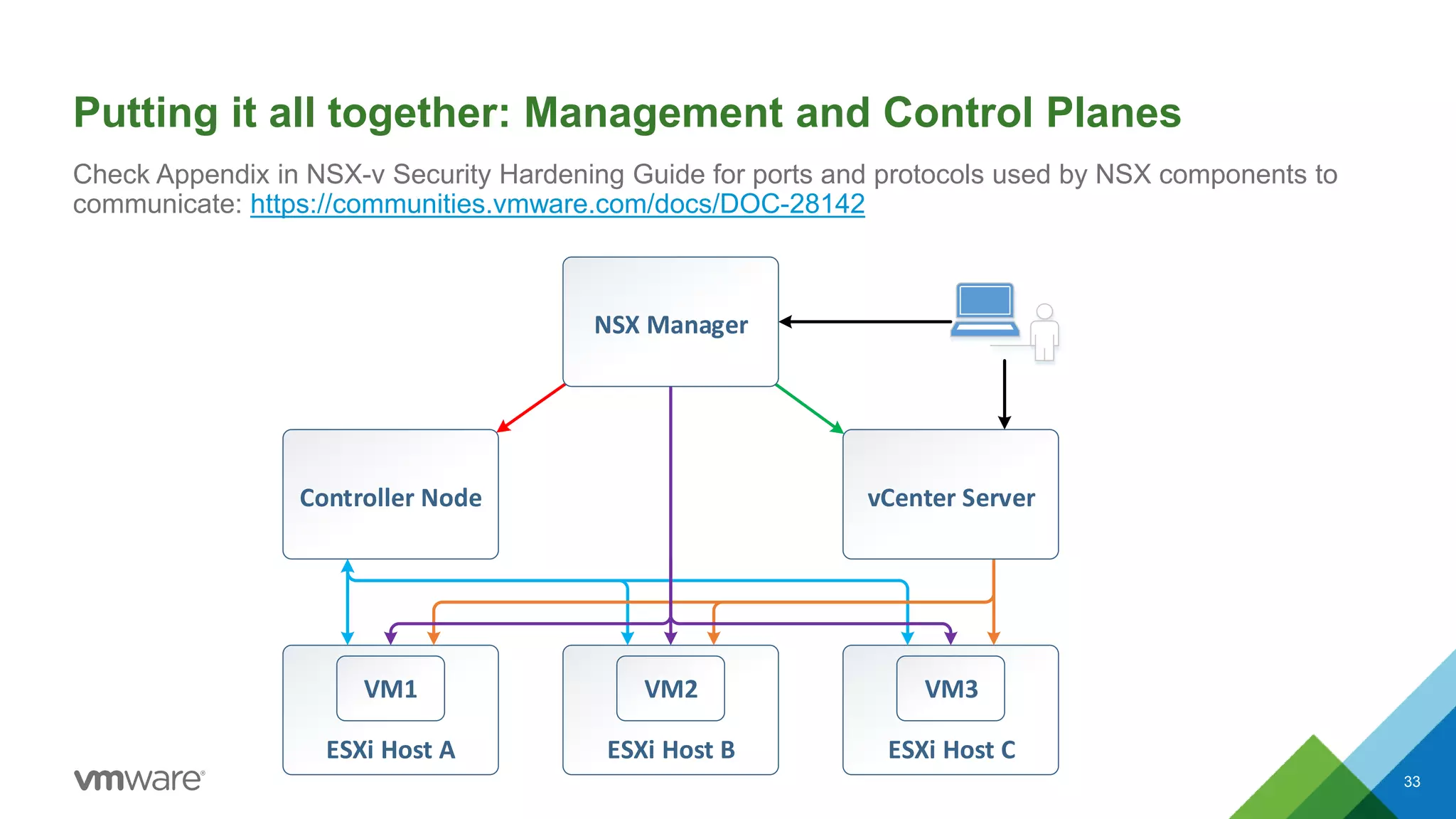
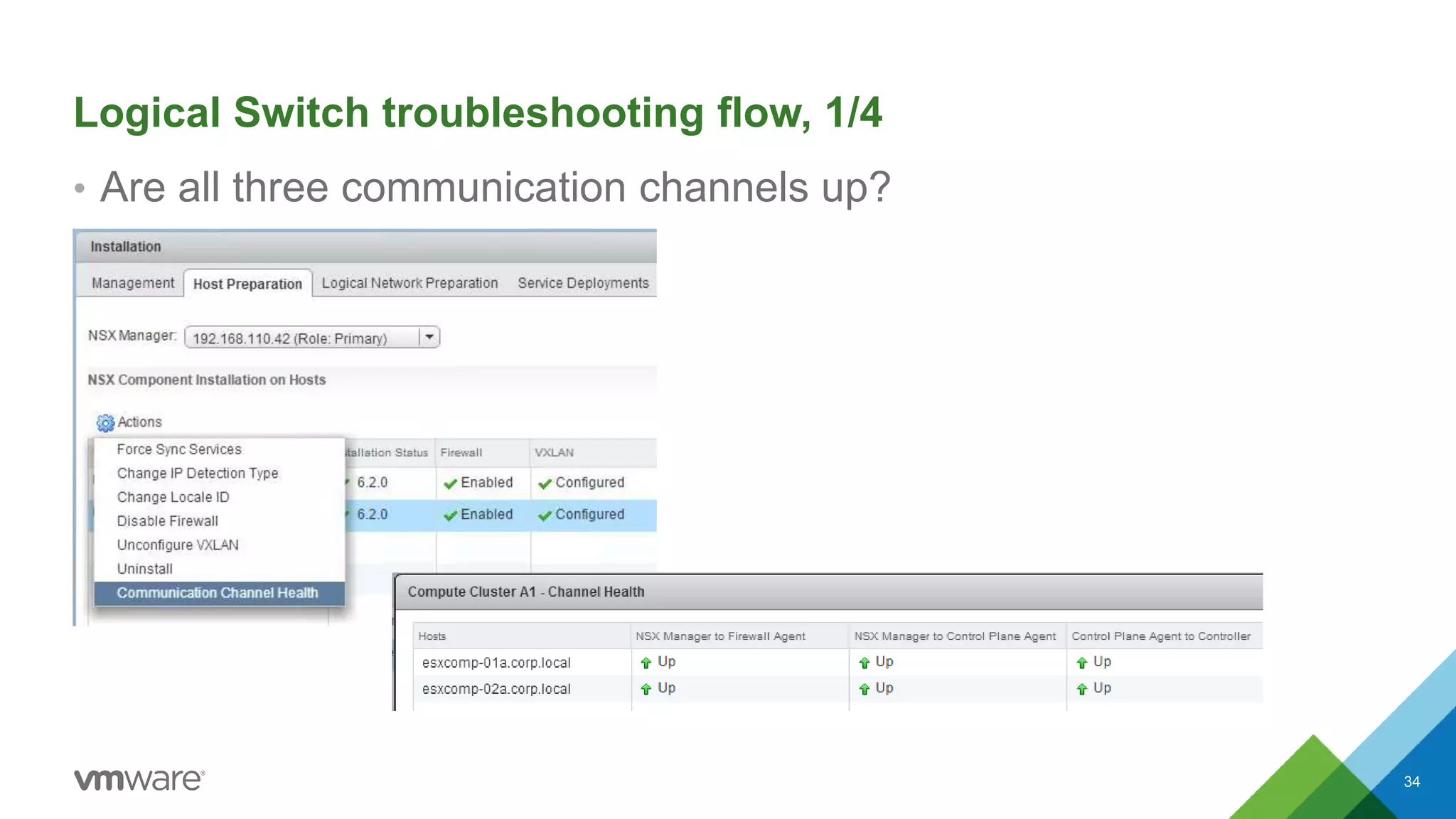
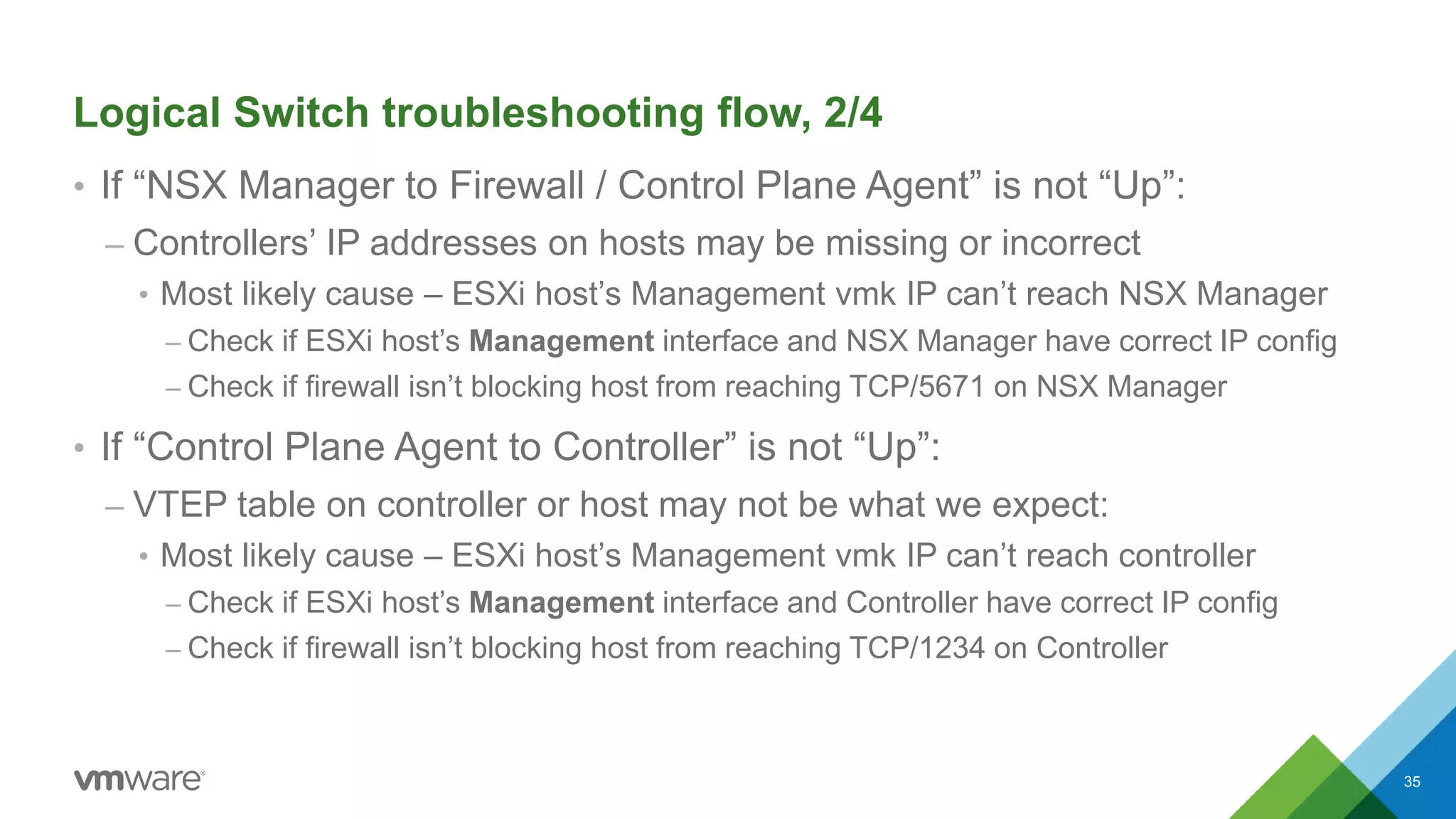
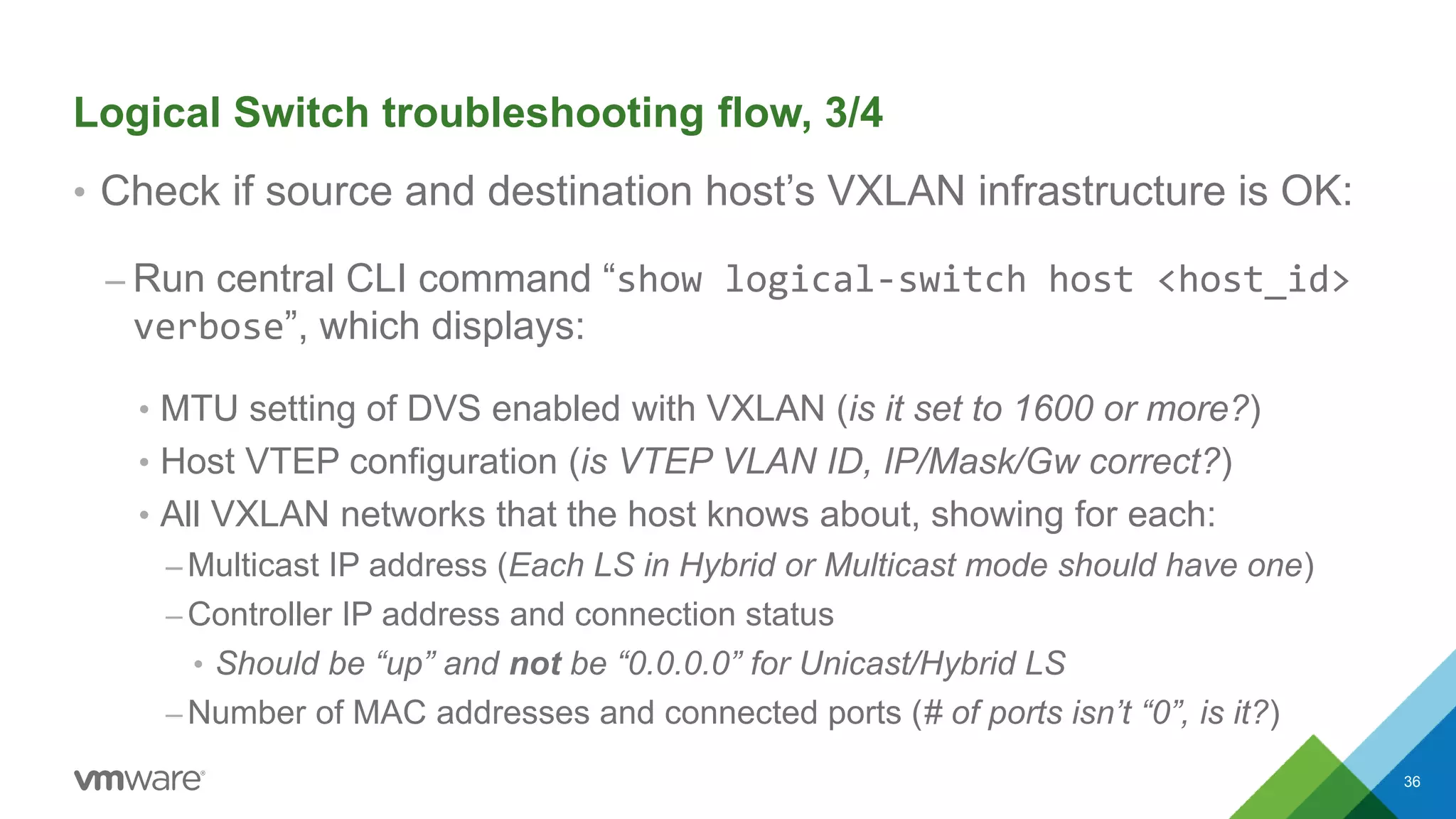
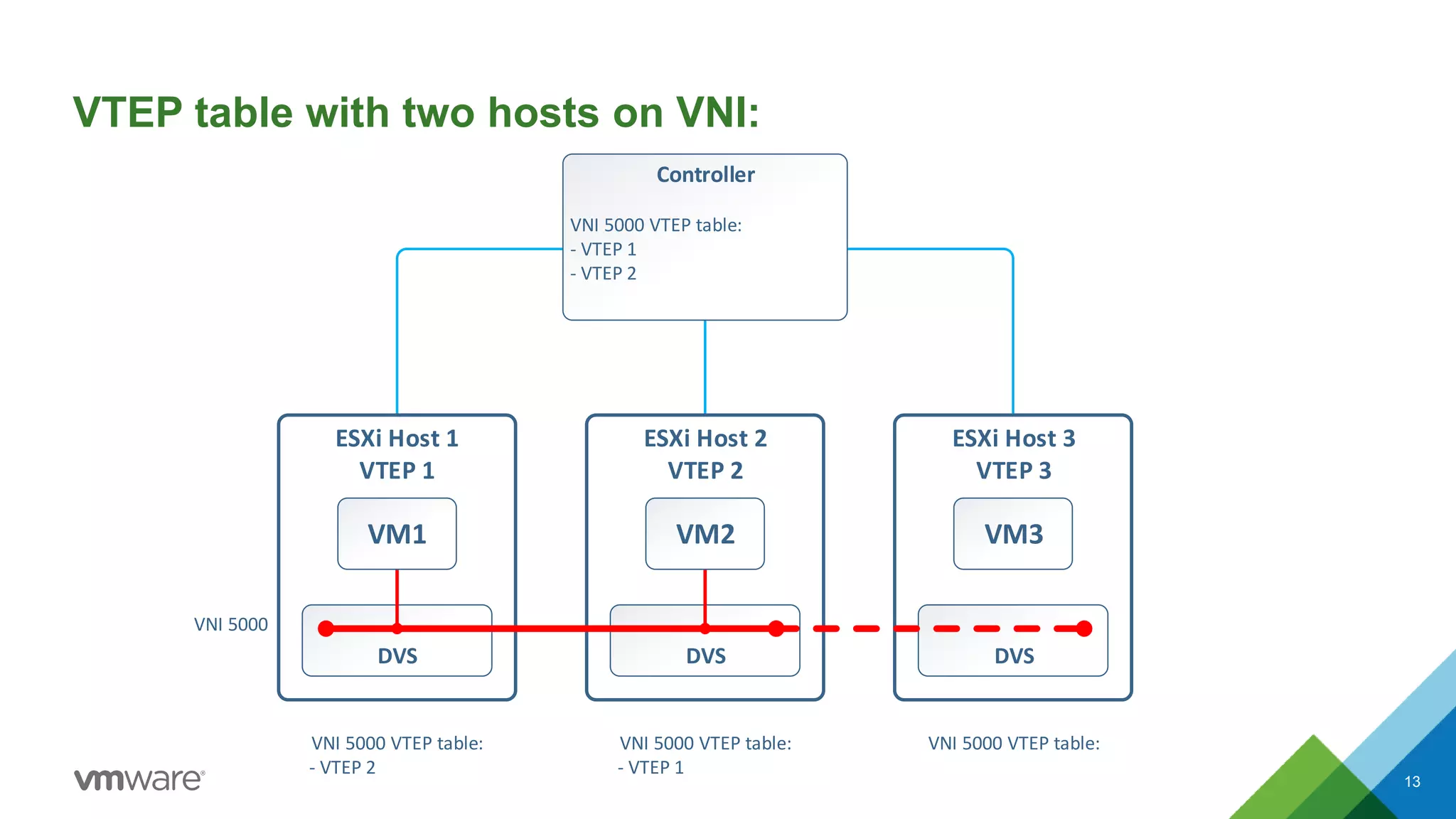
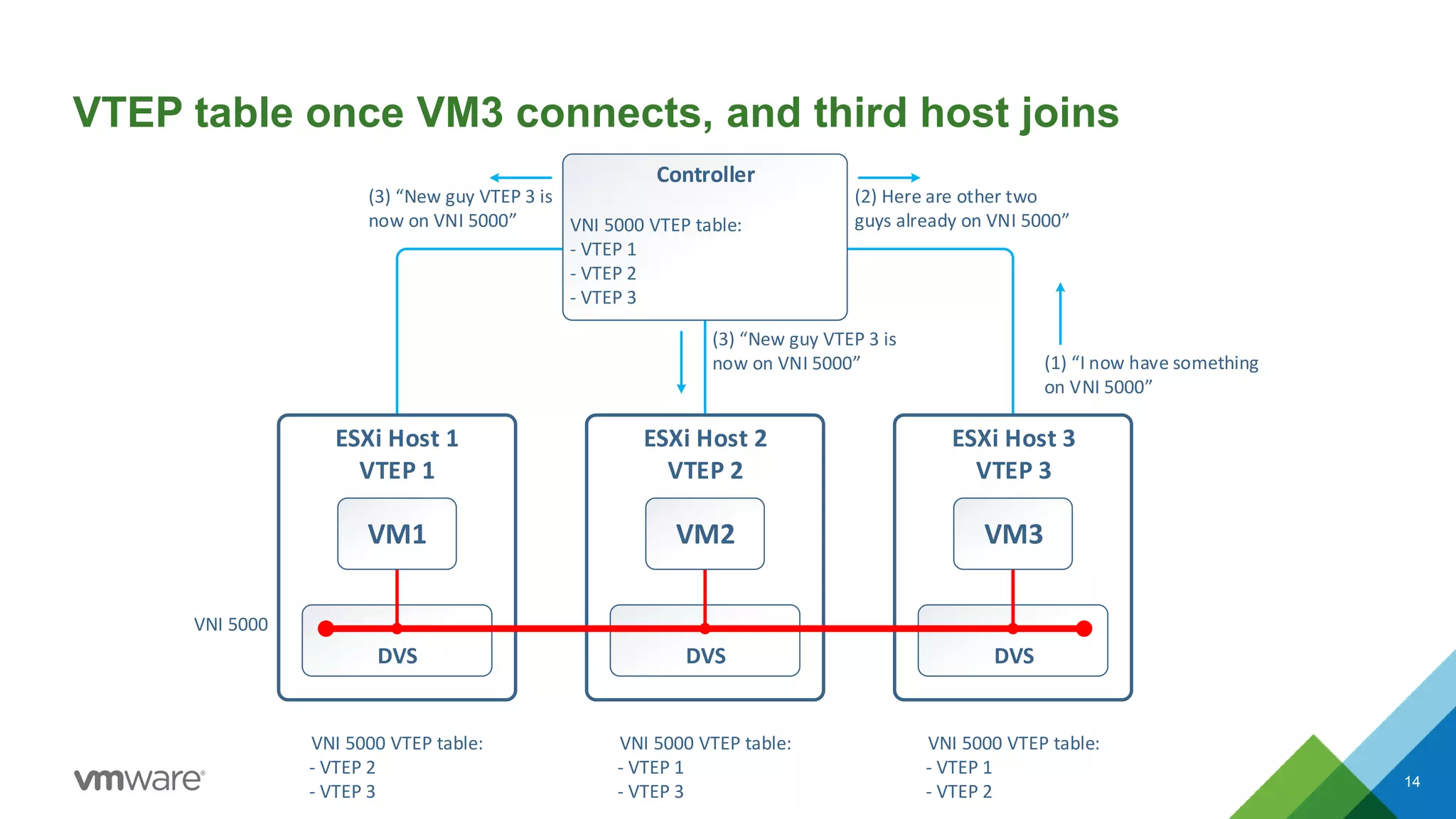
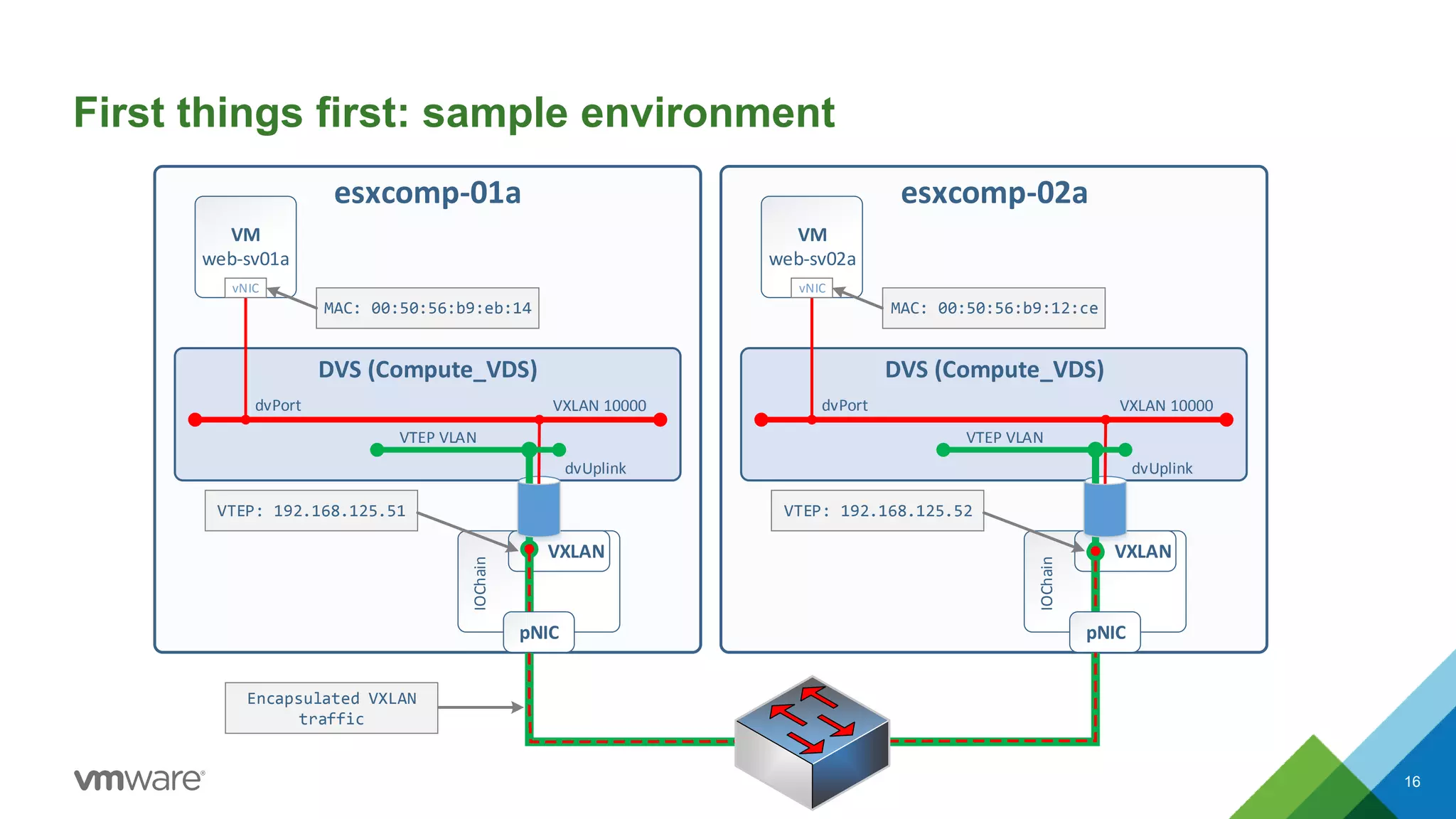
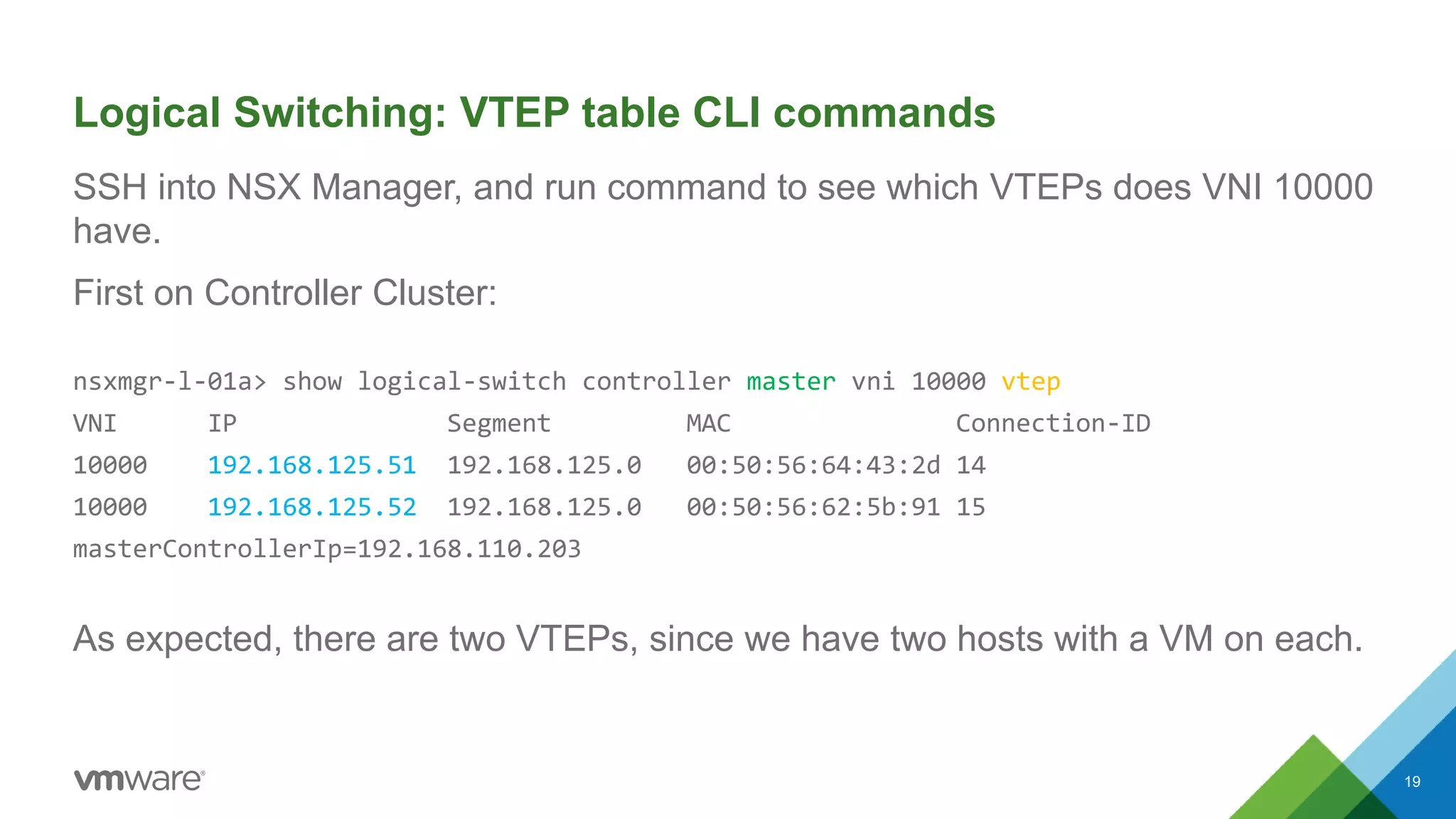
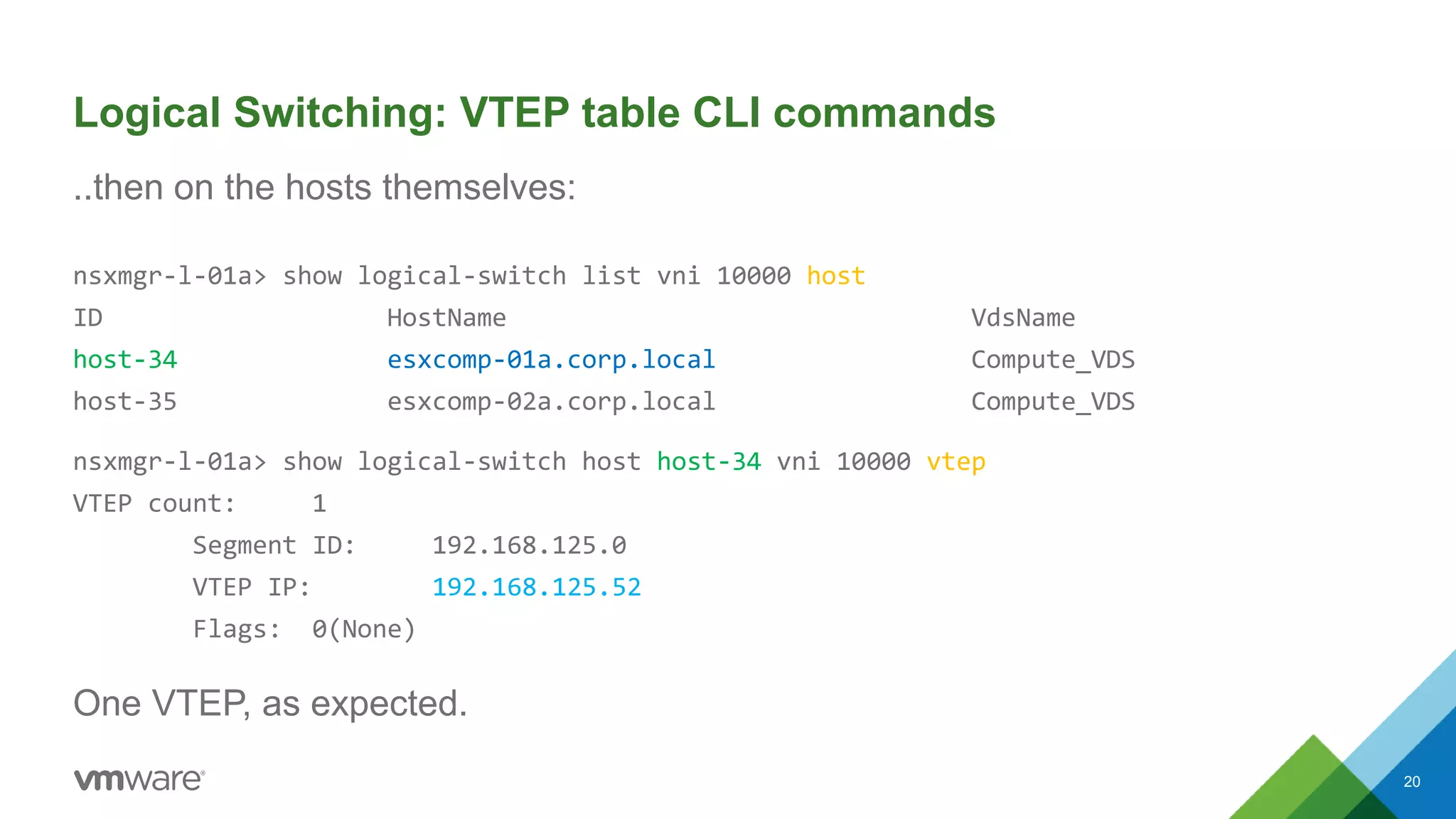
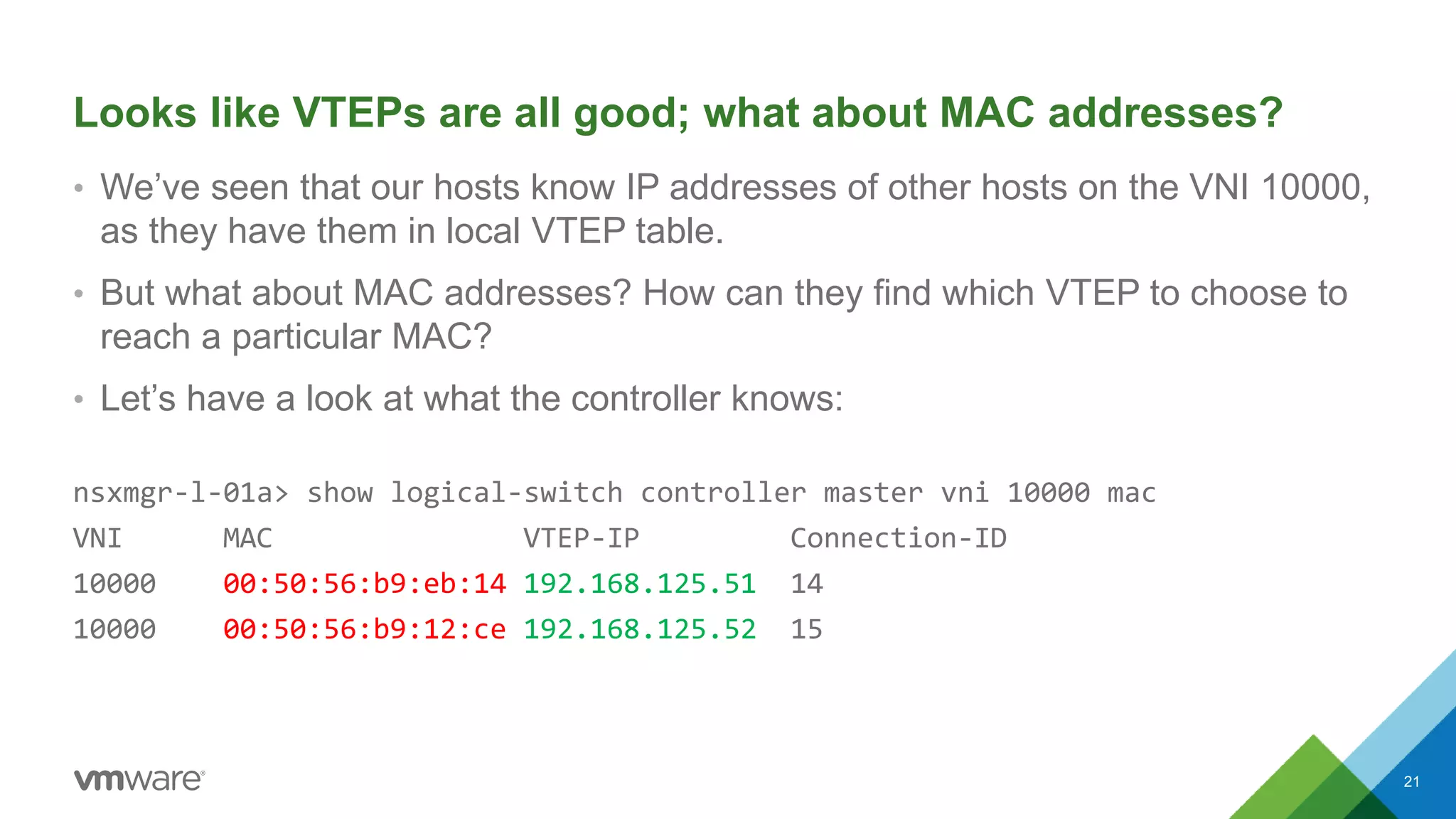
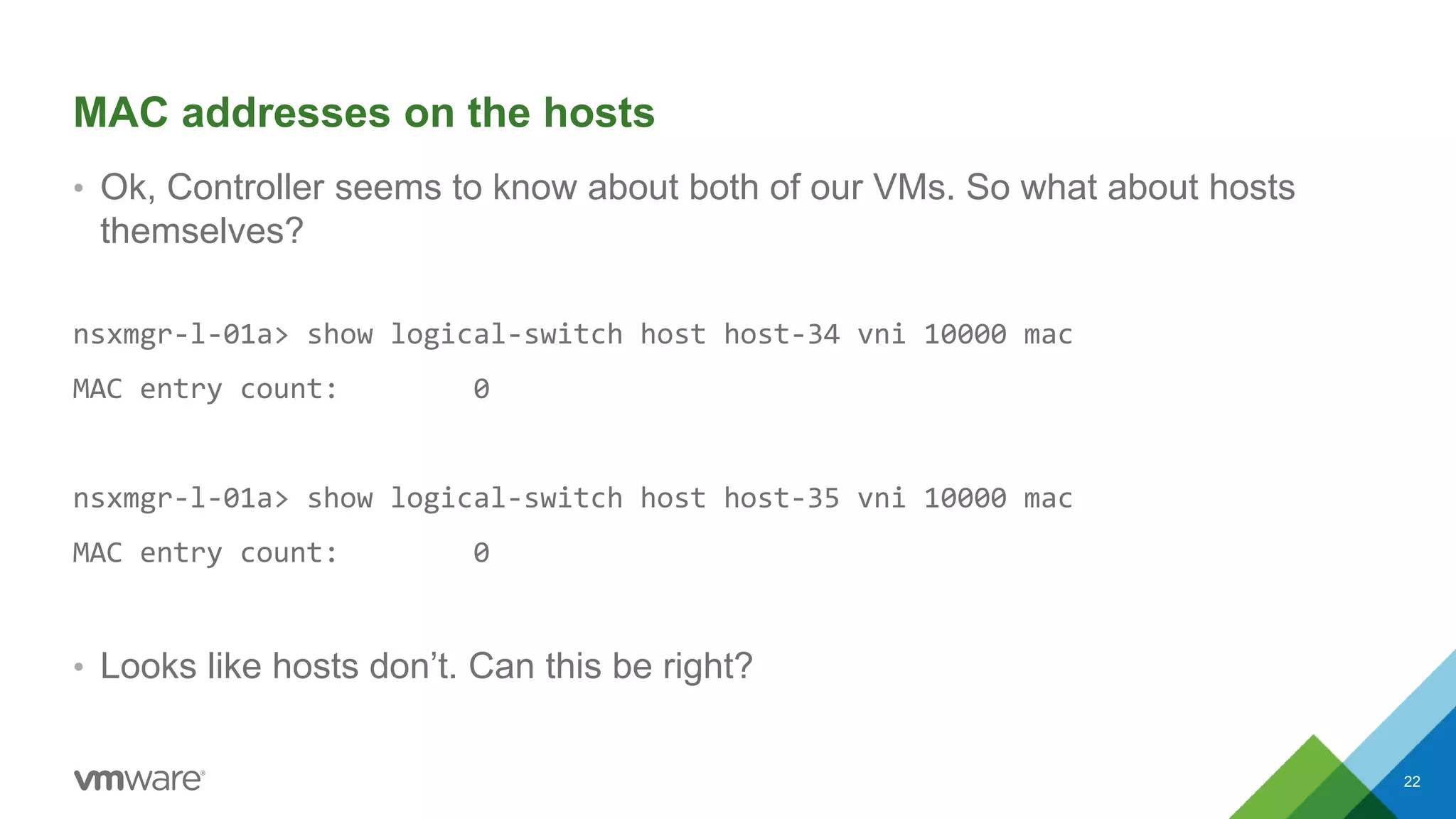
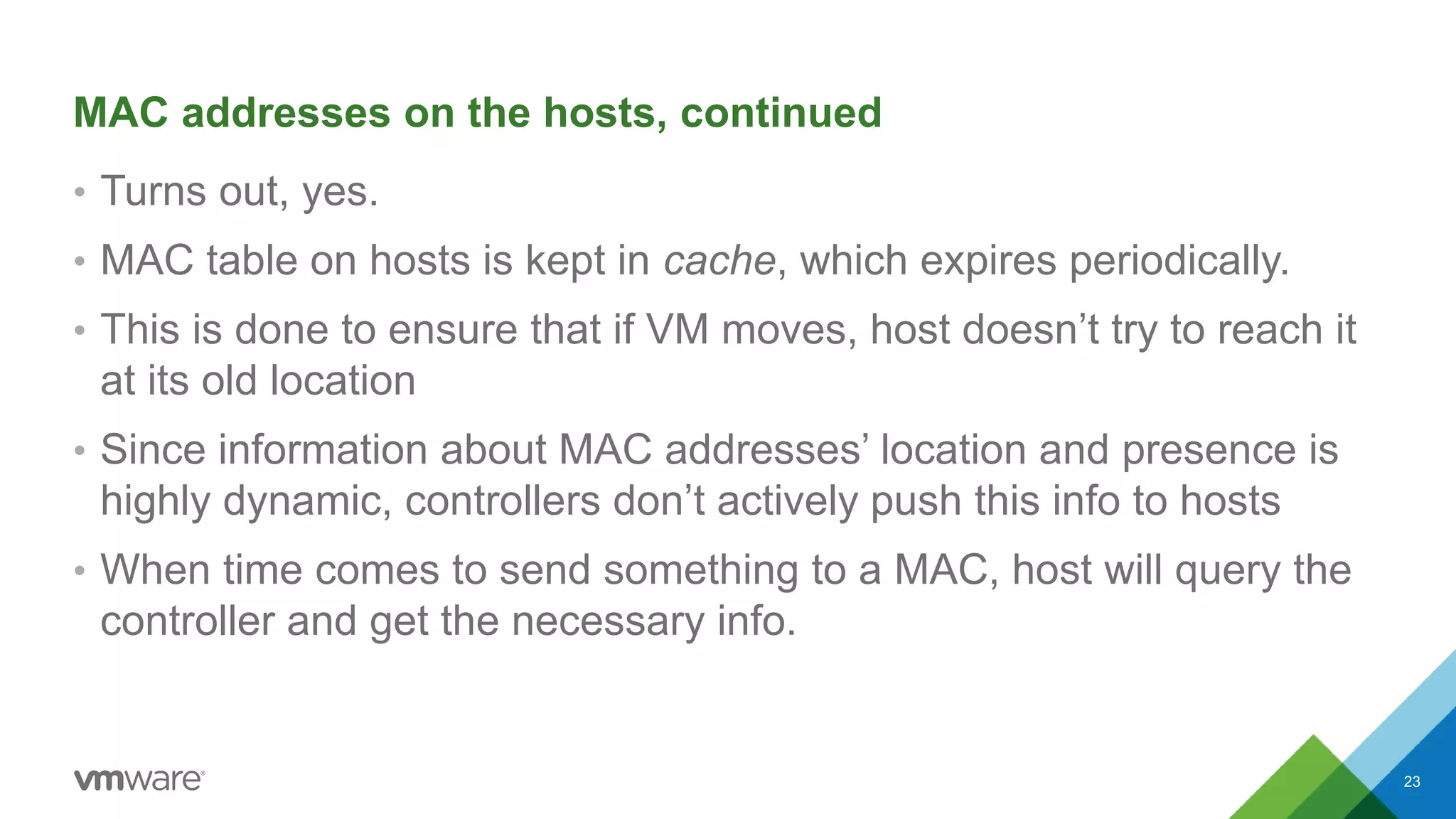
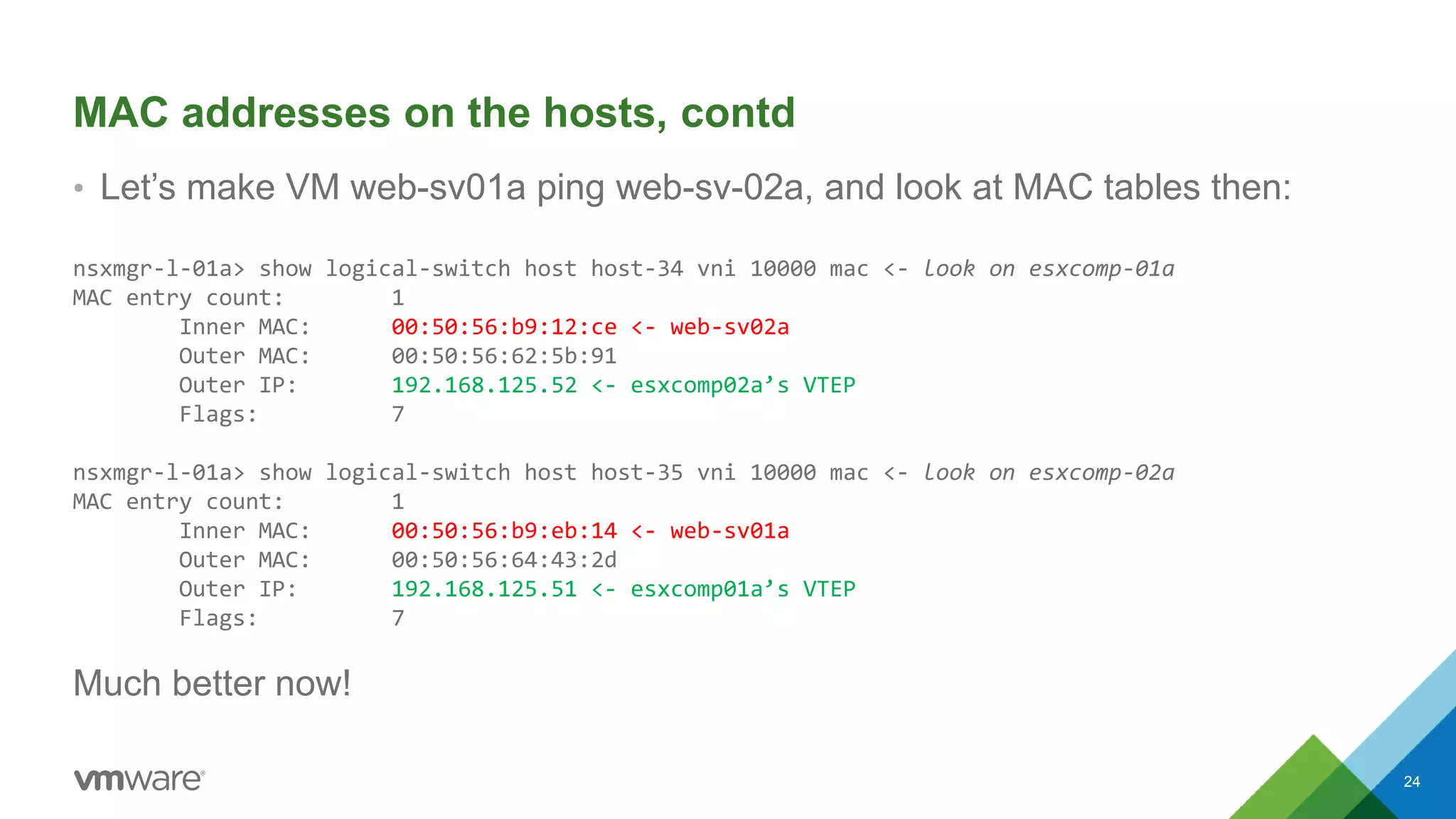
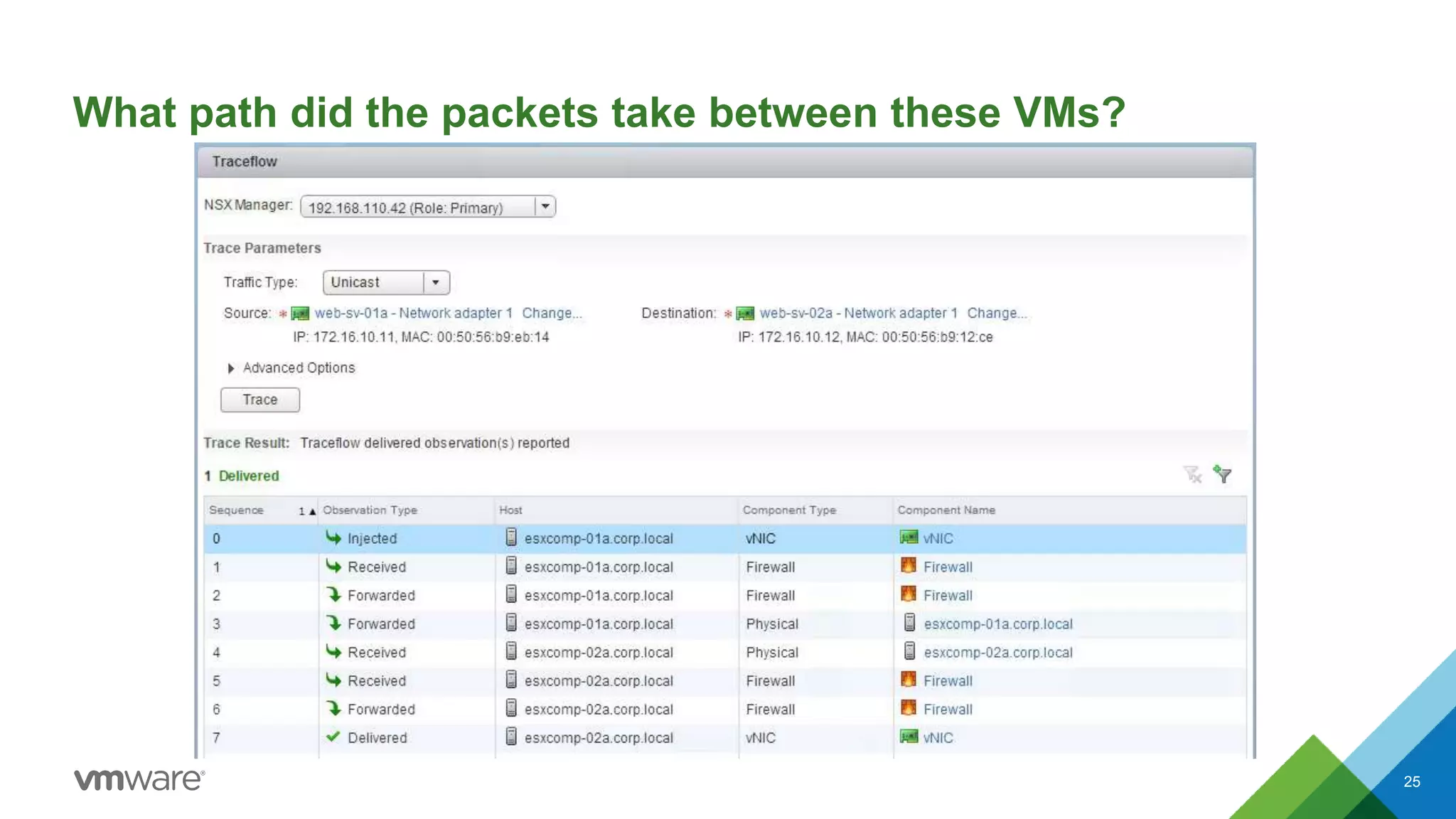
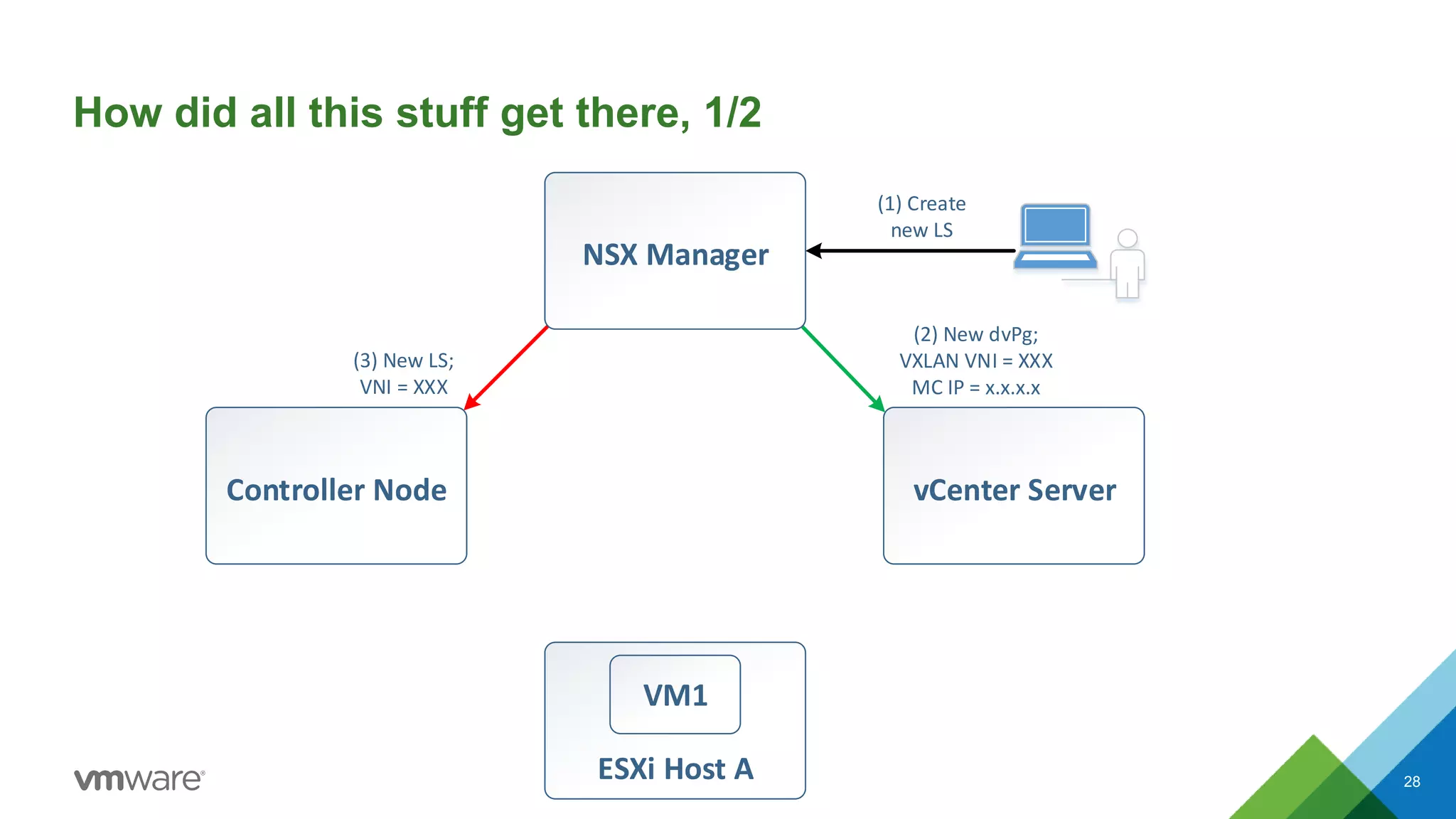
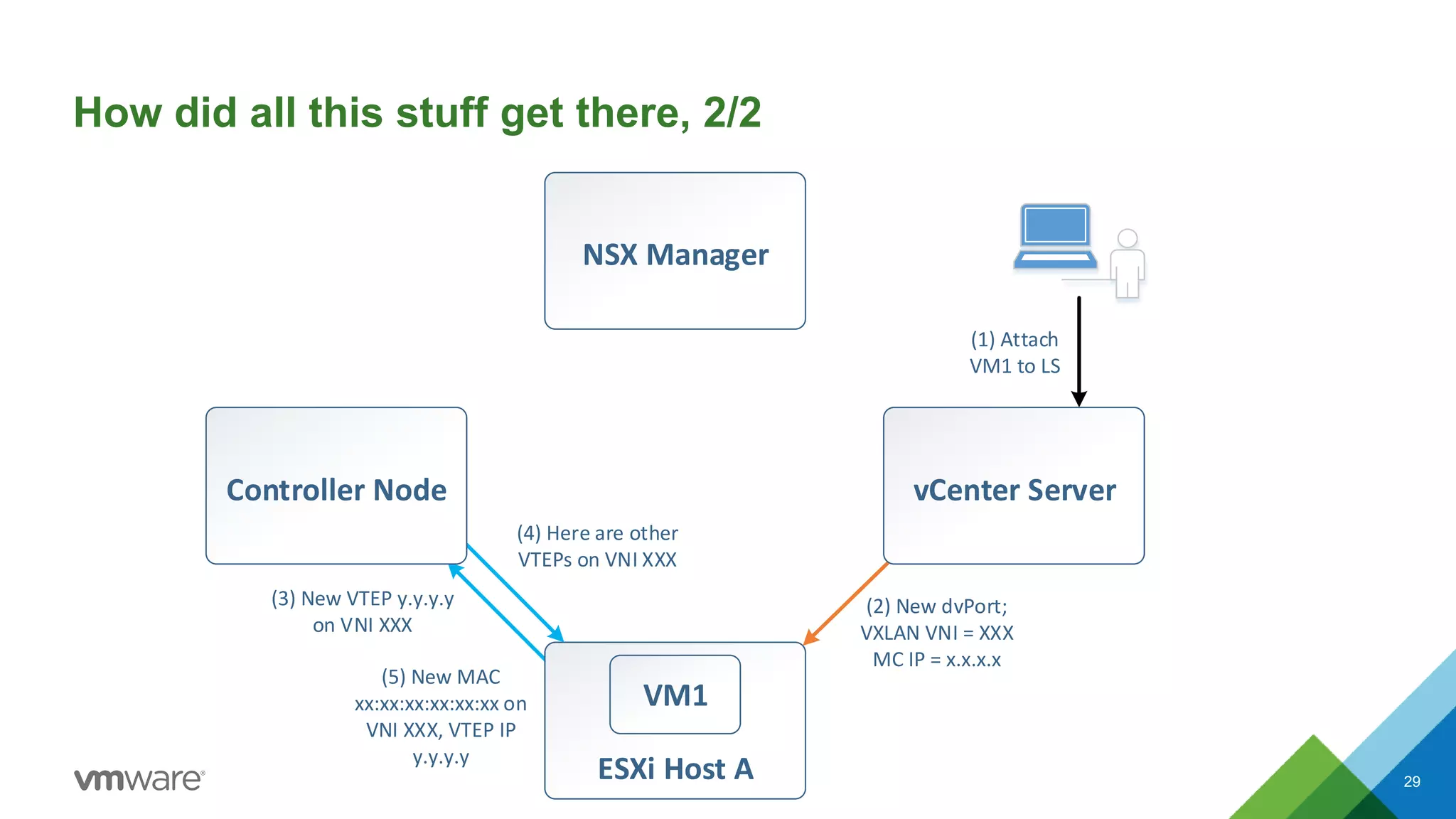
The document provides an overview of troubleshooting methodology for VMware NSX. It discusses that NSX implements logical switching and routing services on top of an IP transport network. The key things to check when troubleshooting include validating the IP transport connectivity using tools like ping, and examining the VTEP tables and MAC tables on the NSX controller and hosts for a given virtual network identifier (VNI) to understand virtual machine connectivity and forwarding. An example is provided where pinging between VMs populates the MAC tables on hosts, demonstrating how NSX forwarding works based on these tables.







![Transport connectivity verification
• Let’s verify that Transport connectivity works. To do this, log into one of the
ESXi hosts and run a vmkping command against other host’s VTEP IP. Force it
to set “do not fragment” flag and size of 1572 to test e2e MTU is correct, too:
[root@esxcomp-01a:~] vmkping ++netstack=vxlan -d -s 1572 192.168.125.52
PING 192.168.125.52 (192.168.125.52): 1572 data bytes
1580 bytes from 192.168.125.52: icmp_seq=0 ttl=64 time=0.715 ms
1580 bytes from 192.168.125.52: icmp_seq=1 ttl=64 time=1.094 ms
1580 bytes from 192.168.125.52: icmp_seq=2 ttl=64 time=0.860 ms
--- 192.168.125.52 ping statistics ---
3 packets transmitted, 3 packets received, 0% packet loss
round-trip min/avg/max = 0.715/0.890/1.094 ms
17](https://image.slidesharecdn.com/net5488kalintsev1-151019033035-lva1-app6892/75/NET5488-Troubleshooting-Methodology-for-VMware-NSX-VMworld-2015-17-2048.jpg)
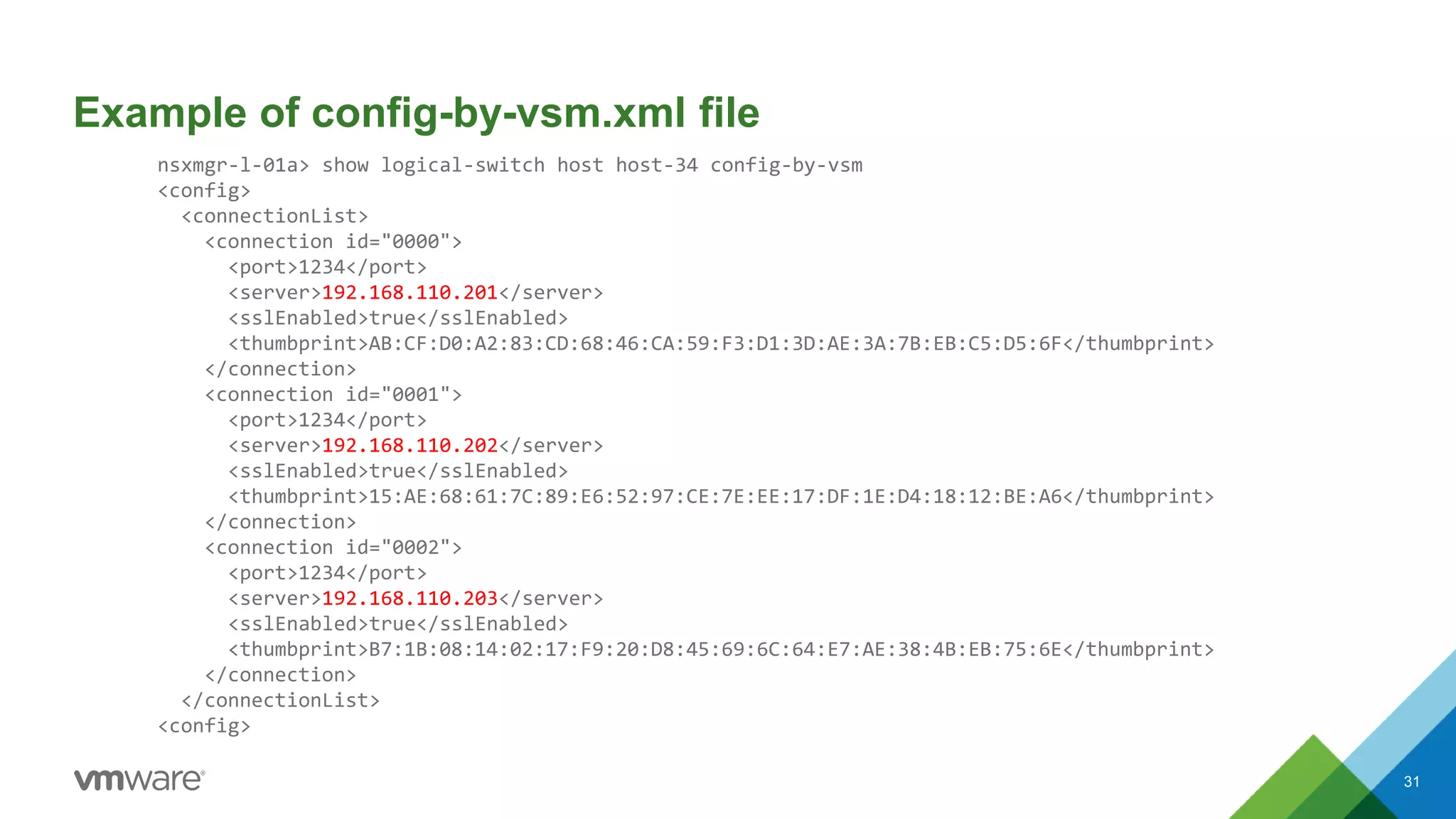
![dvPort opaque attributes – can I see them?
• Yes, you can. They are shown in the “net-dvs -l” ESXi CLI output:
[root@esxcomp-01a:~] net-stats -l
PortNum Type SubType SwitchName MACAddress ClientName
[..skip..]
50331657 5 9 DvsPortset-0 00:50:56:b9:eb:14 web-sv01a.eth0
[root@esxcomp-01a:~] net-dvs -l | grep -B 30 50331657 | grep vxlan
com.vmware.net.vxlan.cp = 0x 0. 0. 0. 1 <- control plane (1=Yes)
com.vmware.net.vxlan.id = 0x 0. 0.27.10 <- VNI (in Hex)
com.vmware.net.vxlan.mcastip = 0x 0. 0. 0. 1 <- MC IP (0.0.0.1=Unicast)
[root@esxcomp-01a:~] printf "%dn" 0x2710
10000
32](https://image.slidesharecdn.com/net5488kalintsev1-151019033035-lva1-app6892/75/NET5488-Troubleshooting-Methodology-for-VMware-NSX-VMworld-2015-32-2048.jpg)