This document by Luigi Capuzzello provides a comprehensive introduction to malware analysis, detailing essential skills and techniques for analyzing modern malware through both static and dynamic analysis. It covers critical tools for network traffic monitoring, file analysis, and behavioral assessment necessary for understanding malware behavior. The text emphasizes the importance of configuring a malware analysis lab and developing a practical toolkit for effective malware forensics.

![Introduction.2
Sommario
Introduction..........................................................................................................................................3
What you will learn..........................................................................................................................3
What you should know.....................................................................................................................3
Basic Static Analysis............................................................................................................................3
Hashing: [winMD5free]...................................................................................................................3
String: [strings].................................................................................................................................3
Packed software [PEiD / exeinfope].................................................................................................4
PE Header [Dependency Walker / PEView / Resource Hacker Tool].............................................5
Basic Dynamic Analysis......................................................................................................................7
Monitor malware activity [procmon / regshot / Process Explorer]..................................................7
Go deep into network traffic.............................................................................................................9
So what the hell can we do ?..............................................................................................................11
Summary............................................................................................................................................11
On the Web.........................................................................................................................................11
About the author.................................................................................................................................12
Other Specification.............................................................................................................................12
Luigi Capuzzello](https://image.slidesharecdn.com/malwareanalysis-140220062046-phpapp01/85/Cutting-out-Malware-2-320.jpg)
![Introduction.3
Introduction.
An email arrives in your inbox; it’s your girlfriend Ann. She invites you to see her in a very funny picture. -Click !“But! What? This picture is not really funny, and …she is not Ann”.
Day by day we store more and more confidential information on our computers, from sites account credentials to our
bank account.
Day by day malware becomes more and more silent, they don’t want you to be suspicious, they just want to stay into
your device to do something …that you don’t want.
What you will learn...
-
Configuring a malware analysis lab
Assembling a really toolkit for malware forensics
Performing behavioral analysis of malicious Windows executables
Performing static and dynamic code analysis of malicious Windows executables
-
What is a PE Header
Knowledge about network protocol
Basic knowledge about windows registry and processes
What you should know...
Basic Static Analysis.
Static Analysis describes the process of analyzing the code and the structure of a program to determine its main
feautures.
In this phase of your analysis the program itself is not running; we are just analyzing a file, a sequence of bytes.
We have to find as many information as possible. All the information, even the ones apparently trivial, are actually
extremely important, above all when you go deep into the malware analysis
You can find several tools to implement static analysis but just a few of them are really interesting.
In the next section I will describe all the most juicy tools and I show to you how you can use them.
Hashing: [winMD5free].
First of all it could be a good idea to get the a fingerprint of the malware.
Hashing is a common method used to uniquely identify malware; the Message Digest Algorithm 5 (MD5) and Secure
Hash Algorithm (SHA-1) are the method most commonly used.
For example we can use winMD5Free to get the hash and then we can search for it online.
If the malware is a well known one you will find all about it; if you know what malware is able to do then it can not
hurt you anymore.
This is an example of winMD5Tool; it can calculate MD5 Hash of a particular program
Once you have the identity card of the malware you can use it on google to discover all about it.
String: [strings].
Another method to find some usefull hints about a malware is to get all the strings from the malware
Luigi Capuzzello](https://image.slidesharecdn.com/malwareanalysis-140220062046-phpapp01/85/Cutting-out-Malware-3-320.jpg)
![Introduction.4
Strings program can anlyze a file to extract both ASCII and UNICODE (indeed the windows implementation of unicode
string also well-known as wide character string); this program ignore the context and formatting, it just analyze all the
bytes one by one. Because of this mechanism it could be find characters or strings when they are not.
You can use strings from command line:
E:>strings.exe Lab01-01.exe
Strings v2.51
Copyright (C) 1999-2013 Mark Russinovich
Sysinternals - www.sysinternals.com
!This program cannot be run in DOS mode.
Richm
.text
`.rdata
@.data
_^[
UVWj
@jjj
D$0
_controlfp
_stricmp
kerne132.dll
Kernel32.
Lab01-01.dll
C:WindowsSystem32Kernel32.dll
WARNING_THIS_WILL_DESTROY_YOUR_MACHINE
Error Messages and IP addresses are the most interesting information we can found on a file.
In the above example I have highlighted some important strings
Packed software [PEiD / exeinfope]
Sometime the malware we are analyzing could be packed. This is a problem because the packer hide us a lot of
information, so that static analysis becomes almost useless.
There are many software that could help us to find the packer used. For example:
PEiD: it is a detector for PE (Portable Executable - Exe/Dll) files, similar to an anti-virus except it detects what
a file is, not what it does.
Mostly it detects packer and protector programs like UPX, PECompact, Armadillo etc but has a customisable
database to add your own detections
Be careful because of this has been disconnected from April 2011 and because many PEiD plugins will run the
executable without warning. Despite of this, it is the best tool available for packer detection.
-
exeinfope is another good tool.
Here is an example of PEiD interface
Luigi Capuzzello](https://image.slidesharecdn.com/malwareanalysis-140220062046-phpapp01/85/Cutting-out-Malware-4-320.jpg)
![Introduction.5
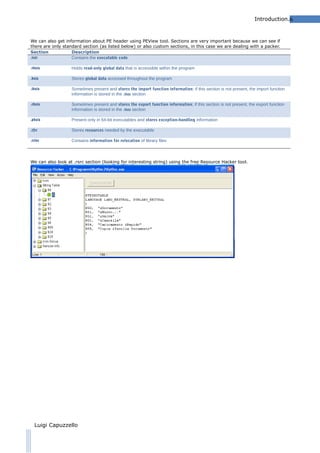
PE Header [Dependency Walker / PEView / Resource Hacker
Tool]
PE Header can give us many information about executable behaviuor.
Using Dependency Walker program we can find information about:
dinamically linked functions;
imported dll;
For example in the above image, at pane 3, we can find all the imported function of the kernl32.dll. If we know which
function are used, we can deduce the malware behavior.
There is also a way to import function ‘on the fly’, using some important function:
LoadLibrary
GetProcAddress
LdrGetProcAddress
LdrLoadDll
So if you find this functions, it means that the malware is going to hide you what is its intention. If you want to
understand more in details its behavior you have to debug it (but this is a story that will relate you another time).
As just said, we can find information about the all dll imported into the executable file and each of them can tell us
something.
Dll
Description
Advapi32.dll
This DLL provides access to the Service Manager and Registry.
User32.dll
This DLL contains all the user-interface components, such as buttons, scrollbars, and
components for controlling and responding to user actions.
Gdi32.dll
This DLL contains functions for displaying and manipulating graphics
Kernel32.dll
This is a very common DLL that contains core functionality, such as access and manipulation of
memory, files, and hardware.
Shell32.dll
Tell us that the program can launch other program.
Ntdll.dll
This DLL is the interface to the Windows kernel. Executables generally do not import this file
directly, although it is always imported indirectly by Kernel32.dll. If an executable imports this file,
it means that the author intended to use functionality not normally available to Windows
programs. Some tasks, such as hiding functionality or manipulating processes, will use this
interface.
WSock32.dll - Ws2_32.dll
These are networking DLLs. A program that accesses either of these most
likely connects to a network or performs network-related tasks.
Wininet.dll
This DLL contains higher-level networking functions that implement protocols such as FTP,
HTTP, and NTP.
Luigi Capuzzello](https://image.slidesharecdn.com/malwareanalysis-140220062046-phpapp01/85/Cutting-out-Malware-5-320.jpg)
![Introduction.7
Basic Dynamic Analysis.
Dynamic analysis techniques are the second step in the malware analysis process. Dynamic analysis is typically
performed after basic static analysis has reached a dead end, whether due to obfuscation, packing, or the analyst
having exhausted the available static analysis techniques.
Monitor malware activity [procmon / regshot / Process Explorer]
Process Monitor, or procmon, is an advanced monitoring tool for Windows that provides a way to monitor certain
registry, file system, network, process, and thread activity. It combines and enhances the functionality of two legacy
tools: FileMon and RegMon.
If you want to filter the activity of a particoular file you have to choose the “Filter Filter” Menu option and you have
to spacify the filename you are looking for.
There are also four important filter on the menu side bar that allow to filter:
Registry
File system
Process activity
Network: attention this logging not work consistently across Microsoft Windows version.
It is very usefull to use promon because it is very usefull to know what our target is doing with the external
environment (registry, file system and network).
Sometime our target generates many operation especially on registry. So it could be very usefull to have a tool that
compare two snapshots and give us just the differences between them.
Regshot is an open source registry comparison tool that allows you to take and compare two registry snapshots.
It is very simple to use regshot. There are only three operation you have to do:
Click on ‘1st shot’ button;
Execute malware ;
Click on ‘2nd shot’ button when you think malware has finished its activity
Click on ‘cOmpare’ button
At the end the software will give you a list of the operations the malware has implemented on the registry.
This type of information could be very usefull because it is not a simple log, it is an elaborated one.
Here is an example of the regshot output:
====================================================================
Regshot 1.9.0 x86 ANSI
Comments:
Datetime: 2014/2/1 21:12:14 , 2014/2/1 21:13:07
Computer: TESTXP , TESTXP
Username: admin , admin
---------------------------------Keys added: 1
---------------------------------HKUS-1-5-21-725345543-73586283-682003330-1003SoftwareMicrosoftMultimediaWaveOwner
---------------------------------Values added: 19
Luigi Capuzzello](https://image.slidesharecdn.com/malwareanalysis-140220062046-phpapp01/85/Cutting-out-Malware-7-320.jpg)




![Introduction.12
●
●
●
●
●
http://sourceforge.net/projects/regshot/ - regshot tool
http://technet.microsoft.com/en-gb/sysinternals/bb896653.aspx - Process Explorer tool
https://www.mandiant.com/resources/download/research-tool-mandiant-apatedns - ApateDNS tool
http://www.inetsim.org/downloads.html - INetSim tool
http://www.wireshark.org/download.html - wireshark tool
About the author
Luigi Capuzzello has started with informatics in late 1986 (with a beautiful Apple IIe) when he was thirteen years old.
After taking a degree in robotics he has working for more than fifteen years in several areas of IT, but now he is strong
focused on IT security.
His main tasks are related to test applications safety (especially web application) and in reverse engineering
techniques.
Specialties: Project Managment, Information Security, Vulnerability Analysis, Penetration Testing, Ethical Hacking, Web
Application Security
You can find him on http://www.linkedin.com/pub/luigi-capuzzello/7/561/12a
Other Specification
- Malware Analyst's Cookbook and DVD: Tools and Techniques for Fighting Malicious Code [Paperback]
- The Hands-On Guide to Dissecting Malicious Software
by Michael Sikorski and Andrew Honig
Luigi Capuzzello](https://image.slidesharecdn.com/malwareanalysis-140220062046-phpapp01/85/Cutting-out-Malware-12-320.jpg)