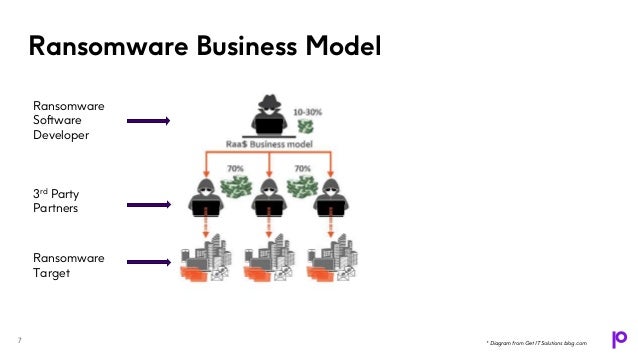
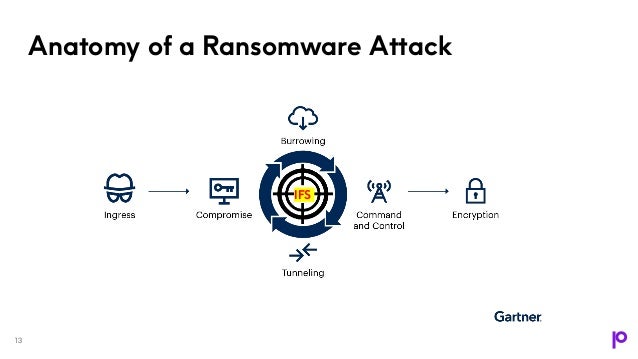
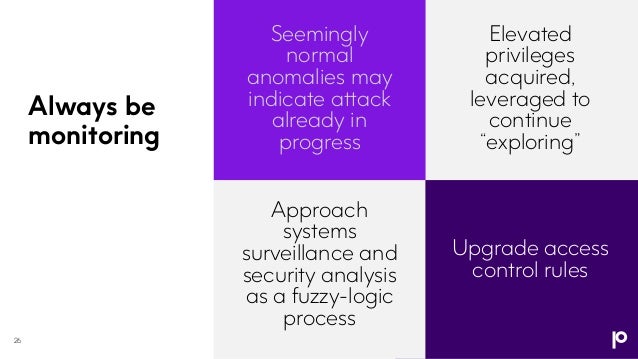
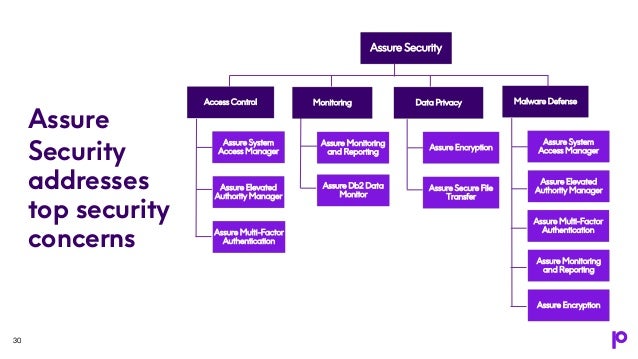
The webinar discusses the evolving landscape of malware threats targeting IBM i systems, emphasizing the need for a multi-layered security approach. It underlines that traditional security practices are insufficient and that organizations must adapt to sophisticated attack methods, including ransomware as a service. Key strategies include advanced multi-factor authentication, continuous monitoring, and integration of security across platforms to protect sensitive data effectively.