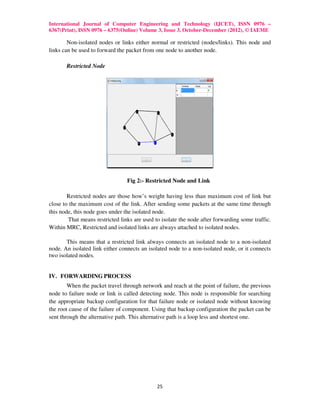
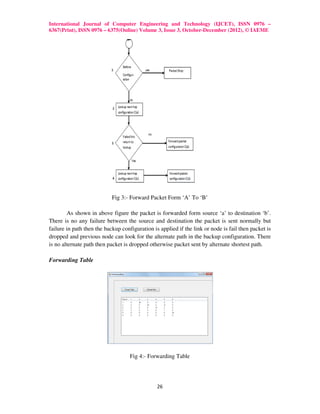
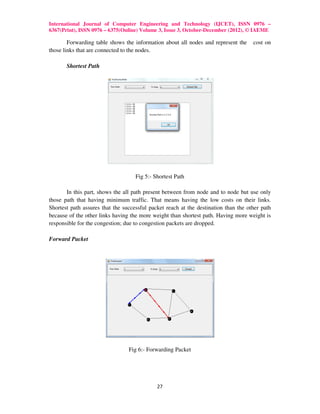
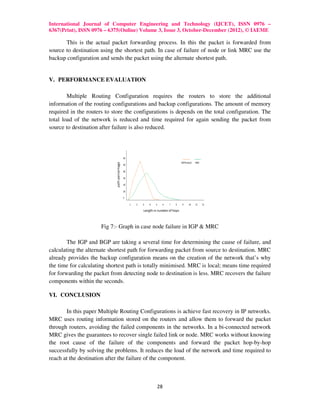
The MRC protocol aims to improve network routing reliability and reduce packet loss during link and node failures. It does so by pre-computing and storing backup routing configurations at each node to allow for fast rerouting onto alternate shortest paths after any failure without needing to determine the root cause. The MRC approach is evaluated to show it can reduce network traffic loads and recovery times compared to standard protocols like IGP and BGP that require more time to detect failures and recalculate routes.


![International Journal of Computer Engineering and Technology (IJCET), ISSN 0976 –
6367(Print), ISSN 0976 – 6375(Online) Volume 3, Issue 3, October-December (2012), © IAEME
REFERENCES
1] Amund Kvalbein, Member, IEEE, Audun Fosselie Hansen, Tarik ˇ Ciˇcic´, Member, IEEE,
Stein Gjessing, Member, IEEE, and Olav Lysne, Member, IEEE
2] A. Basu and J. G. Riecke, “Stability issues in OSPF routing,” in Proc. ACM SIGCOMM,
San Diego, CA, Aug. 2001, pp. 225–236.
3] A. Markopoulou, G. Iannaccone, S. Bhattacharyya, C.-N. Chuah, and C. Diot,
“Characterization of failures in an IP backbone network,” in Proc. IEEE INFOCOM, Mar.
2004, vol. 4, pp. 2307–2317.
4] S. Nelakuditi, S. Lee, Y. Yu, Z.-L. Zhang, and C.-N. Chuah, “Fast local rerouting for
handling transient link failures,” IEEE/ACM Trans. Networking, vol. 15, no. 2, pp. 359–372,
Apr. 2007.
5] P. Francois, M. Shand, and O. Bonaventure, “Disruption free topology reconfiguration in
OSPF networks,” in Proc. IEEE INFOCOM, Anchorage, AK, May 2007, pp. 89–97
6] P. Francois, C. Filsfils, J. Evans, and O. Bonaventure, “Achieving sub-second IGP
convergence in large IP networks,” ACM SIGCOMM Comput. Commun. Rev., vol. 35, no. 2,
pp. 35–44, Jul. 2005.
7] A. Markopoulou, G. Iannaccone, S. Bhattacharyya, C.-N. Chuah, and C. Diot,
“Characterization of failures in an IP backbone network,” in Proc. IEEE INFOCOM, Mar.
2004, vol. 4, pp. 2307–2317.
29](https://image.slidesharecdn.com/multipleroutingconfiguration-121218003533-phpapp02/85/Multiple-routing-configuration-7-320.jpg)