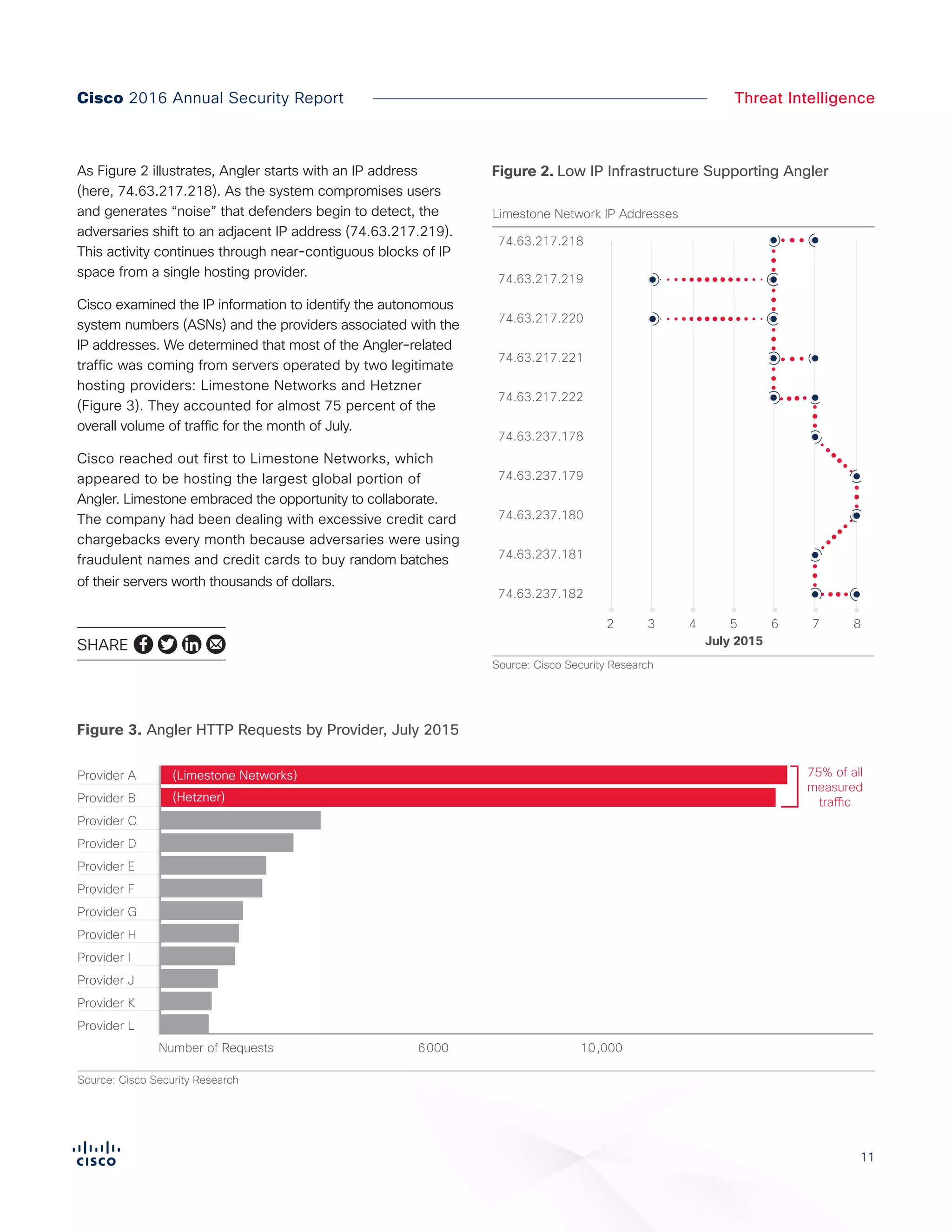
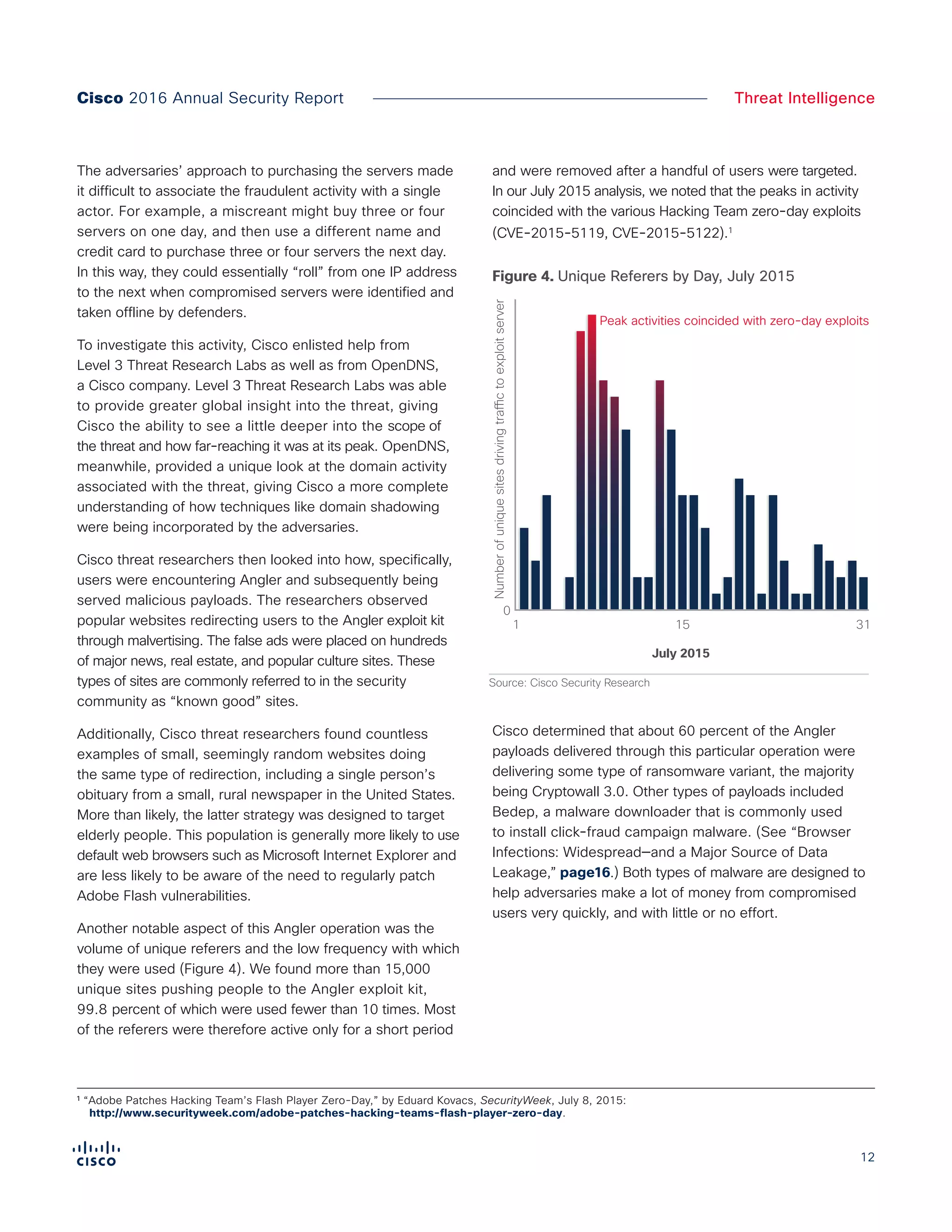
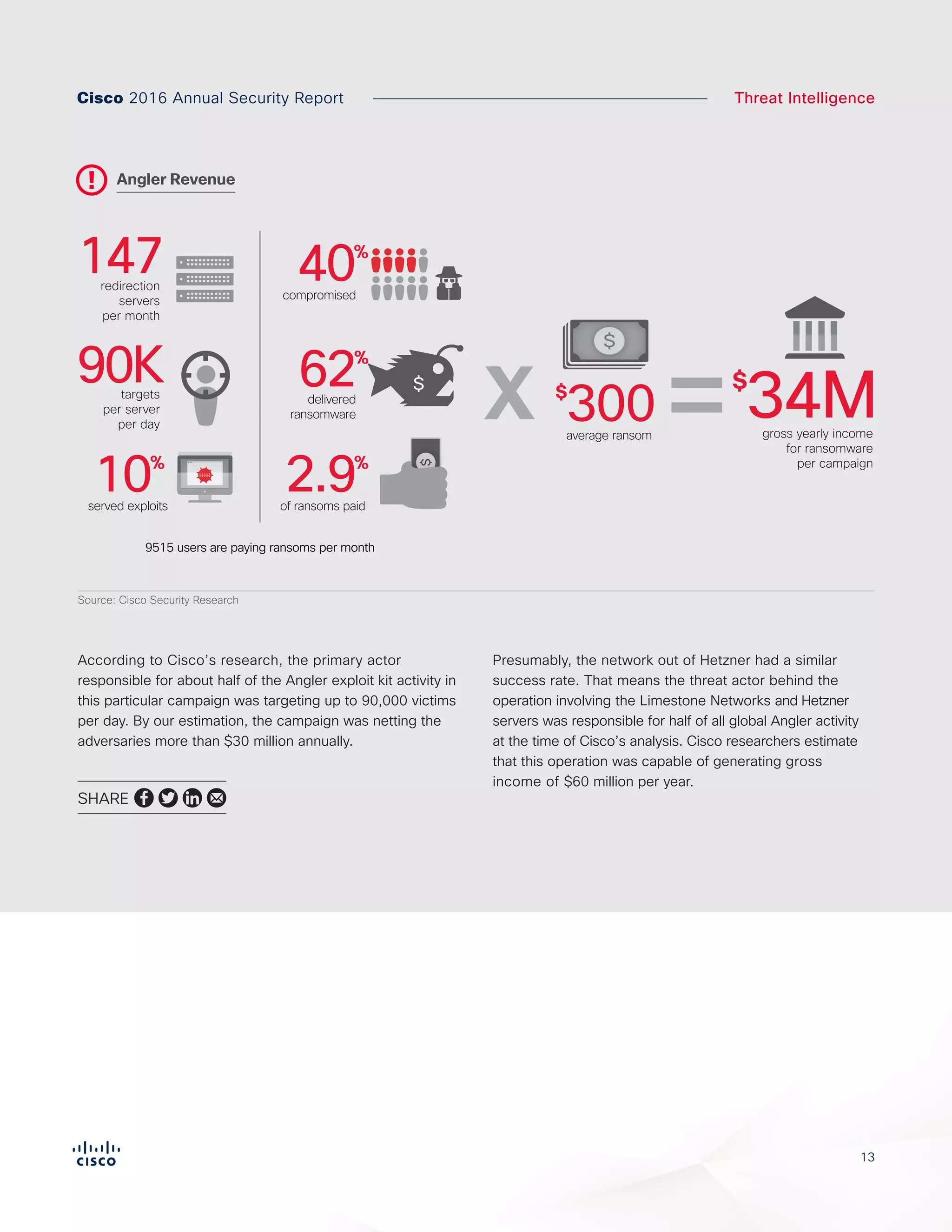
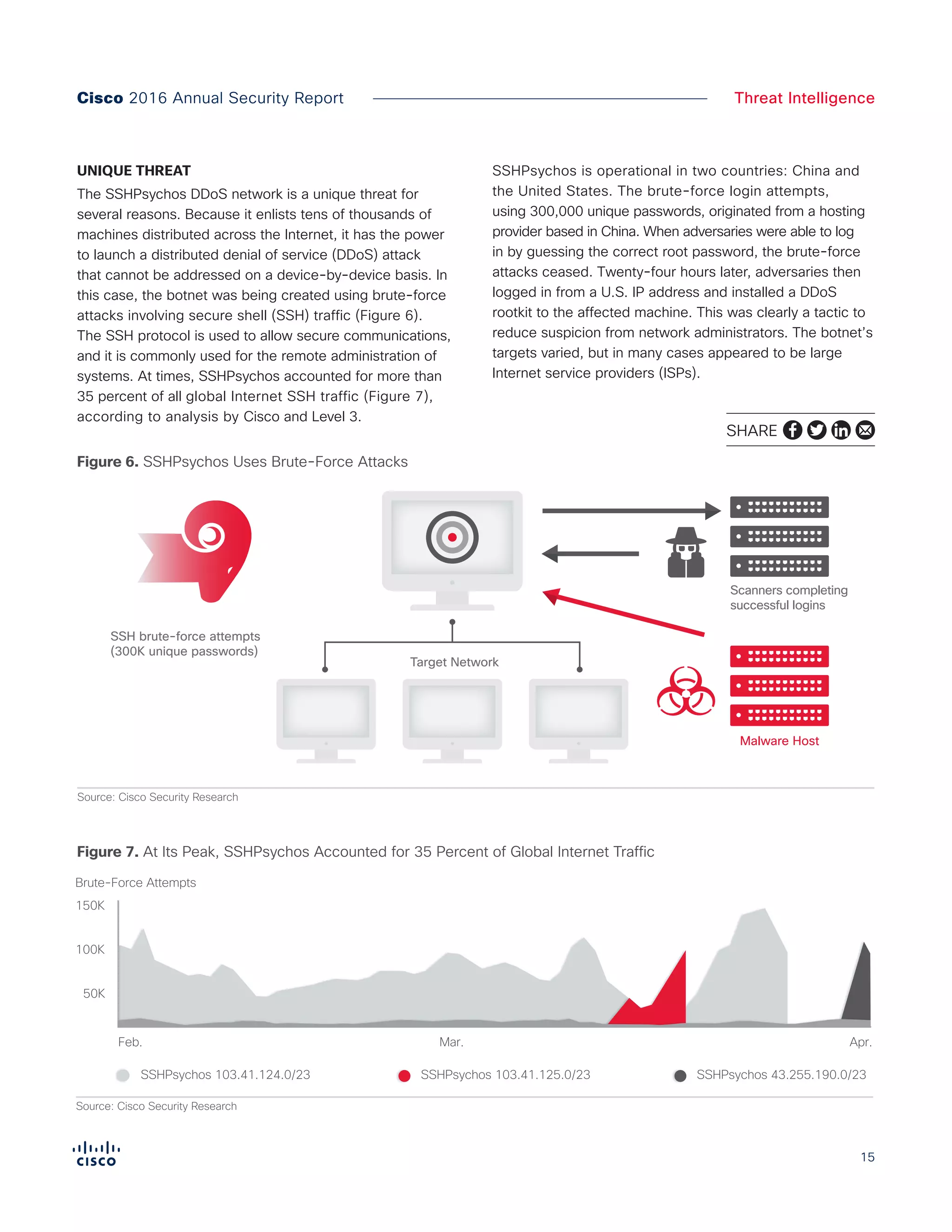
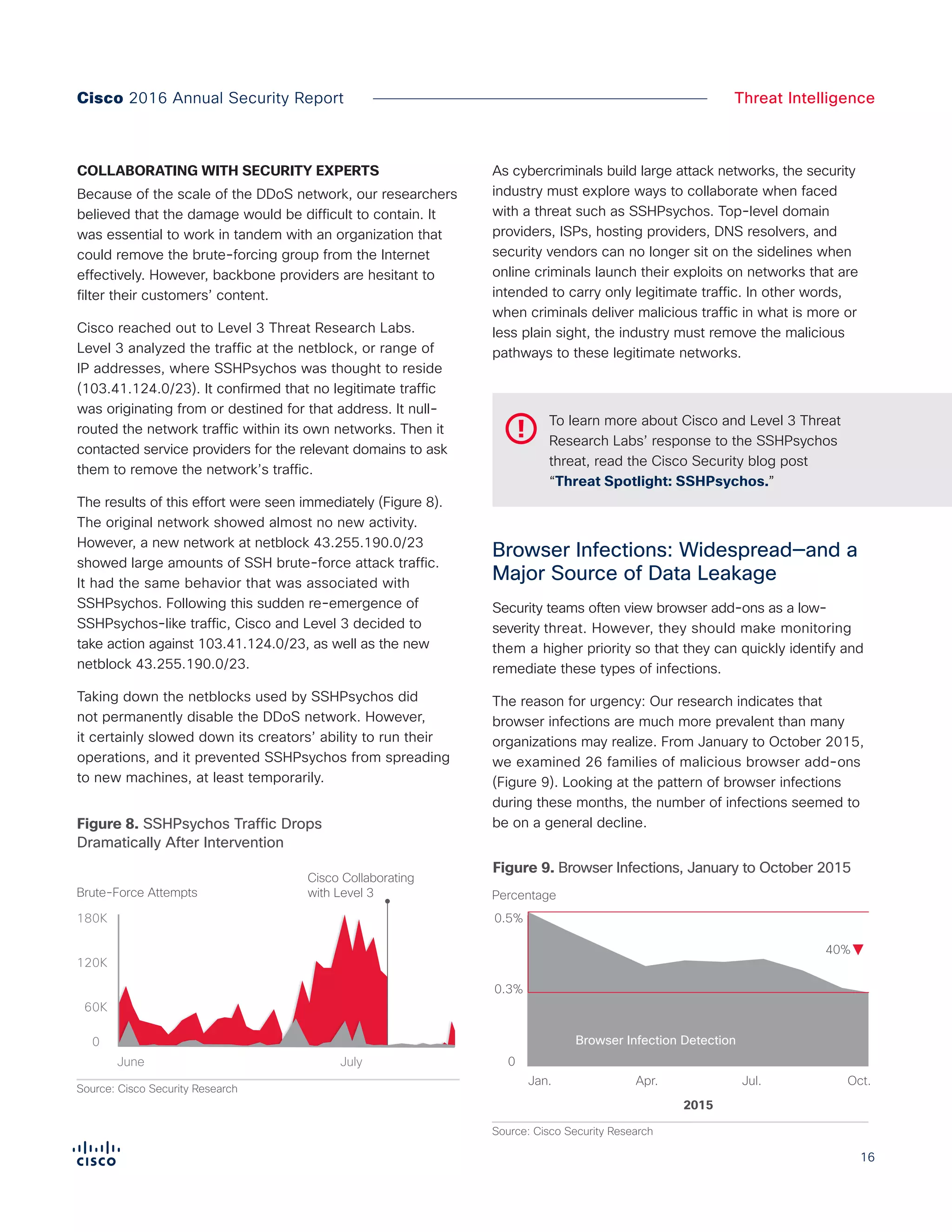
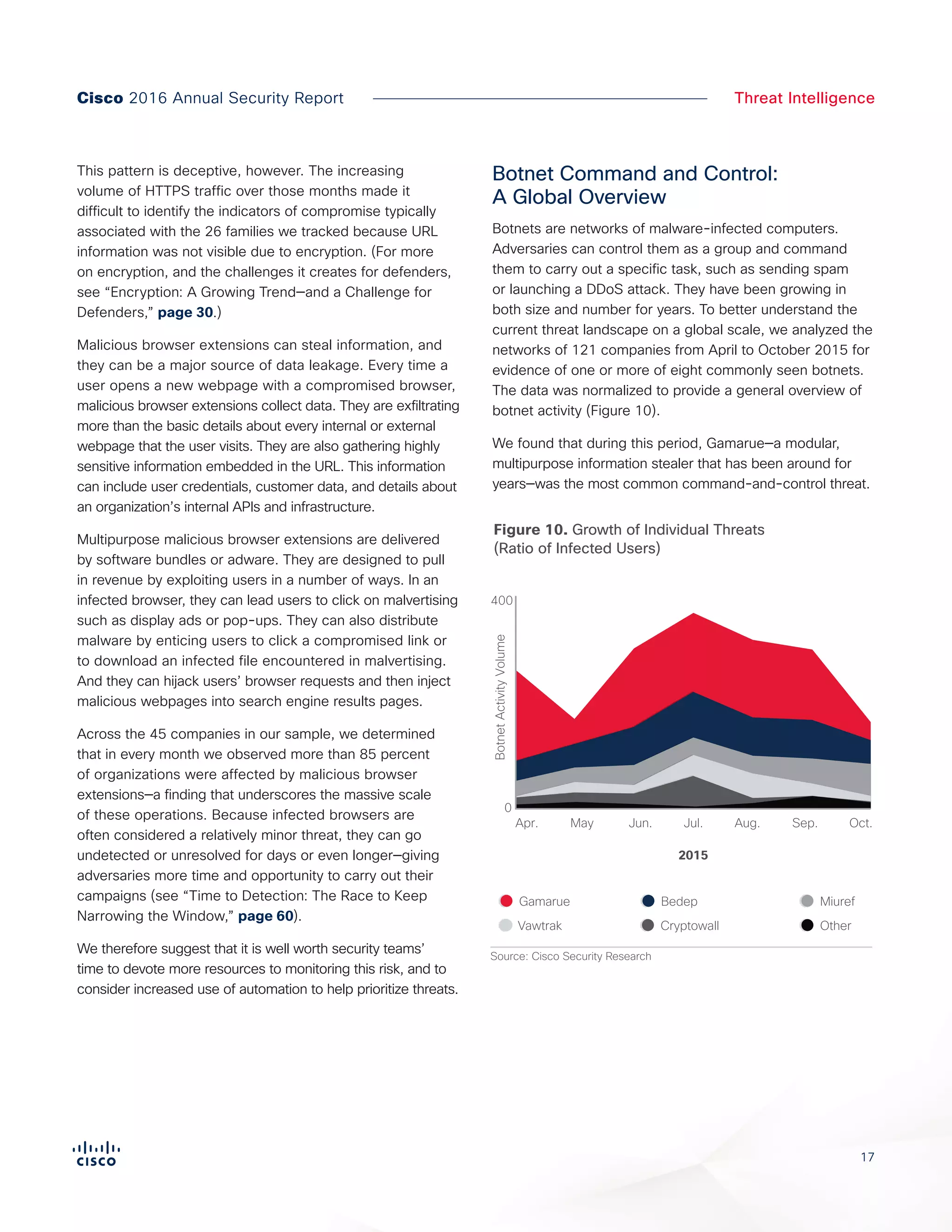
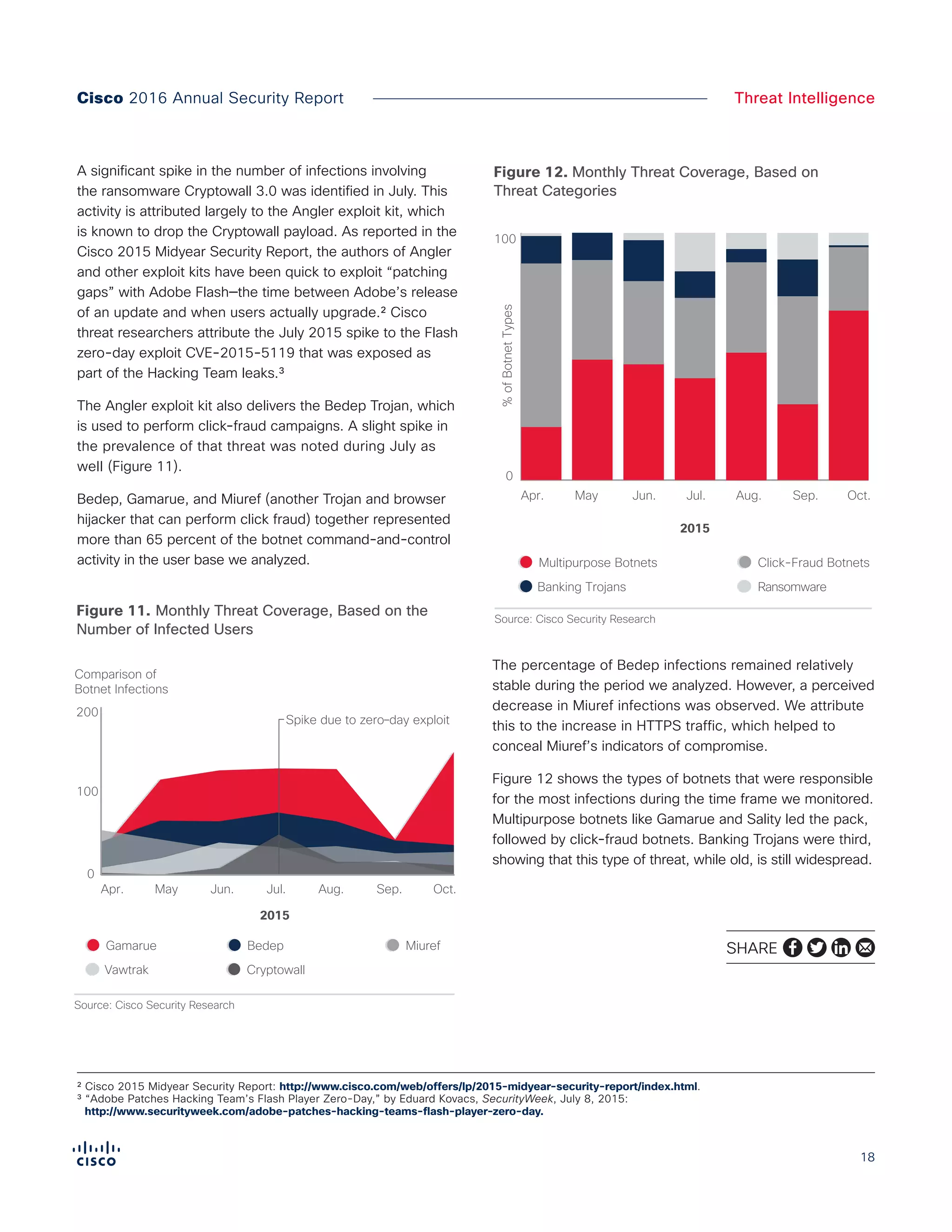
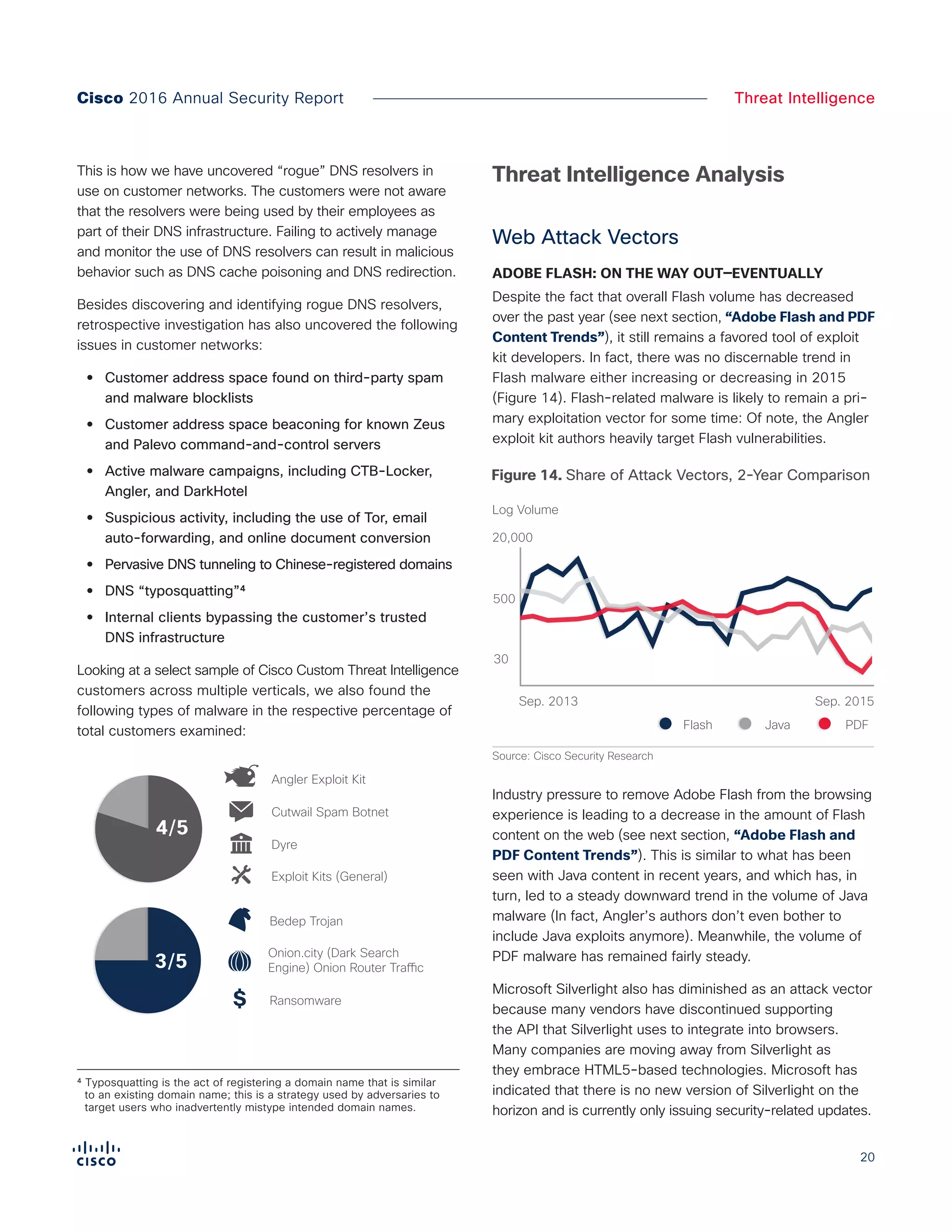
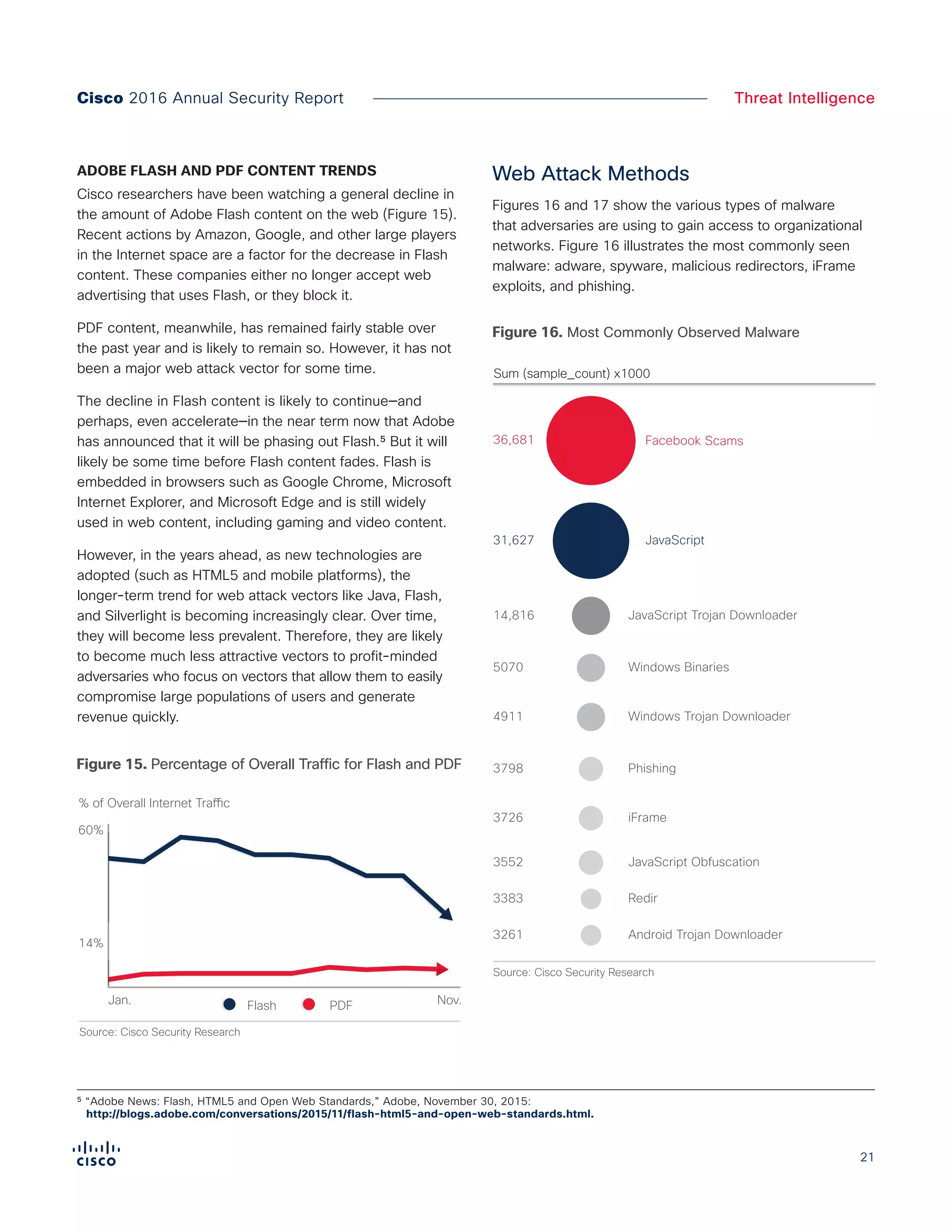
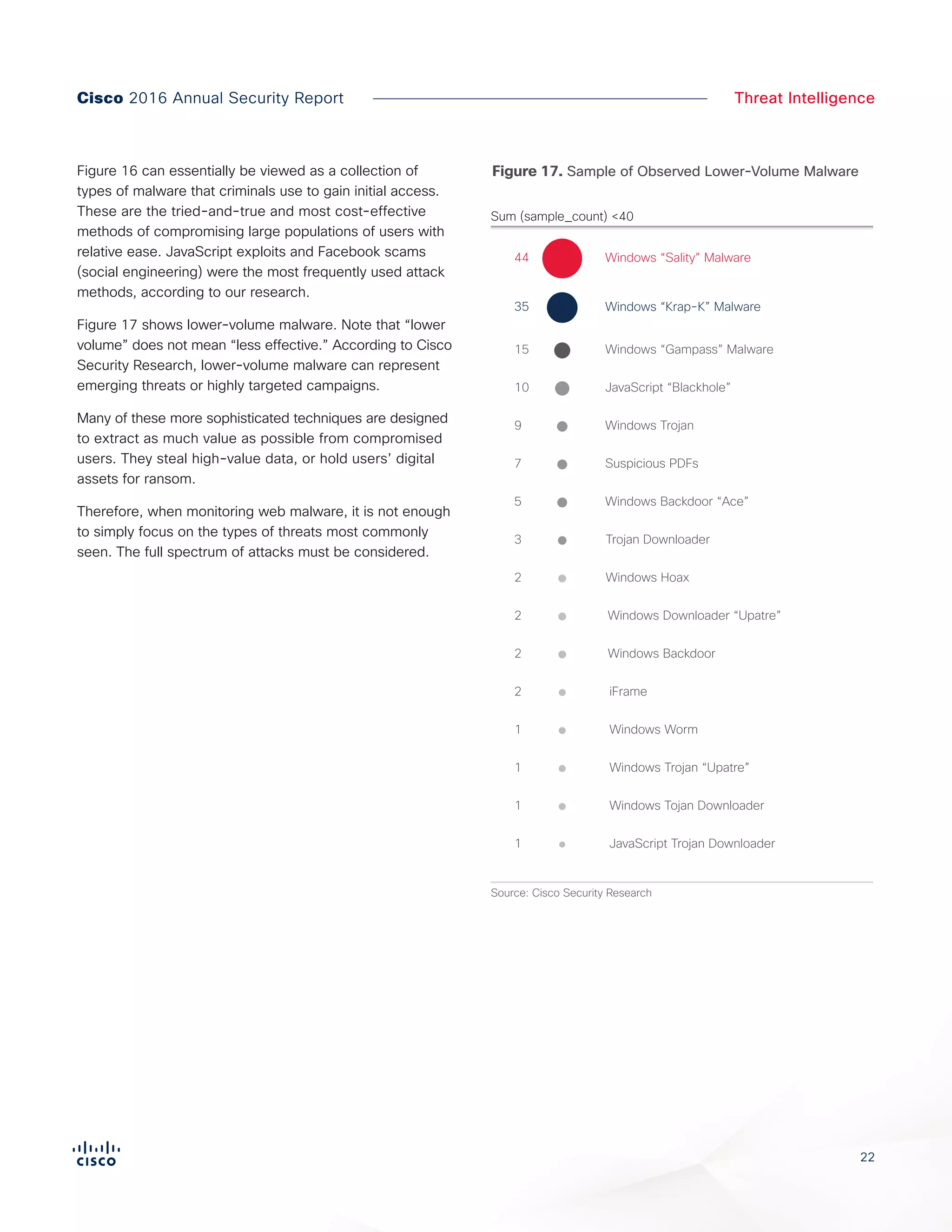
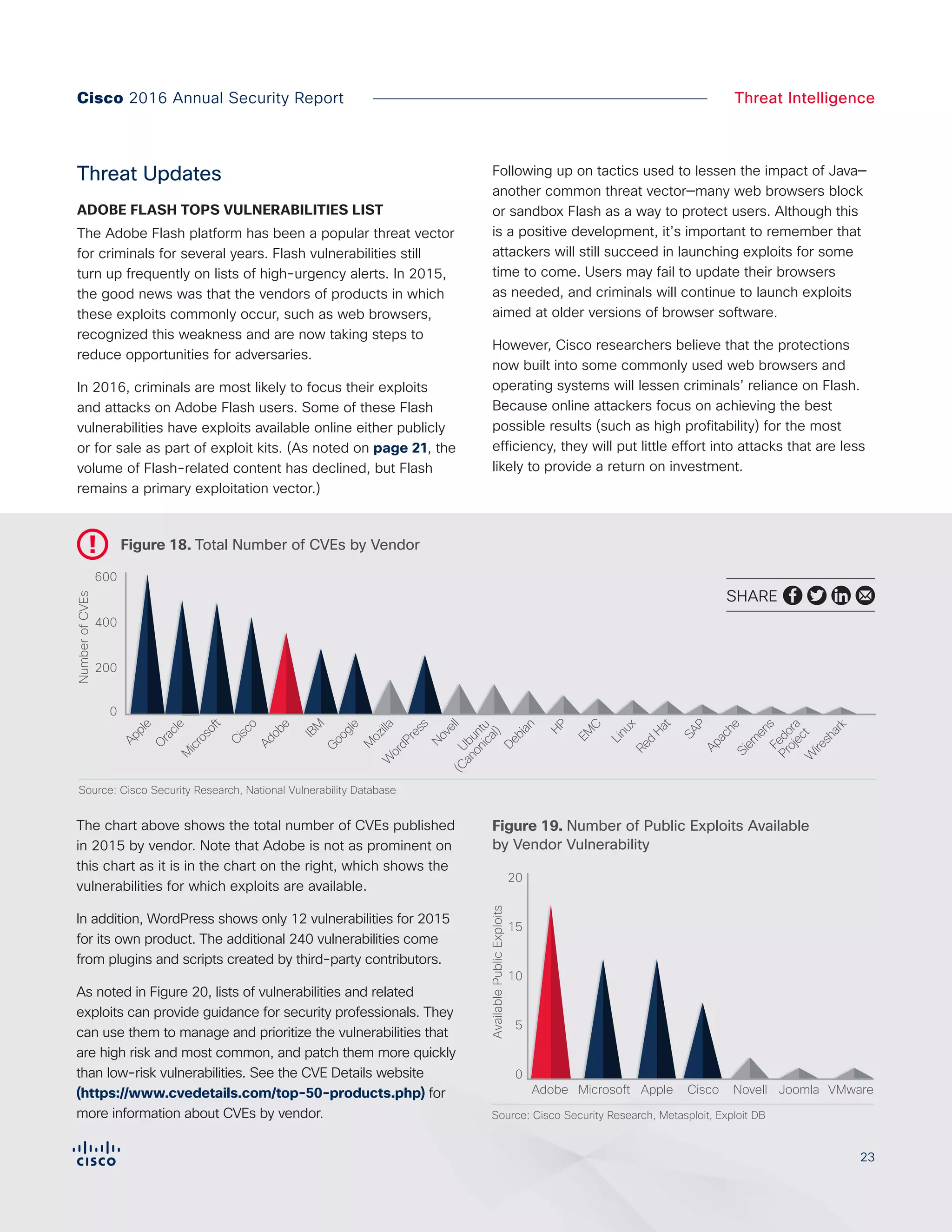
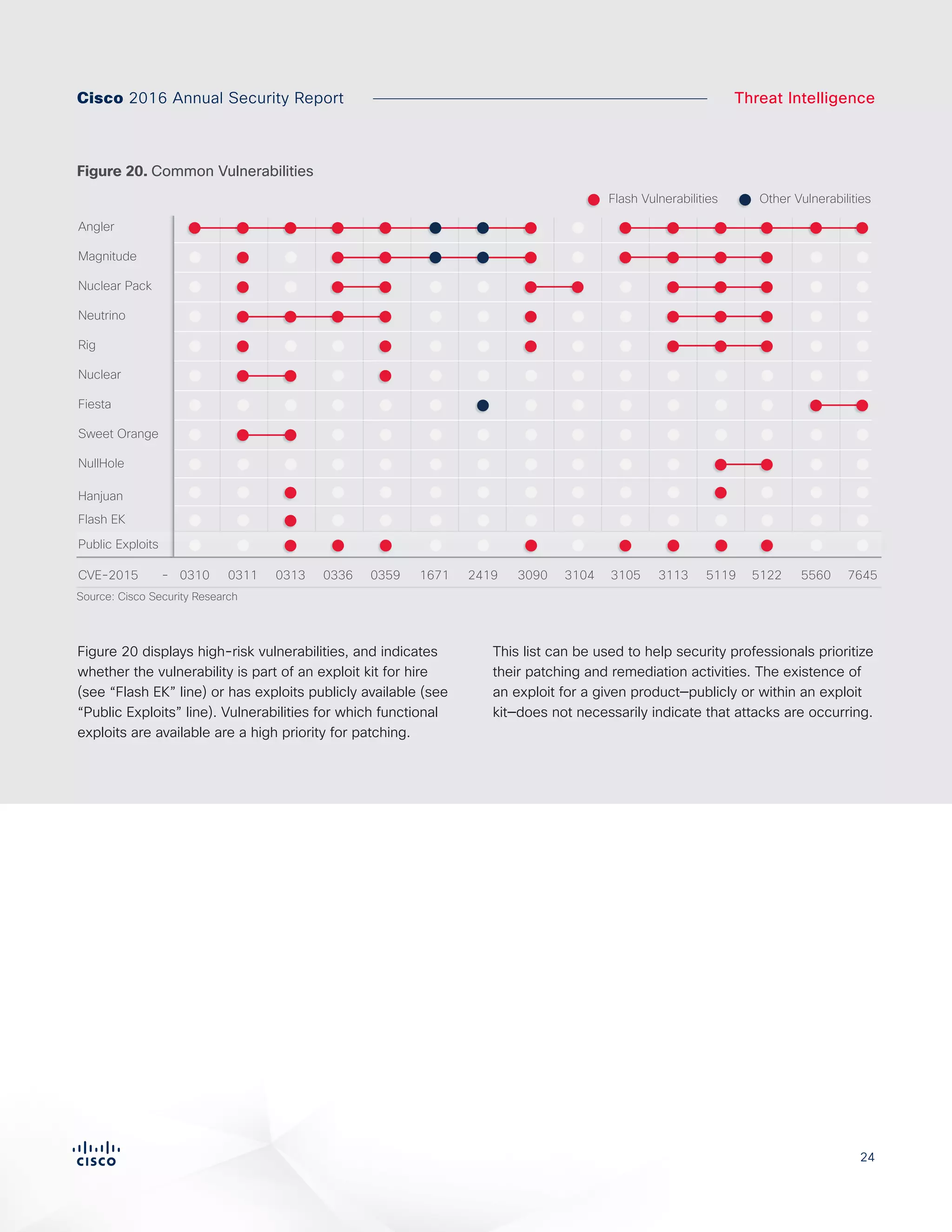
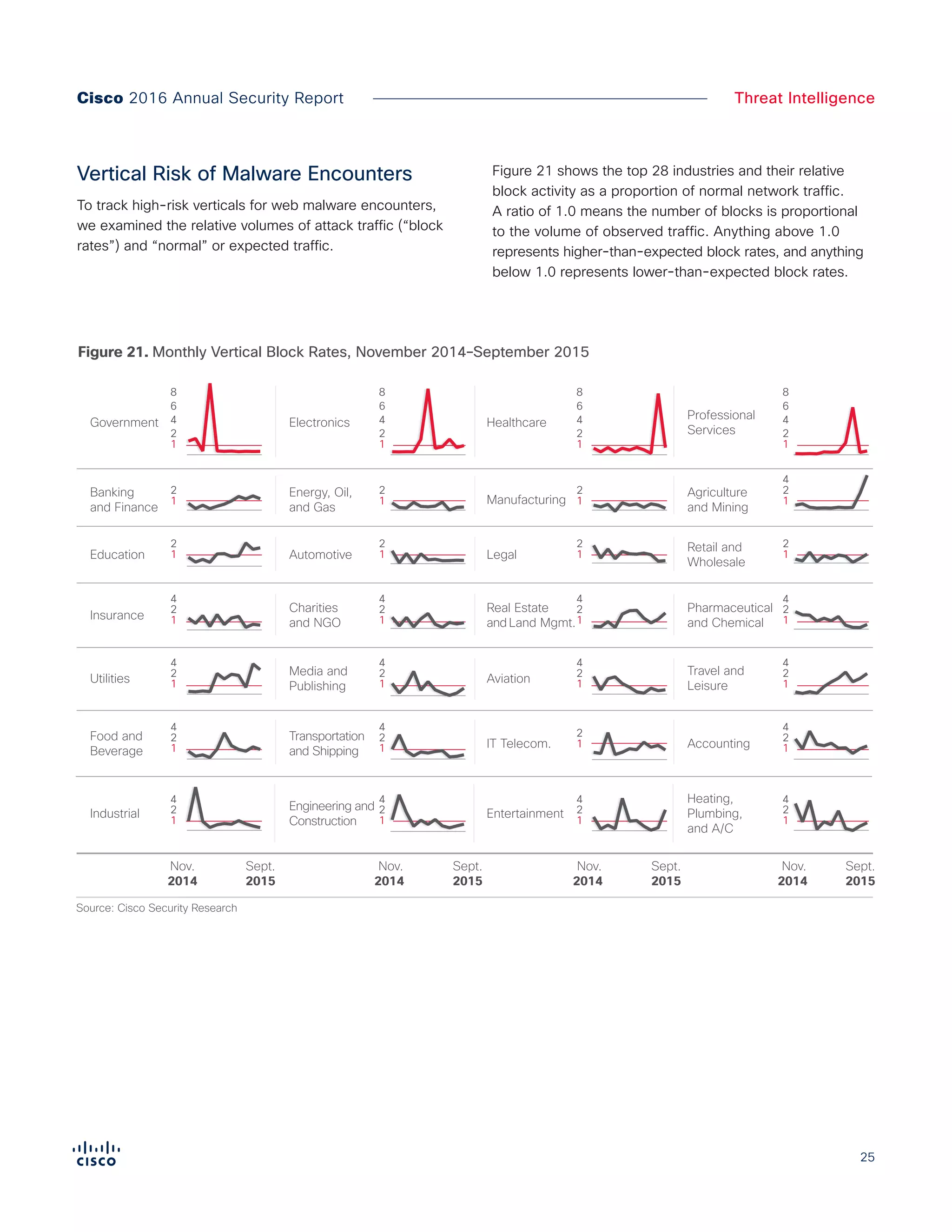
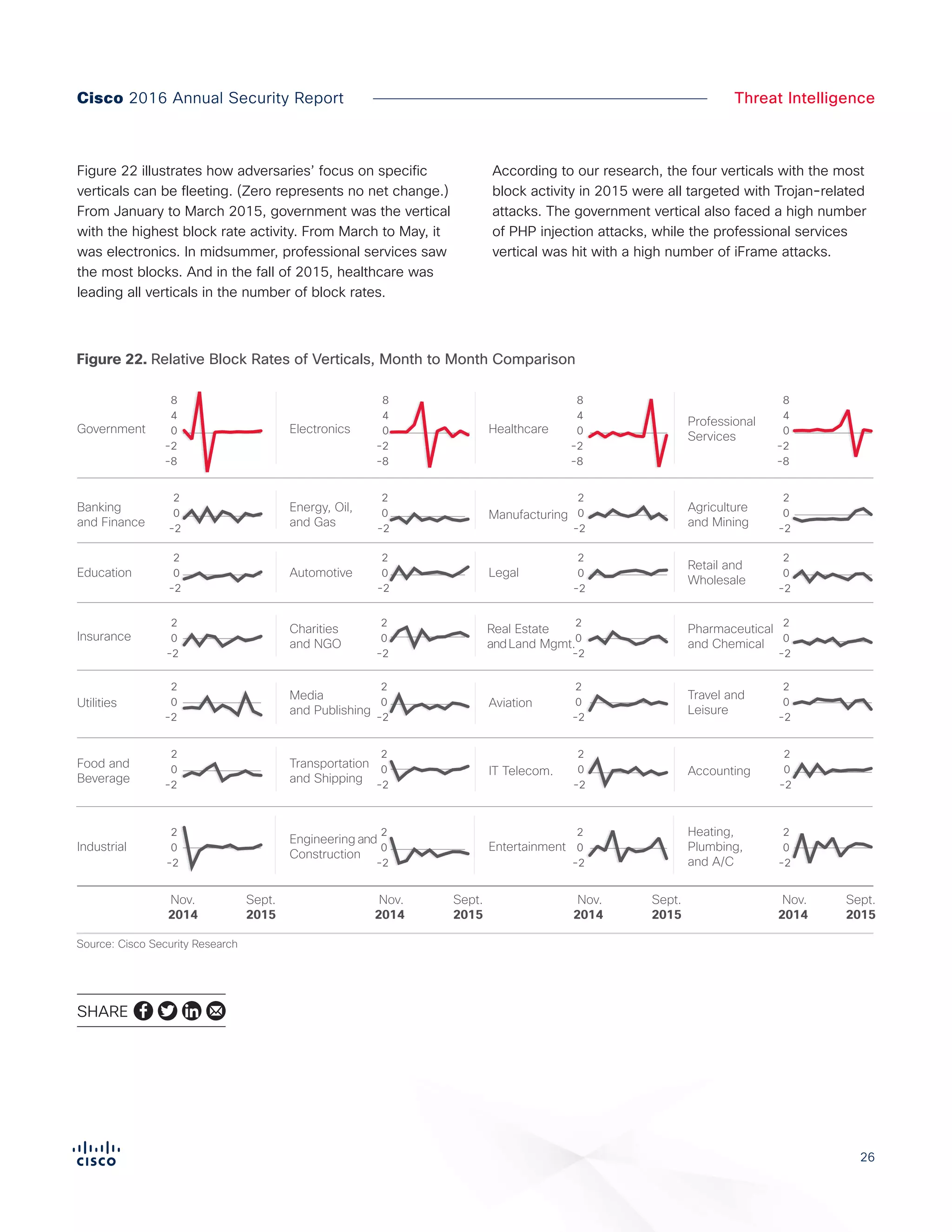
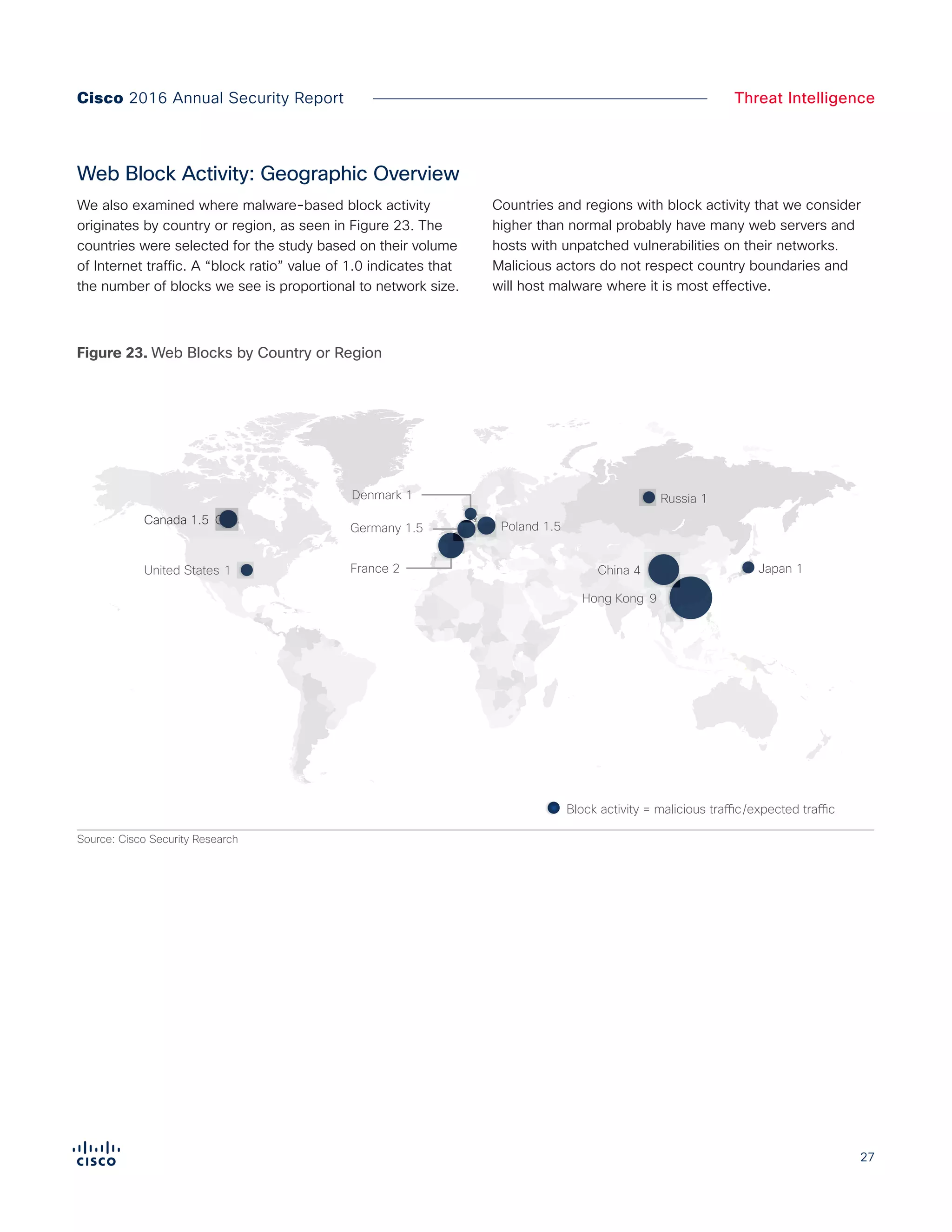
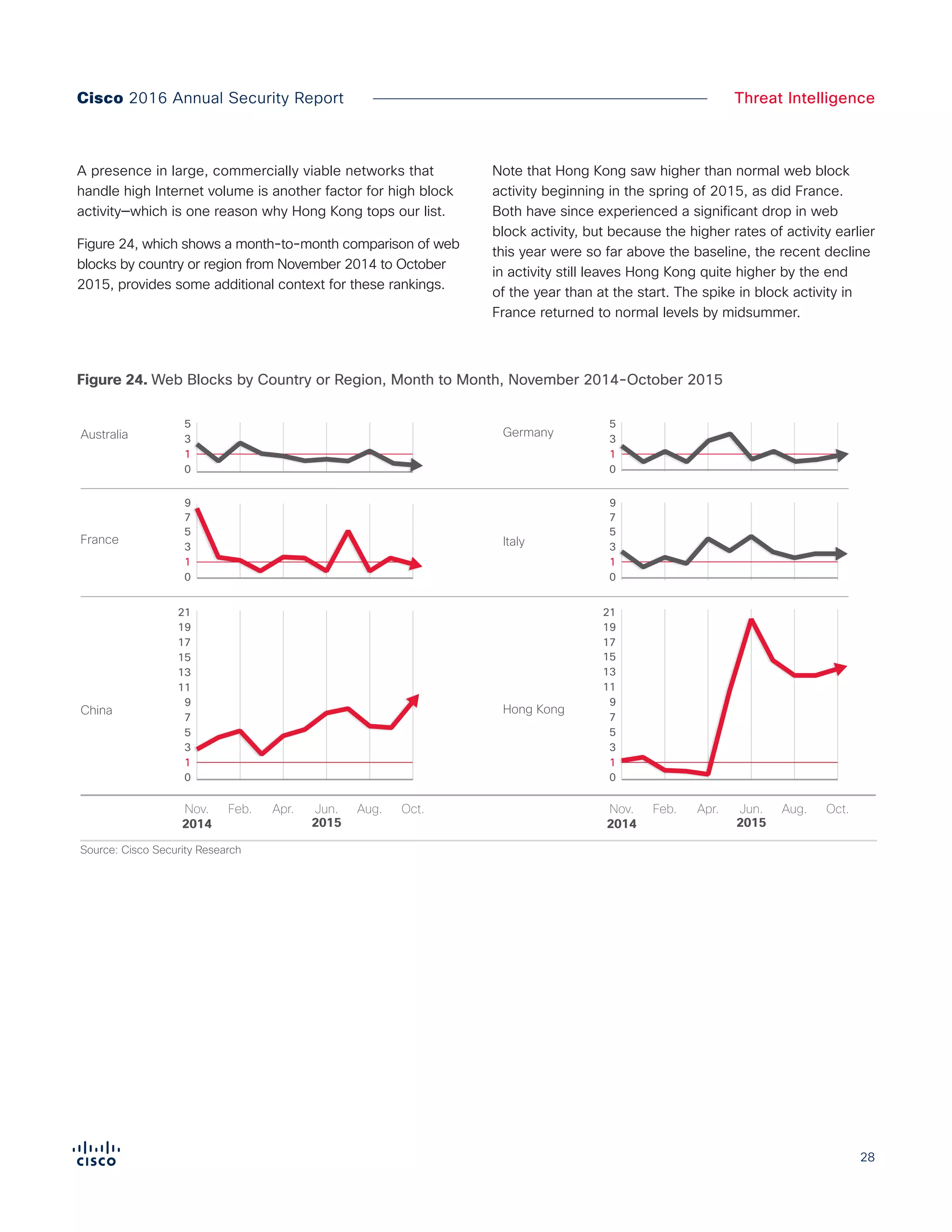
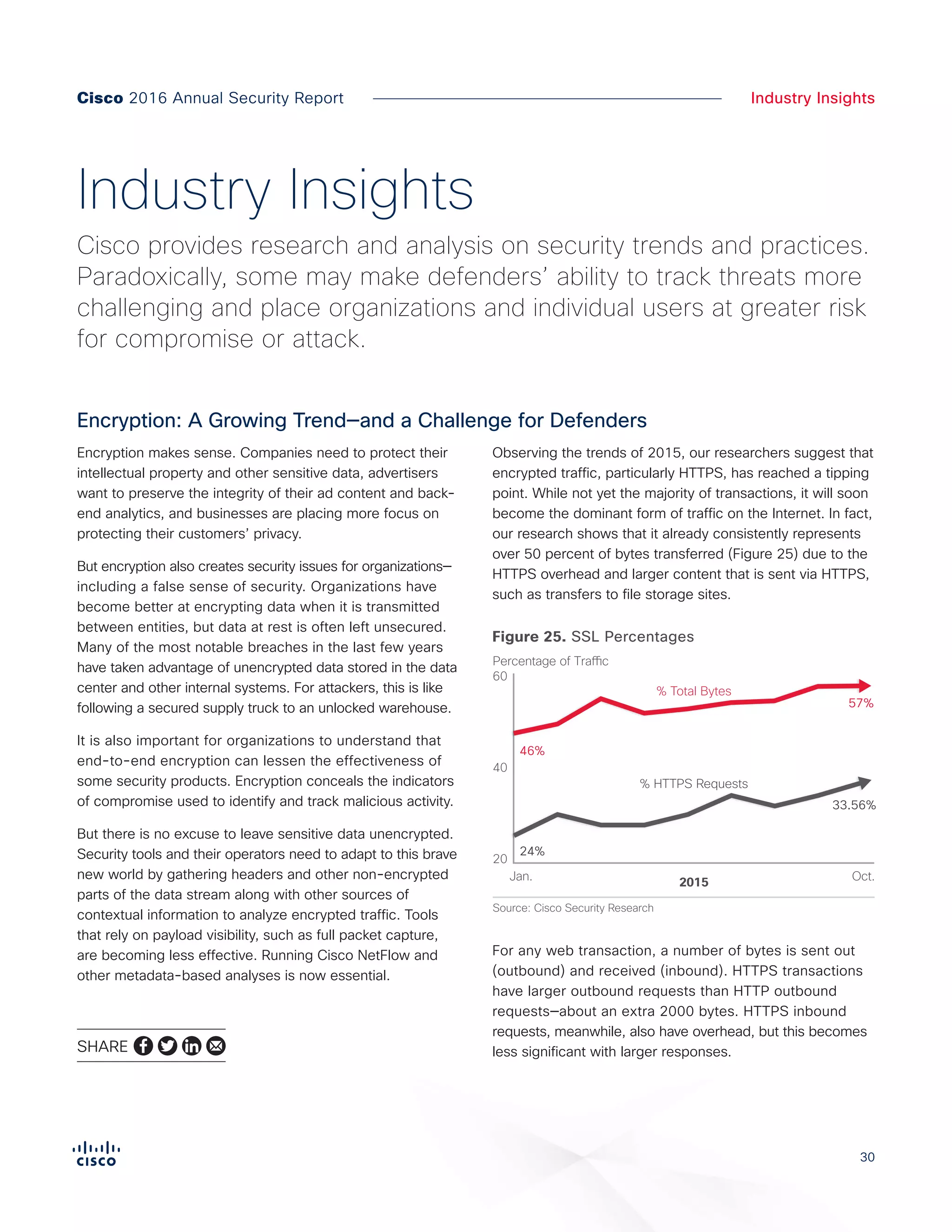
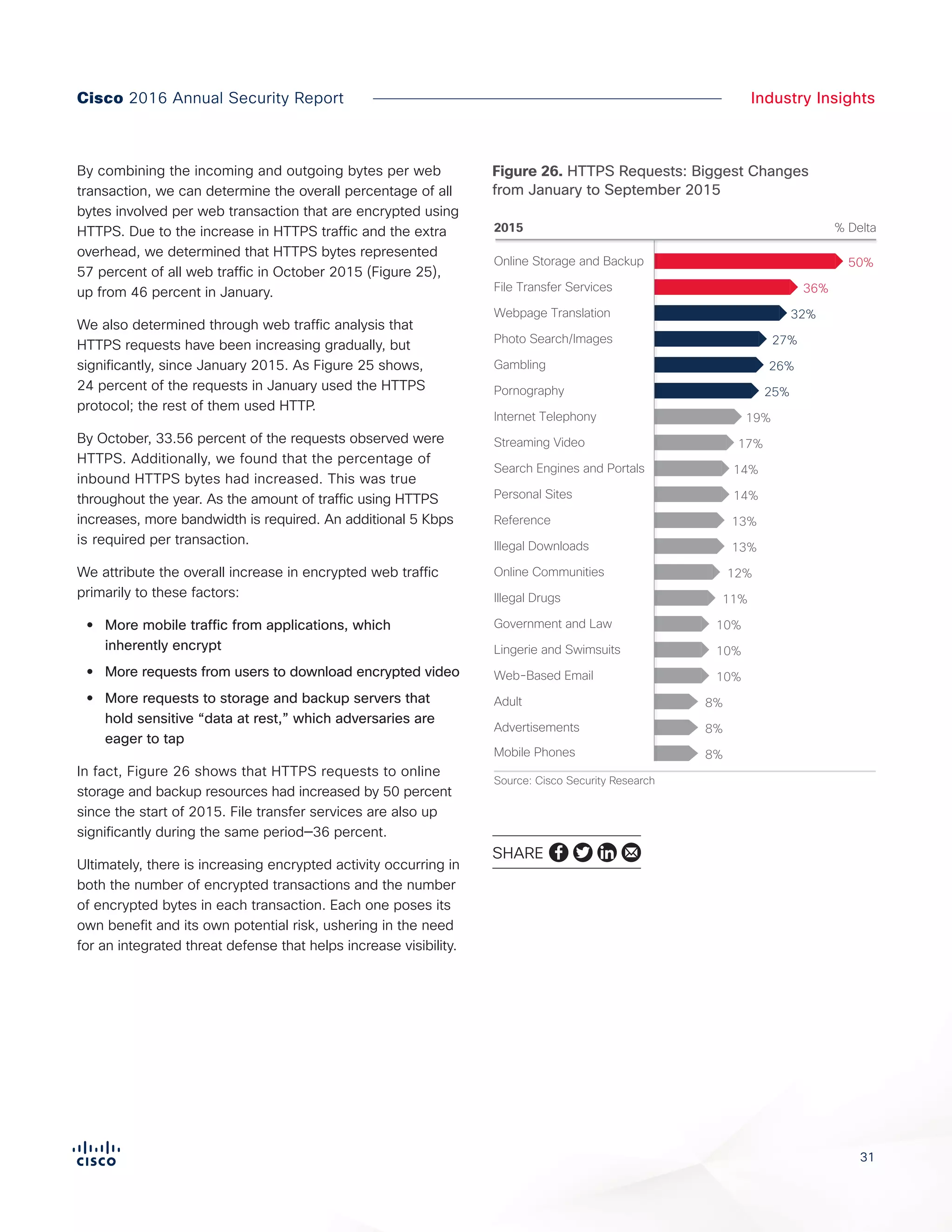
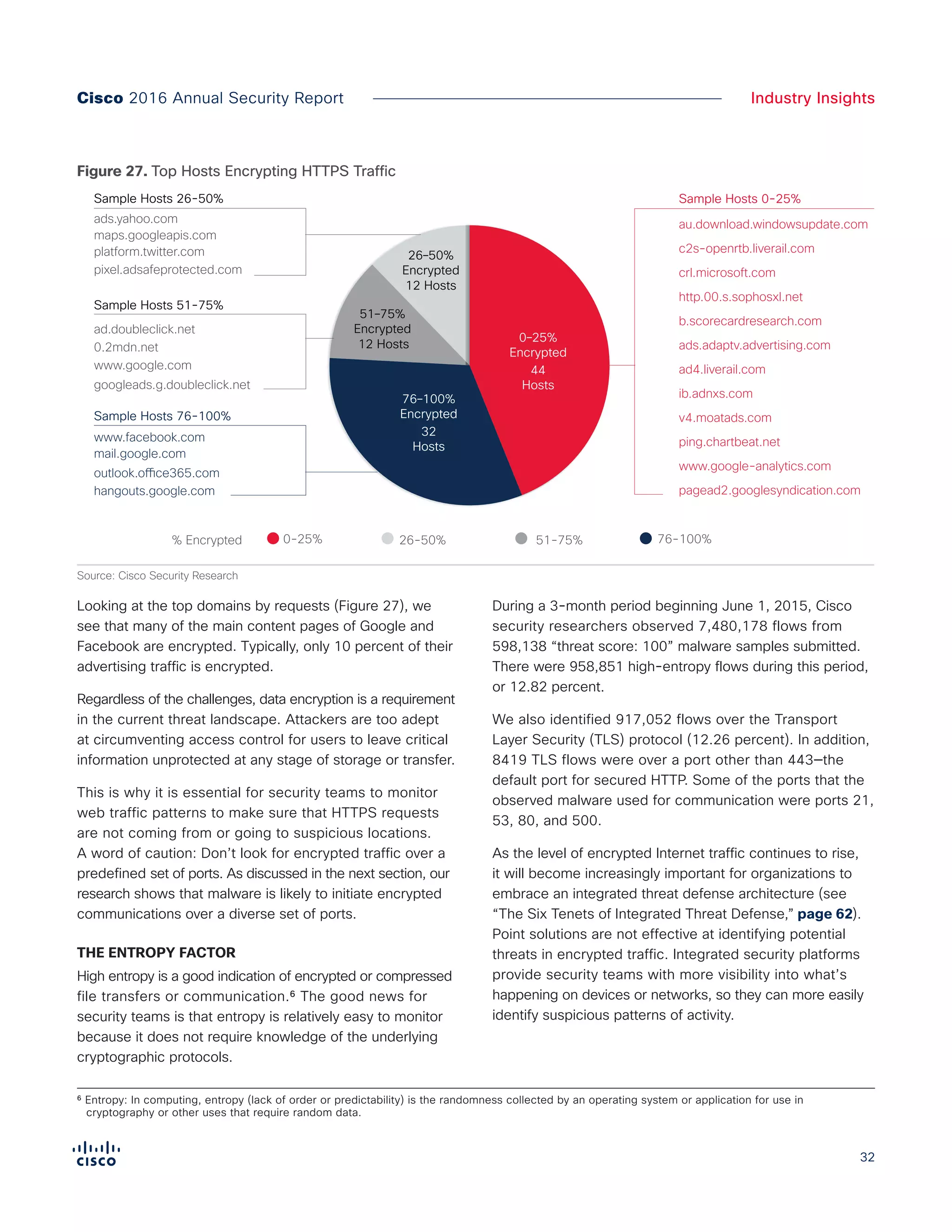
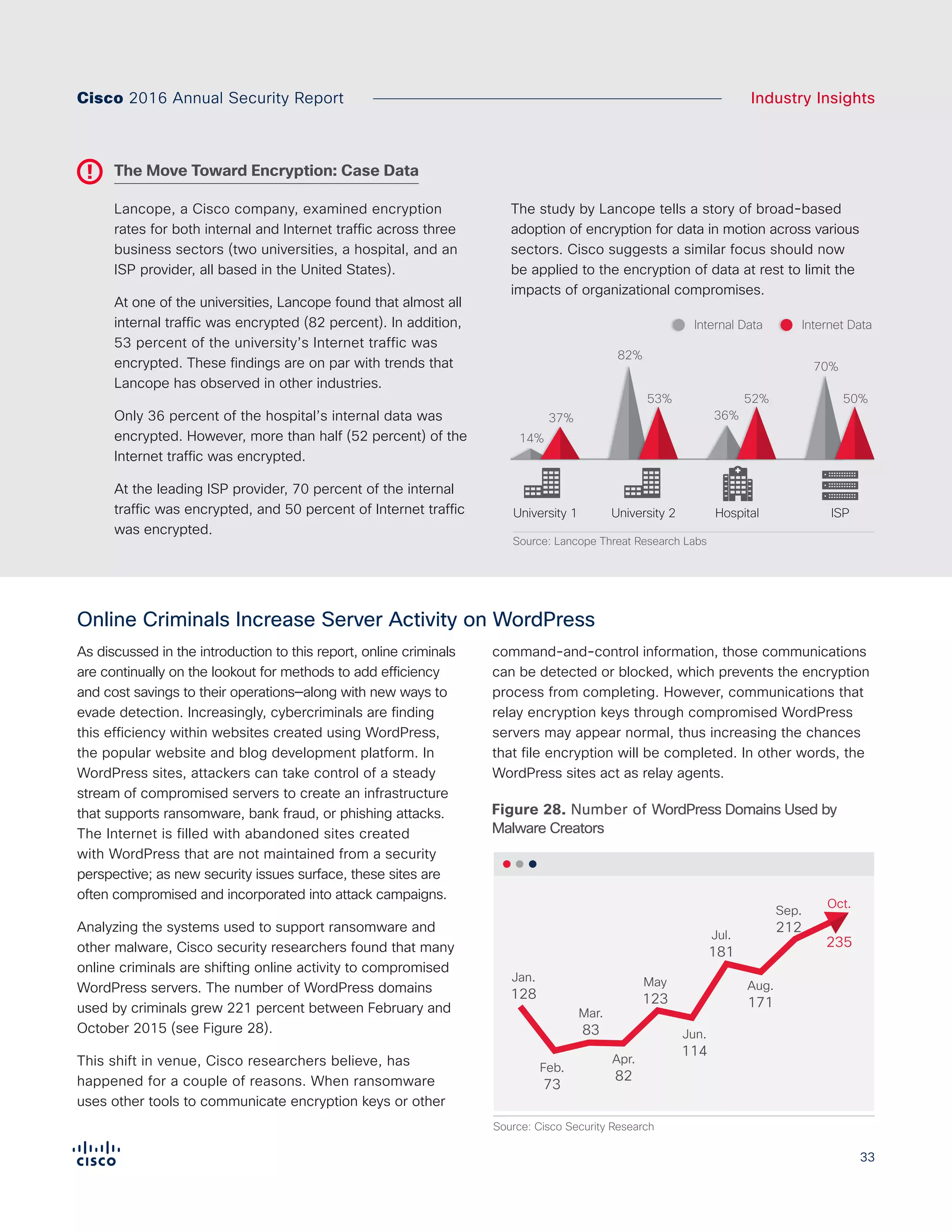
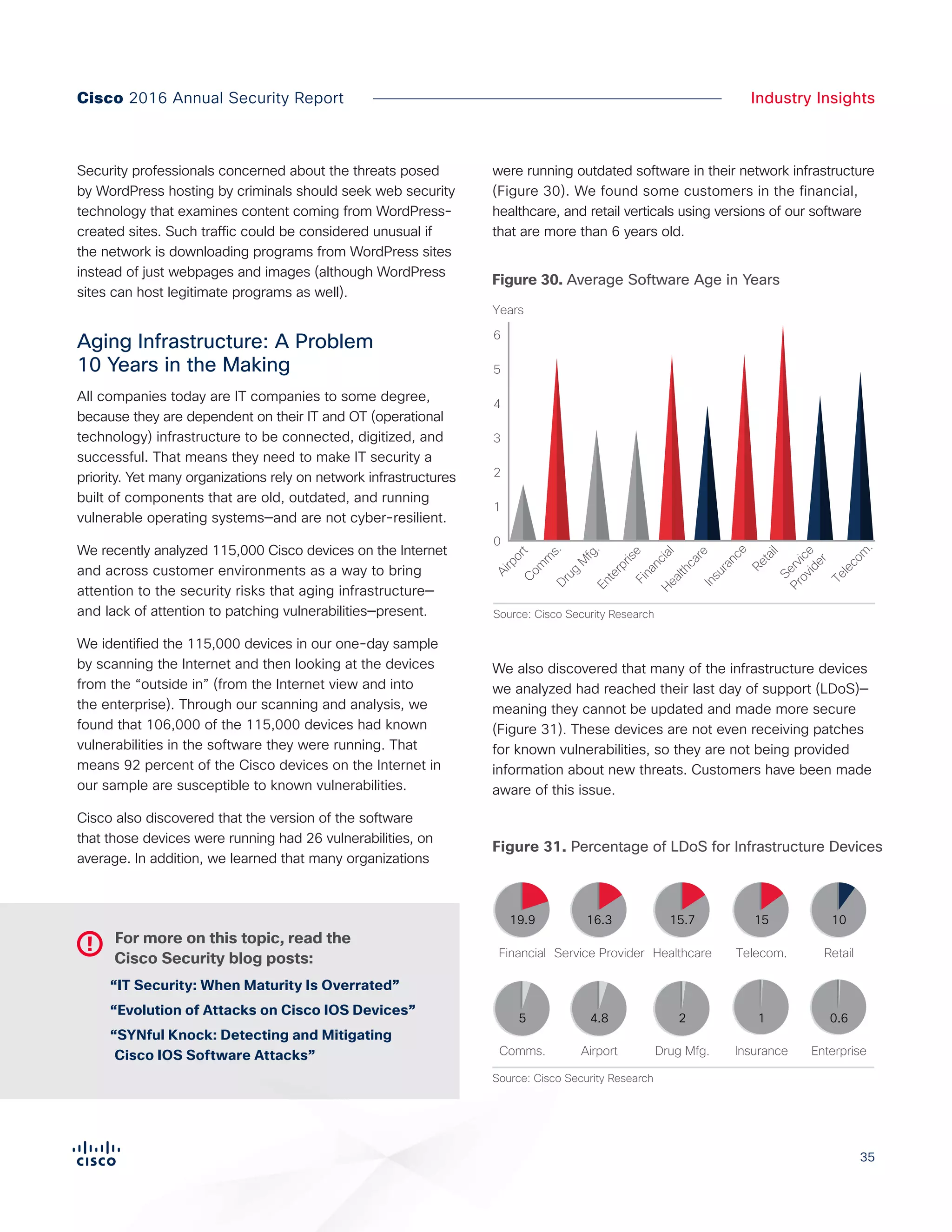
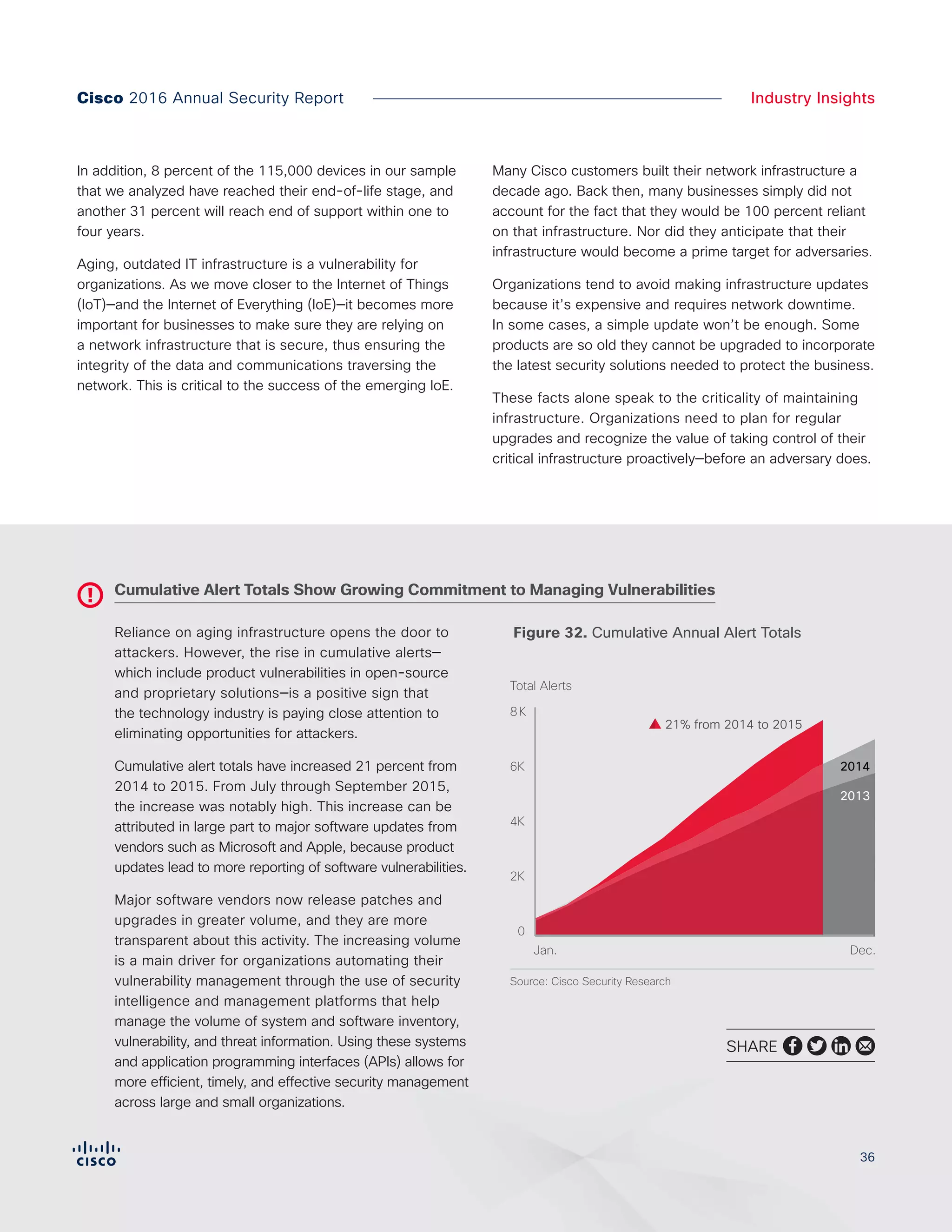
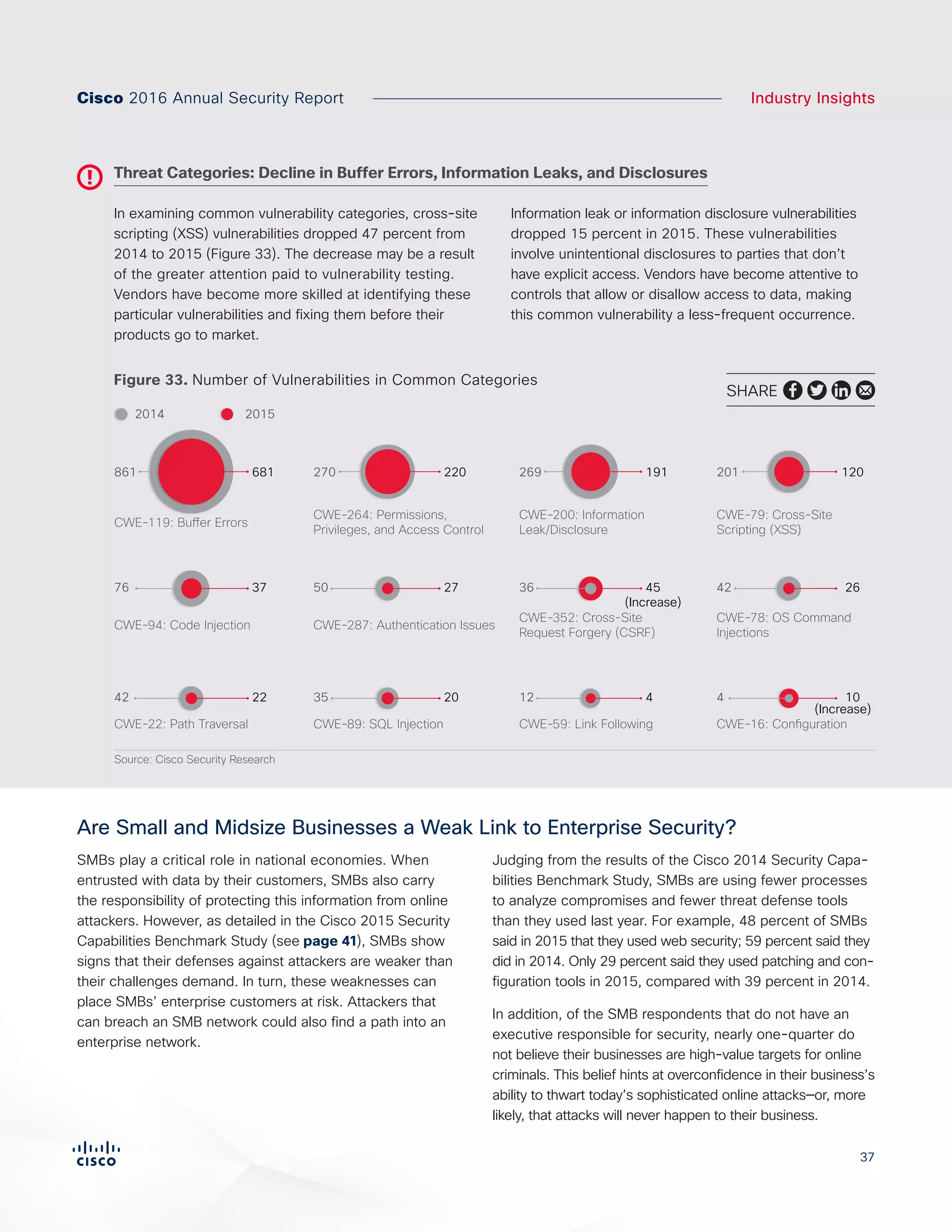
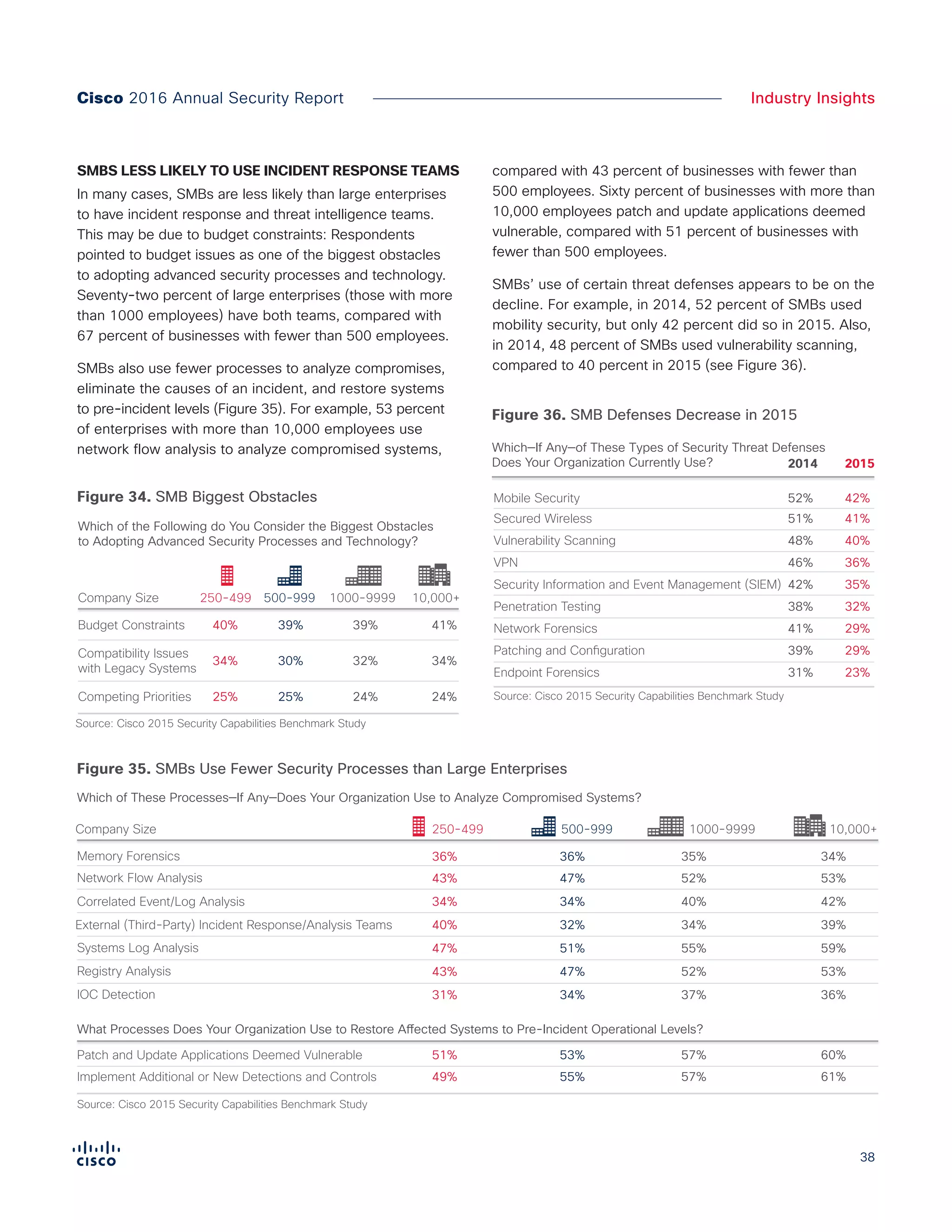
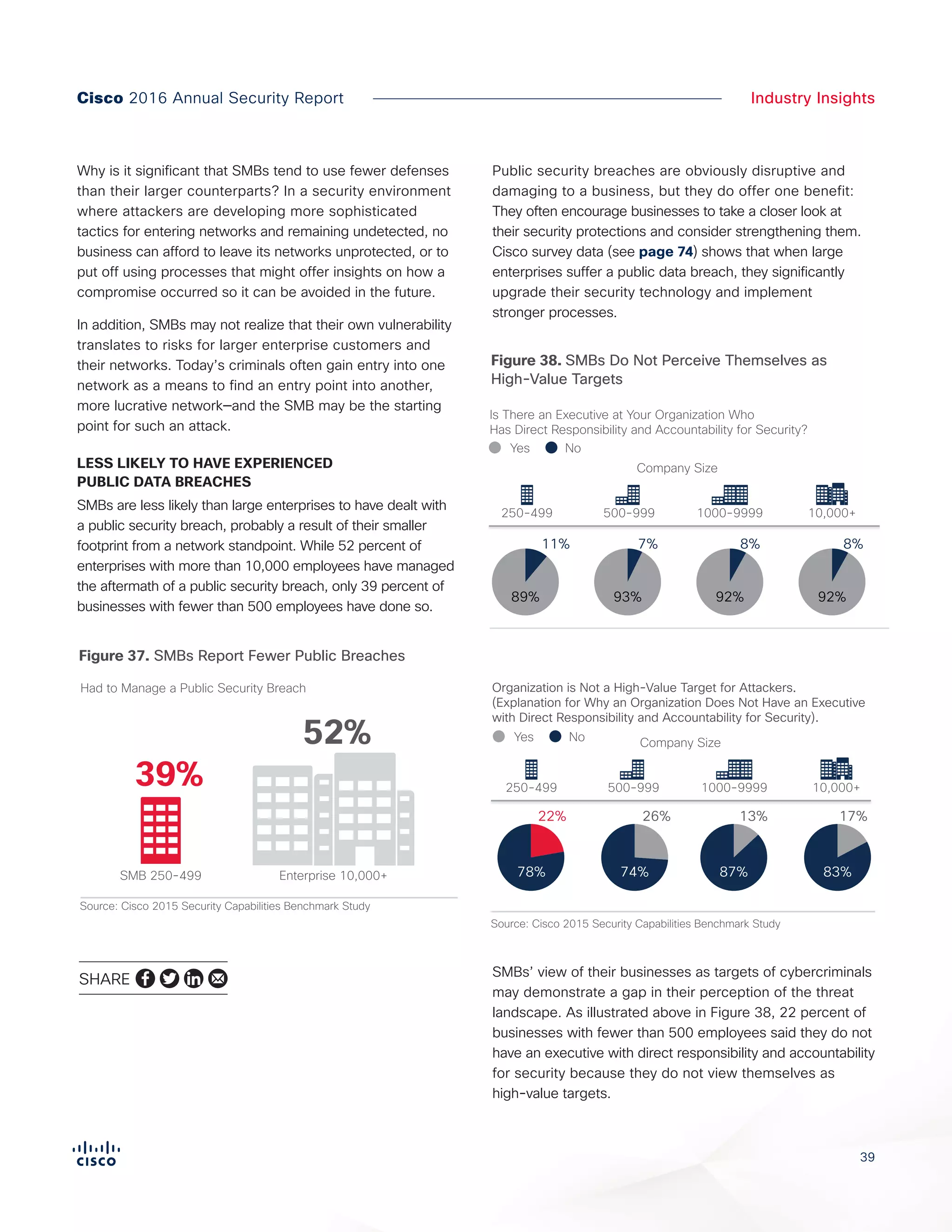
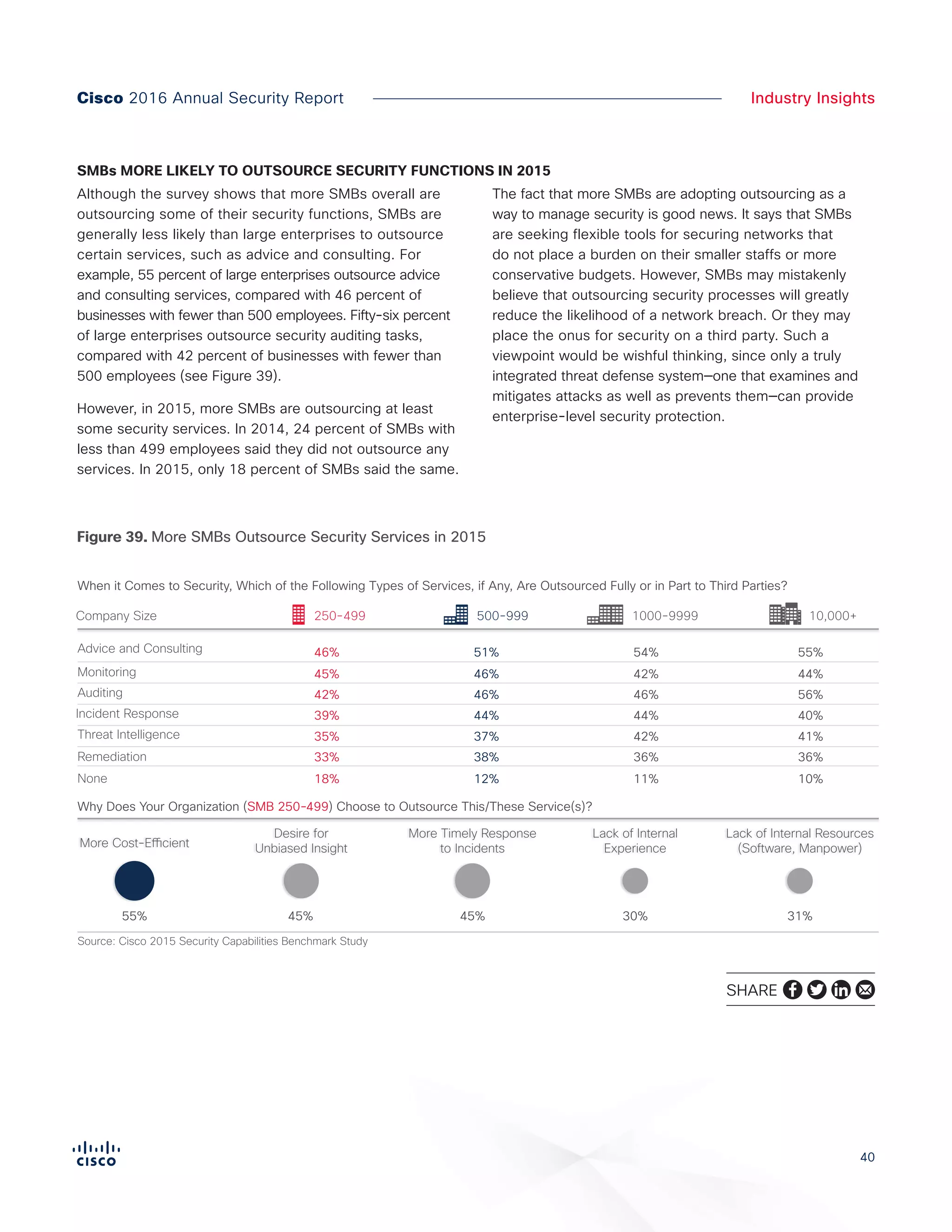
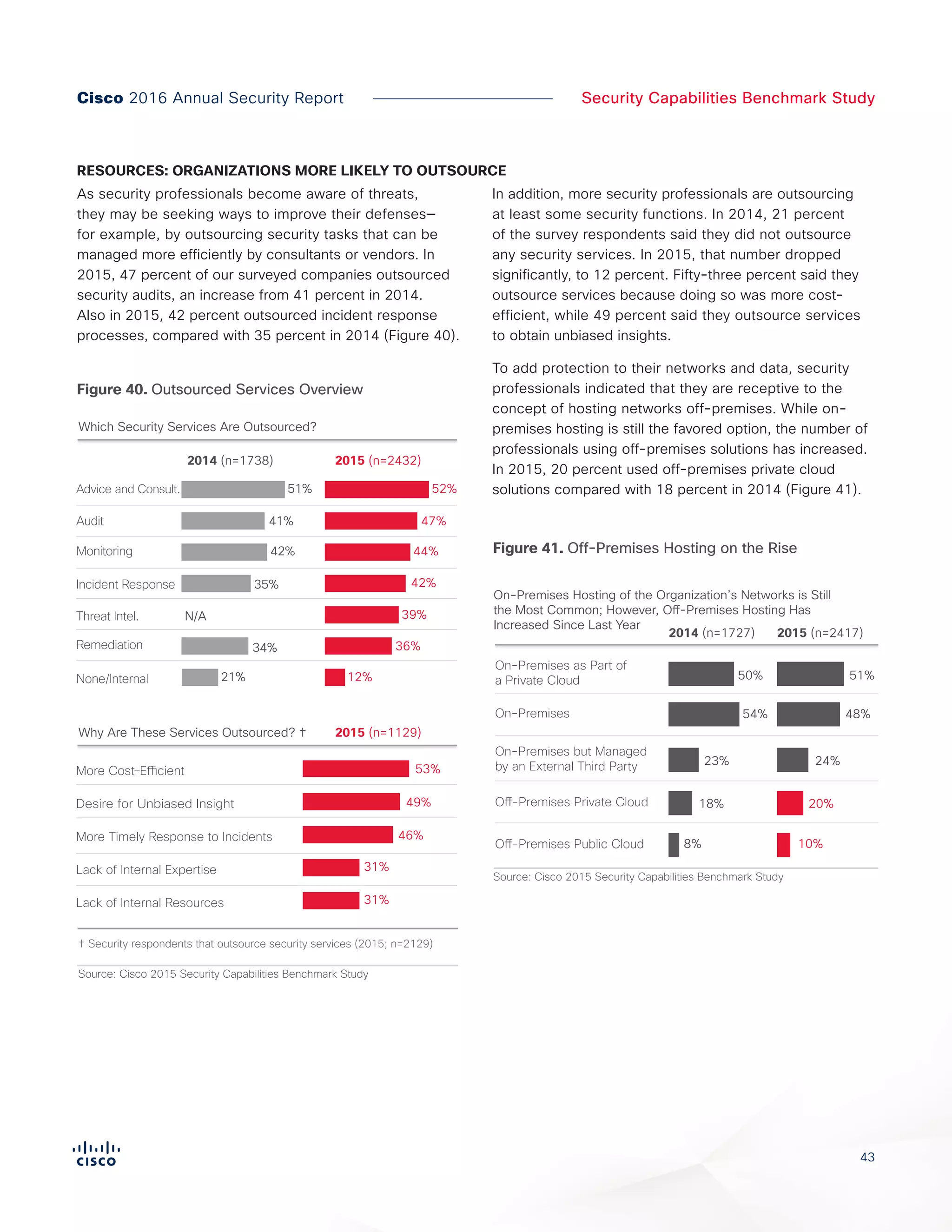
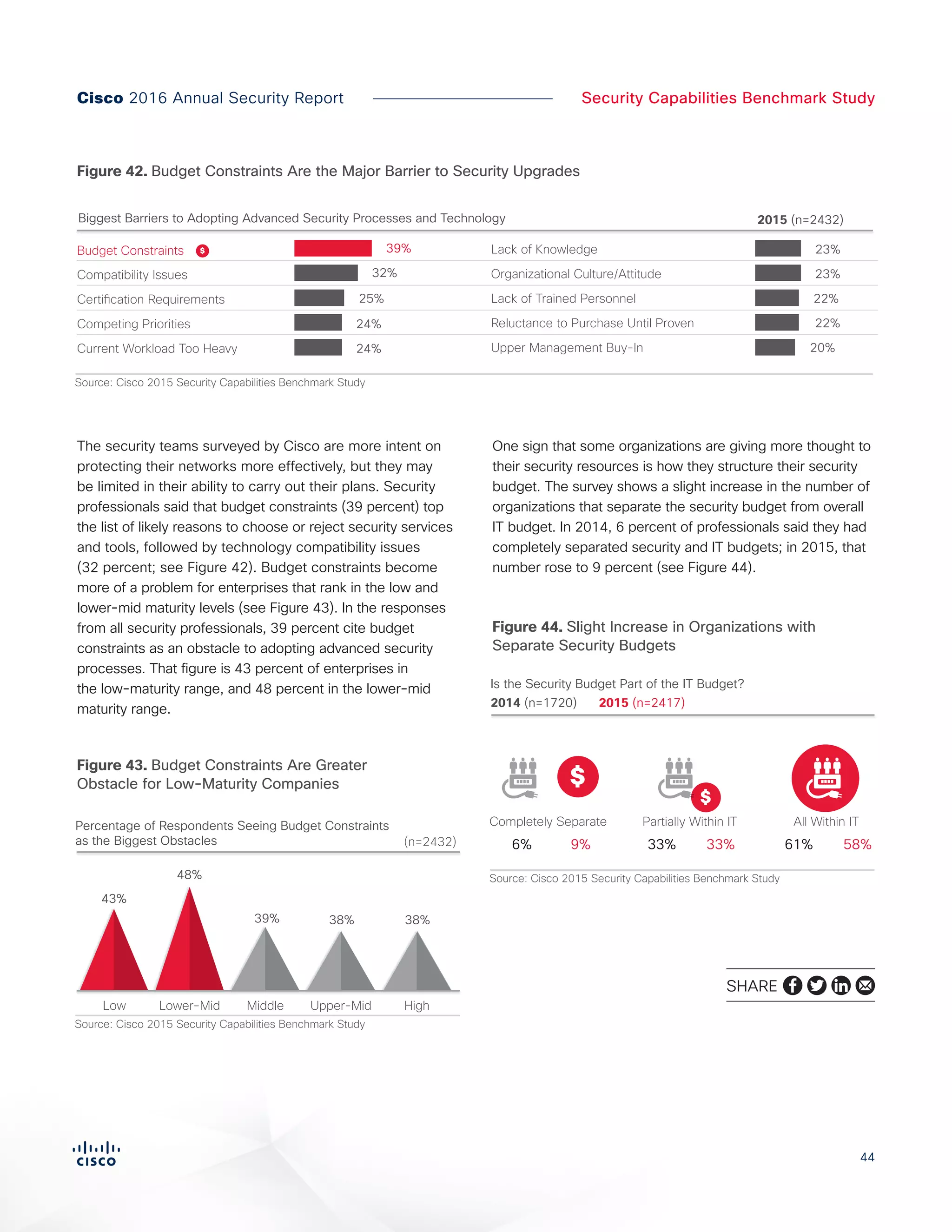
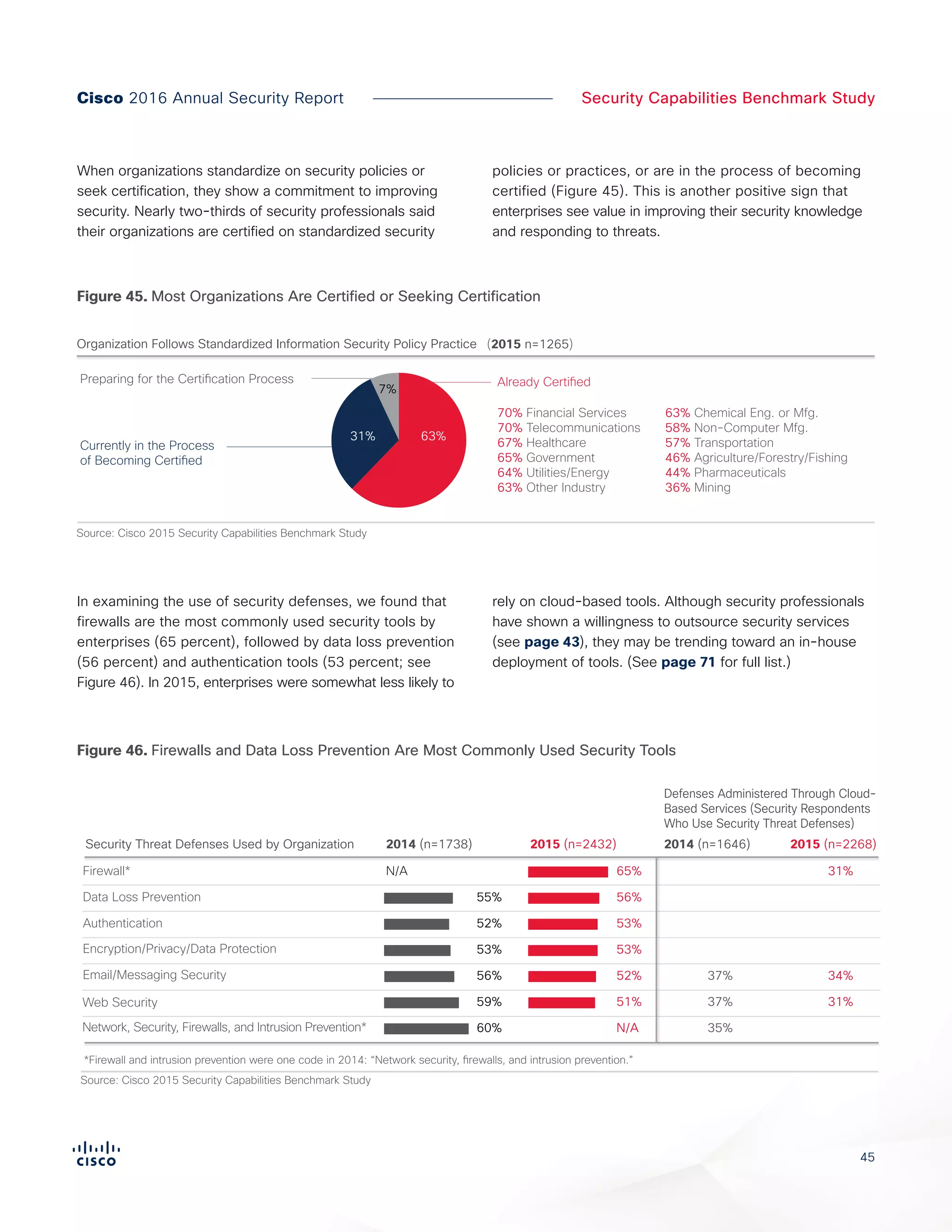
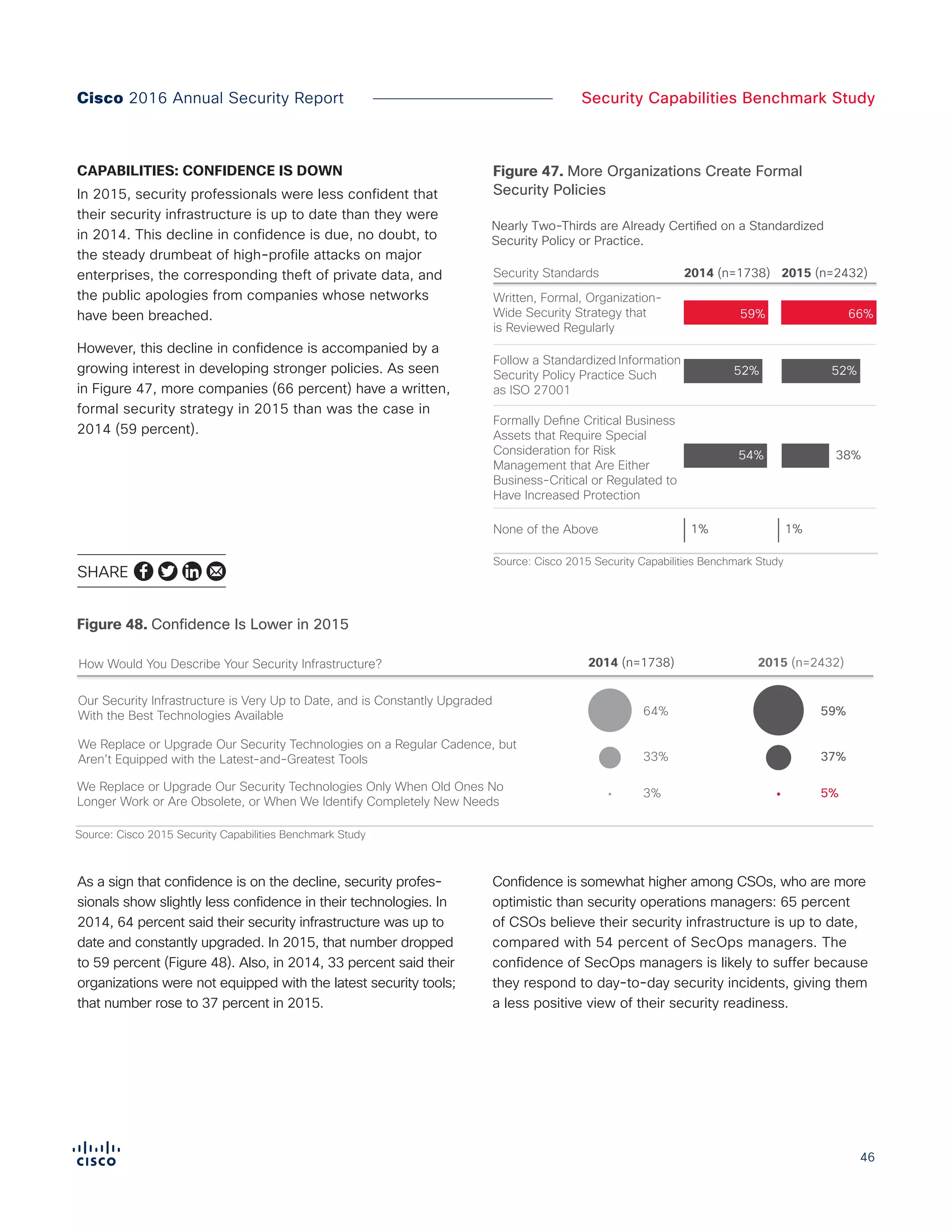
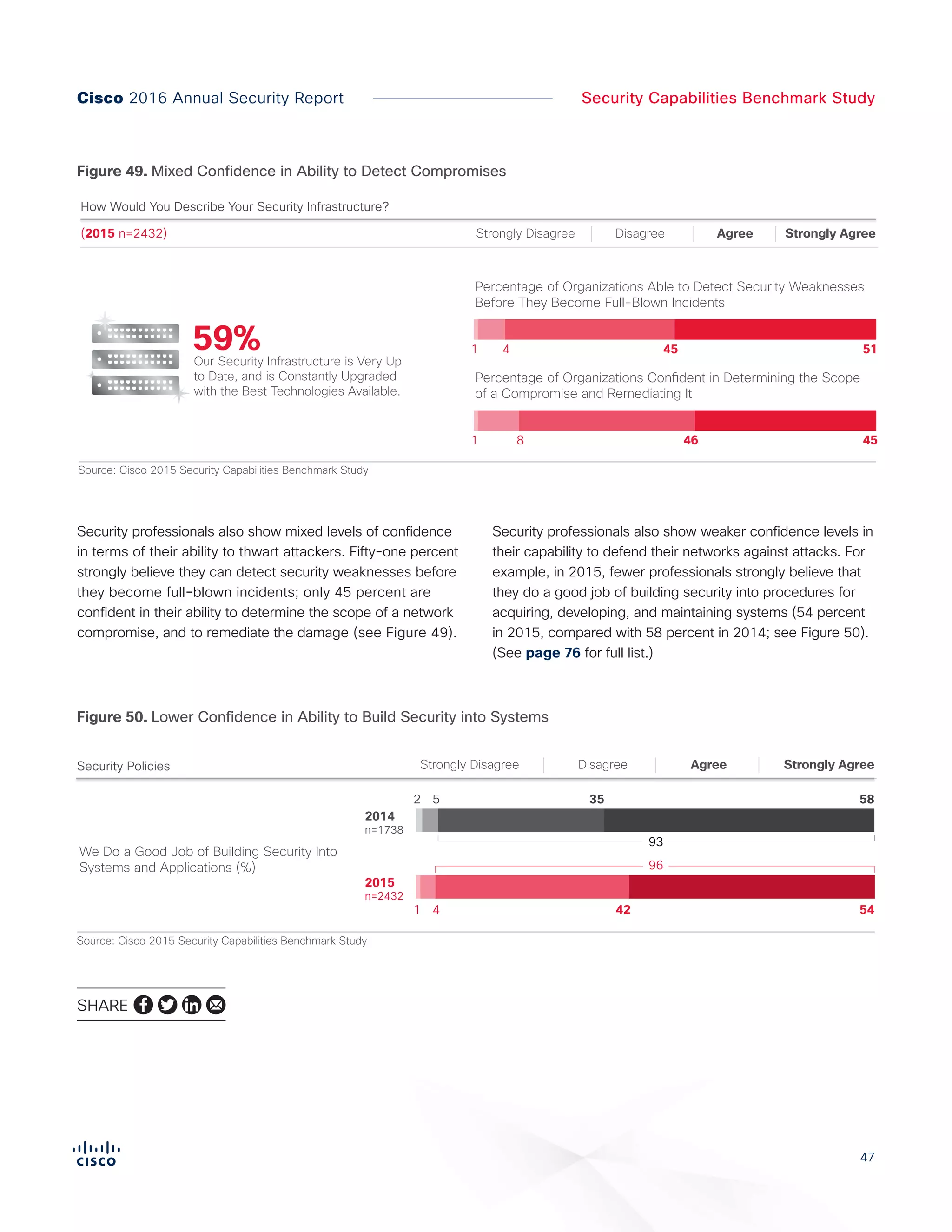
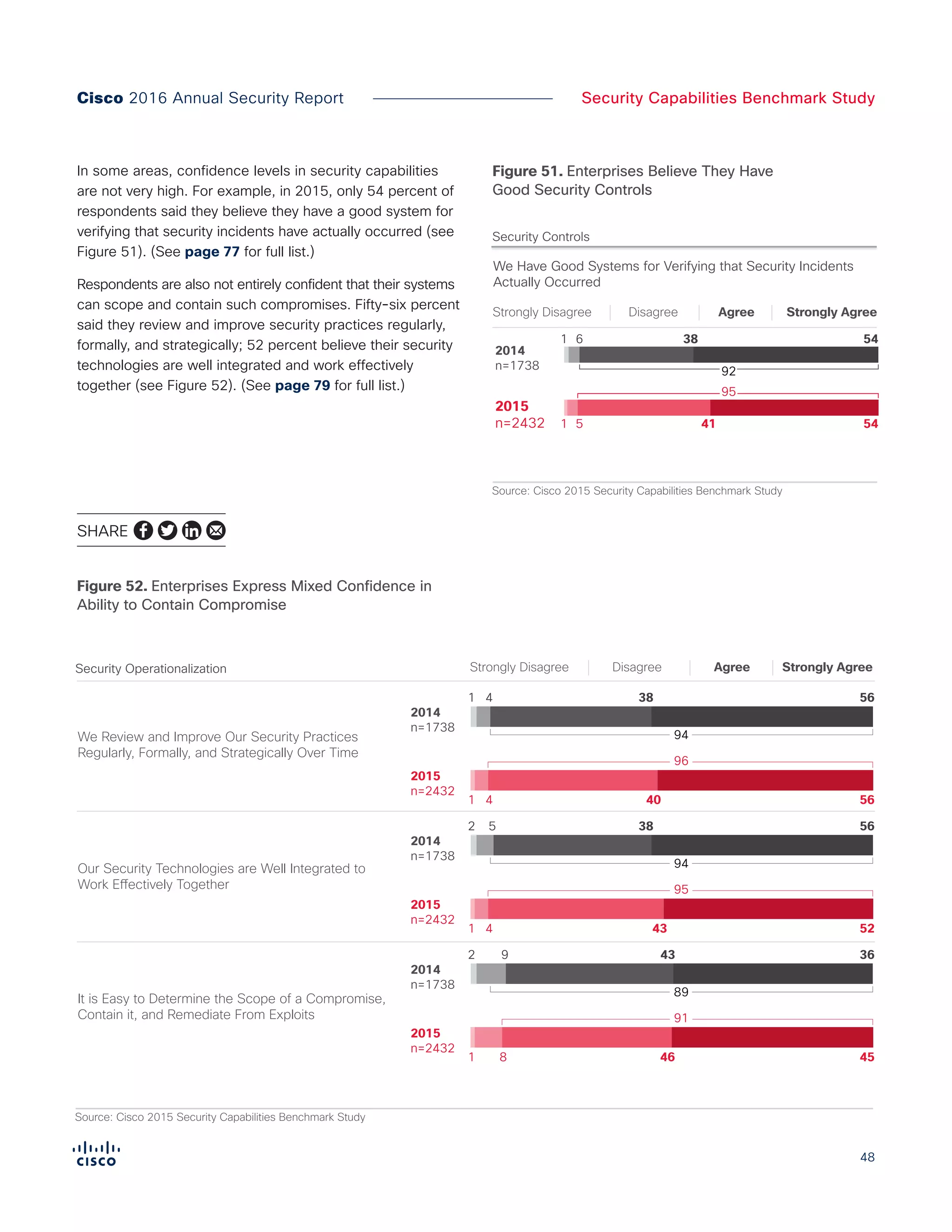
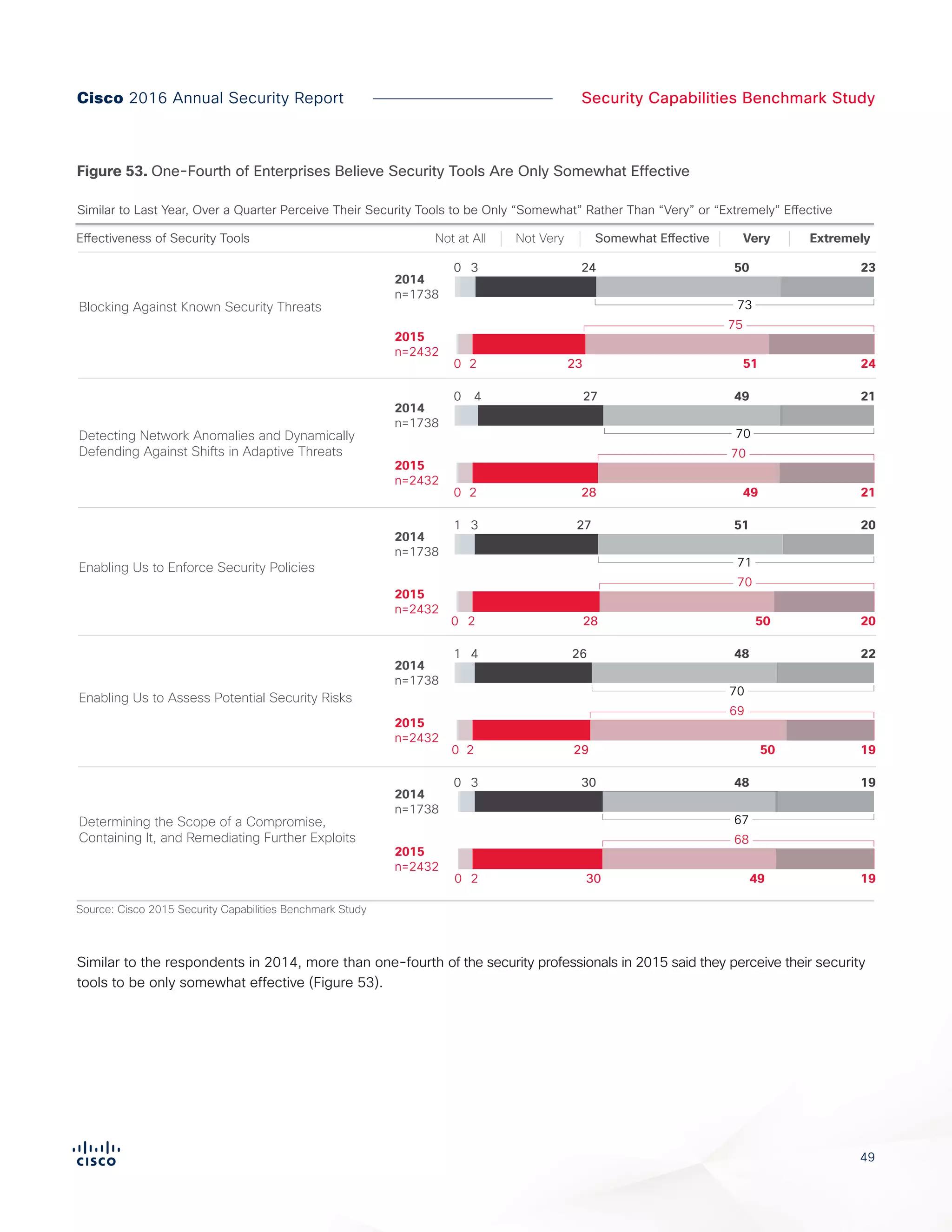
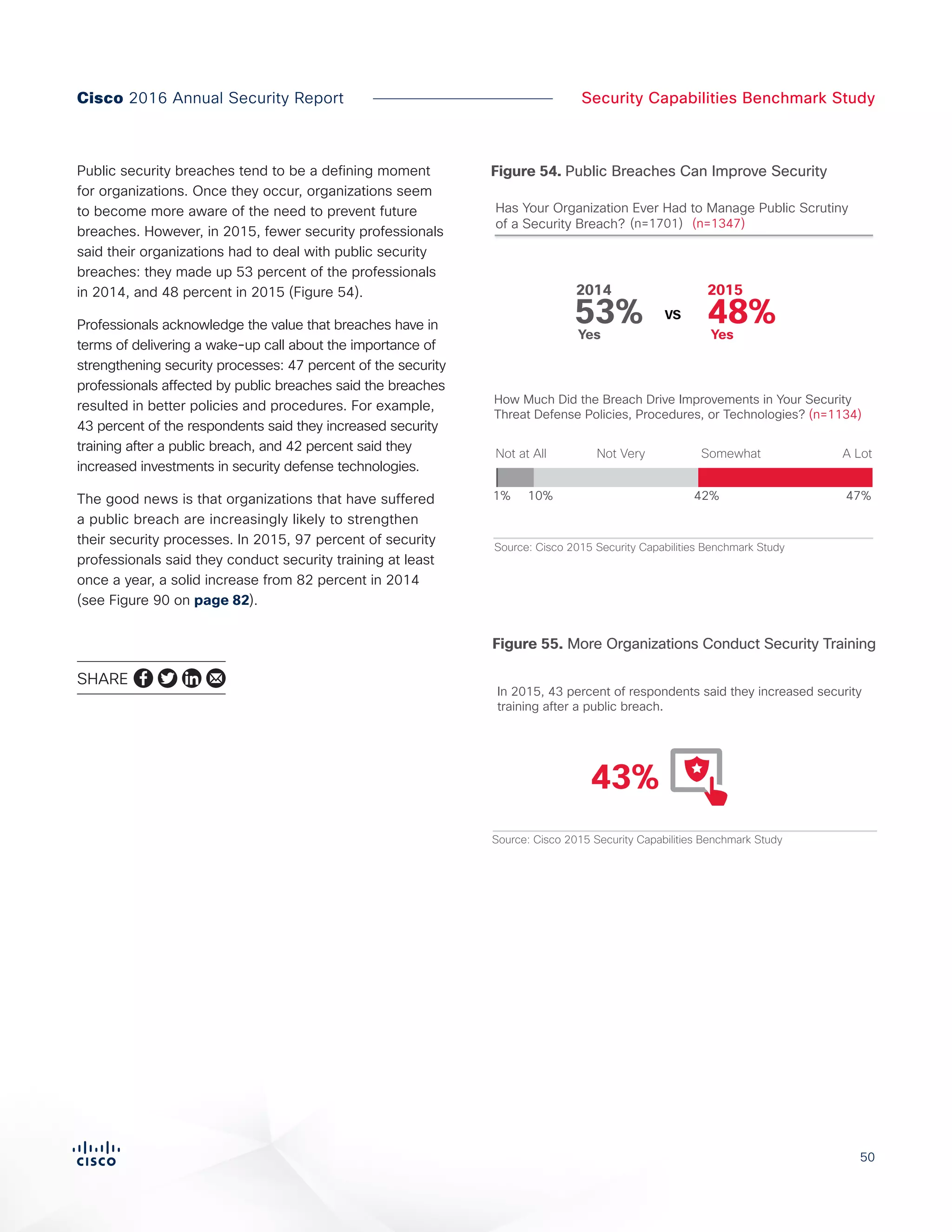
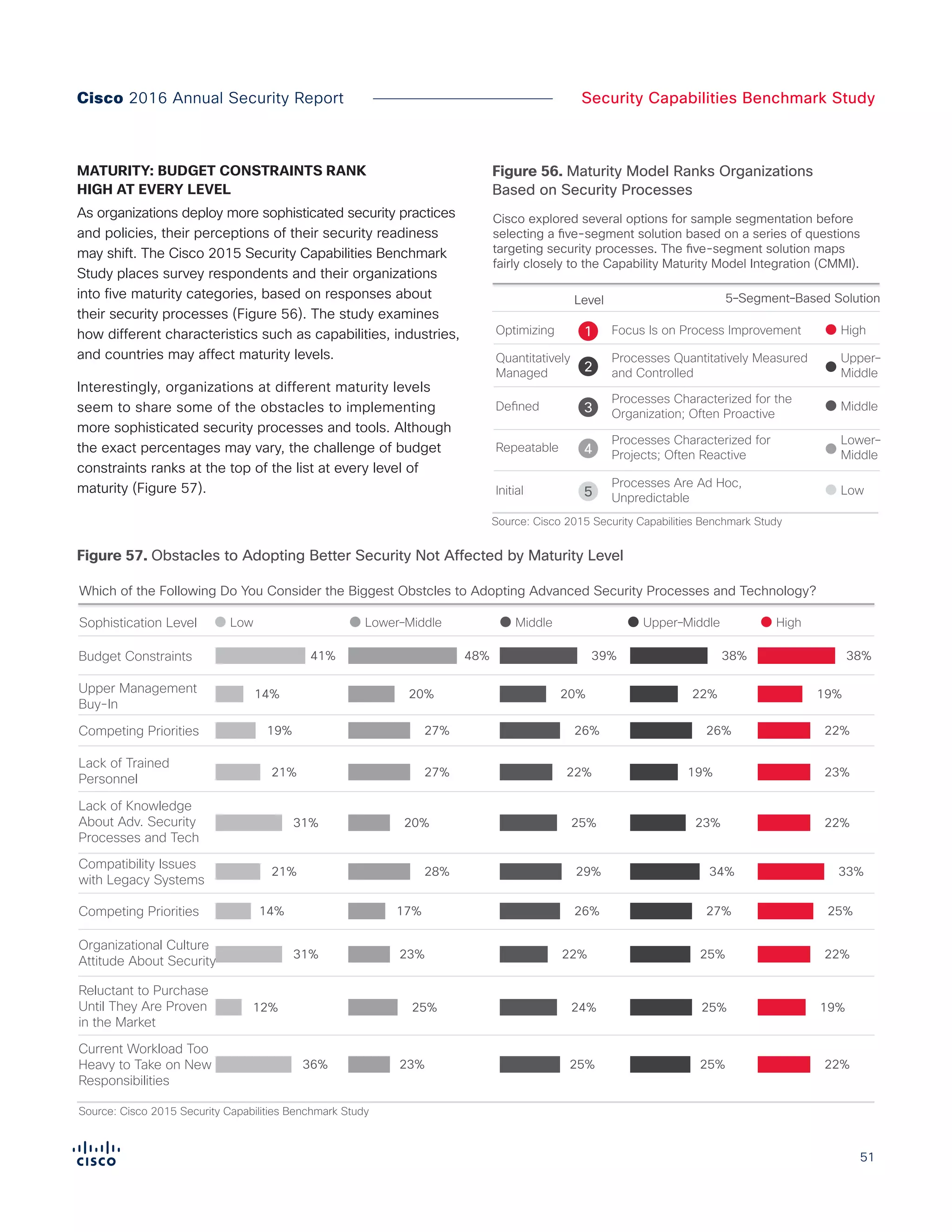
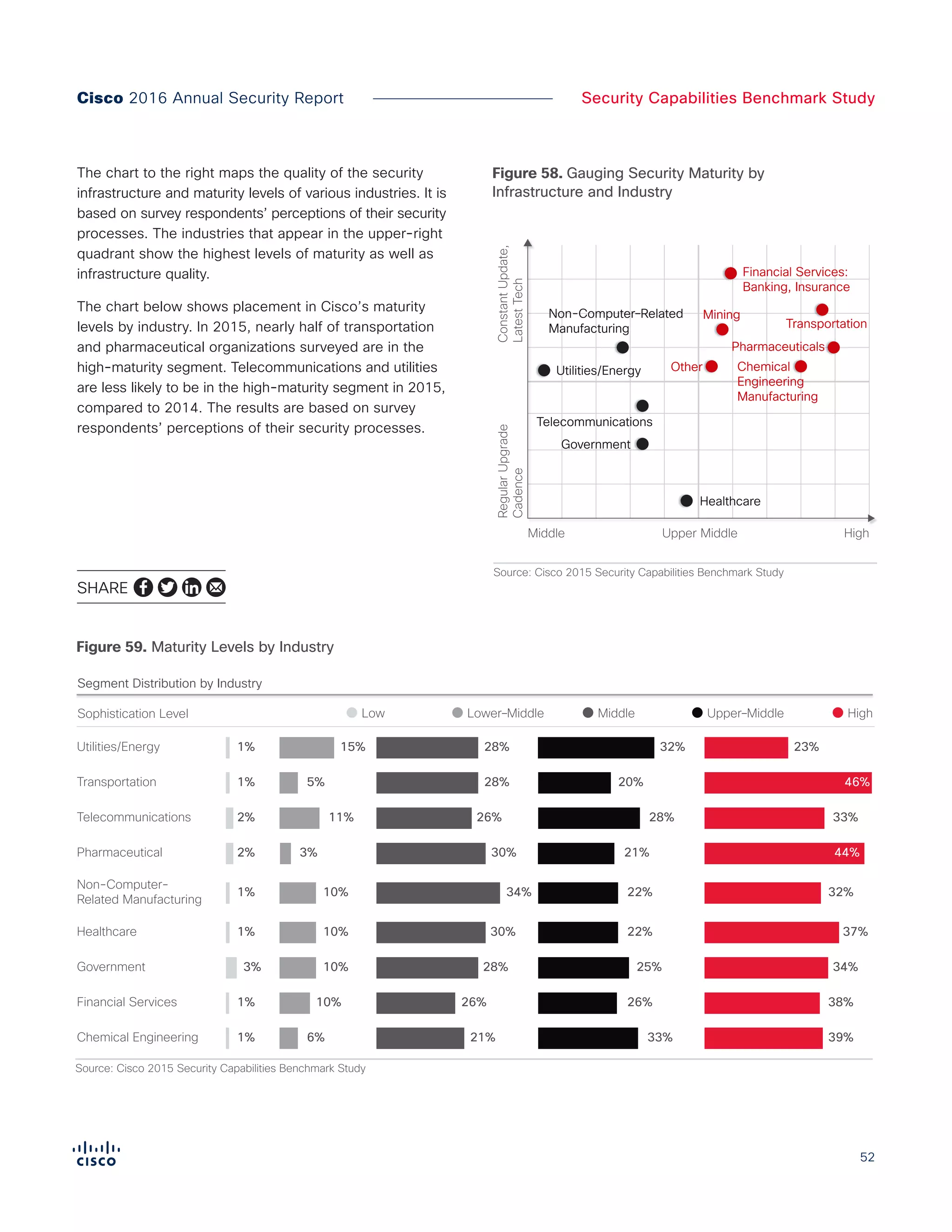
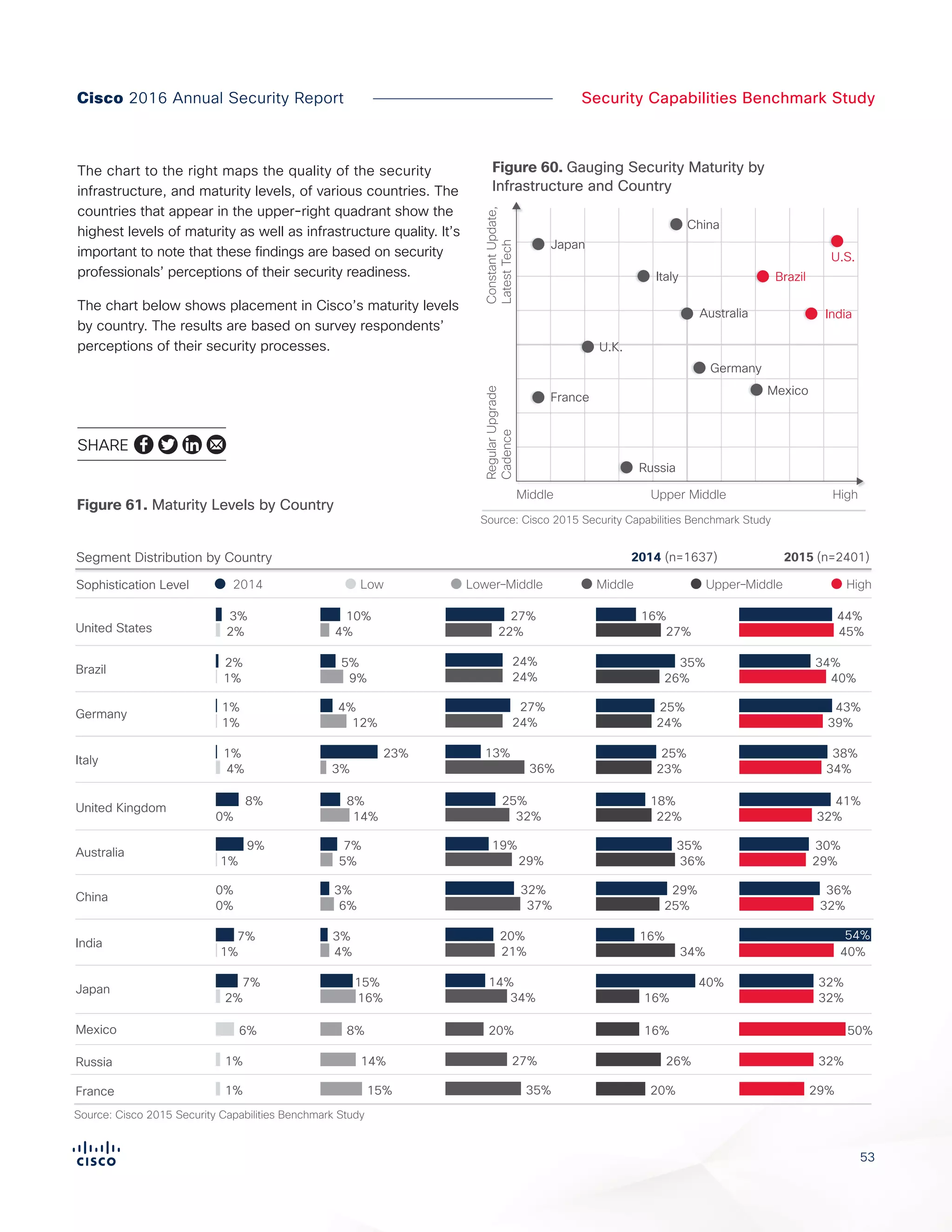
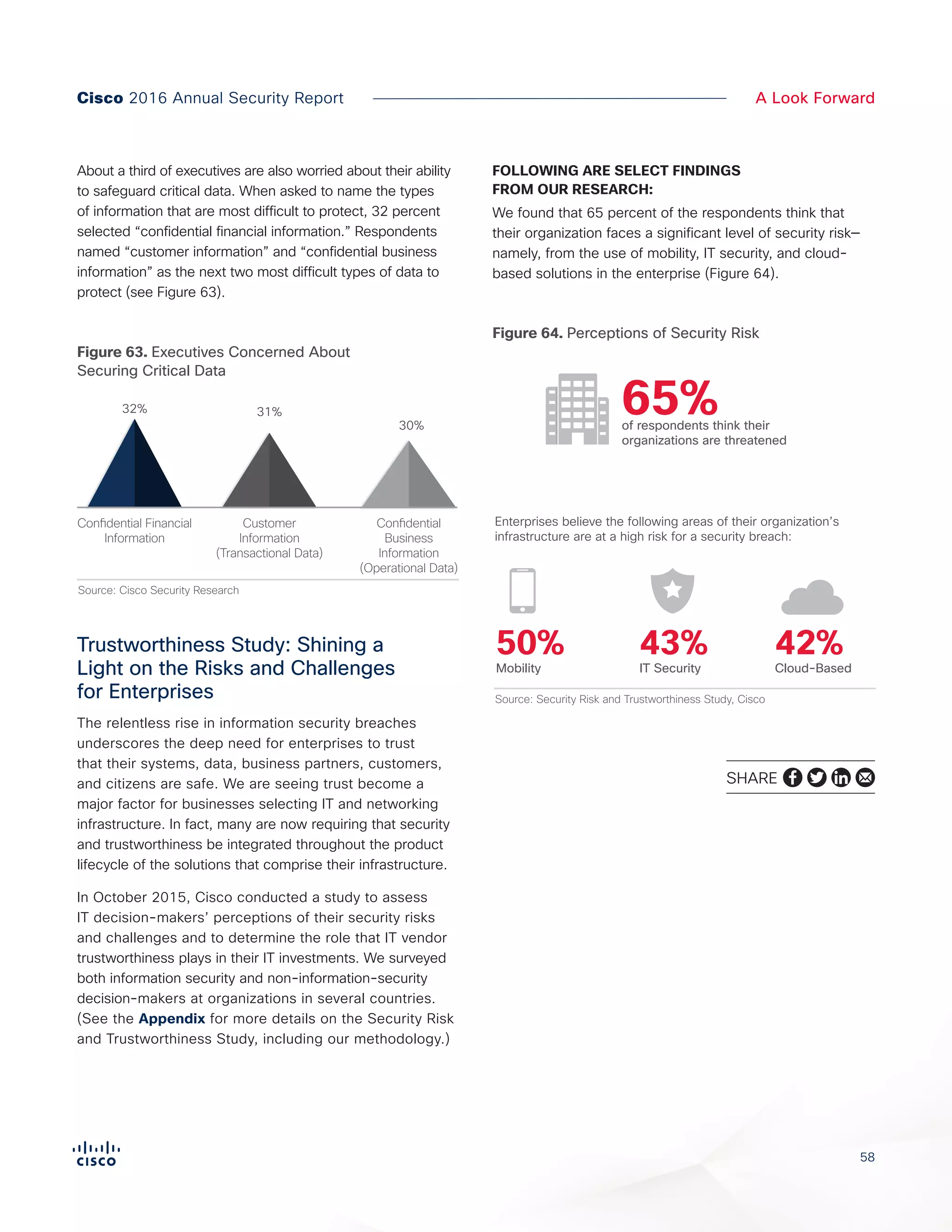
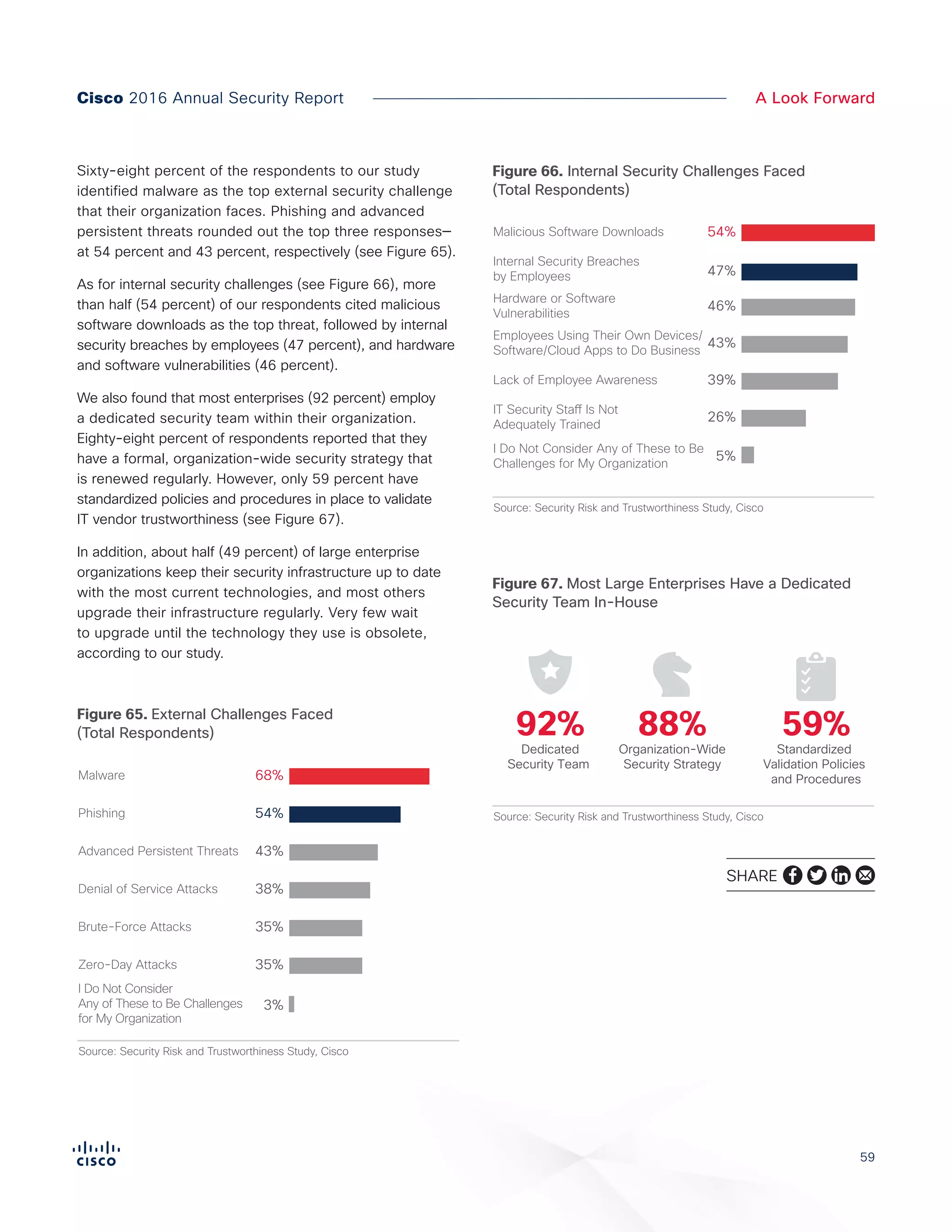
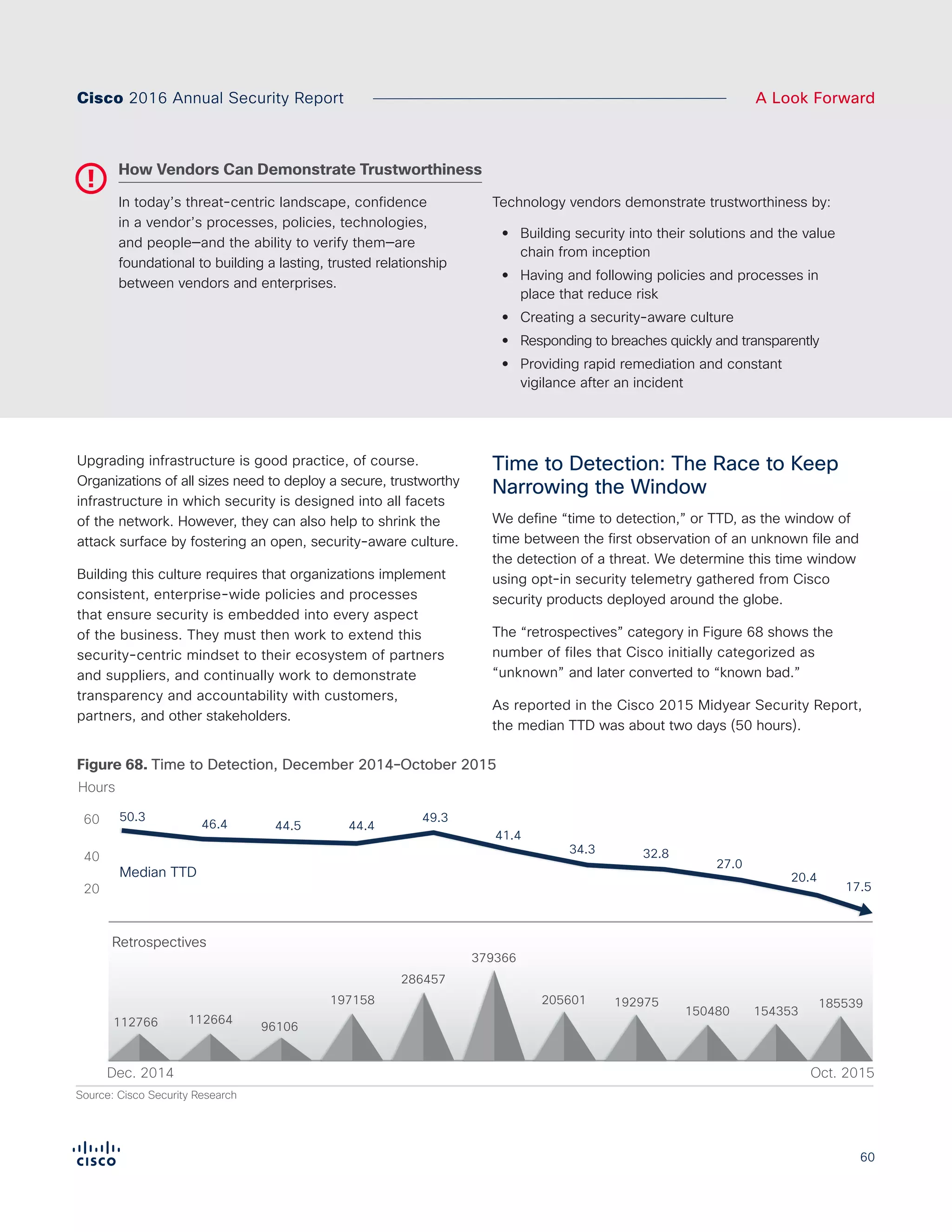
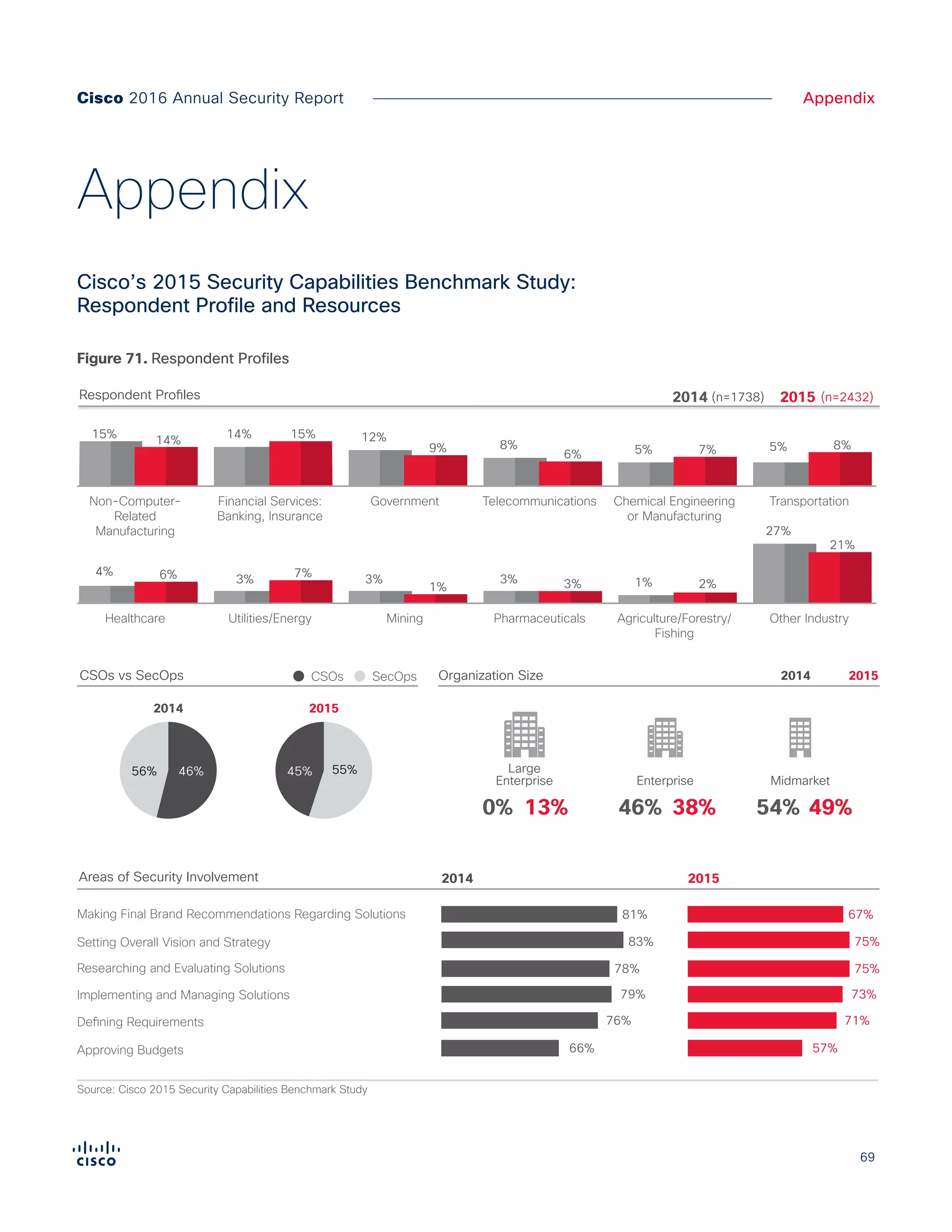
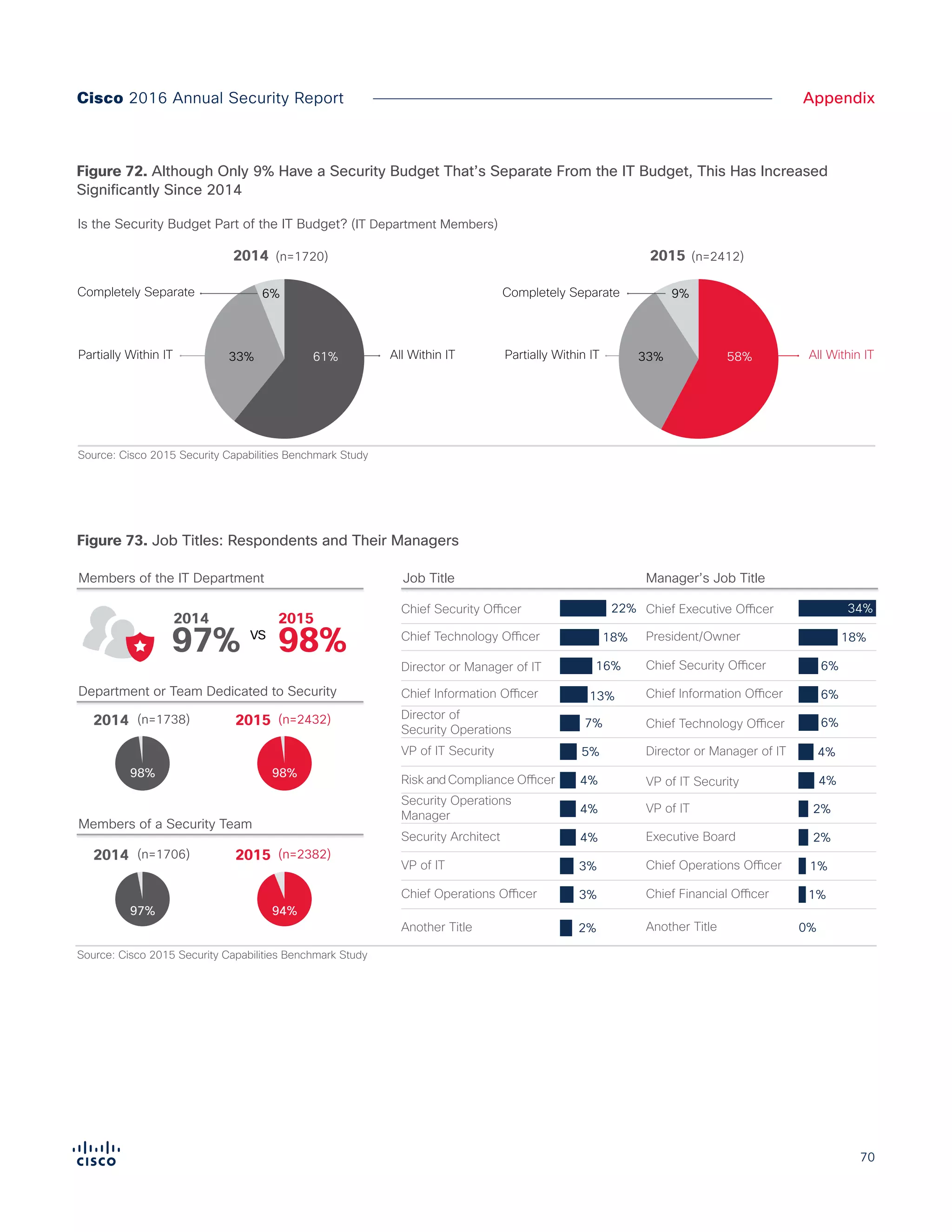
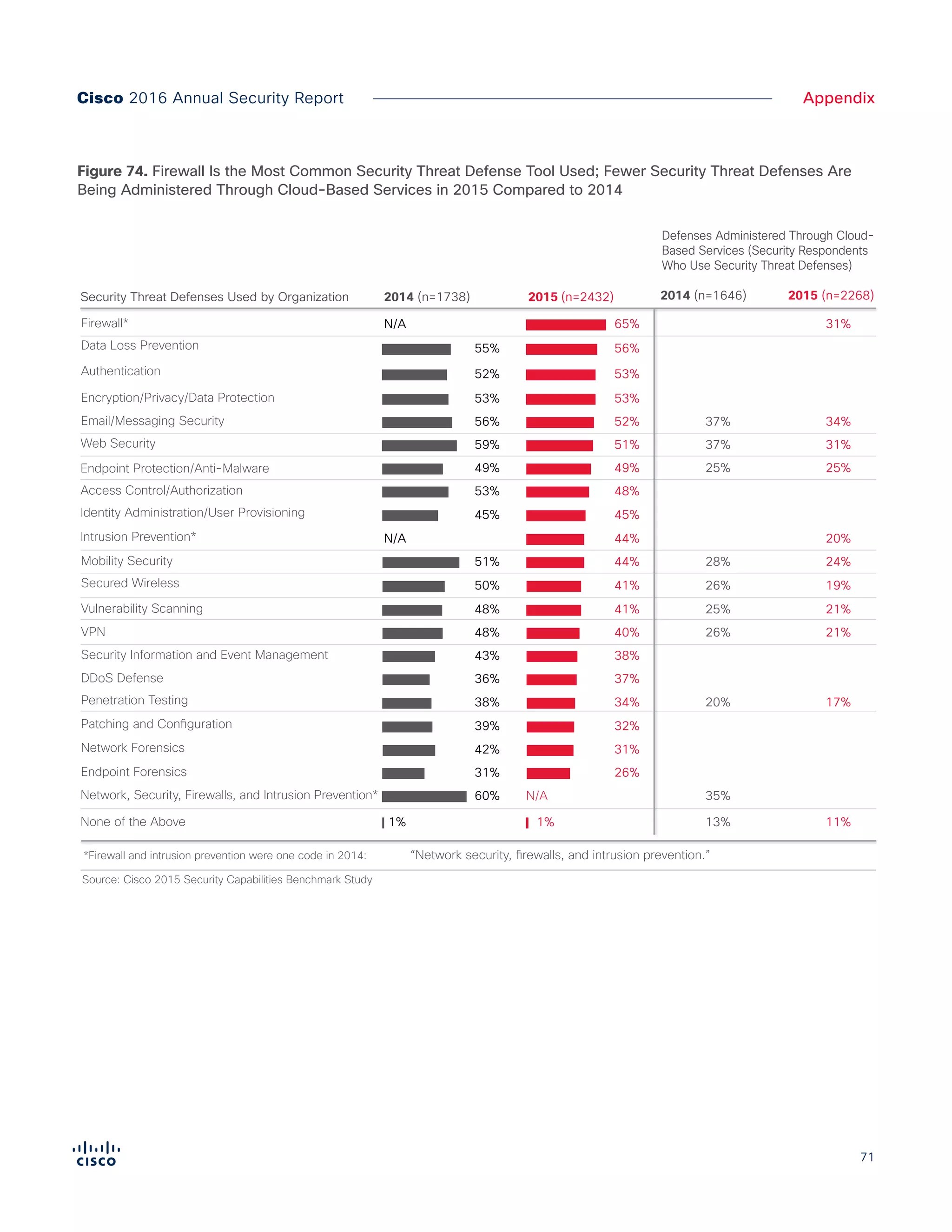
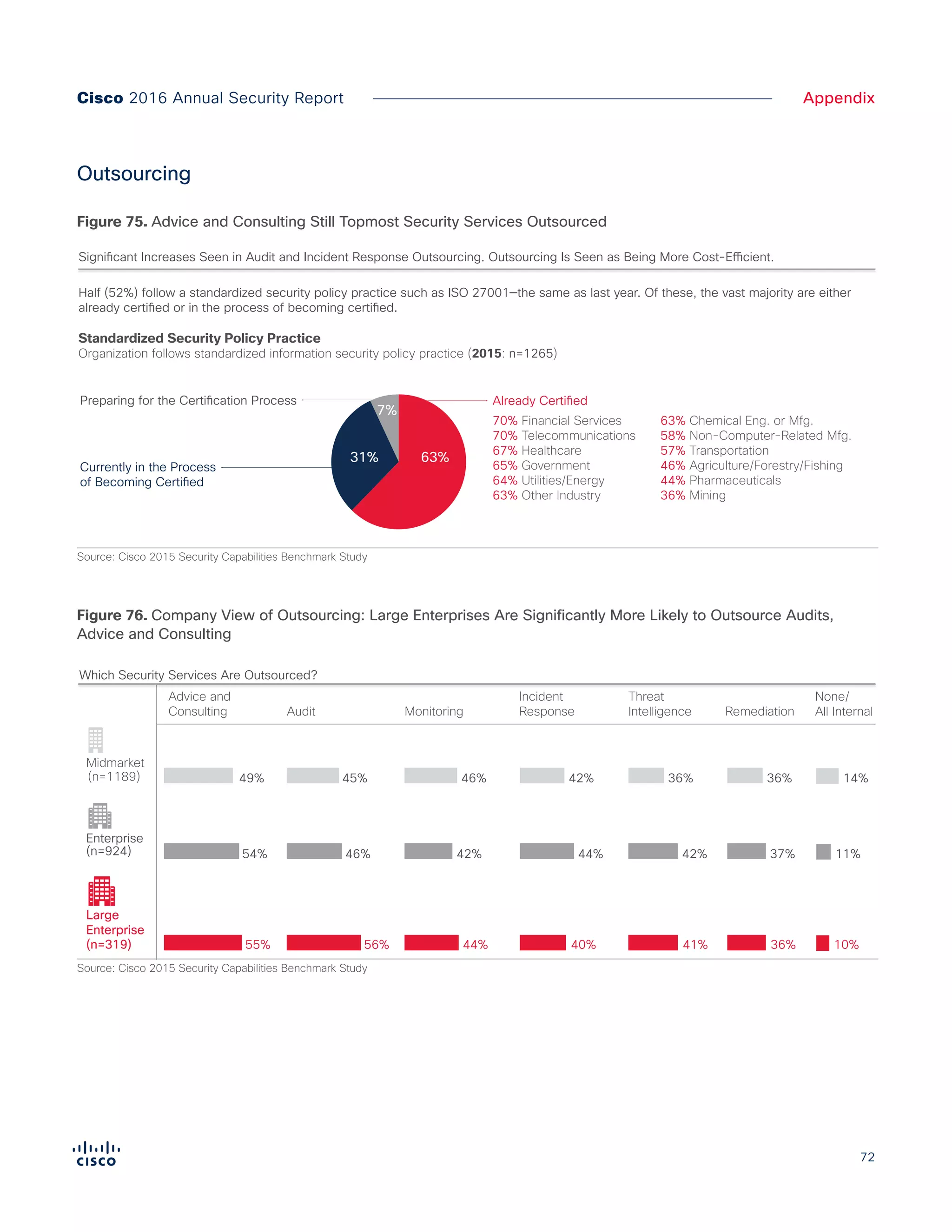
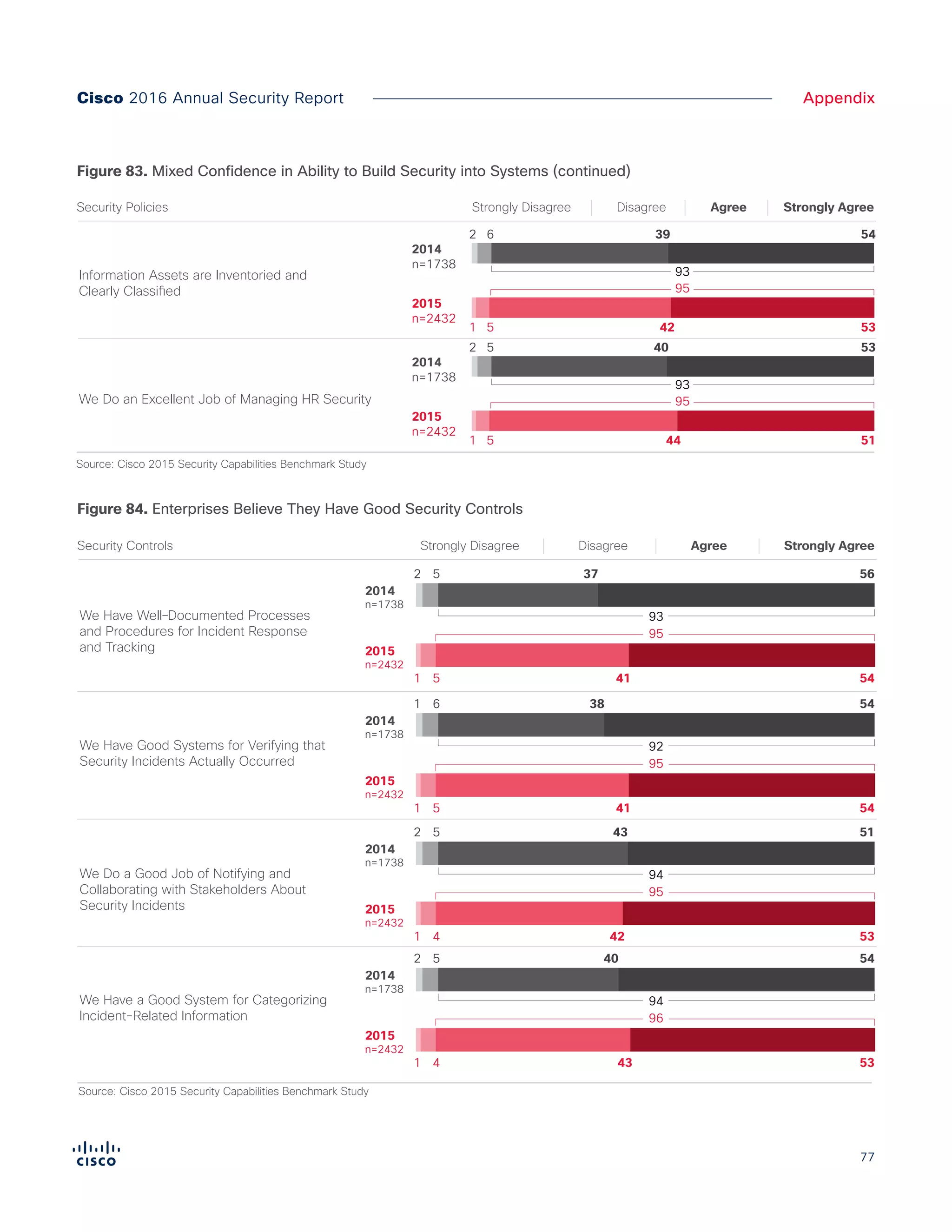
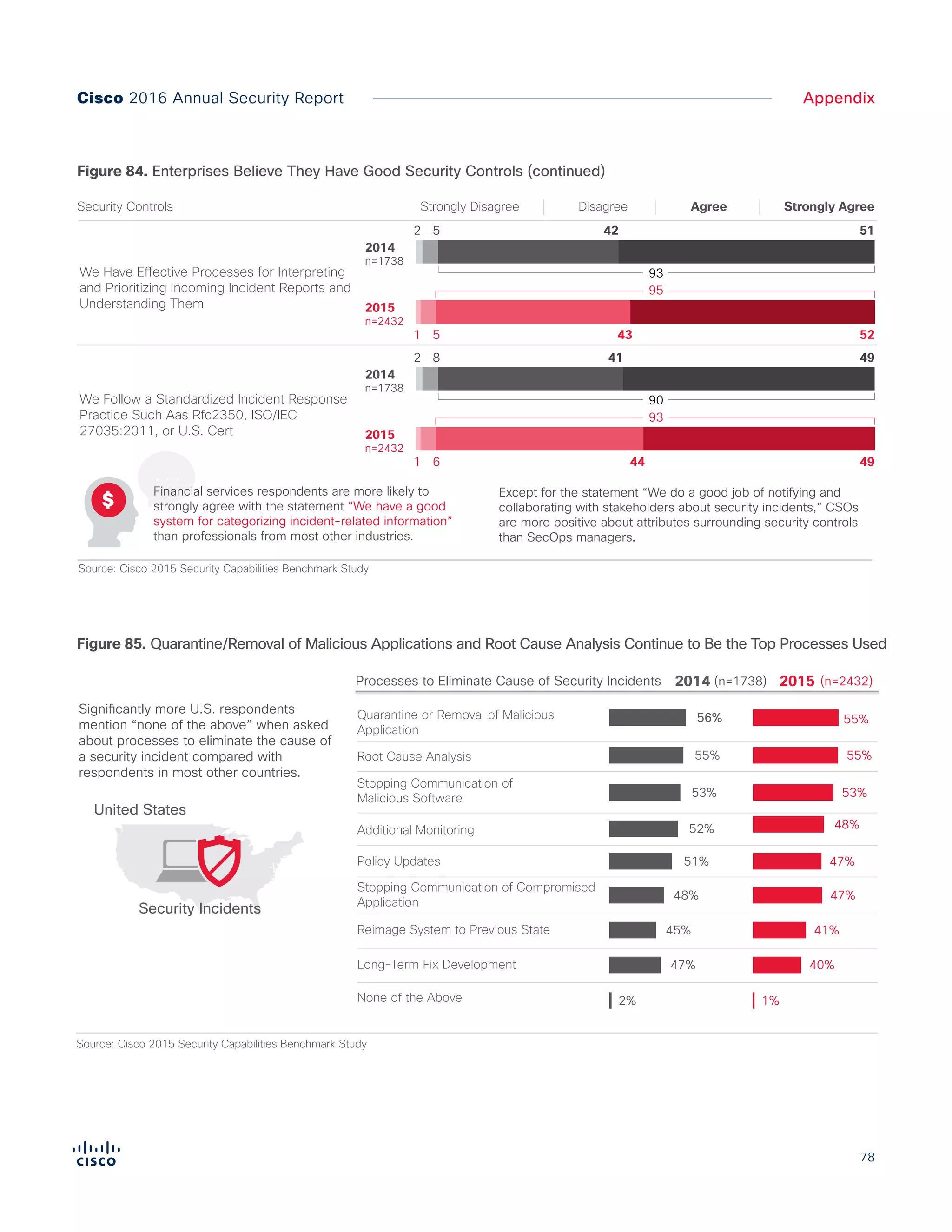
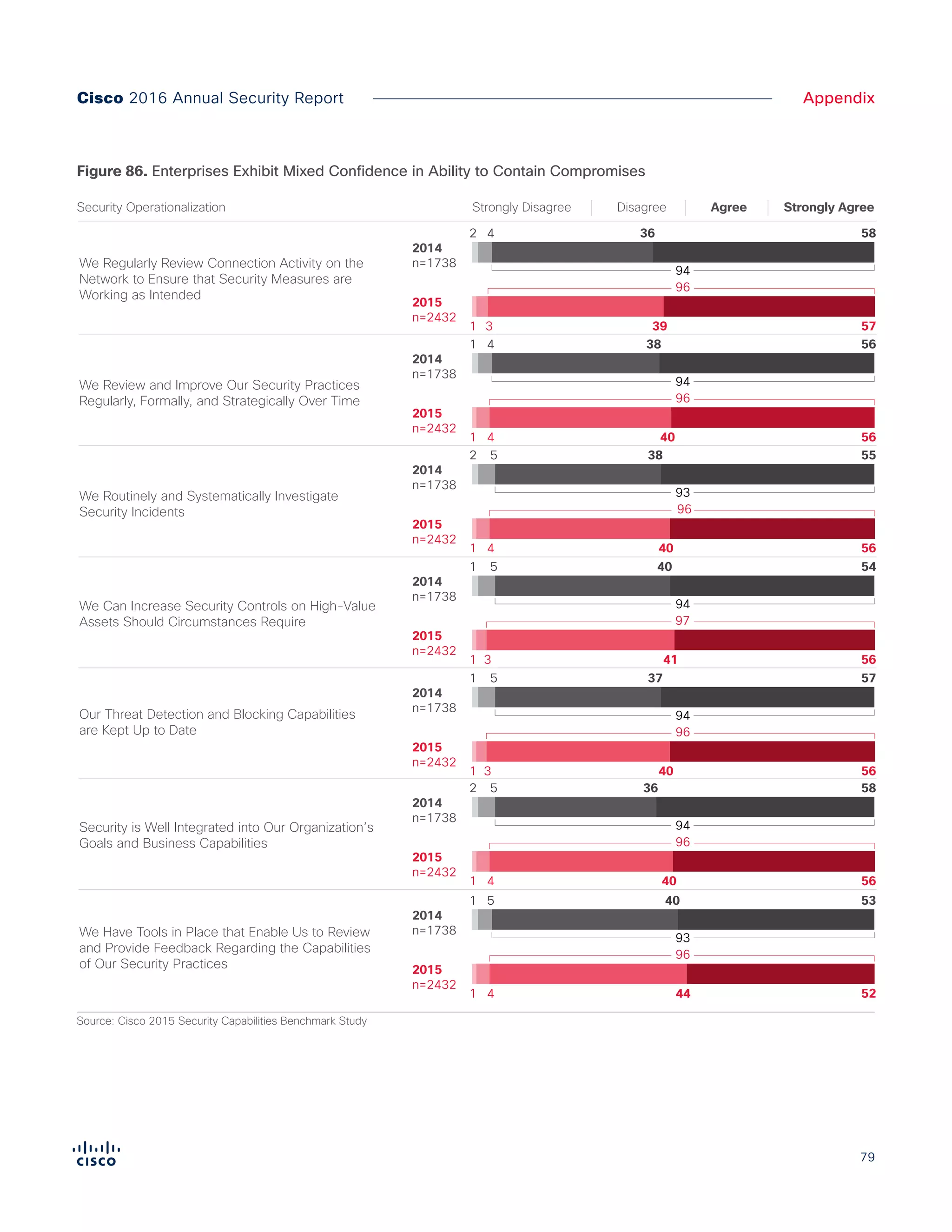
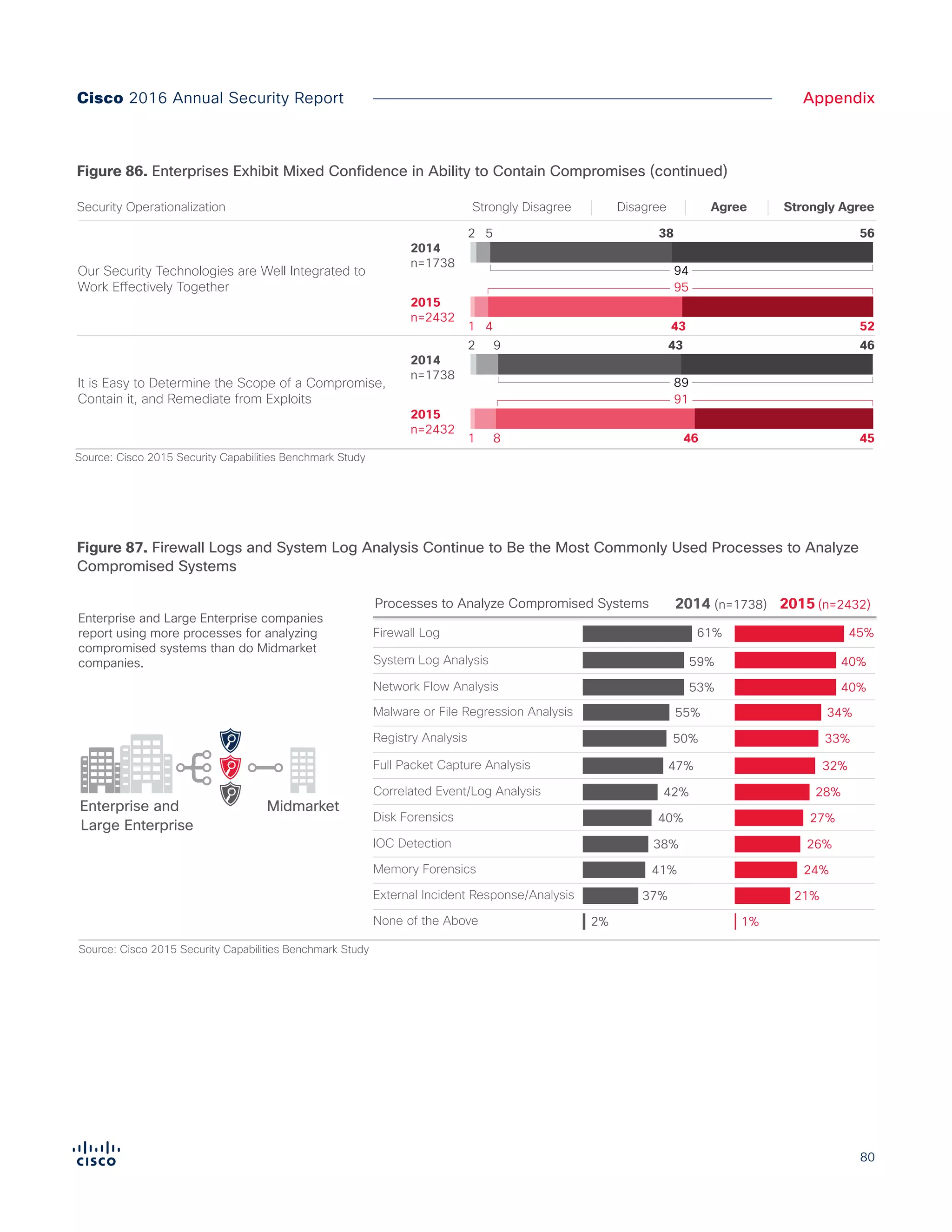
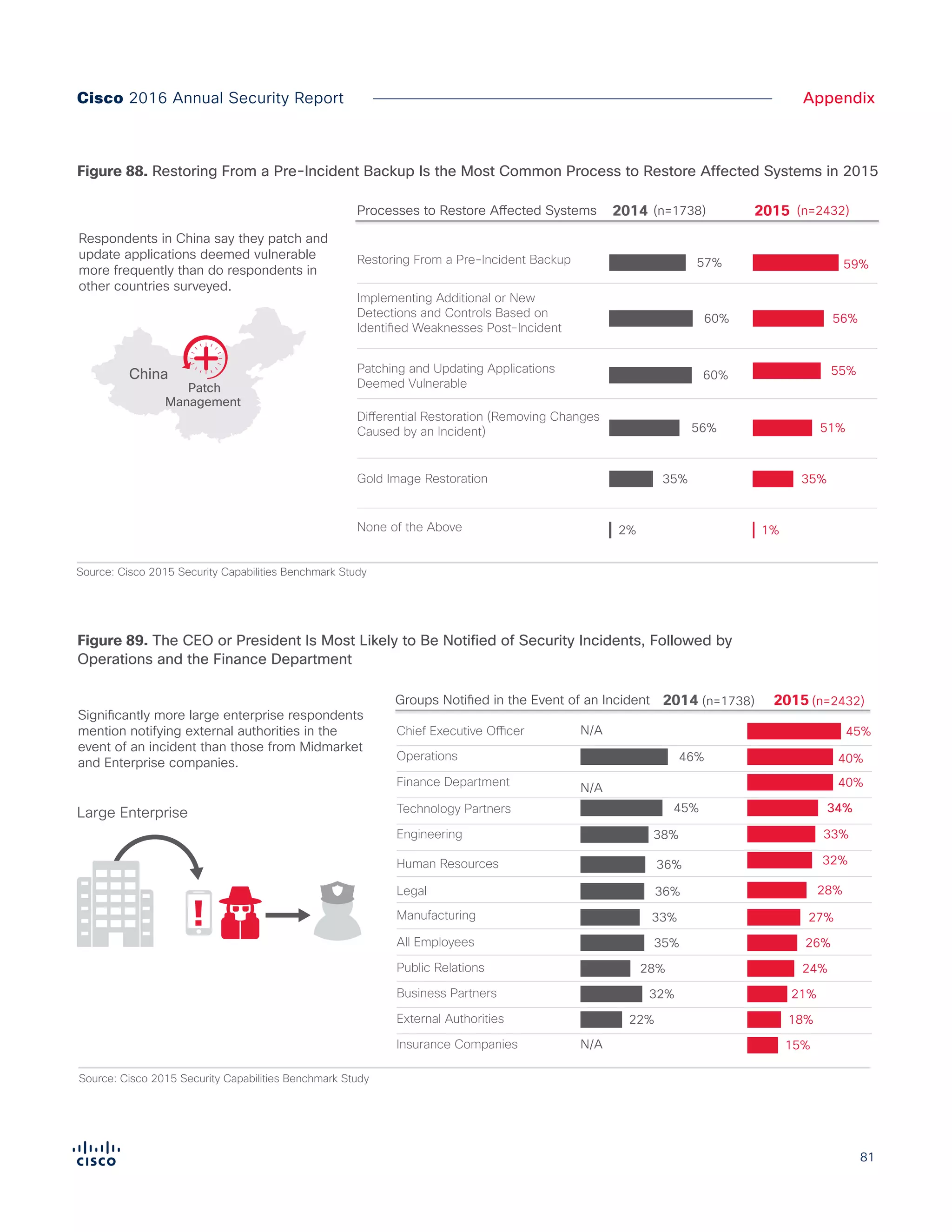
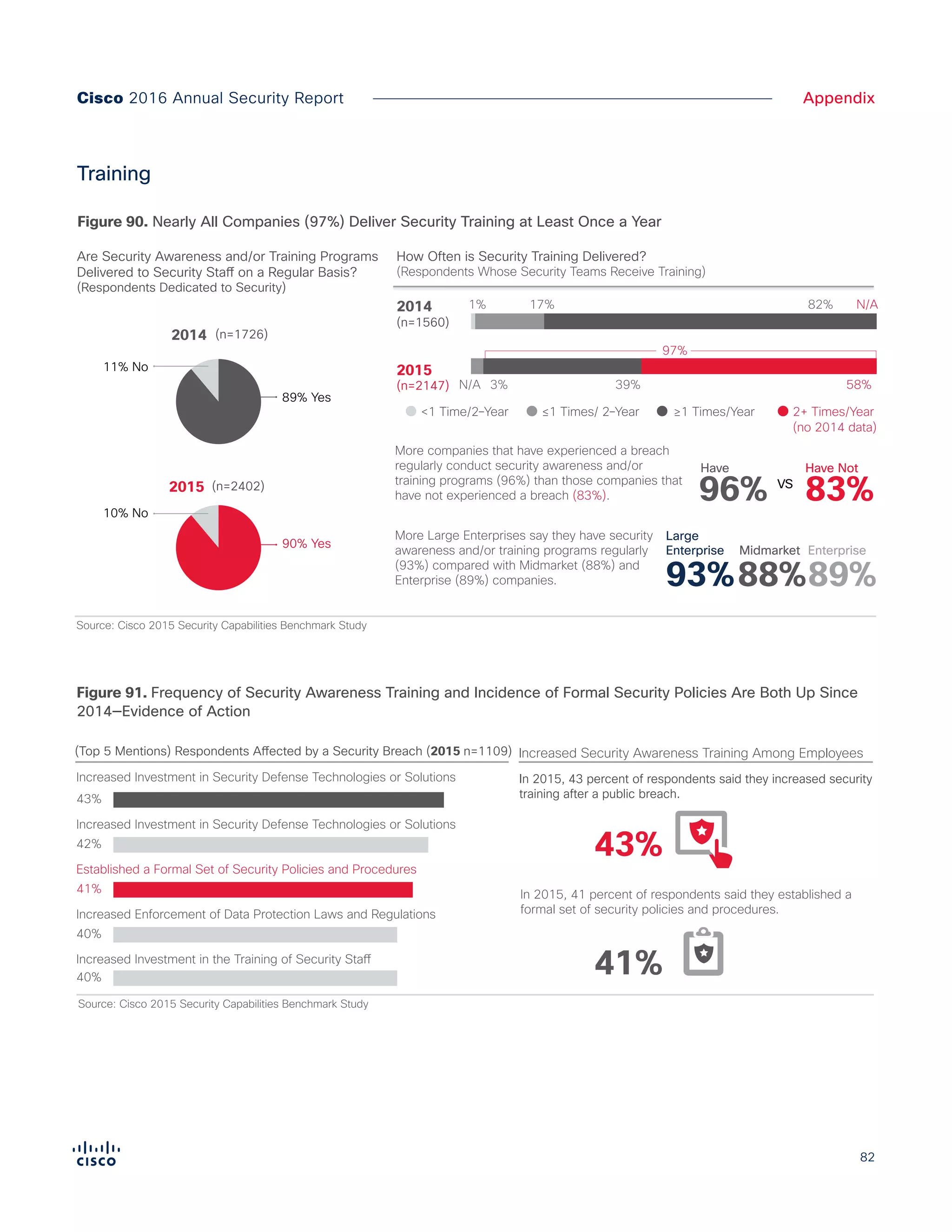
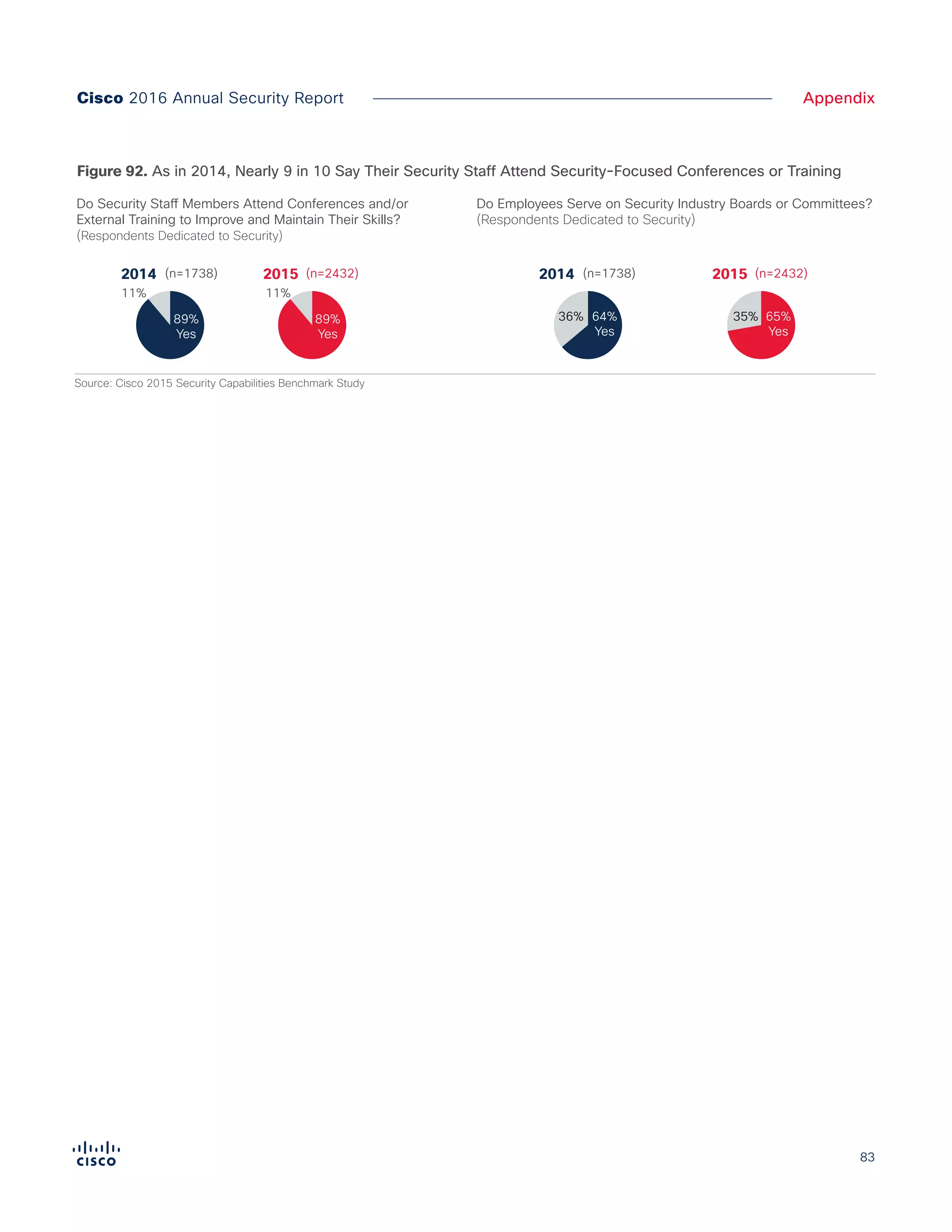
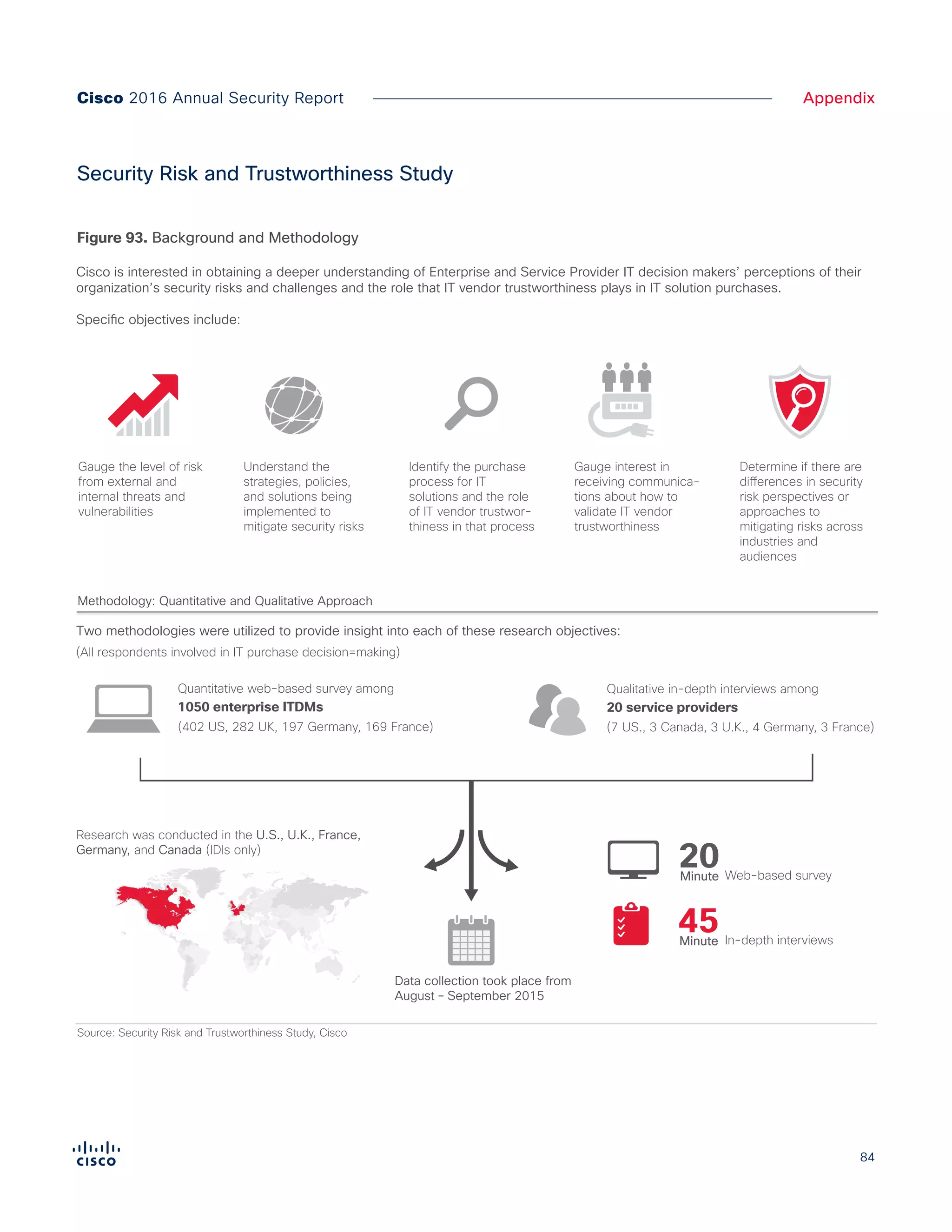
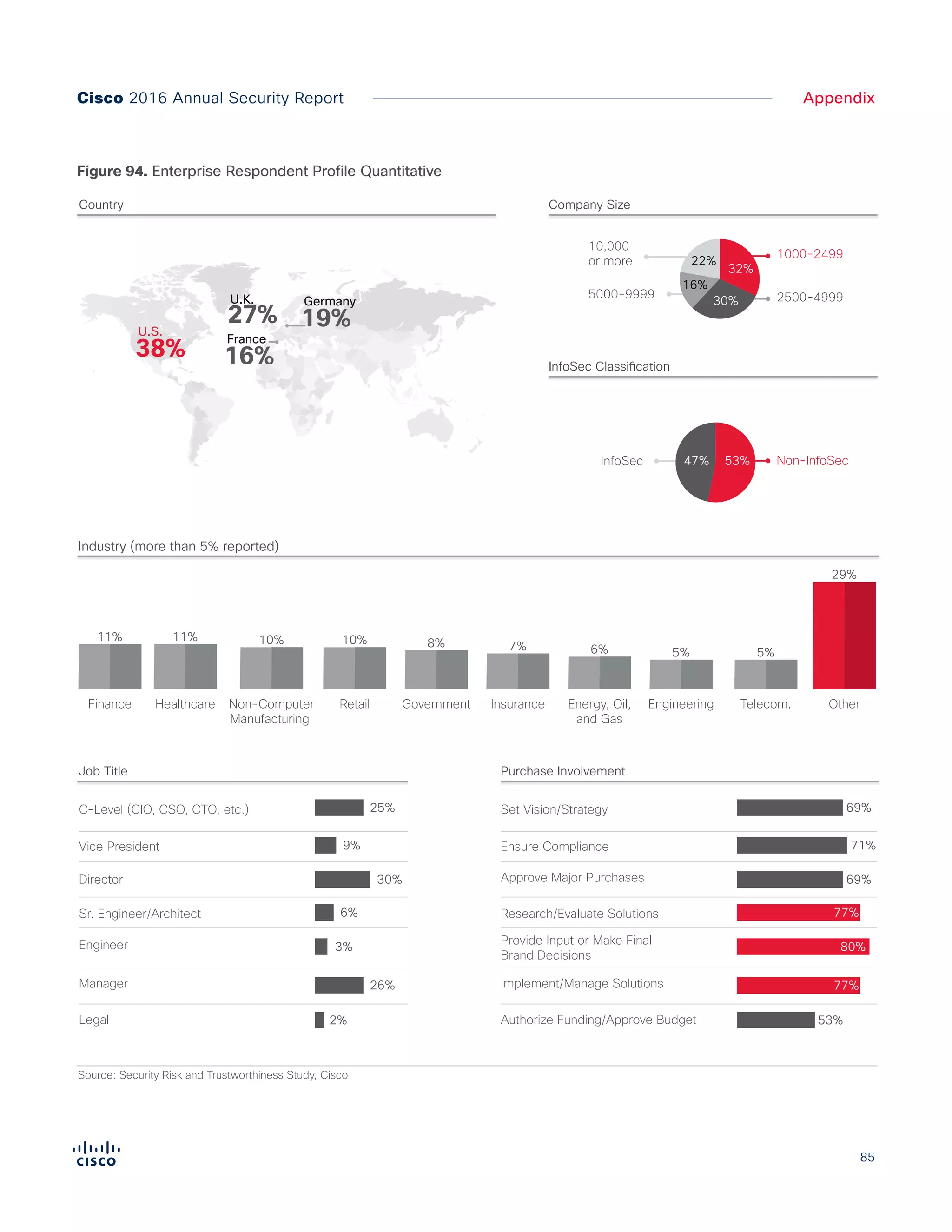
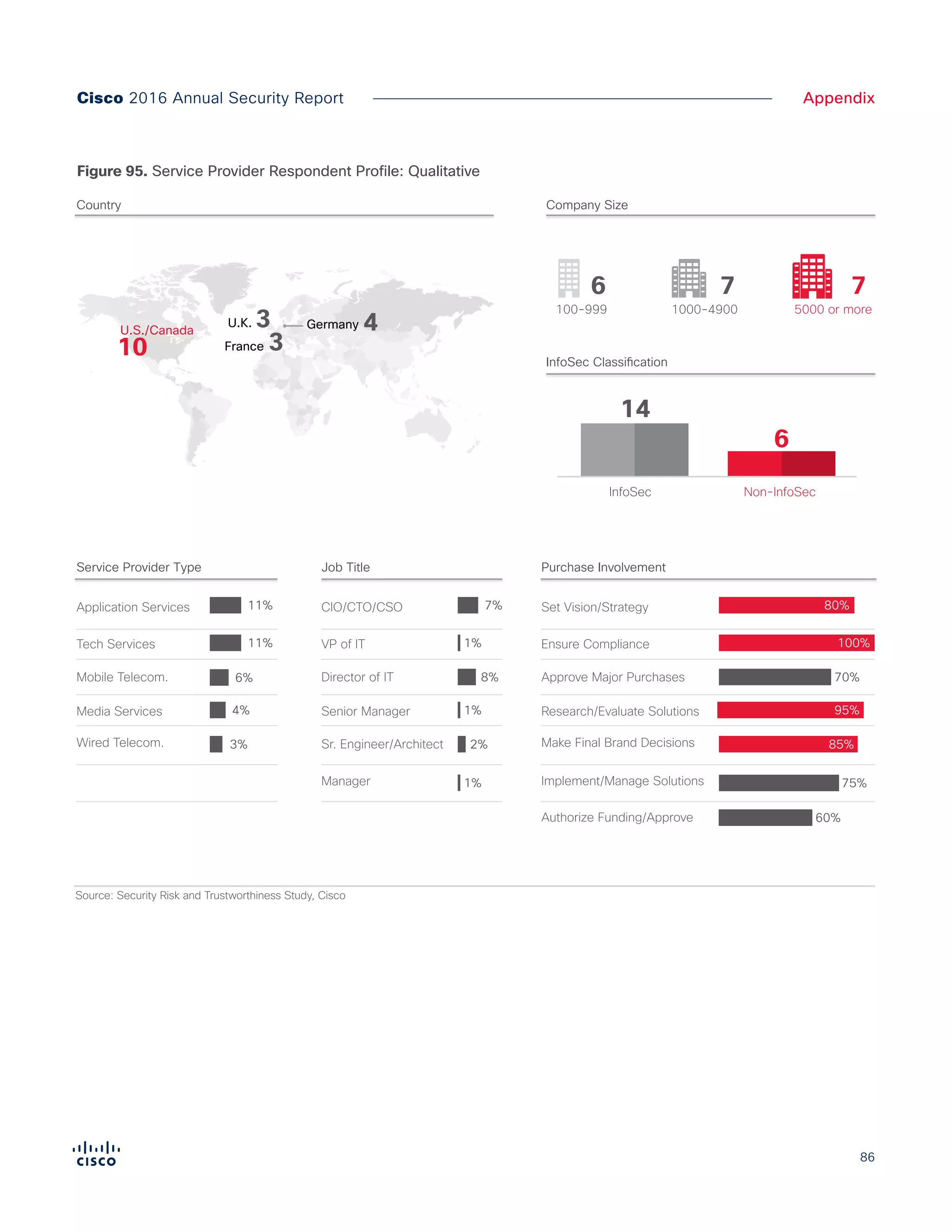
The Cisco 2016 Annual Security Report outlines the evolving threat landscape in cybersecurity, highlighting sophisticated tactics used by cybercriminals to monetize their activities, such as ransomware campaigns. It emphasizes the rising challenges faced by security professionals due to aging infrastructure, declining confidence in security tools, and the use of encryption which complicates threat detection. The report draws from extensive research and collaboration with external experts to provide insights on threat intelligence, industry trends, and security capabilities benchmarking.