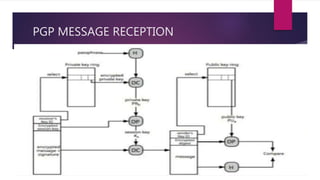
The document discusses email security, highlighting the importance of confidentiality, authentication, integrity, and non-repudiation. It details methods such as Privacy Enhanced Mail (PEM) and Pretty Good Privacy (PGP), explaining their processes for ensuring secure email communication through techniques like digital signatures, encryption, and compression. Additionally, it introduces S/MIME as an enhancement for secure multipurpose internet mail with various cryptographic algorithms.























![SIGNED MAIL
1. The user writes the message as clear-text .
2.The message digest is being calculated
(using SHA-1[2] or MD5[3])
3.The message digest is being encrypted using the signer’s private key
(DSS[4] or RSA[5]).](https://image.slidesharecdn.com/networksecurity-220206135236/85/Network-security-25-320.jpg)

![ENCRYPTED MAIL
1.The user writes the message as clear-text
2.A random session key is being created(triple DES[6] or rc2[7])
3.The message is being encrypted using the random session key.
4. For every recipient ,the session key is being encrypted using the recipient’s
public key(DH[8] or RSA[5]).](https://image.slidesharecdn.com/networksecurity-220206135236/85/Network-security-27-320.jpg)



