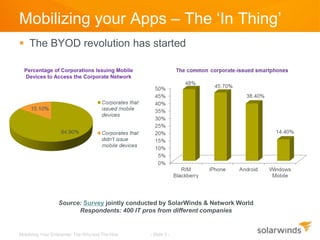
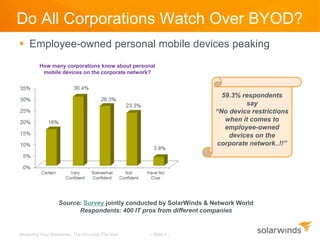
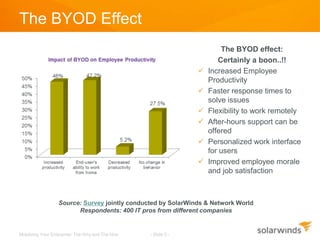
The document discusses the mobilization of enterprise applications, highlighting the rise of BYOD (Bring Your Own Device) and its implications for productivity and security. It outlines best practices for providing mobile access, such as encryption and authentication, while addressing potential security risks like data loss and malware threats. Additionally, it mentions how Solarwinds Mobile Admin can assist IT professionals in managing and resolving IT issues through mobile devices.