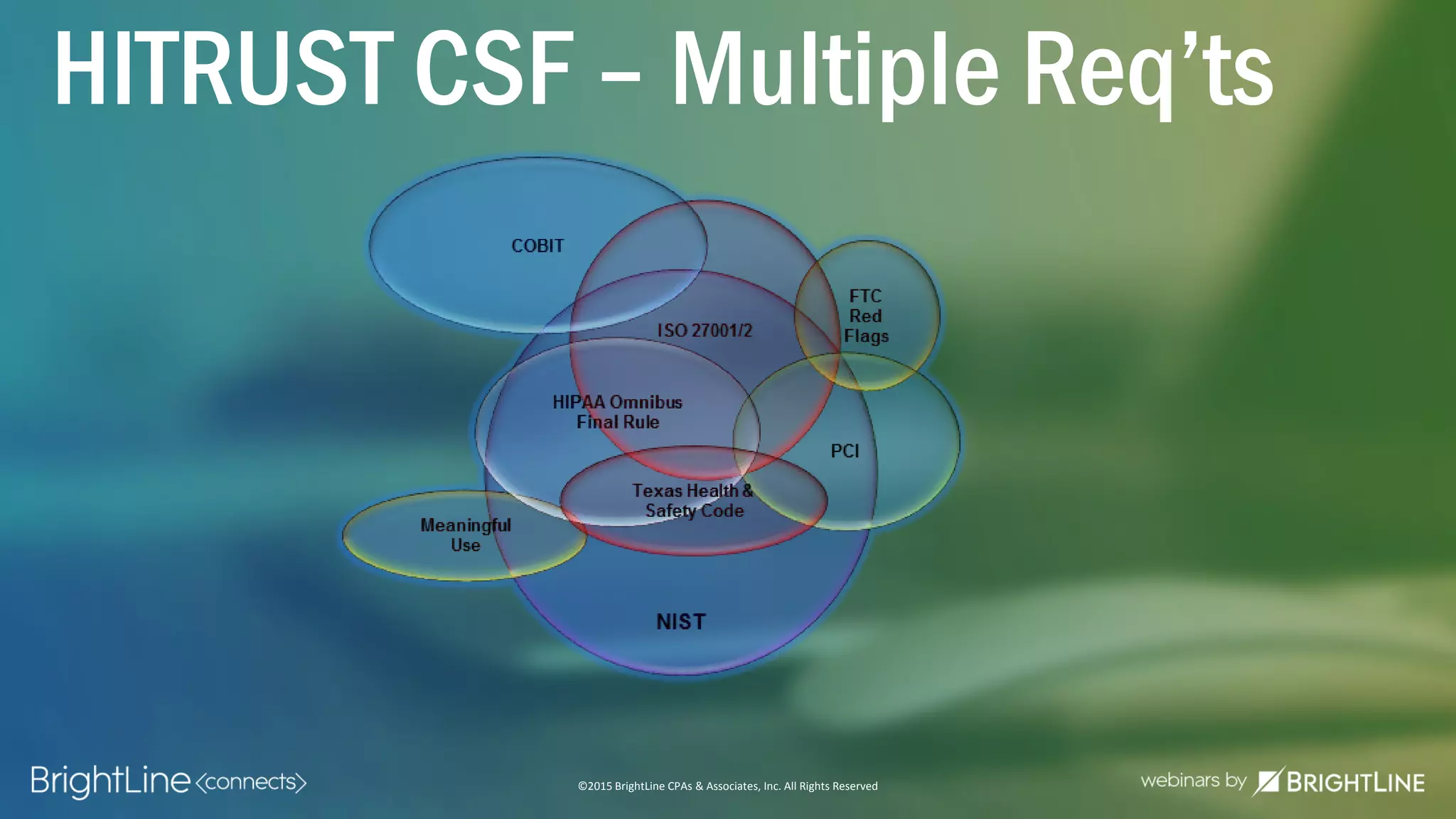
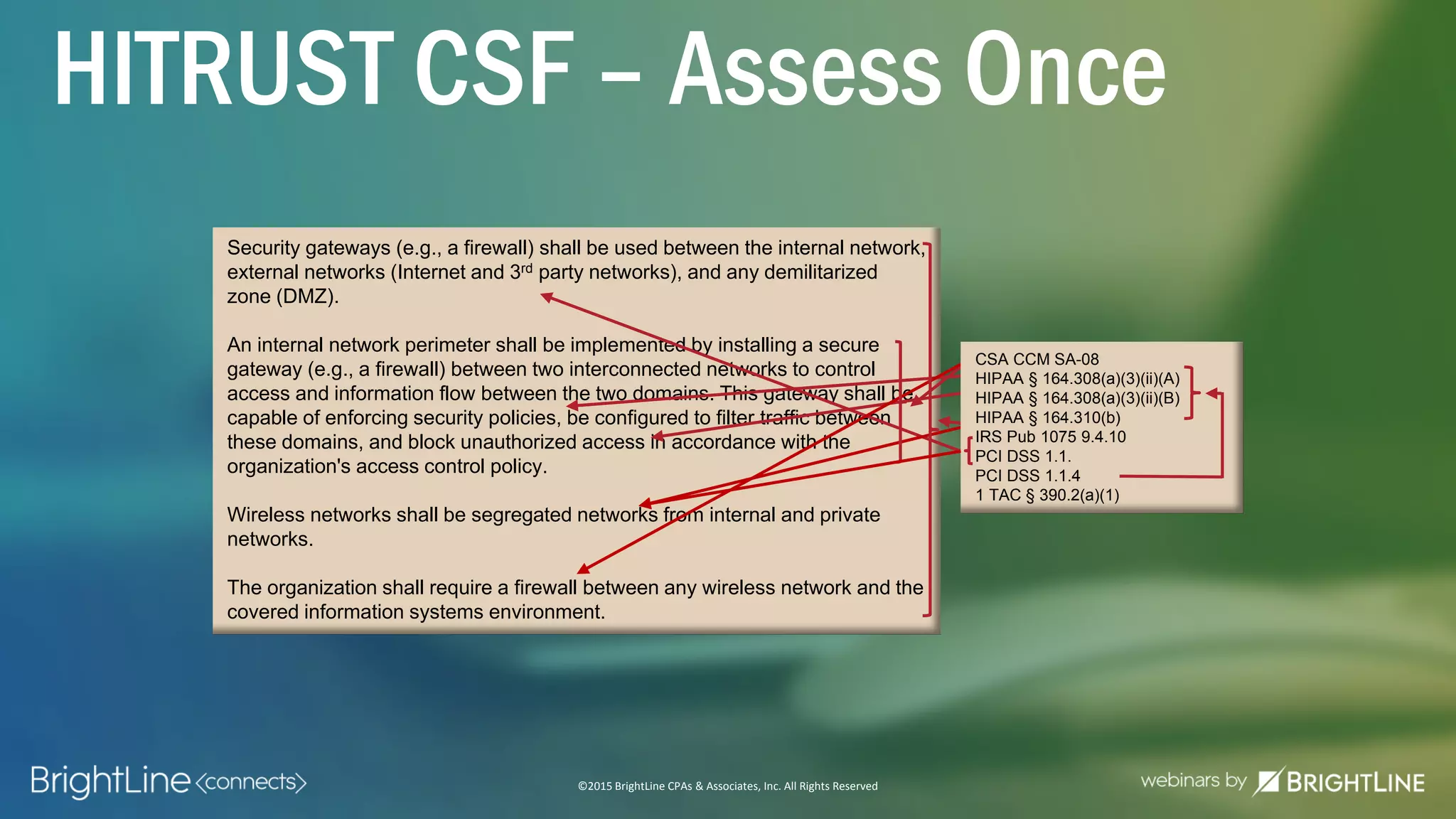
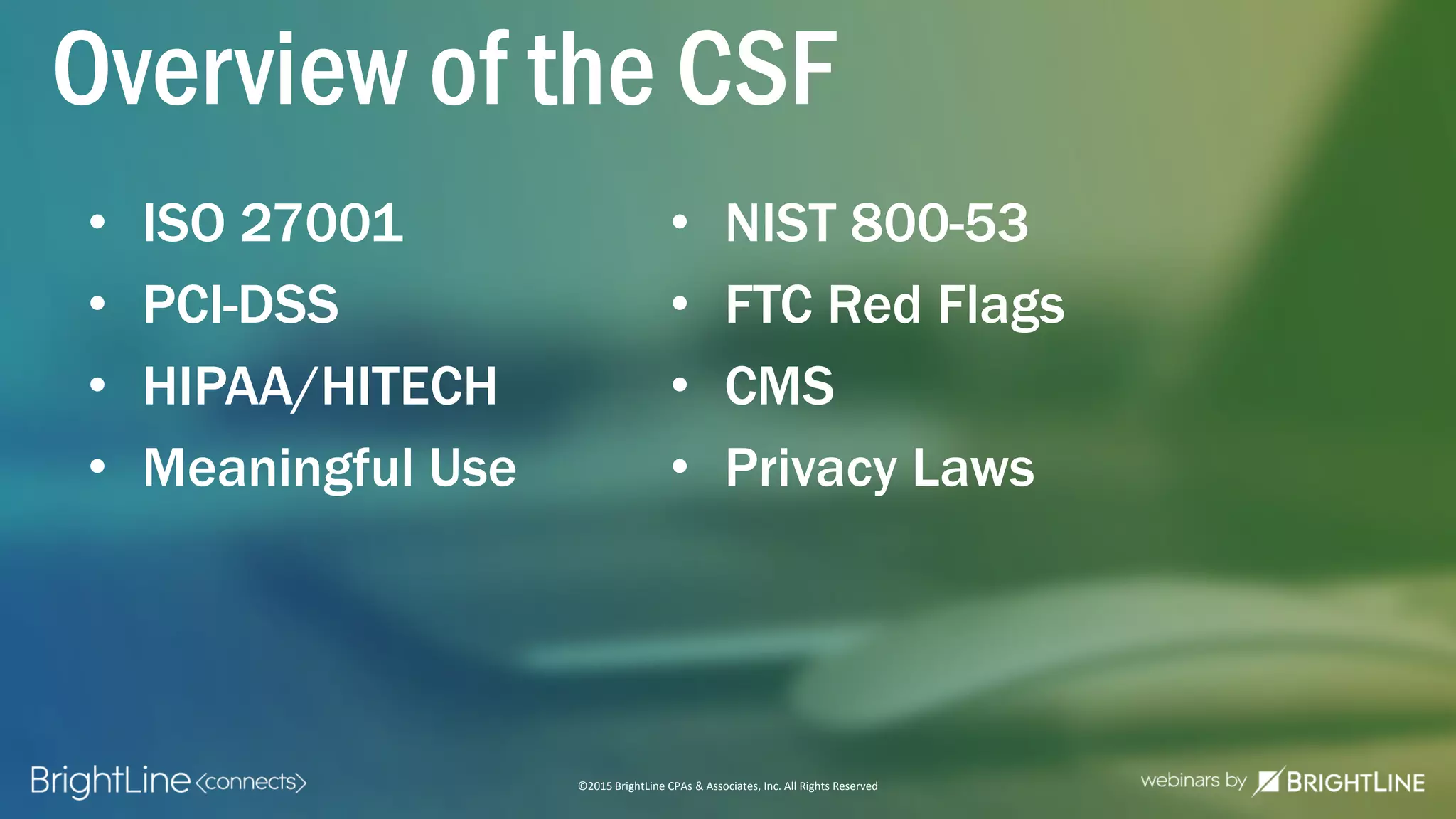
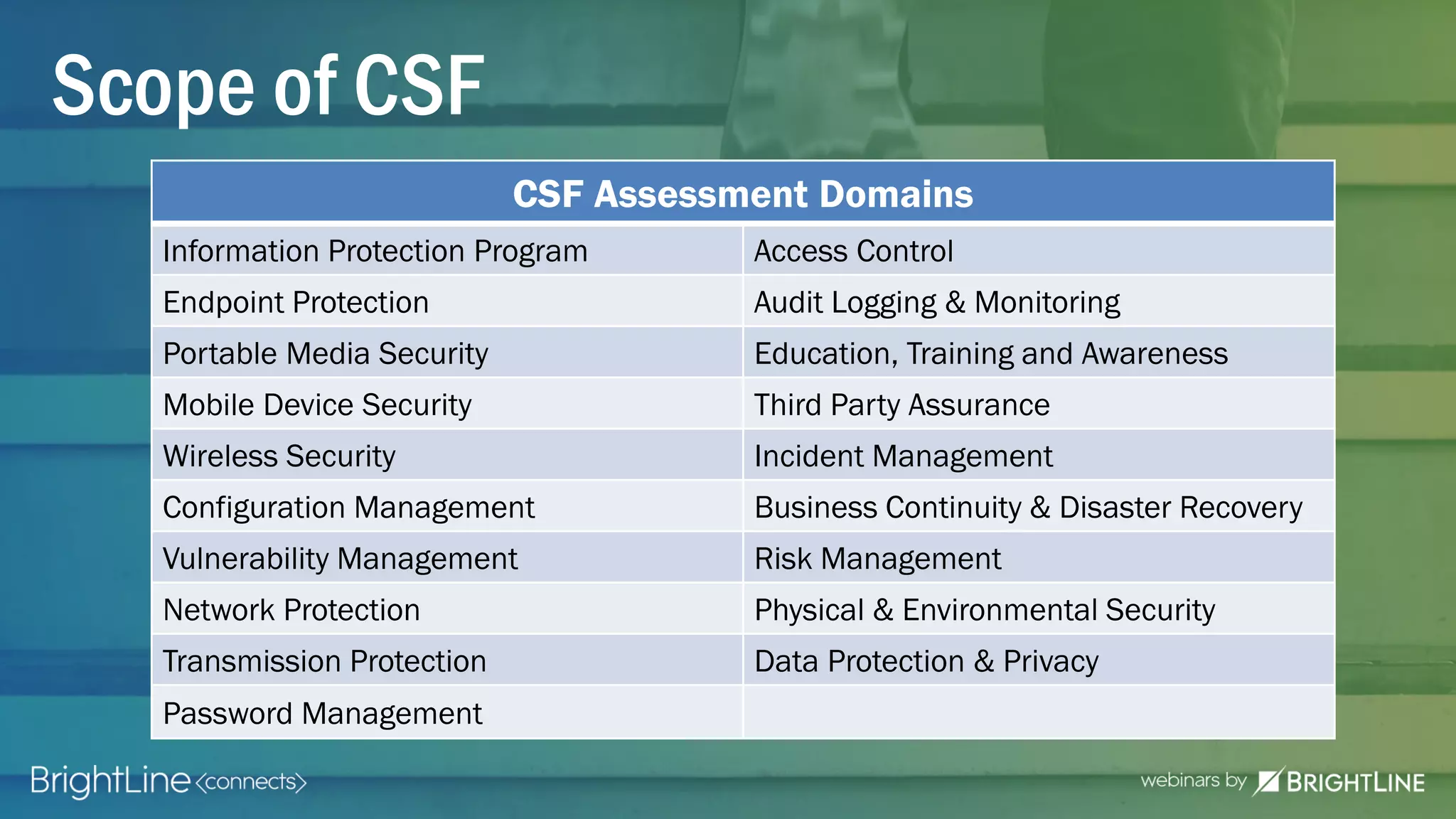
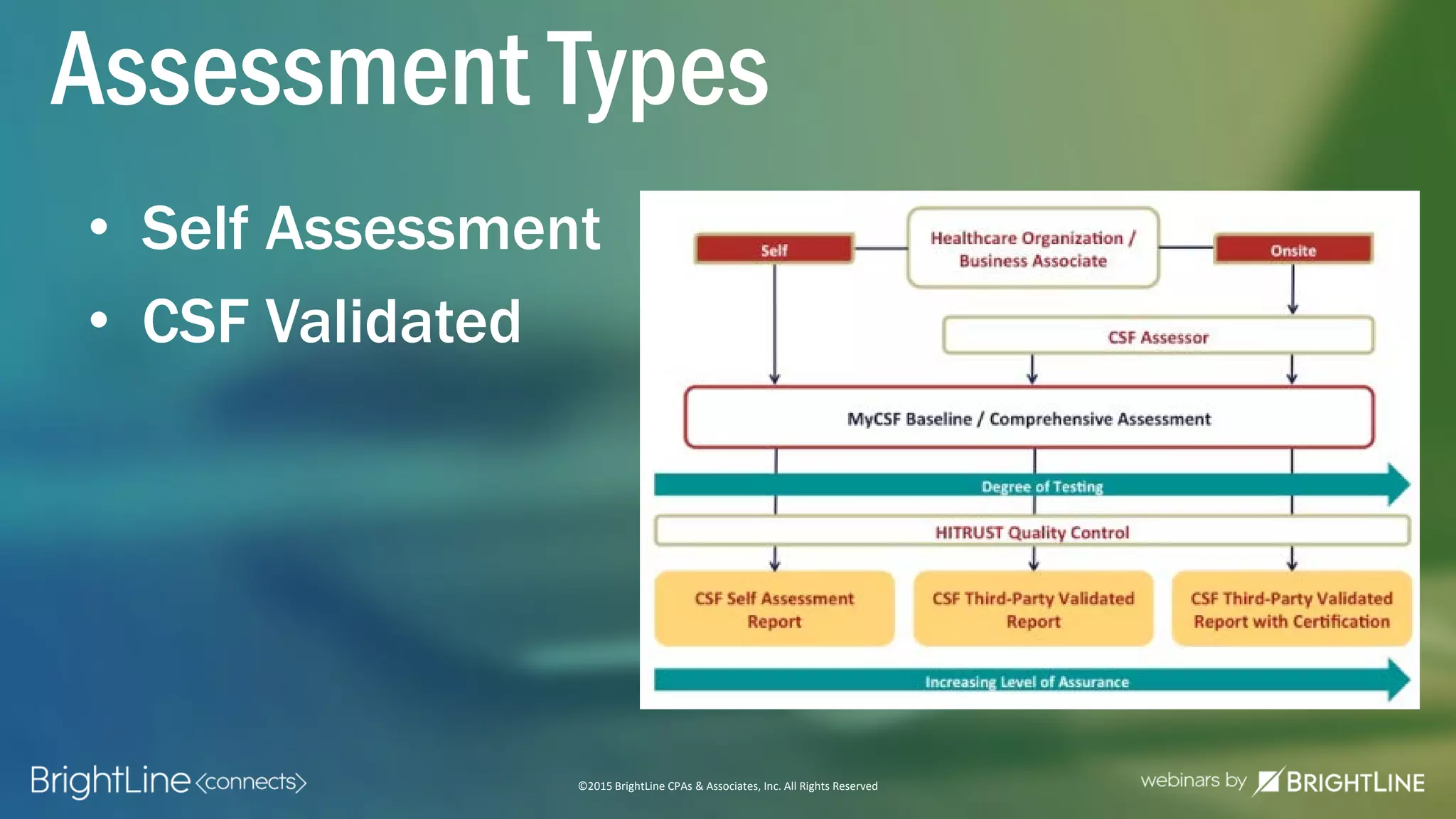
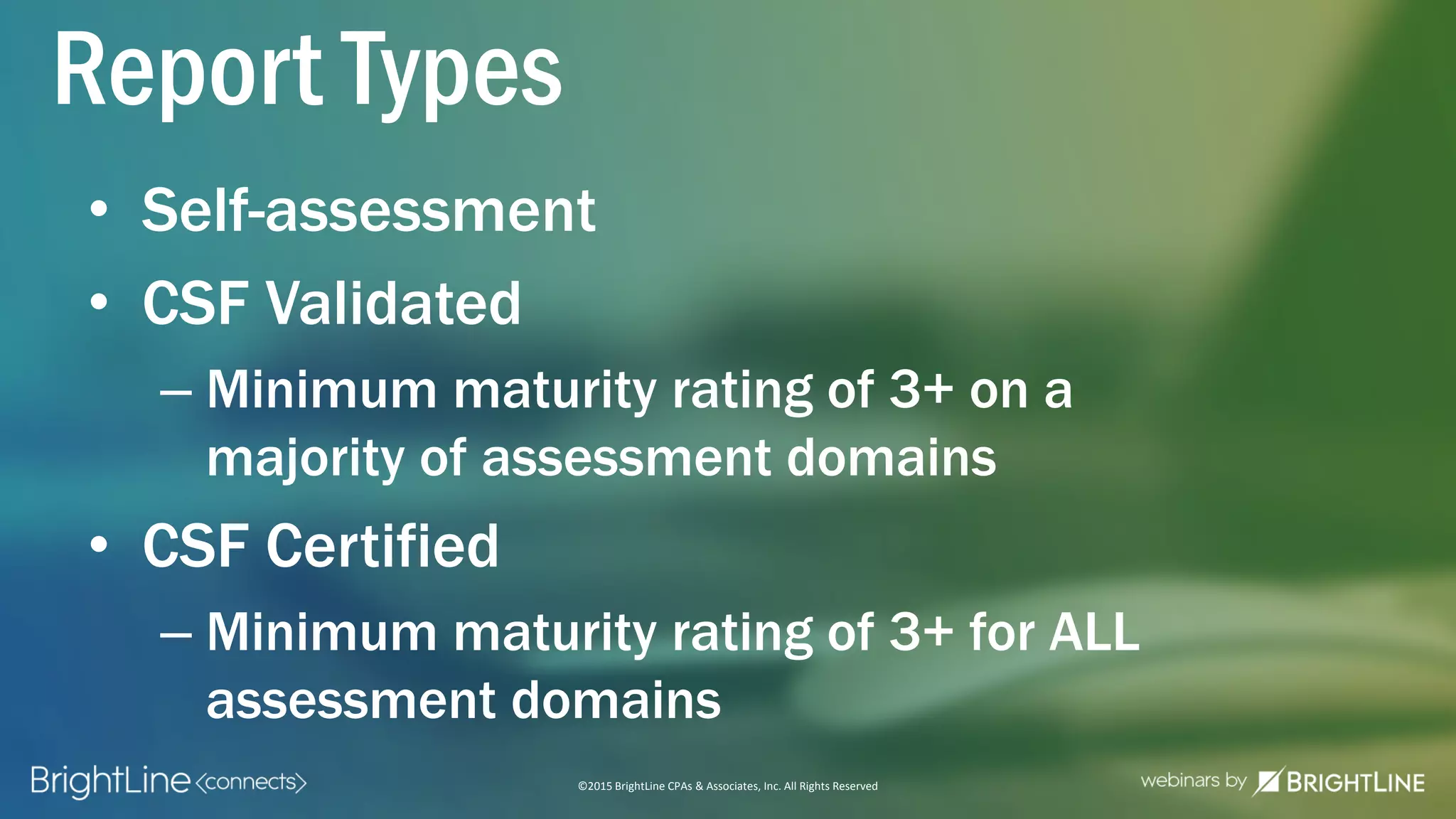
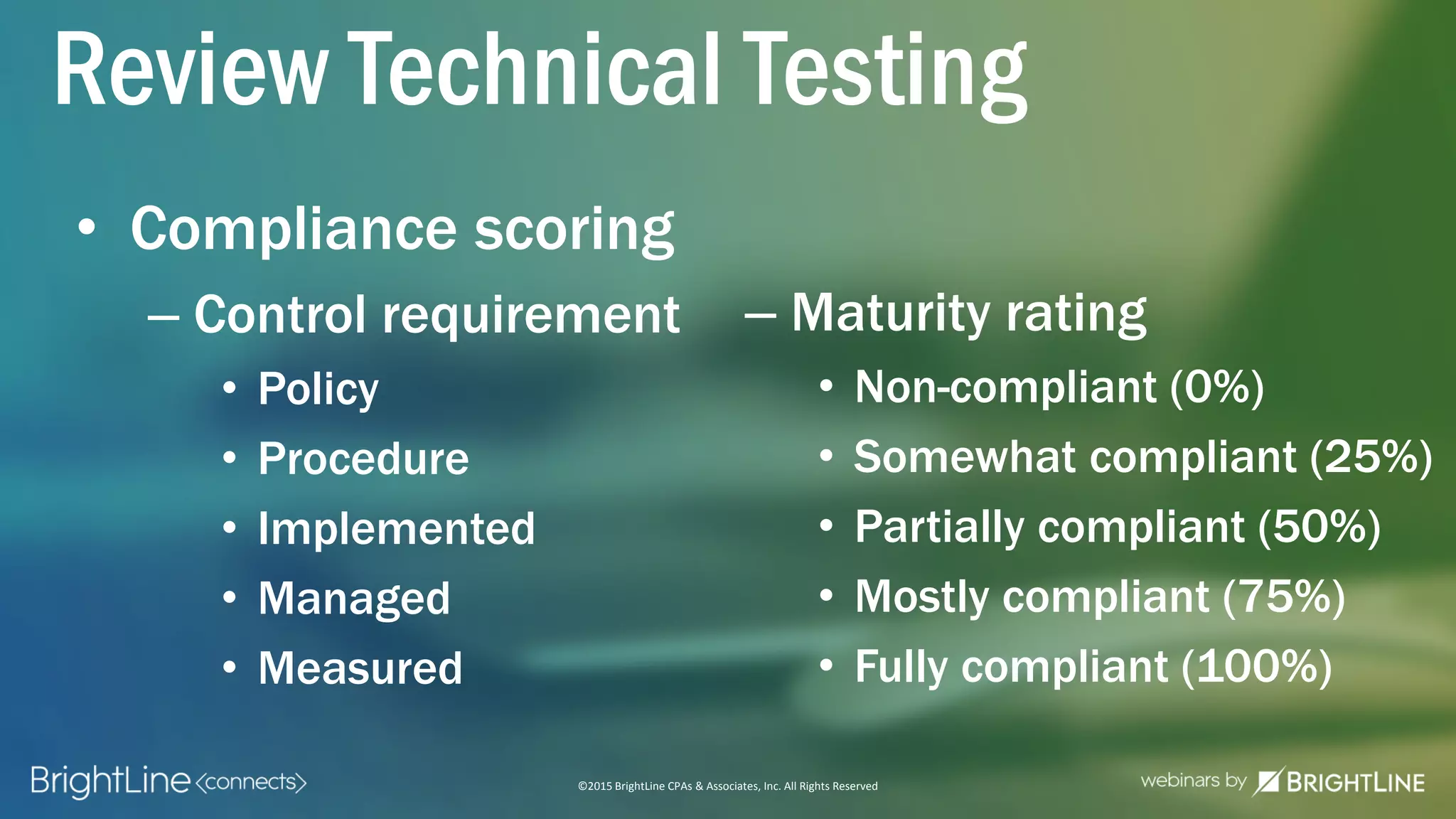
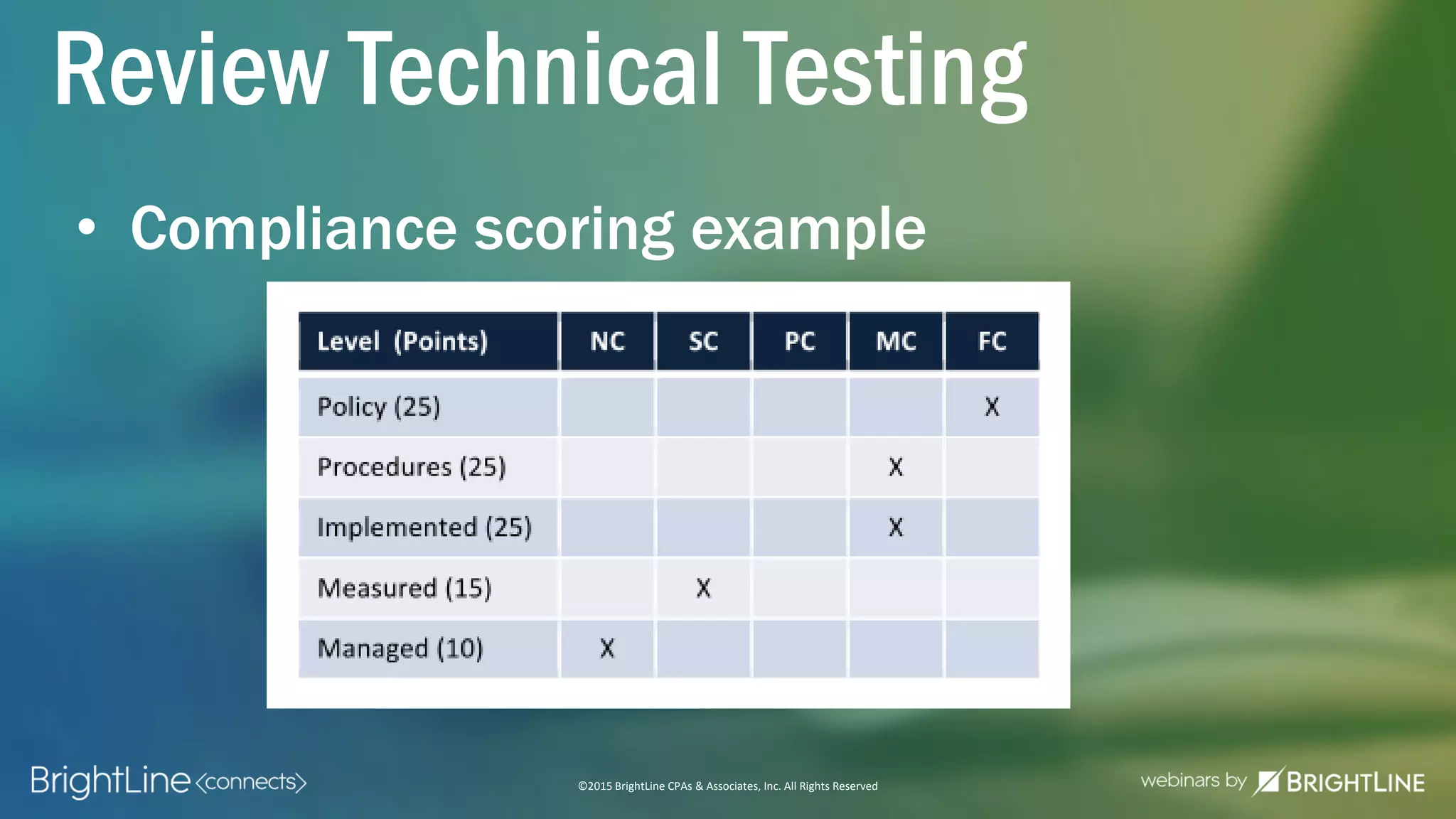
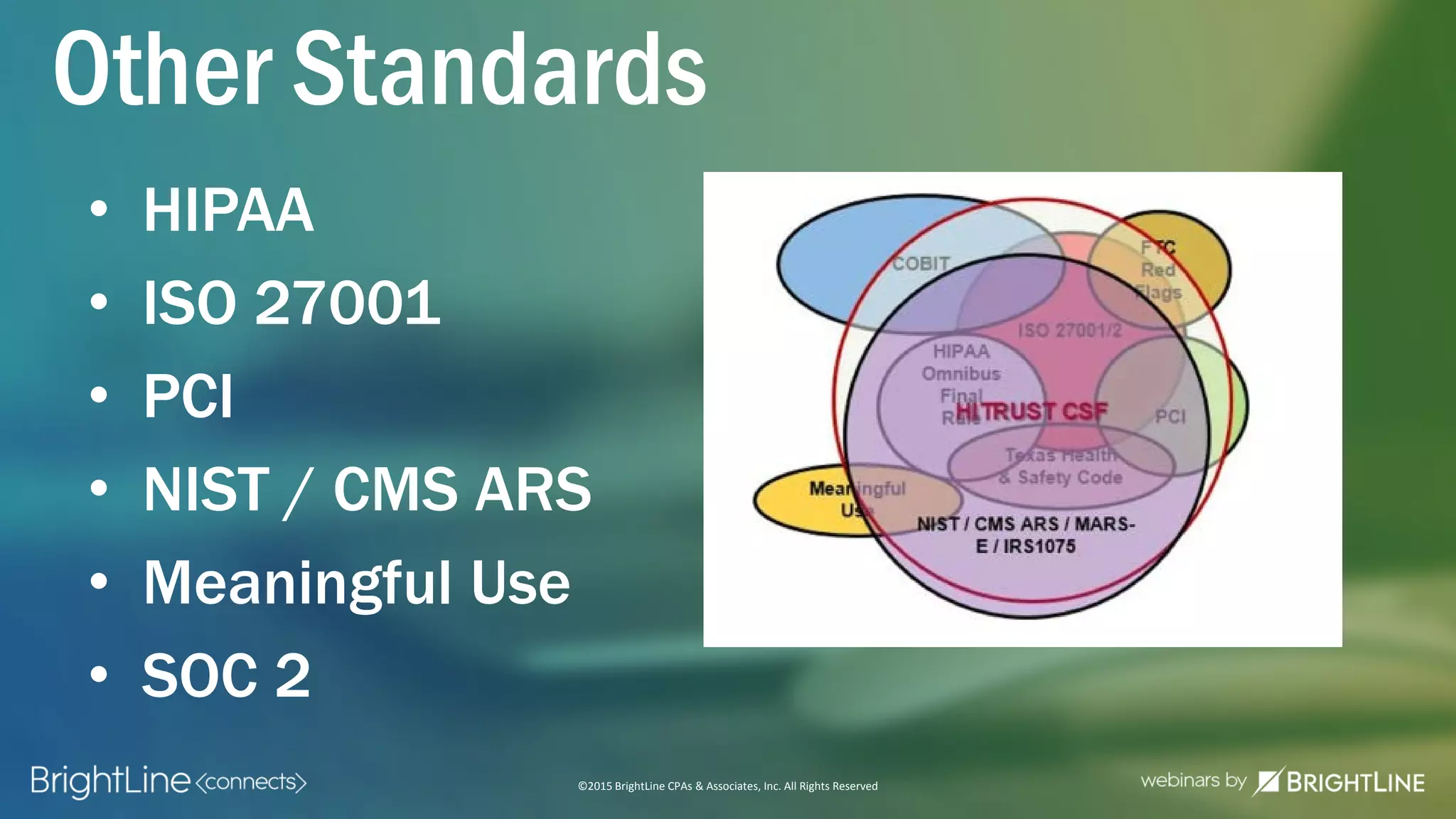
The document outlines the HITRUST CSF certification process, detailing its background, framework, and the steps required for compliance and certification in the healthcare industry. It emphasizes the importance of security and privacy in healthcare, highlights the expansion of CSF to address increasing cyber threats, and enumerates the various assessment options and organizational scopes for achieving certification. Additionally, it maps the CSF standards to other regulatory requirements, including HIPAA, ISO 27001, and PCI standards.