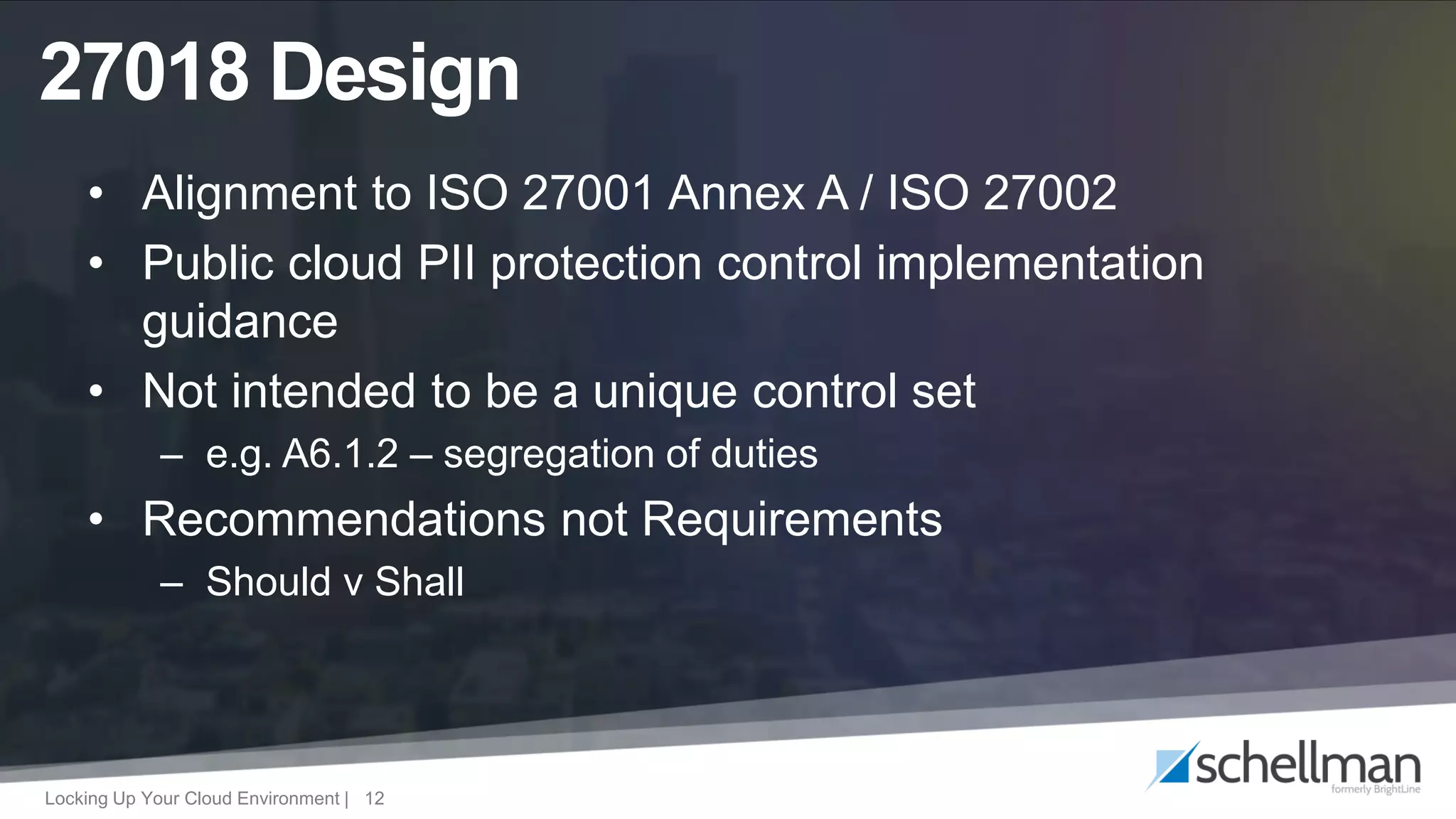
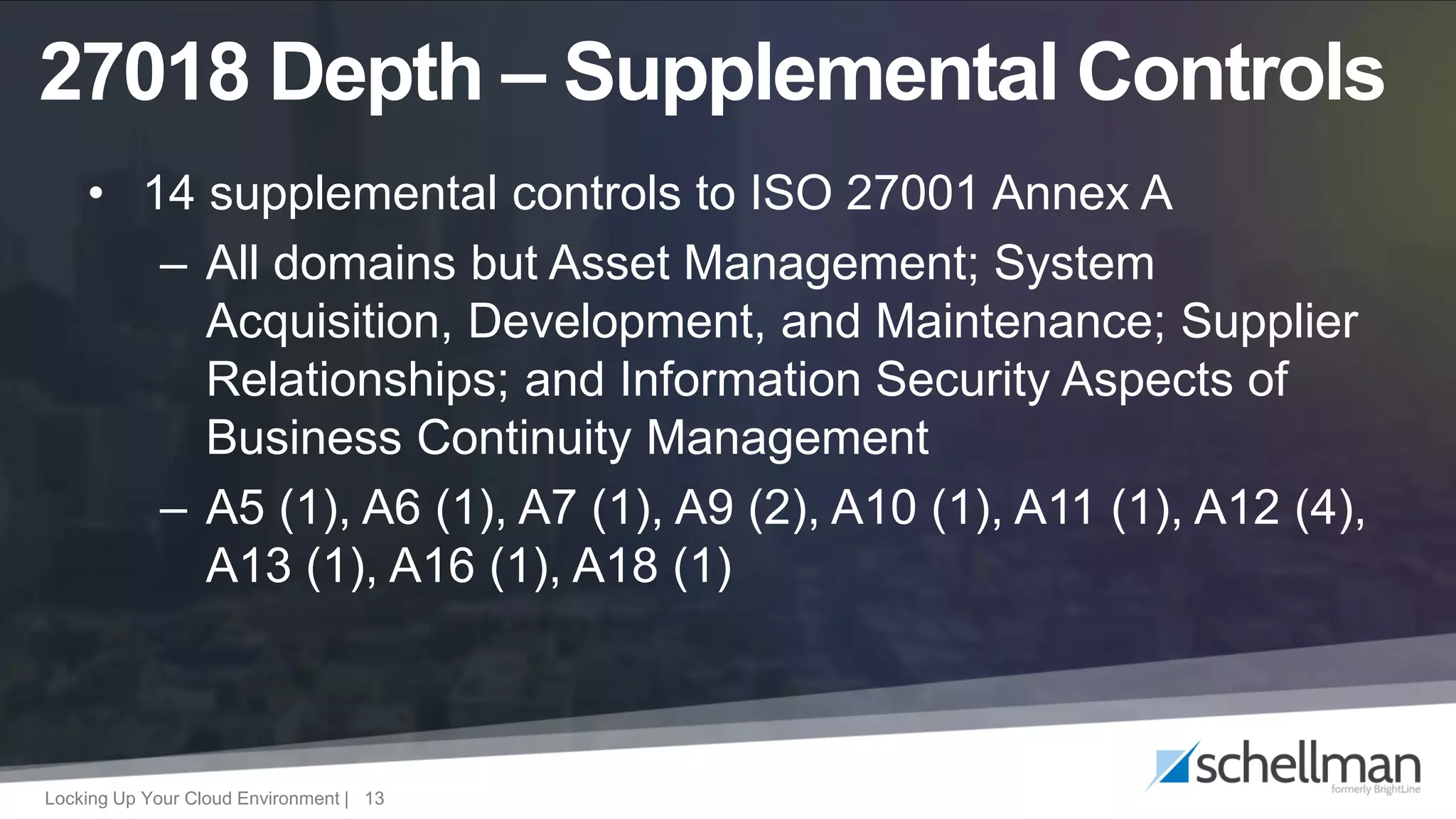
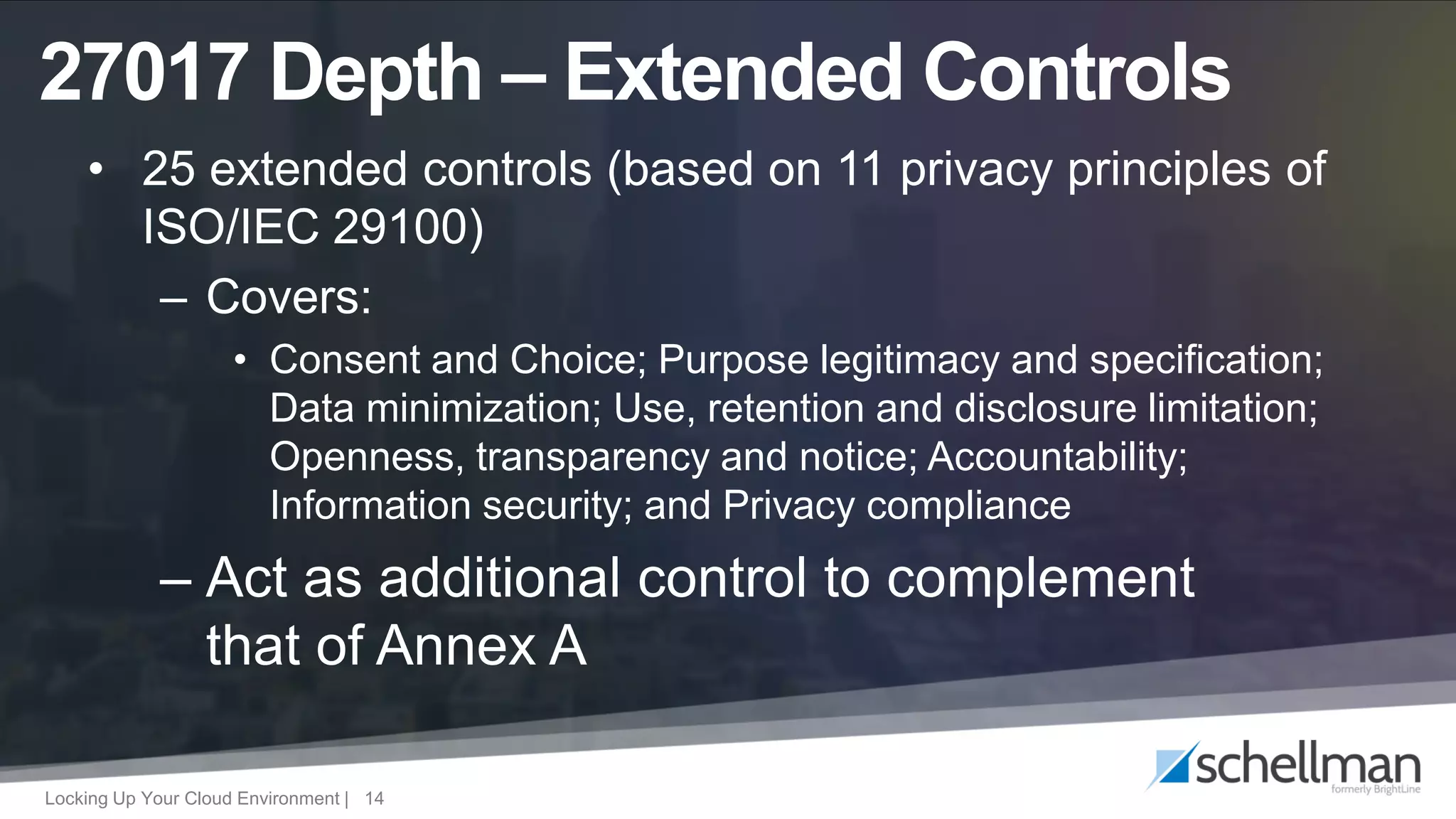
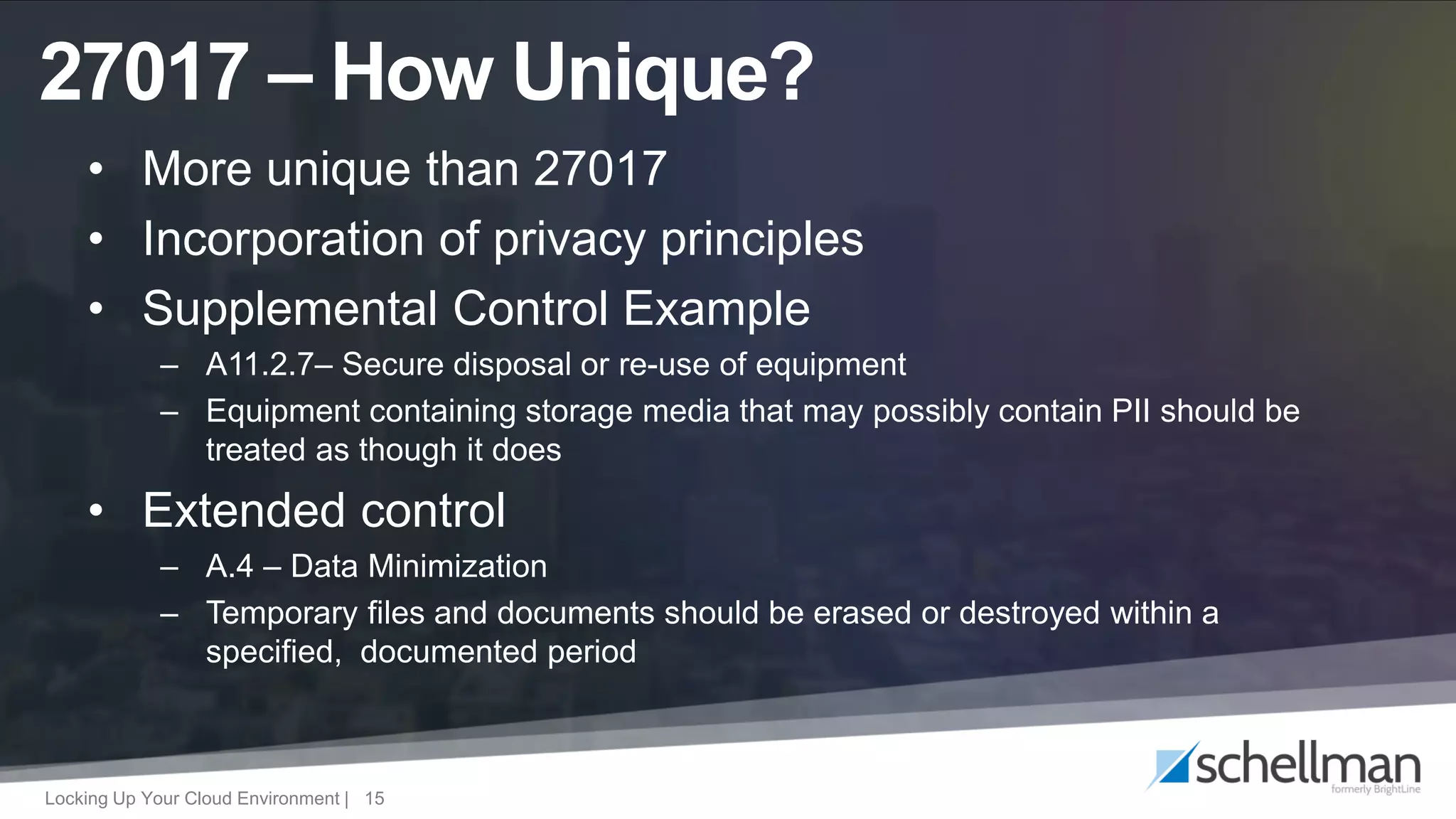
The document provides an overview of ISO/IEC 27017 and ISO/IEC 27018, focusing on their application in cloud service environments for security and privacy management. It outlines supplemental and extended controls related to information security and the protection of personally identifiable information in public clouds. Additionally, it discusses the audit process and market acceptance of these standards in the context of increasing privacy concerns and compliance requirements.