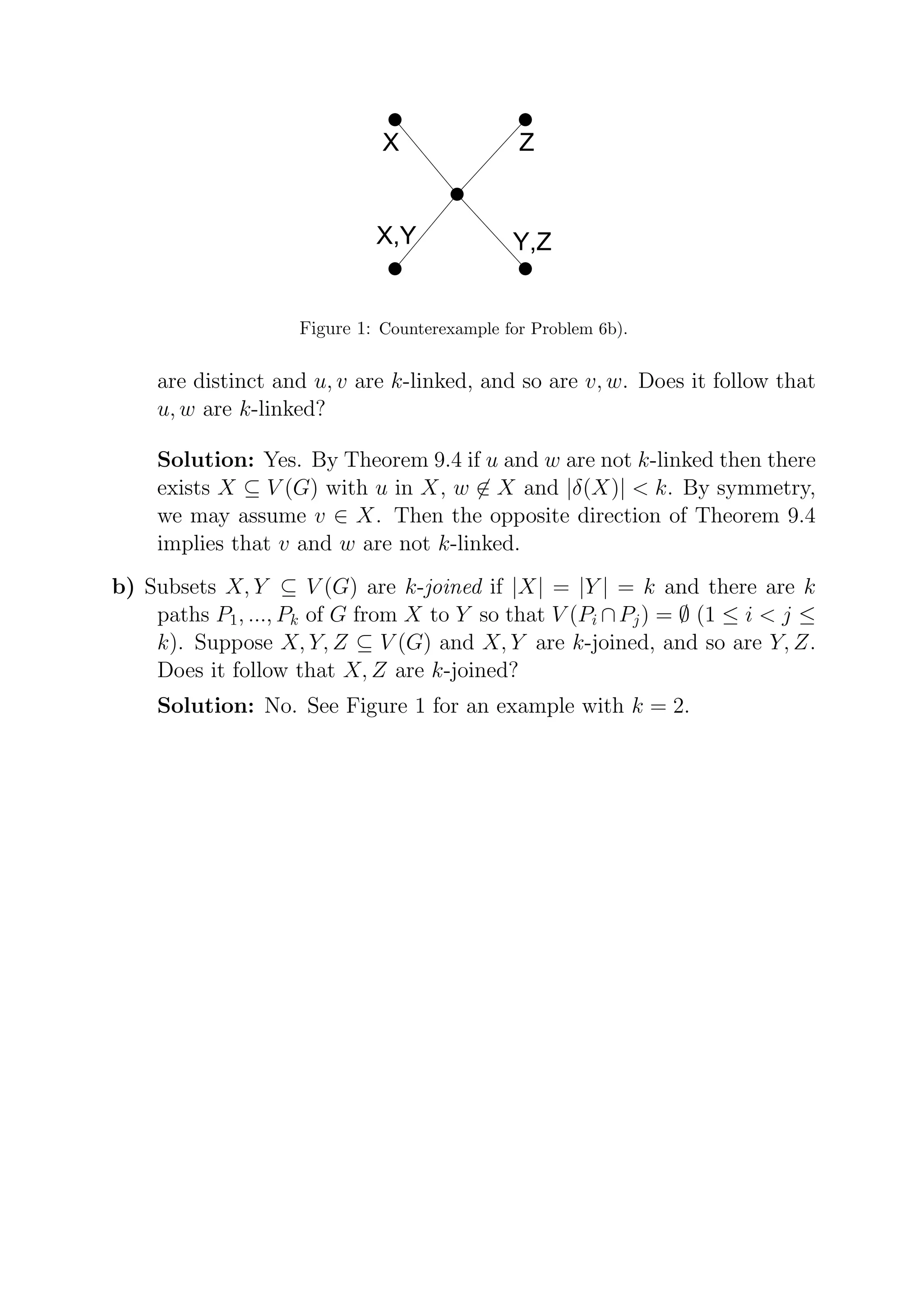
This document contains solutions to problems in graph theory and combinatorics from a course assignment. It addresses questions about bipartite graphs, matchings, connectivity, and more. The problems cover topics like showing a graph is bipartite based on independent sets, determining the size of maximum matchings, existence of matchings covering subsets of vertices, and conditions for when edges lie on common cycles. Counterexamples are provided for some statements about linking and joining vertices and subsets.