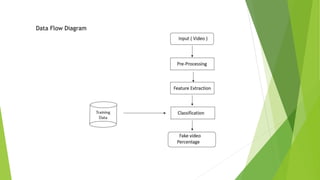
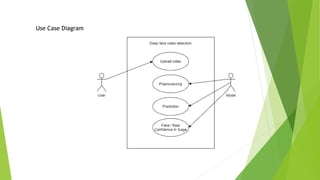
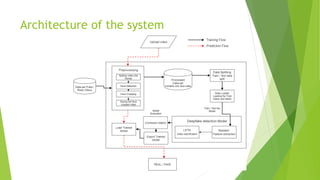
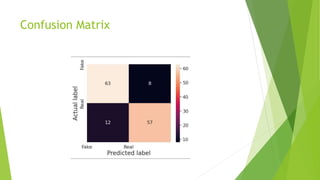
The document outlines a project aimed at developing a deep fake video detection system using AI techniques to address the rising threat of manipulated media. It details the methodology including dataset acquisition, preprocessing steps, and model architecture combining CNN and LSTM for video classification. The application aims to maintain media integrity and prevent misinformation in various contexts such as news, elections, and social media.