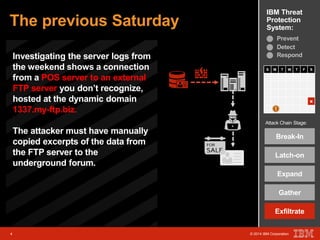
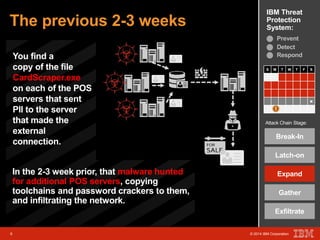
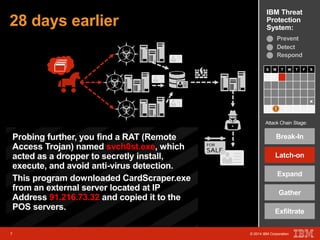
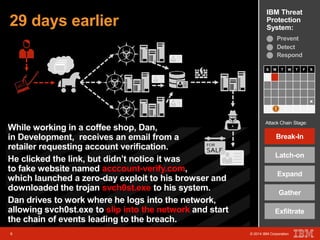
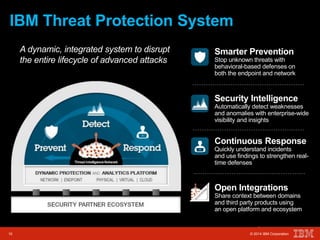
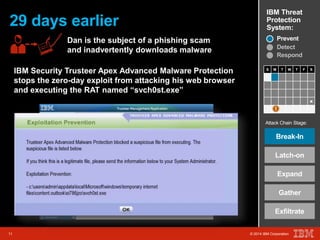
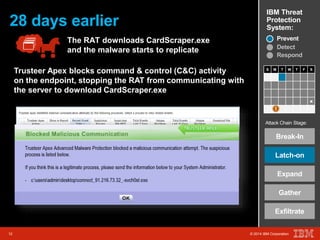
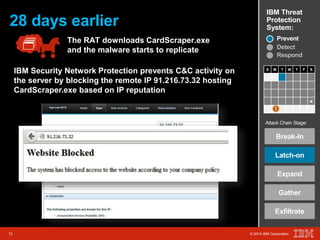
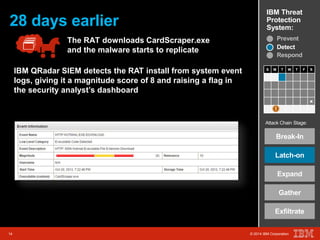
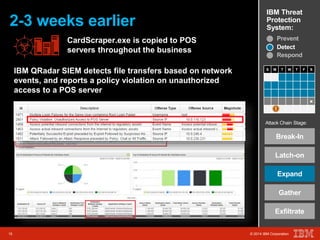
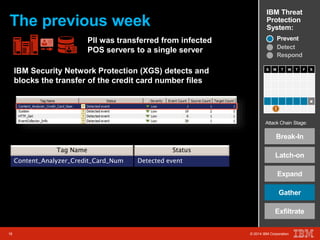
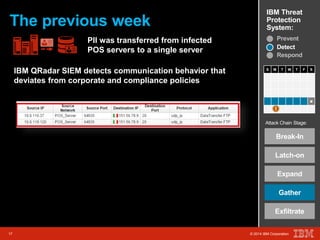
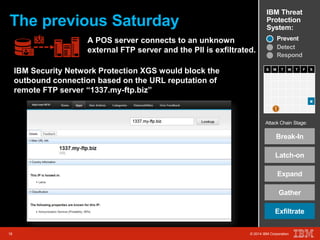
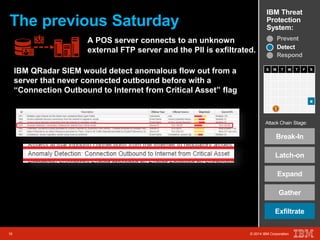
The document outlines a scenario involving a security breach at a global retail corporation, managed by an IT security manager facing a data exfiltration incident that includes credit card information. It details the attack's progression, highlighting how malware infiltrated the point of sale systems and the subsequent investigative measures taken to identify the breach's origin. Additionally, it emphasizes the importance of proactive threat management and advanced prevention techniques to mitigate such attacks, including behavioral-based defenses and incident response services offered by IBM.