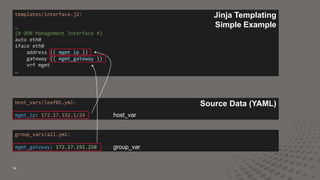
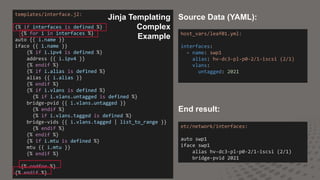
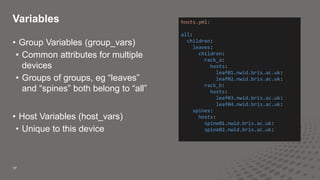
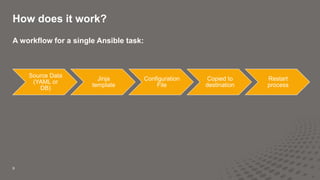
This document discusses using Ansible and Python to automate network configuration. It provides examples of using Ansible to initially provision and consistently configure switches in a data center network. Templates and variables are used to generate configuration files that are deployed using Ansible roles and plays. This allows the network to be rapidly built, changed, and validated in an automated and consistent manner.








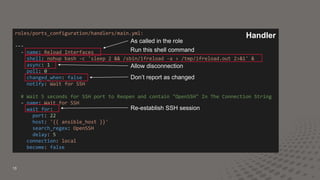
![10
---
- name: Configure Cumulus Linux Switches
hosts: all
become: yes
gather_facts: False
pre_tasks:
- name: Create ports.conf list for 100G switch
set_fact: ports_list_qsfp="{{ ports_40g | ports_list_100G }}"
when: ports_40g is defined
- name: Create ports.conf list for 25G switch
set_fact: ports_list_sfp="{{ ports_10g | ports_list_25G }}"
when: ports_10g is defined
- name: Create vlan_range used in jinja2 later
set_fact:
vlan_range: "{{ vlans | json_query('[*].number') | list_to_range }}"
when: vlans is defined
roles:
# Only required on first installation
# - base_config
# Normal roles
- ports_configuration
- interface_configuration
- routing_configuration
Run on all hosts
“sudo”
Run these
things first
Variable with a filter
Inherit other tasks
and variables
Example Playbook:
Configures a Cumulus
Leaf & Spine Network](https://image.slidesharecdn.com/thurs1000lt5elliott-190412133943/85/Network-automation-with-Ansible-and-Python-10-320.jpg)
![11
filter_plugins/custom_filters.py:
#!/usr/bin/env python
# [1, 3, 4, 7, 8, 9] becomes "1 3-4 7-9"
def list_to_range(numlist):
newlist = sorted(set(numlist))
output = ''
i = 0
while i < len(newlist):
nextval = ''
if i + 1 < len(newlist) and newlist[i + 1] == newlist[i] + 1:
nextval += (str(newlist[i]) + '-')
while(i + 1 < len(newlist) and newlist[i + 1] == newlist[i] + 1):
i += 1
nextval += (str(newlist[i]) + ' ')
i += 1
output += nextval
return(output[:-1])
class FilterModule(object):
def filters(self):
return {
'list_to_range': list_to_range
}
Python in Ansible
“filter_plugin”](https://image.slidesharecdn.com/thurs1000lt5elliott-190412133943/85/Network-automation-with-Ansible-and-Python-11-320.jpg)