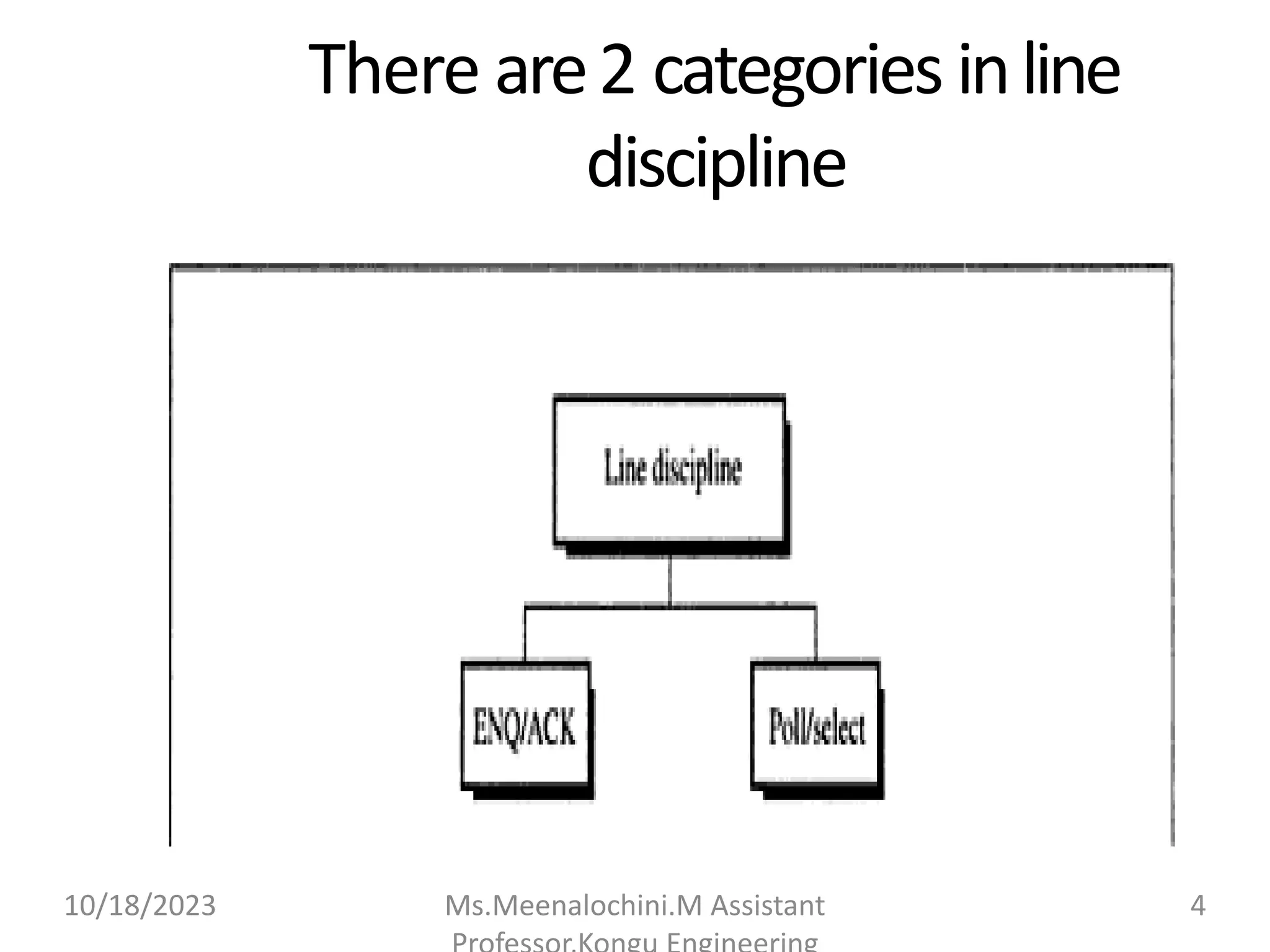
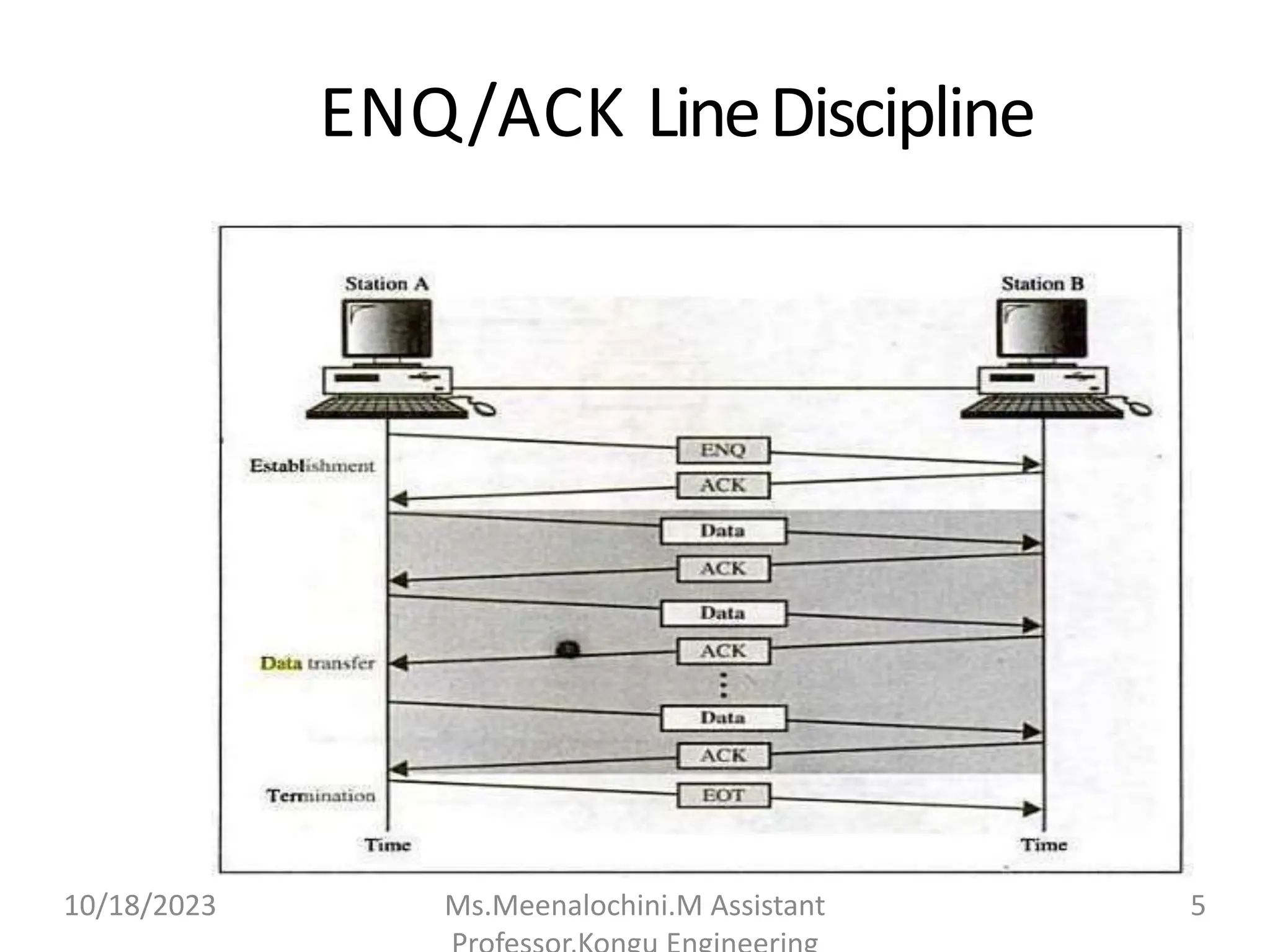
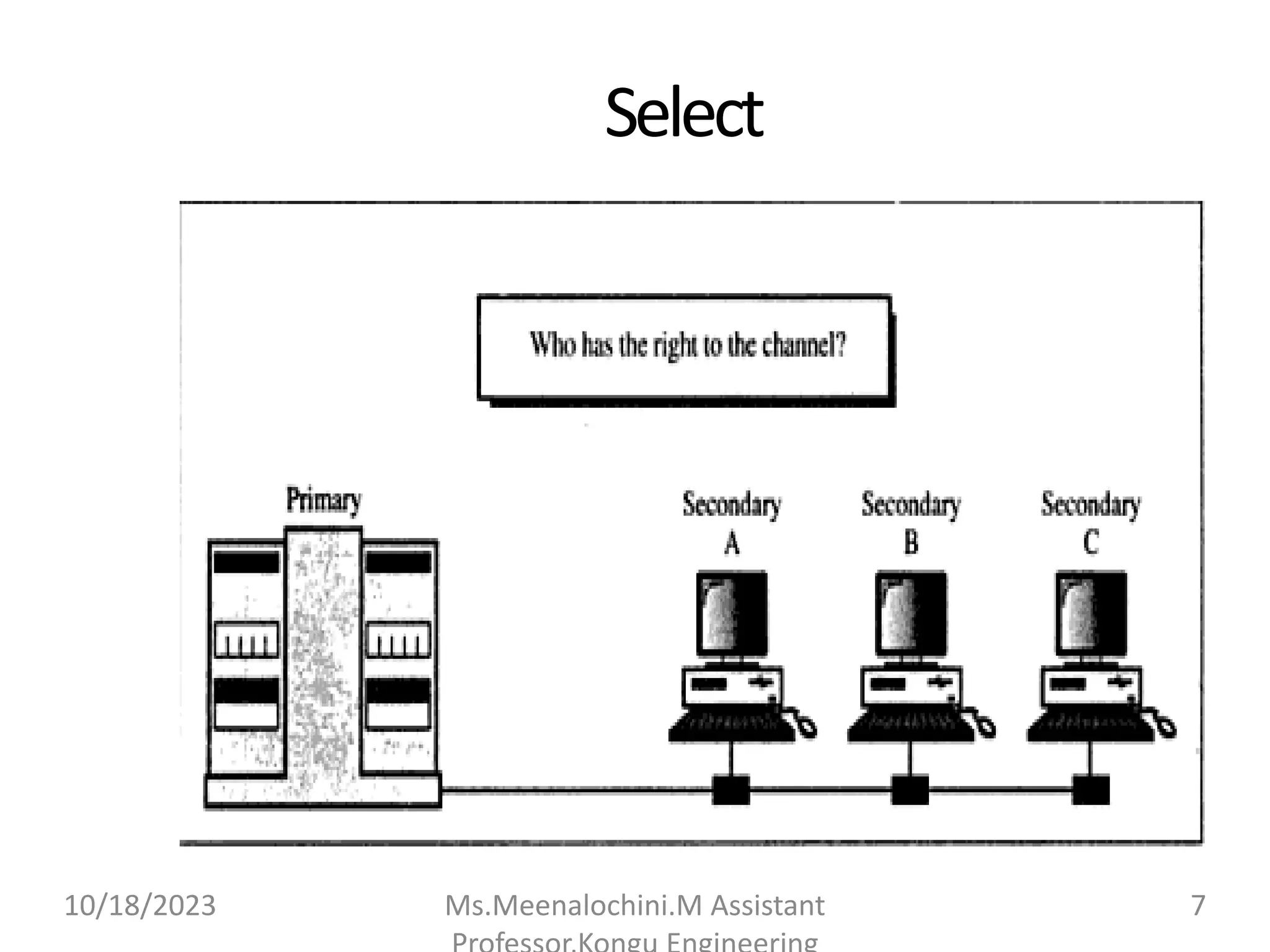
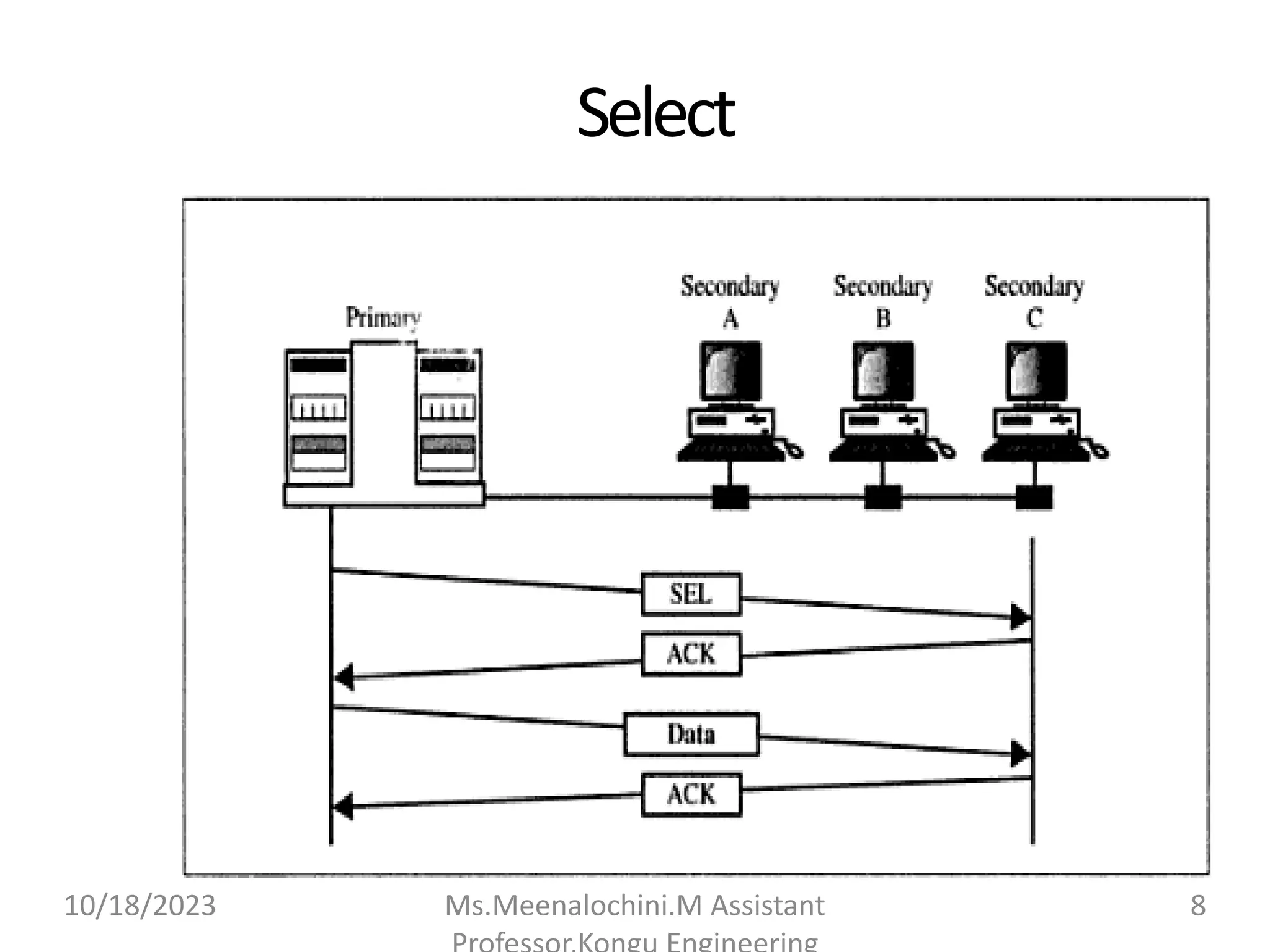
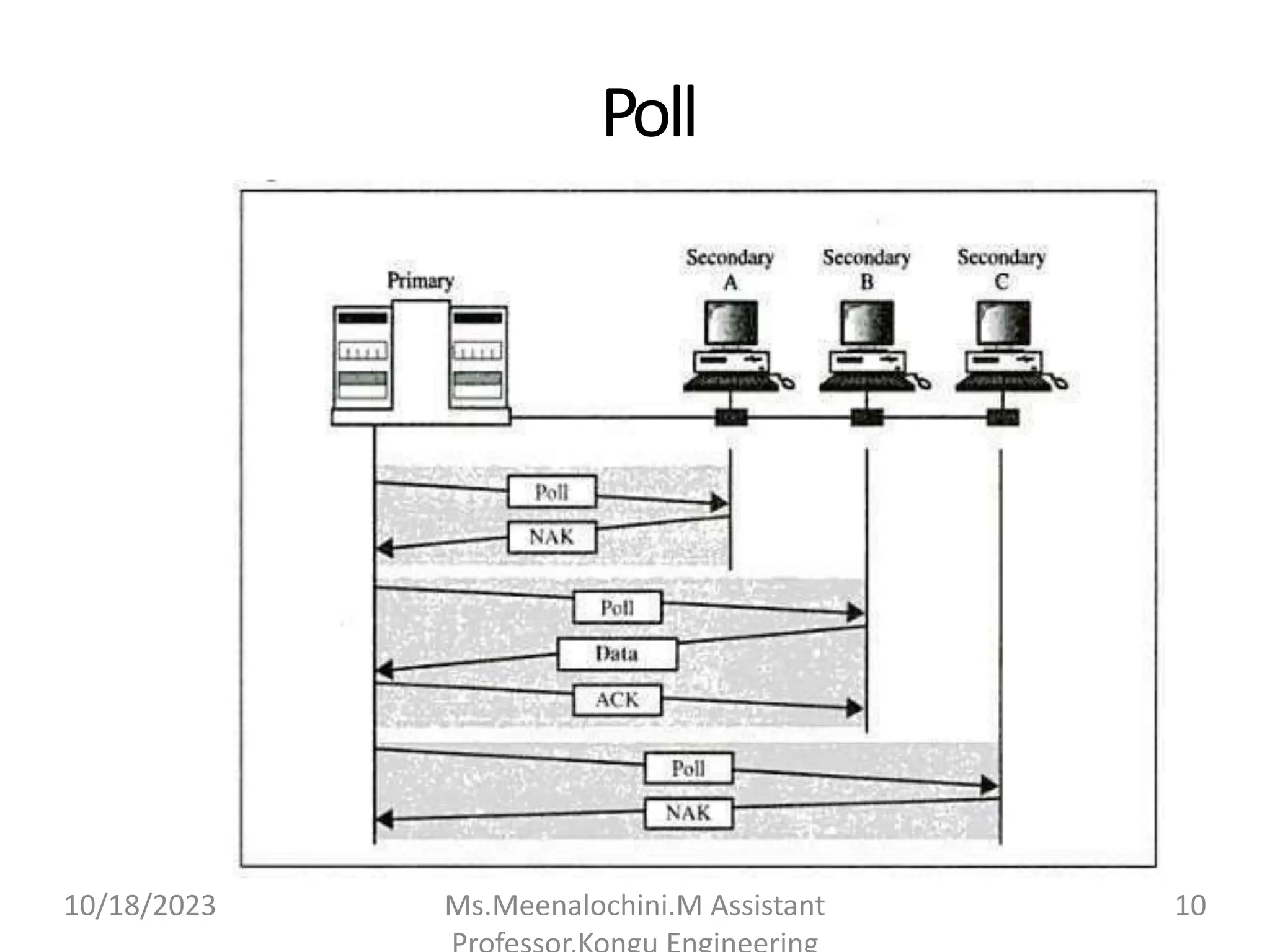
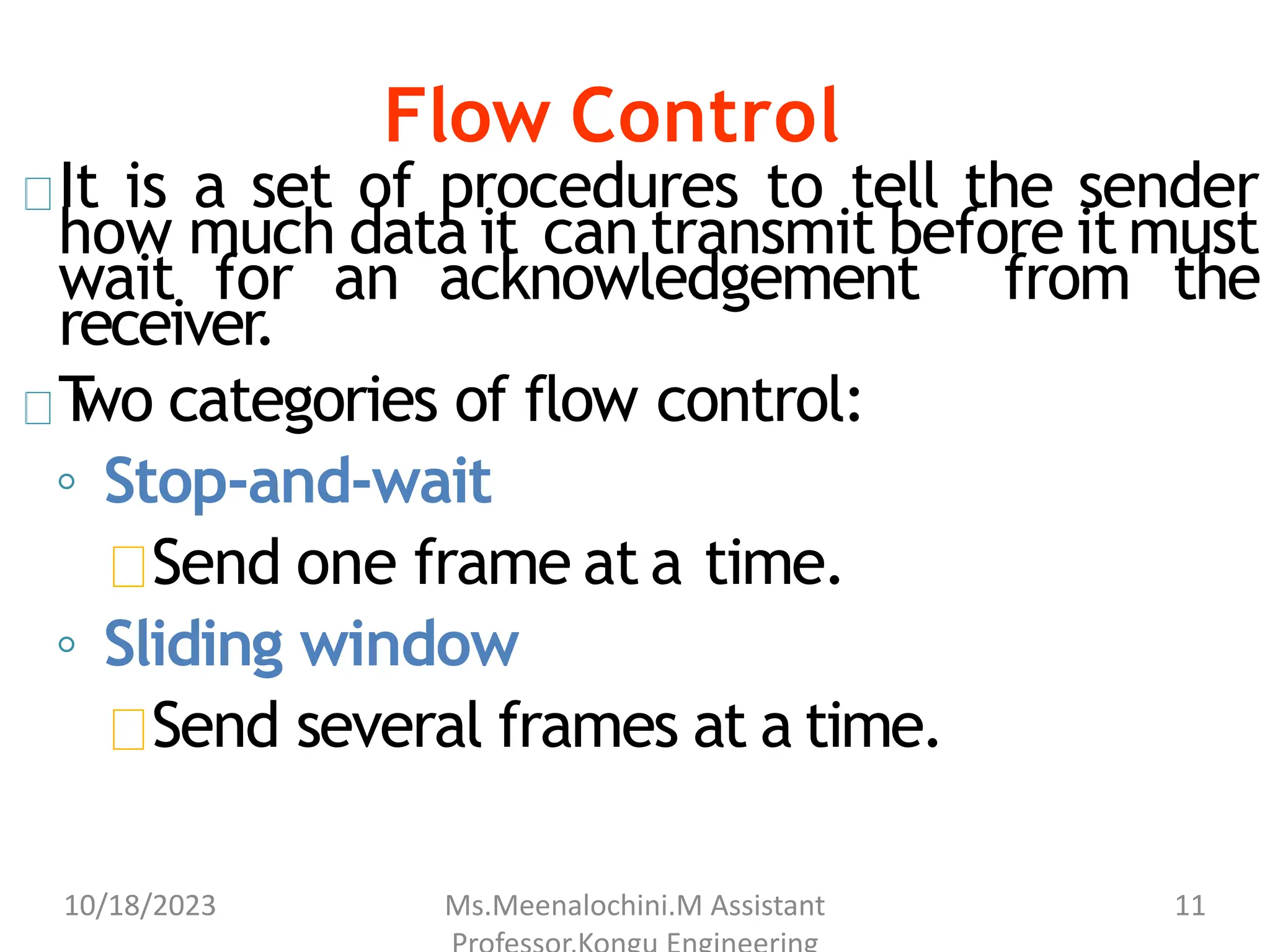
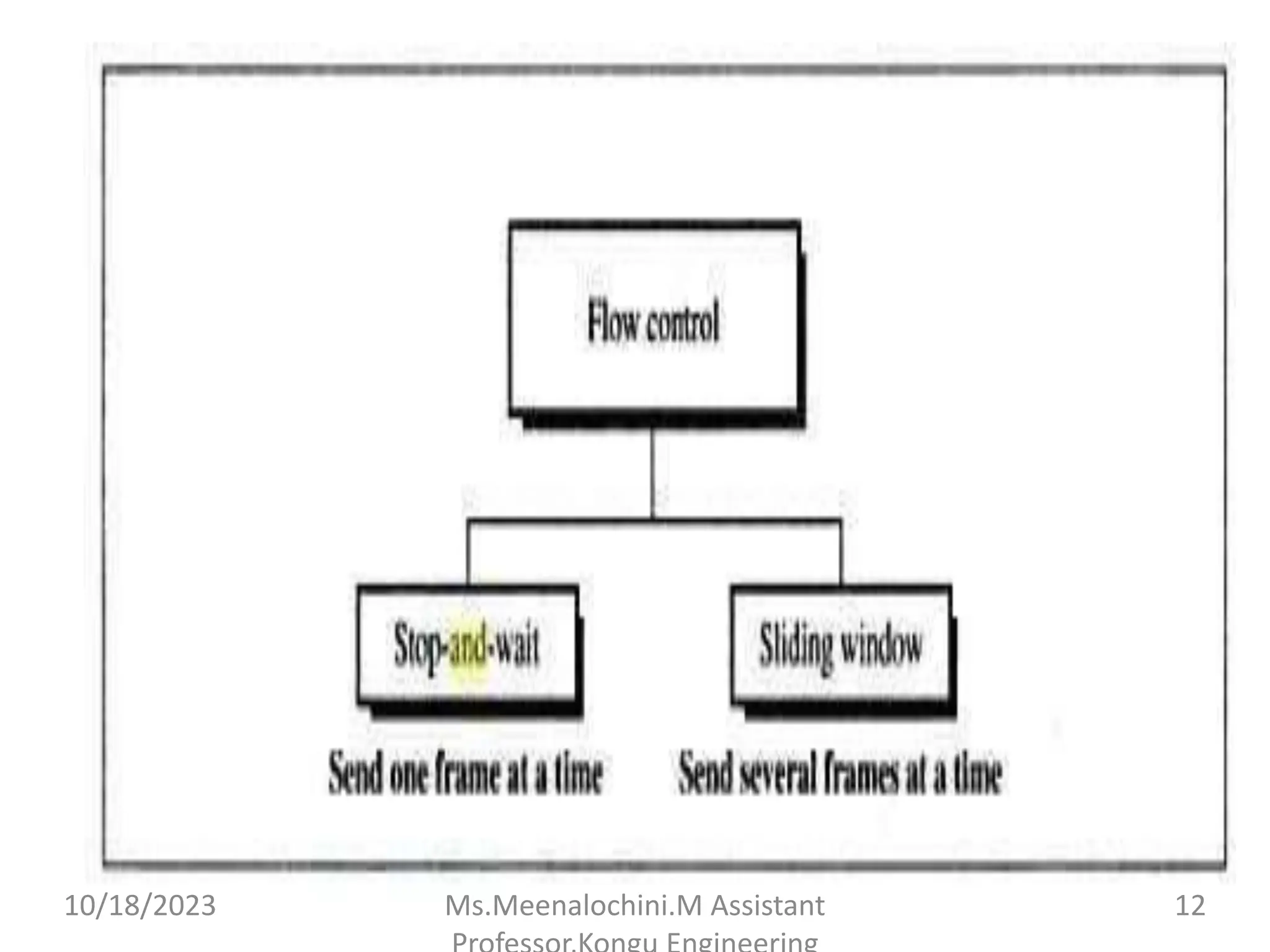
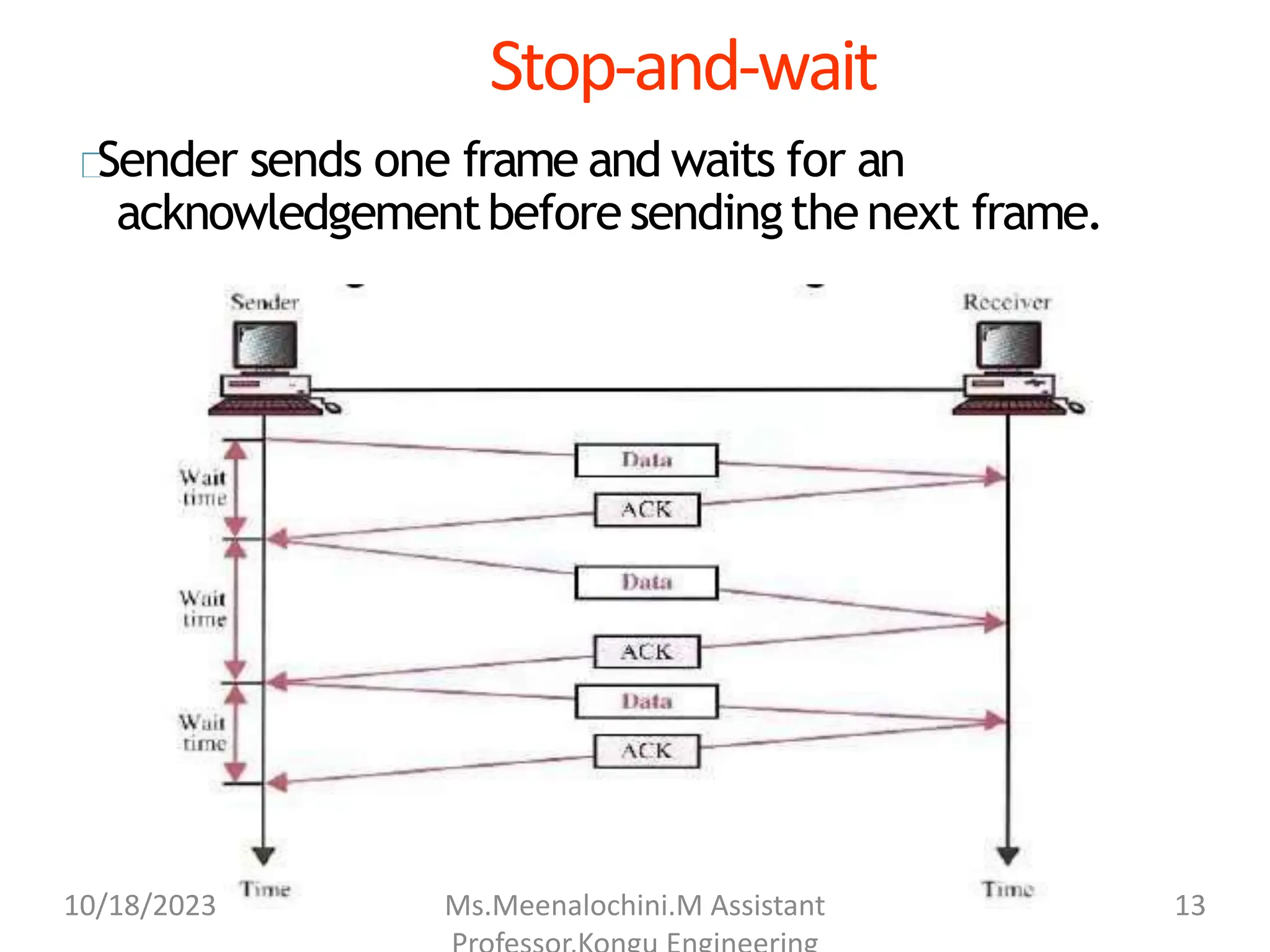
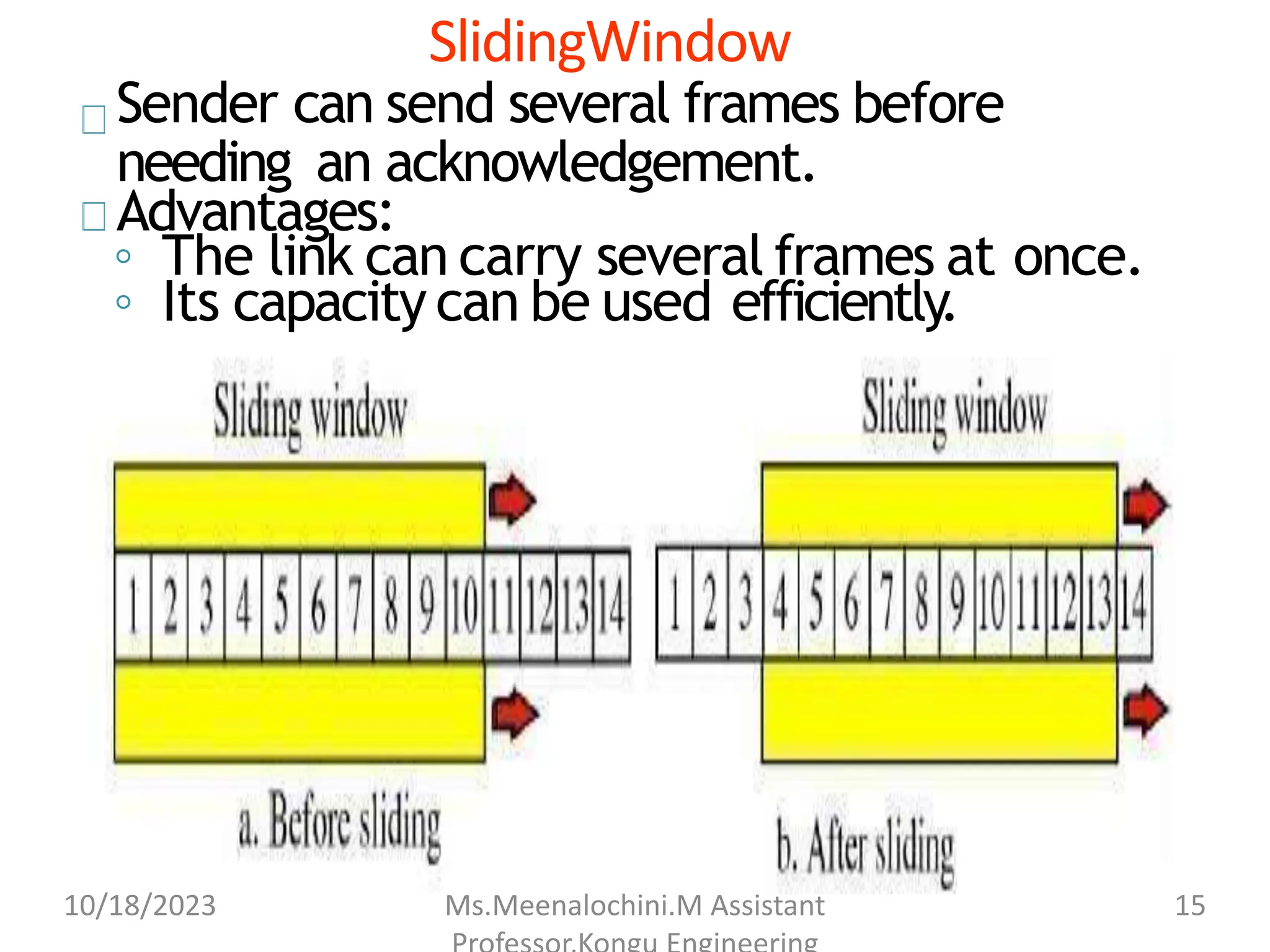
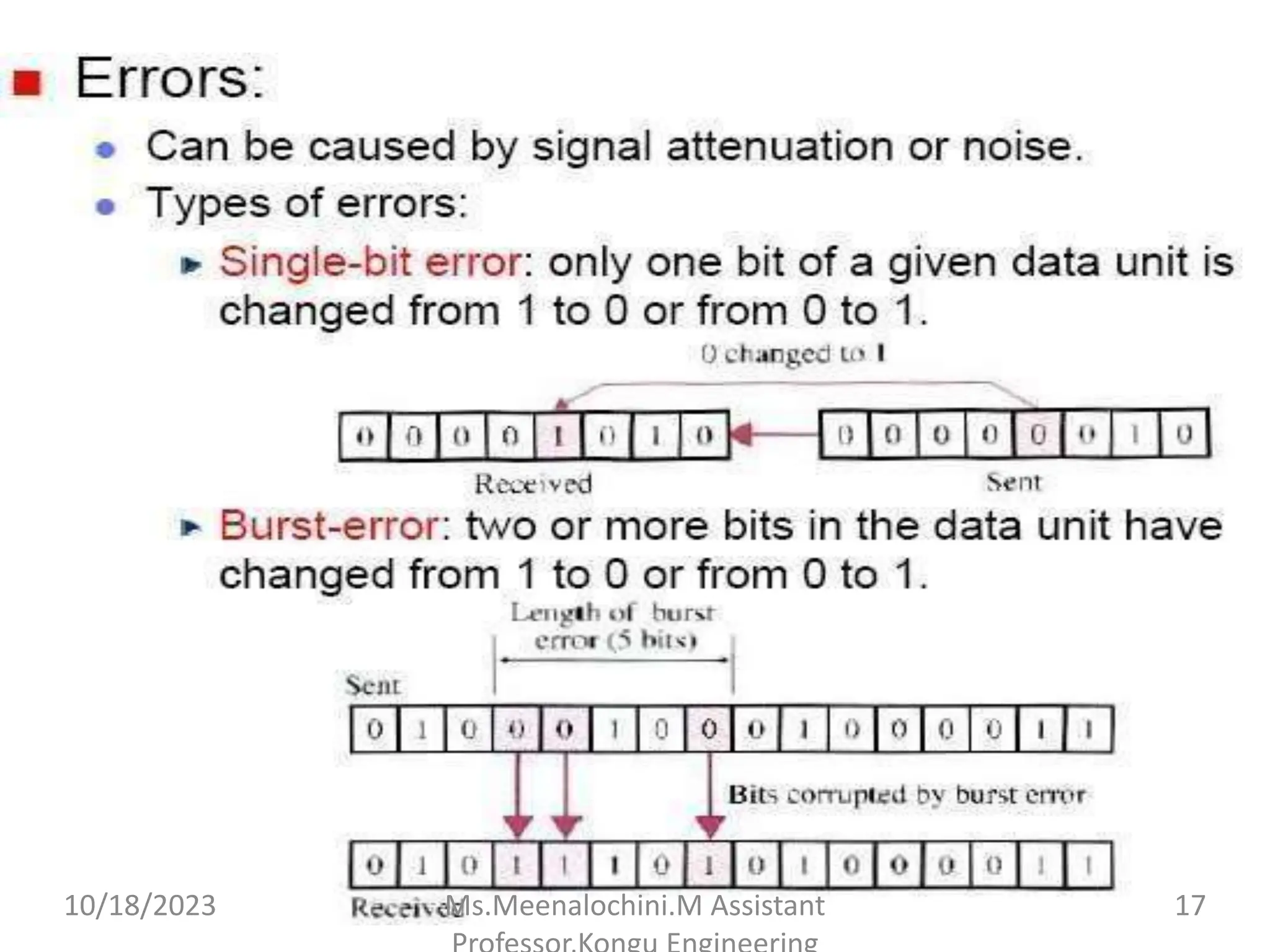
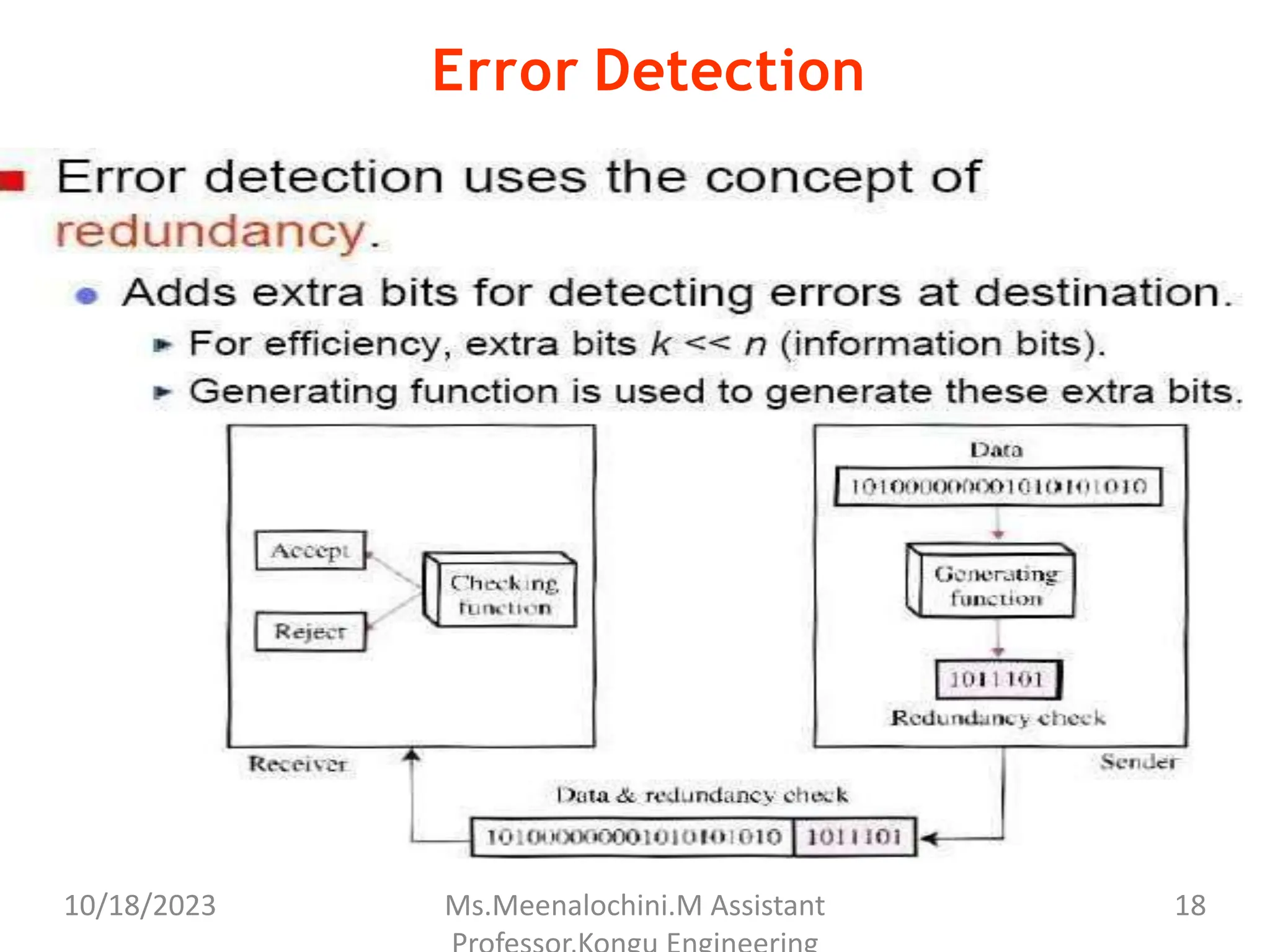
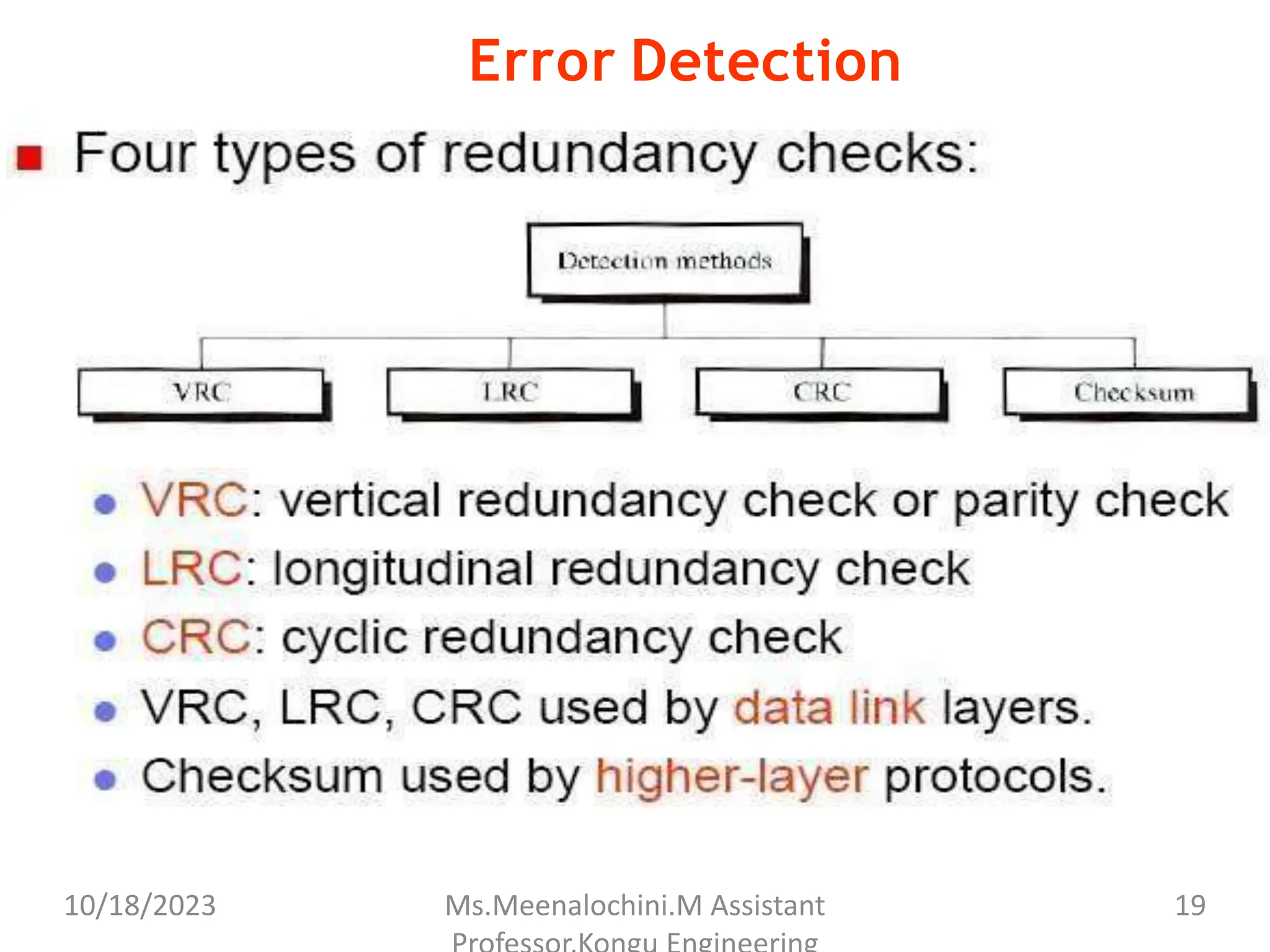
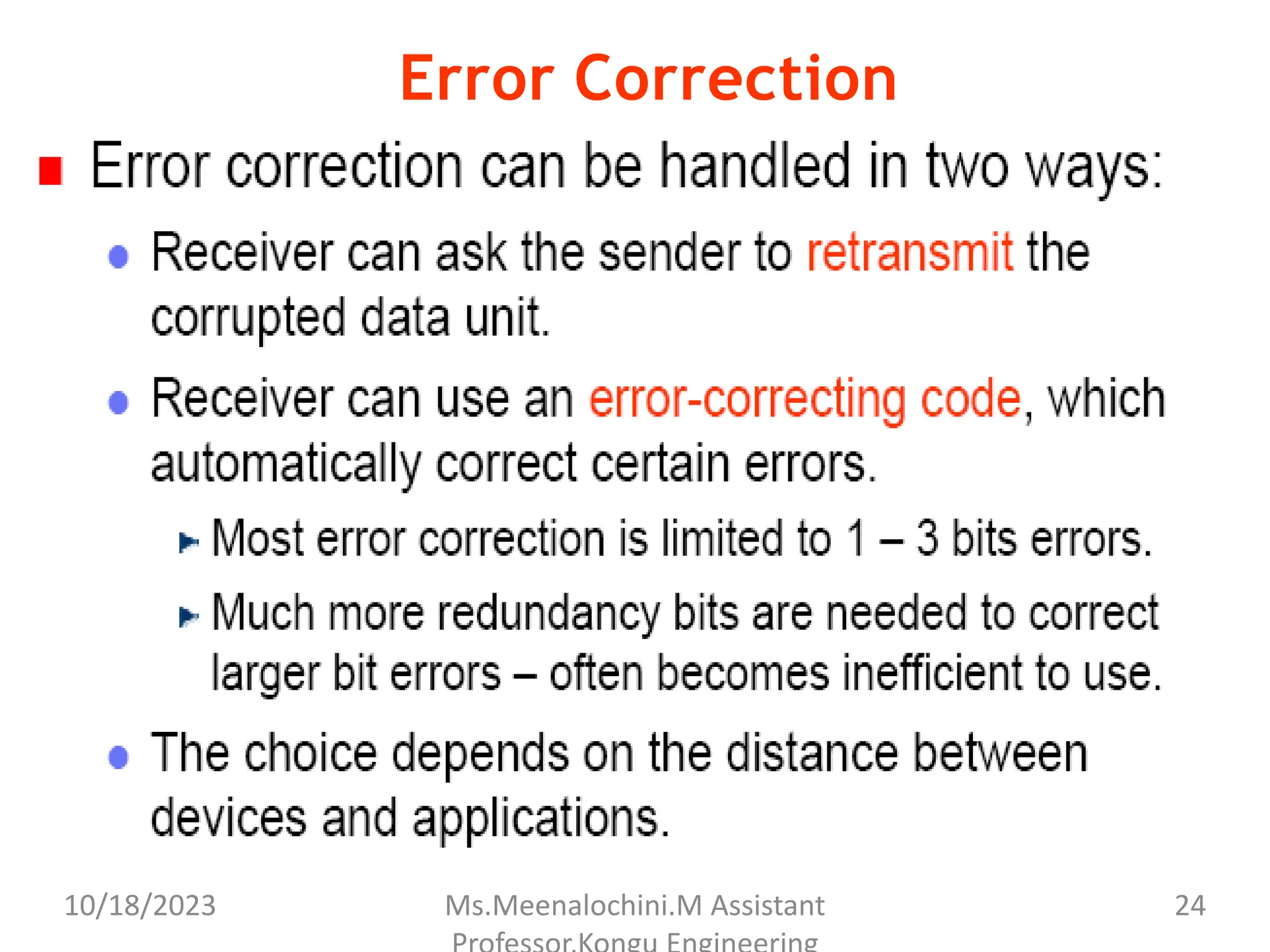
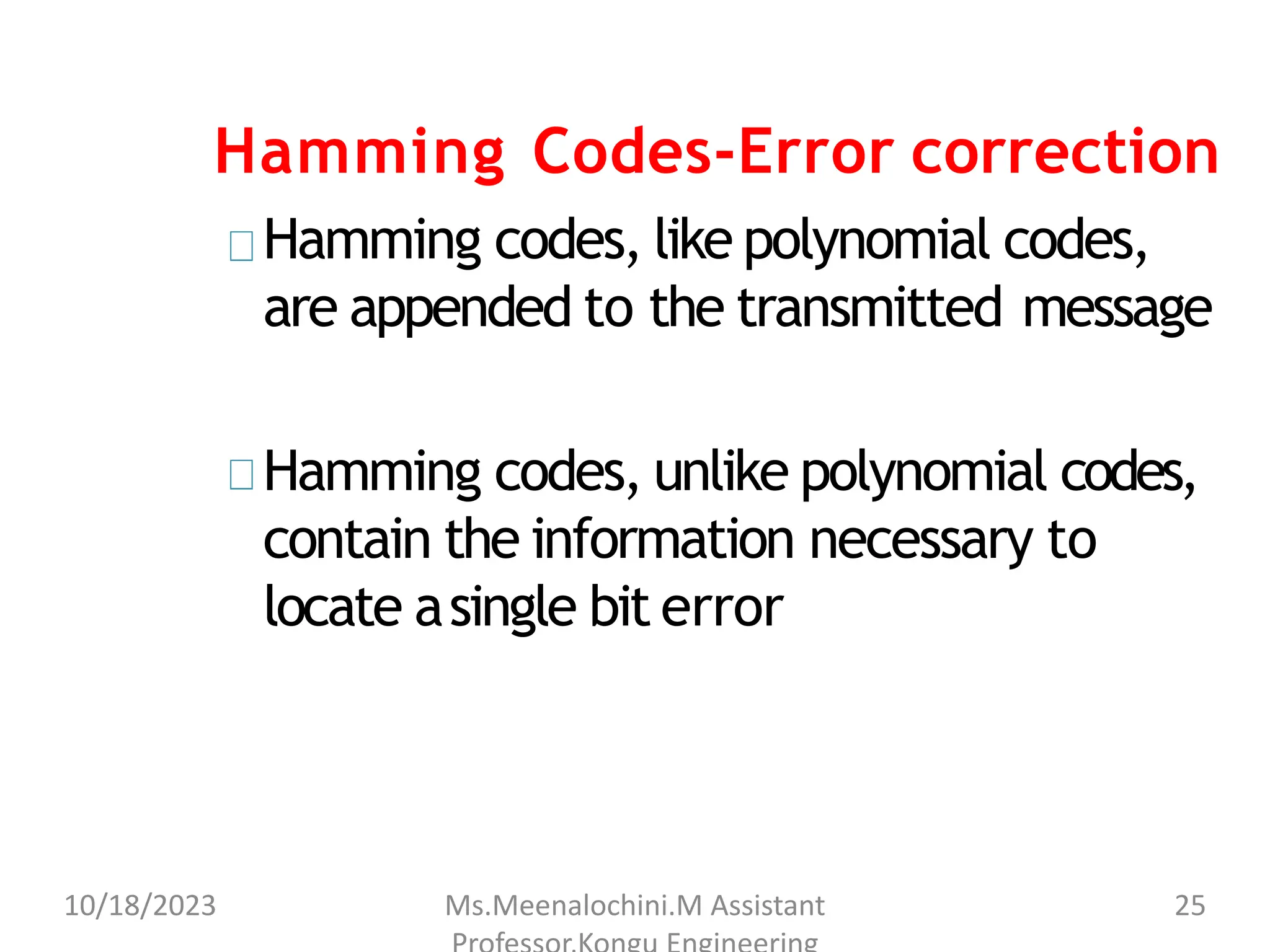
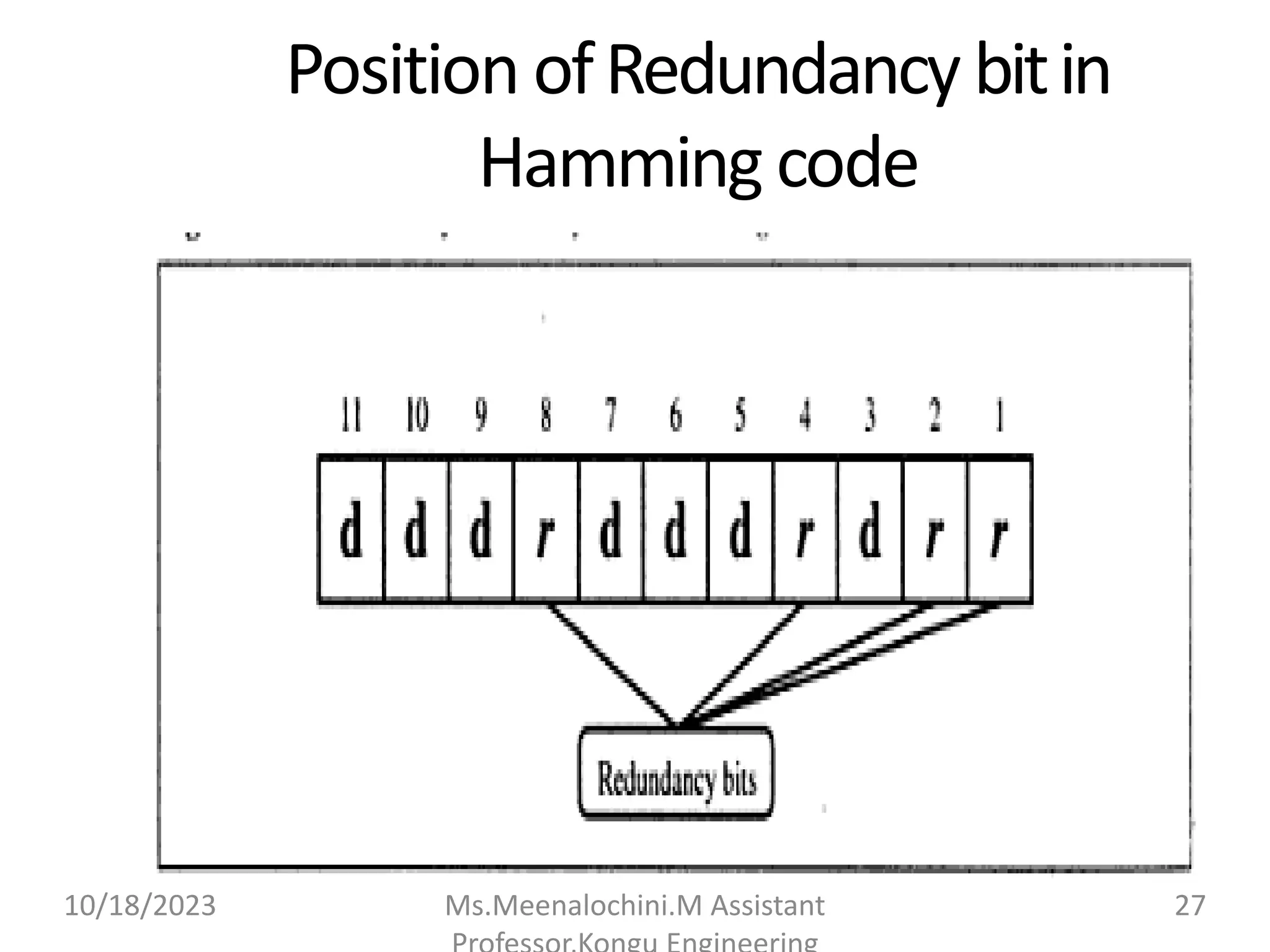
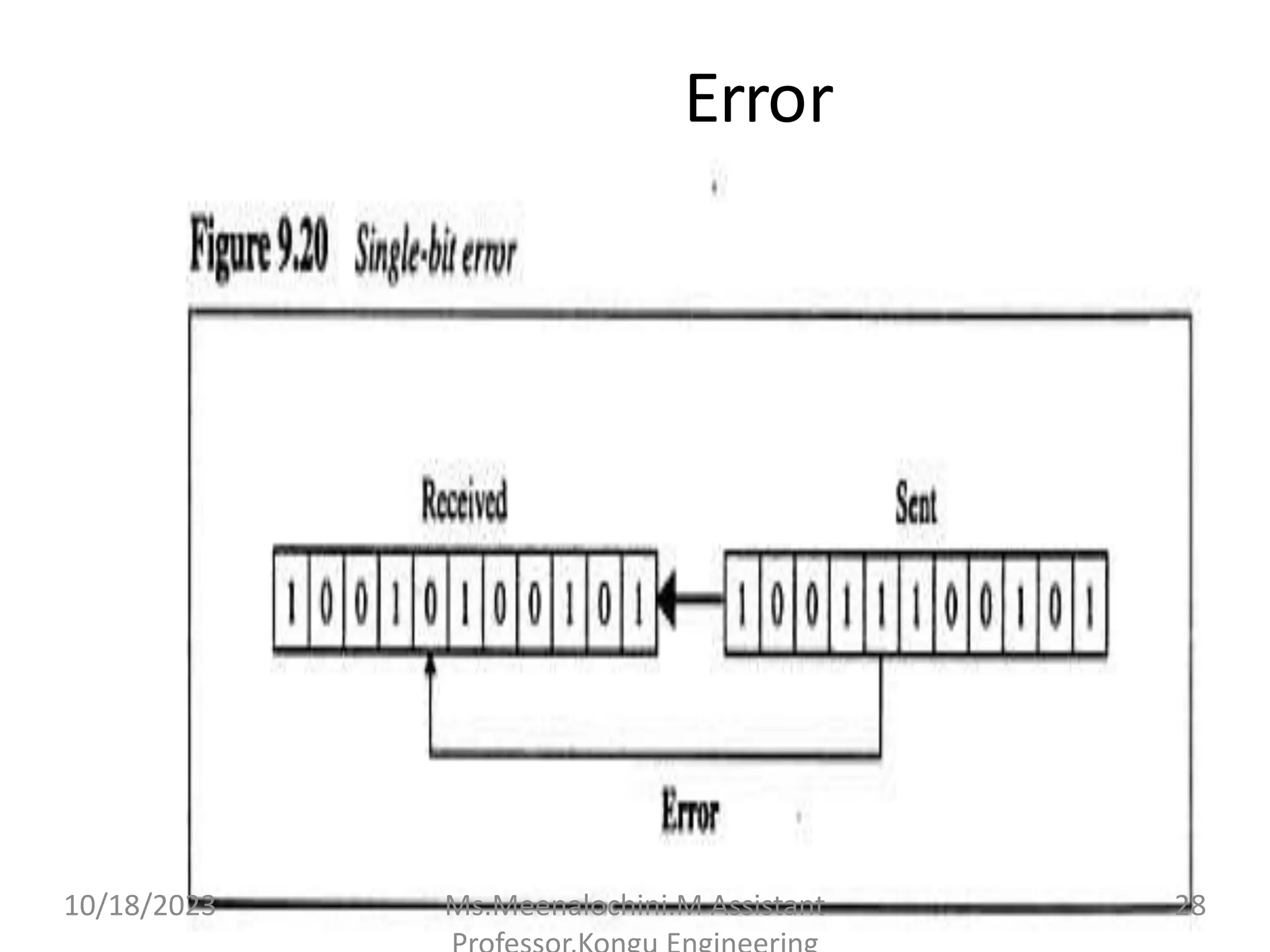
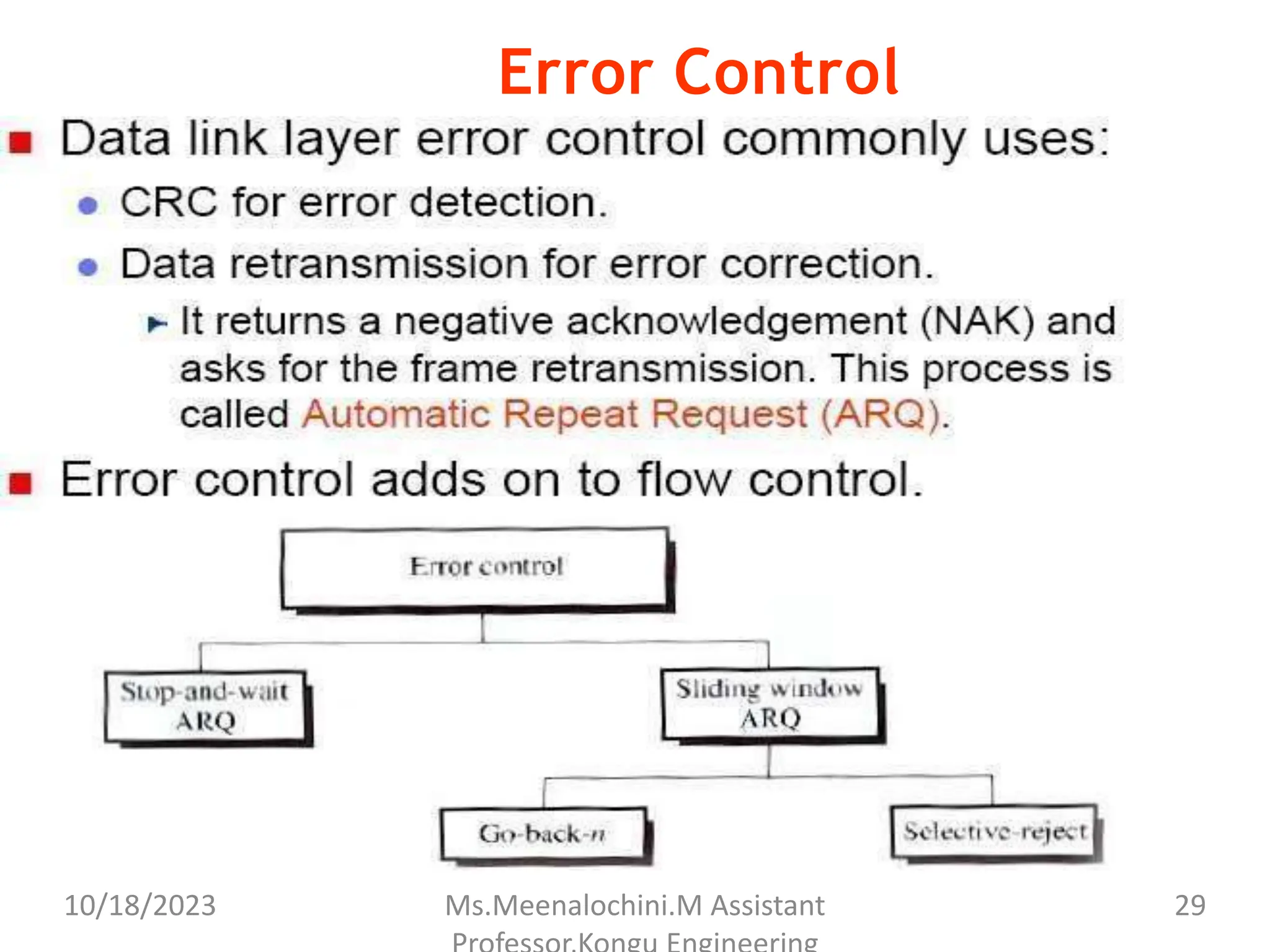
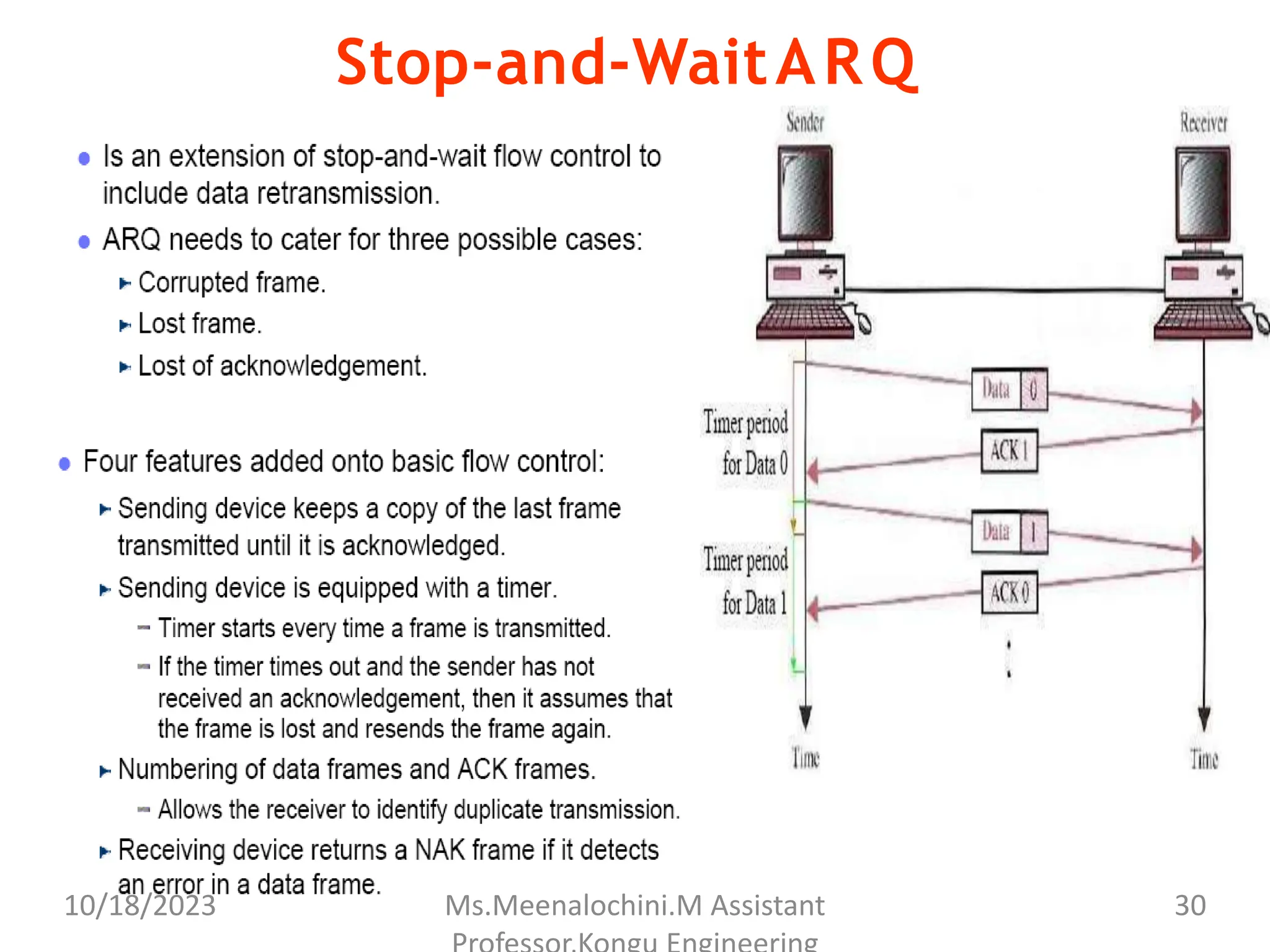
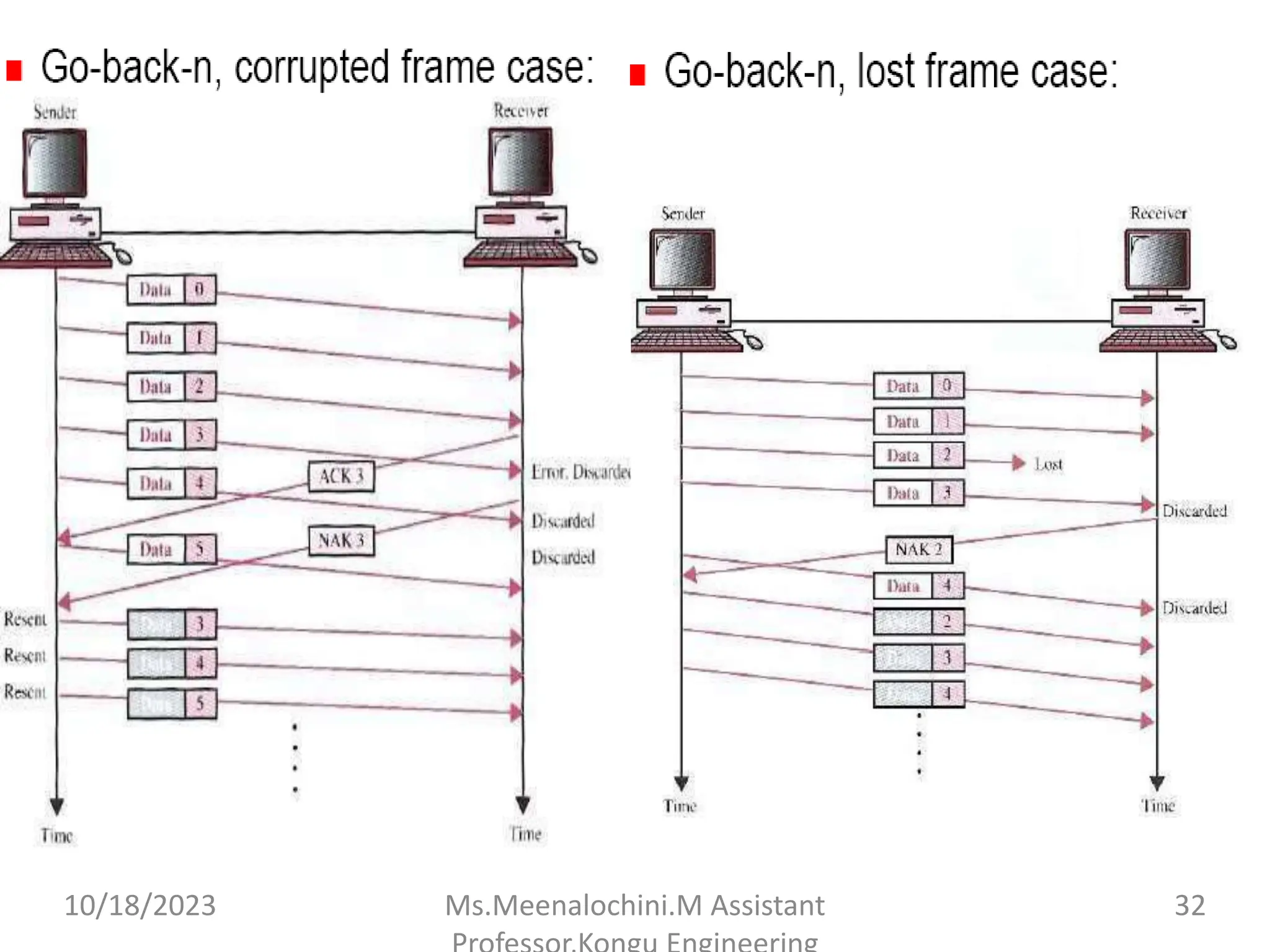
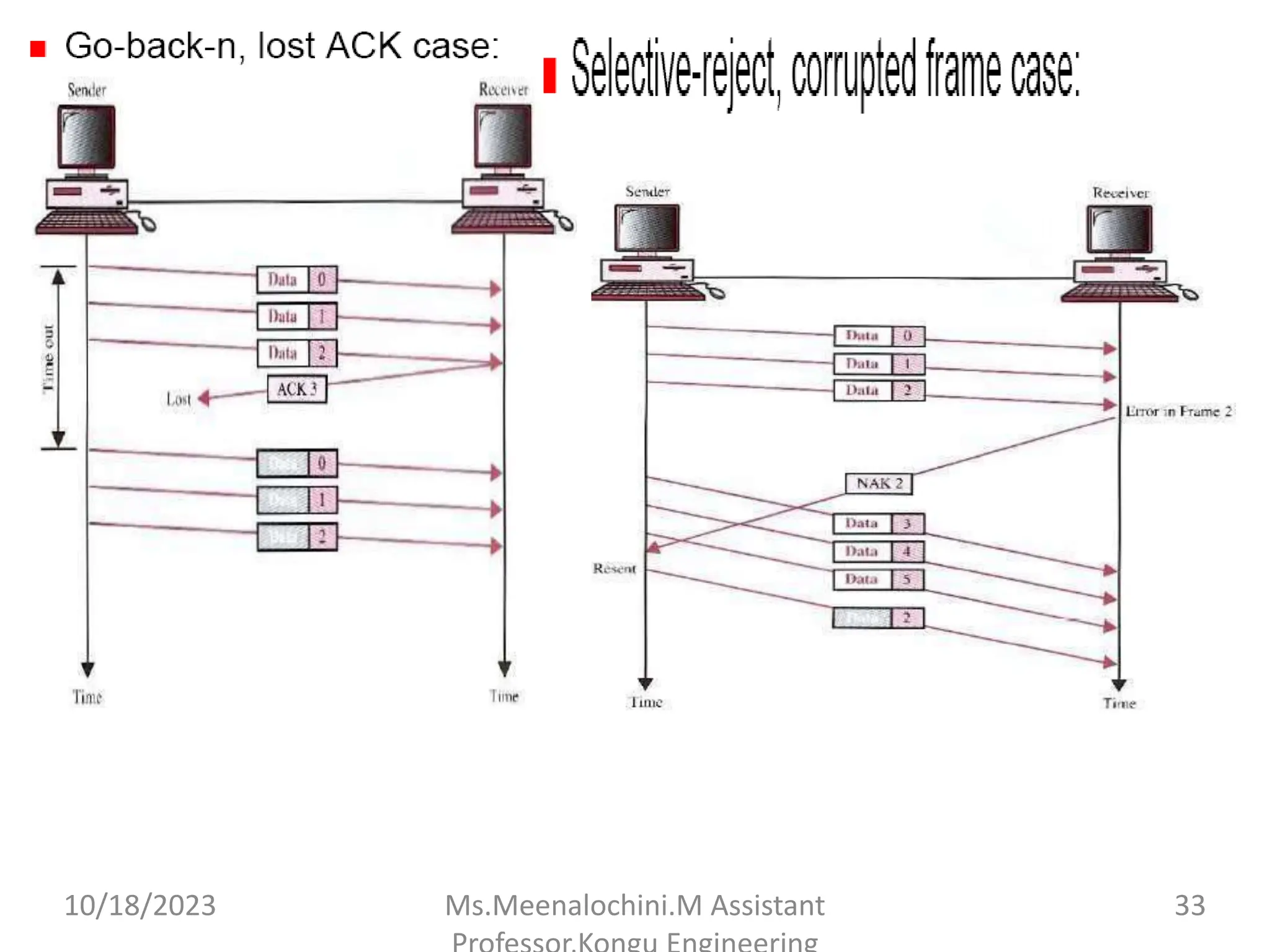
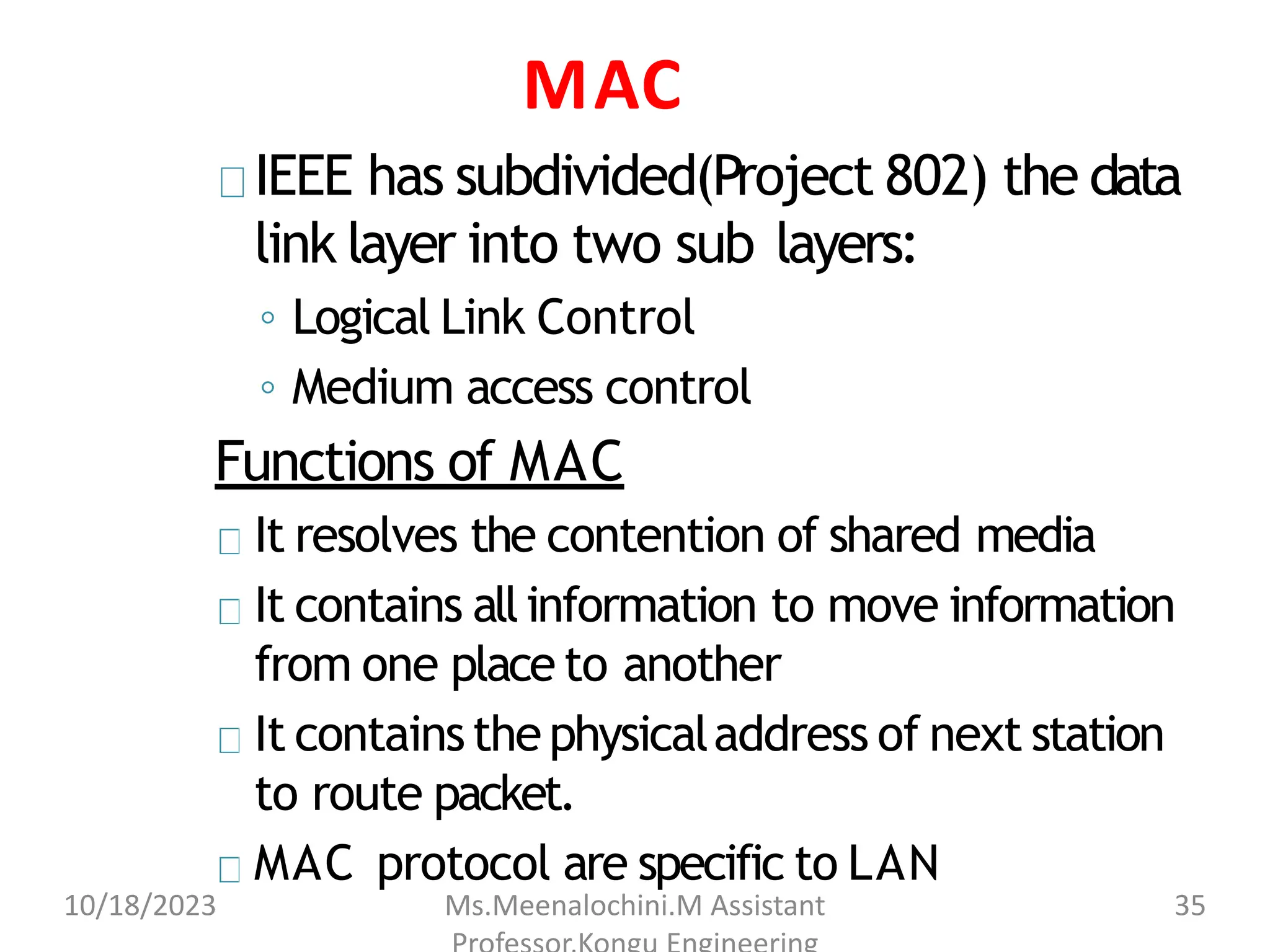
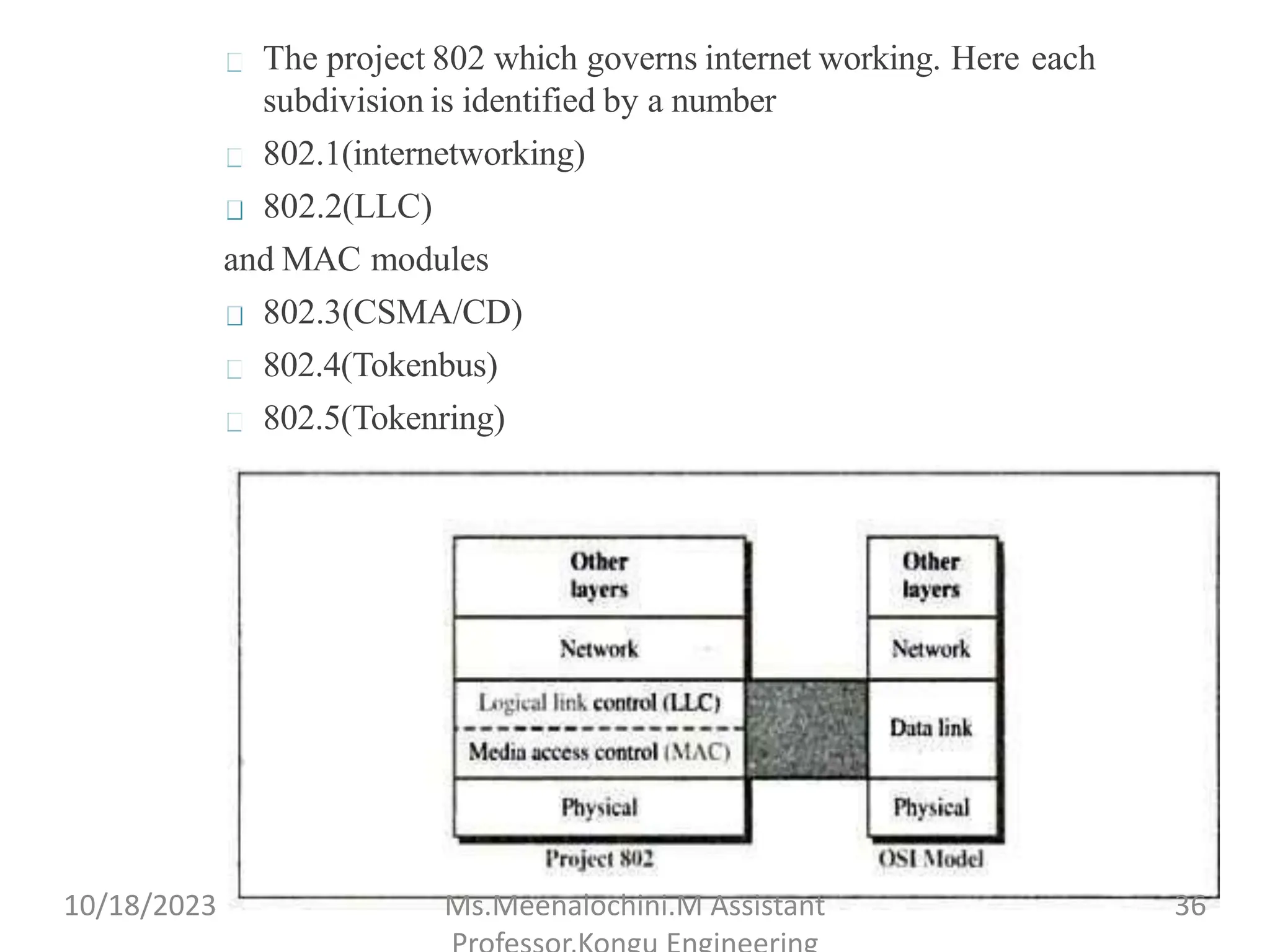
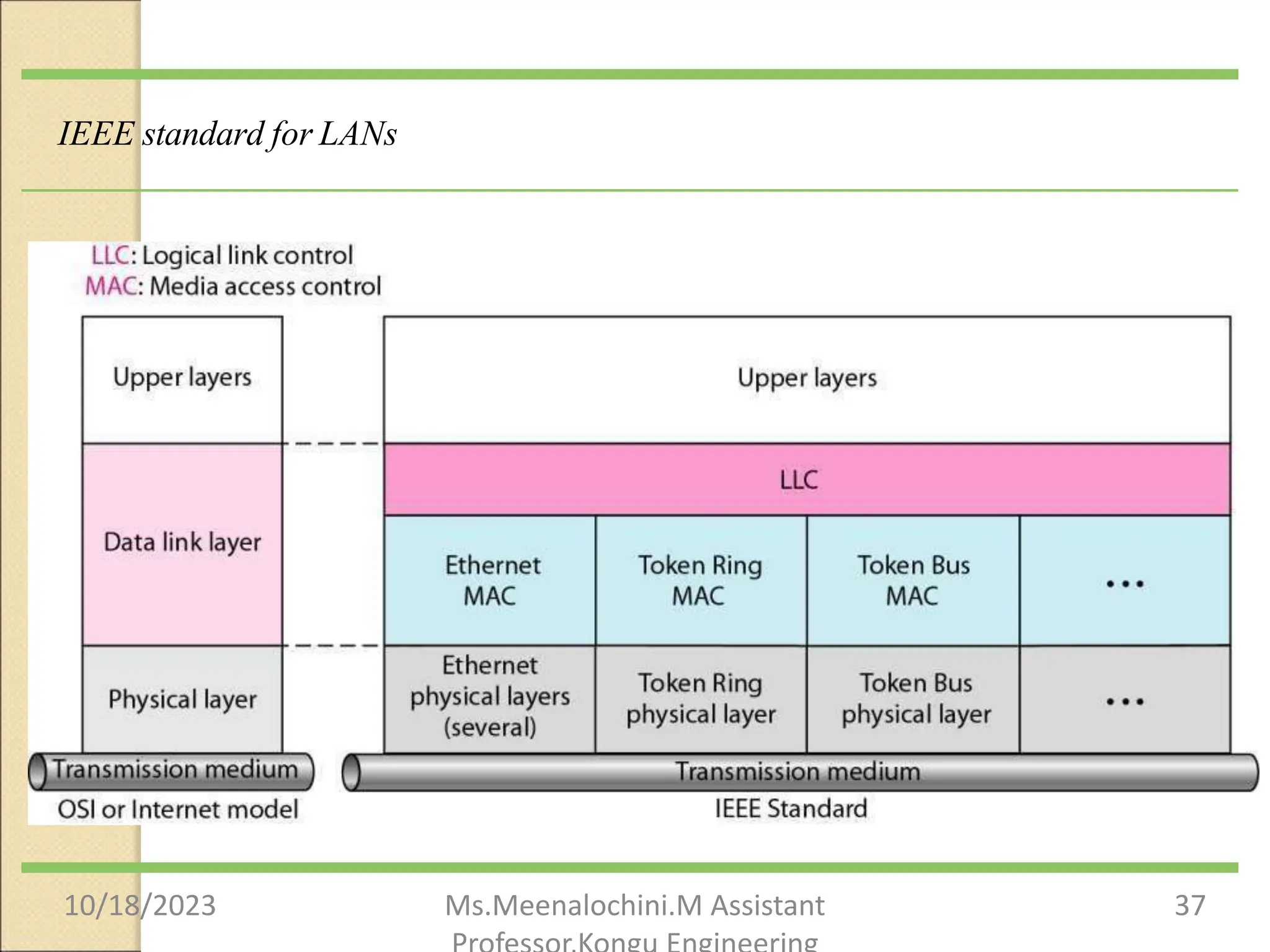
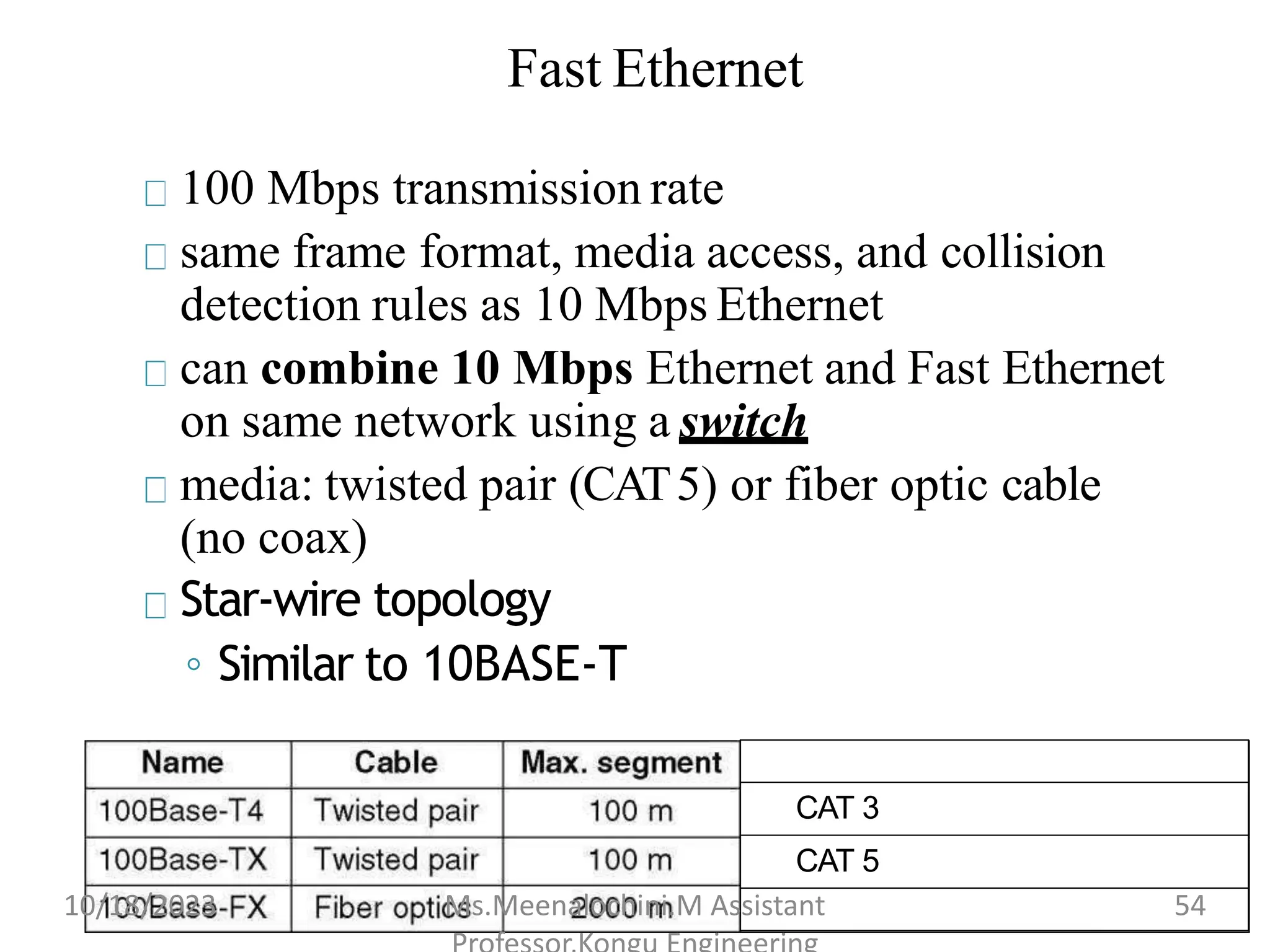
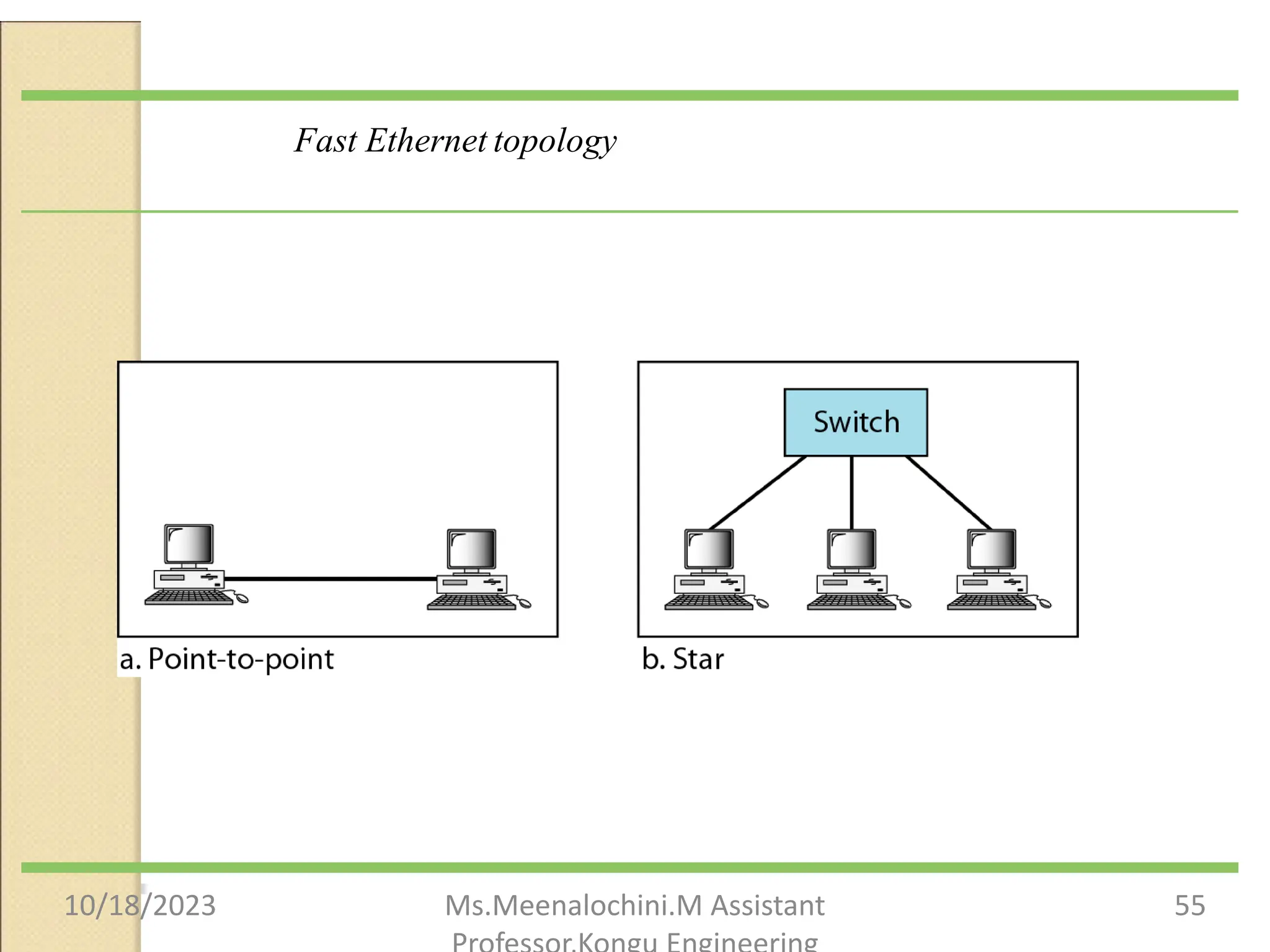
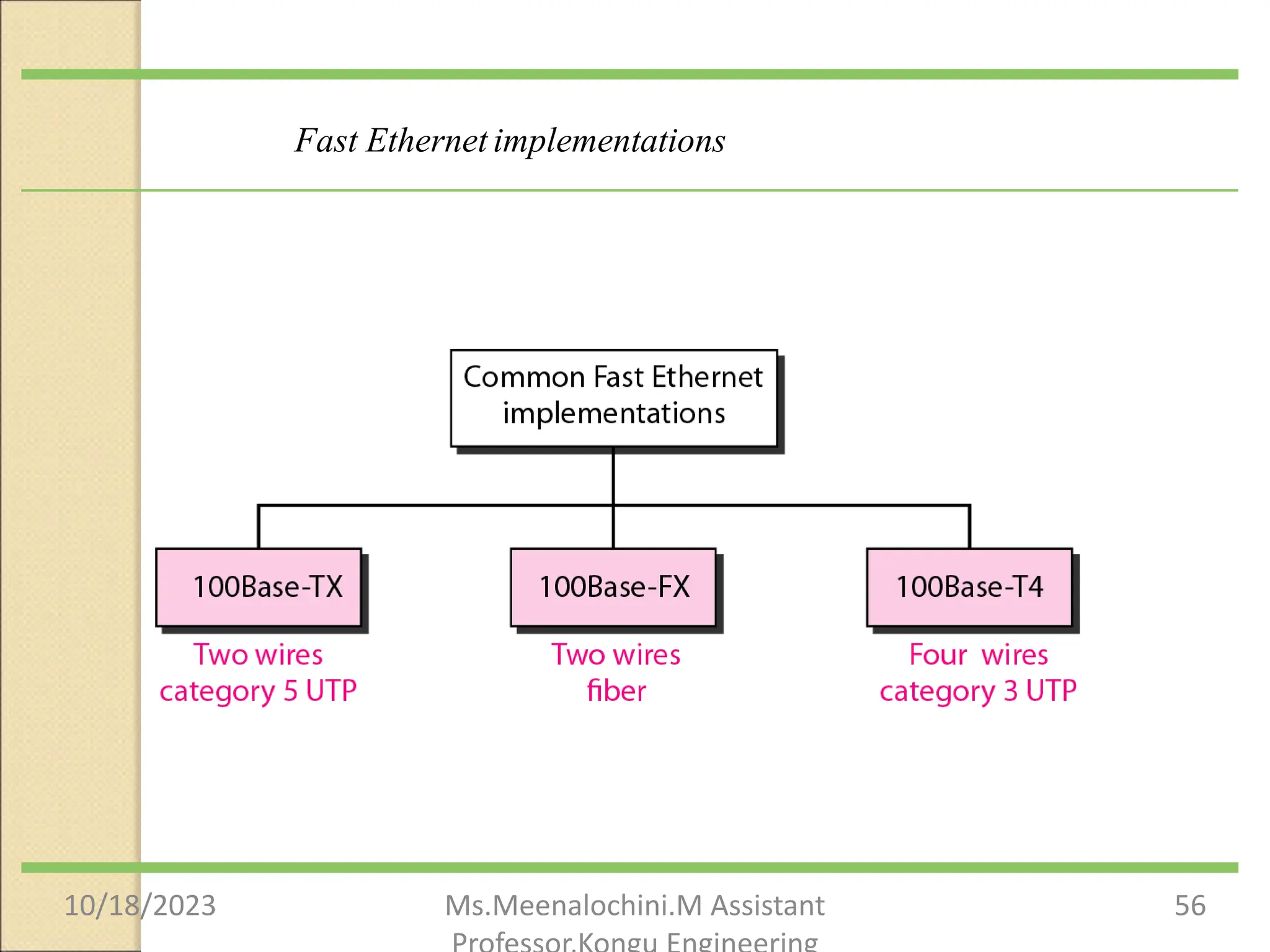
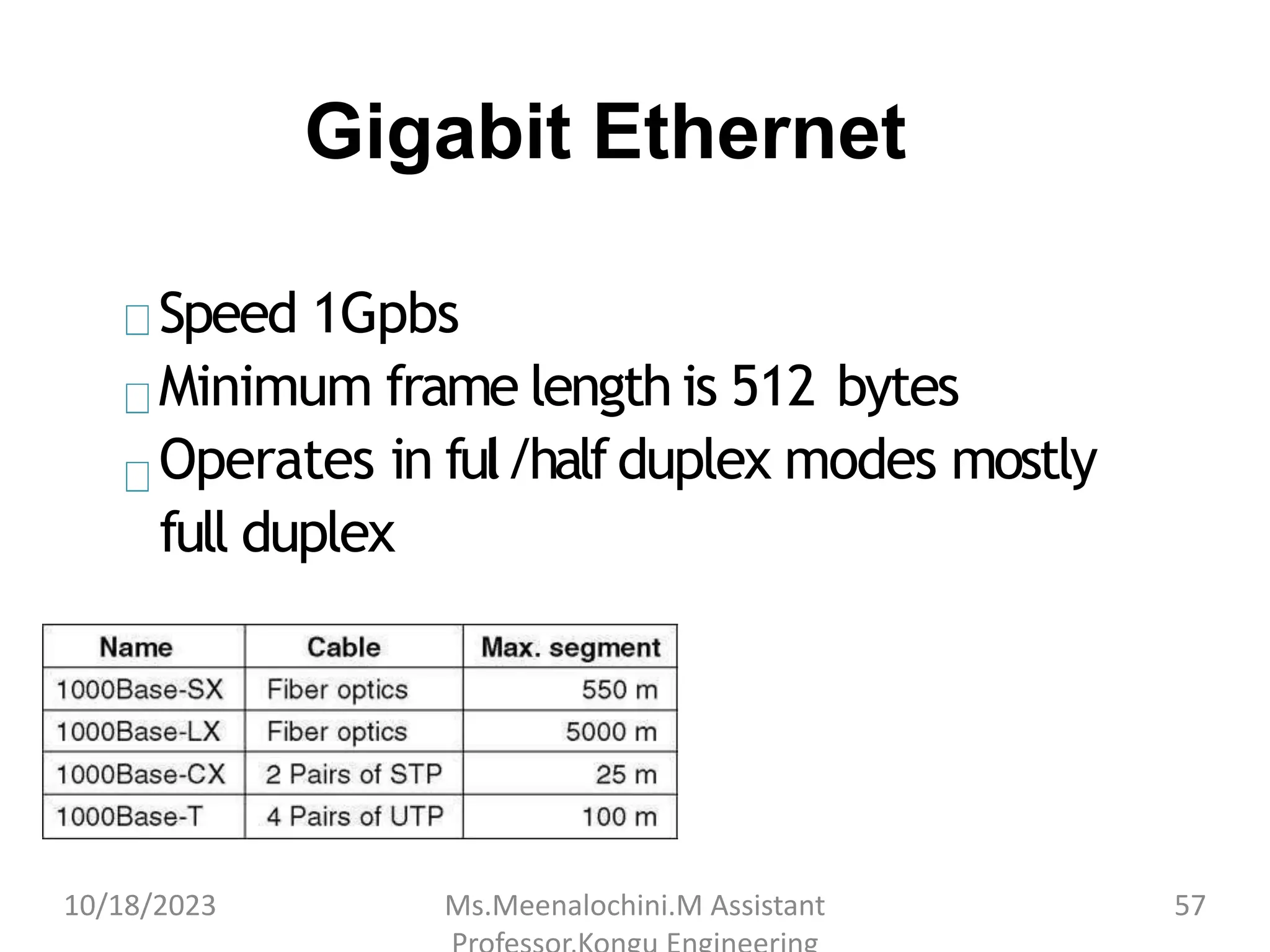
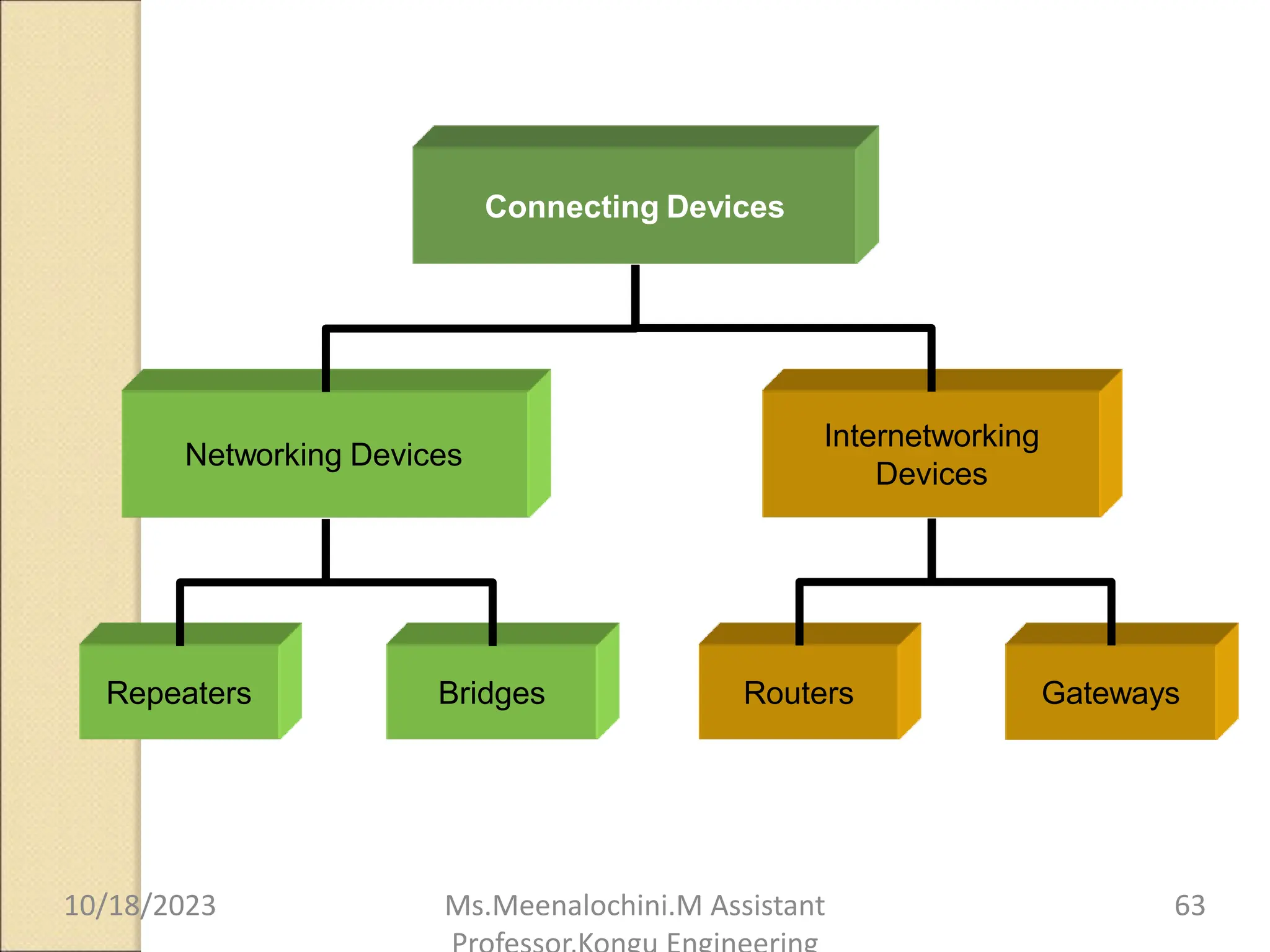
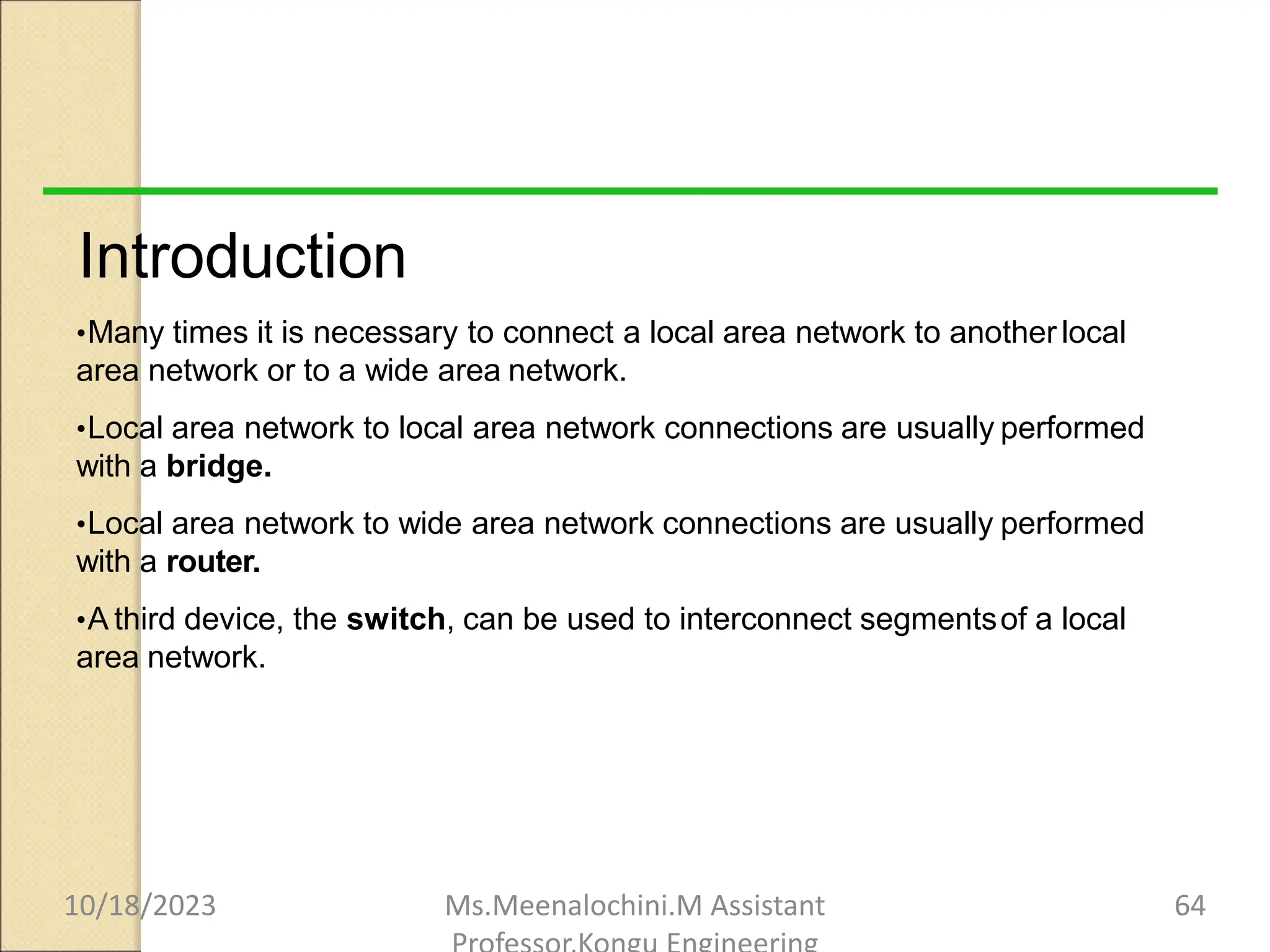
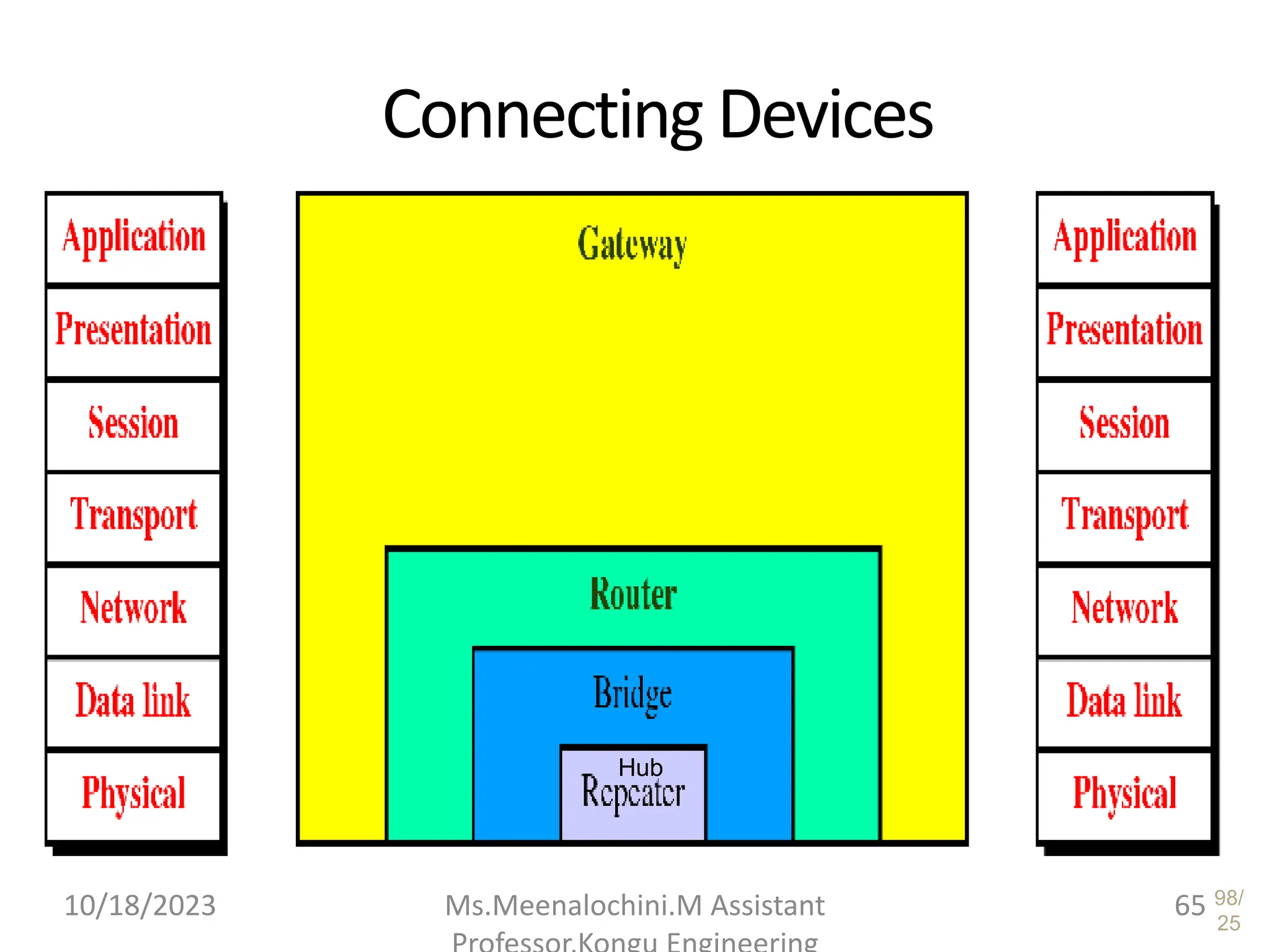
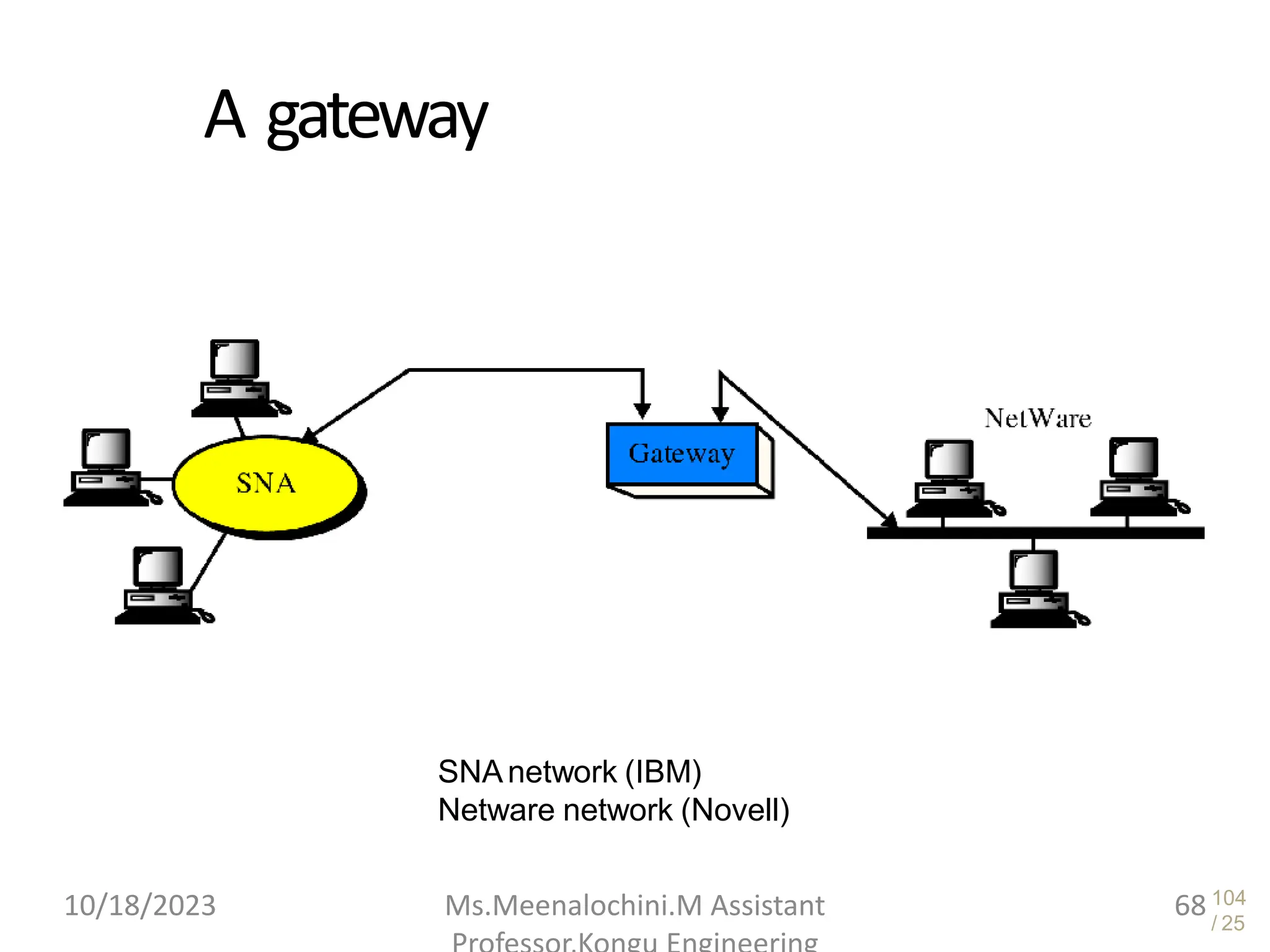
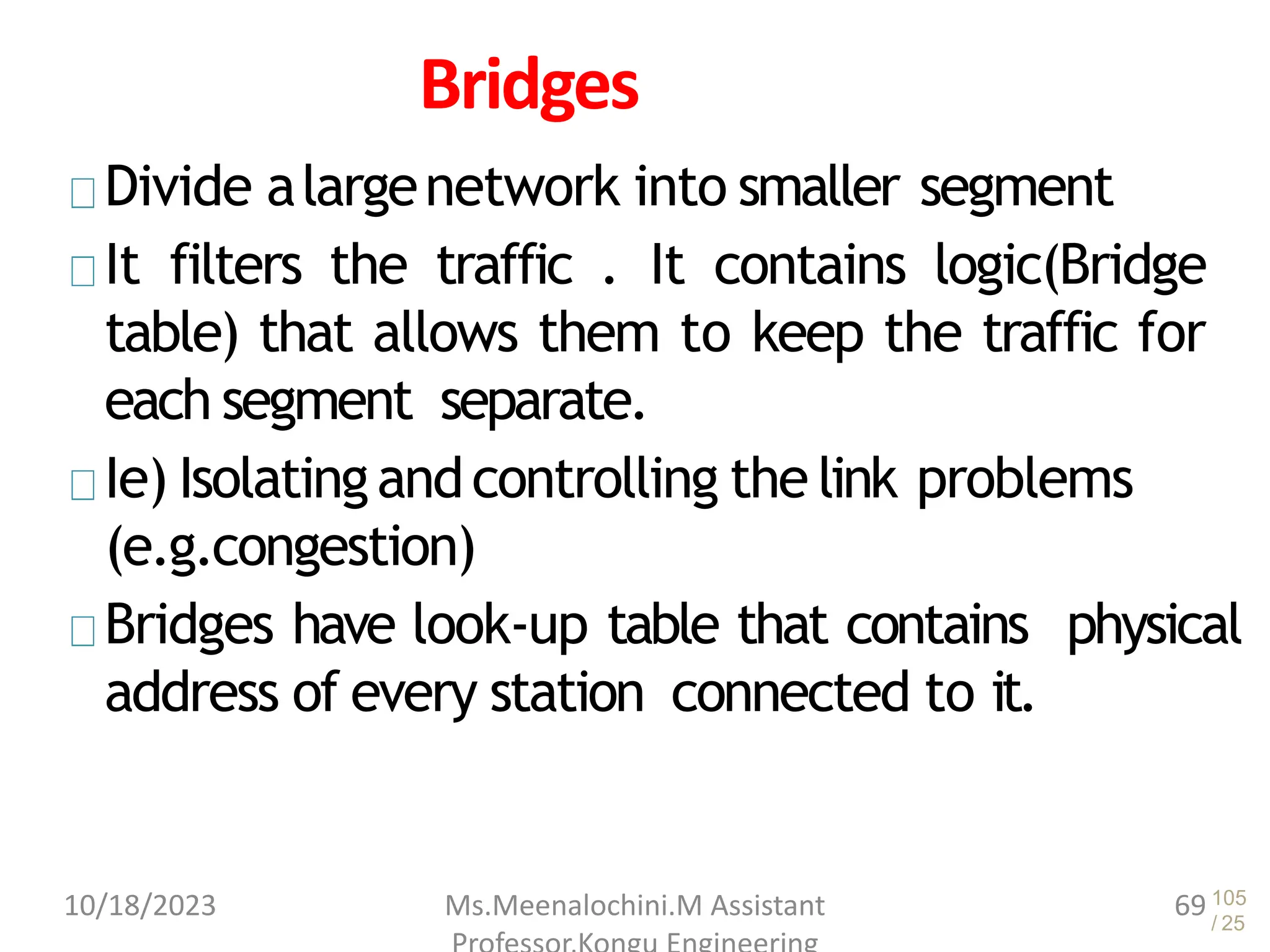
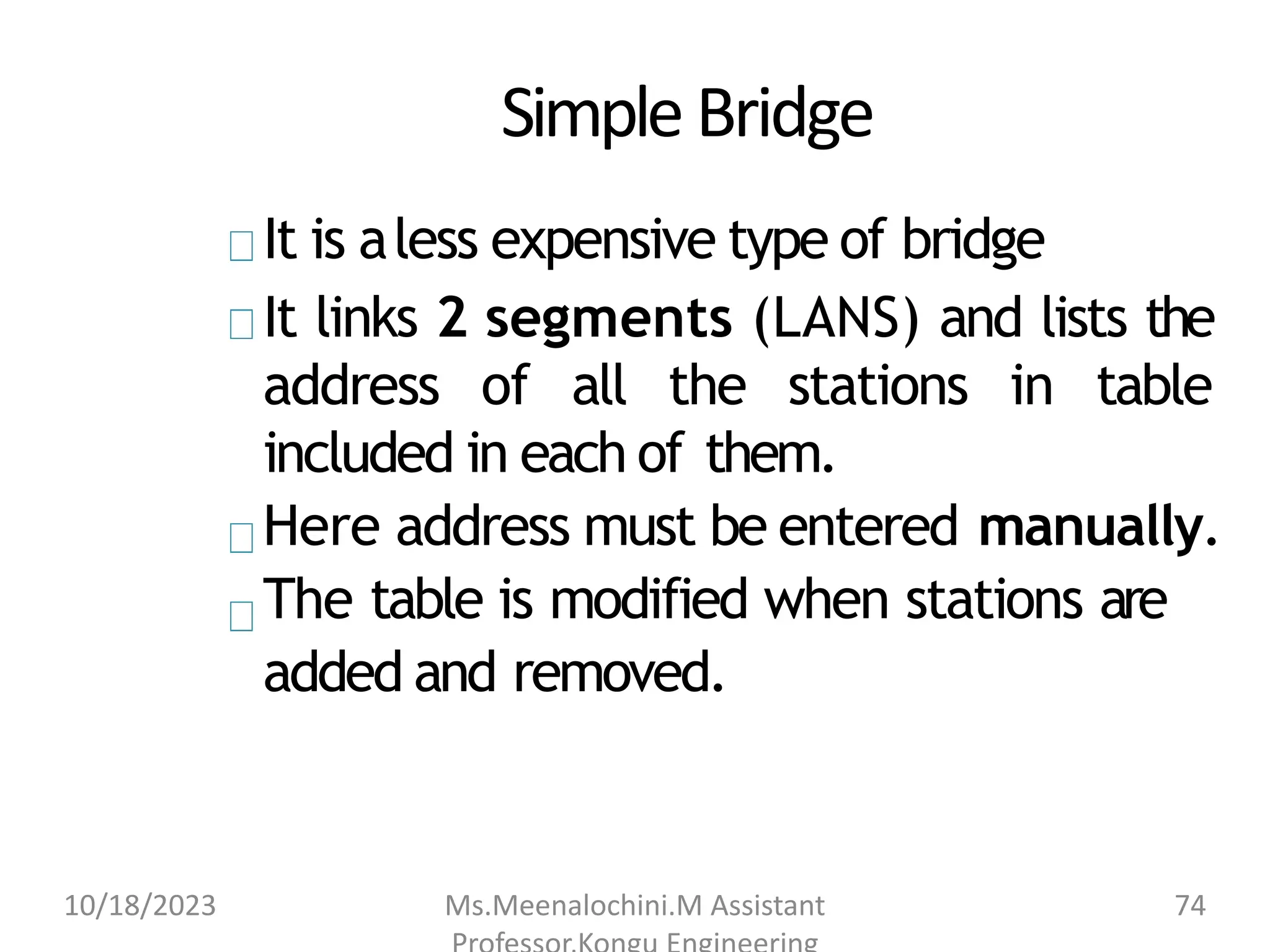
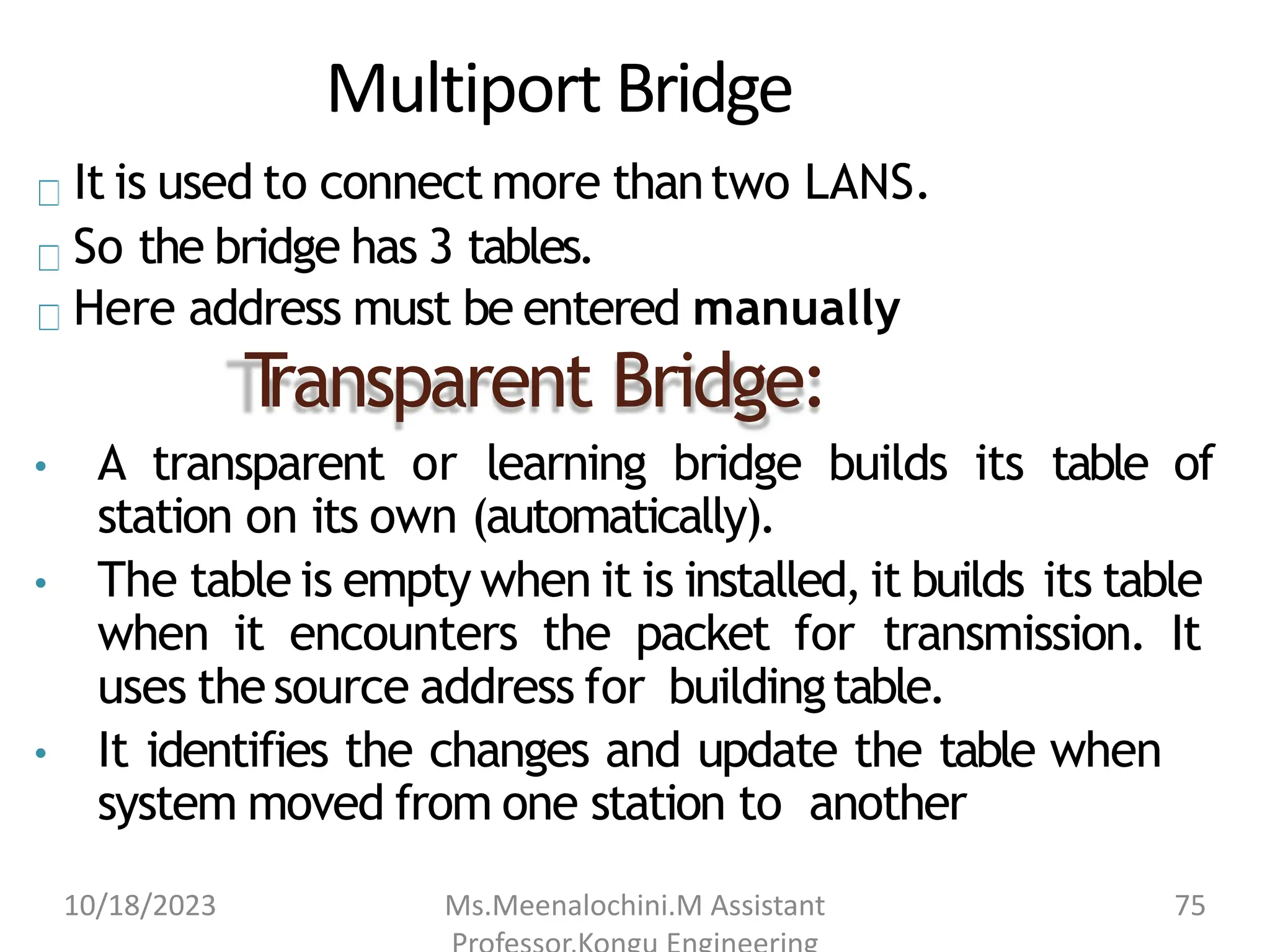
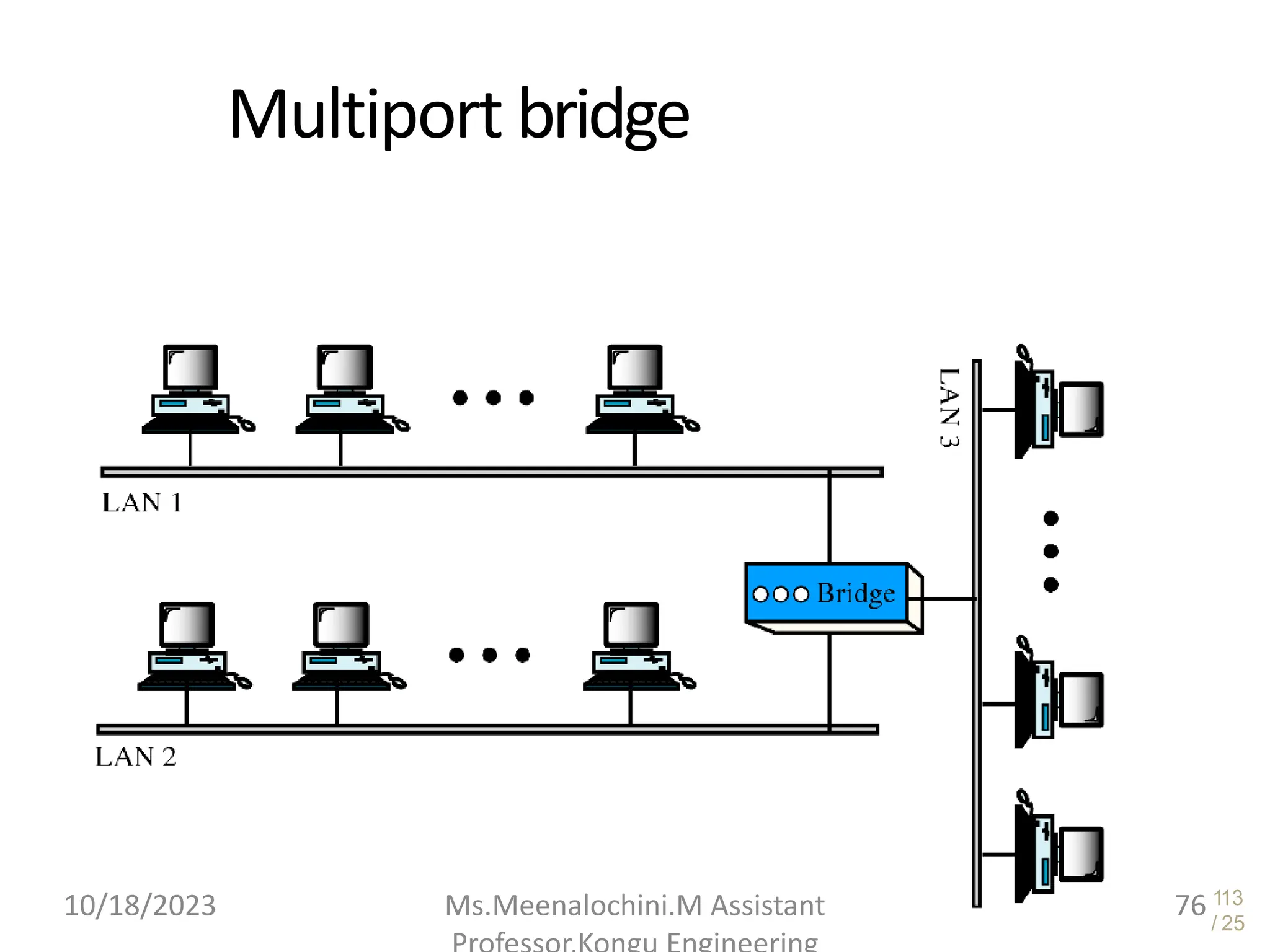
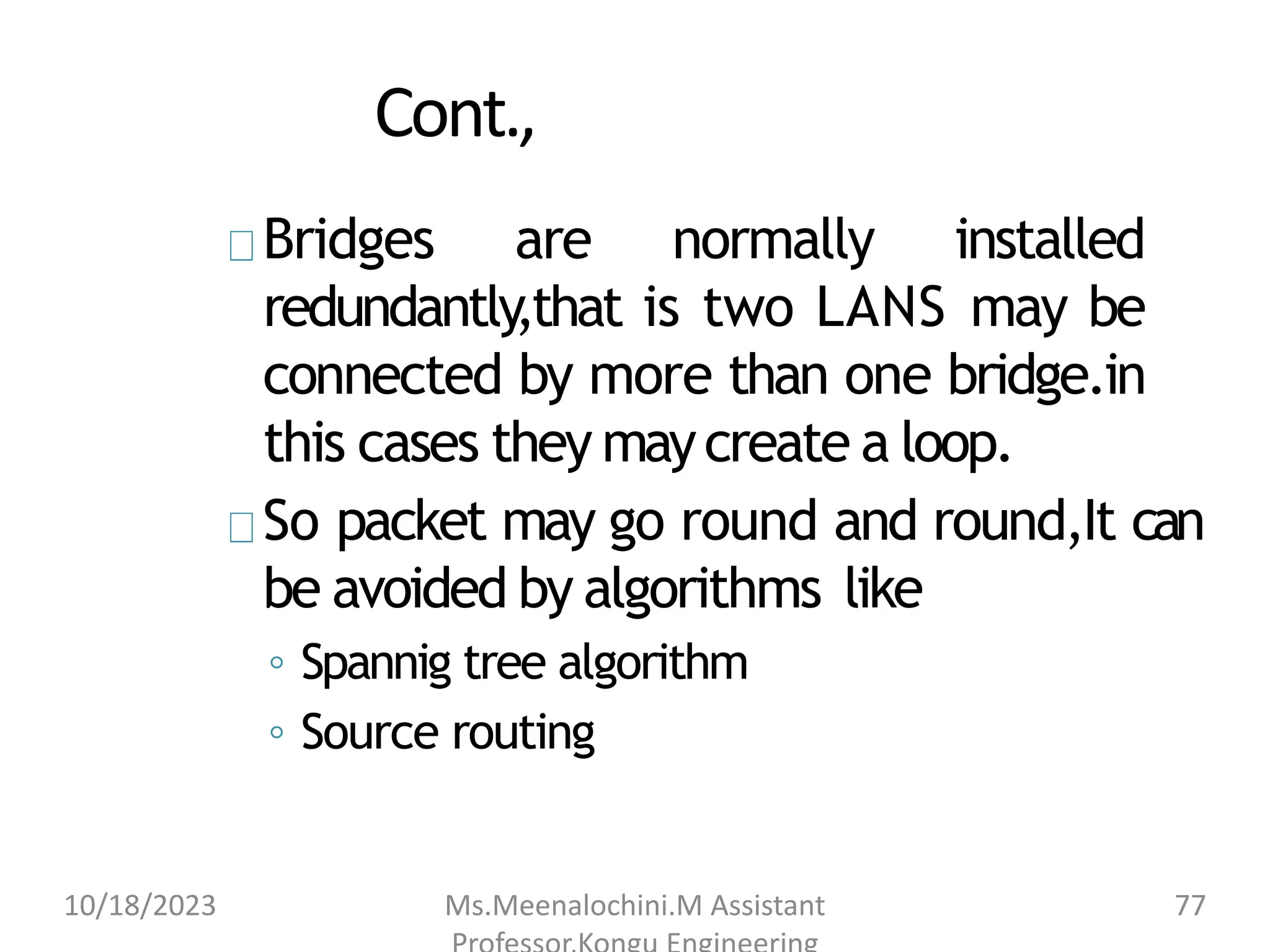
The document explains the functions and importance of the Data Link Layer in data communication, emphasizing flow control and error control mechanisms such as stop-and-wait and sliding window protocols. It also discusses protocols used in Local Area Networks (LANs) including Ethernet, detailing IEEE standards and the evolution of Ethernet technologies. Additionally, it covers the role of networking devices like routers, switches, and gateways in connecting different networks and ensuring efficient communication.




















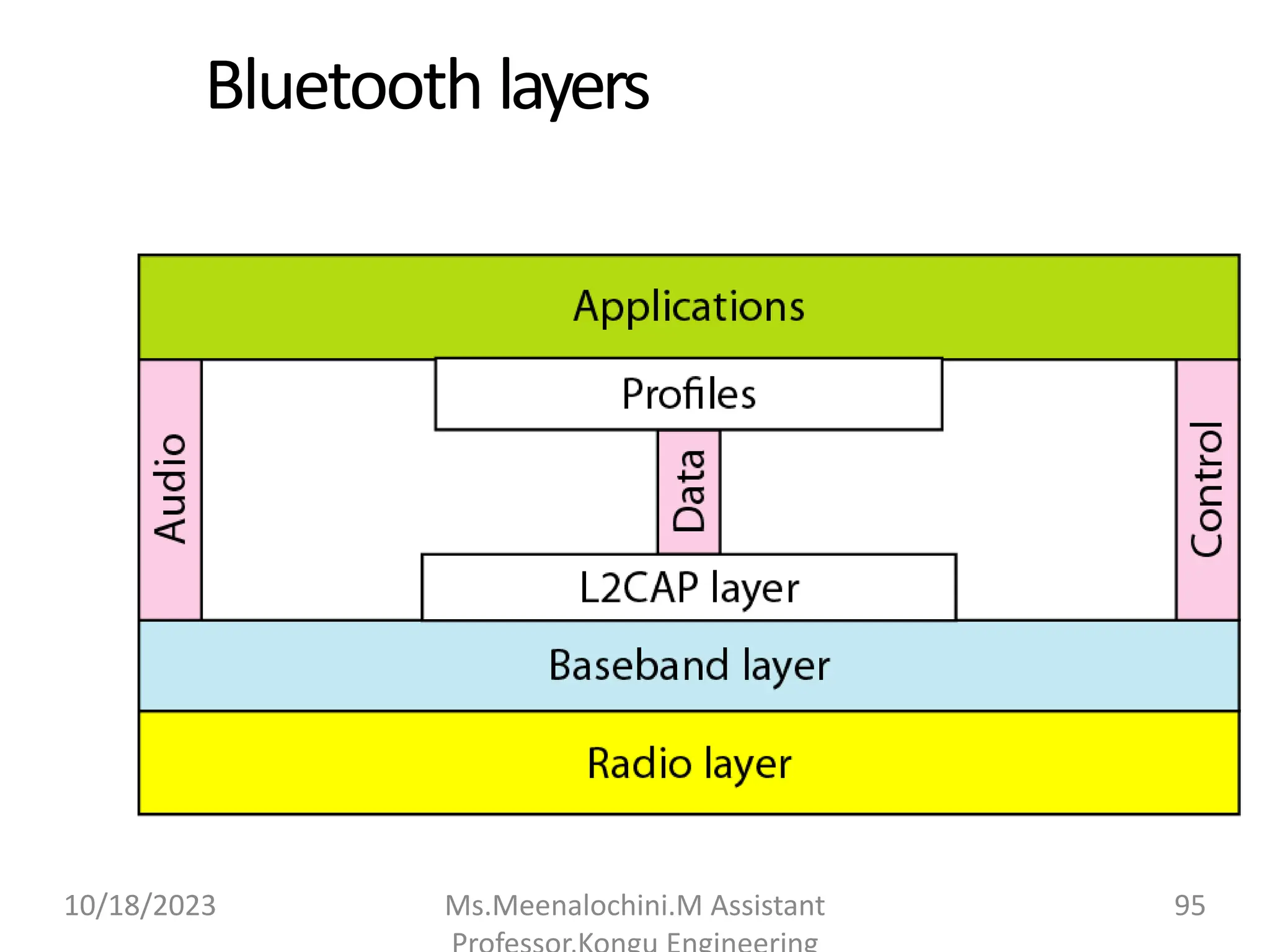
![Bluetooth layers
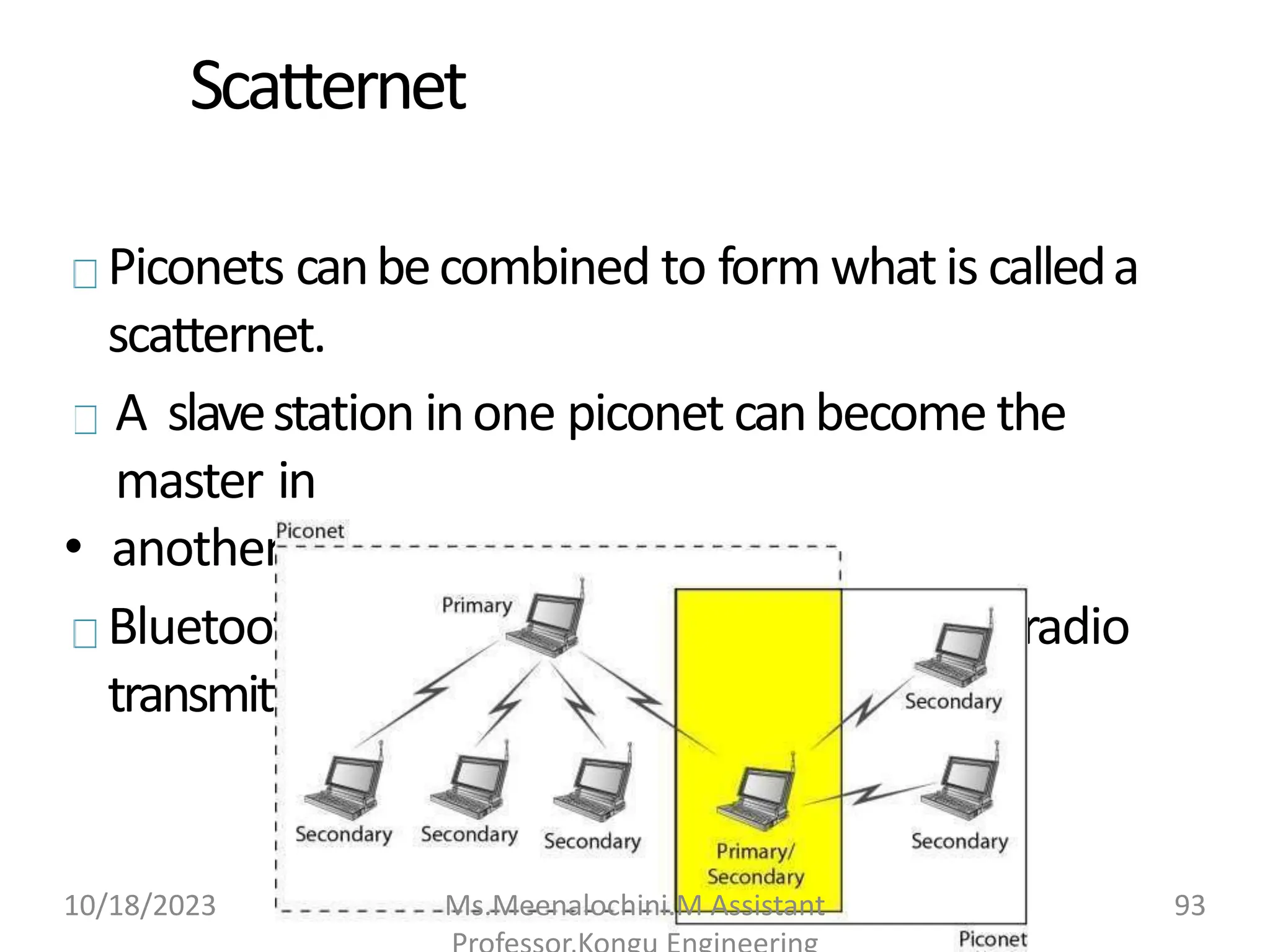
Radio Layer:Roughly equivalent to physicallayerof theInternet model.
Physicallinks canbesynchronous or asynchronous.
◦ Uses Frequency-hopping spread spectrum [Changing frequencyof usage].
Changes itmodulation frequency1600 timesper second.
◦ Uses frequencyshiftkeying(FSK )withGaussian bandwidthfiltering to
transform bits to a signal.
Basebandlayer:Roughly equivalent to MAC sublayerinLANs. Accessis
usingTime Division (Time slots).
◦ Length of timeslot = dwelltime= 625 microsec. So,during one frequency
,a
sender sends aframeto aslave,or aslavesends aframeto themaster
.
Time division duplexingTDMA (TDD-TDMA) is a kind of half-duplex
communicationinwhichtheslaveandreceiver send andreceivedata,but
not atthesametime(half-duplex). However
,thecommunicationfor each
directionuses differenthops,like walkie-talkies.
10/18/2023 Ms.Meenalochini.M Assistant 94](https://image.slidesharecdn.com/unit2-linklayerchecksumethenet-231018050144-0352effe/75/Link-layer-checksum-ethenet-pptx-94-2048.jpg)
![PhysicalLinks
Synchronous connection-oriented (SCO)
◦ Latency is important than integrity
.
◦ T
ransmission using slots.
◦ No retransmission.
Asynchronous connectionless link (ACL)
◦ Integrity is important than latency
.
◦ Does like multiple-slave communication.
◦ Retransmission is done.
L2CAP (Logical Link Control andAdaptationProtocol)
◦ Equivalent to LLC sublayer in LANs.
◦ Used for dataexchange onACL Link.SCO channels do not use L2CAP
.
◦ Frame format has 16-bit length [Size of datacoming from upper layerin bytes],
channel ID, data and control.
◦ Can do Multiplexing, segmentation and Reassembly
, QoS [with no QoS, best-
effort delivery is provided] and Group mangement [Can do like multicast group,
using some kind of logical addresses].
10/18/2023 Ms.Meenalochini.M Assistant 96](https://image.slidesharecdn.com/unit2-linklayerchecksumethenet-231018050144-0352effe/75/Link-layer-checksum-ethenet-pptx-96-2048.jpg)
