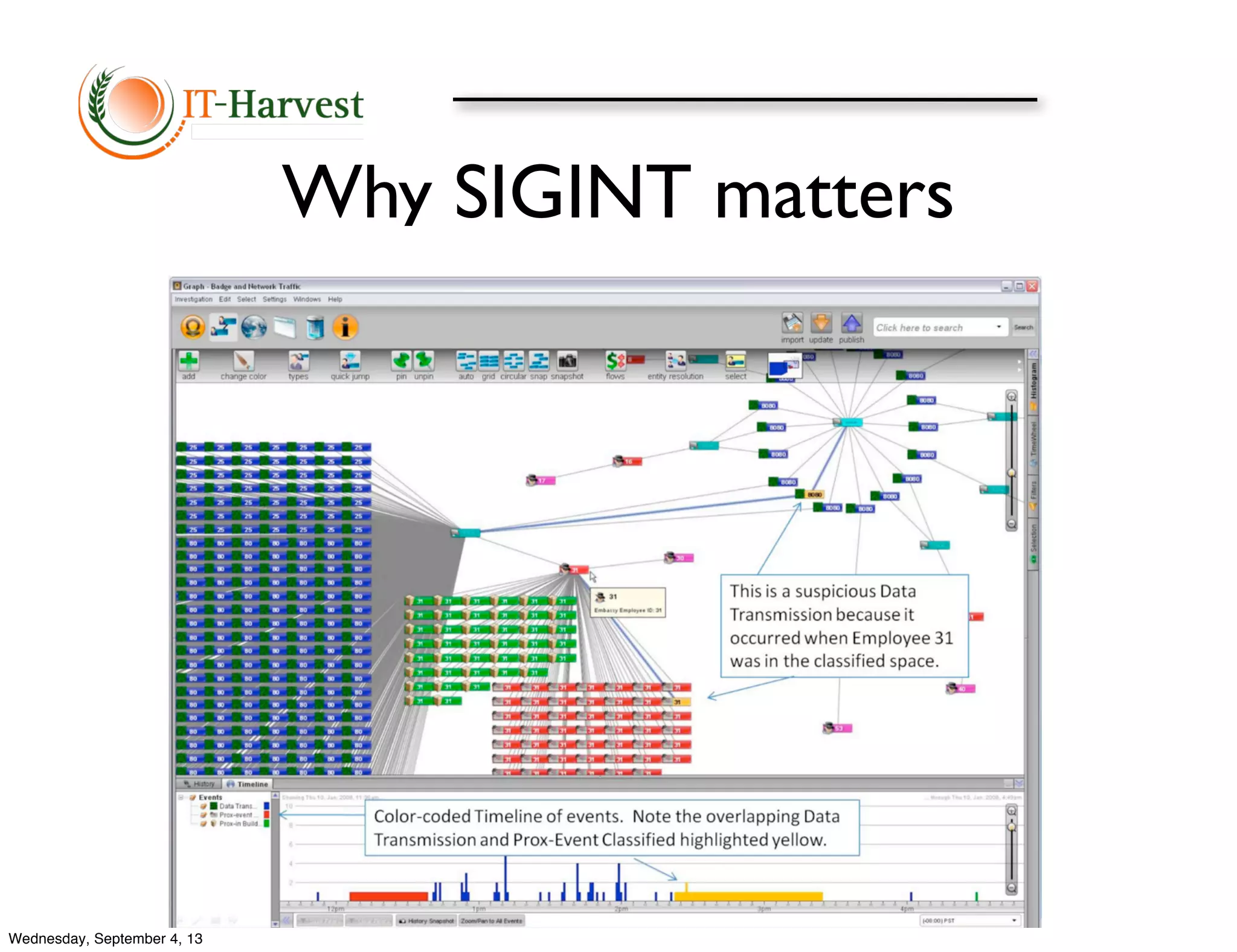
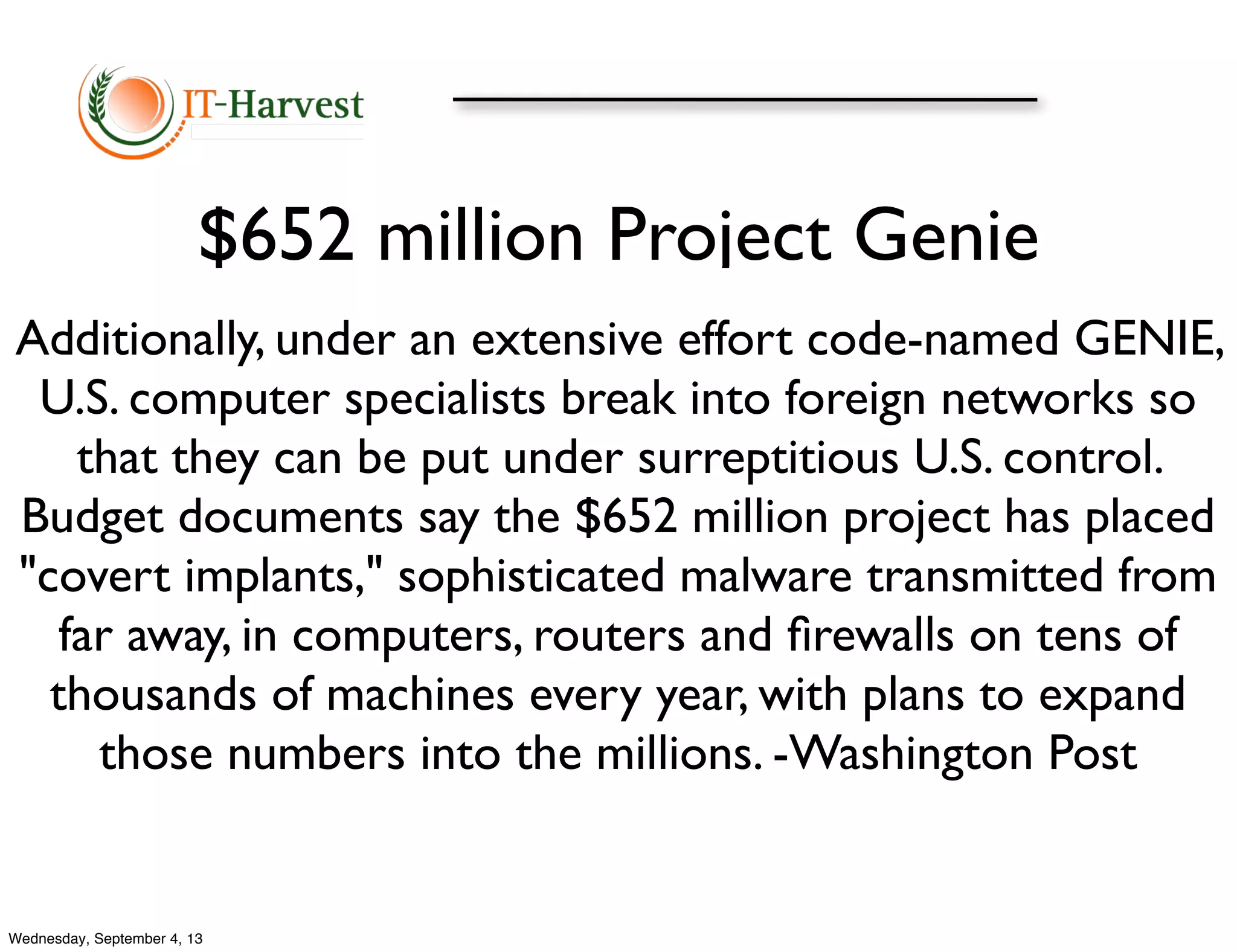
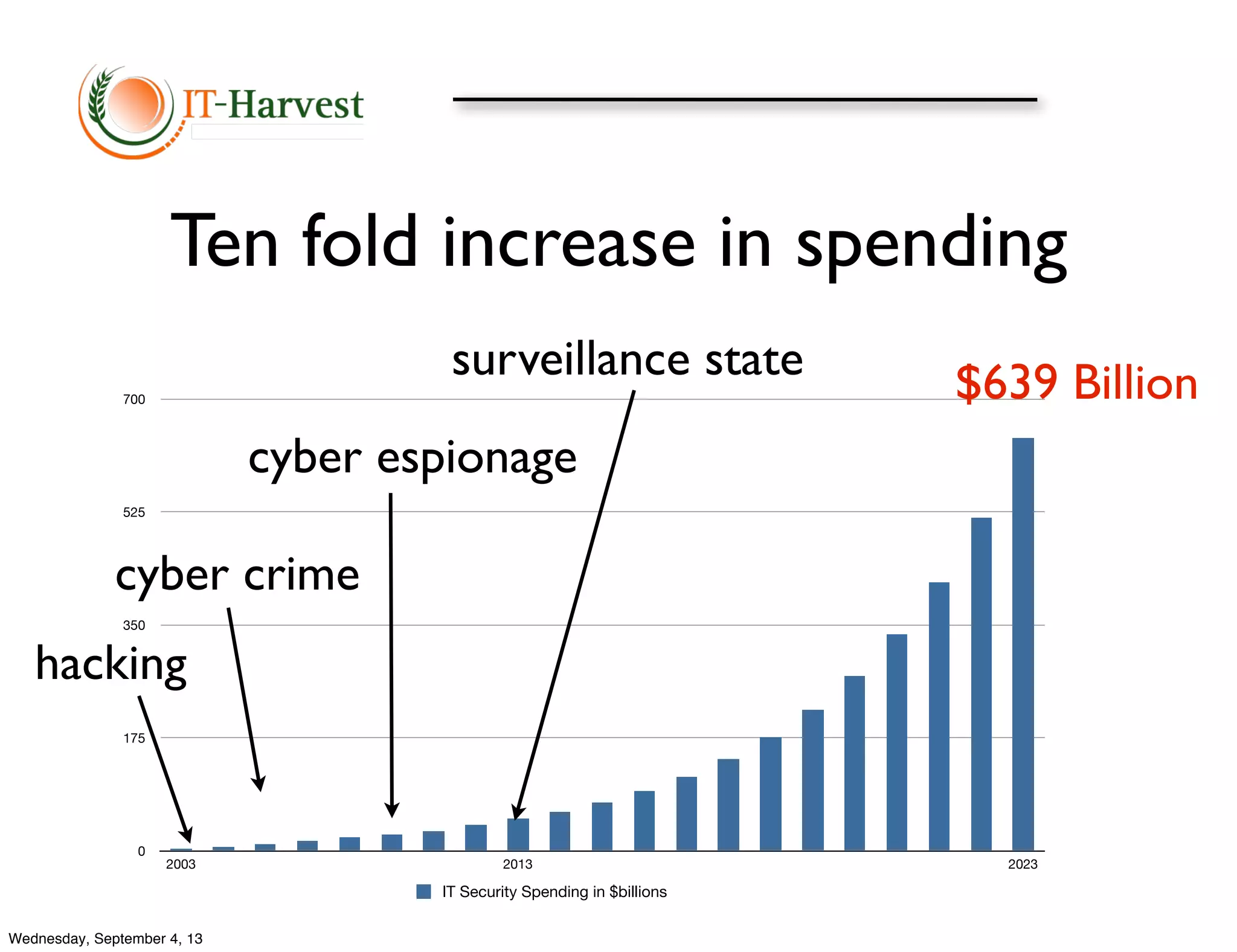
The document discusses how revelations about government surveillance programs are fundamentally changing IT security. It outlines how surveillance by intelligence agencies like the NSA poses a new top threat that is driving a massive increase in security spending by companies to protect themselves and their customers. Trillions will be spent in the coming years on encryption and other security measures to prevent spying and safeguard private information in response to the new risks presented by global government surveillance programs.