This document discusses an enhancement to the S-MAC protocol called Enhanced S-MAC. S-MAC is a MAC protocol for wireless sensor networks that aims to improve power efficiency. Enhanced S-MAC further improves power efficiency by allowing nodes to adaptively turn their receivers on and off based on traffic load. It also addresses issues with clock synchronization and overhearing in the original S-MAC protocol. The document outlines related work on MAC protocols, problems encountered with implementing S-MAC, and how Enhanced S-MAC addresses these issues through adaptive listening modes and an improved synchronization protocol. It proposes to simulate Enhanced S-MAC to demonstrate improved power efficiency over standard S-MAC.
![TERM PAPER, CS5461/ECE5461, MOBILE NETWORKS, MICHIGAN TECHNOLOGICAL UNIVERSITY, SPRING 2015 1
Enhanced S-MAC protocol to improve the power
efficiency
Naveena Vemulapalli, Ruimin Zhang, Aliasghar Parandoosh, Zhaoxiang Jin
Abstract—Enhanced S-MAC is proposed to solve the fundamen-
tal problem in Wireless Sensor Network(WSN), how to keep the
network more power efficient. In order to minimize the energy
consumption, Enhanced S-MAC is devised to track the traffic
loading to adaptively turn on and off the receiver. There are issues
like clock synchronization, overhearing when we implemented
our protocol. In this proposal we would present all the necessary
techniques to solve these mentioned problems. Finally we simulate
our proposed mechanism and show how Enhanced S-MAC can
fit into the WSN application and optimize the power issue.
Keywords—Wireless Sensor Network, Power Efficiency, S-MAC,
MAC protocol, Adaptive listening mode
I. INTRODUCTION
Wireless sensor networking is a rapidly growing technol-
ogy. A wireless Sensor Network (WSN) distinguishes from
other wireless or wired networks through its capability of
interaction with the environment. Such networks have many
applications, such as environmental monitoring, smart spaces,
robotic exploration, search and rescue, smart environments and
localization system. WSNs usually include a large number of
nodes deployed in ad-hoc fashion to form a multi-hop wireless
network. Usually, all these nodes together carry out the same
task, for example keep tracking the temperature. Each node
may have one or more sensors, embedded processors, low-
power radios, and is operated with battery. Applications of
WSNs may require a large number of such smart nodes and
generally designed for long-term deployments without human
intervention. Consequently, energy efficient and scalability are
important design objectives.
Like all shared-medium networks, we need medium access
control (MAC) techniques to guarantee successful operation of
the system. The most fundamental job of the MAC protocol
is to avoid collisions from interfering nodes. Many MAC pro-
tocols have been developed, such as Time-Division Multiple
Access (TDMA), Code-Division Multiple Access (CDMA)
and contention-based protocols like IEEE 802.11 [1]. However,
they are not ideal for wireless sensor networking without
thinking much of energy efficiency and scalability.
S-MAC is a medium access control protocol designed for
wireless sensor networks. In addition to fulfilling the funda-
mental job, that avoids collisions from interfering nodes, S-
MAC puts emphasis on sensors’ energy consumption. The
reason behind it is that as stated above that all sensor nodes
are battery operated. In fact, we expect, in near future, that
these nodes become cheap enough so we discard them once
running out of battery. Therefore, we may prolong the network
life by reducing energy consumed by sensor nodes.
Four major sources are considered in S-MAC protocol for
causing inefficient use of energy as well as we can trade off
to reduce energy consumption. The first one is collision. If a
transmitted packet gets corrupted by other packets, it will be
discarded which in return would increase energy consumption
unnecessarily. S-MAC overcomes this problem with RTS-CTS
approach. The second reason is idle listening in which case
it listens to possible traffic that is not sent. Nodes with S-
MAC protocol are periodically put into sleep mode in order
to consume less energy. Each node, if it does not transmit or
receive nay data, turns off itself and sets a timer to wake itself
up at later time. This process happens periodically to make
sure no transmission is missed. The third source for energy
inefficiency is control overhead, i.e. sending and receiving
control packets which consumes energy too and less useful
data packets can be transmitted. S-MAC handles this issue
by a technique called message passing. In message passing,
we fragment a long message into many independent small
packets and transmit them in a burst. In this technique only
one RTS and one CTS are used. They reserve the medium
for transmitting all fragments. The last source is overhearing.
Overhearing occurs when a node receives a packet that is
destined to other nodes. Overhearing can be a major reason of
energy waste mainly with a high node density causing a heavy
traffic load. S-MAC tries to deal with this issue with a novel
idea of putting nodes to off mode (by switching their radio
off) when transmission is not meant for that node. S-MAC
tries to reduce the waste of energy from all above sources
while accepting some reduction in both per-hop fairness and
latency. Although per-hop fairness and latency are reduced, it
does not necessarily result in lower end-to-end fairness and
latency.
Fig. 1: The construction of the frame
Synchronization is a very big issue in S-MAC, since the
network size, topology and node density change over time and](https://image.slidesharecdn.com/0f9e5352-c240-438e-af94-897af3f585c4-160218220747/75/mn-paper-1-2048.jpg)
![TERM PAPER, CS5461/ECE5461, MOBILE NETWORKS, MICHIGAN TECHNOLOGICAL UNIVERSITY, SPRING 2015 2
individual nodes may have different clock drift. In S-MAC, a
node first waits for a random time. If it does not receive any
SYNC message it will start sending its own schedule. All other
nodes that receive this, should synchronize and change their
schedules to this one. This process will happen periodically.
A typical SYNC packet consists of Sender ID and Next-Time
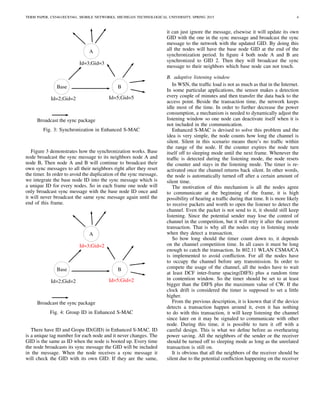
Sleep of that particular node. In S-MAC, listening period will
be divided into two parts. One for sending/receiving SYNC
messages and one for sending/receiving Data communication.
Figure 1 illustrates this point. As we can see that Data
communication period consists of sending/receiving control
packets like ACKs, RTS-CTS packets and Data transmission.
The ratio of the listening time to the whole period is called
duty cycle.
The major problems in S-MAC are that first fixed duty
cycles prevent S-MAC to be adaptive to traffic load. In wireless
sensor networks, traffic load changes all the time. Fixed duty
cycles prevent S-MAC to further exploit energy savings during
light traffic load. In this paper, we enhance S-MAC protocol,
by adopting variable duty cycle, to save more energy in a
wireless sensor network with light traffic load. Second, in order
to turn different nodes into Sleep mode, it should have the
knowledge when it will wake up. In order to minimize the
listening time and shorten the transmission delay, trade-off is
needed to determine the schedule of each node. In our protocol
(Enhanced S-MAC), we have redesigned the synchronization
protocol such that we do not need any of these information to
initiate a transmission or synchronize nodes together. The rest
of this paper is as follows.
In section II we will talk about the related past protocols
proposed by other researchers. We divide their protocols into
three groups of Contention-based MAC protocol, TDMA-
based MACs and S-MAC protocols. In section III we will point
out all the problems we encounter when we implement the
protocol. In section IV & V we will explain our own protocol
and system model for it as well as we bring our experimental
results acquired from the Enhanced-SMAC. SectionVI will be
the Conclusion.
II. RELATED WORK
MAC is a very broad research area. It includes research
mainly in the area to reduce the power consumption. Most of
the MACs that are used at present are the contention based
MAC protocols and TDMA protocols [2] [4] [5] [6].
A. Contention based MAC protocol
The IEEE 802.11 is one of the contention based protocol.
It is mostly used in the ad-hoc networks that is in the wireless
networks. This type of protocols has many advantages because
of its simplicity, robustness it also avoids the hidden terminal
problem. This protocol has a very high energy consumption
especially in the idle mode. This problem arises when the
nodes are in the listening state even when there is no data
transfer. Due to this idle listening the power consumption is
very high. PAMAS (power aware multiple access signaling)
is an energy saving mode to avoid overhearing among the
neighboring nodes. We have used the similar technique in our
paper that is related to the PAMAS [4].
B. TDMA-based MACs
TDMA based protocols have more energy conservation than
the contention based MAC protocols. This type of proto-
col is based on reservation and scheduling. TDMA protocol
contains nodes in the form of clusters. These clusters can
only communicate with in the cluster. Managing the inter
cluster communication and interference is not an easy thing.
Moreover when we deal with the mobile network. It is not
easy for the TDMA based protocol to dynamically change
the frame length and the time slot according to the network.
Then they proposed a new protocol for the wireless sensor
networks. In this protocol every node has different schedules
to communicate with its neighbors. Every time slot it only
talks with only one neighbor. To avoid interference different
channels are assigned to the interfering links that is FDMA
or CDMA. One of the main drawback of this protocol is its
low bandwidth utilization. If a node wants to send packets to
only one neighbor then it cannot reuse the time slots that are
scheduled to the other neighbors.
The next technology that has been developed to avoid the
low bandwidth utilization in the previous one is to have to an
adaptive rate control mechanism in CSMA. The main goal of
this is to have a good and fair bandwidth allocation to all the
nodes in the network. Next existing technology is piconet [7]
which is closely related to S-MAC. It keeps all the nodes to
periodically sleep so as to reduce the energy consumption.
But this mechanism does not have any coordination and
synchronization among the nodes about the sleep and the listen
intervals. The main feature of this scheme is to have the
communication between the neighboring nodes by allowing
the nodes to broadcast the address when it wakes up from the
sleep state. If a sender wants to talk to a neighbor it must be
in the listening state until it receives the broadcast from the
neighbor. While S-MAC gets synchronized with the schedules
of the neighboring nodes to reduce the energy consumption
and the latency.
The power saving mode in the IEEE 802.11 is almost related
to the S-MAC operation. The only difference is 802.11 is
designed for the single-hop network where all nodes can hear
each other. S-MAC is designed for the multi-hop network.
In the S-MAC the sleep schedules of all the nodes are
synchronized together.
C. S-MAC protocol
S-MAC has many approaches so as to reduce the energy
consumption due to idle listening, collision, overhearing and
control overhead. S-MAC takes the assumption that all the
communications occur between the nodes that are close to
each other. Another assumption is that we consider all the
applications will have long idle periods and can resist latency.
The basic feature of S-MAC scheme is that every node
sets a timer and sleeps for some time and then wakes up to
see if any node wants to send the data. All the nodes in the
network can choose their own listen/sleep schedules but they
should be synchronized to the neighboring nodes. It is possible
that all the nodes cannot synchronize in a multi-hop network.
They exchange their schedules by periodically broadcasting](https://image.slidesharecdn.com/0f9e5352-c240-438e-af94-897af3f585c4-160218220747/85/mn-paper-2-320.jpg)
![TERM PAPER, CS5461/ECE5461, MOBILE NETWORKS, MICHIGAN TECHNOLOGICAL UNIVERSITY, SPRING 2015 3
the SYNC packet to their neighboring nodes. If multiple
nodes want to talk with the same node to avoid collision,
avoidance S-MAC follows virtual and physical carrier sense.
Each packet contains the information about how much time
the transmission of the message will be. Every node records
this value and sets a timer. It is called the network allocation
vector. Before initiating the transmission every node looks at
its NAV and then starts the transmission if its NAV is zero.
NAV not equal to zero indicates that the medium is busy. This
type of sensing is called virtual carrier sensing. If the node fails
to get the medium it goes to sleep and wakes up again if when
the receiver is free and listening again. After the exchange of
the RTS/CTS the nodes will not sleep again until the data
transmission is complete.
In our Enhanced S-MAC protocol all nodes follow the
schedule of the dominant node and all the nodes are synchro-
nized only once before the data transmission. We know there
is a lot of energy waste due to the periodic synchronization
and scheduling which is removed in our Enhanced S-MAC
III. PROBLEM STATEMENT
In order to design a good mac protocol we have to consider
the following attributes. The first and the most important thing
is the energy consumption. We know that the sensor nodes
are powered with a battery and it is onerous to change or
replace the batteries frequently. Another important factor is
the adaptivity of the network to the changes in the traffic. A
good MAC protocol should give all of the above advantages. In
this paper we have presented the Enhanced S-MAC protocol
[2]. The main reasons for the increased power consumption
is that the nodes are in the idle state even when there is no
data transfer. In most of the present networks the nodes have
the fixed sleeping time and fixed listening time due to this
the nodes keep listening even in the idle state which wastes
a lot of power. If we change the listening time of the nodes
based on the traffic in the network then a lot of power can
be conserved. The next problem that is common in all the
wireless sensor network is the synchronization of the clock. It
is necessary for all the nodes in the network to synchronize
with each other in order to communicate with the nodes. For
the successful communication all the nodes should know the
sleep and listening times of their neighboring nodes. Therefore
synchronization is very important for communication. Next
major problem is the duty cycle, all the wireless sensor
networks that are present today have a fixed duty cycle. This
increases the power consumption in the nodes. This power
consumption is greatly reduced if we use the variable duty
cycle based on the traffic conditions.
IV. DESIGN SPACE
In order to further improve the power efficiency in Wireless
Sensor Network, we proposed our own MAC layer protocol
named as Enhanced S-MAC. The major difference between
our mechanism and S-MAC is we redesign the sync protocol
and adapt to a variable duty cycle for listening window.
We simplify the sync packet protocol by the clock drift by
which WSN can minimize the listening time for synchronous
functionality. The variable duty cycle can further reduce the
listening time by tracking the current traffic load. It may
introduce some new problems such as longer latency, but in our
application scenario we consider the latency as second priority
compared to power efficiency.
A. Sync Package
In wireless network, all the devices are isolated from each
other physically. There has no way to synchronize the clock
information through all the devices. That will not be a problem
if the receiver is always on since it will never miss a single
transaction except the conflictions. But in a WSN network it
will cause a substantial problem due to the clock drift.
Listen Period
0s 1s 2s 3s 4s
0s 1s 2s 3s 4s 5s
B
A
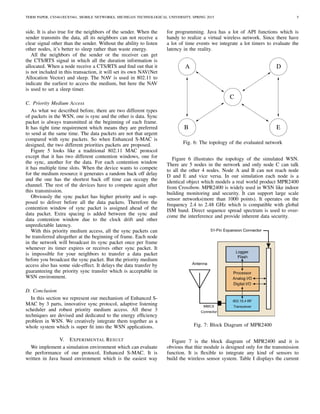
Fig. 2: Miss listening due to clock drift
In figure 2, there have 2 device nodes in the network, node
A and node B. Because of the clock drift the variation of their
own timers are getting larger and larger. In this example all
the devices are only wake up at the beginning of each second.
Thus if one node want to communicate with another, it has to
establish the link at the beginning of the second. Since they
have no ideas about the other one’s timer, they can not talk
to each other when one node is transmitting but the other is
sleeping.
What is missing here is synchronization. We can not count
on the clock accuracy since even two clocks are running
very close to each other, there may have a non-negligible
accumulative error which is big enough to cause the problem.
The concept of synchronization is to periodically reset all the
timers except the base one. Therefore no accumulative error
will be imposed.
In our project we propose an innovative mechanism to
deal with the synchronization problem. It is very easy to
implement and taking very short time to synchronize all the
nodes connected in the network. The protocol is designed
by the assumption that the clock drift is constant during the
operation, on the other words, the clock frequency of each node
will never change. For example, the node which is running
faster will always run faster.
With this assumption, one can easily find out that the fastest
timer will always be the first one to count down one second.
We select this fastest node to be our base node and all the
other nodes have to reset their timer when they receive the
sync package sent from the base node. Thus the frame starts
from the sync packet from base node and all the others will
be synchronized to this base node.](https://image.slidesharecdn.com/0f9e5352-c240-438e-af94-897af3f585c4-160218220747/85/mn-paper-3-320.jpg)
![TERM PAPER, CS5461/ECE5461, MOBILE NETWORKS, MICHIGAN TECHNOLOGICAL UNIVERSITY, SPRING 2015 7
TABLE III: Listening time for each node
data set 2986kB; Time 999.7S
node A 55.1S
node B 63.6S
node C 74.0S
node D 54.7S
node E 54.3S
data set 5916kB ; Time 997.5S
node A 89.4S
node B 88.7S
node C 130.1S
node D 81.4S
node E 93.8S
data set 12229KB ; Time 991.3S
node A 170.5S
node B 169.3S
node C 233.9S
node D 168.7S
node E 152.3S
TABLE IV: Energy consumption in 3 protocols
data set 2986kB; Time 999.7S
Enhanced S-MAC 1207.5 mAS
S-MAC 9857 mAS
802.11 19694 mAS
data set 5916kB ; Time 997.5S
Enhanced S-MAC 1922.6 mAS
S-MAC 9835.35 mAS
802.11 19650.75 mAS
data set 12229KB ; Time 991.3S
Enhanced S-MAC 3541.4 mAS
S-MAC 9774.2 mAS
802.11 19528.61 mAS
clock drift. We have built a Java-based simulation environment
to evaluate our Enhanced S-MAC. We simulated a wireless
sensor network, consisting two subnets with one node covered
by both. Our preliminary results show that our Enhanced S-
MAC might have good potential to dramatically reduce energy
consumption in a wireless sensor network with light traffic
load.
REFERENCES
[1] I. C. S. L. M. S. Committee et al., “Wireless lan medium access control
(mac) and physical layer (phy) specifications,” 1997.
[2] W. Ye, J. Heidemann, and D. Estrin, “An energy-efficient mac protocol
for wireless sensor networks,” in INFOCOM 2002. Twenty-First Annual
Joint Conference of the IEEE Computer and Communications Societies.
Proceedings. IEEE, vol. 3. IEEE, 2002, pp. 1567–1576.
[3] S. Singh and C. S. Raghavendra, “Pamaspower aware multi-access pro-
tocol with signalling for ad hoc networks,” ACM SIGCOMM Computer
Communication Review, vol. 28, no. 3, pp. 5–26, 1998.
[4] S. Singh, M. Woo, and C. S. Raghavendra, “Power-aware routing in
mobile ad hoc networks,” in Proceedings of the 4th annual ACM/IEEE
international conference on Mobile computing and networking. ACM,
1998, pp. 181–190.
[5] W. R. Heinzelman, A. Chandrakasan, and H. Balakrishnan, “Energy-
efficient communication protocol for wireless microsensor networks,”
in System sciences, 2000. Proceedings of the 33rd annual Hawaii
international conference on. IEEE, 2000, pp. 10–pp.
[6] A. Woo and D. E. Culler, “A transmission control scheme for media
access in sensor networks,” in Proceedings of the 7th annual interna-
tional conference on Mobile computing and networking. ACM, 2001,
pp. 221–235.
[7] F. Bennett, D. Clarke, J. B. Evans, A. Hopper, A. Jones, and D. Leask,
“Piconet: Embedded mobile networking,” Personal Communications,
IEEE, vol. 4, no. 5, pp. 8–15, 1997.](https://image.slidesharecdn.com/0f9e5352-c240-438e-af94-897af3f585c4-160218220747/85/mn-paper-7-320.jpg)