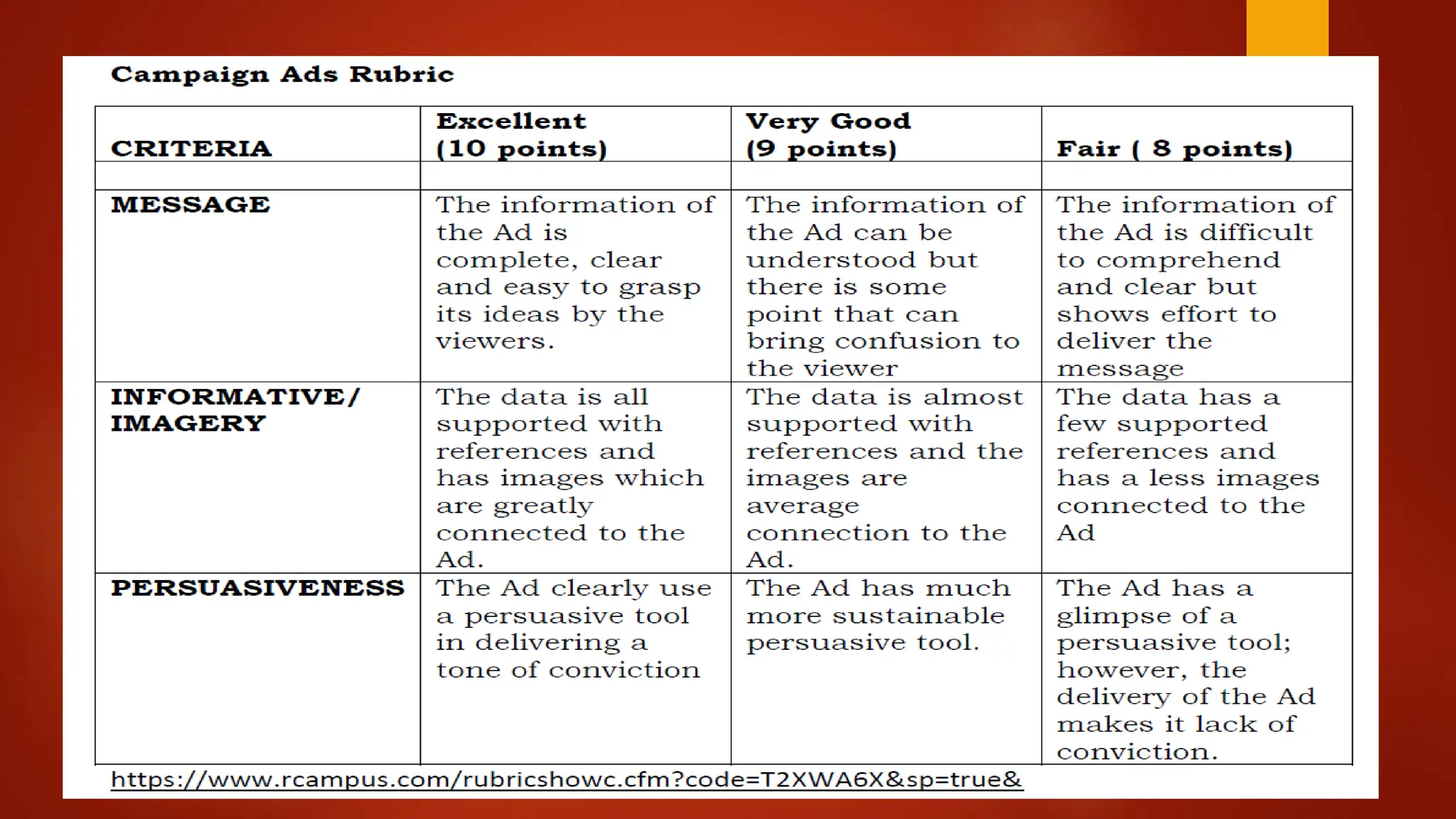
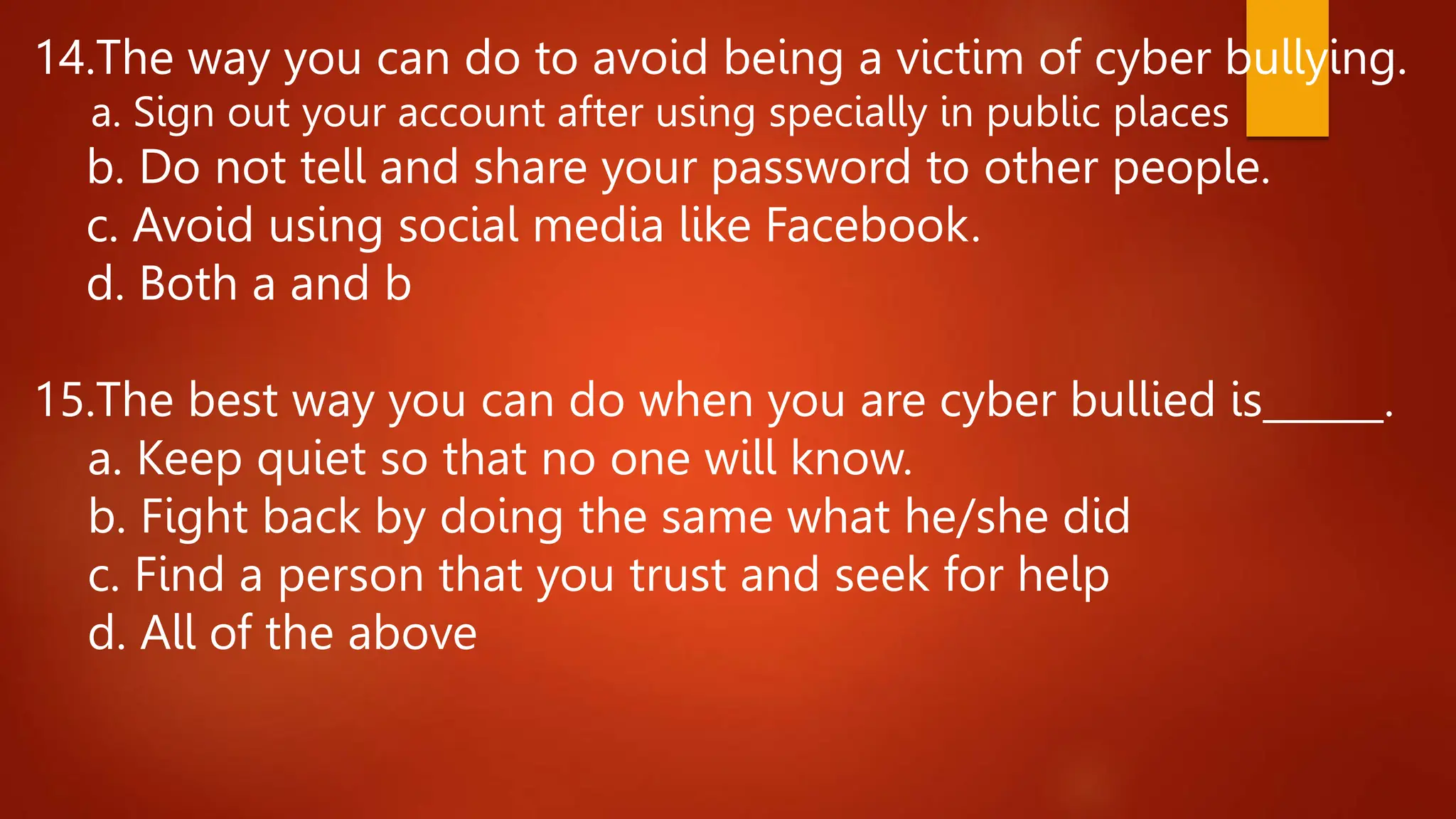
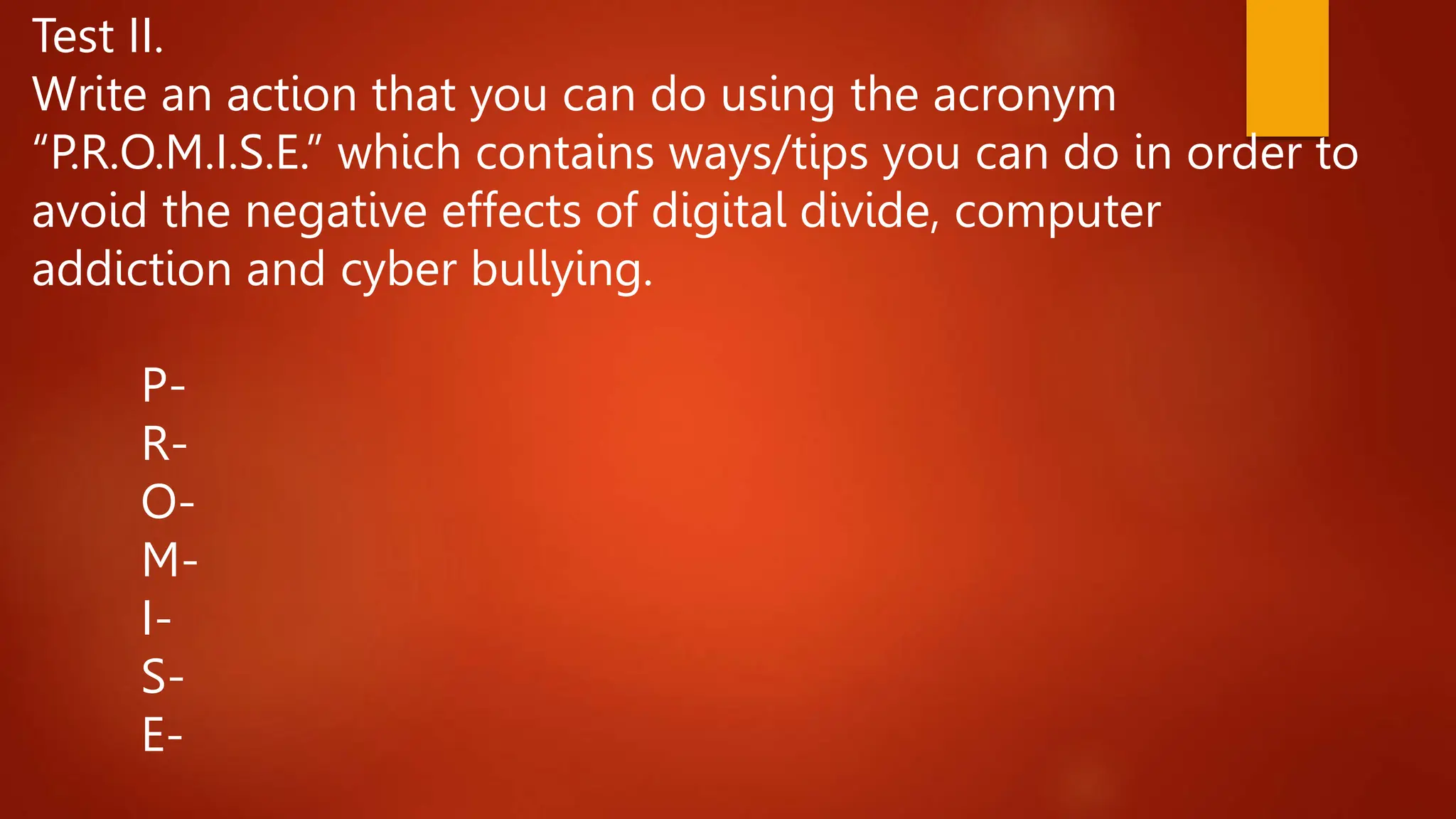
This document provides an overview of Module 7 which covers digital divide, computer addiction, and cyberbullying. The objectives are to define these terms, discuss current issues related to them, and develop an advertising campaign to address them. It then provides background information on each topic, including definitions, causes, effects, and ways to prevent them. Multiple choice questions are included to assess understanding, and an activity is assigned to have students create an advertising campaign poster with slogans to combat these issues.