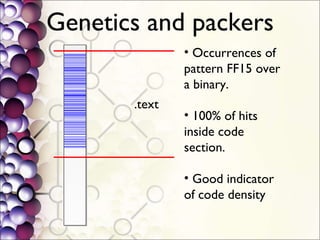
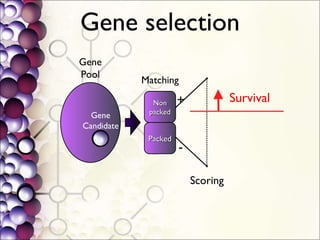
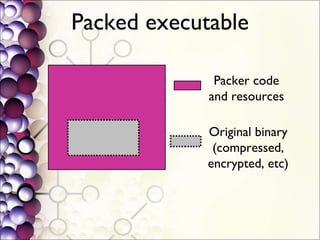
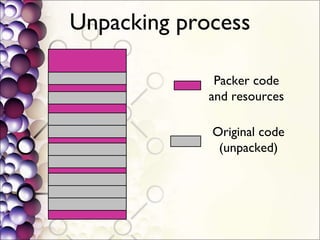
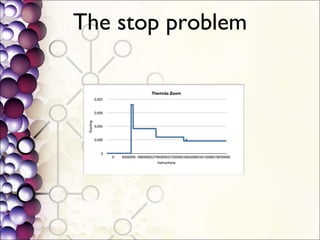
The document discusses the integration of a Python interpreter with the Bochs CPU emulator to automate the unpacking of packed executables. It outlines the challenges faced in capturing generic unpacking behaviors and optimizing emulation time, while emphasizing the need for a simplified approach to detecting various packers. The project aims to develop a 'gene[tr]ic' unpacker supported by plugins for post-processing tasks and a better understanding of packed binaries.

















![Gene[tr]ic unpacker](https://image.slidesharecdn.com/recon2010-100714205302-phpapp01/85/Packer-Genetics-The-selfish-code-28-320.jpg)




![Work in progress Gene[tr]ic unpacker as an online tool Plugins (optional post-processing): Deobfuscator VM analysis (as described in [1] to obtain more accurate callgraphs) Support for other CPUs, OSs and VMs [1] Rotalume: A Tool for Automatic Reverse Engineering of Malware Emulators. http://bit.ly/9XtAeb](https://image.slidesharecdn.com/recon2010-100714205302-phpapp01/85/Packer-Genetics-The-selfish-code-34-320.jpg)
