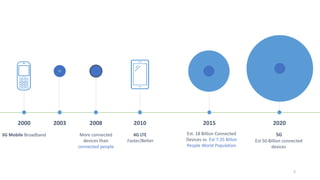
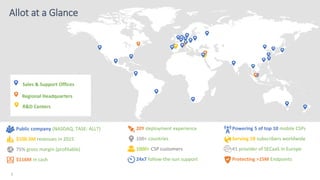
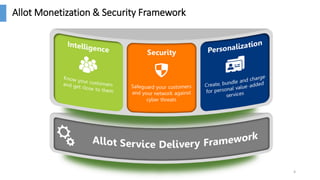
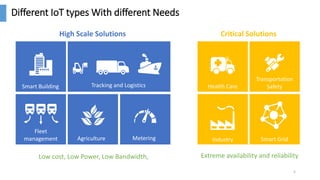
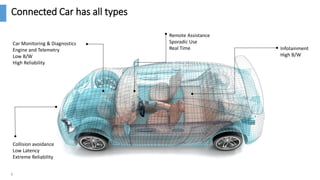
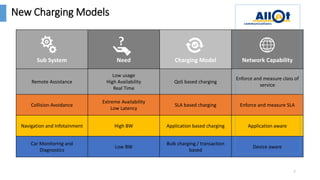
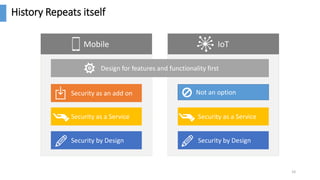
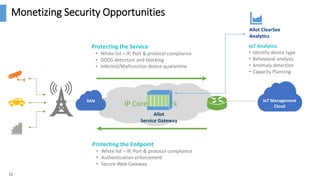
The document discusses the monetization and security opportunities associated with the growing number of connected devices, expected to reach 50 billion. It highlights Allot's capabilities in analytics and security as a service, demonstrating its role in managing network traffic, preventing fraud, and enhancing customer engagement through detailed insights and reporting. The text also emphasizes the importance of understanding IoT device identities and behaviors to optimize costs and maximize profits.