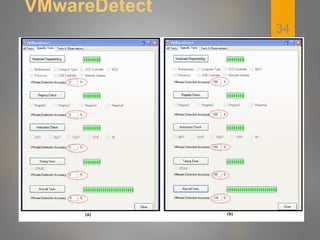
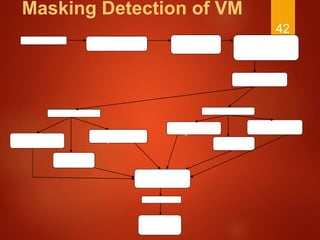
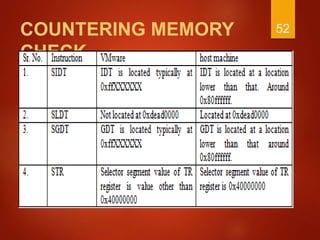
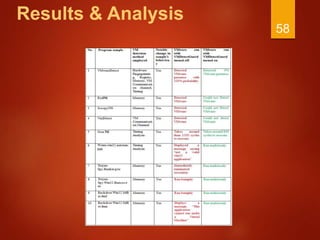
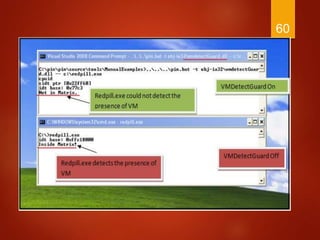
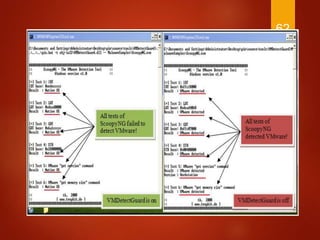
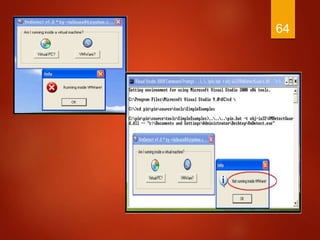
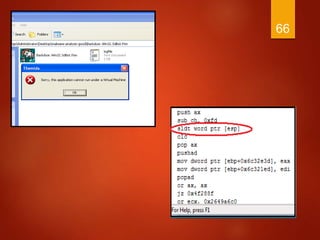
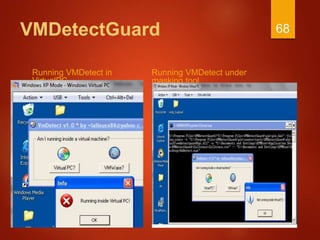
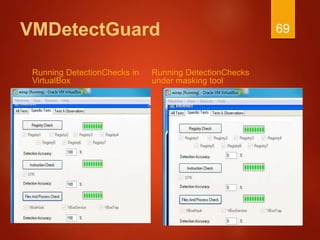
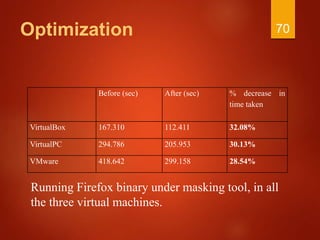
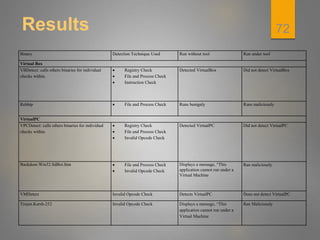
The document discusses techniques used by malware to detect virtual machines and strategies to prevent such detection. It outlines several techniques malware uses to detect virtual machines, including hardware fingerprinting, registry checks, process/file checks, memory checks, timing analysis, and communication channel checks. It then discusses approaches used by popular virtual machines like VMware, VirtualBox, and VirtualPC. The document proposes developing a tool called VMDetectGuard that would monitor for calls and instructions used in detection and mask the virtual machine's identity by providing false information to tricks malware.