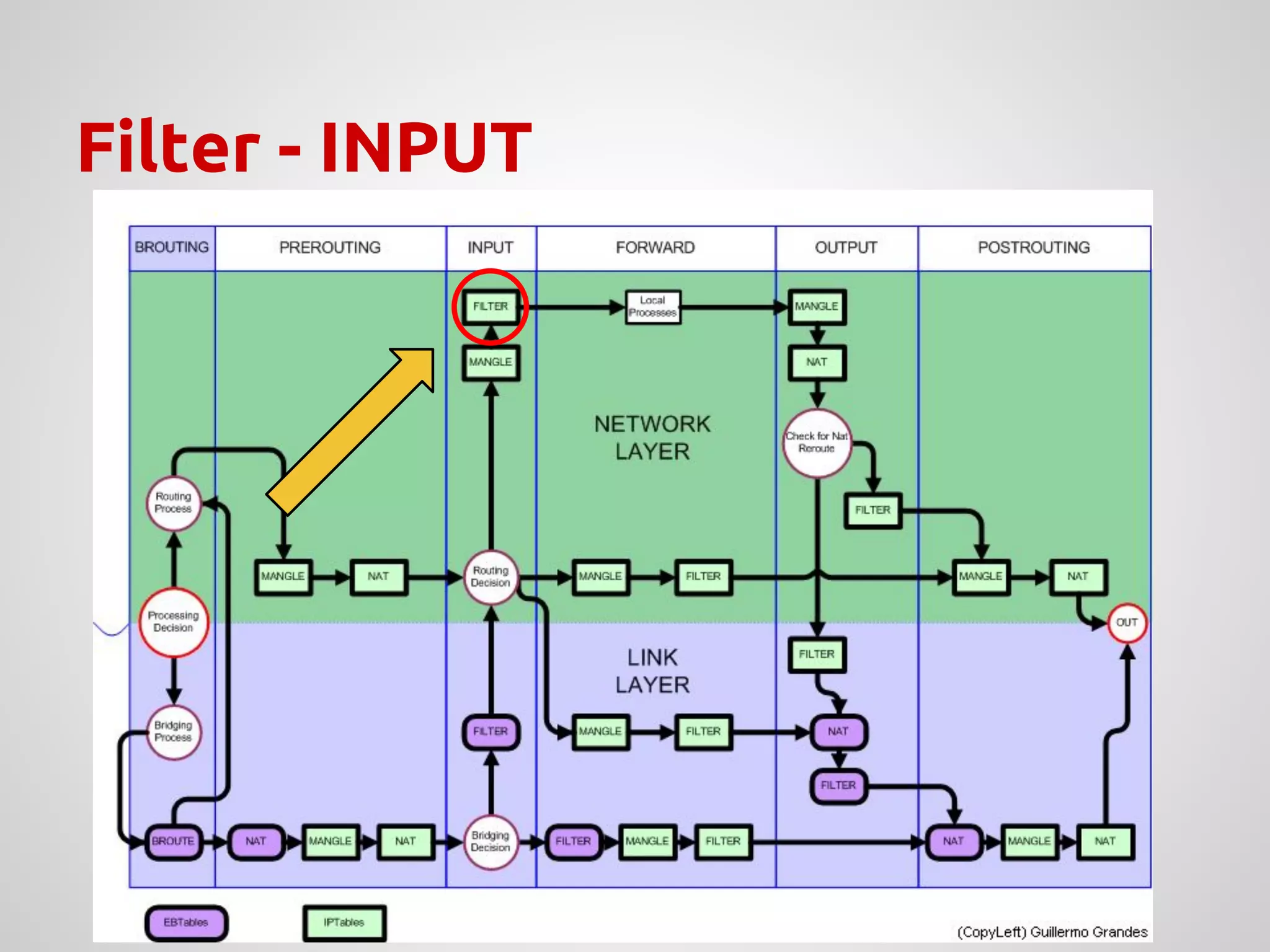
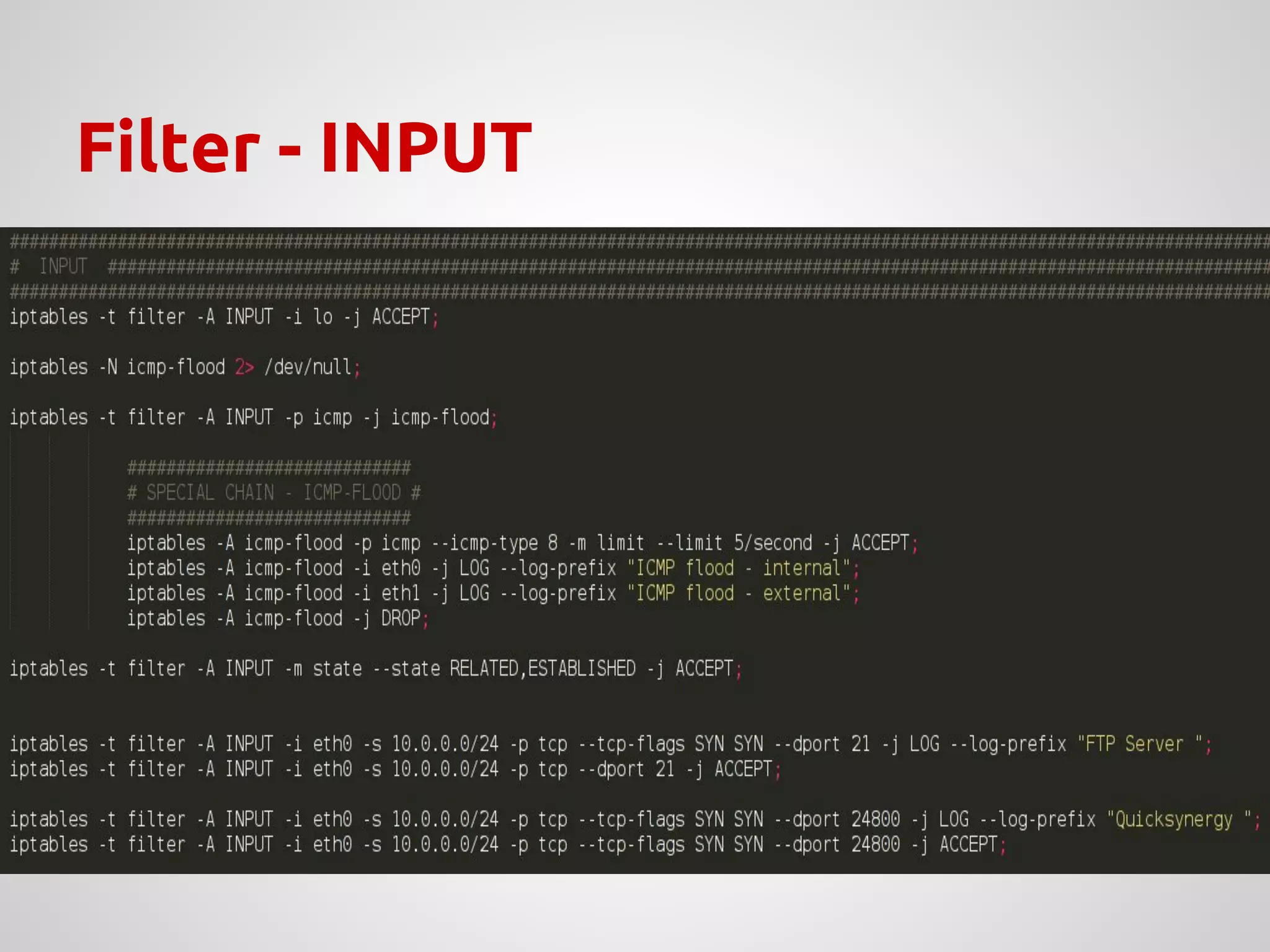
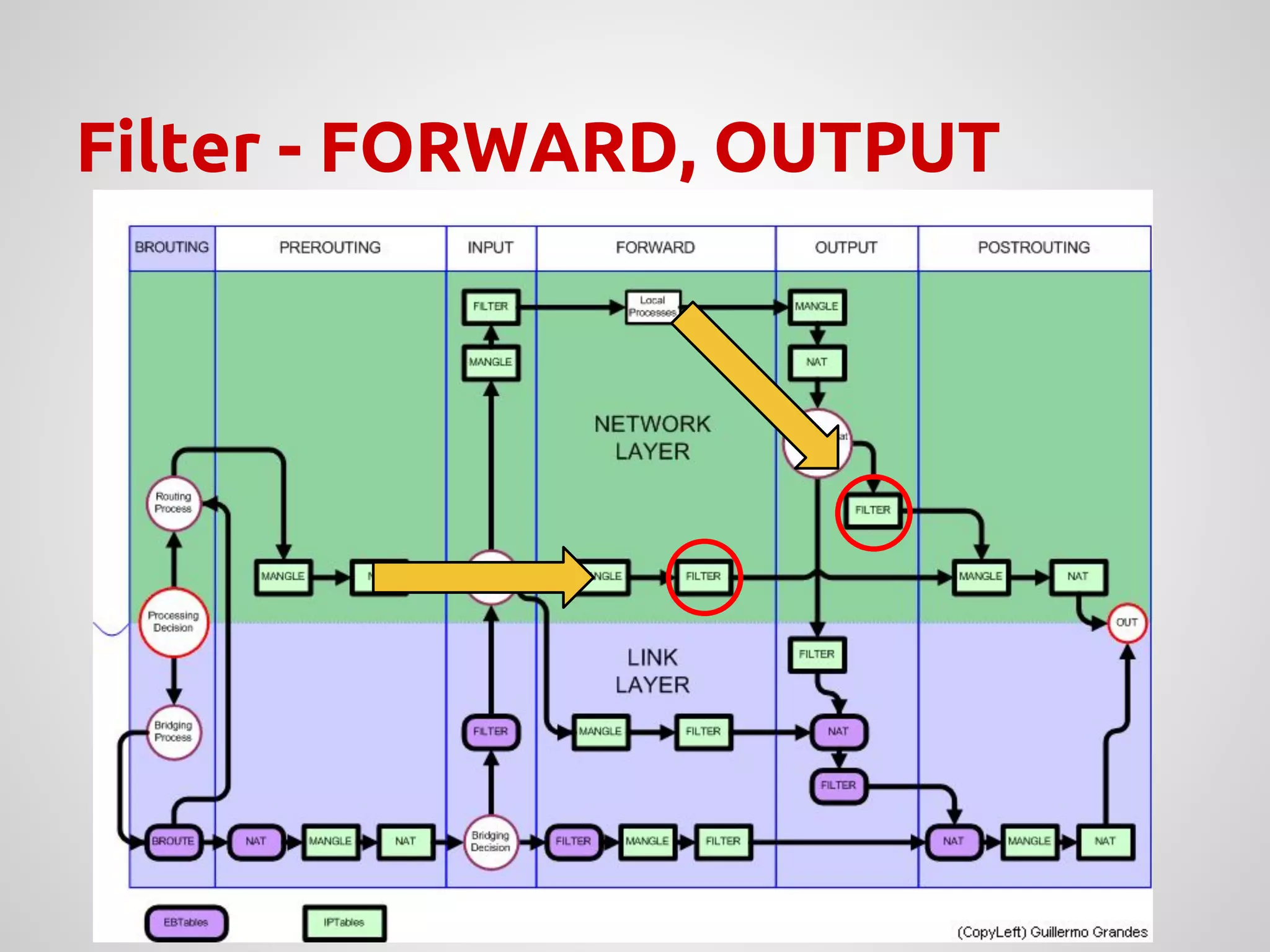
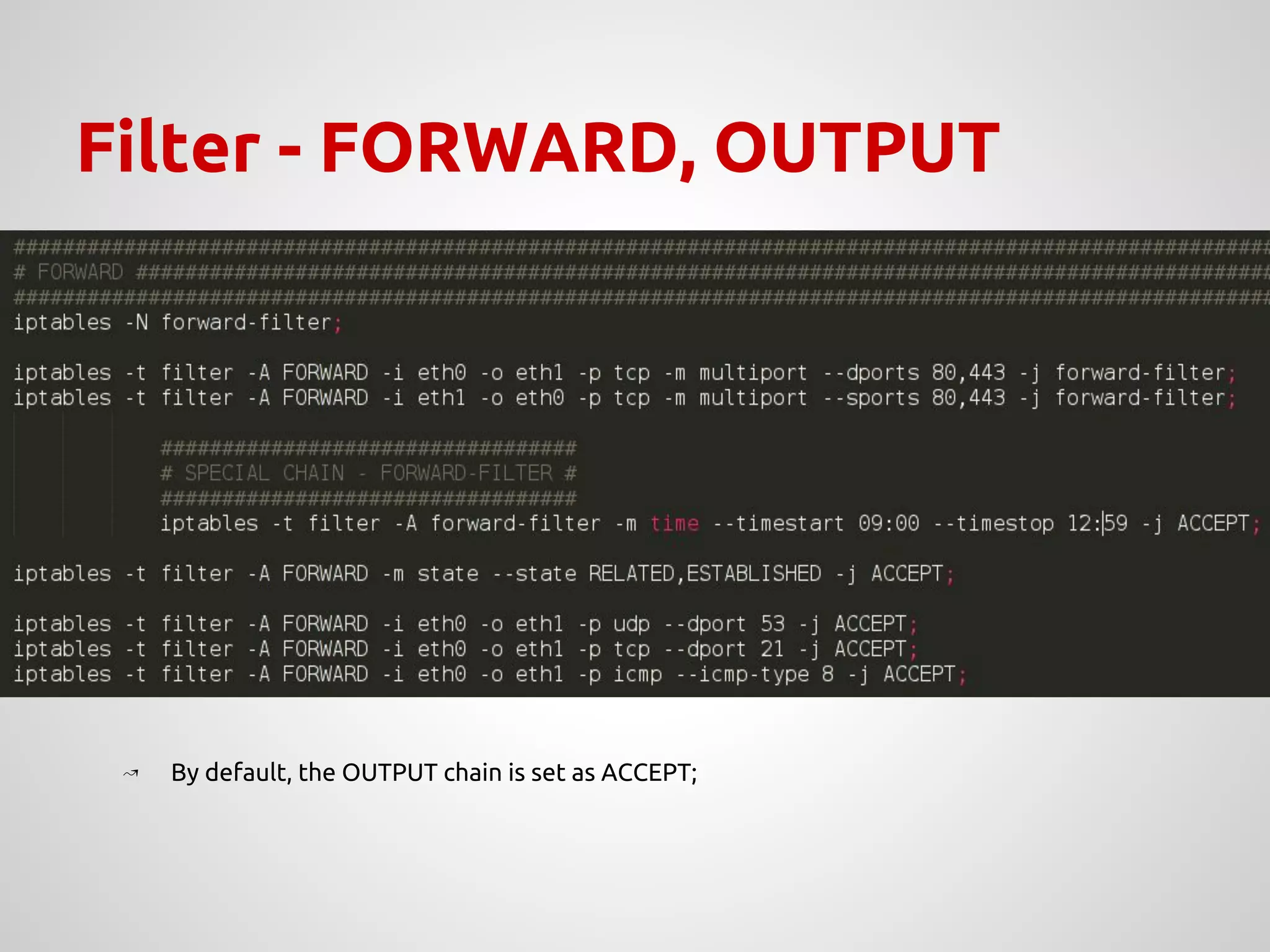
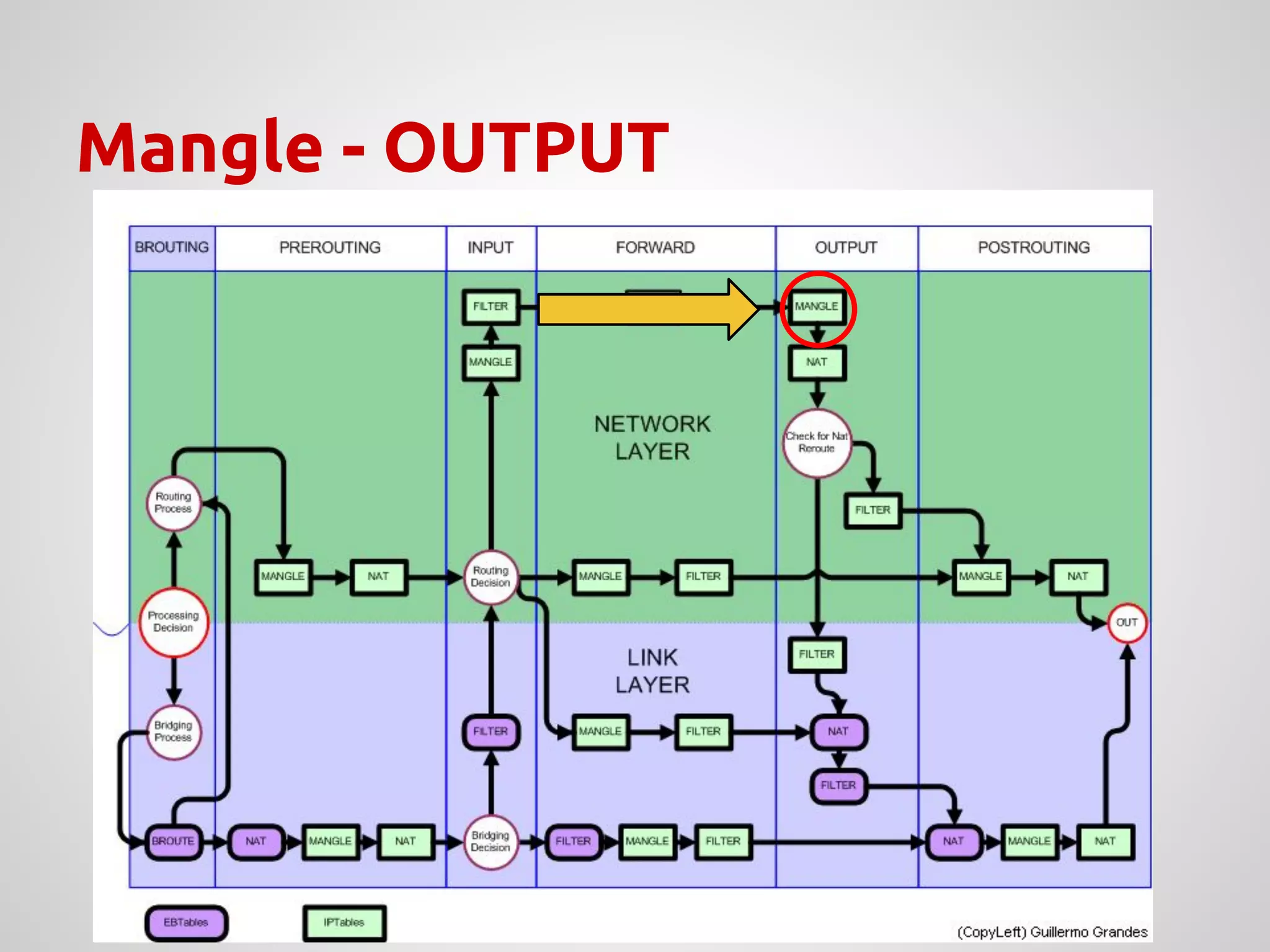
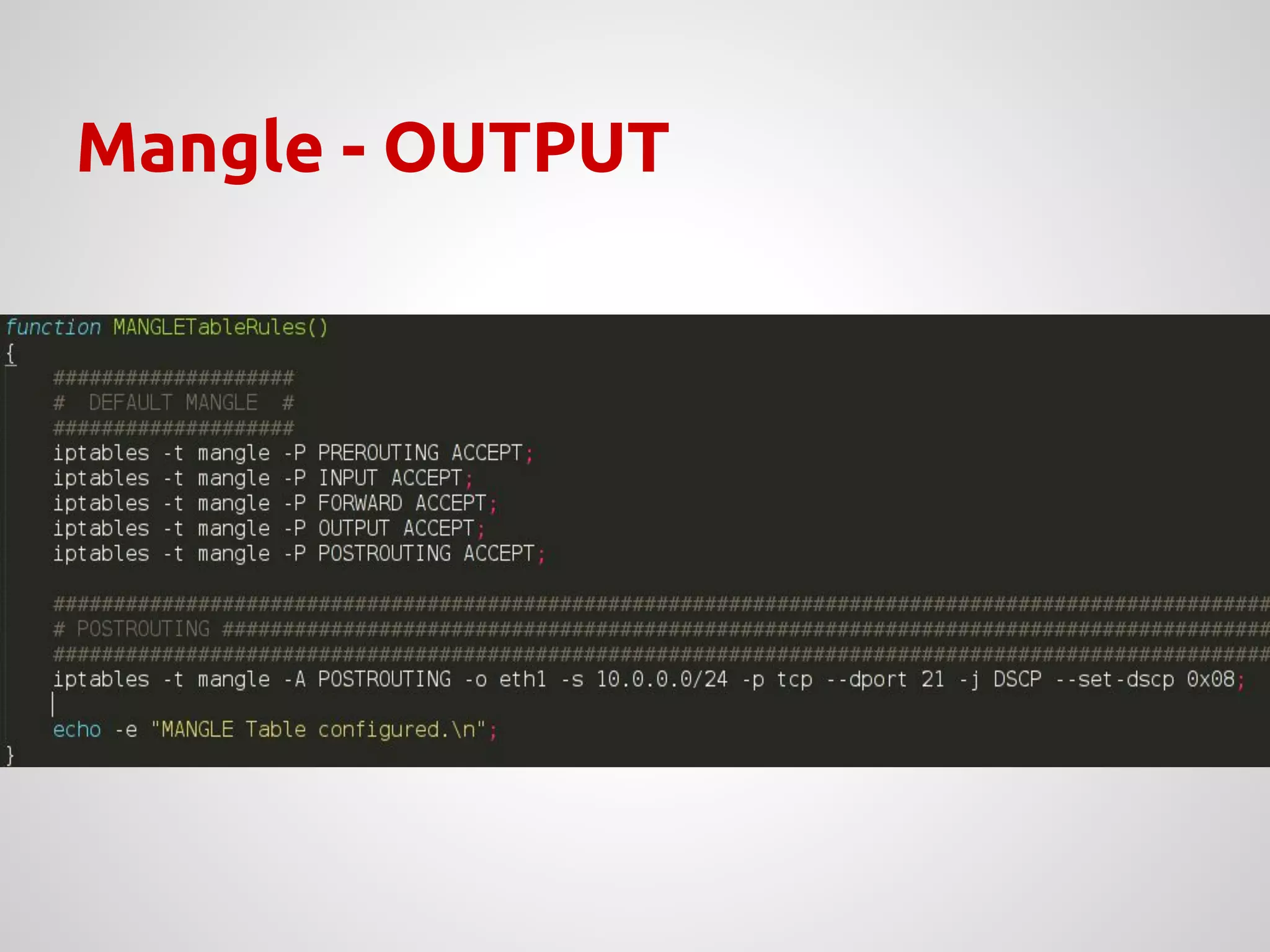
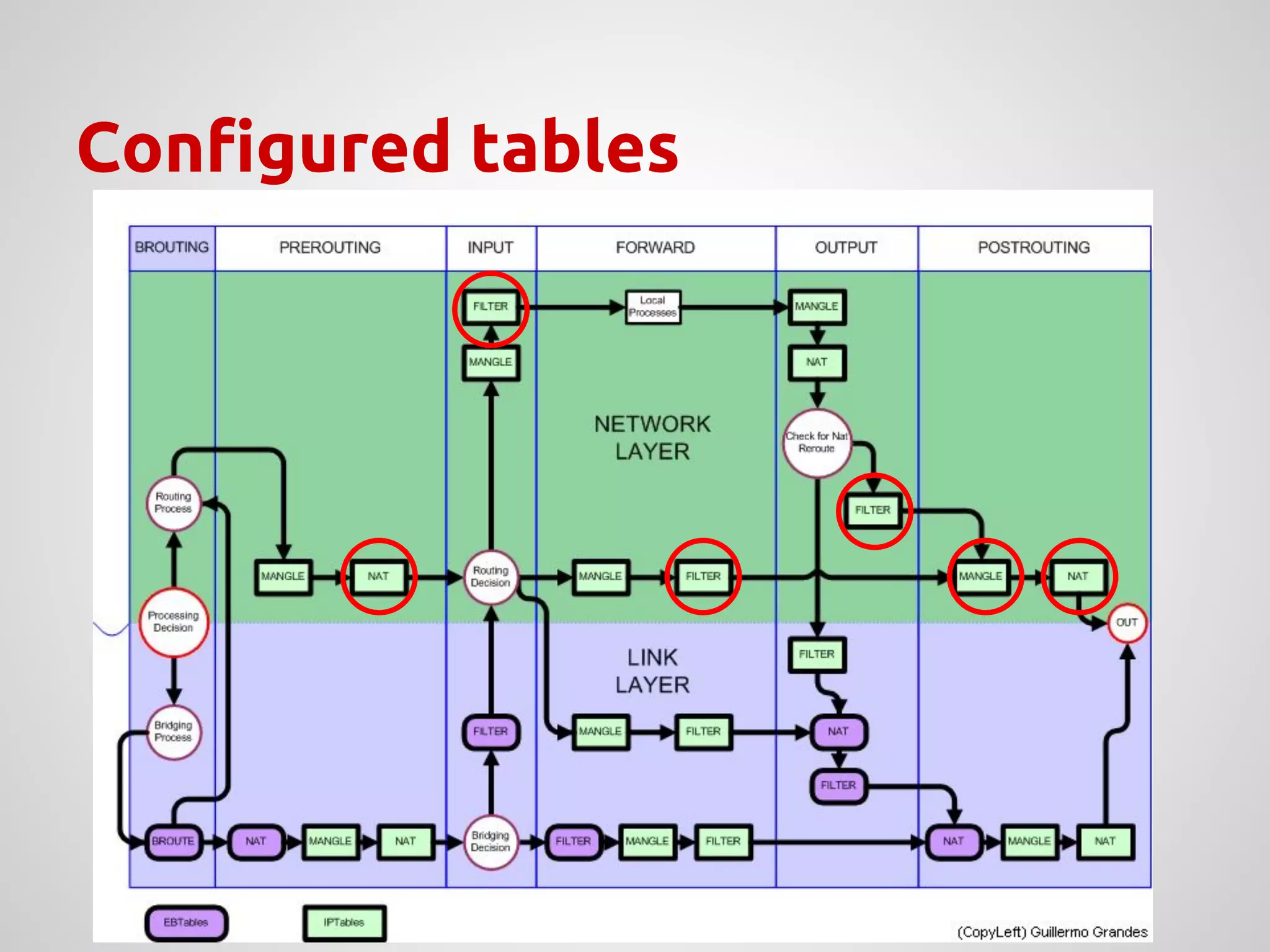
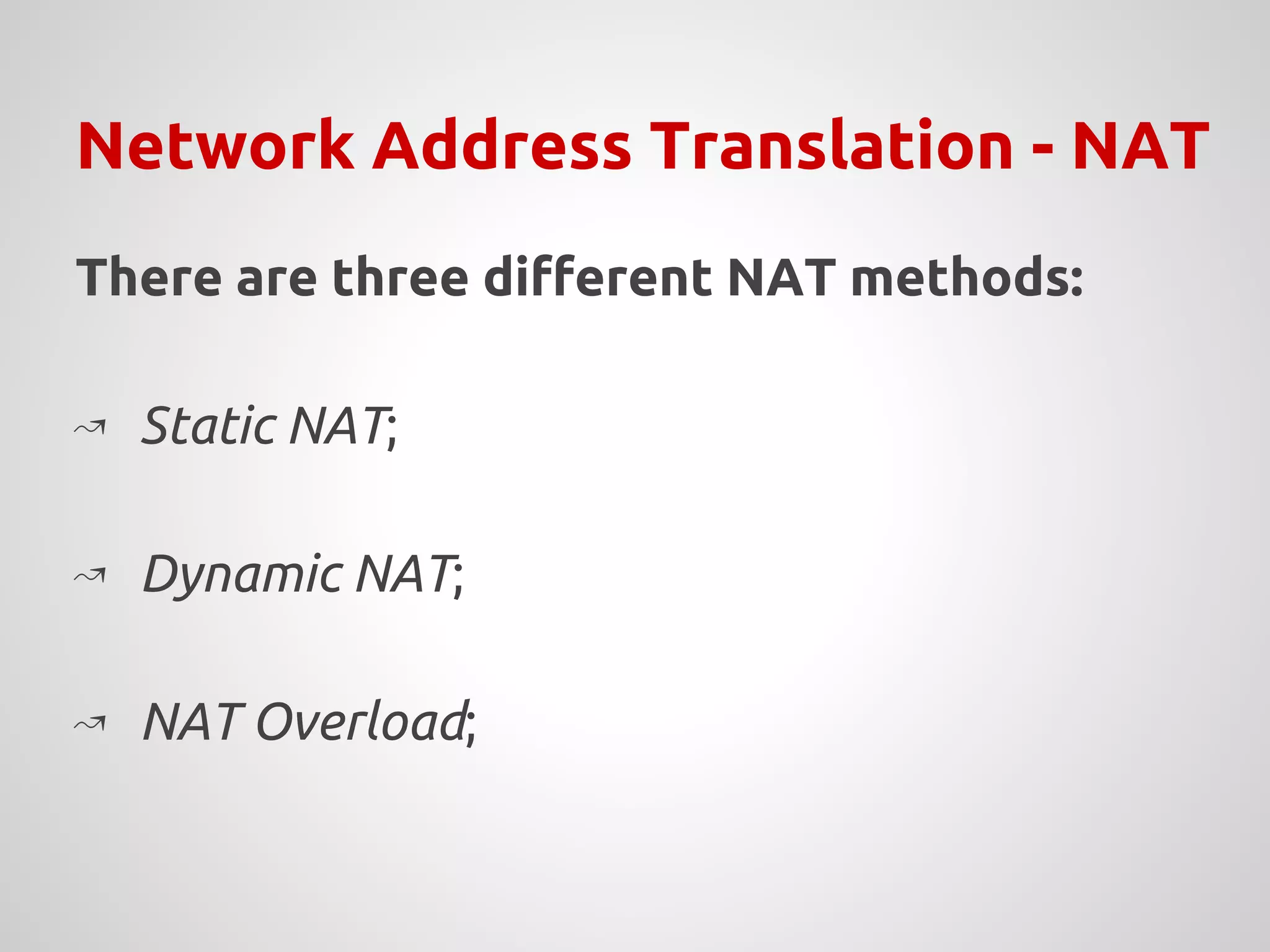
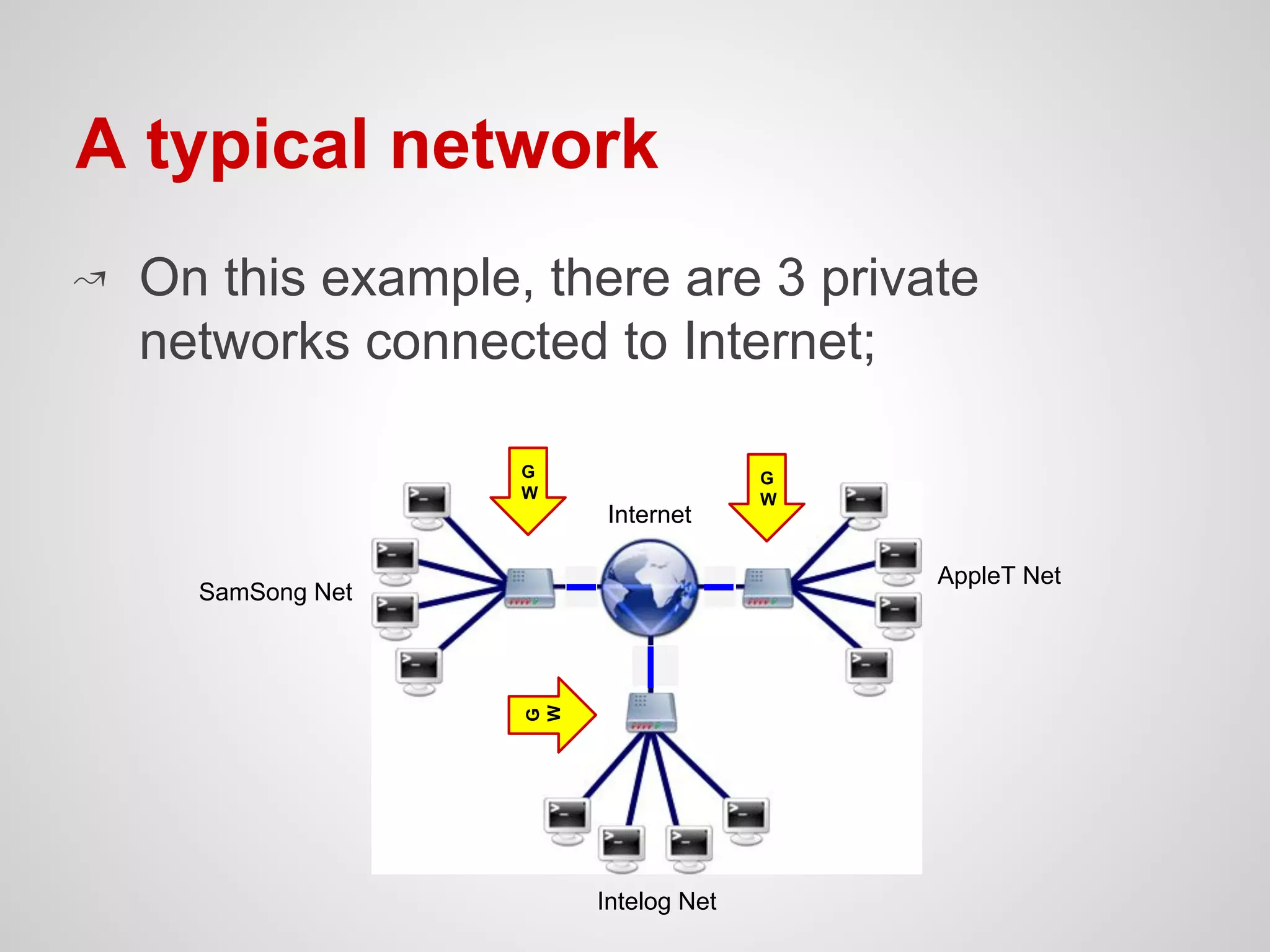
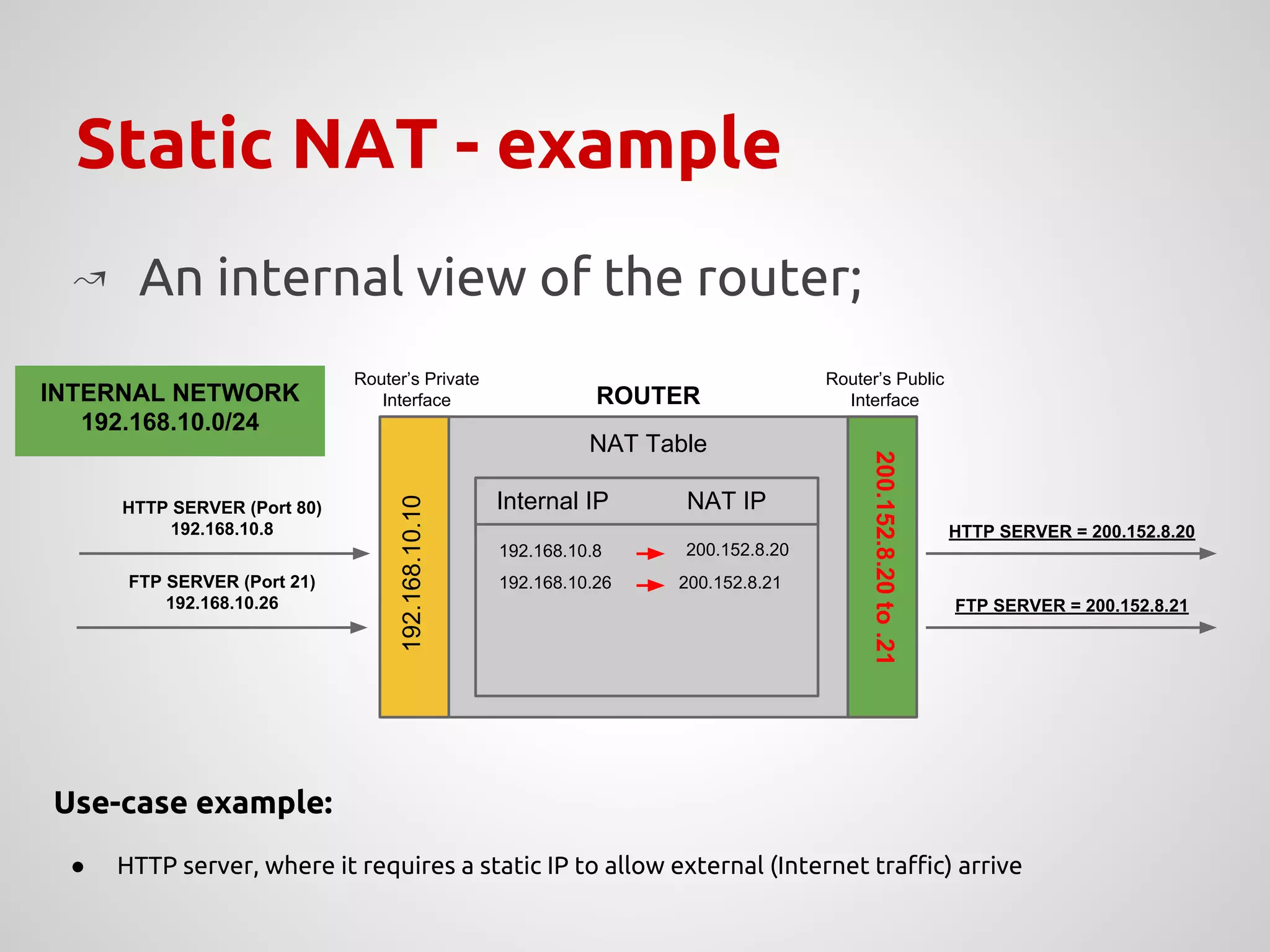
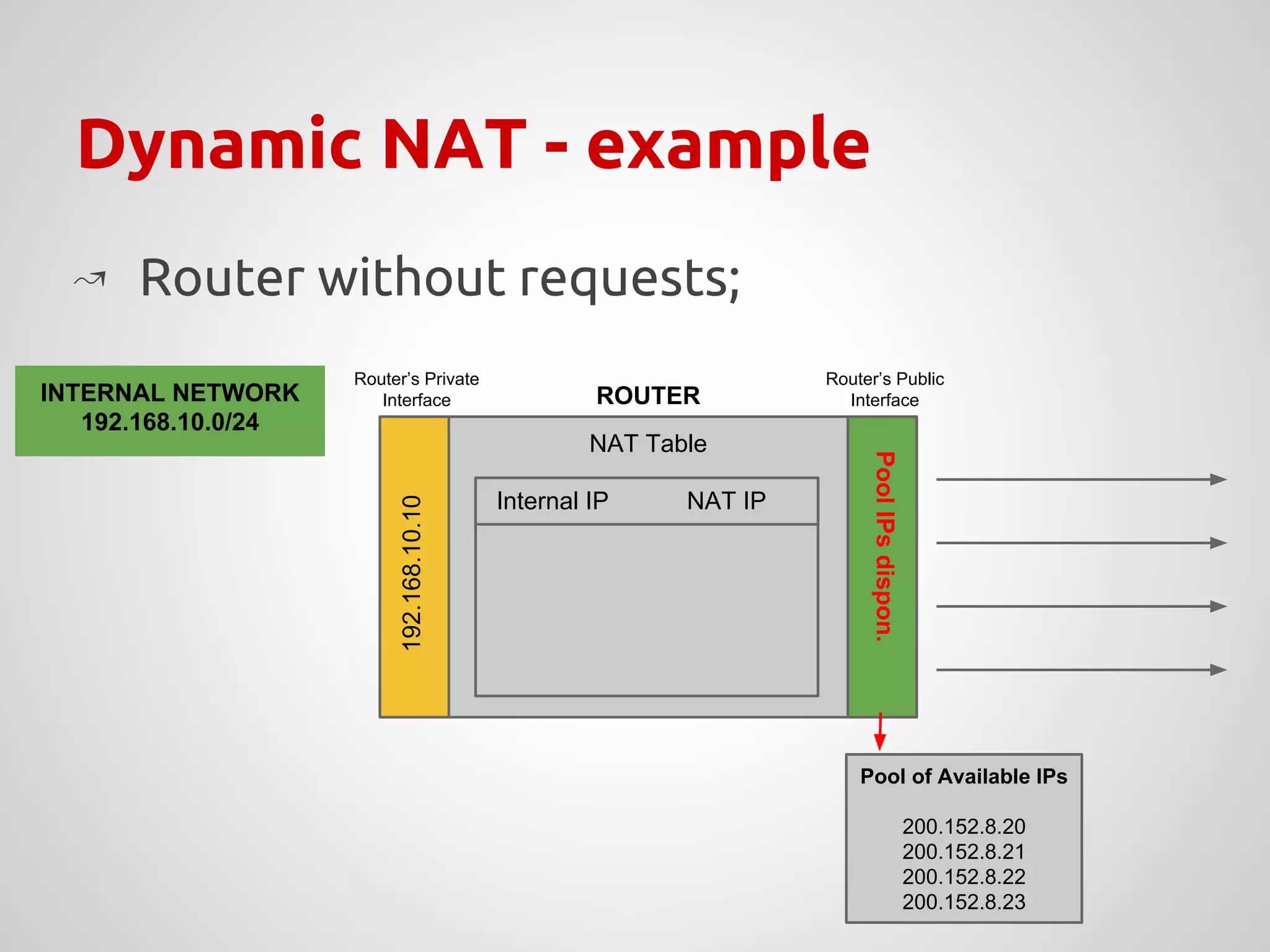
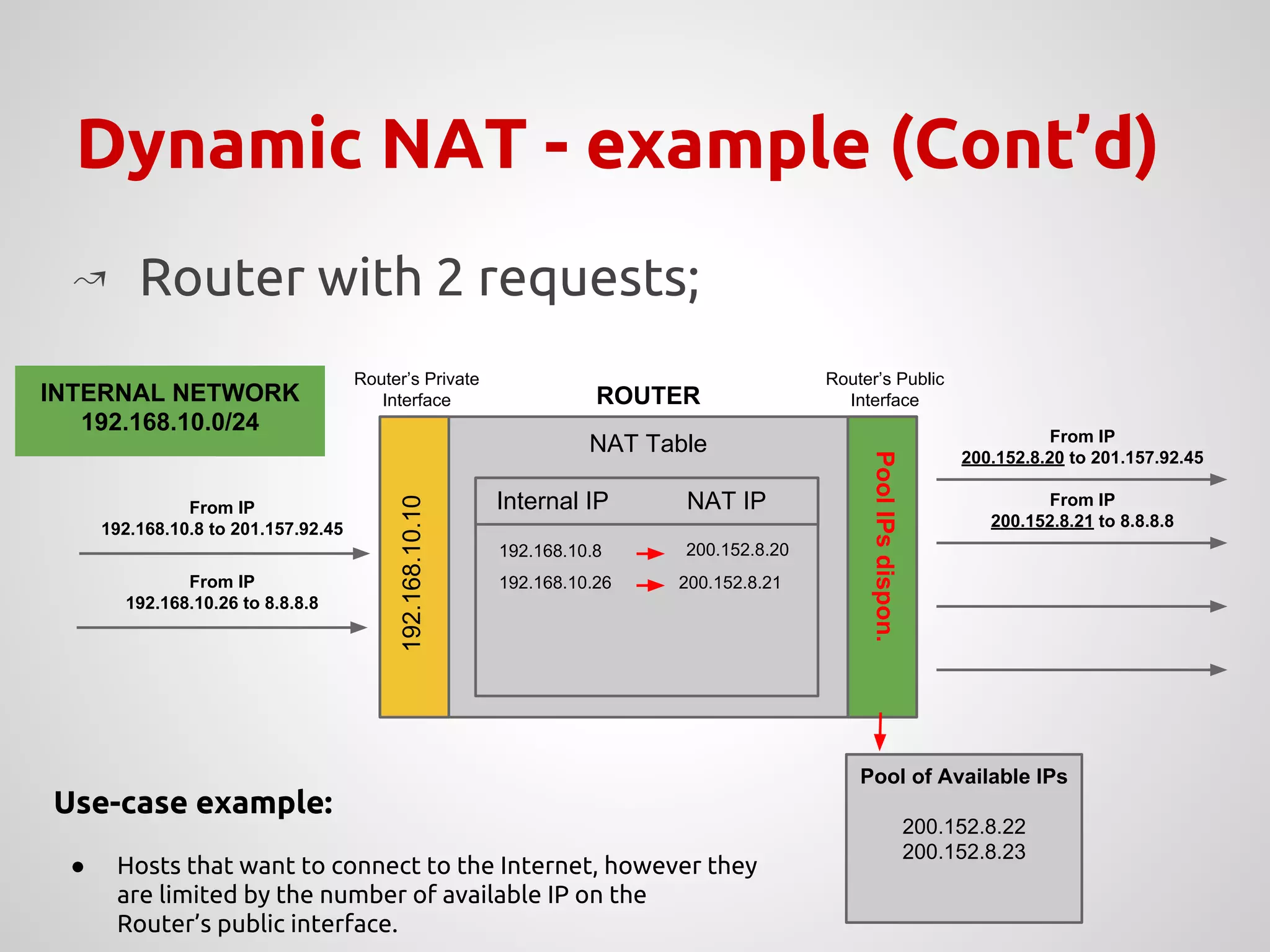
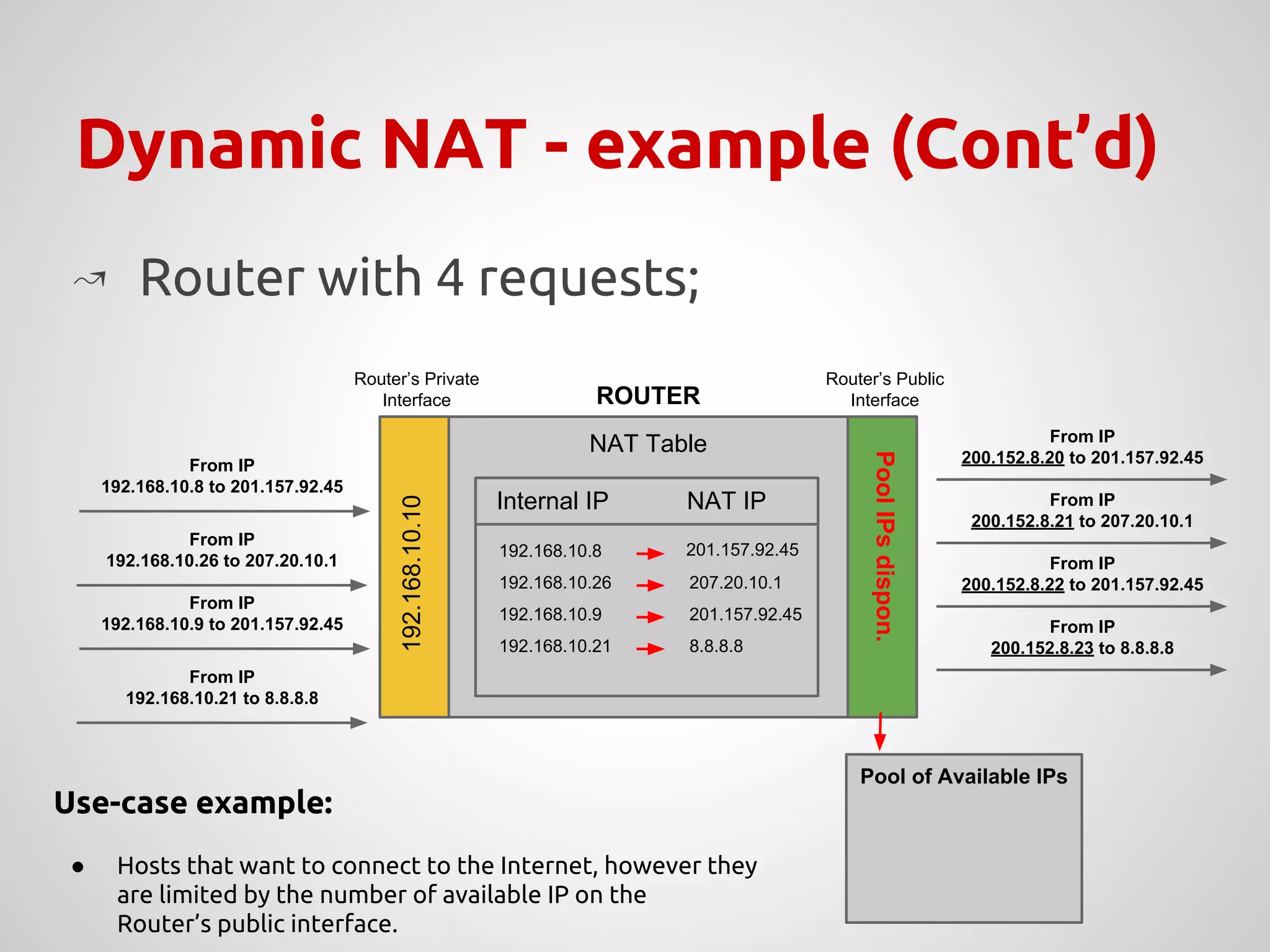
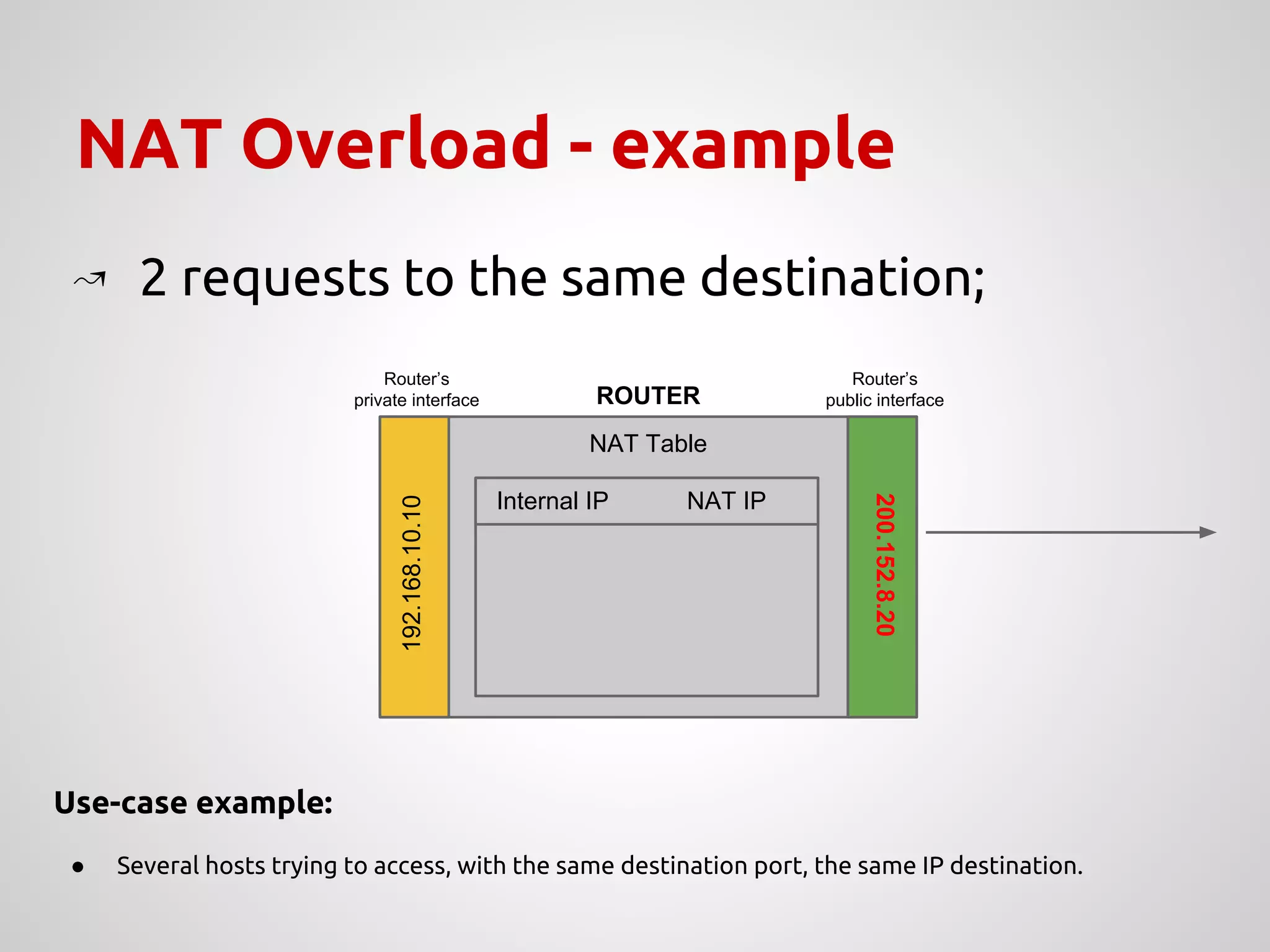
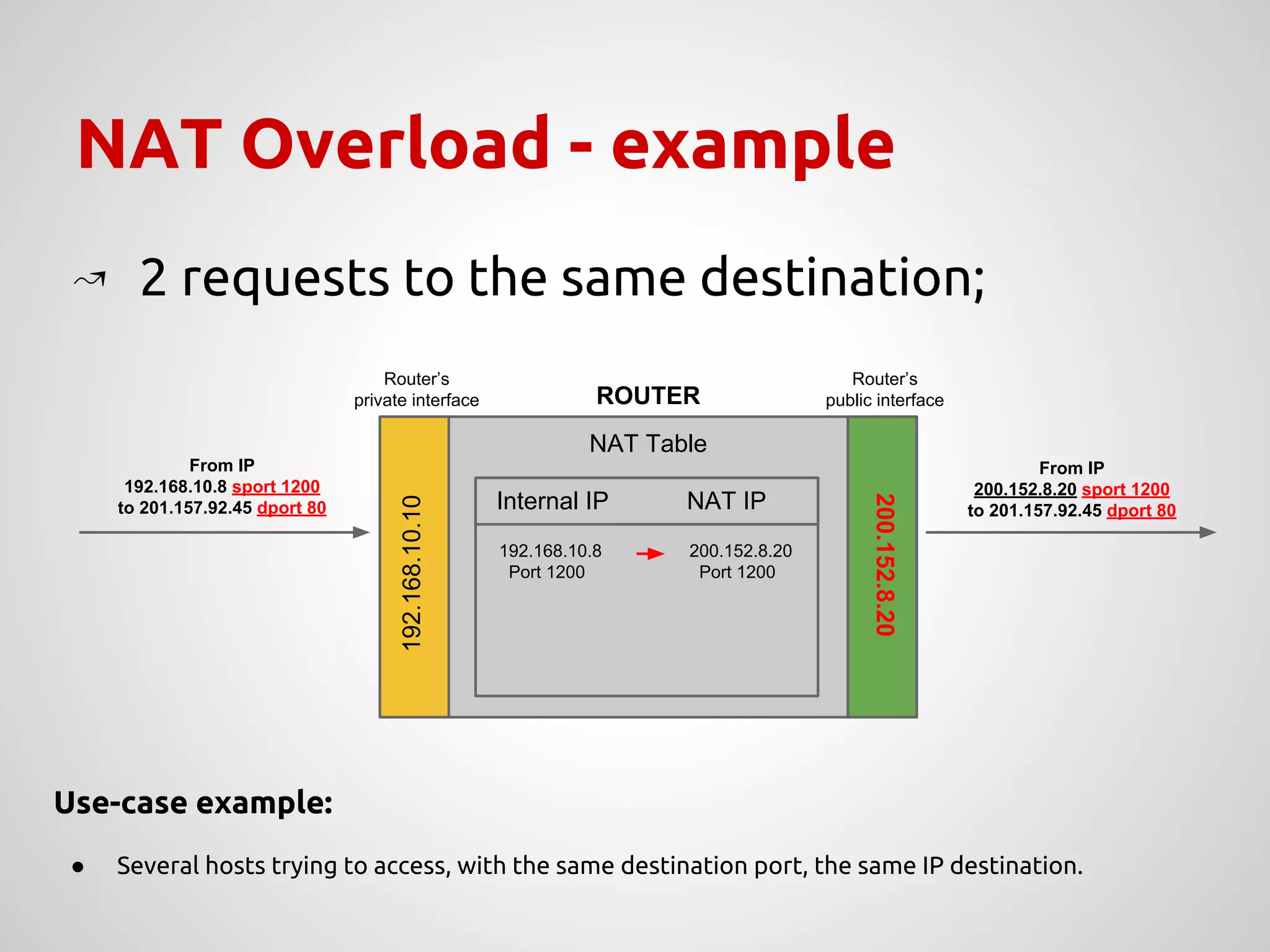
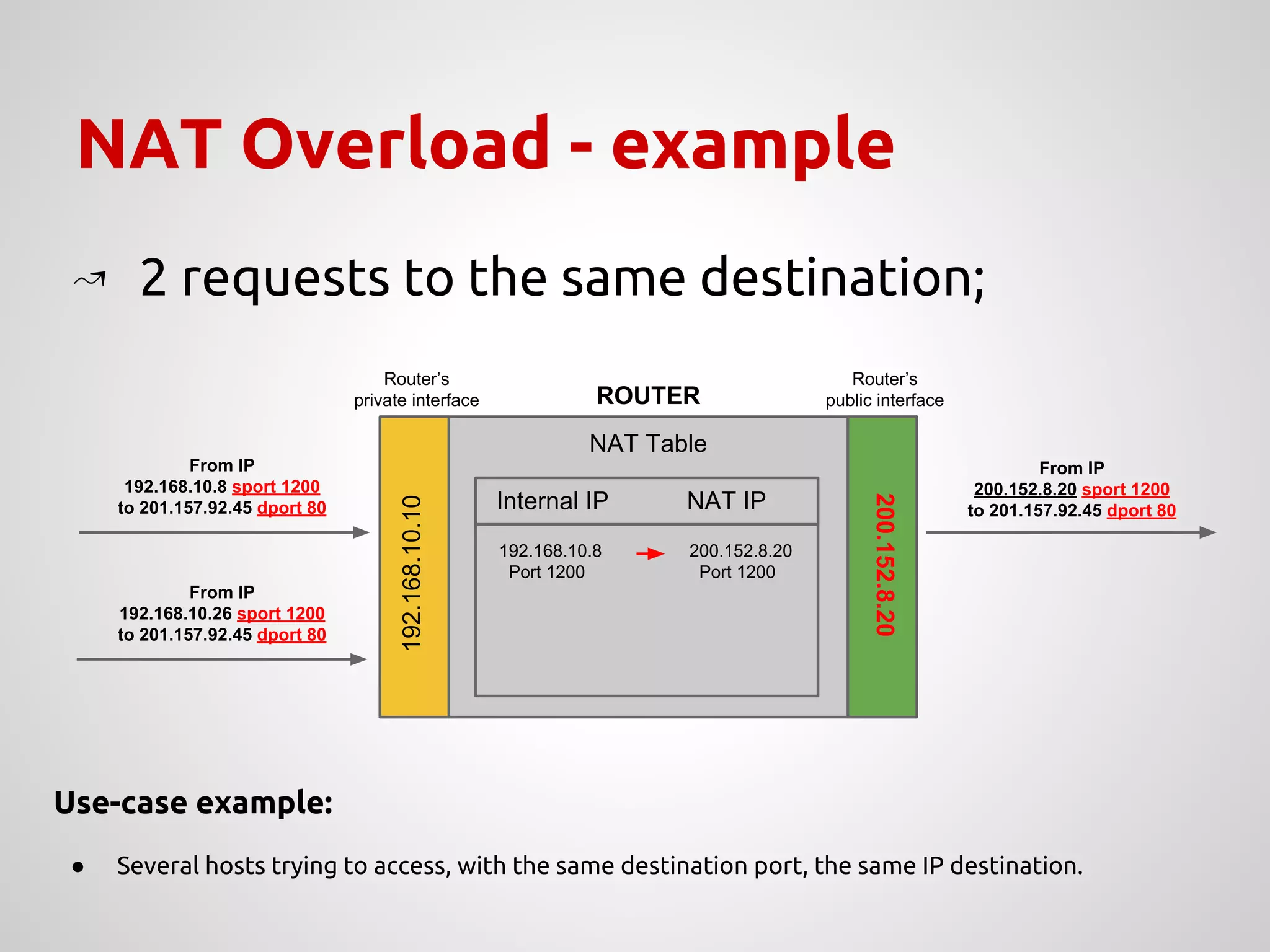
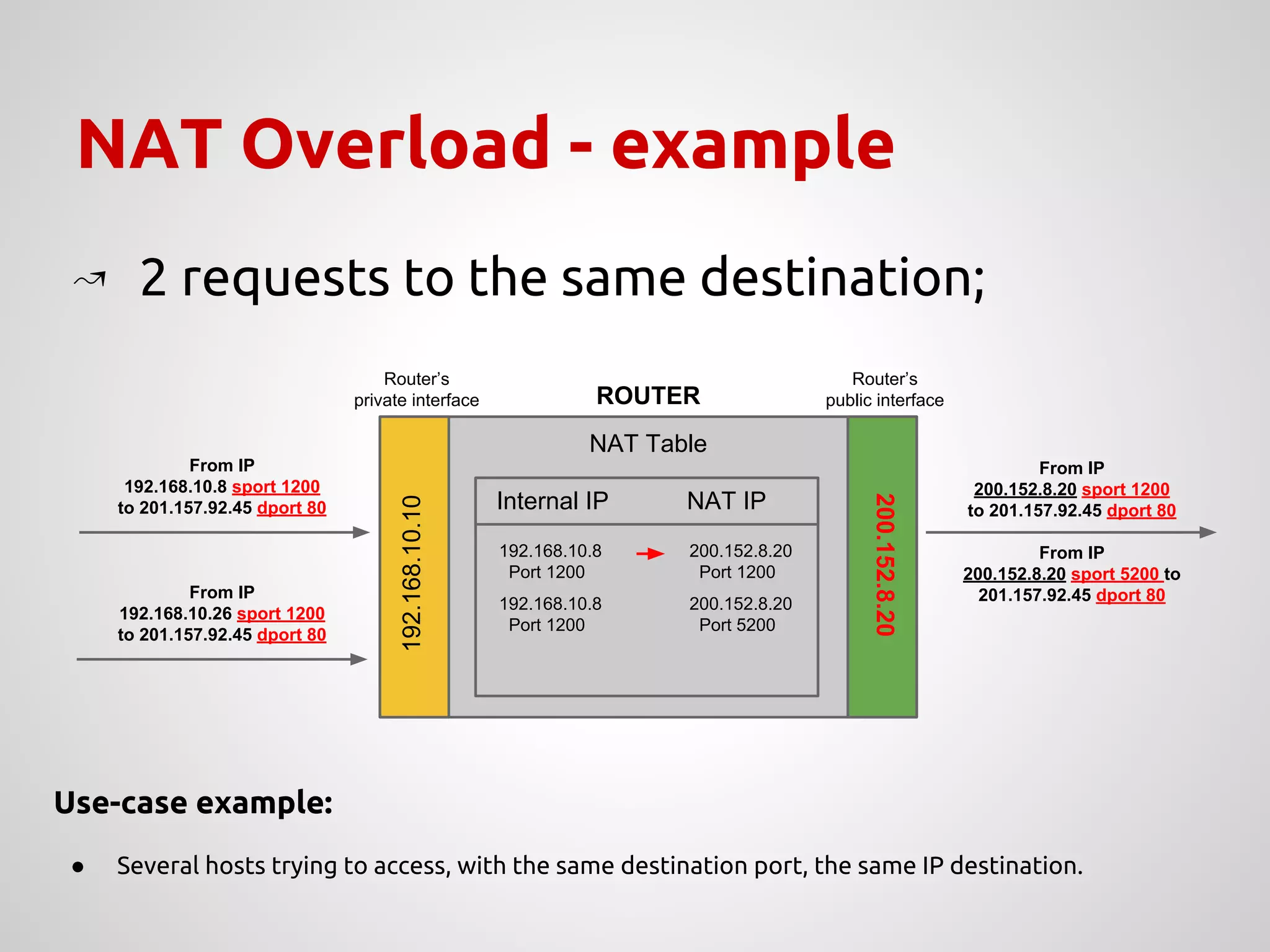
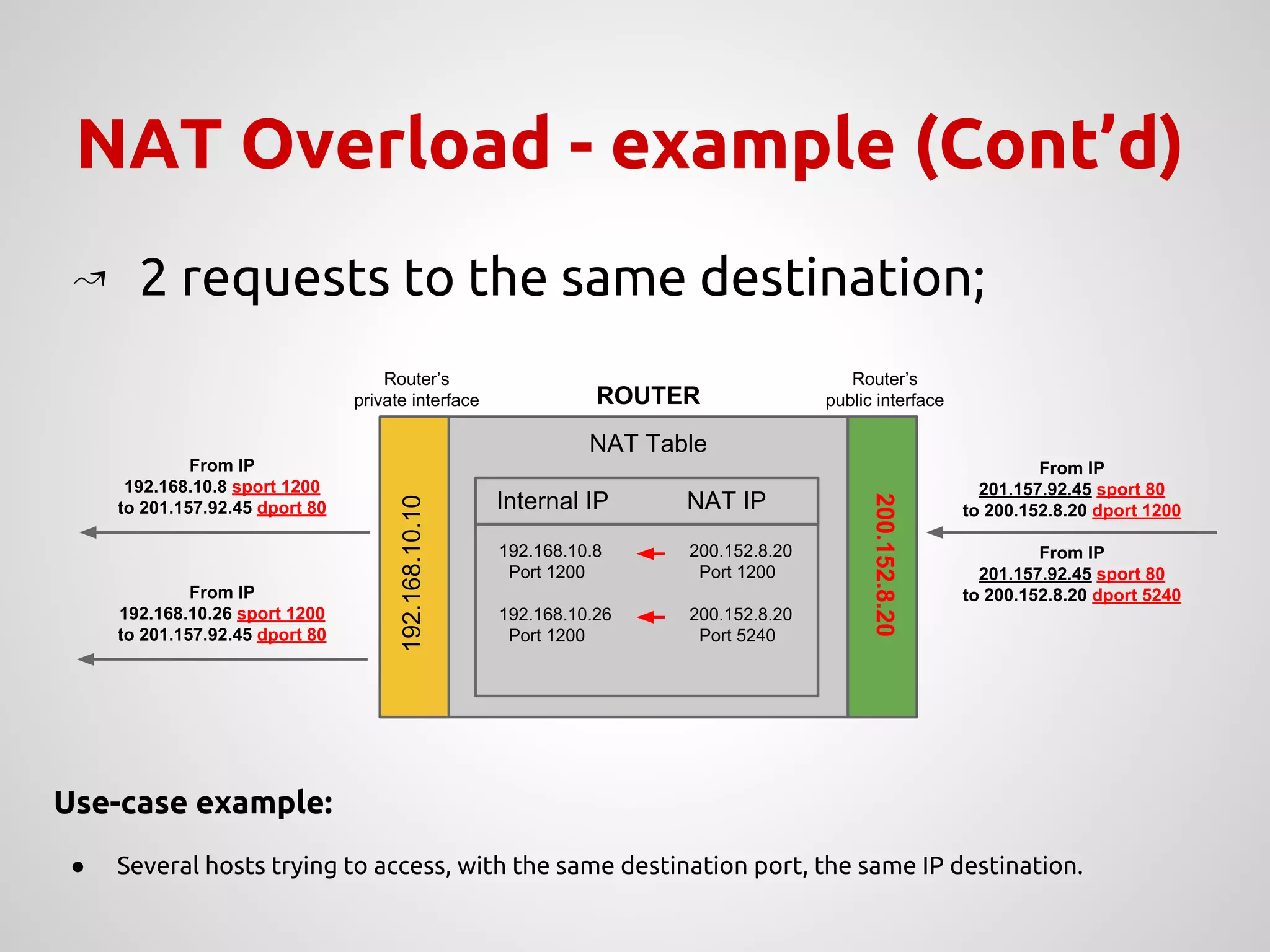
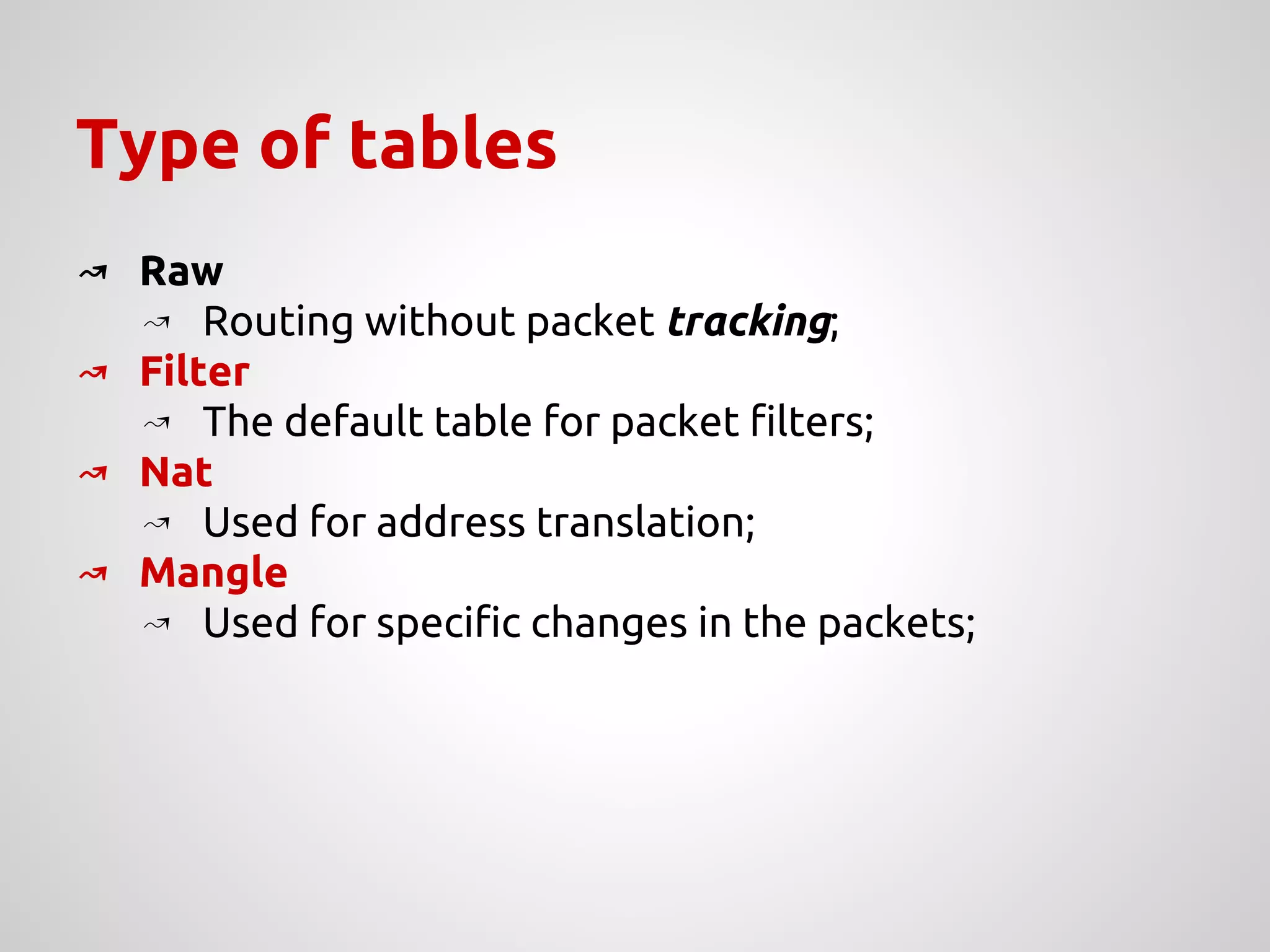
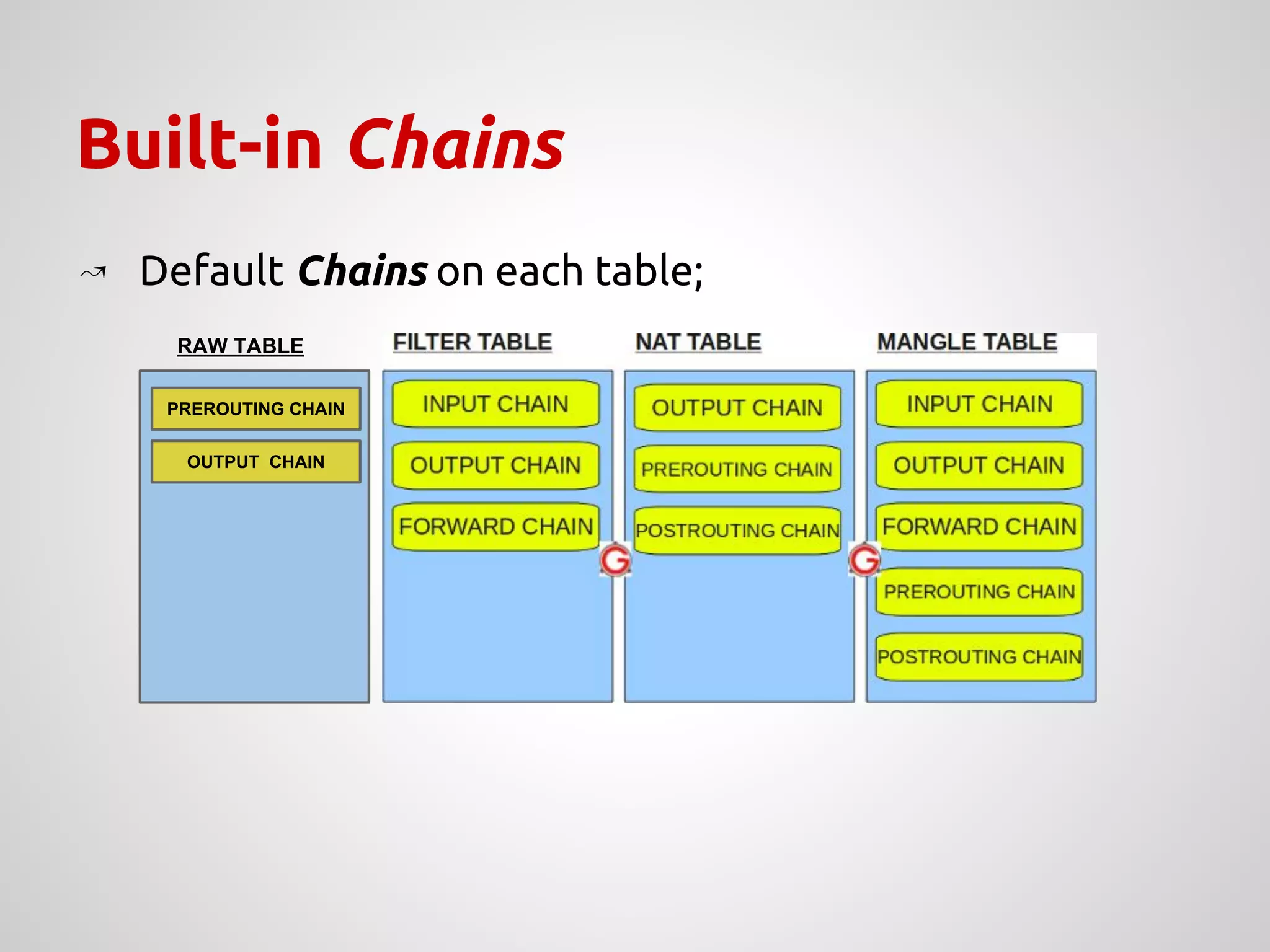
The document provides an overview of Network Address Translation (NAT) methods including static NAT, dynamic NAT, and NAT overload, detailing their functions and use-cases in allowing communication between distinct networks. It also discusses firewall configurations using iptables to manage data traffic and secure private networks, emphasizing the importance of packet manipulation and rules for traffic control. Specific examples of NAT tables and firewall rules are presented, illustrating configurations for networking scenarios within a Linux environment.


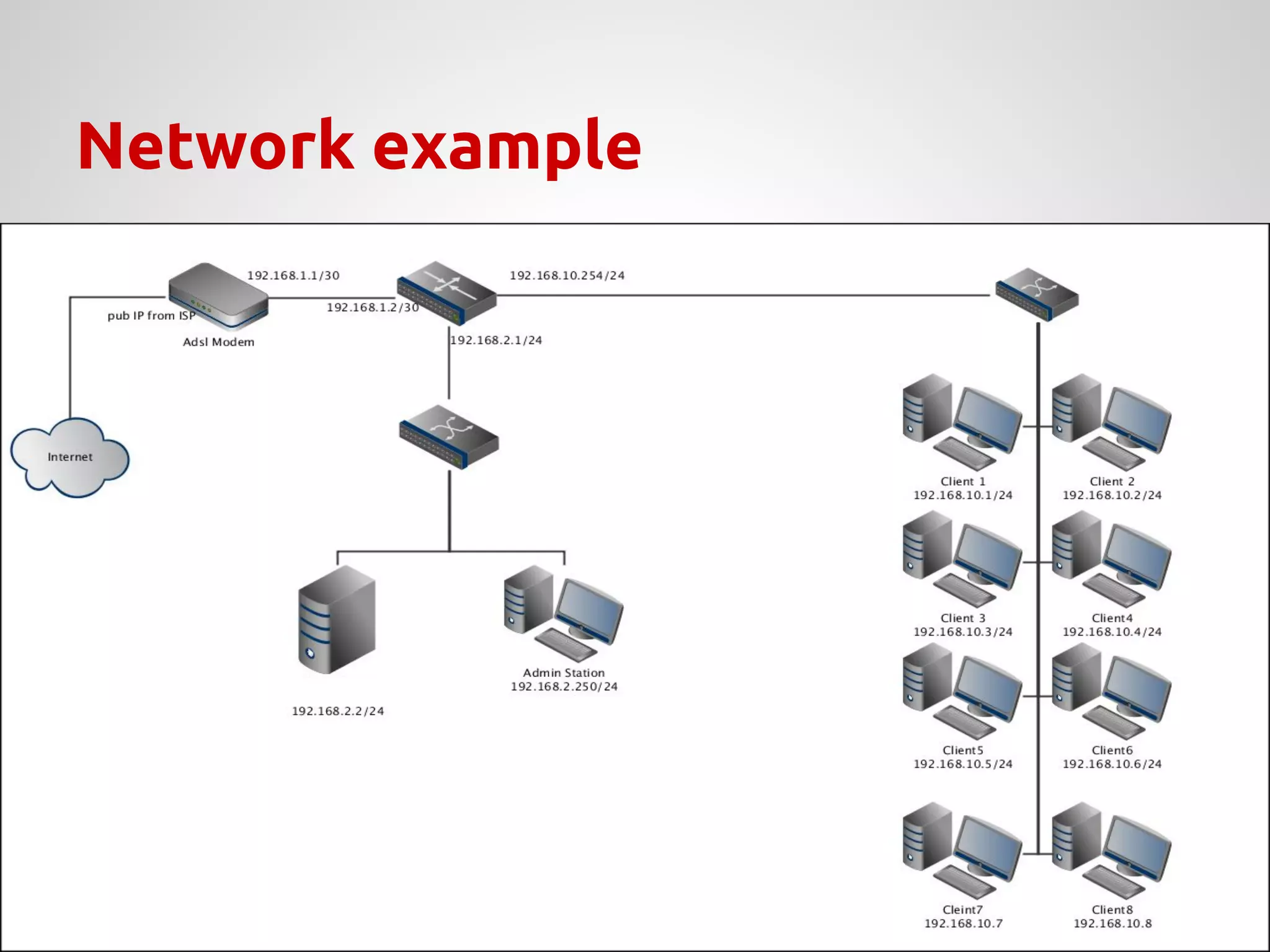





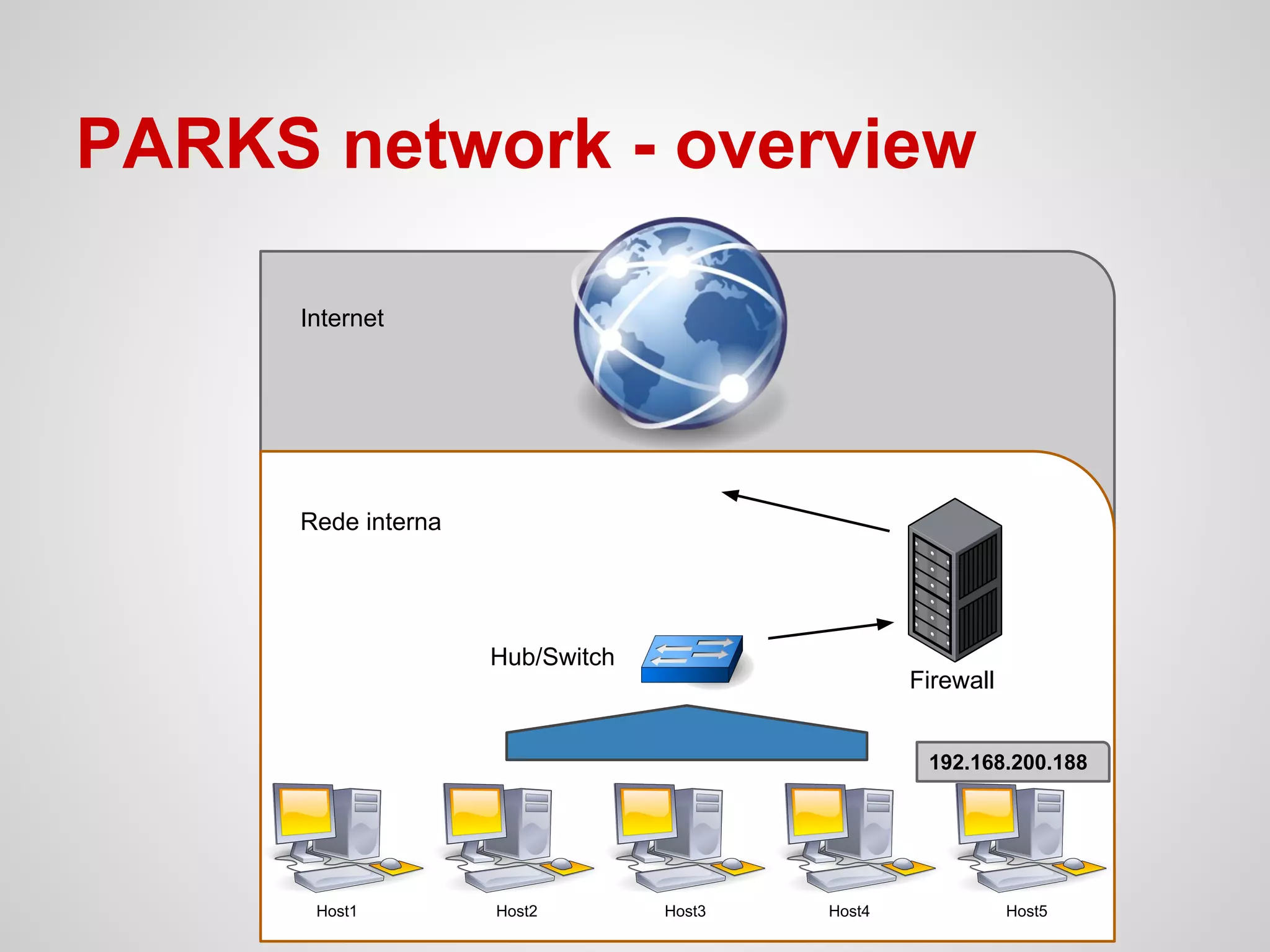
![Server properties
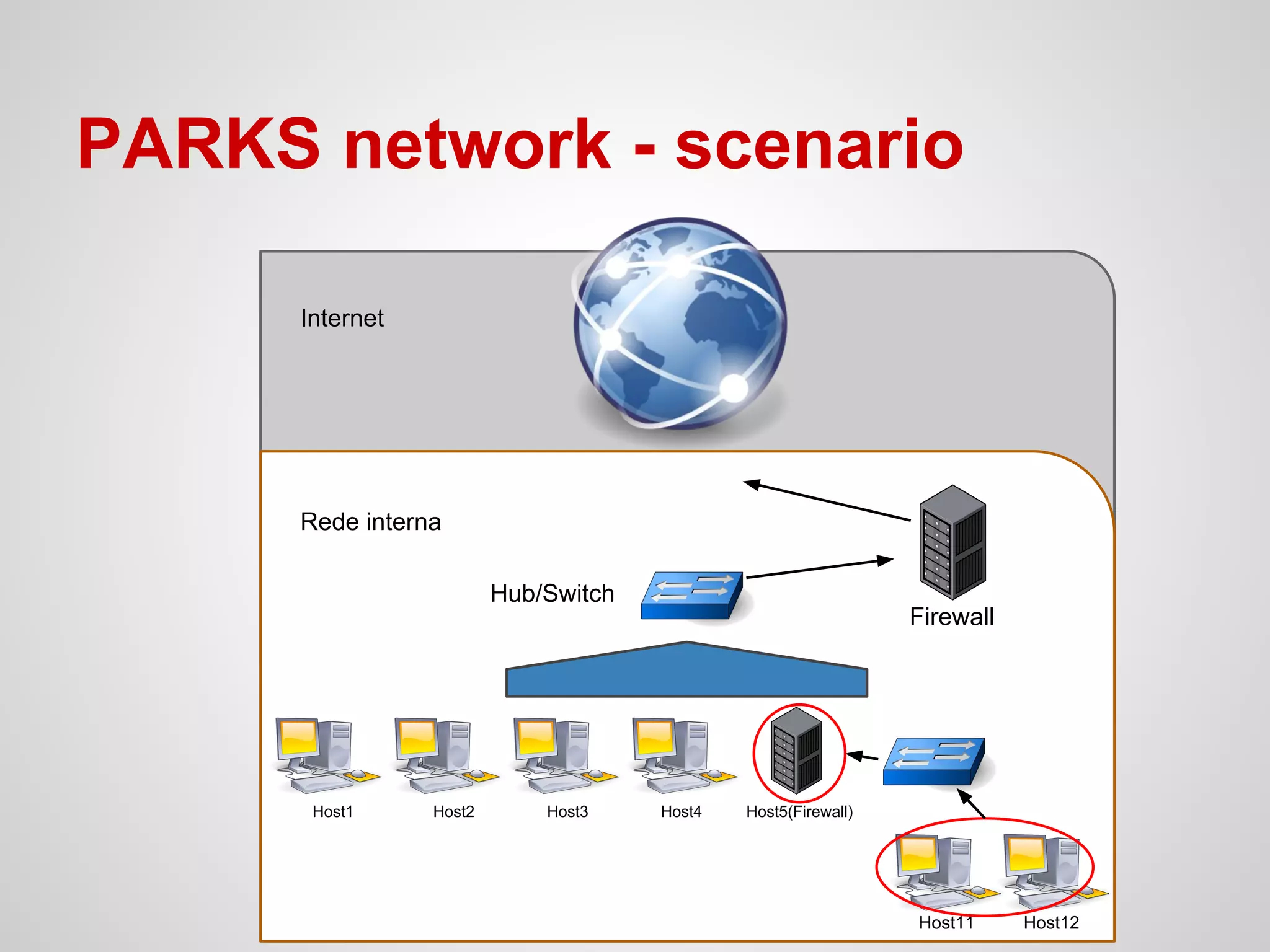
↝ Create a subnetwork in a PARKS host;
↝ Configure a DHCP server;
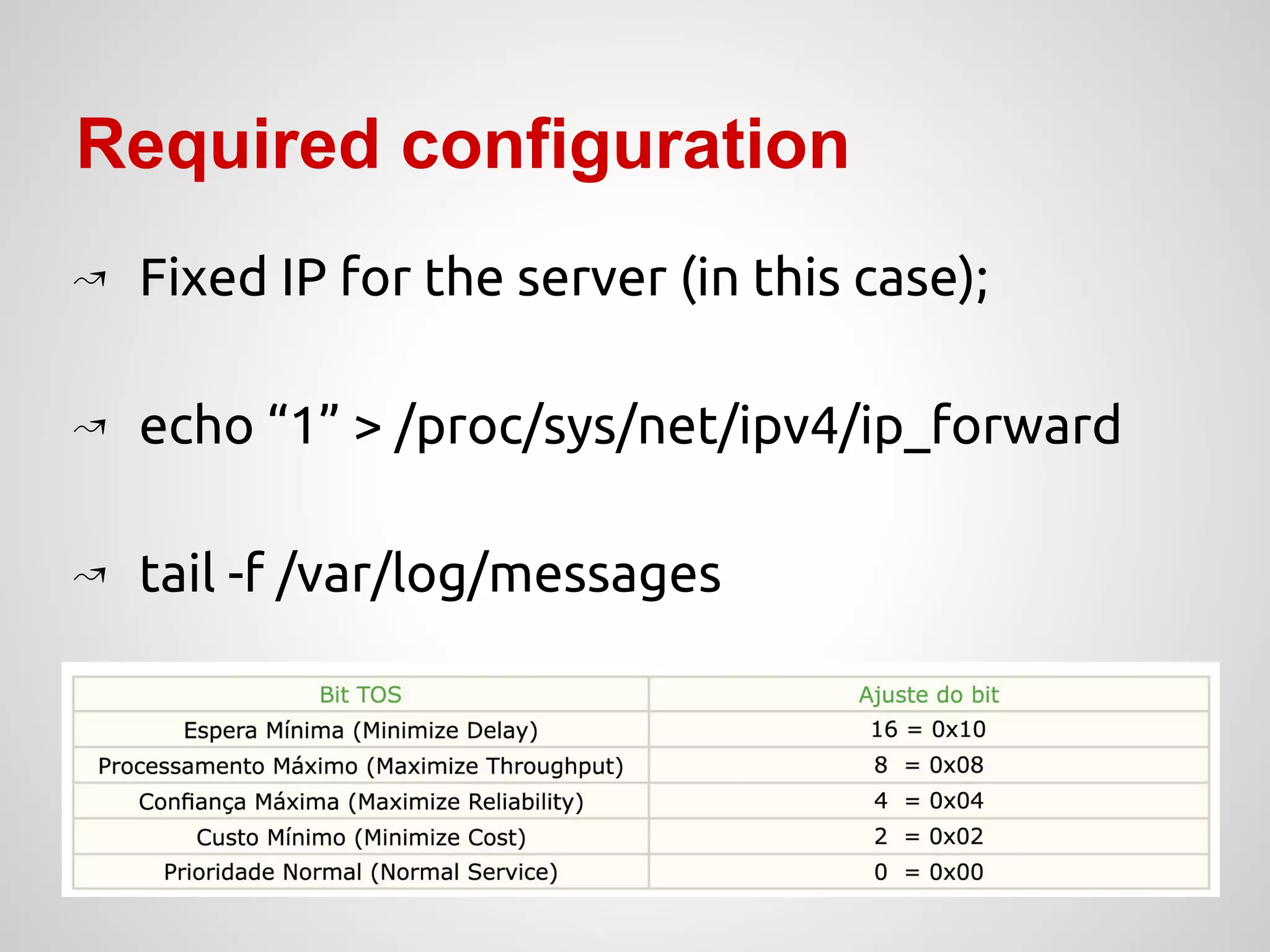
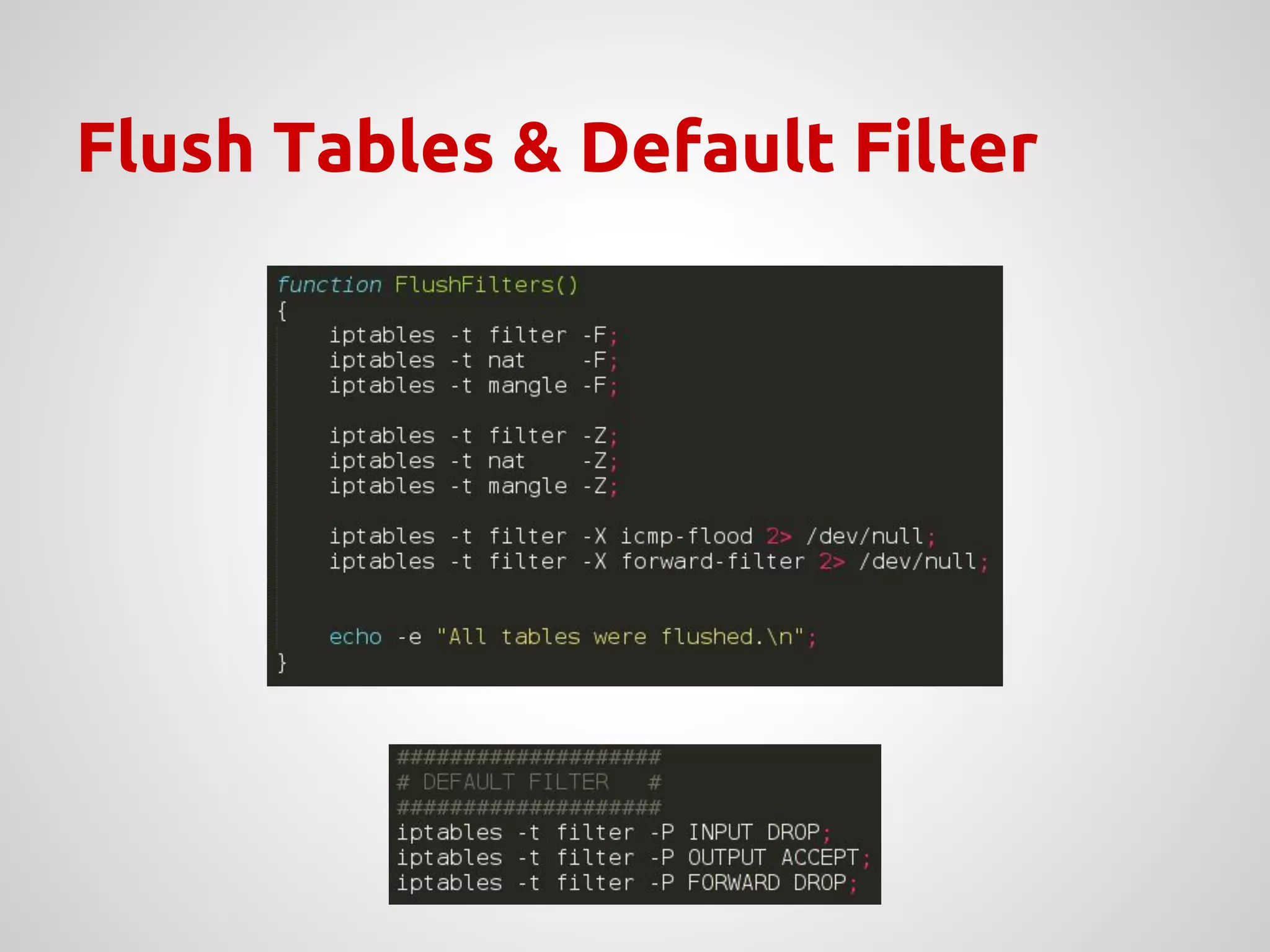
↝ Configure iptables with specific rules:
➢ Allow HTTP[S] traffic to a specific time;
➢ Translate addresses with access to Internet;
➢ Allow FTP traffic;
➢ HTTP server in a specific host in the subnet, with
external access permission;
➢ FTP server allowed only to work within the subnet;](https://image.slidesharecdn.com/parks-presentation-181116062908/75/NAT-and-firewall-presentation-how-setup-a-nice-firewall-28-2048.jpg)

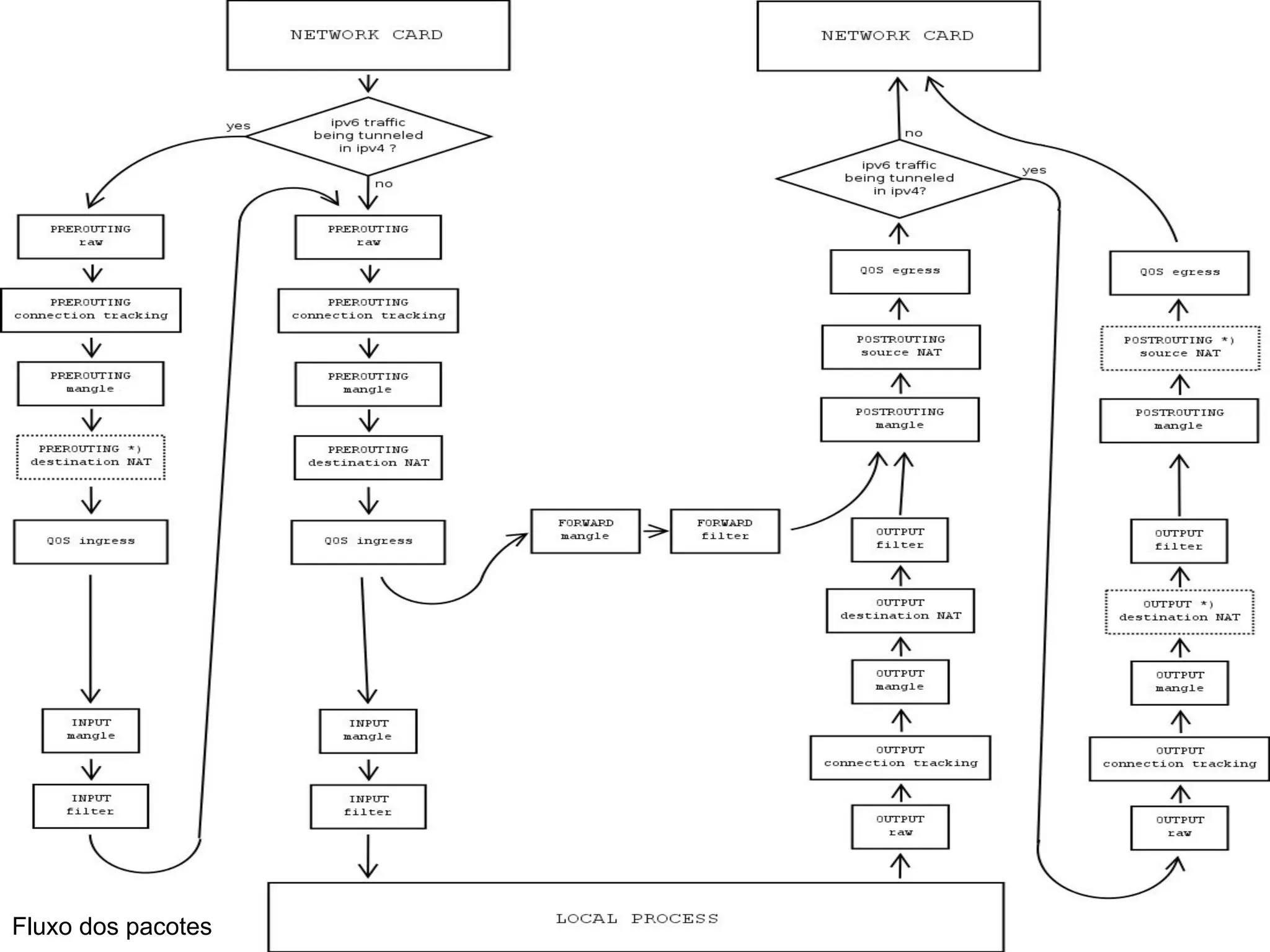
![NAT - [PRE-POST]ROUTING](https://image.slidesharecdn.com/parks-presentation-181116062908/75/NAT-and-firewall-presentation-how-setup-a-nice-firewall-33-2048.jpg)
![NAT - [PRE-POST]ROUTING](https://image.slidesharecdn.com/parks-presentation-181116062908/75/NAT-and-firewall-presentation-how-setup-a-nice-firewall-35-2048.jpg)
![NAT - [PRE-POST]ROUTING](https://image.slidesharecdn.com/parks-presentation-181116062908/75/NAT-and-firewall-presentation-how-setup-a-nice-firewall-36-2048.jpg)