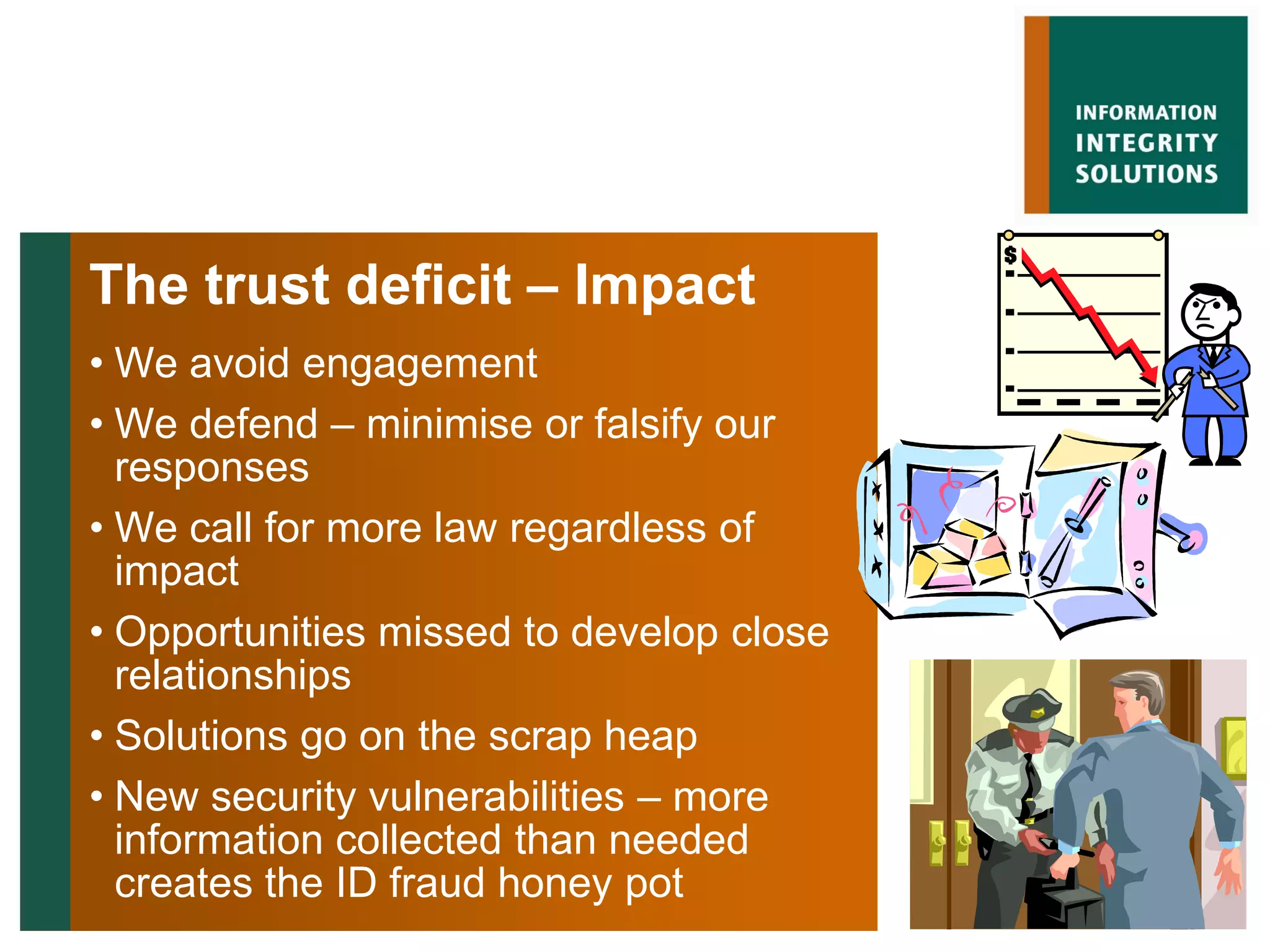
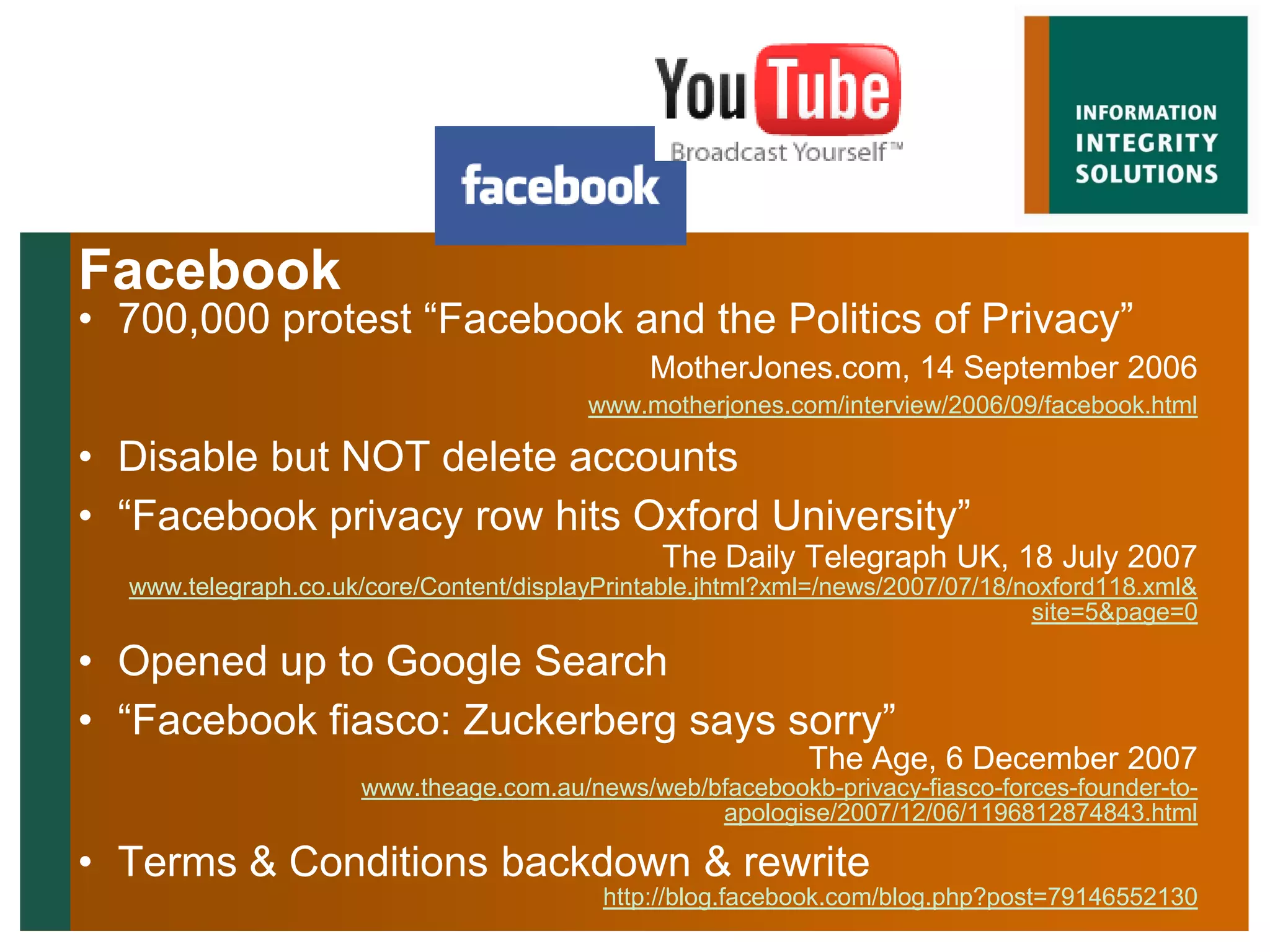
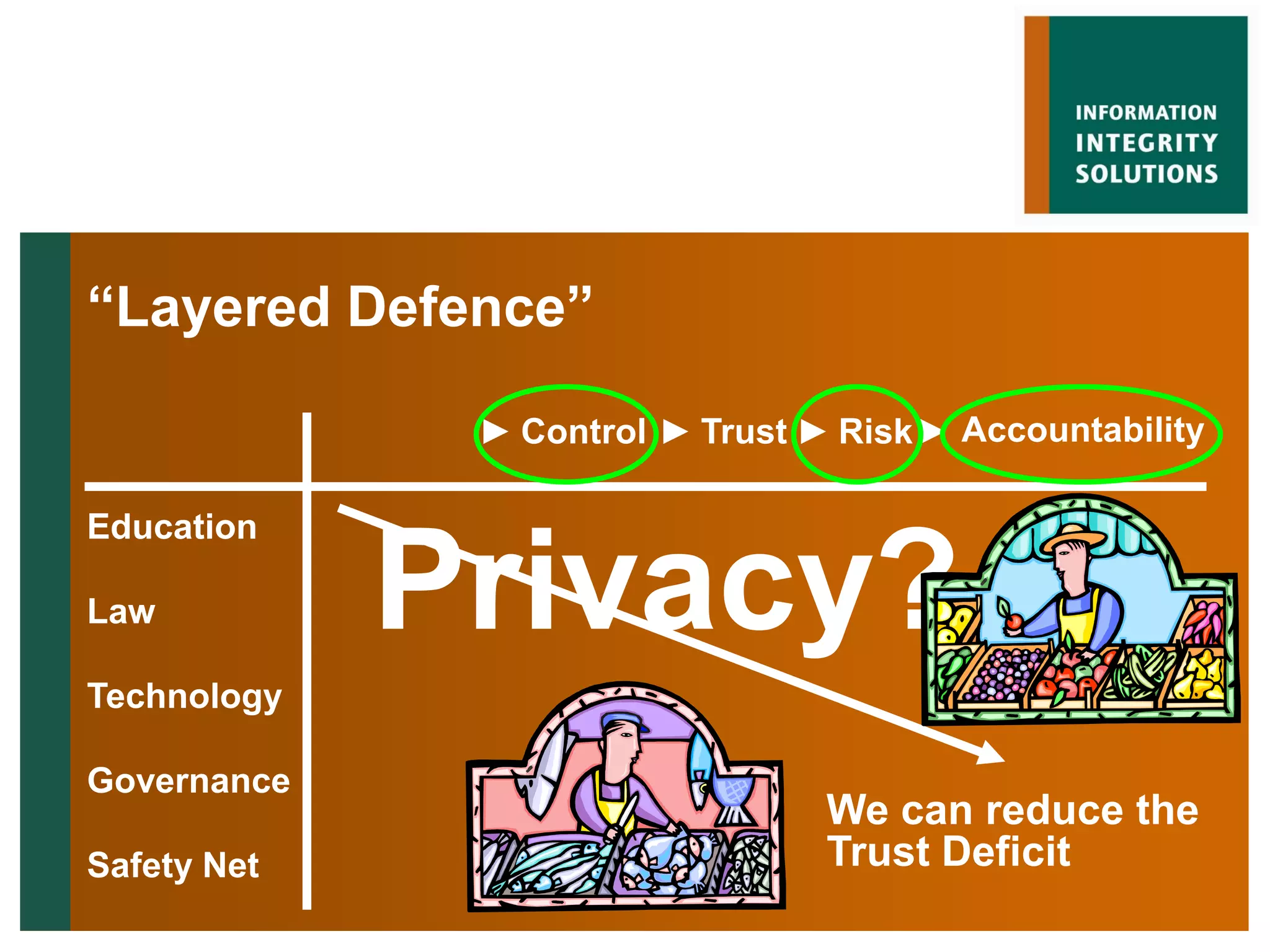
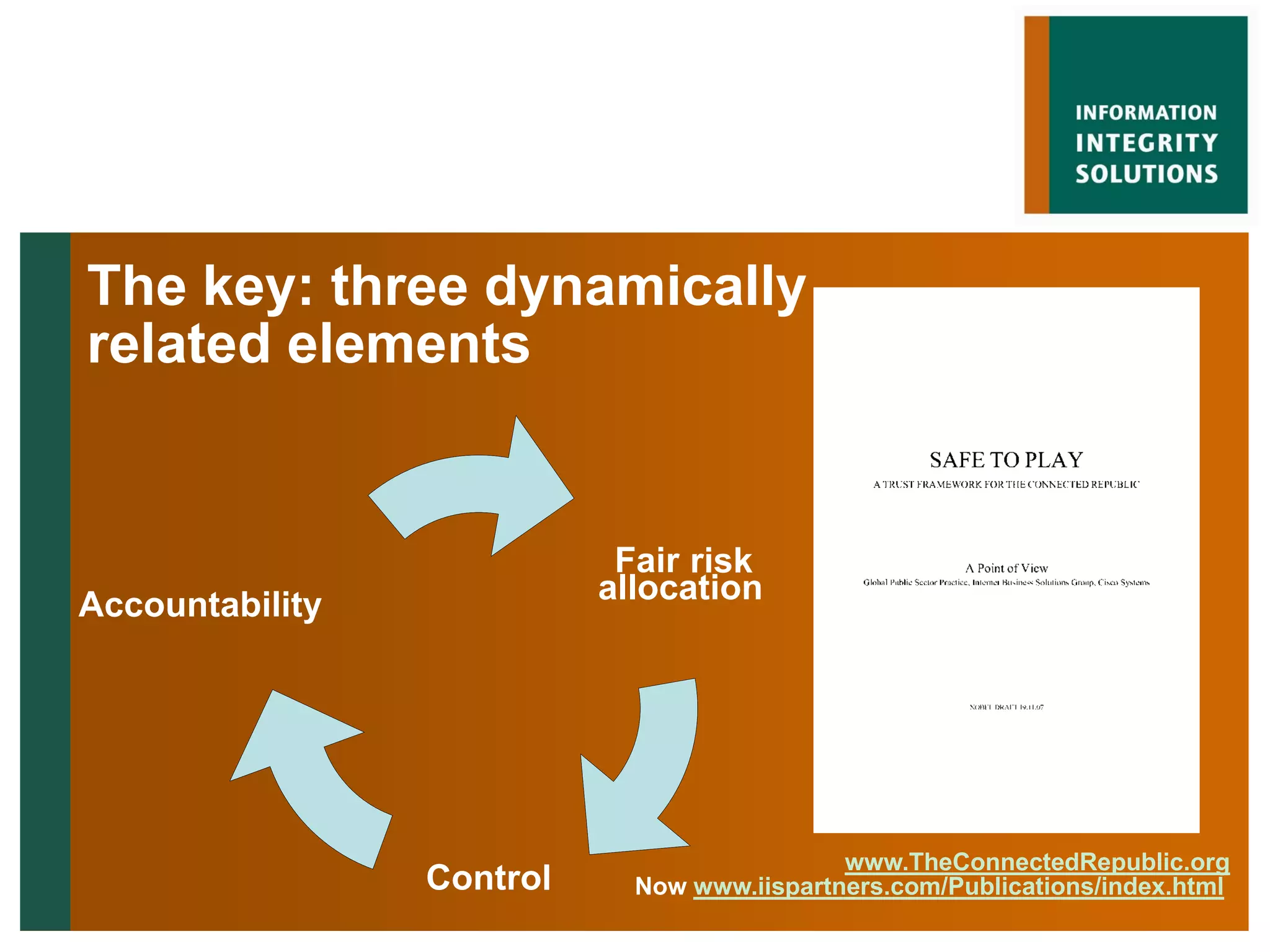
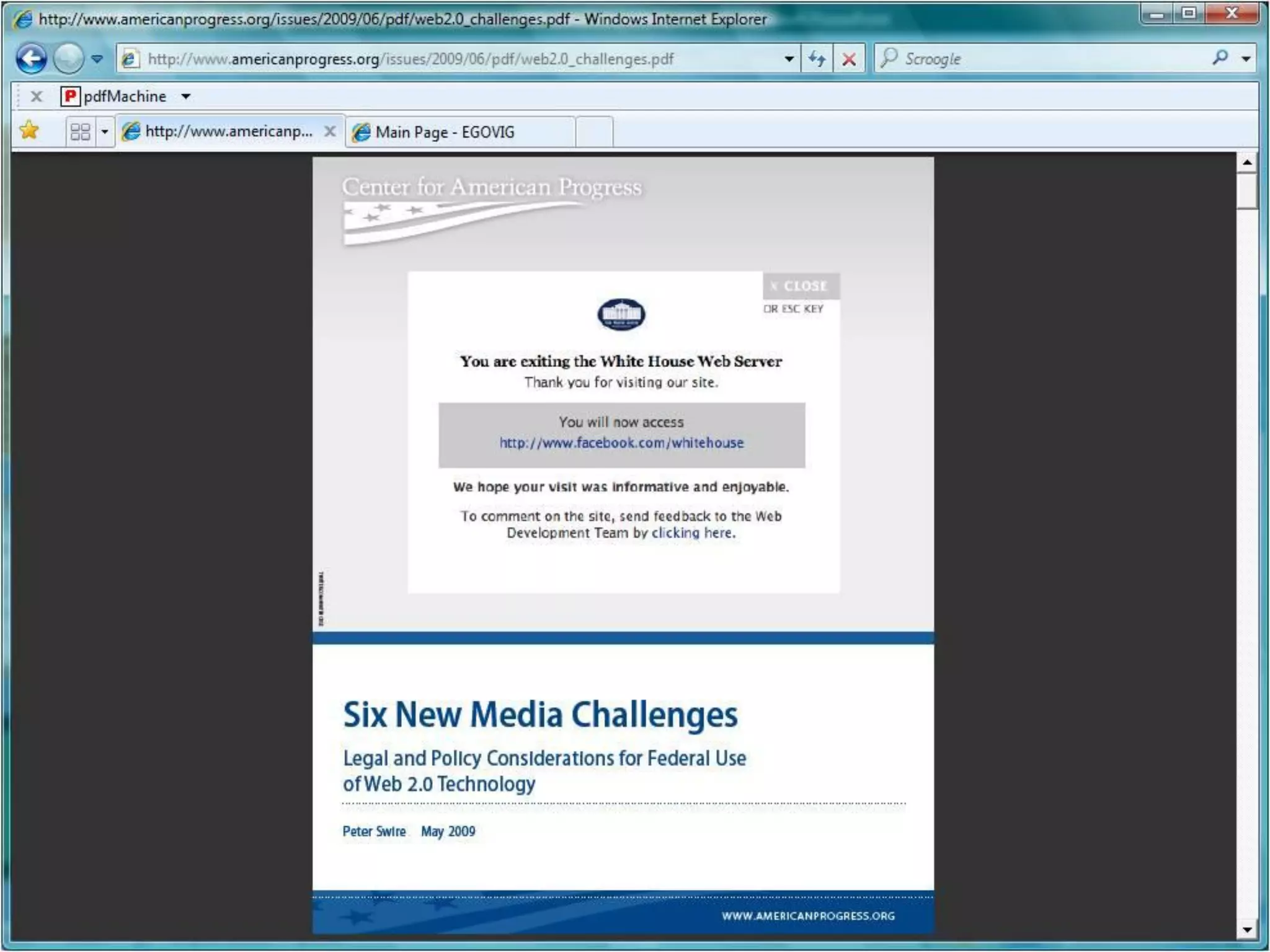
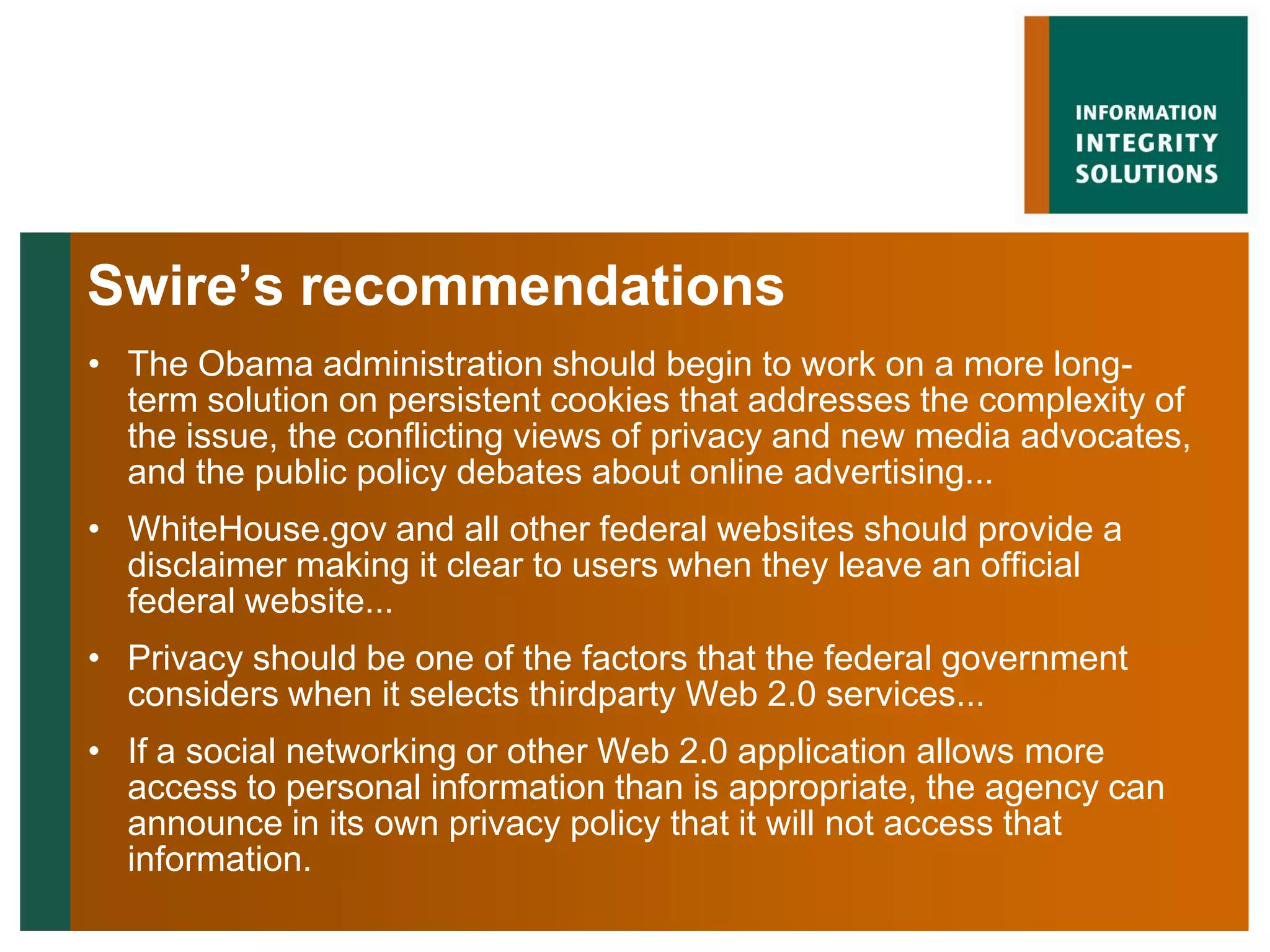
Malcolm Crompton presented at the Web 2.0 in Government conference in 2009. He discussed the inherent challenge for governments in balancing their roles as service providers and regulators. His presentation addressed the key issue of privacy and building trust between governments and citizens in the digital age. Crompton examined past failures like Australia's Access Card and strategies for a "layered defense" approach using education, law, technology, governance and safety nets to reduce the trust deficit between governments and those they serve.