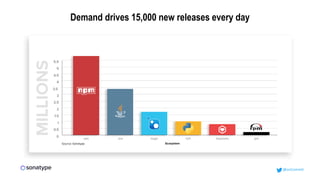
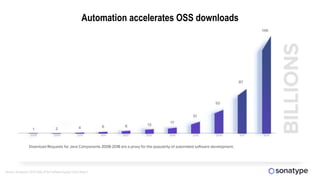
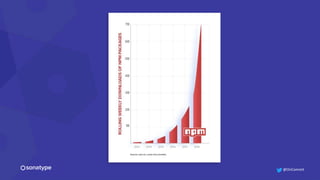
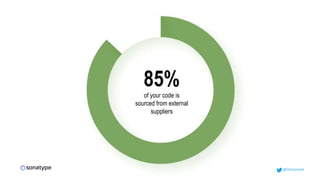
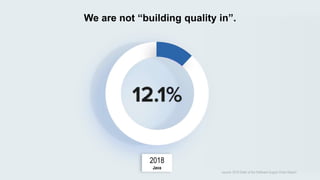
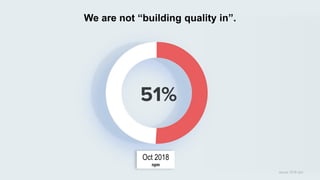
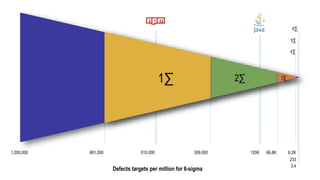
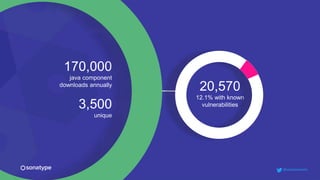
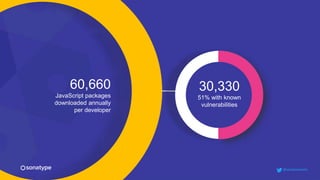
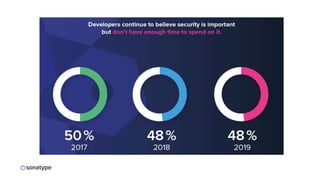
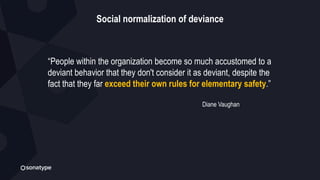
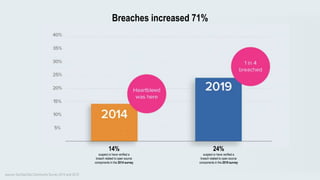
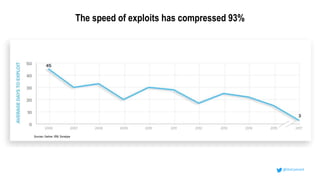
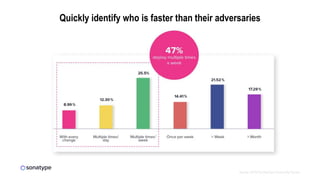
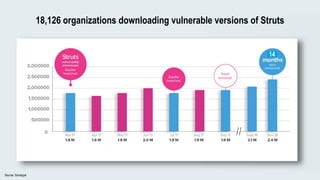
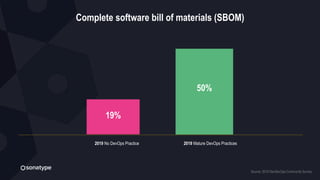
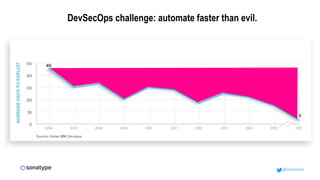
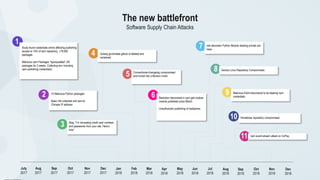
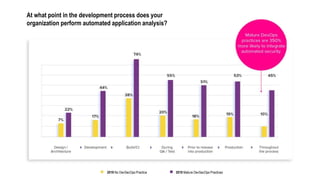
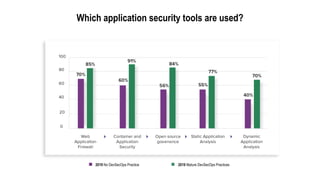
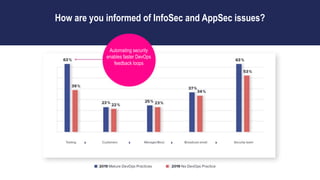
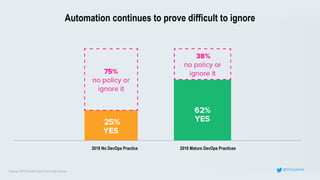
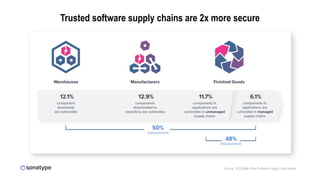
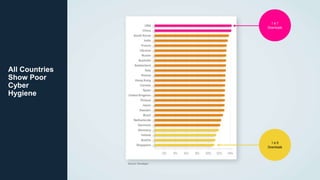
This document discusses the importance of building quality and security into software from the beginning through practices like DevSecOps. It notes that while many organizations deploy code multiple times per week, many are still downloading outdated or vulnerable open source components. Automating security processes and having complete visibility into software supply chains is key to reducing vulnerabilities and speeding up remediation times. The document advocates for prioritizing the performance of the entire system over any individual part and never passing defects downstream.