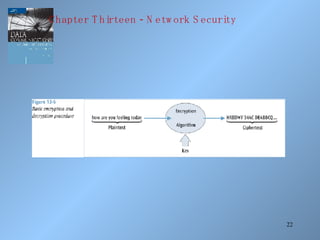
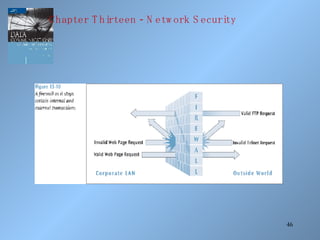
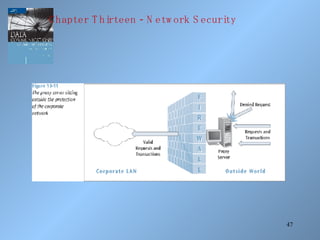
The document discusses various methods of network security including viruses, worms, system attacks like denial of service, encryption techniques from basic substitution ciphers to public key cryptography. It covers physical security measures, access control, passwords, auditing and the data encryption standard as well as its replacement, the advanced encryption standard.