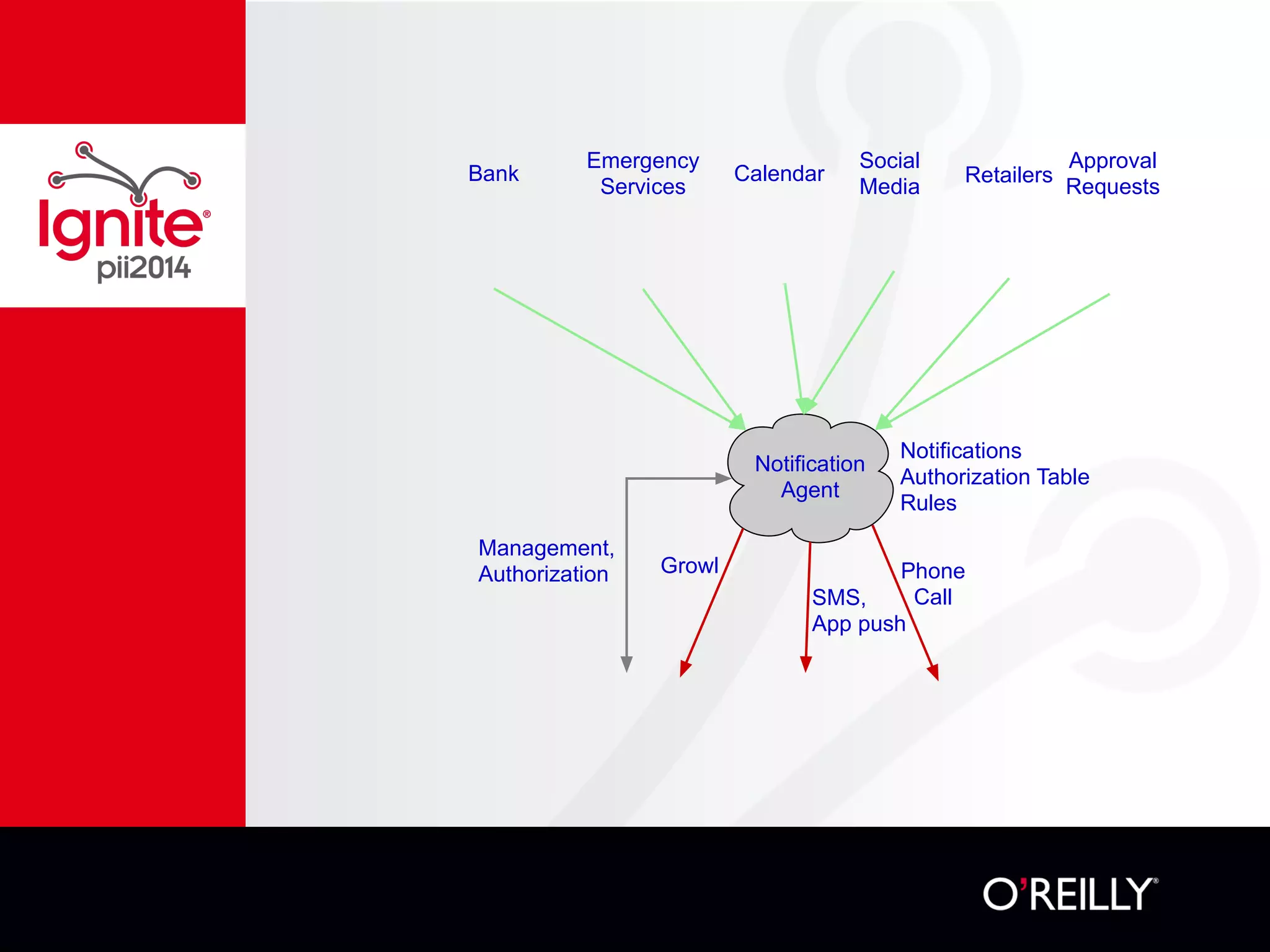
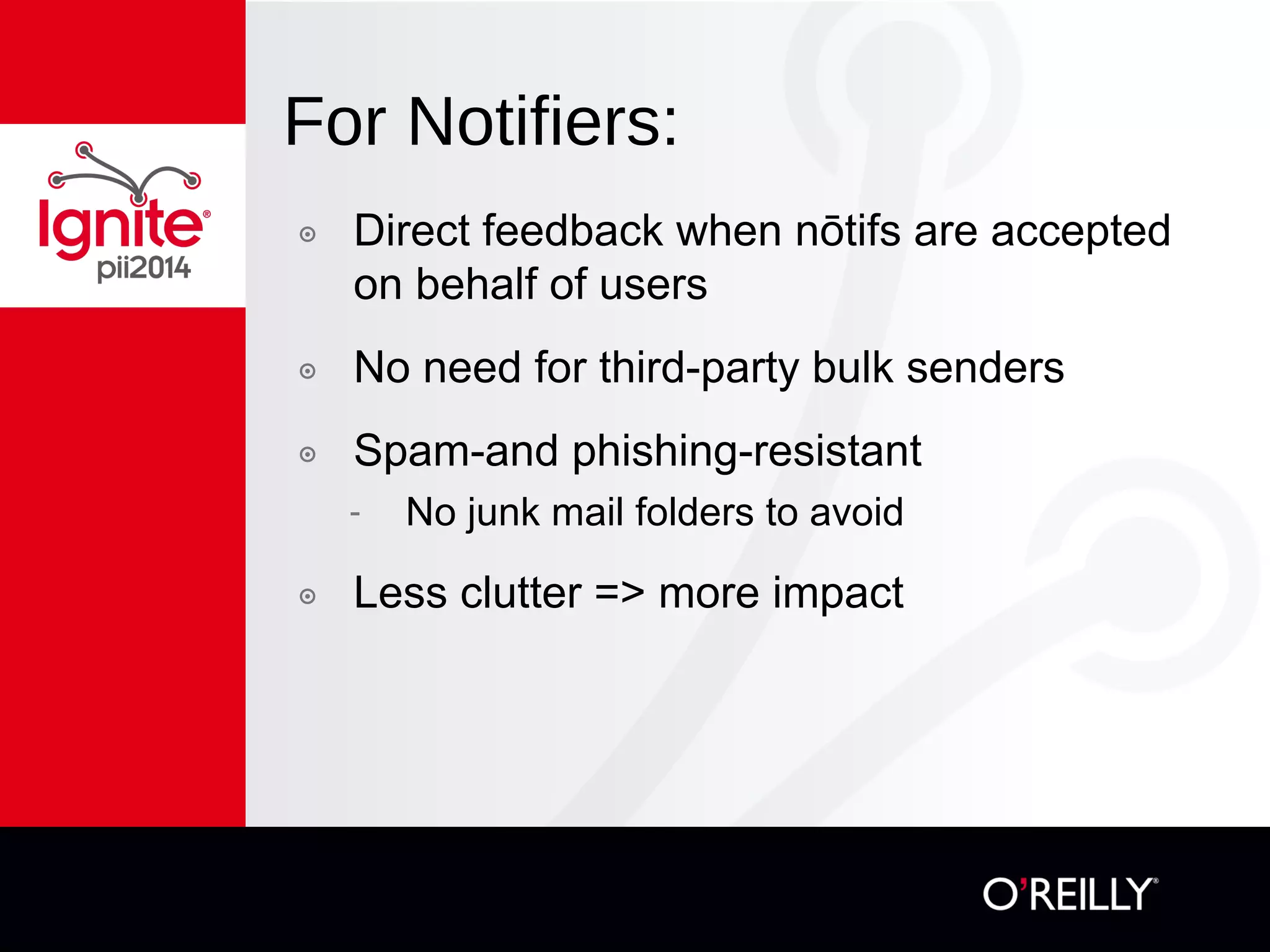
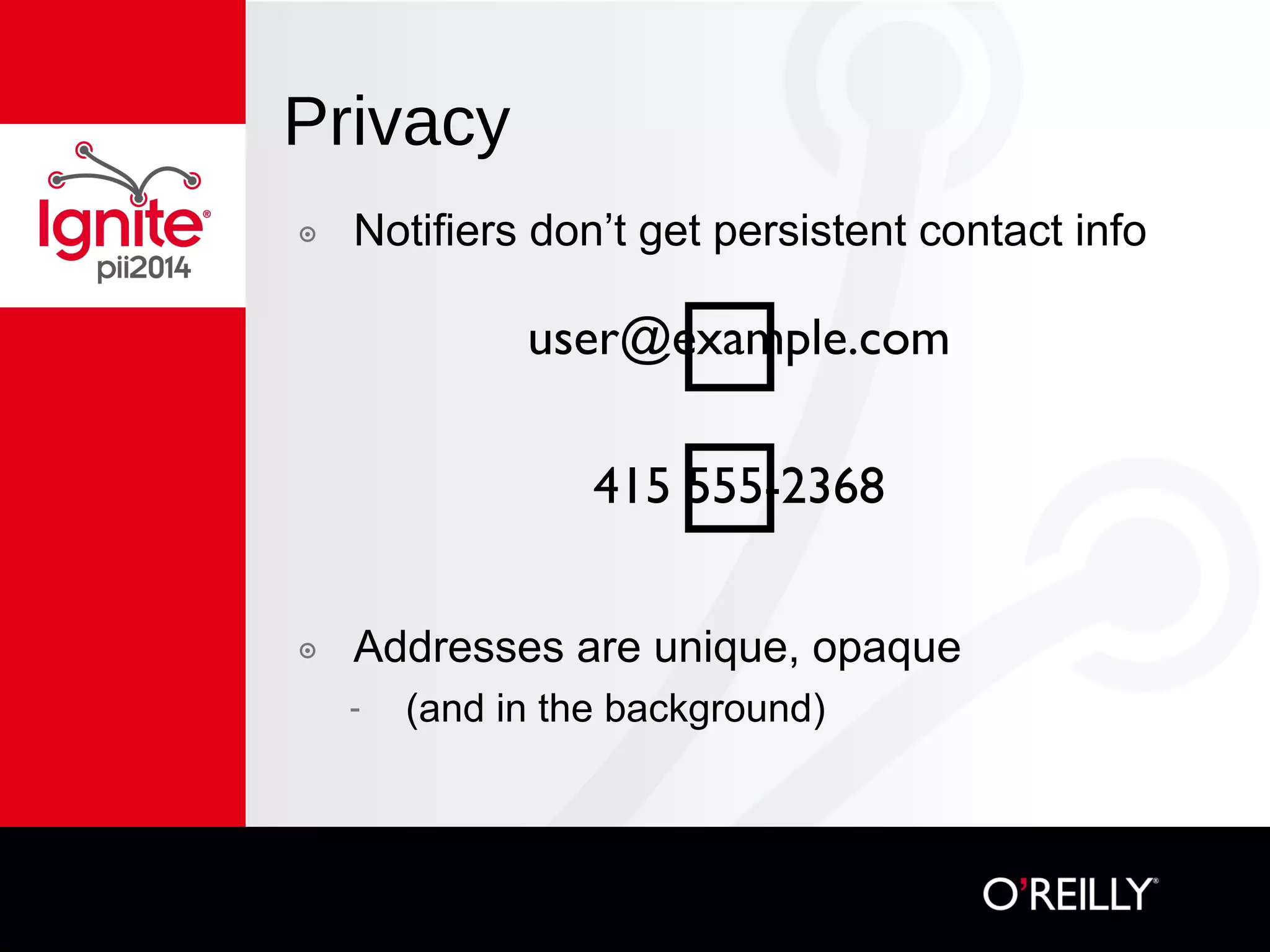
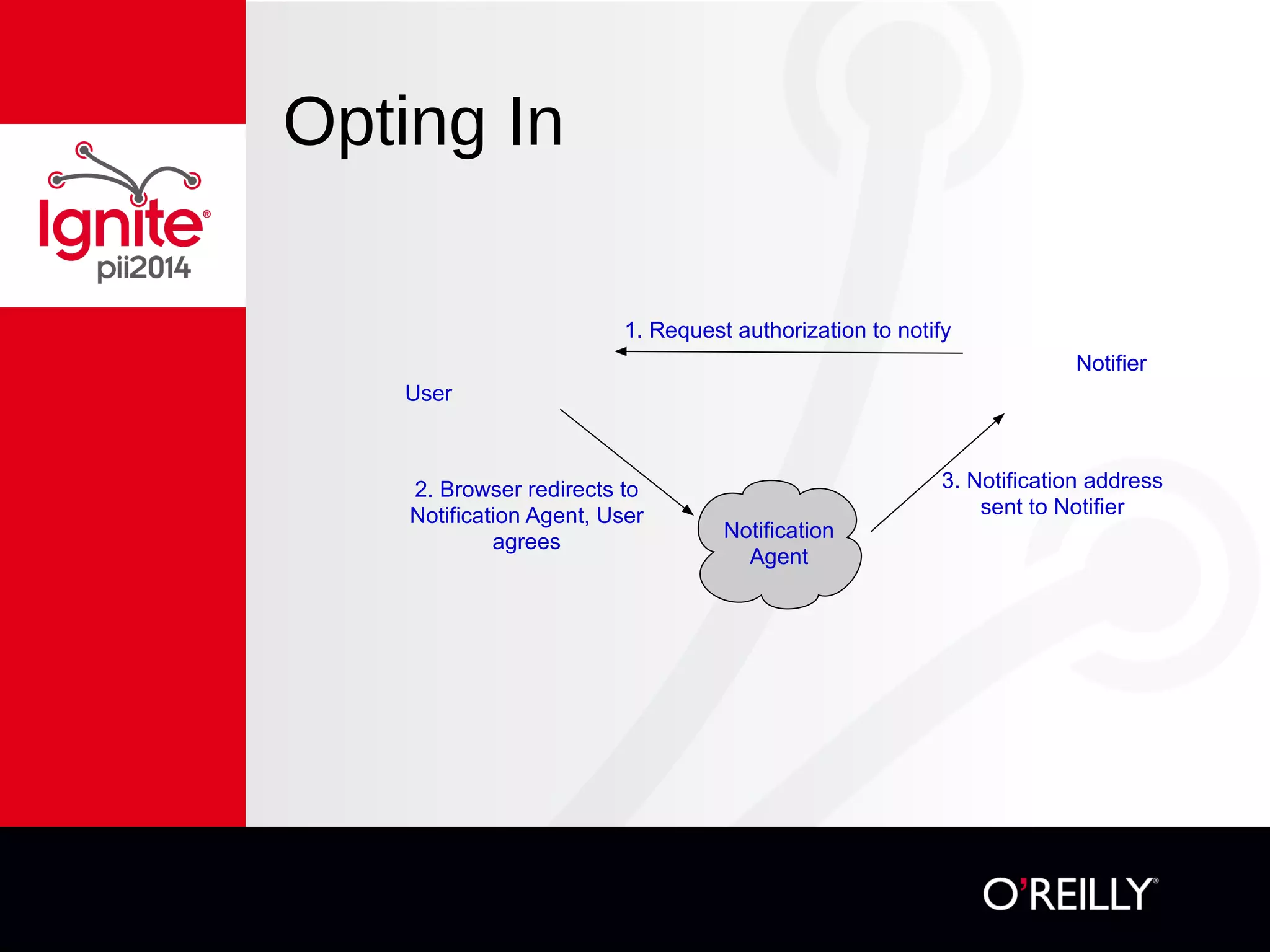
The document discusses the concept of 'nōtifs', a new notification management system aiming to provide users with more control over how and when they receive notifications, particularly in the context of mobile usage. Nōtifs are characterized as one-way, solicited, time-sensitive messages that enable centralized management, spam resistance, and user-defined preferences for alerts. The system includes mechanisms for updating, deleting, and expiring notifications while promoting vendor independence and ease of integration with existing services.