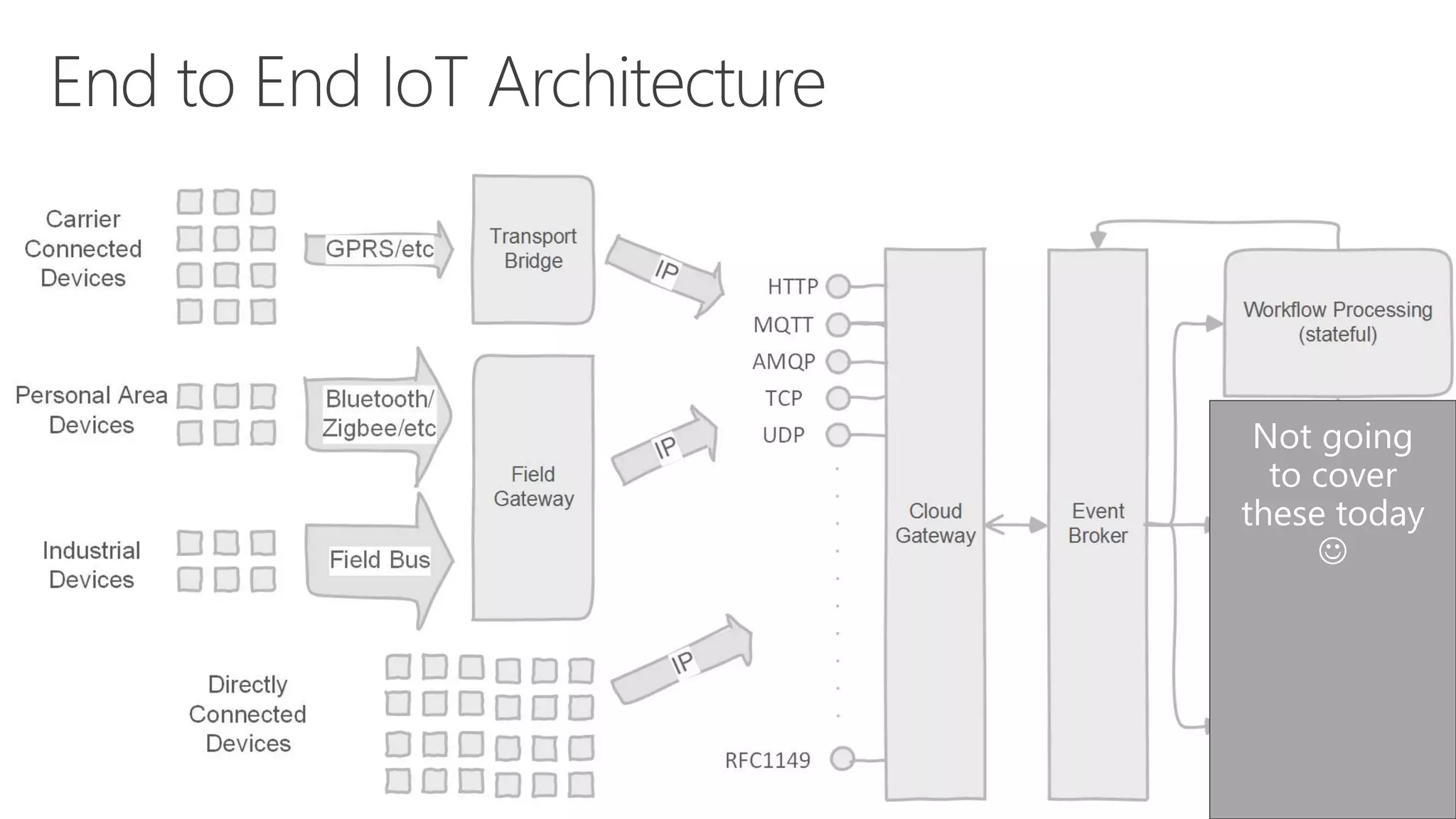
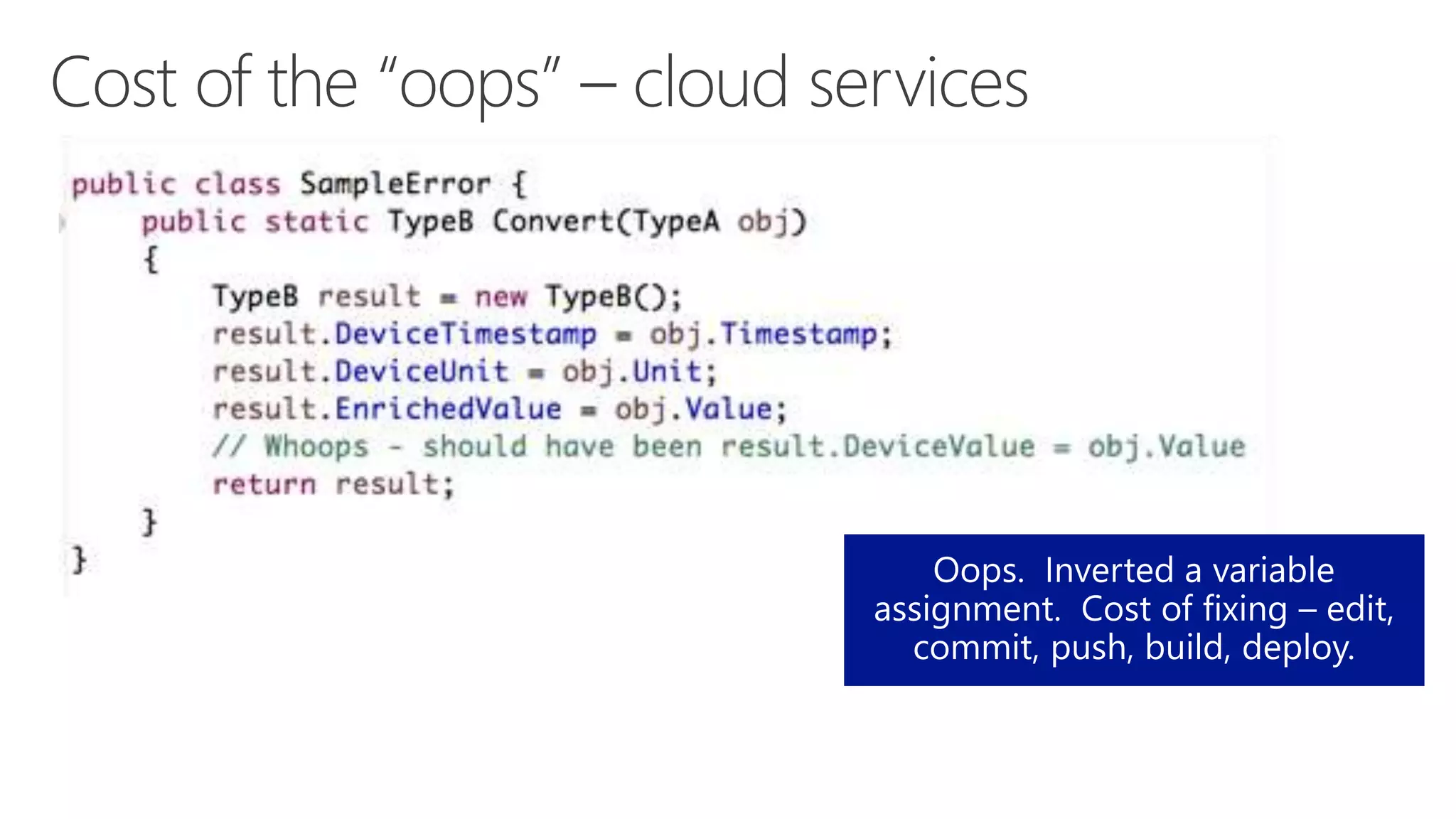
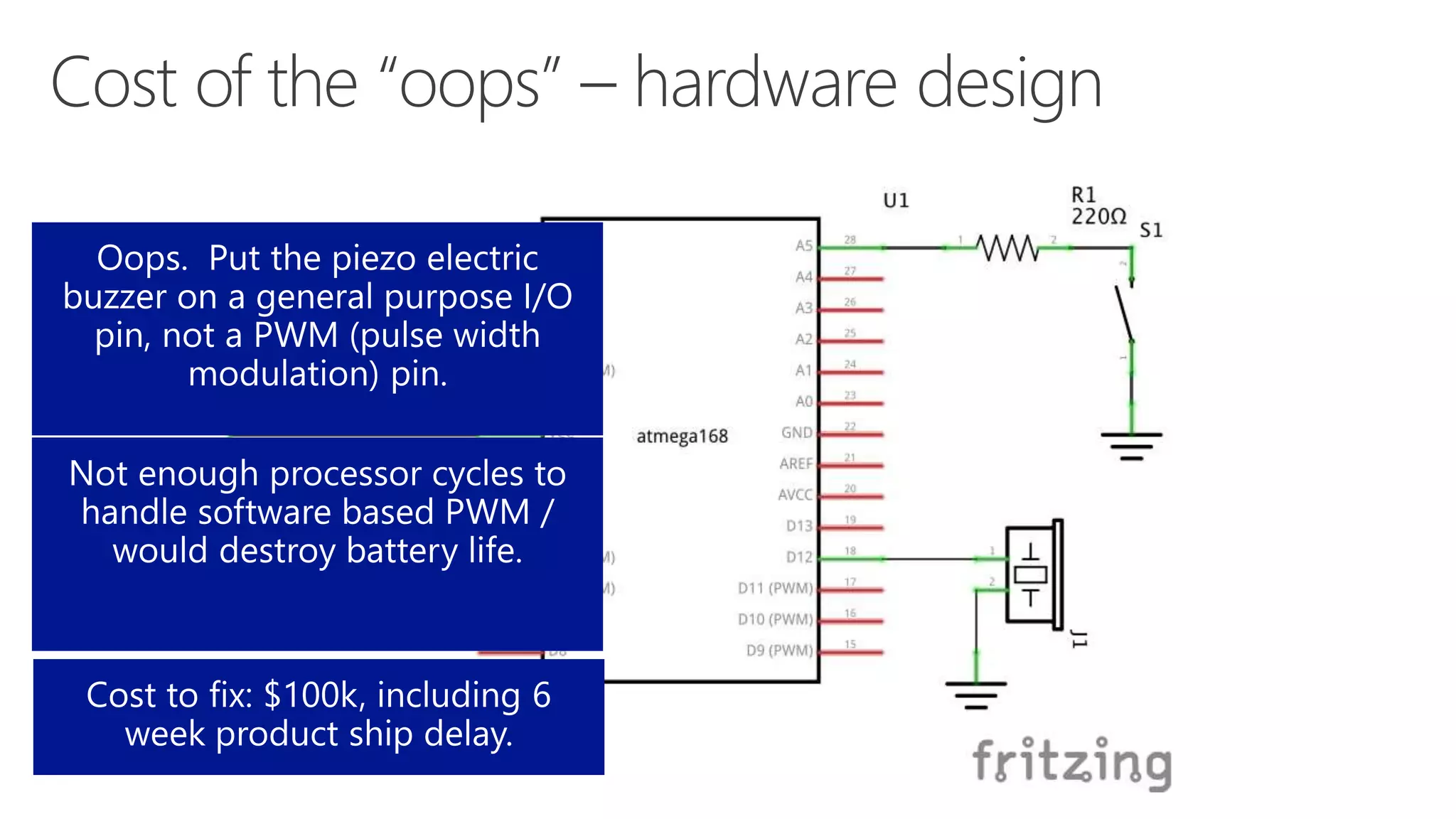
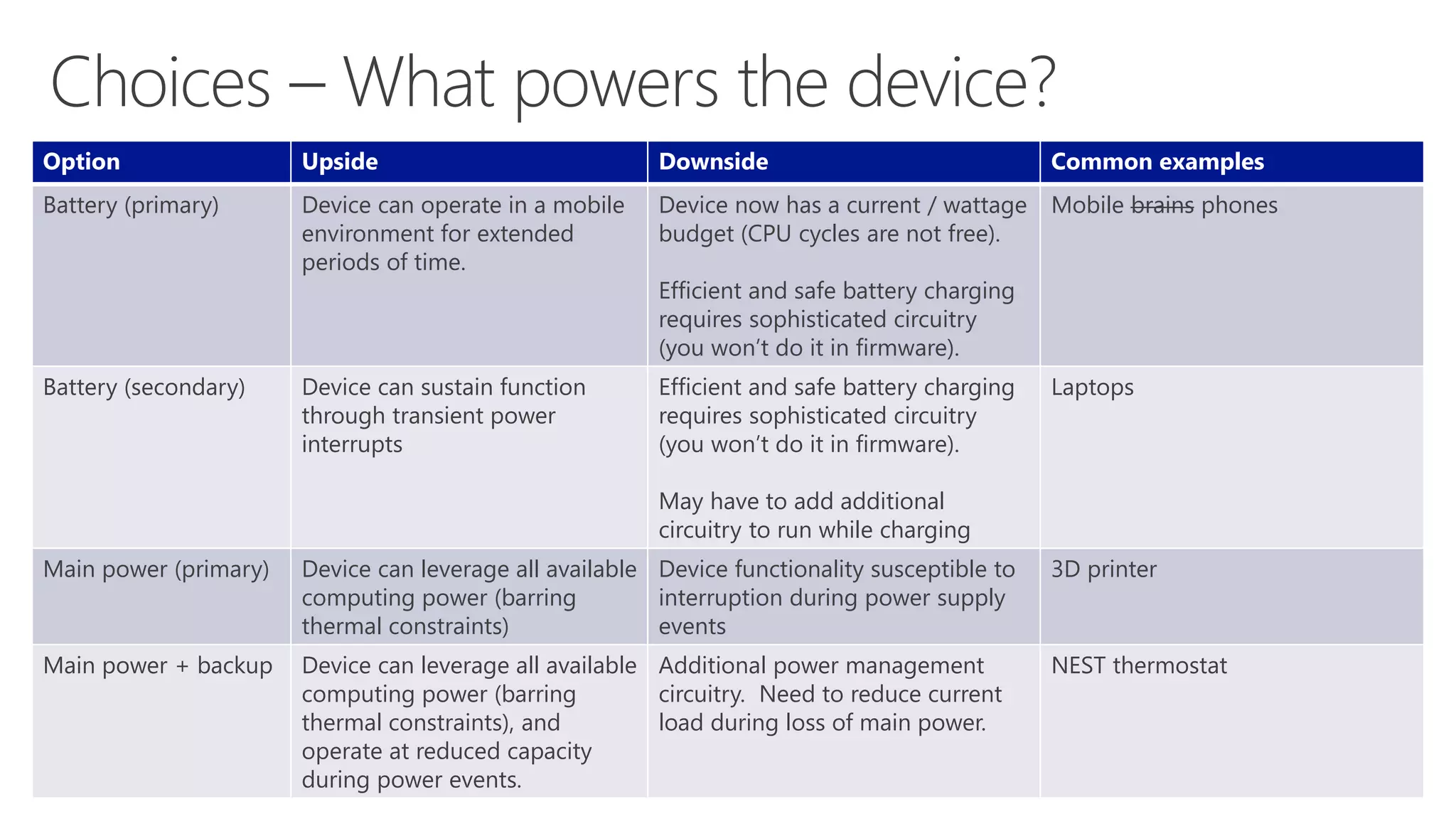
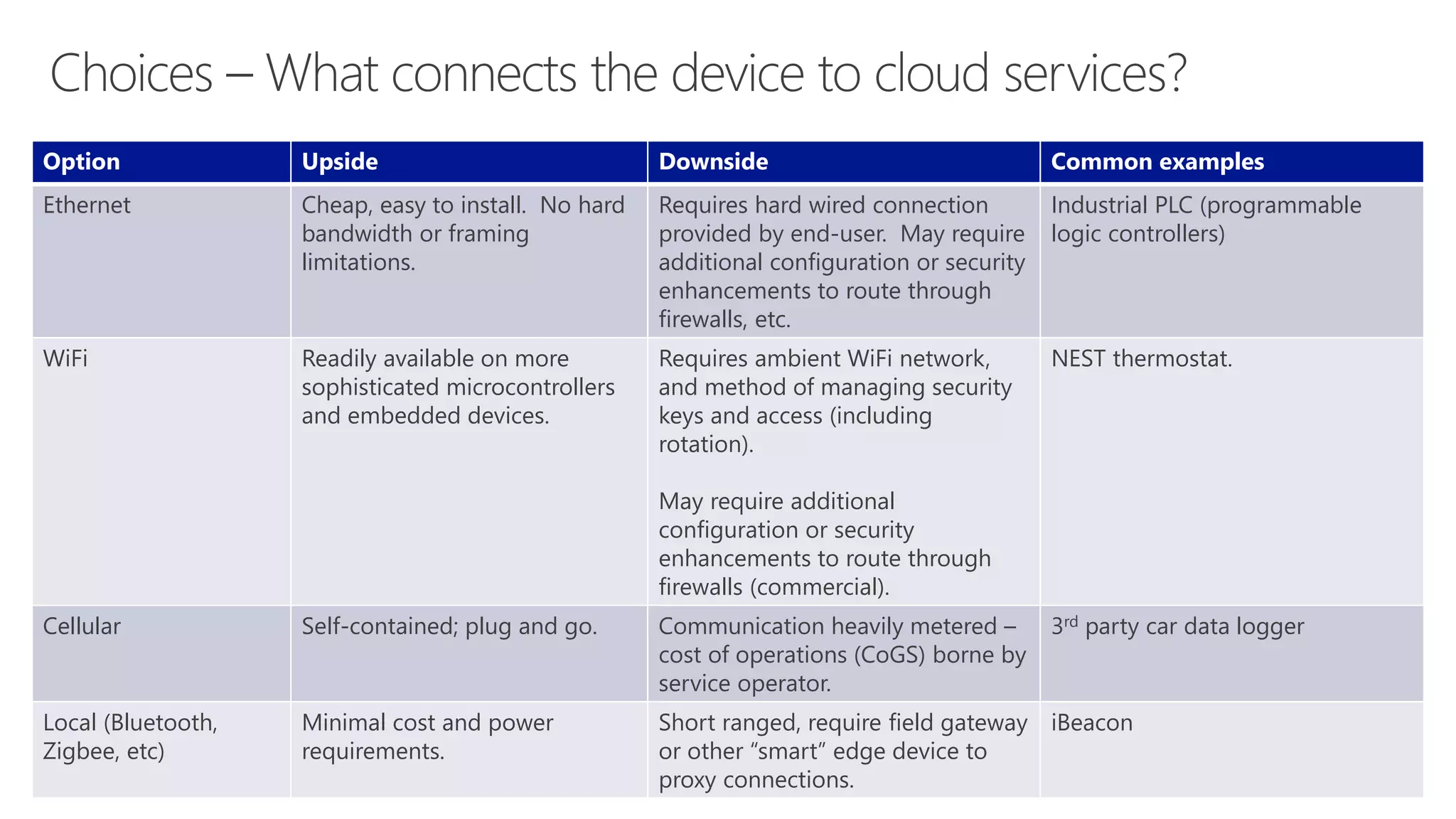
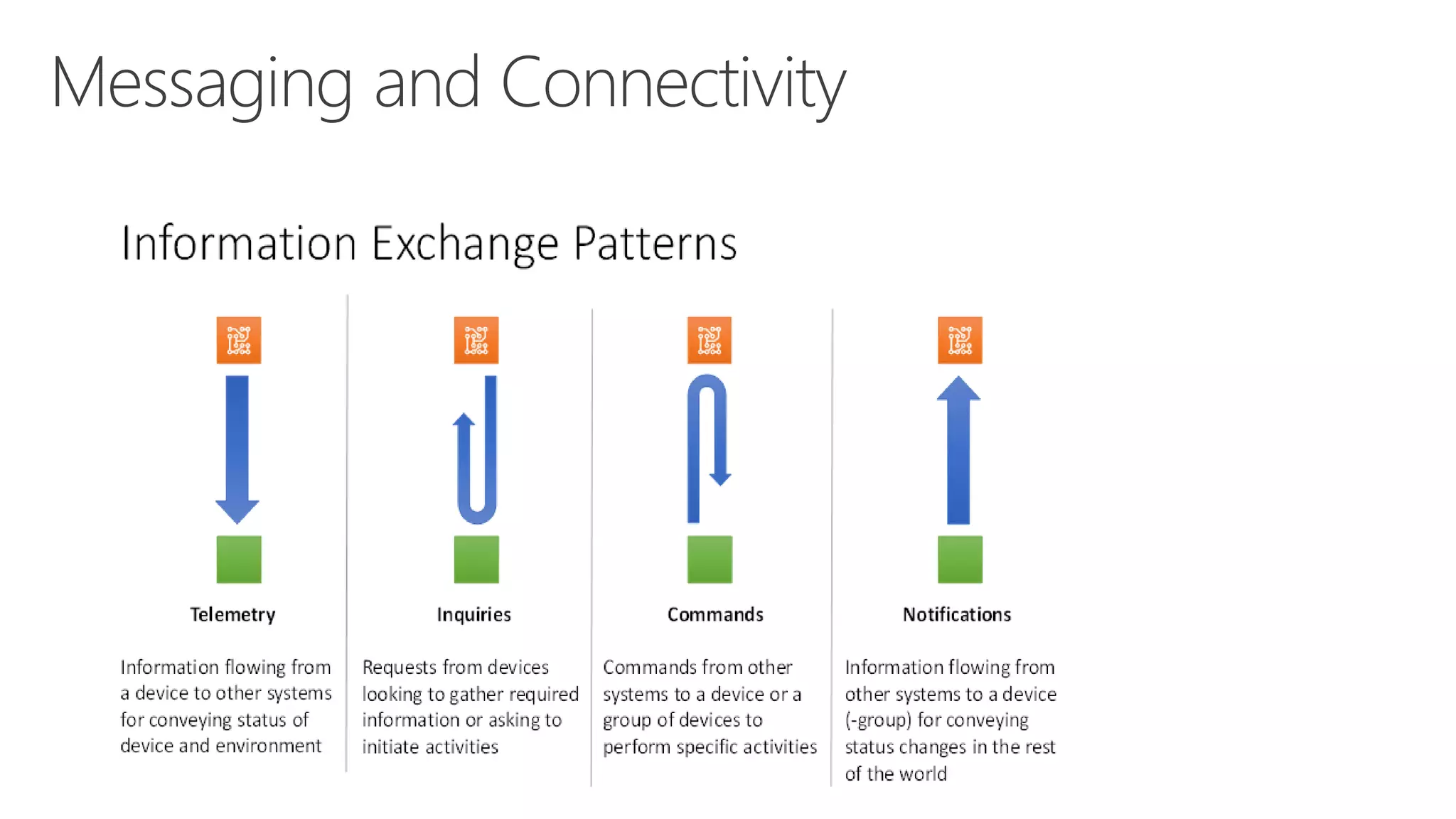
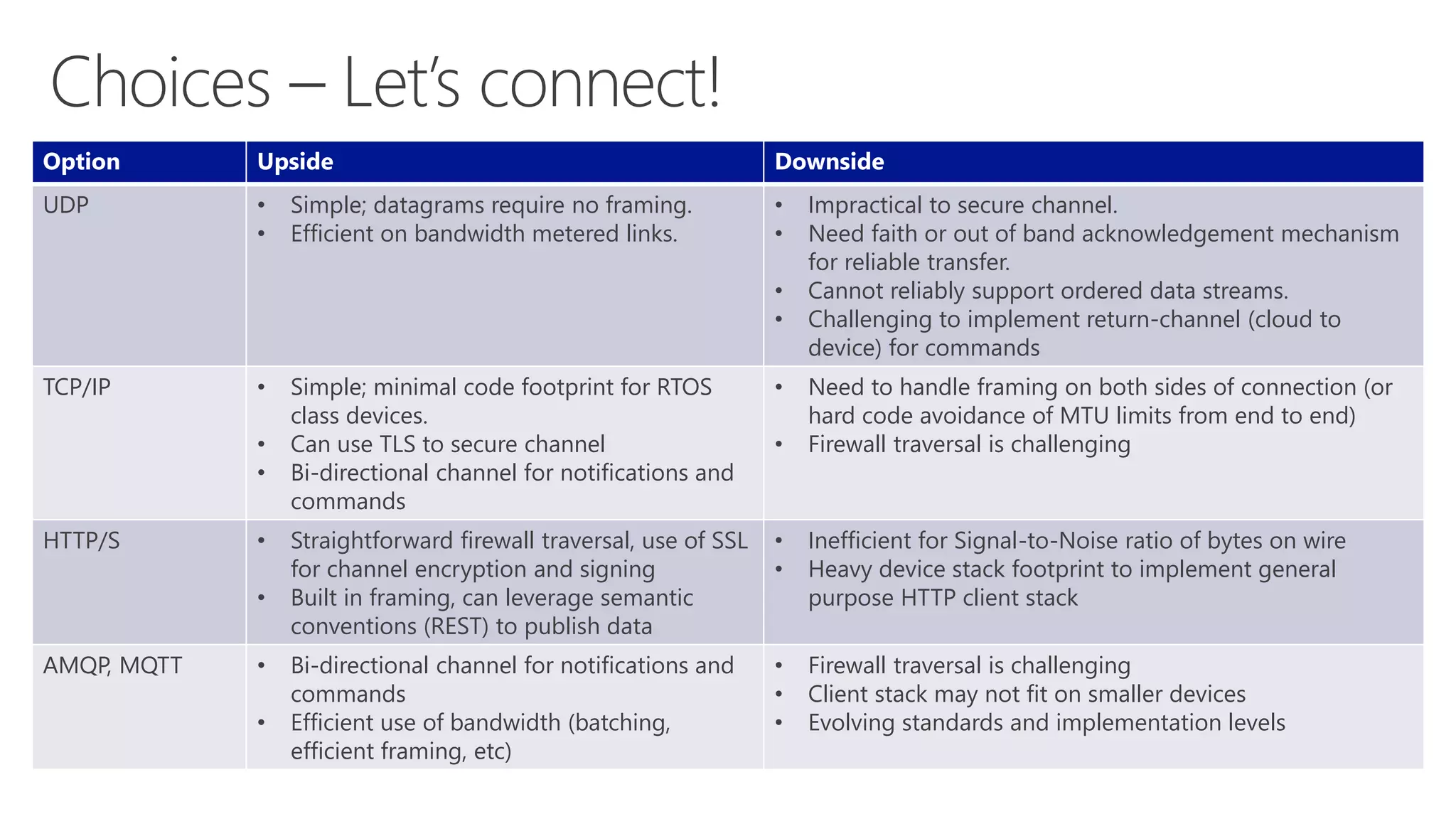
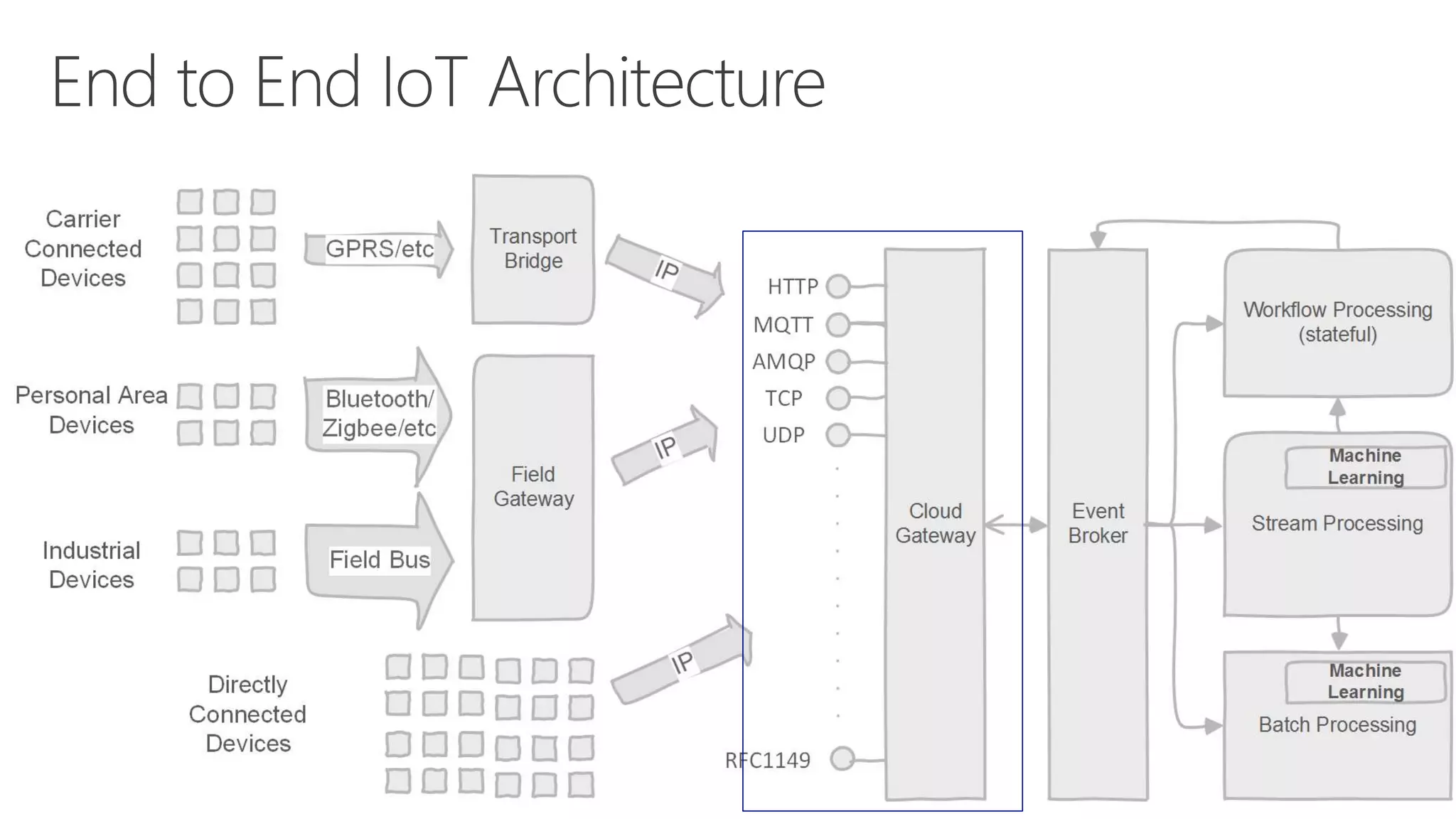
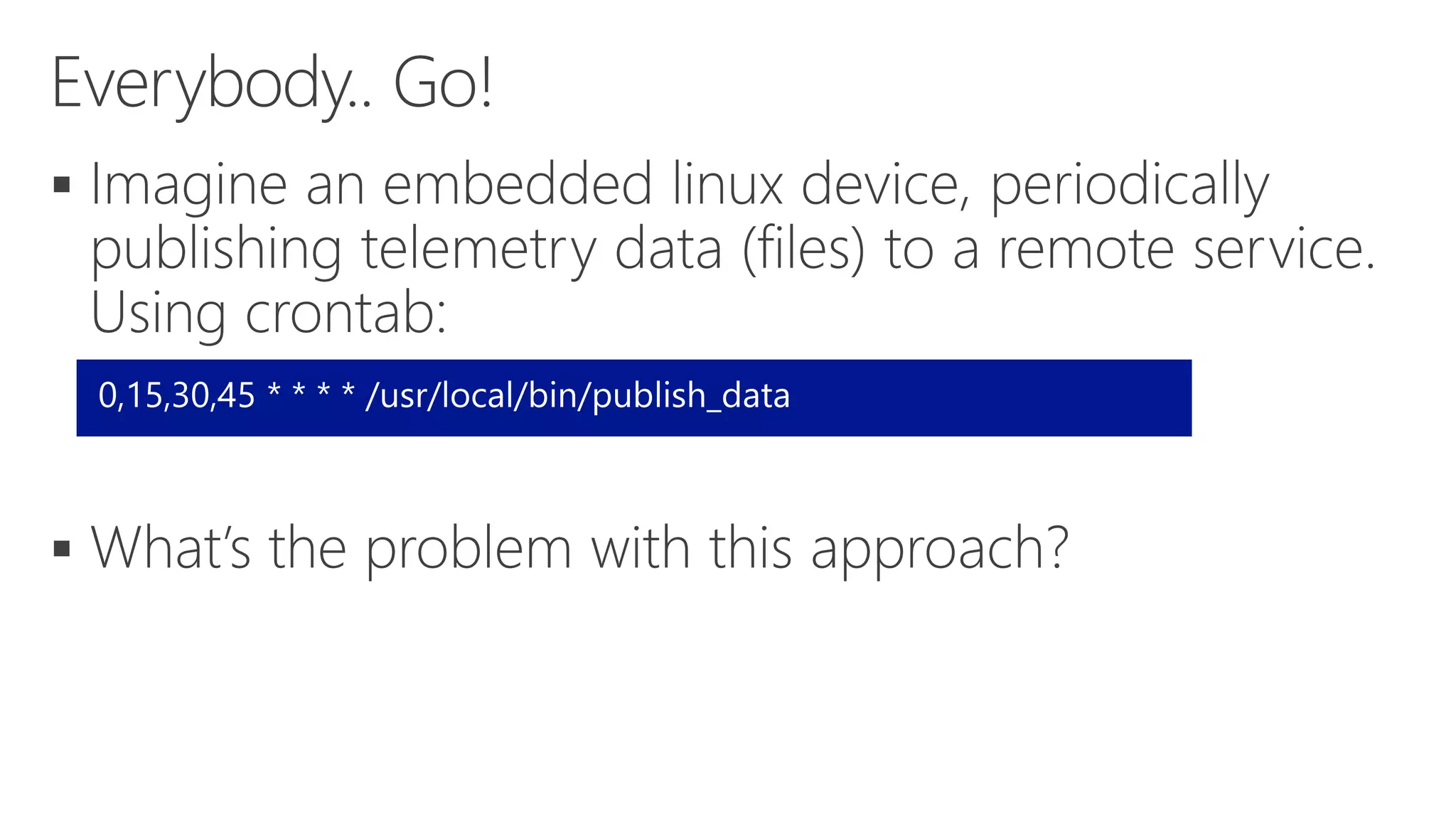
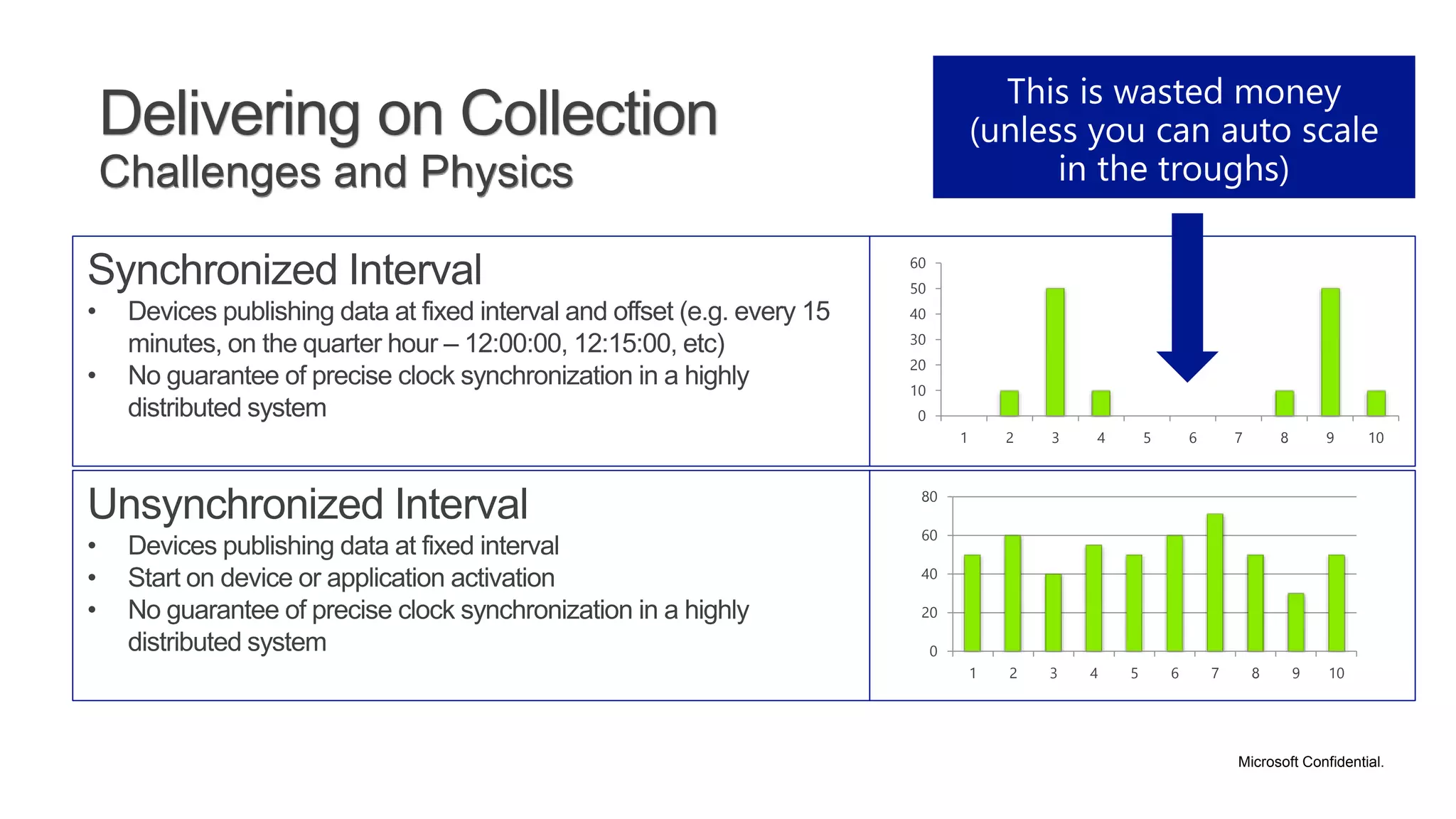
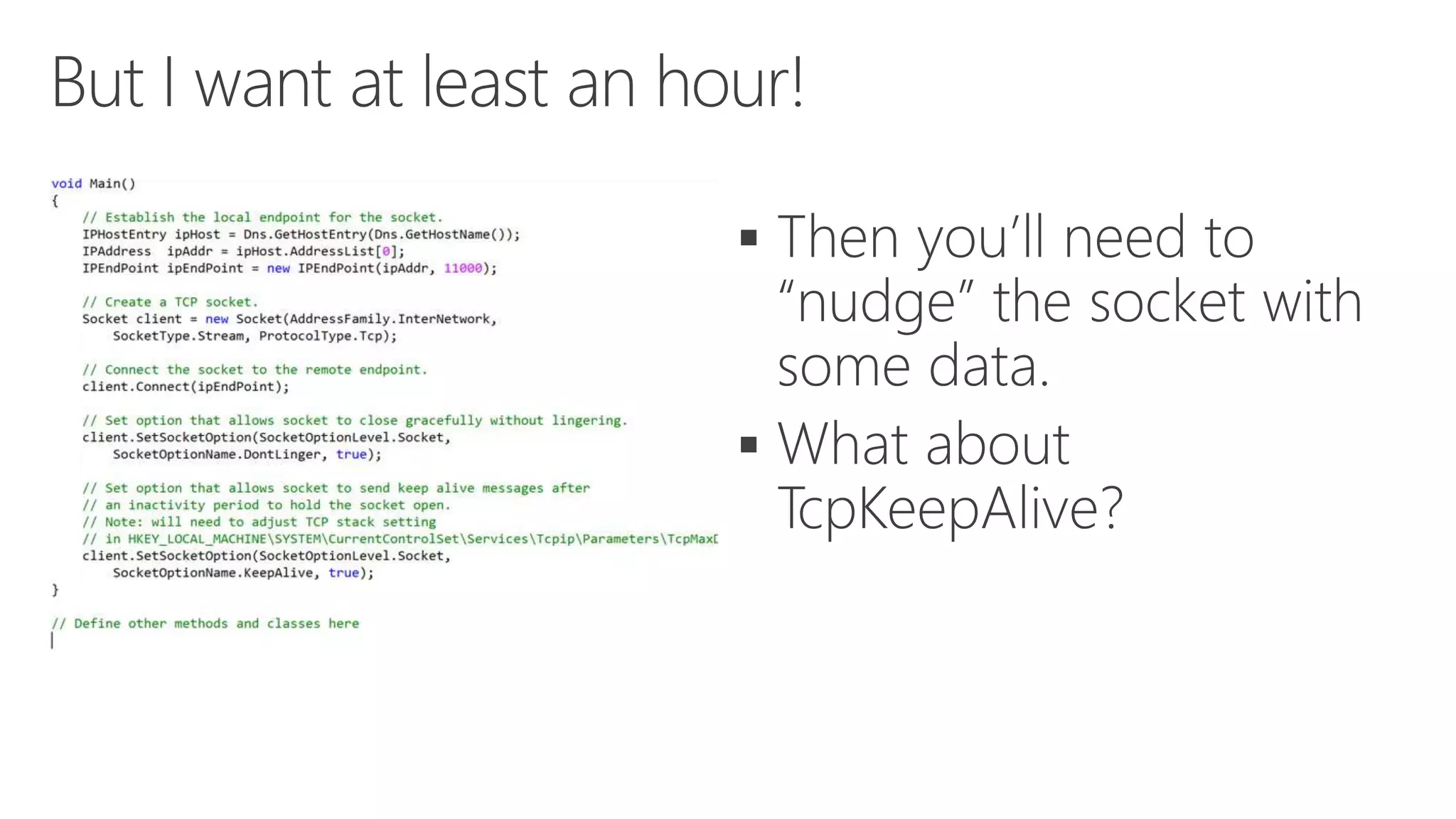
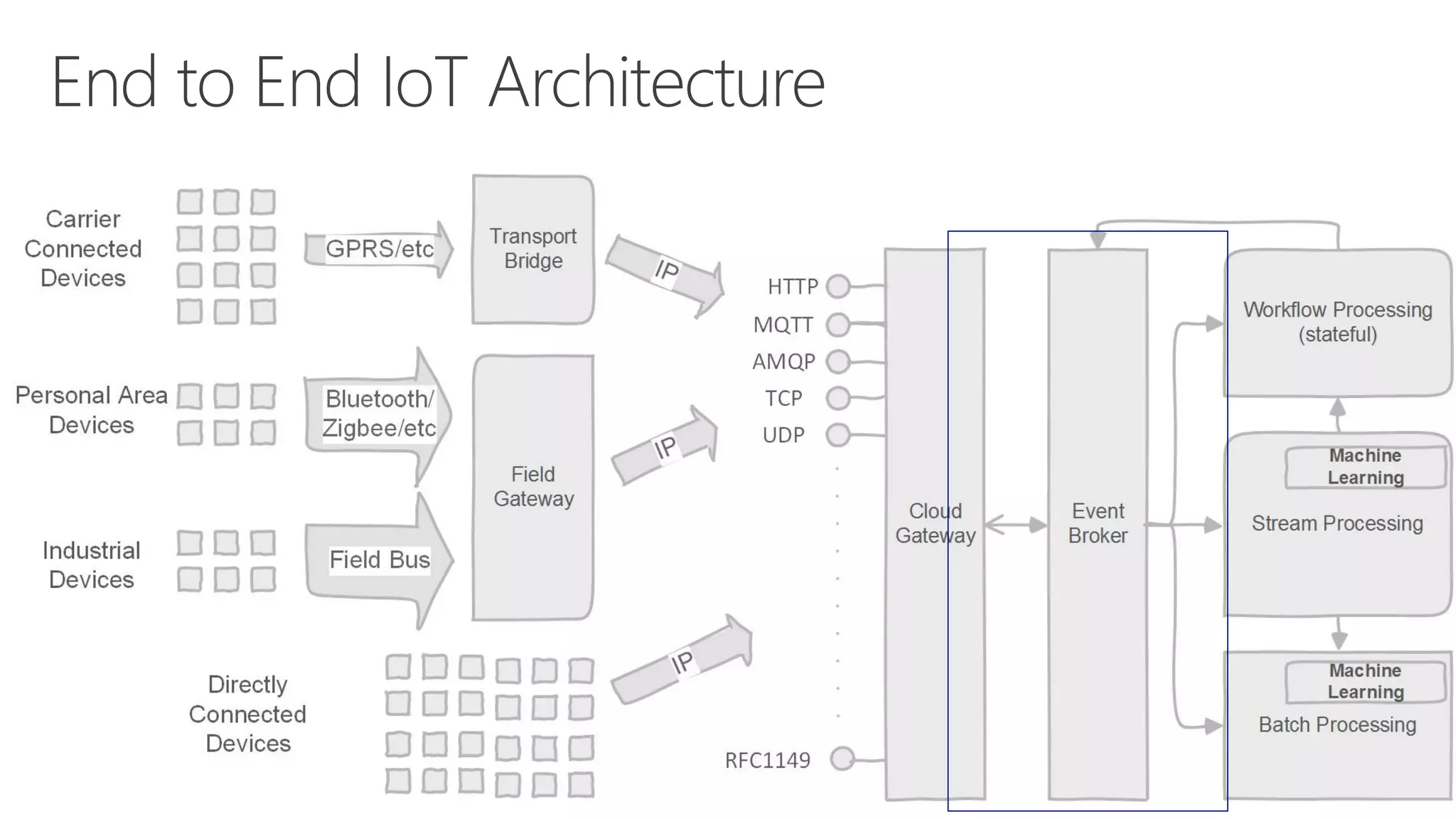
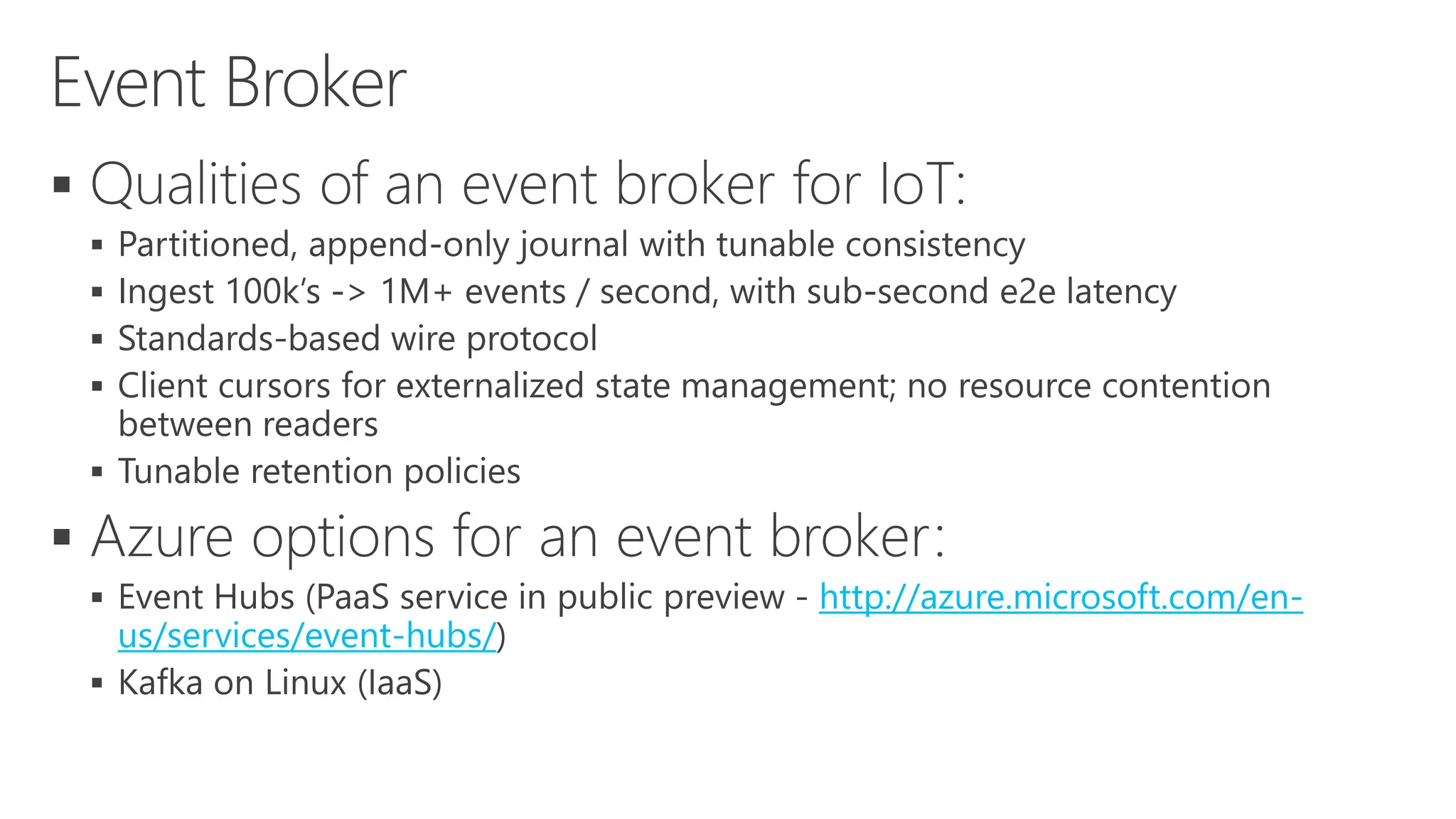
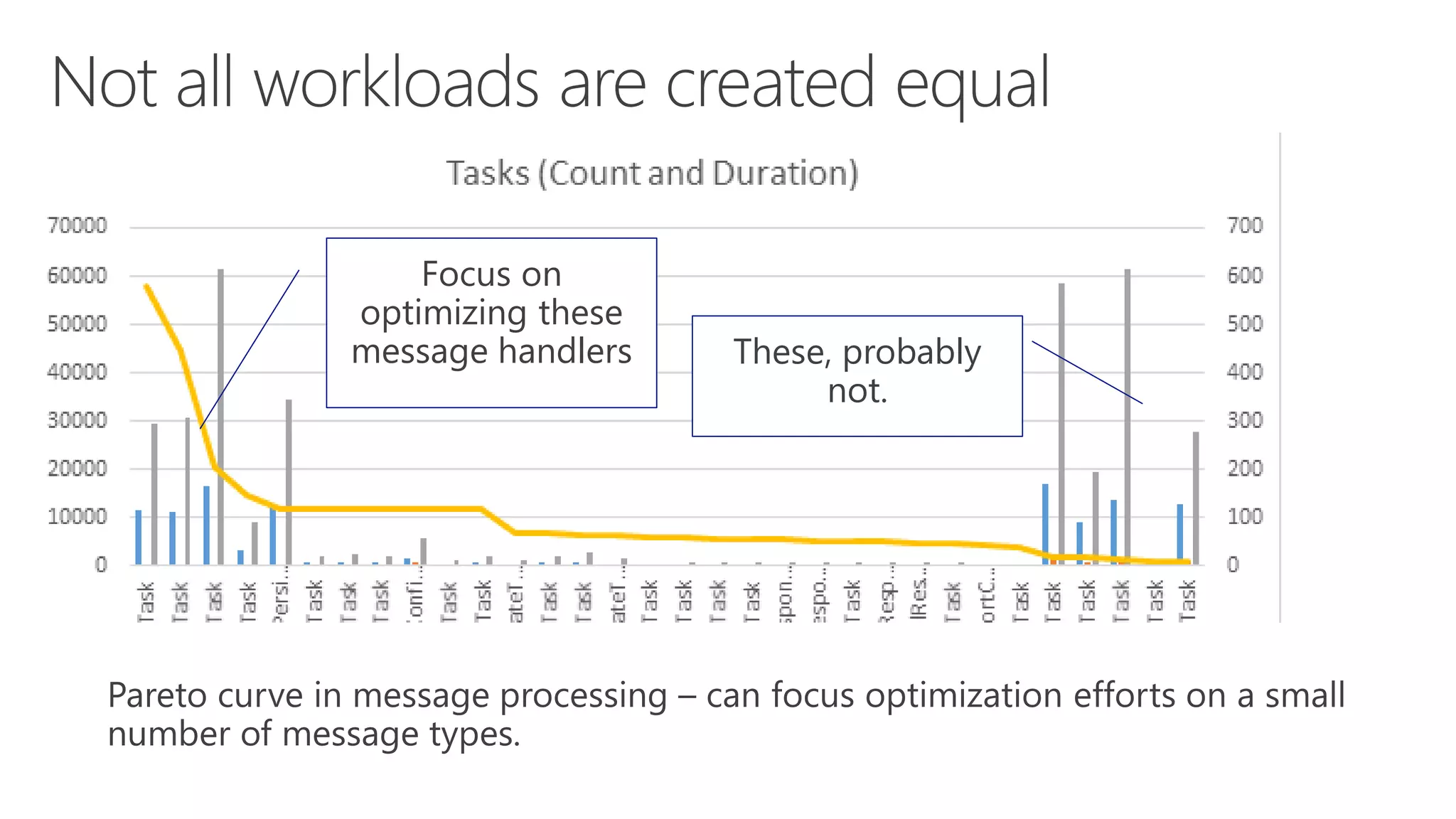
The document discusses various communication options for devices in the Internet of Things (IoT), comparing their advantages and disadvantages, including battery and power management considerations. It outlines different communication protocols such as UDP, TCP/IP, HTTP/S, AMQP, and MQTT, highlighting their efficiency, security, and complexity based on device capabilities. Additionally, it addresses data formats like JSON and XML, and mentions specific examples of IoT devices, along with challenges related to firewall configuration and connection management.