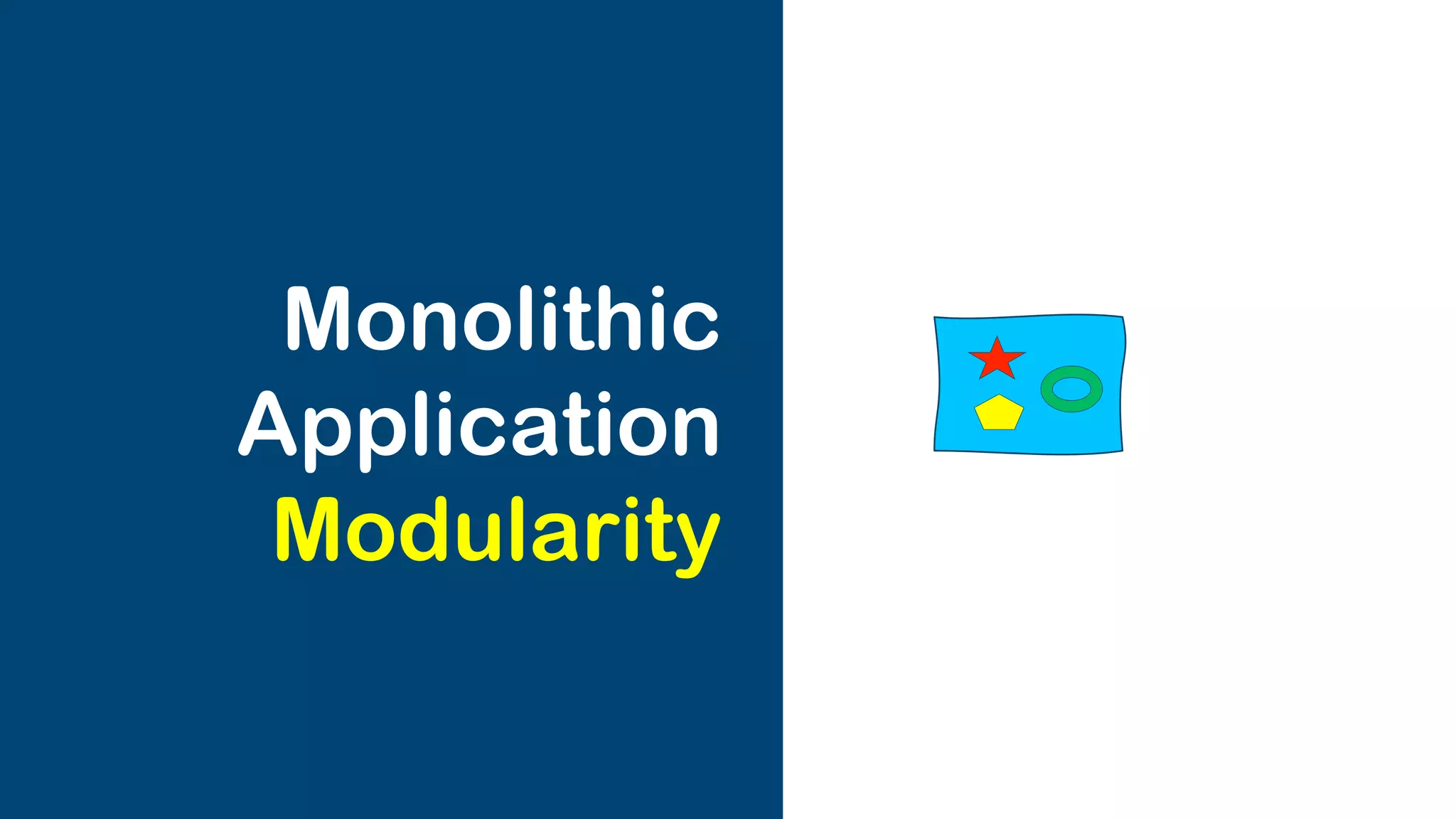
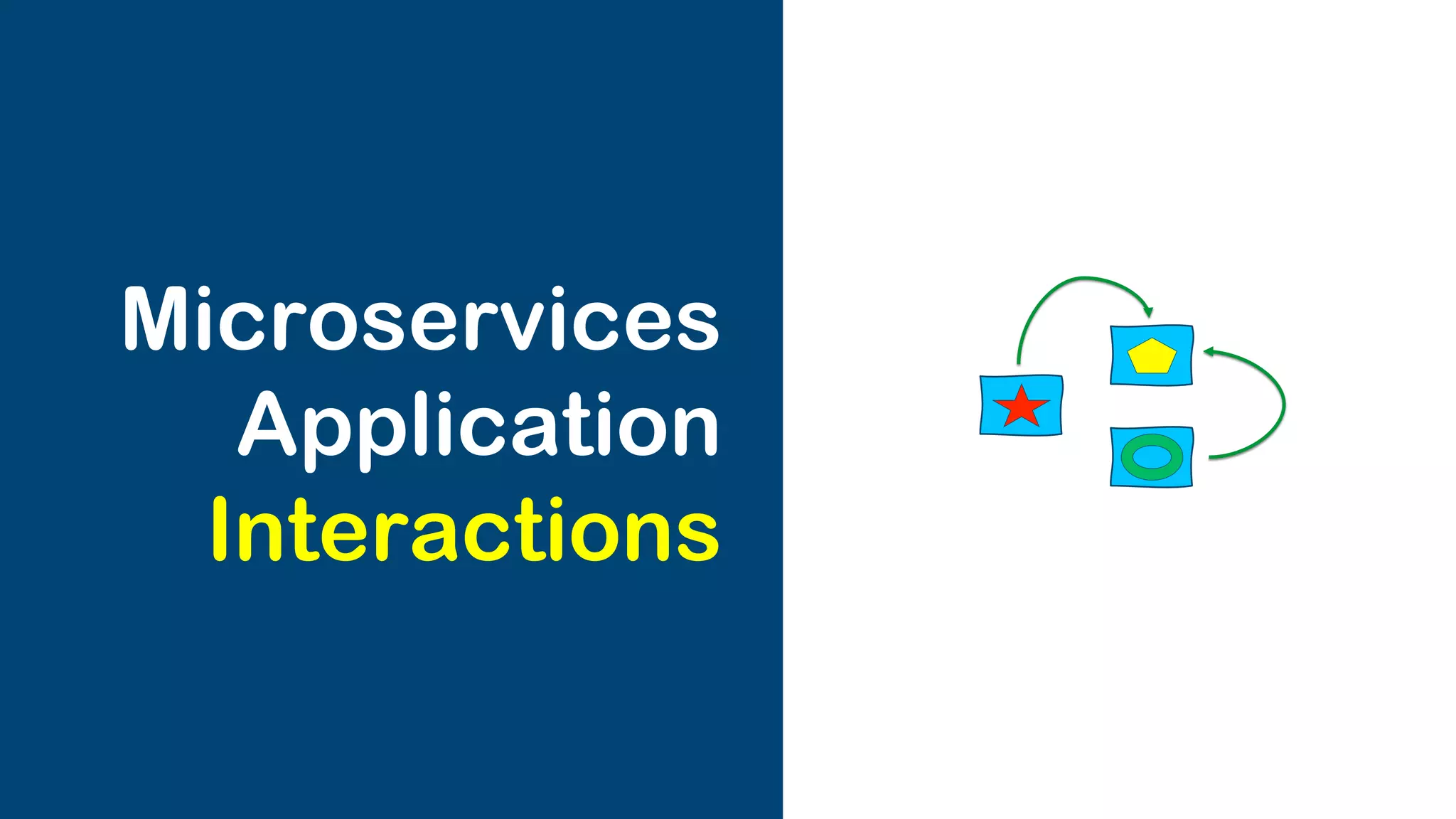
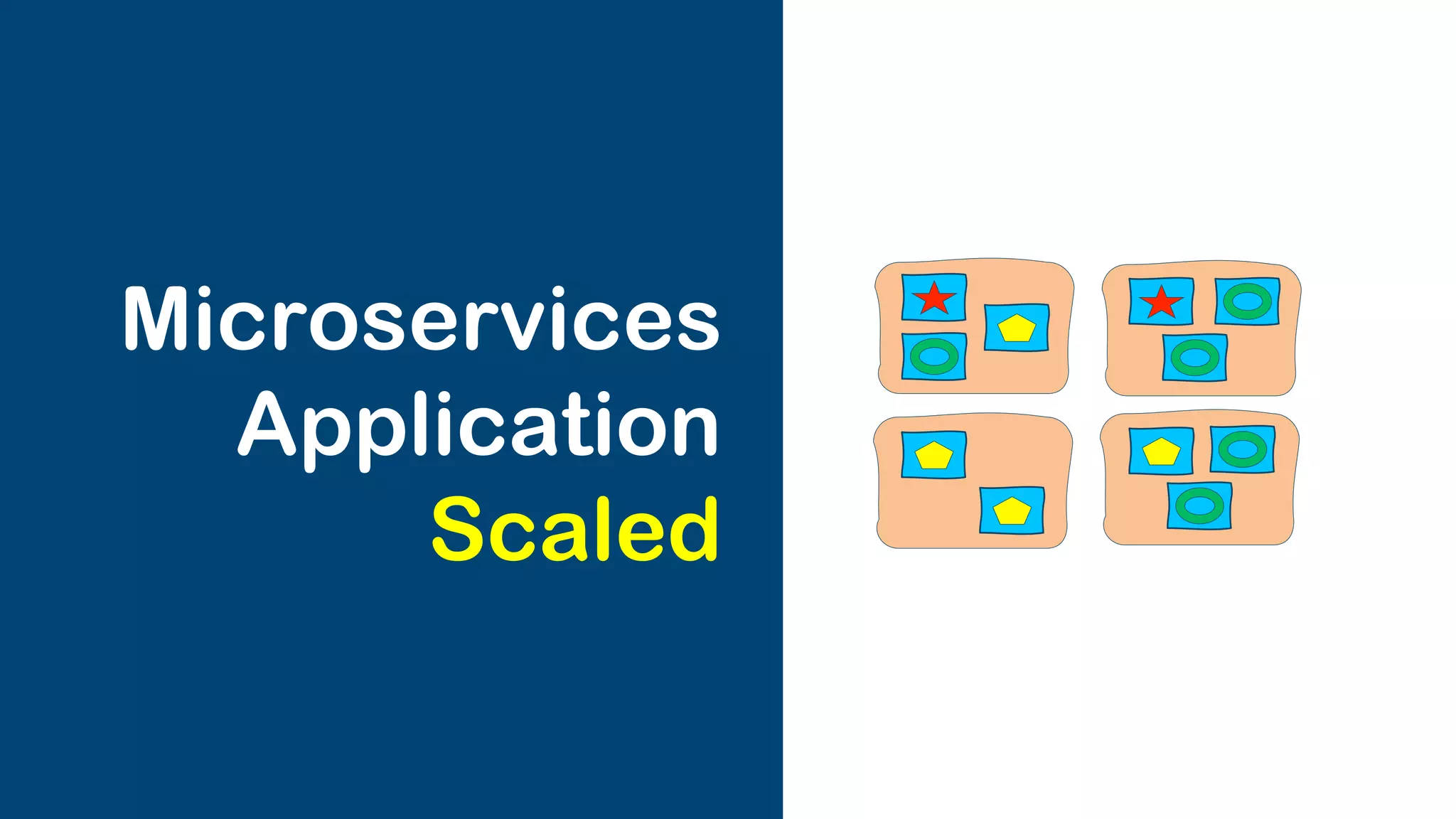
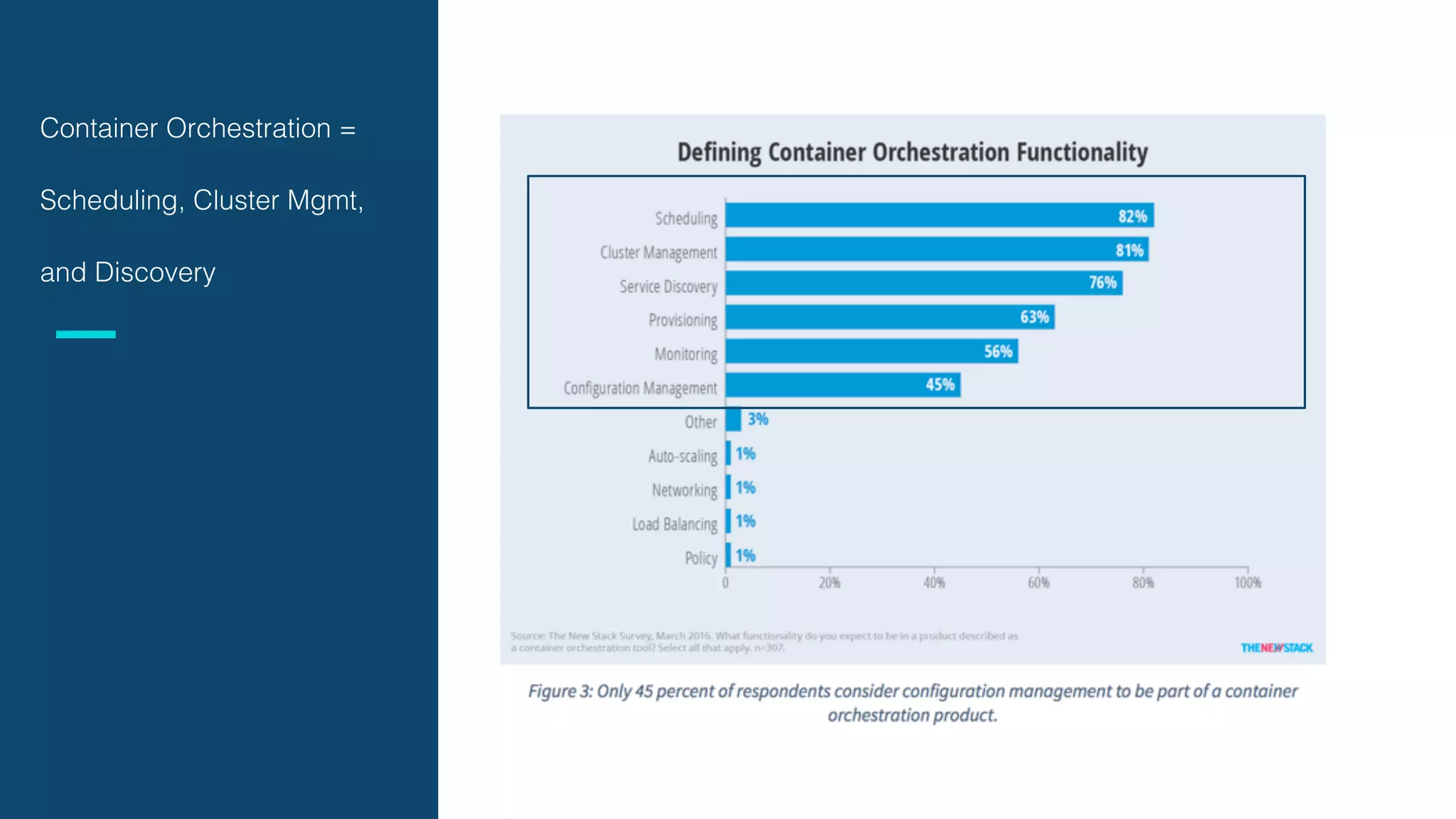
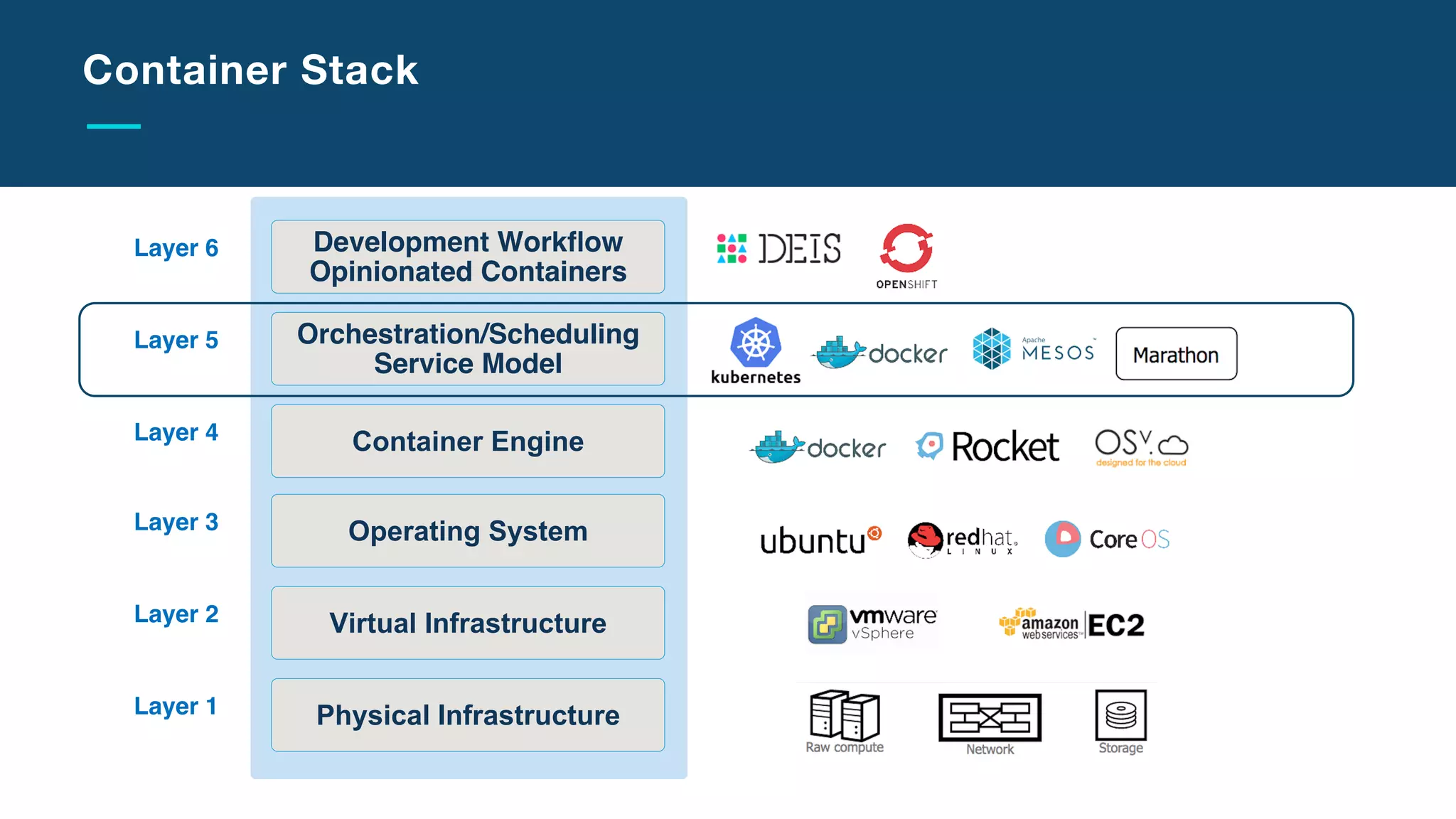
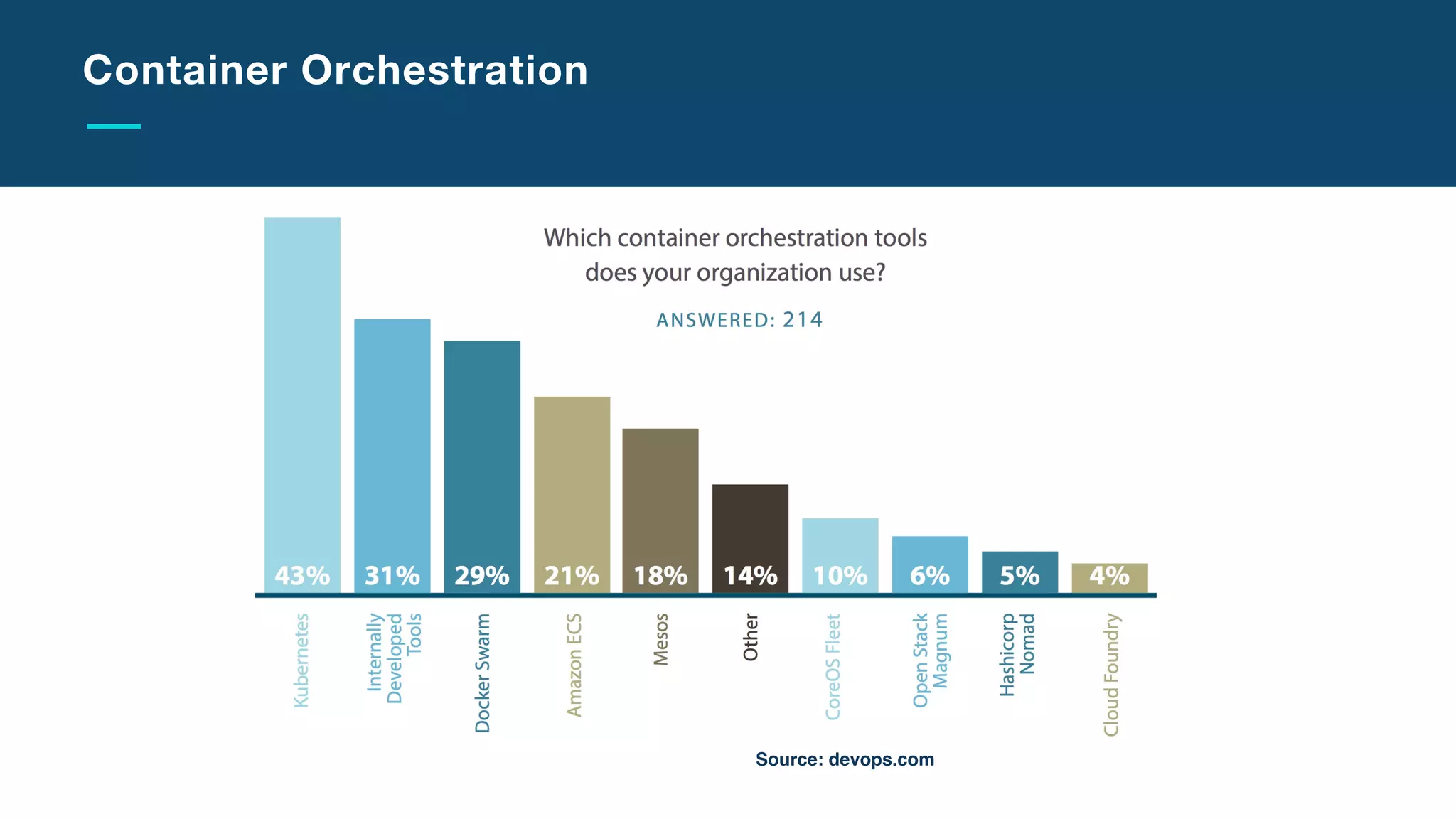
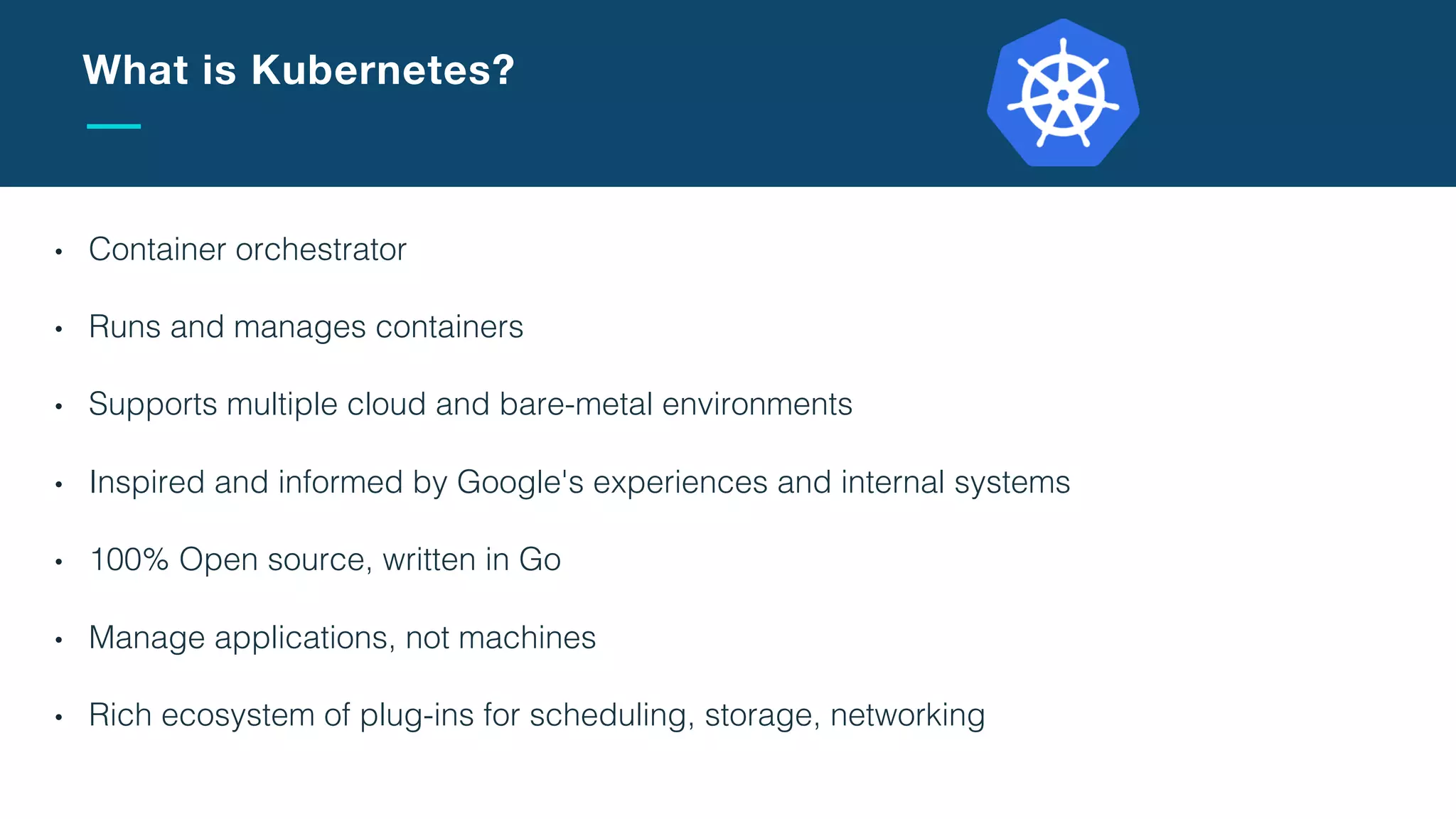
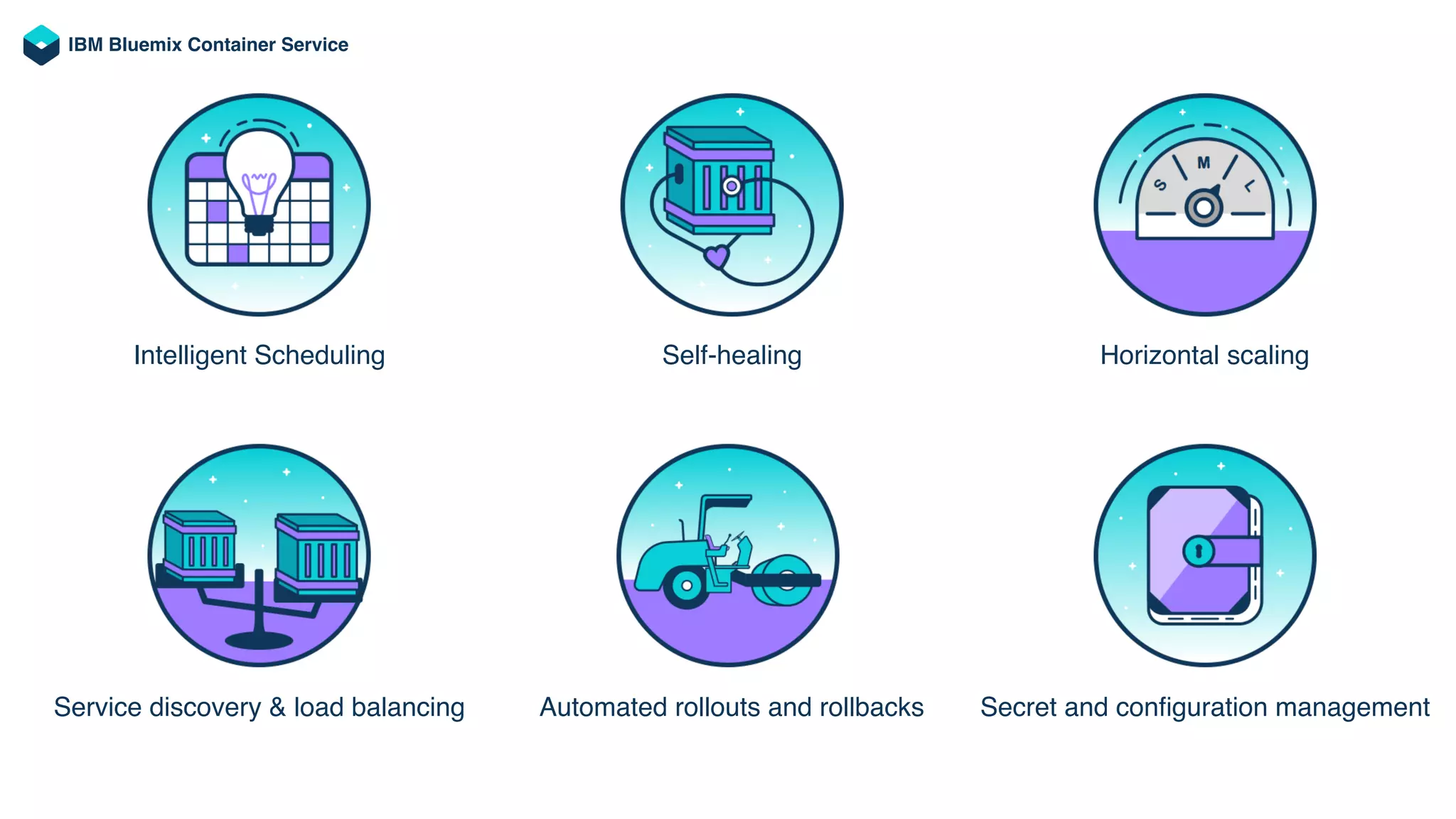
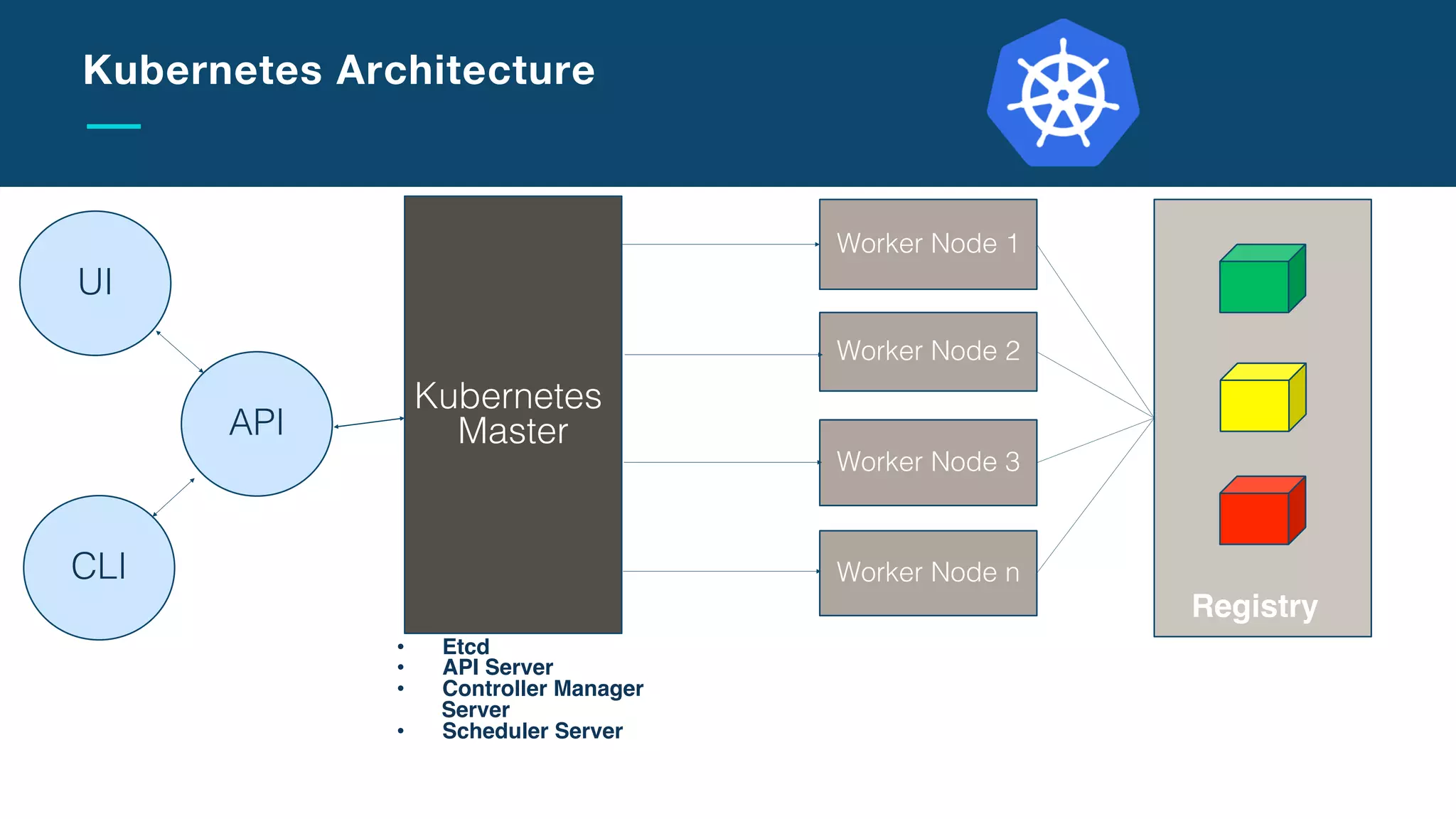
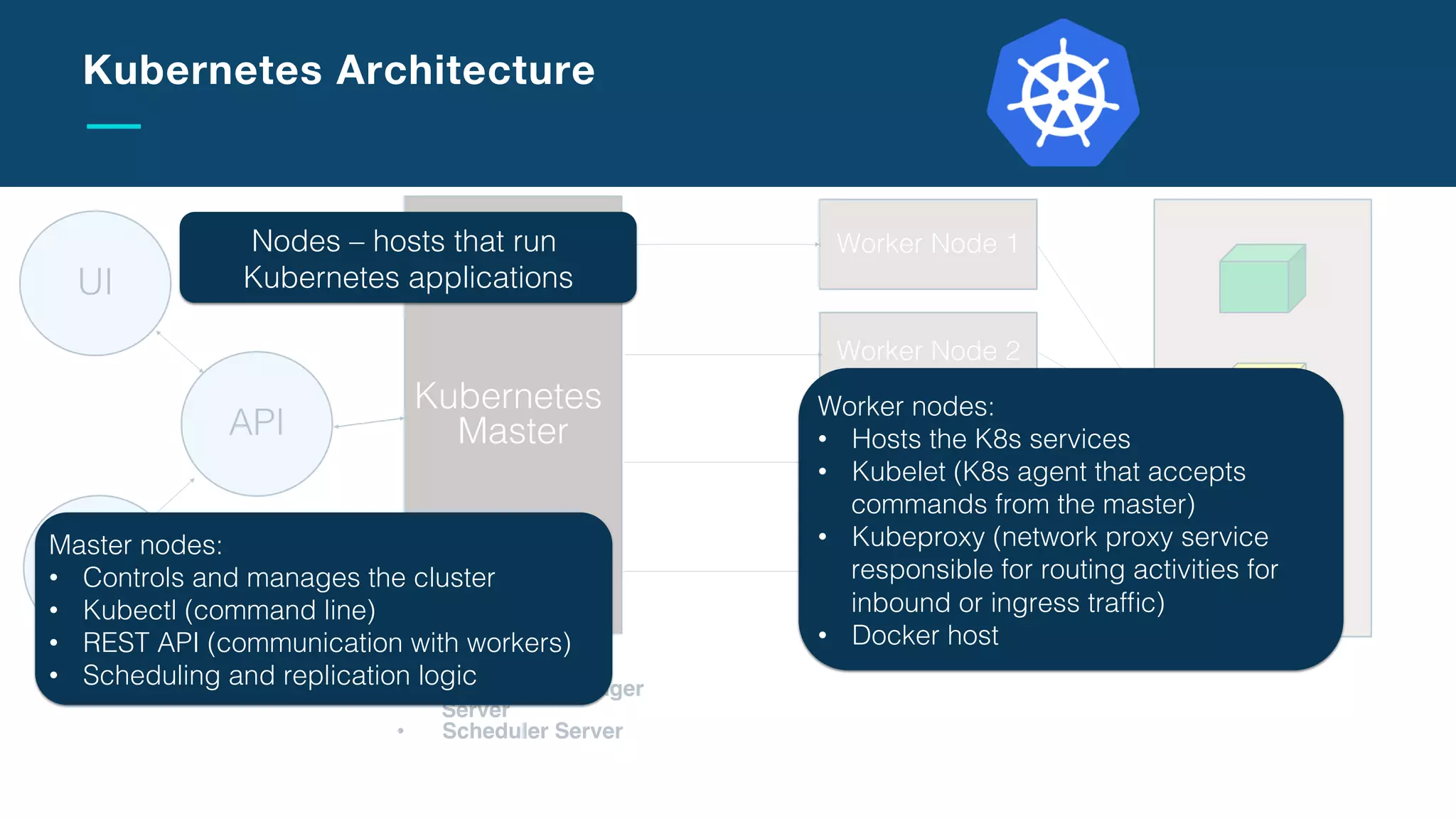
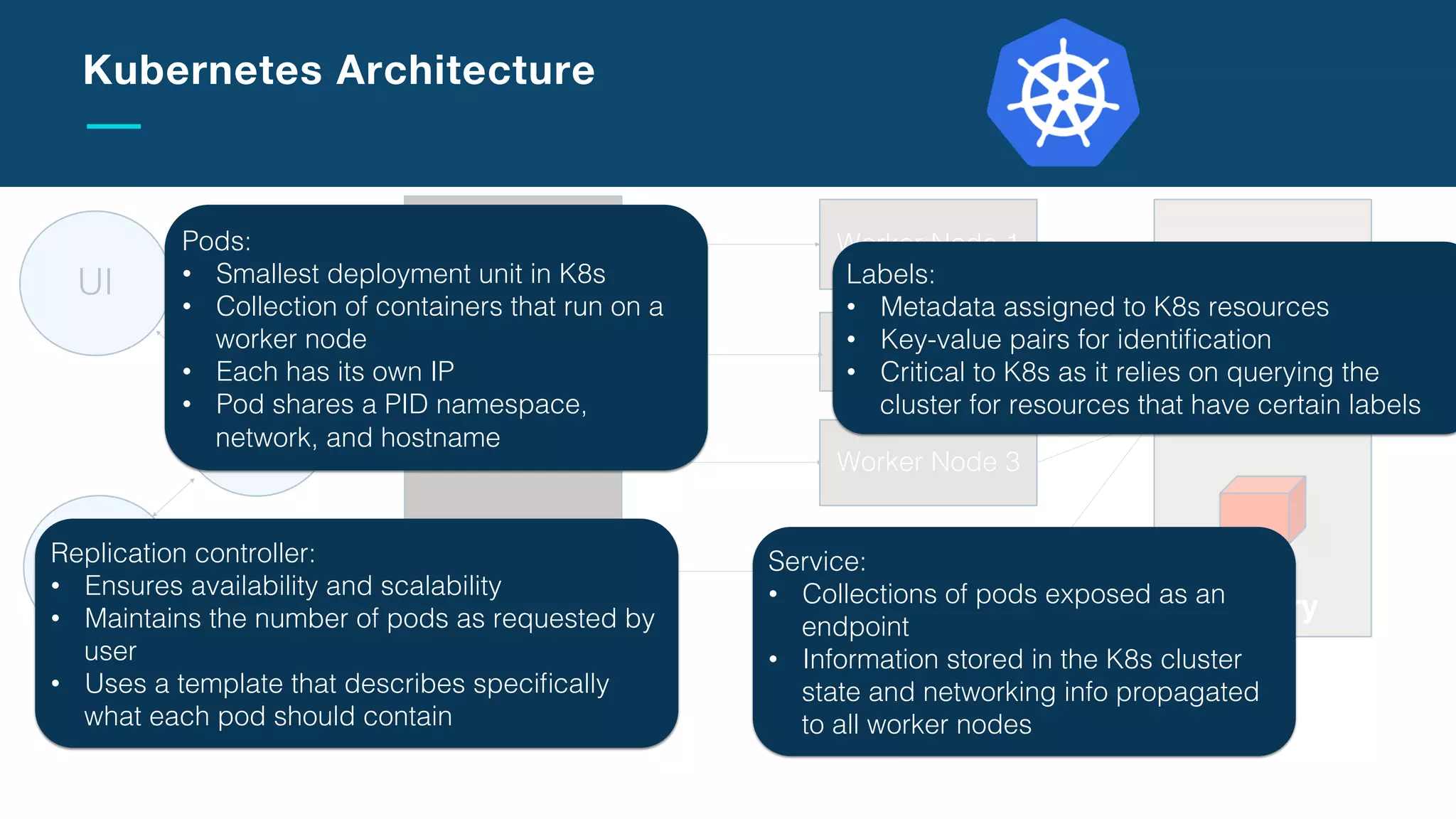
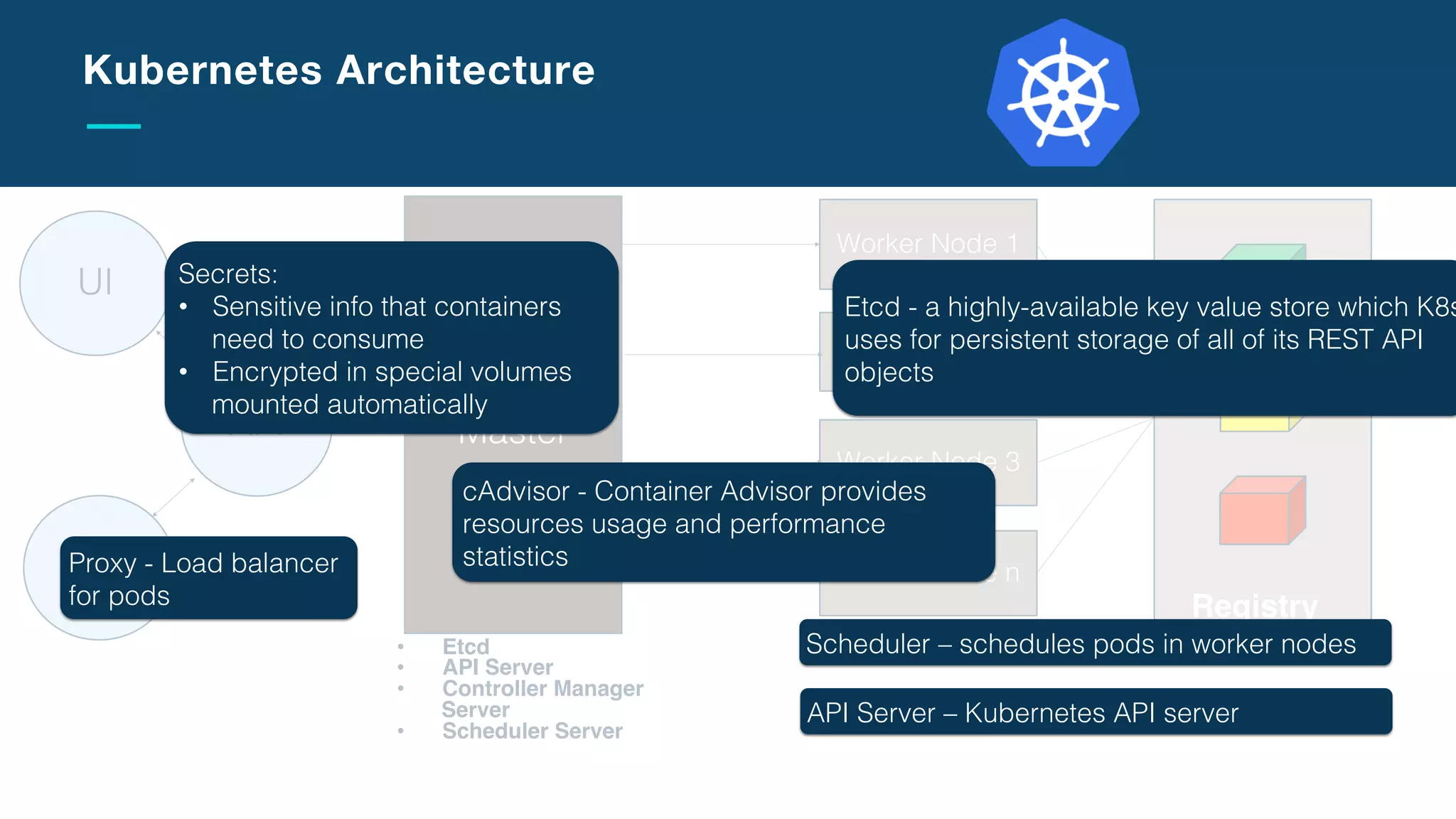
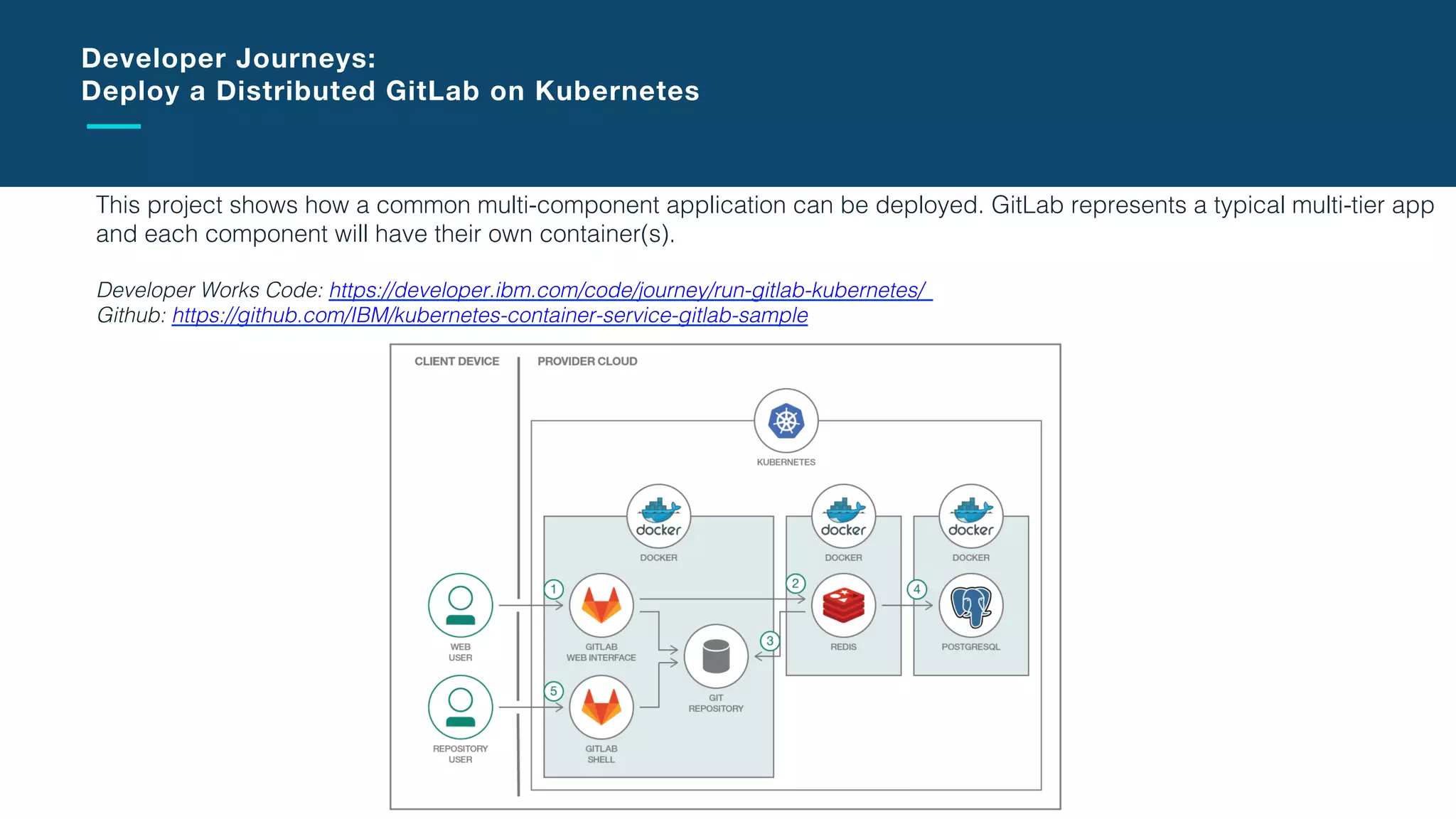
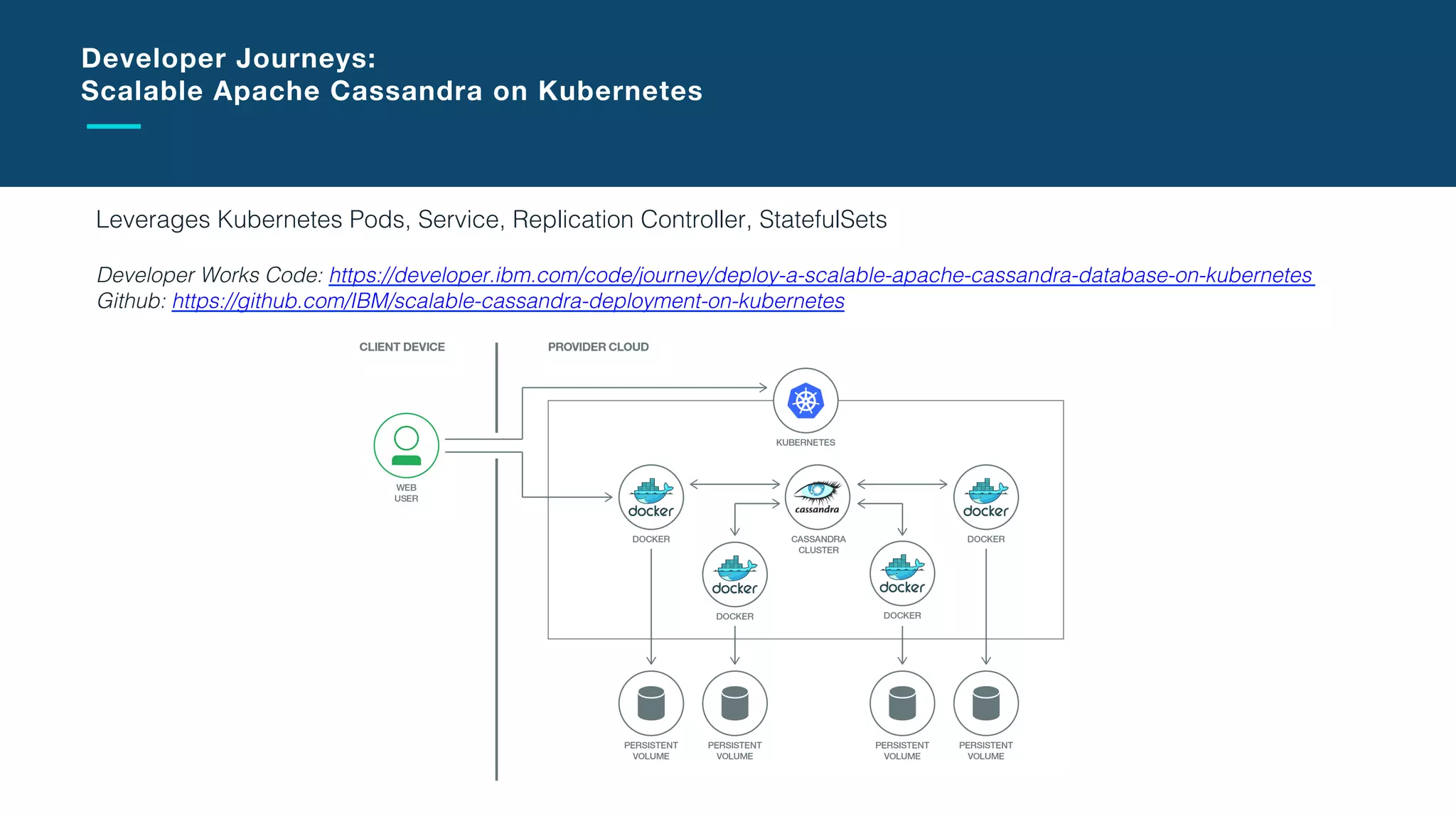
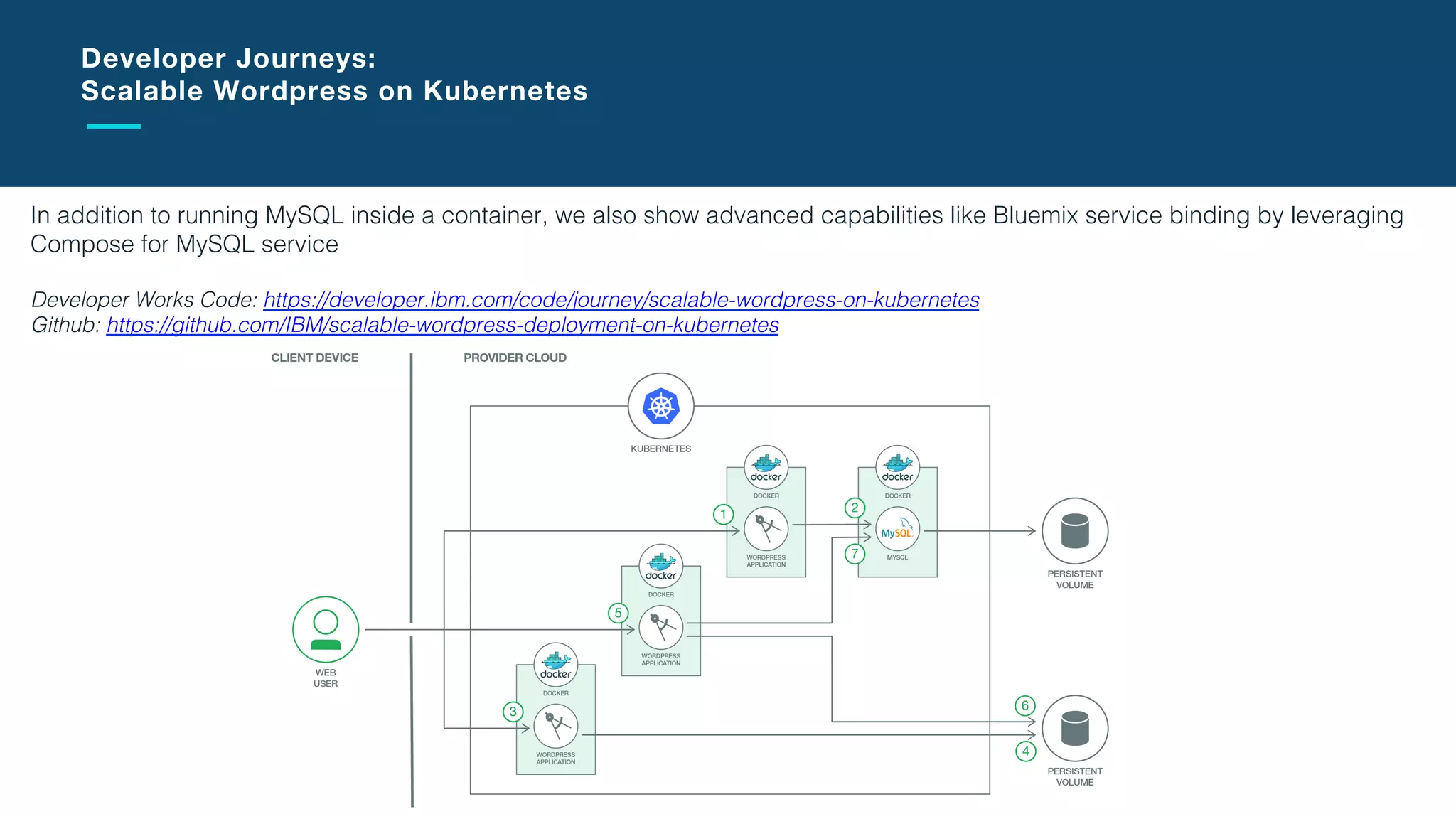
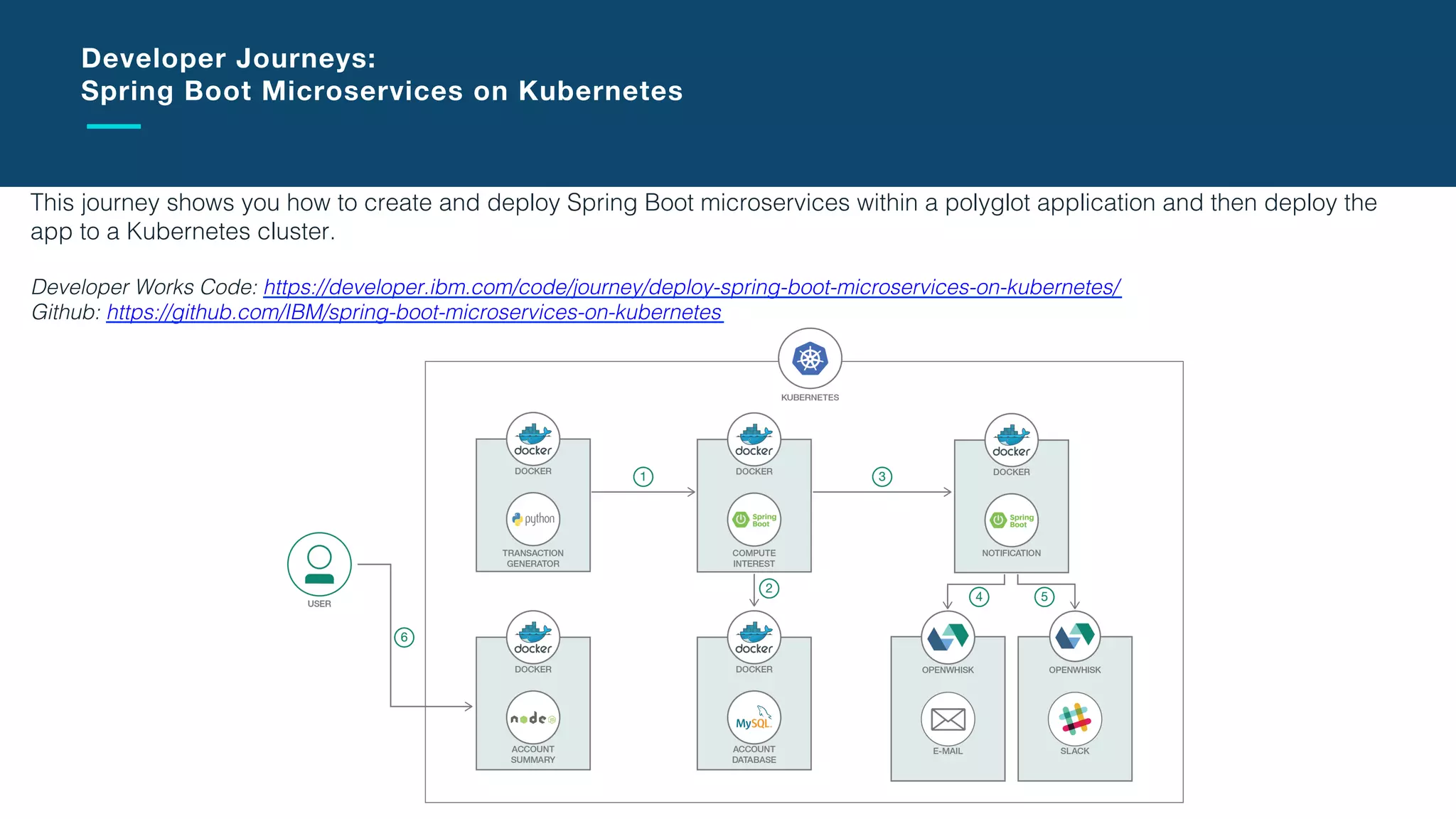
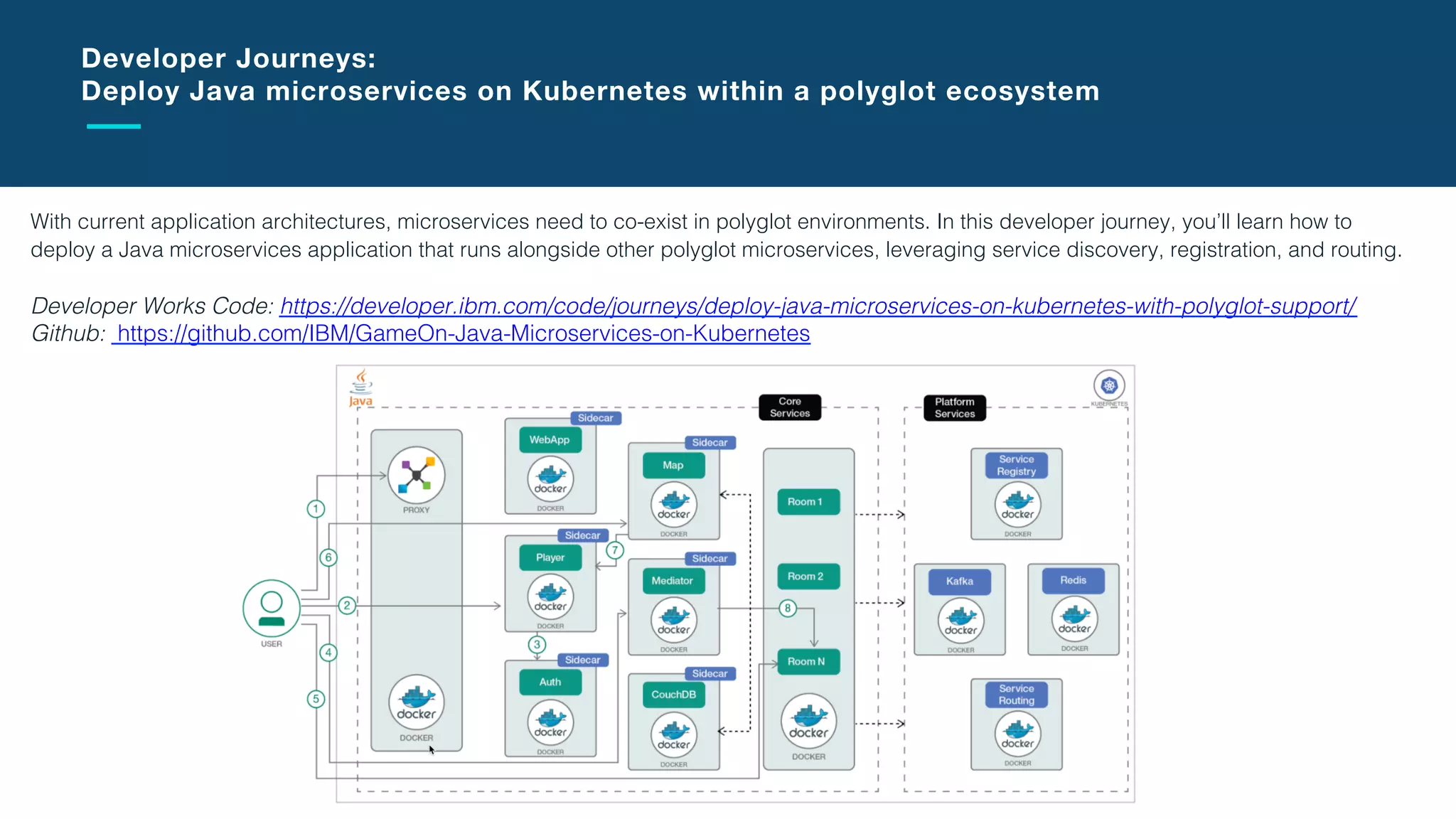
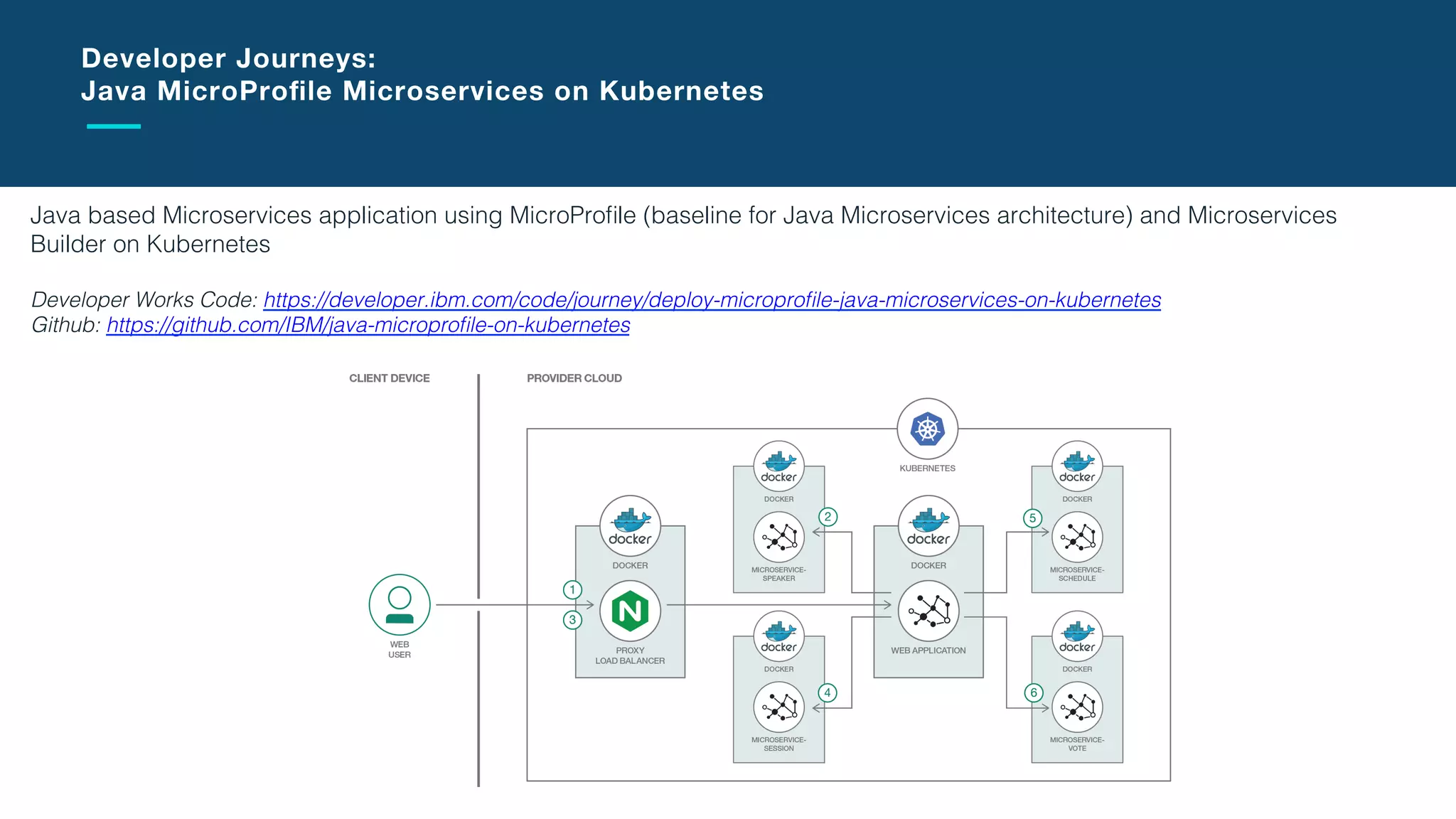
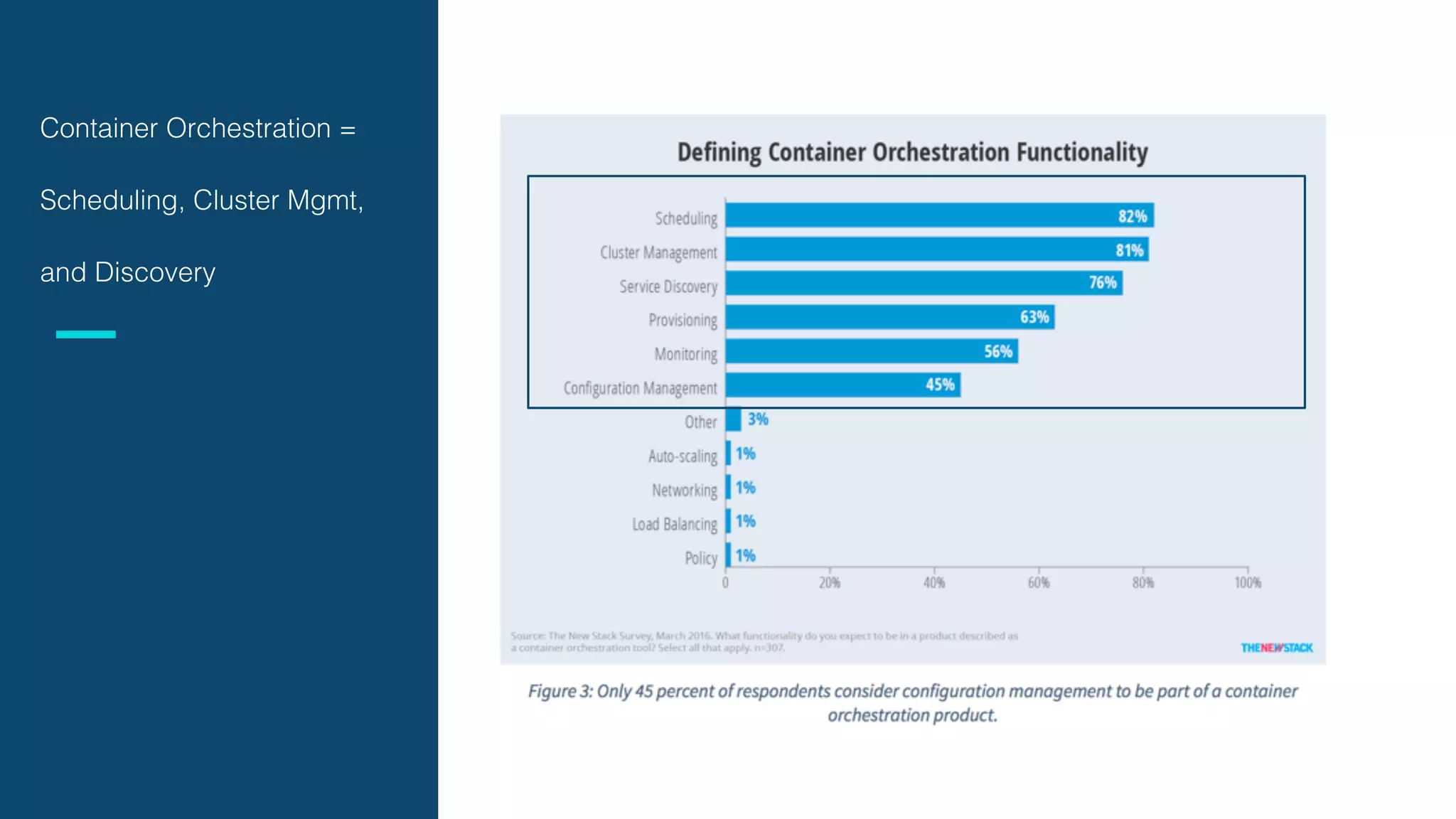
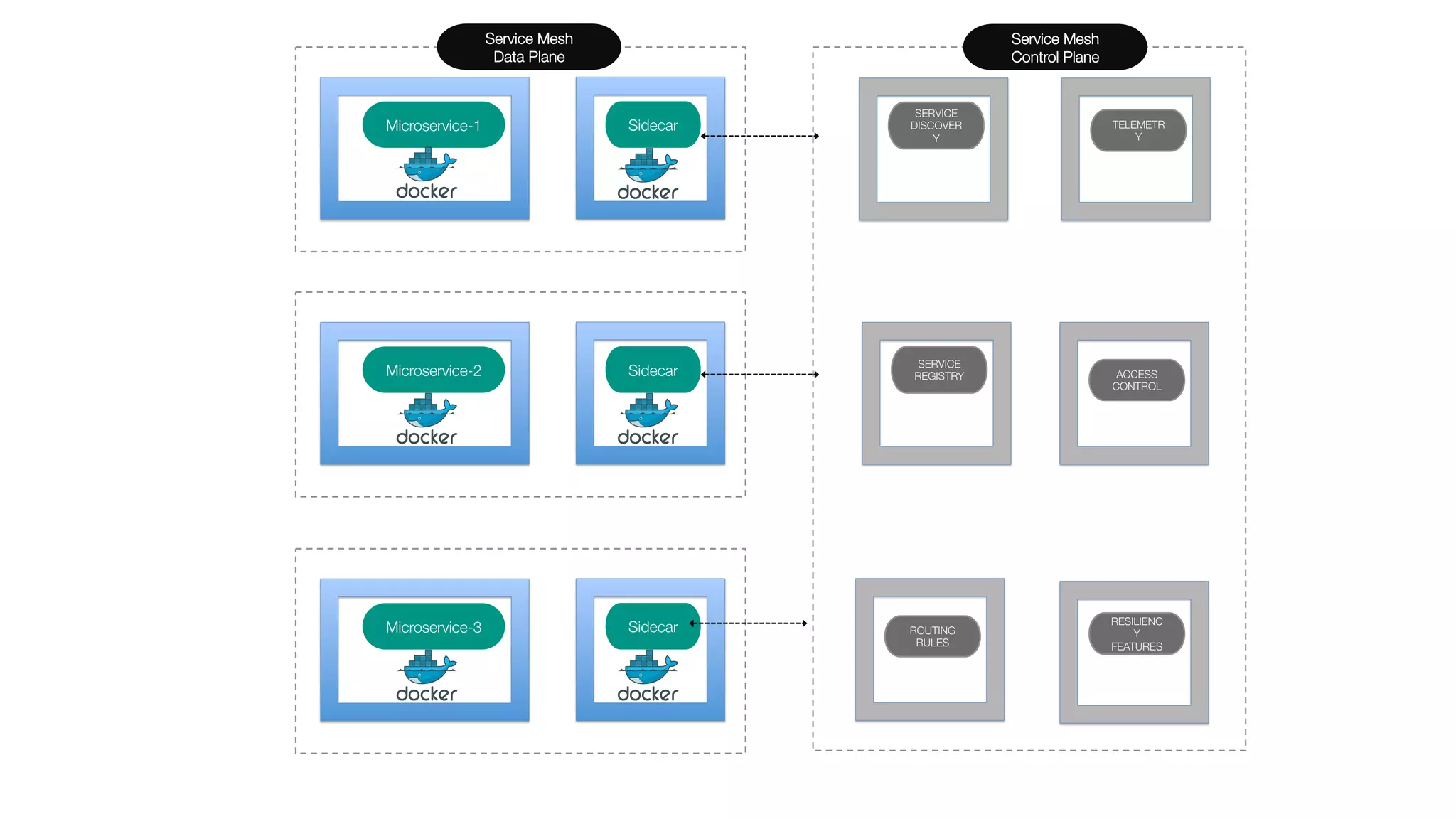
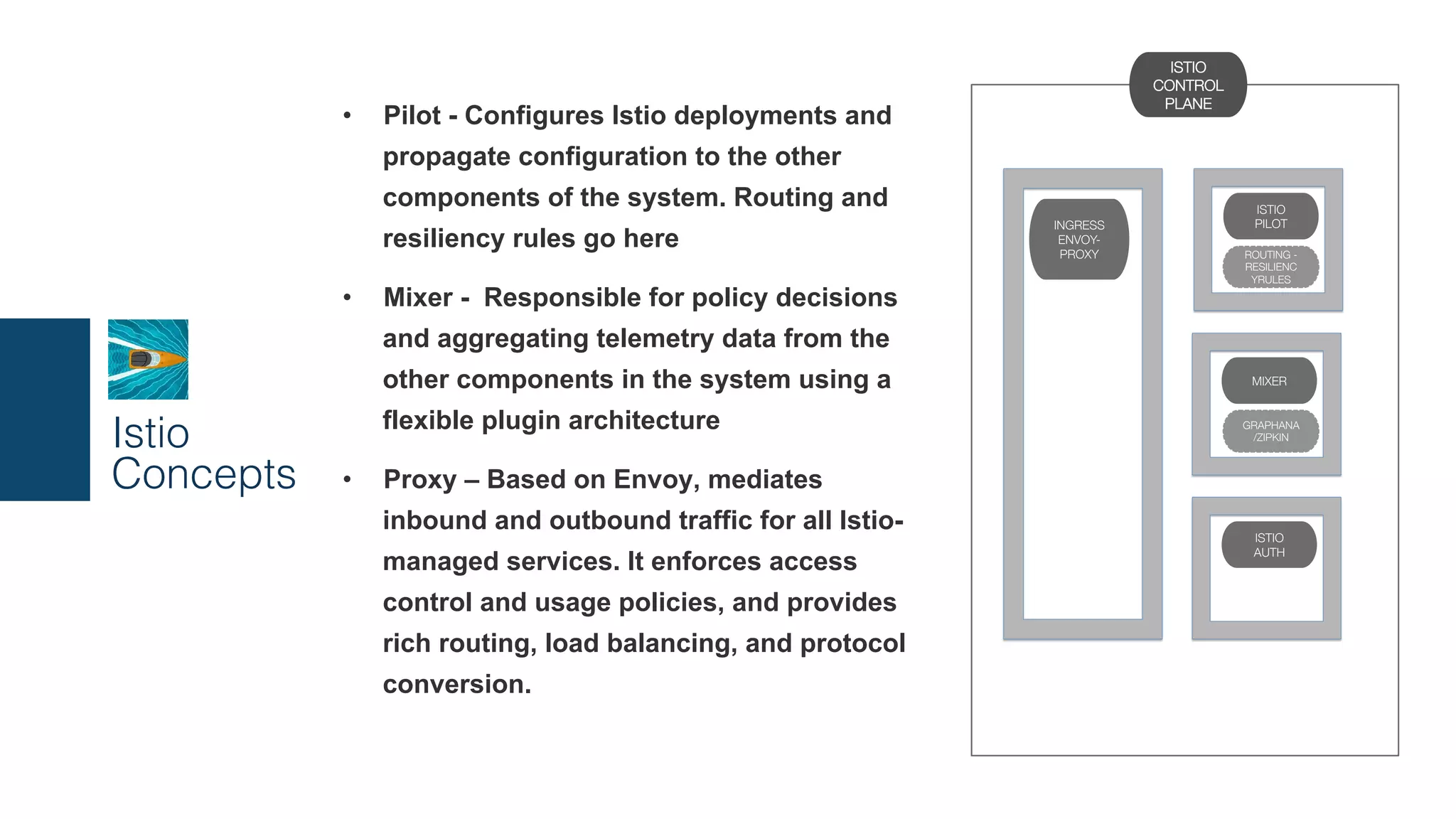
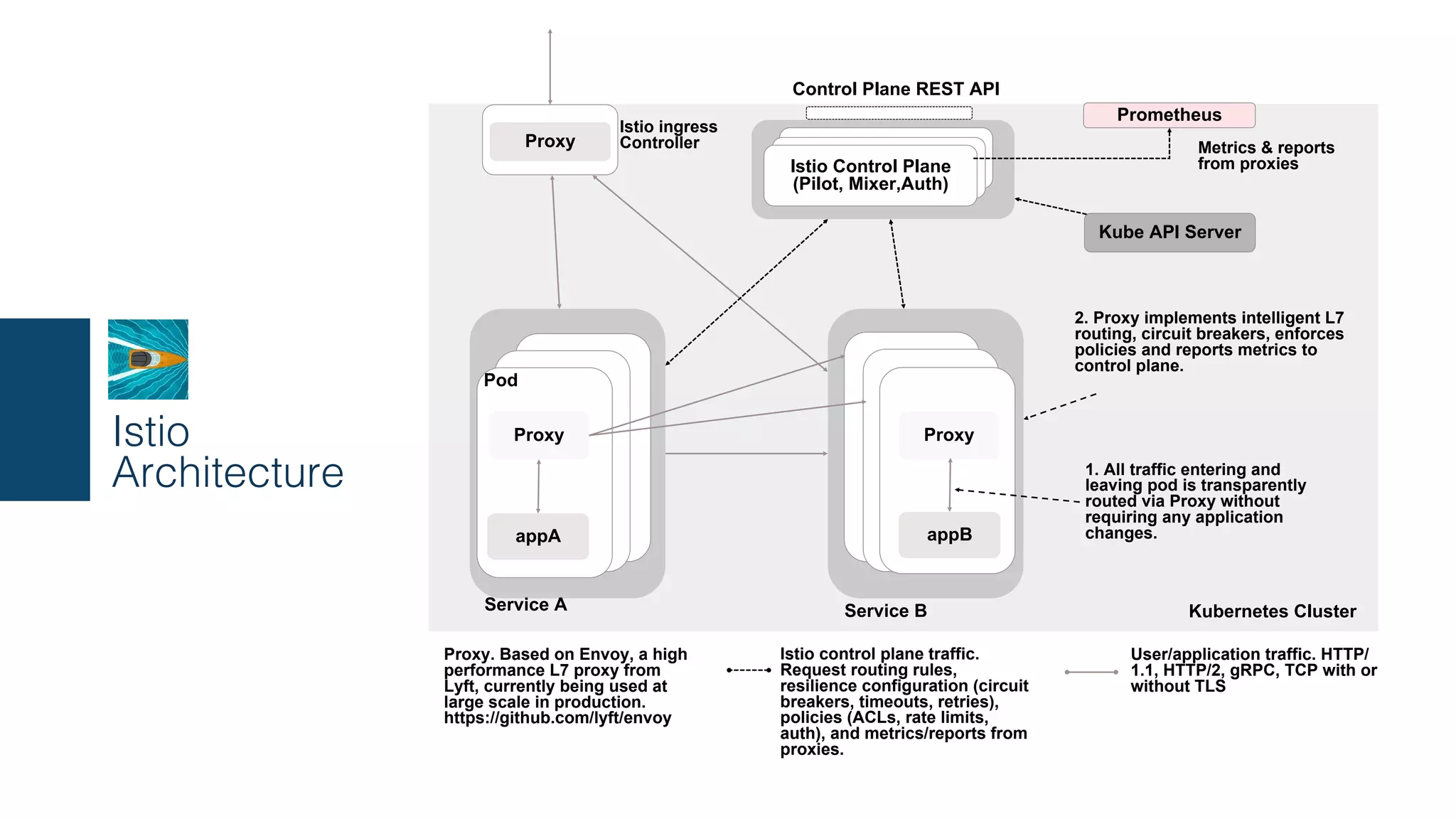
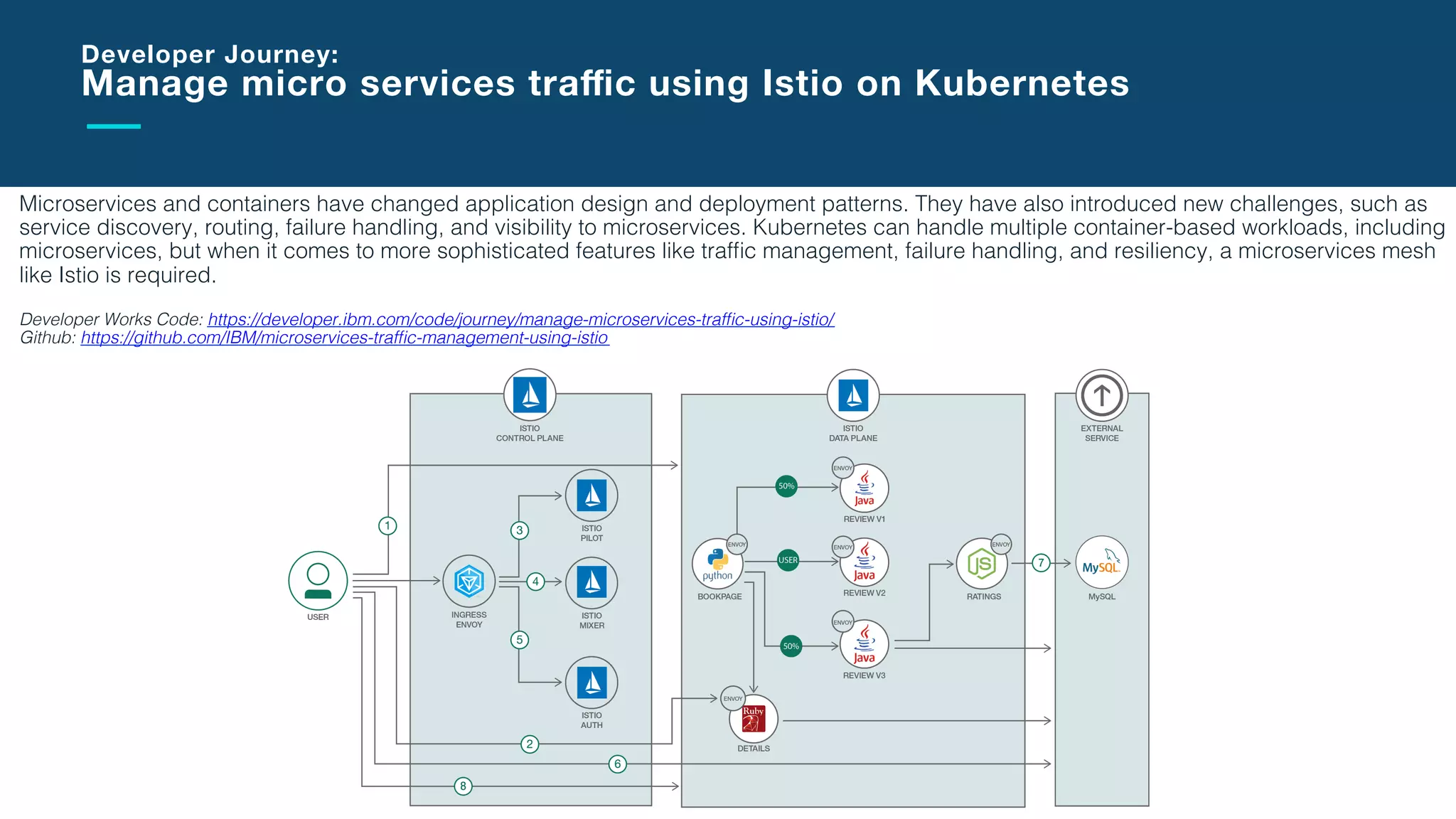
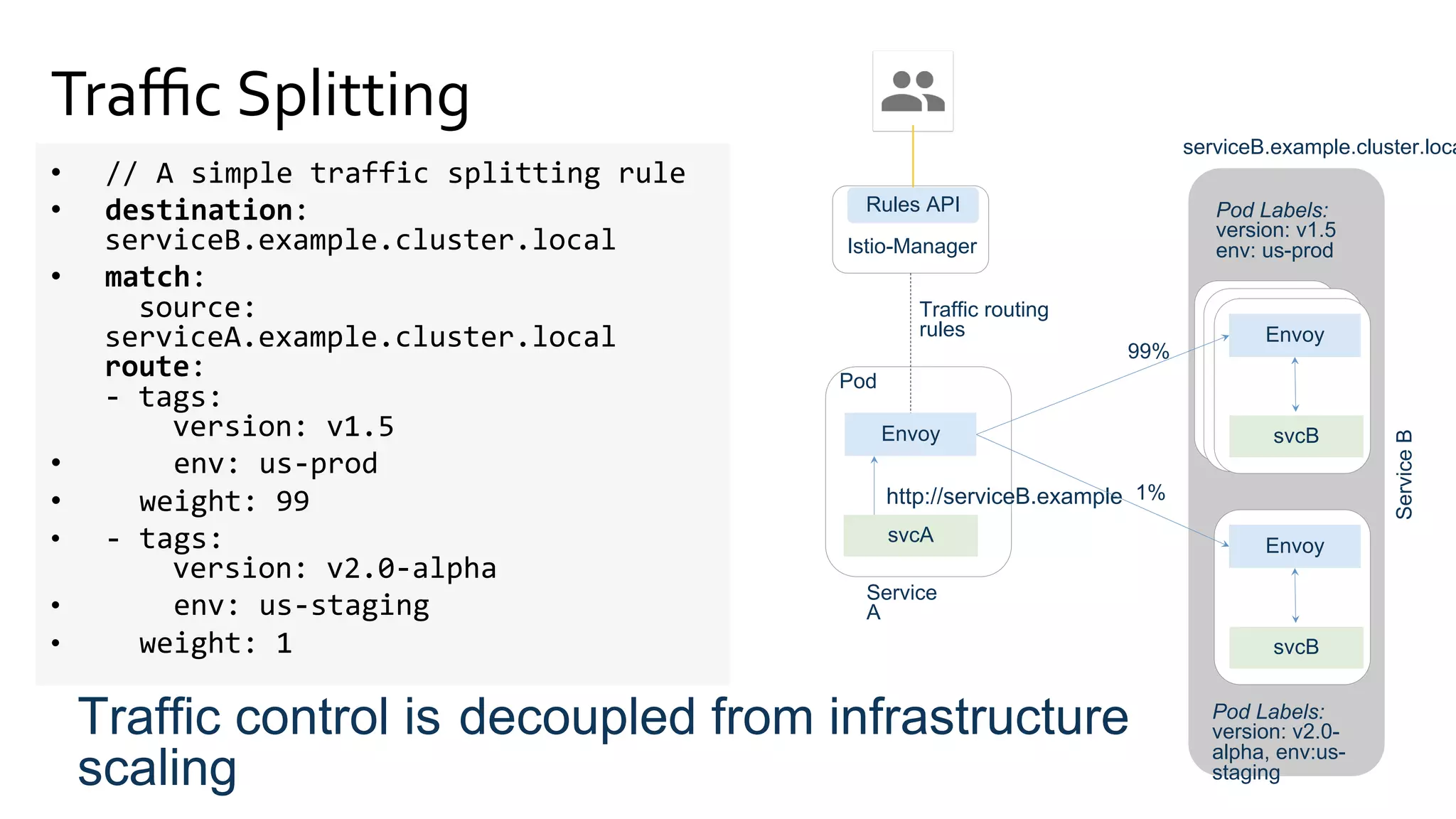
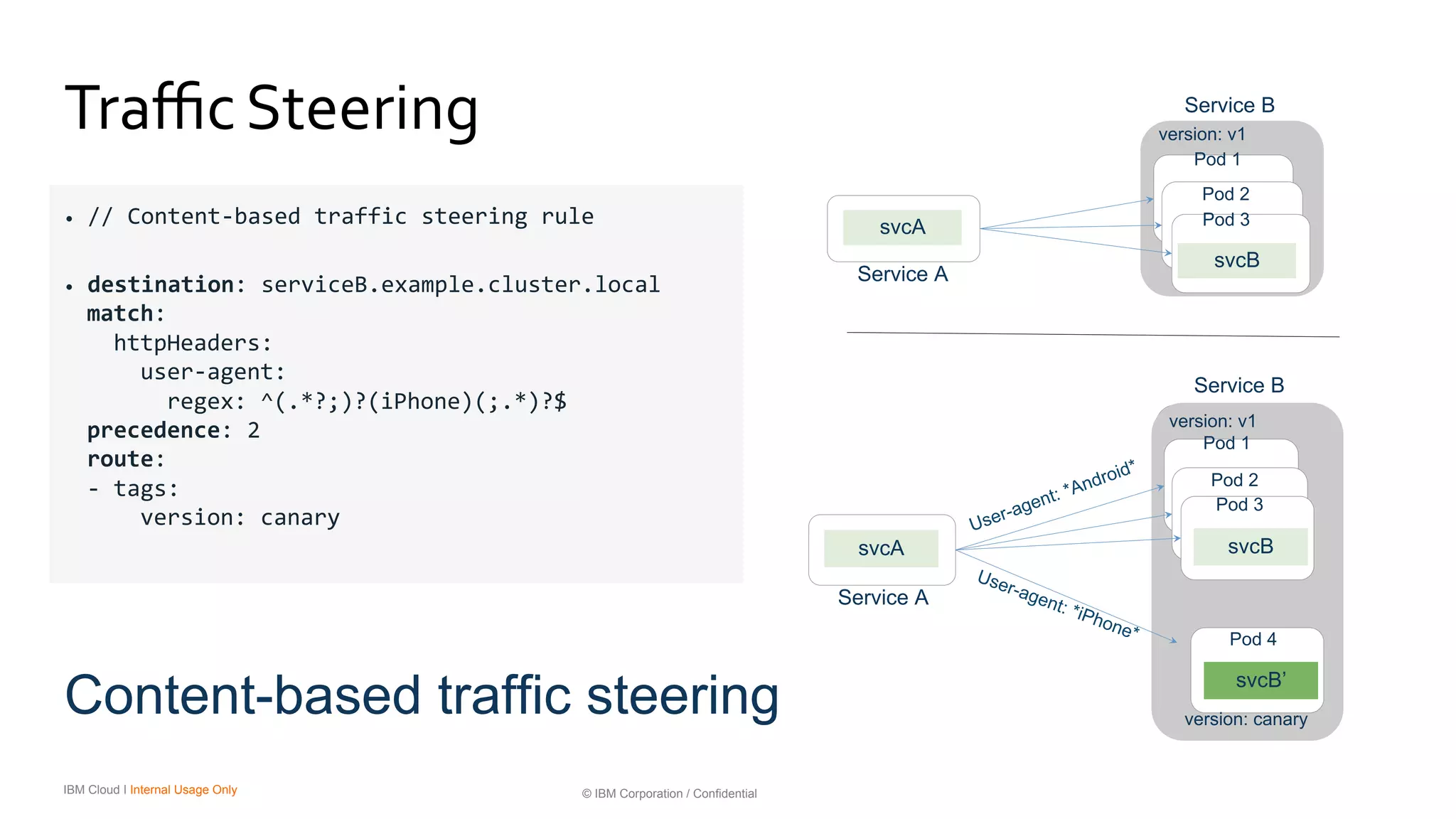
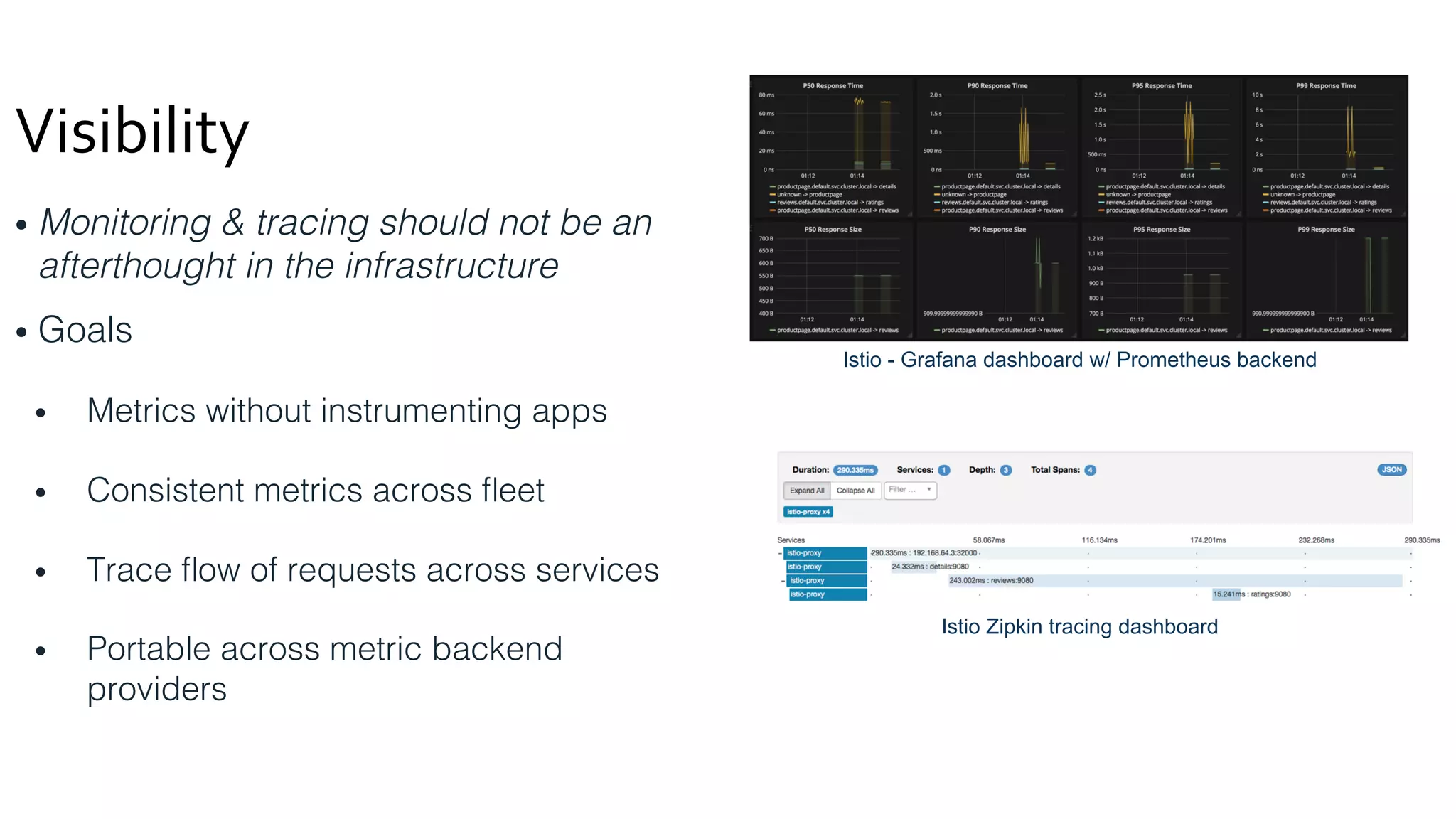
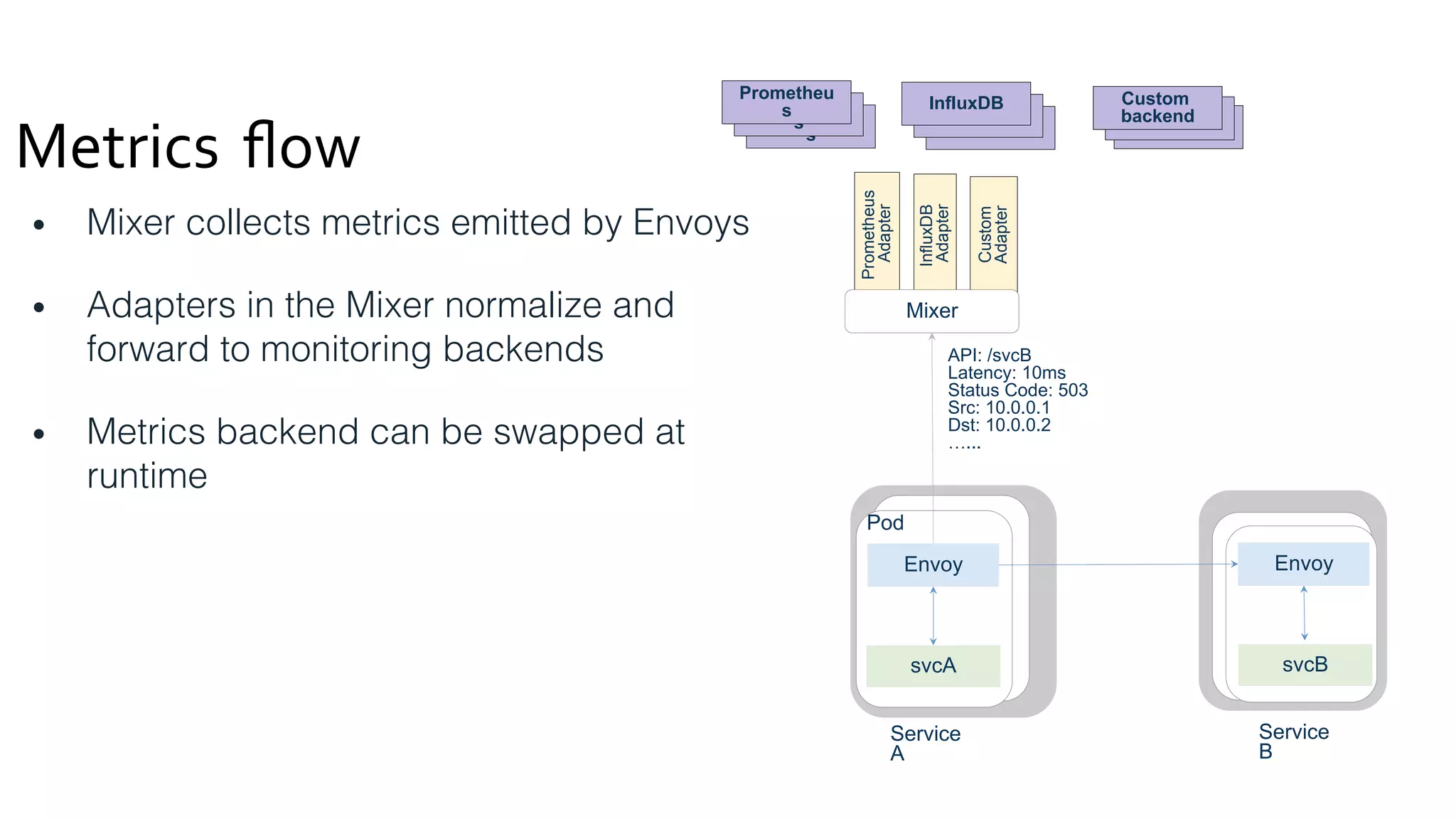
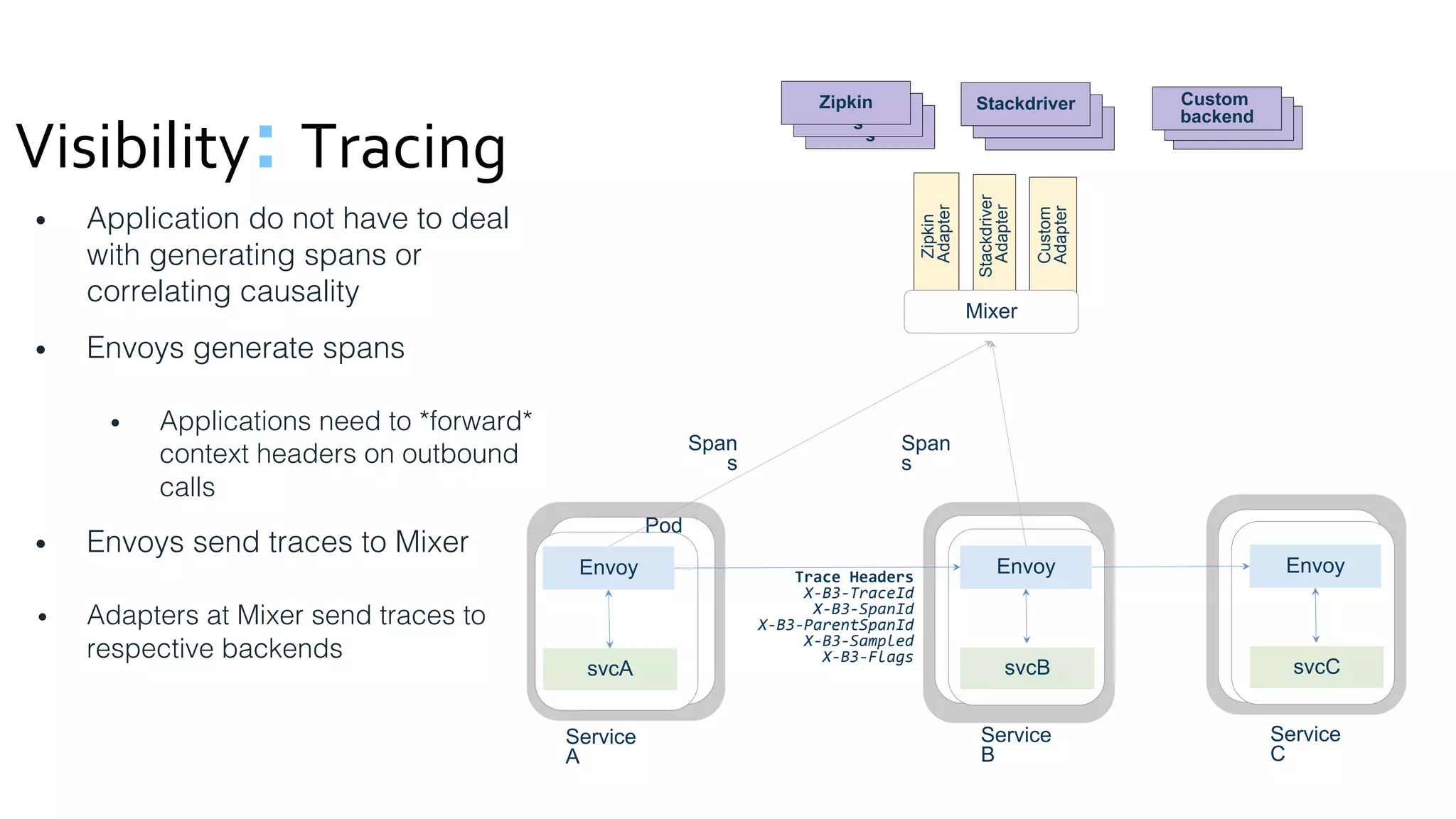
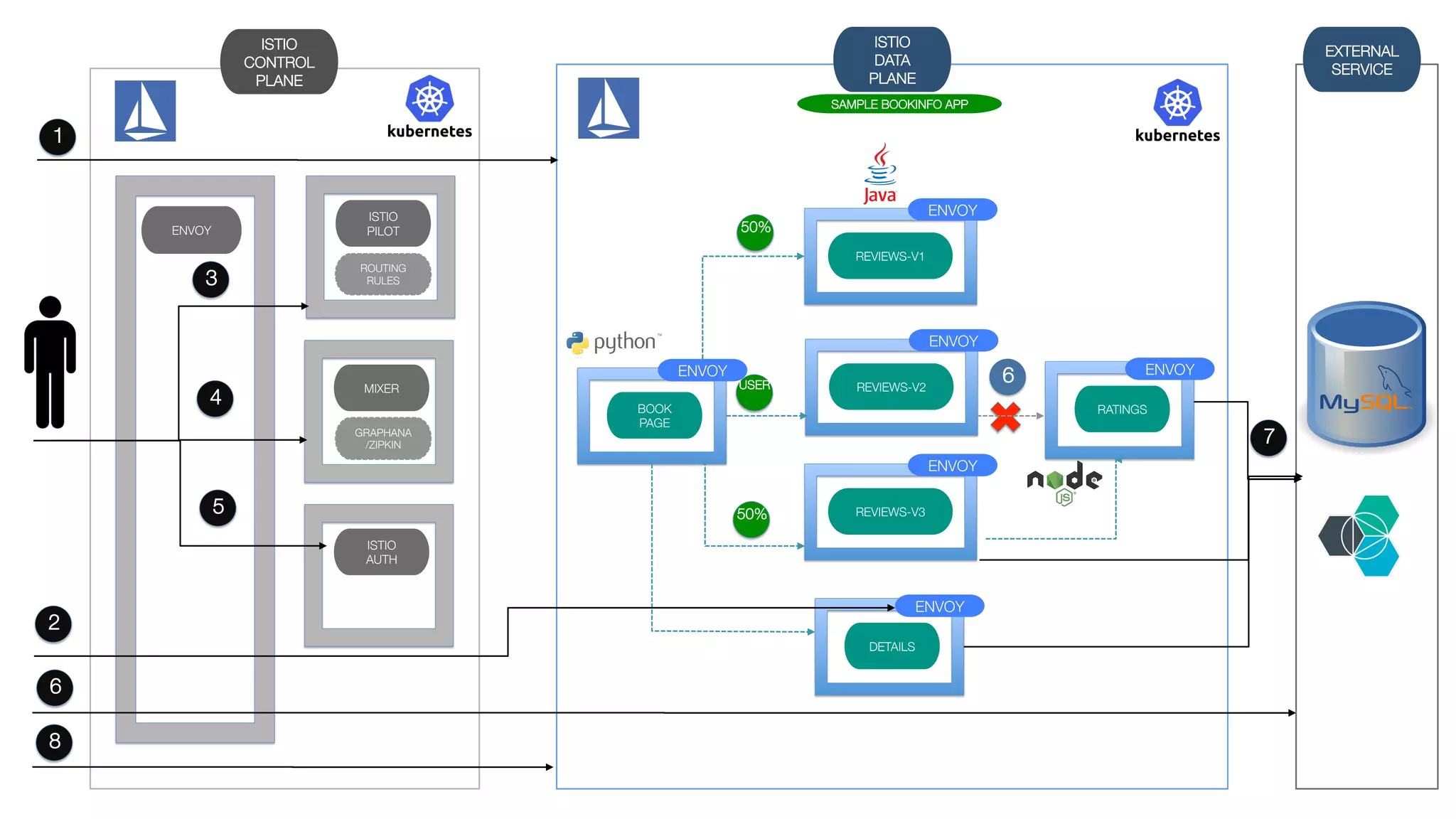
The document discusses the integration of microservices with Kubernetes and Istio, emphasizing the importance of container orchestration and service meshes for efficient service management. It outlines the architecture of Kubernetes and details on how Istio enhances microservices with features like traffic control, resilience, and visibility. Additionally, it provides links to developer journeys and examples for deploying various applications on Kubernetes.