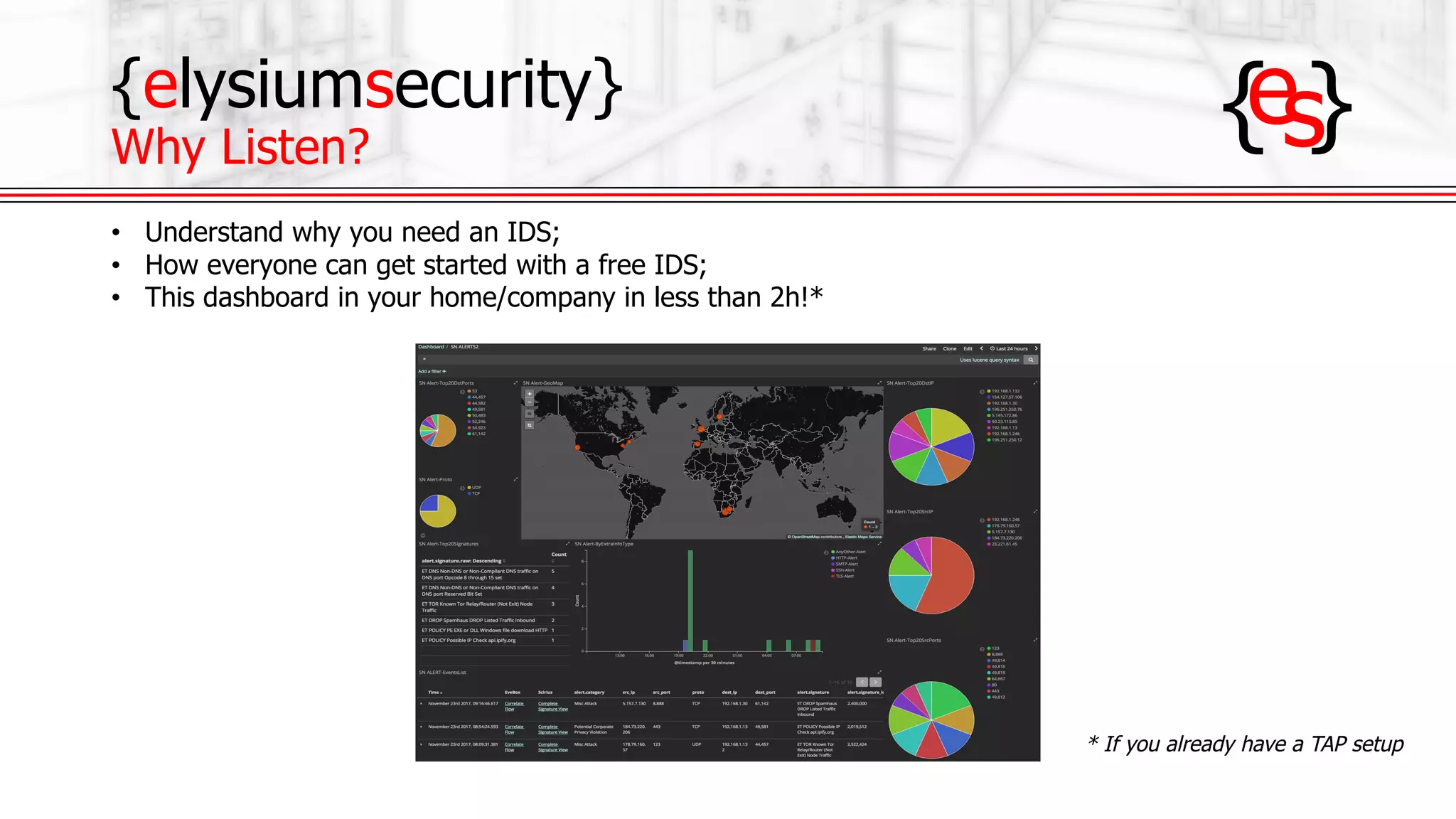
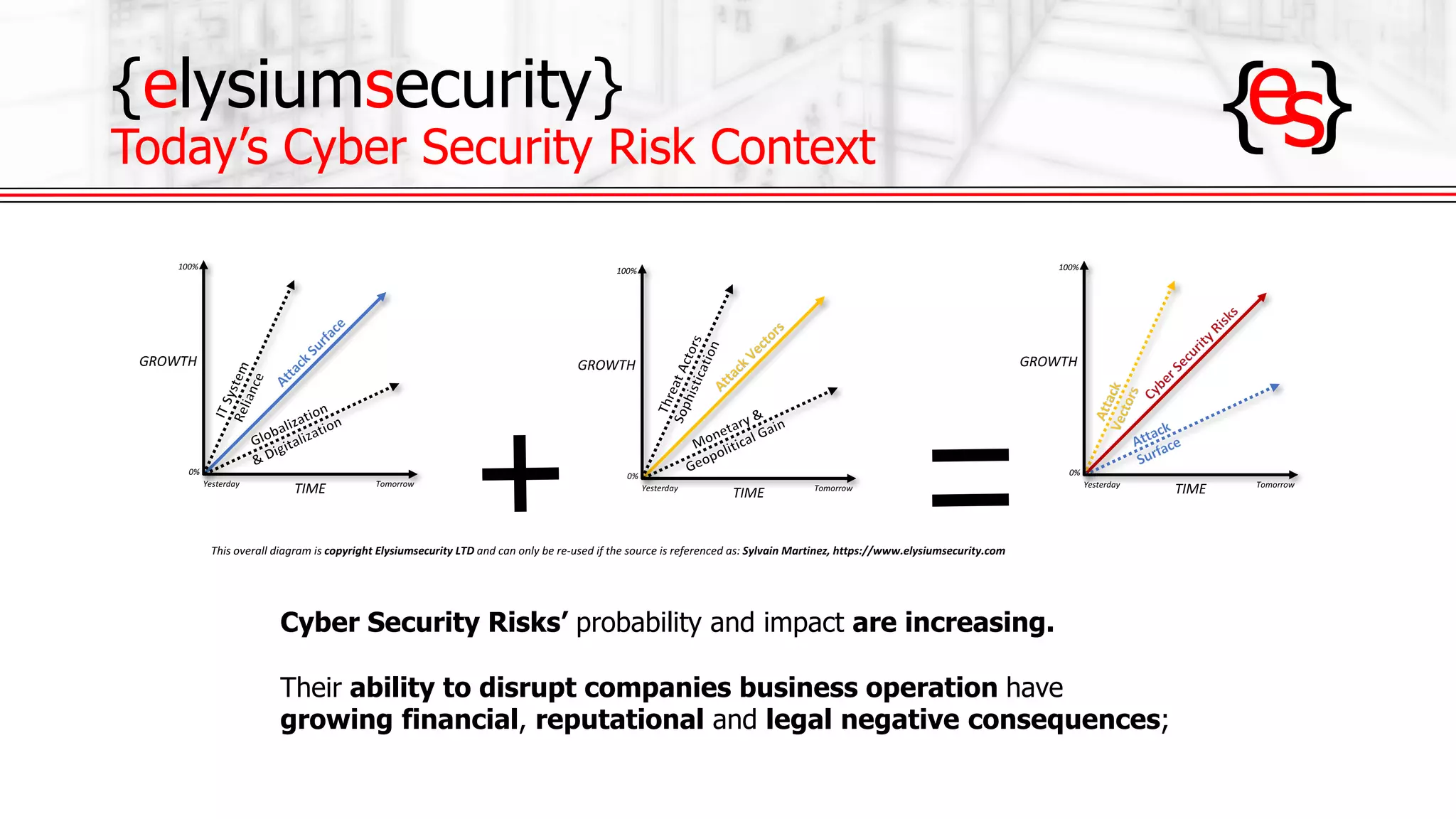
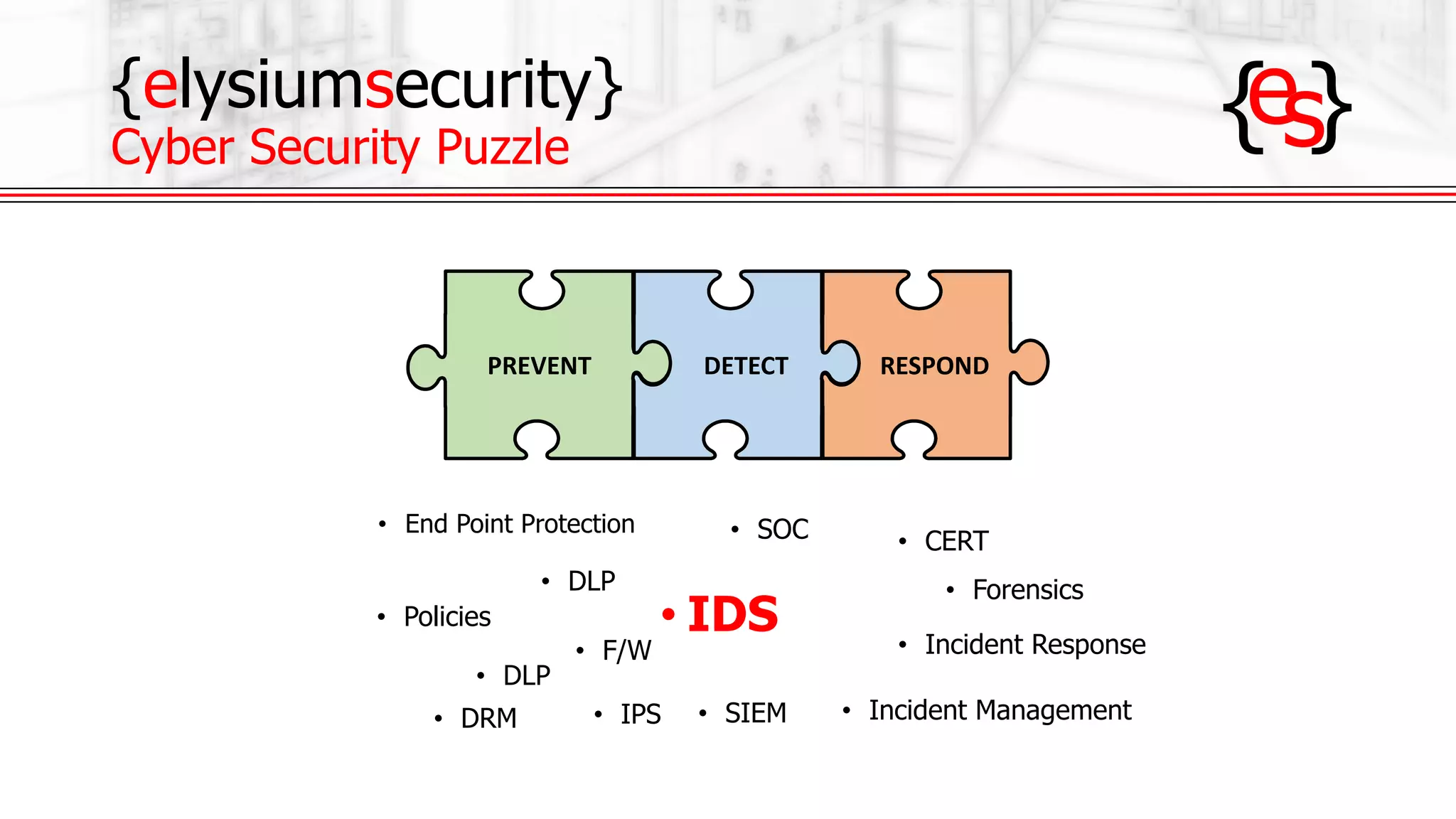
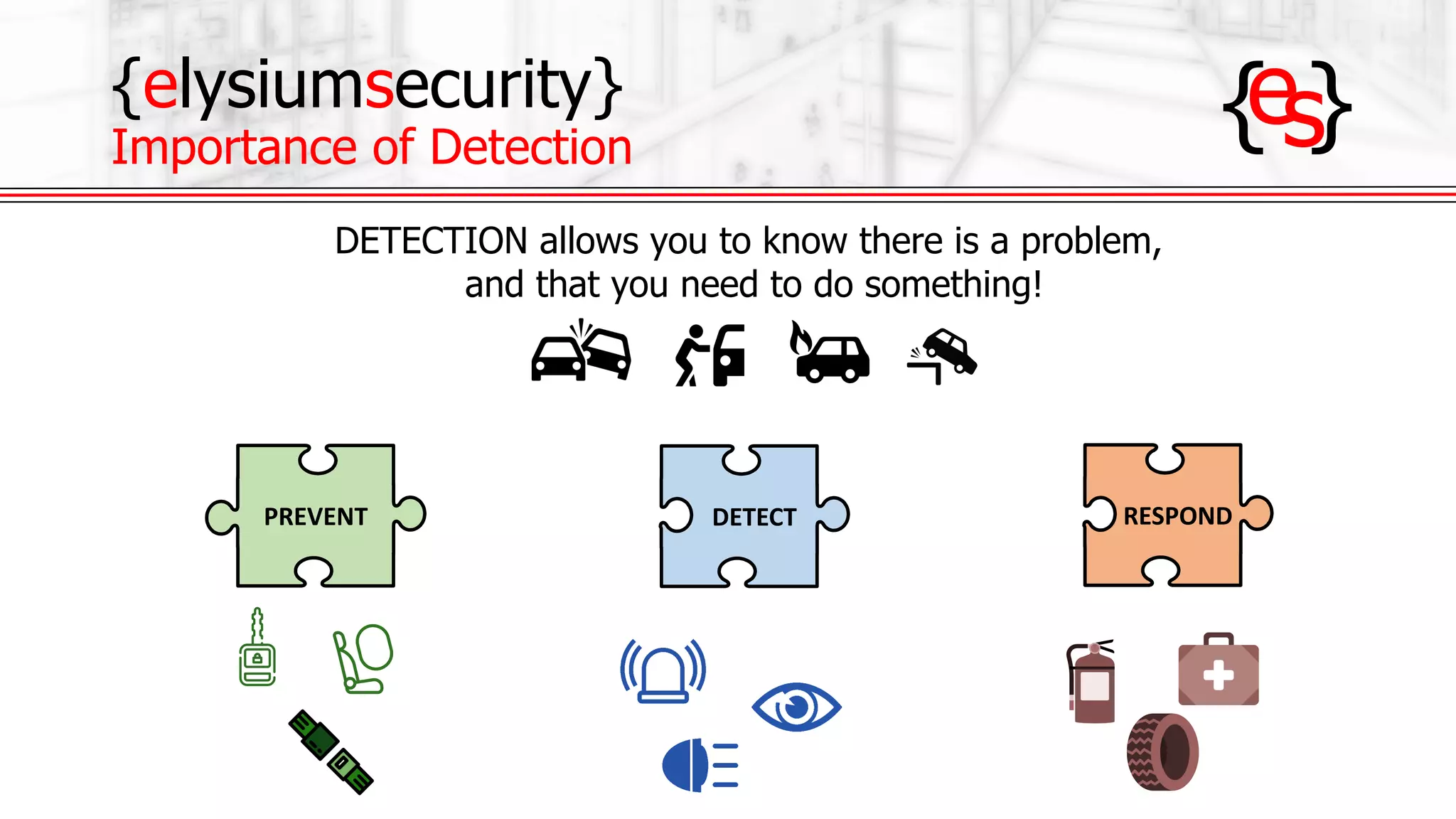
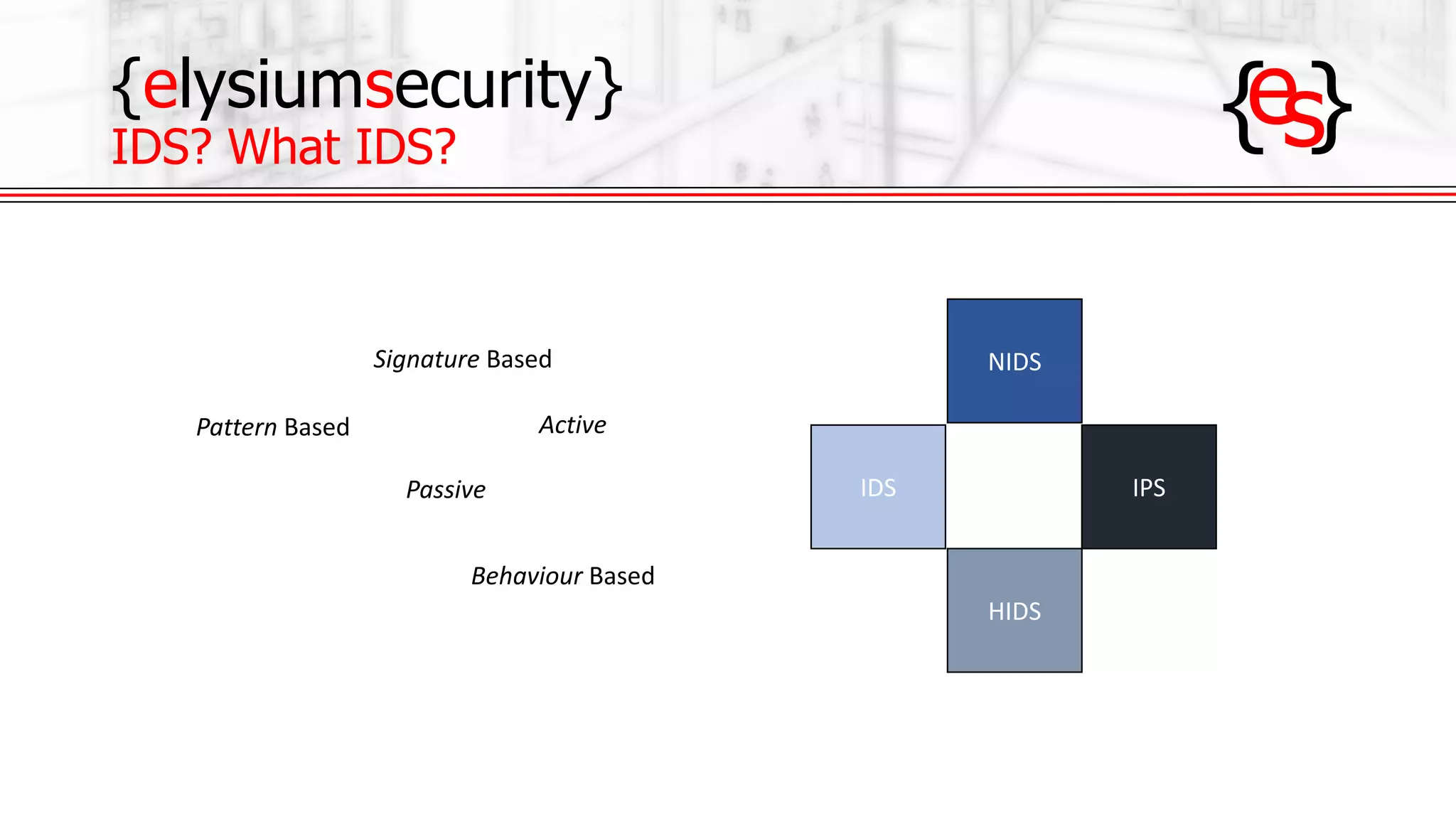
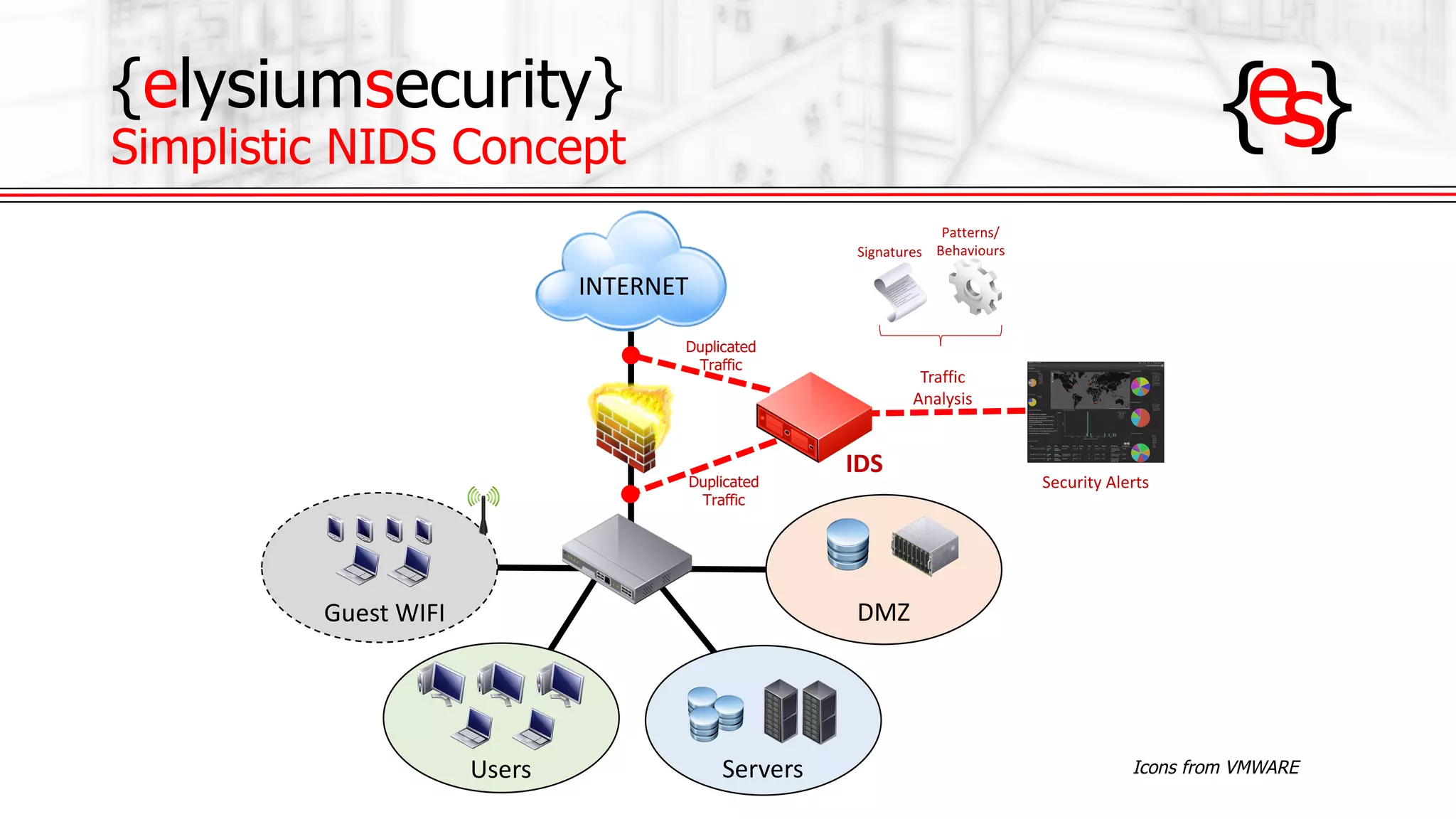
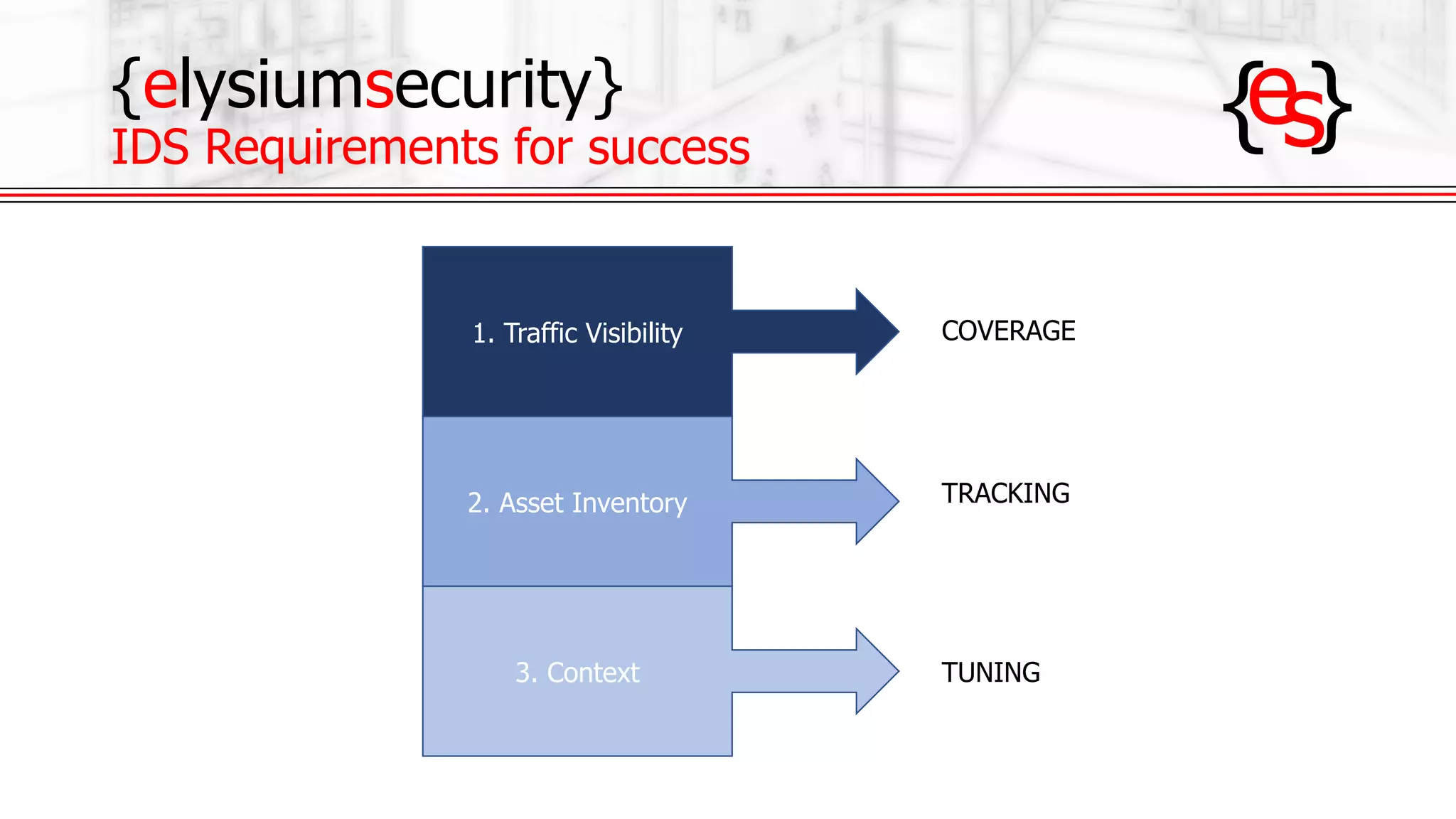
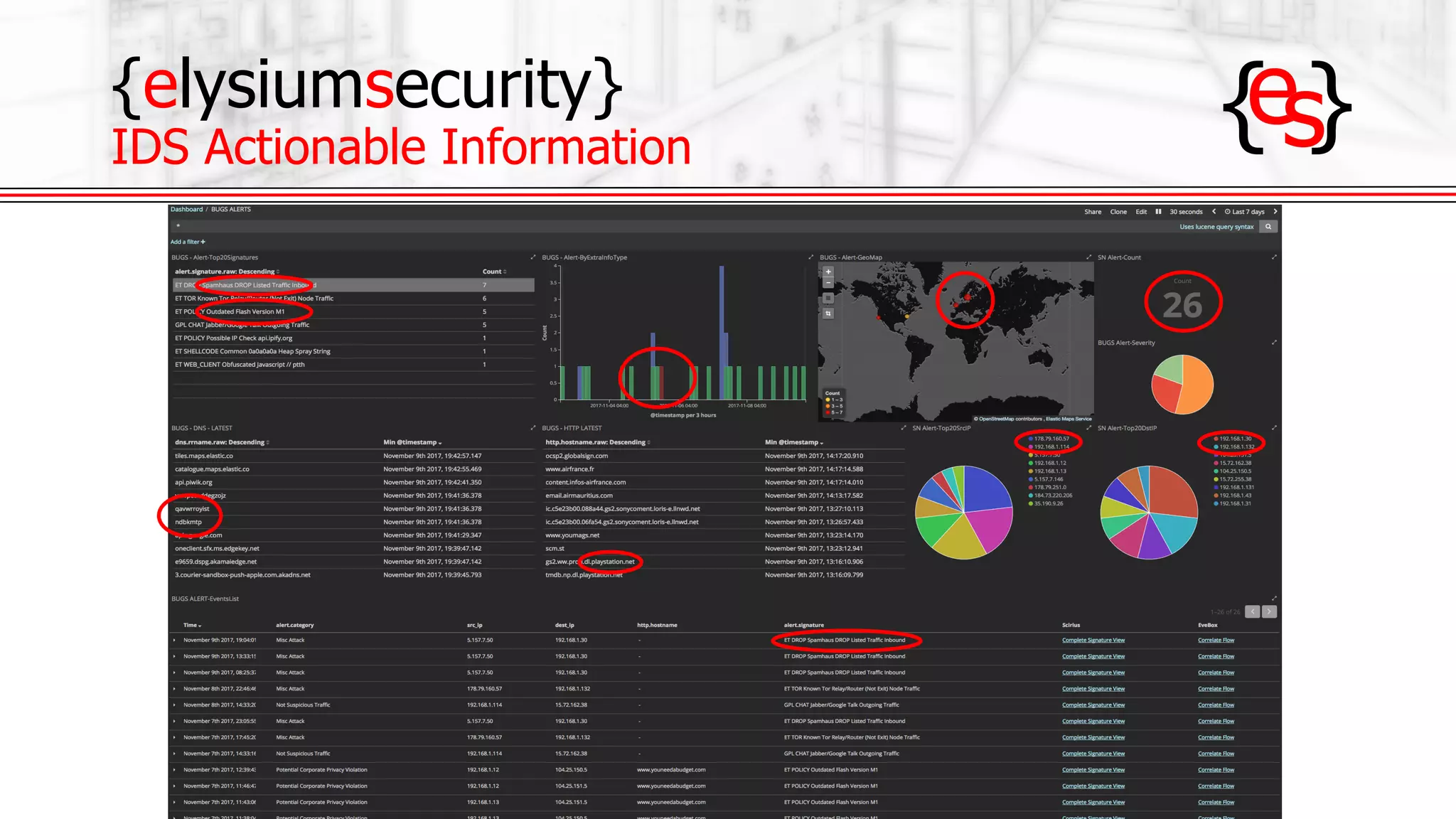
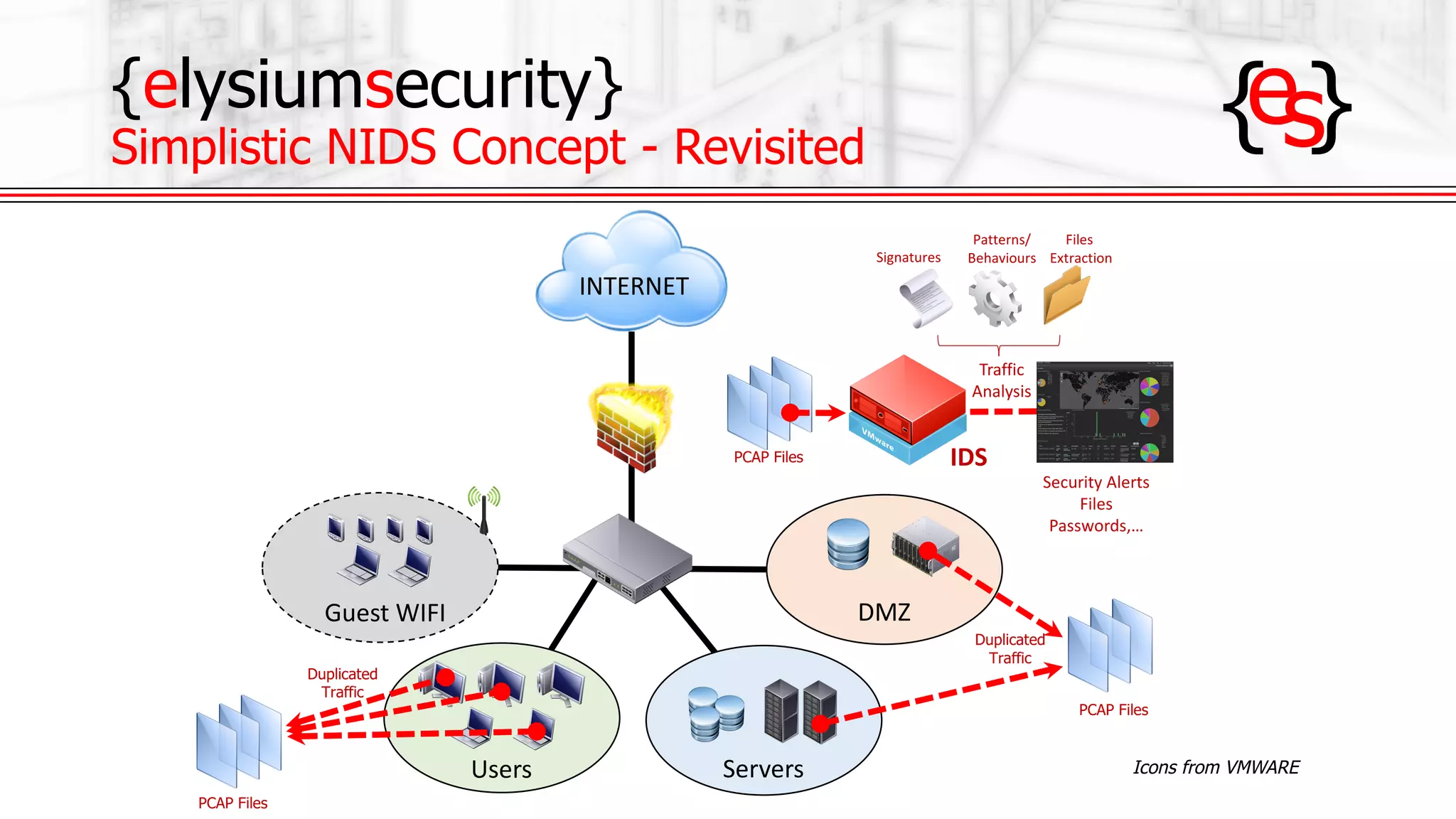
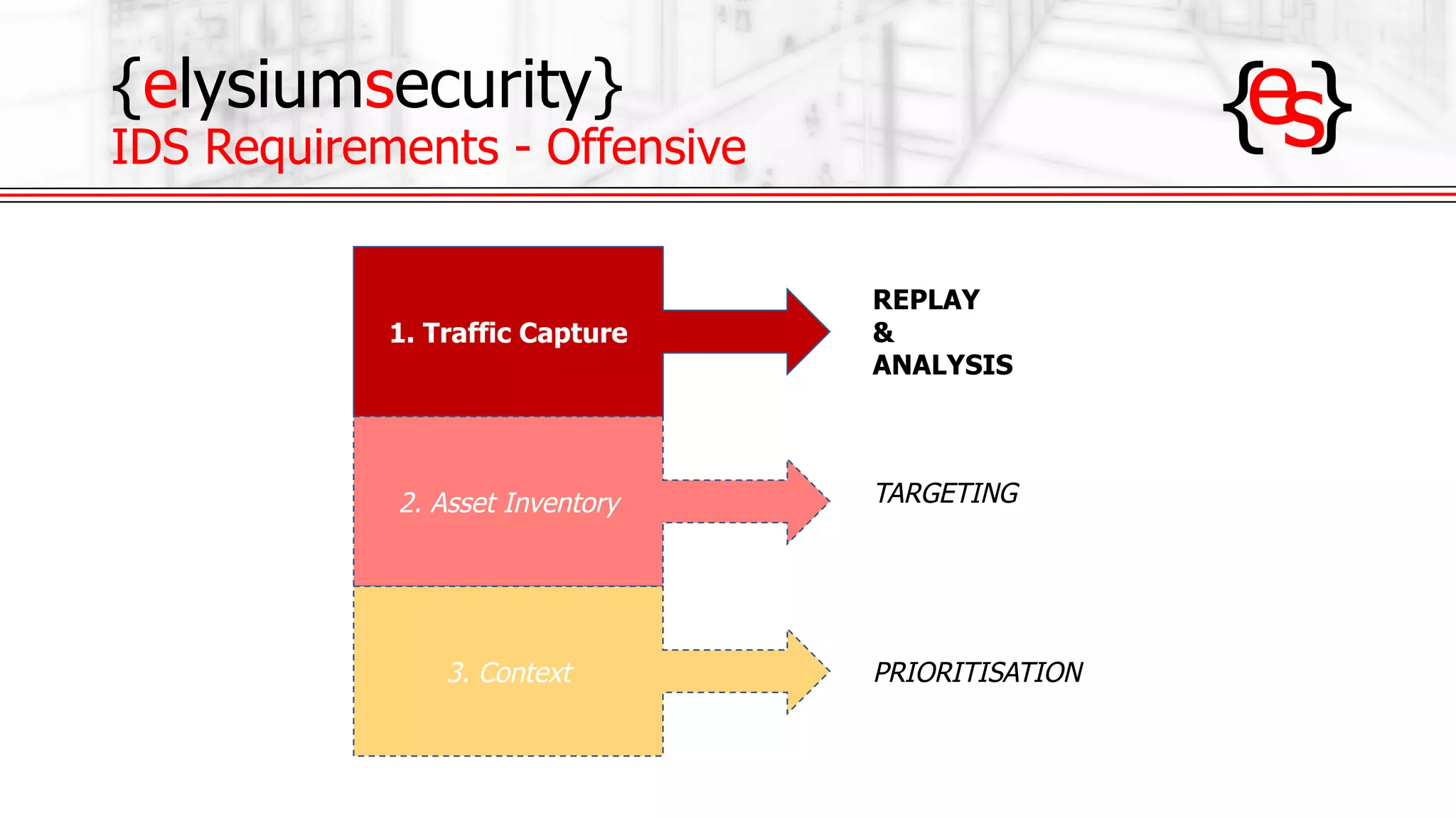
The document outlines the use of open-source Intrusion Detection Systems (IDS) as both defensive and offensive cybersecurity tools, discussing their benefits, requirements, and implementation. It emphasizes the increasing necessity for cybersecurity measures due to rising risks and highlights various free IDS options like Snort and Suricata. The document also provides insights on effective traffic visibility, asset inventory, and actionable information to enhance an organization's security posture.