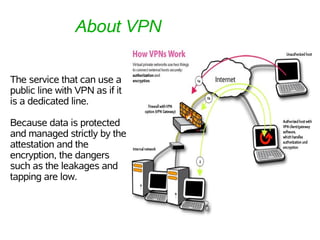
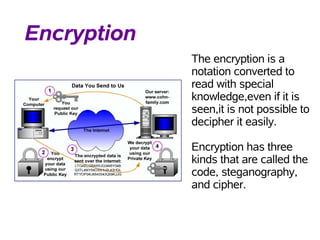
The document discusses different methods of securing data transmission including firewalls, VPNs, and encryption. It explains that firewalls control communication between networks to maintain security, and VPNs allow using public lines securely by protecting and strictly managing data with authentication and encryption. Encryption involves converting data into code that can only be read with special knowledge, making it difficult to decipher without the proper means even if seen.