This document provides information on shell operators in 3 sections:
1) It discusses arithmetic operators and how to perform arithmetic evaluations in the shell using expr and $((expression)).
2) It covers relational operators for numeric comparisons and conditional statements.
3) It describes string, file test, and boolean operators for evaluating strings and conditions.


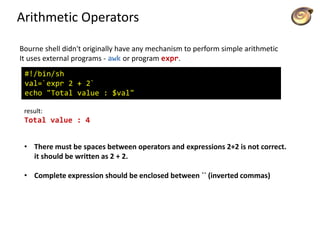
![Arithmetic Operators
Ex. variable a holds 10 and variable b holds 20 then:
+ Addition - Adds values on either side of the operator
`expr $a + $b` will give 30
- Subtraction - Subtracts right hand operand from left hand operand
`expr $a - $b` will give -10
* Multiplication - Multiplies values on either side of the operator
`expr $a * $b` will give 200
/ Division - Divides left hand operand by right hand operand
`expr $b / $a` will give 2
% Modulus - Divides left hand operand by right hand operand and returns remainder
`expr $b % $a` will give 0
= Assignment - Assign right operand in left operand
a=$b would assign value of b into a
== Equality - Compares two numbers, if both are same then returns true.
[ $a == $b ] would return false
!= Not Equality - Compares two numbers, if both are different then returns true.
[ $a != $b ] would return true
All conditional expressions are put inside square braces with one spaces around them.
[ $a == $b ] is correct; [$a==$b] is incorrect.
All the arithmetical calculations are done using long integers.](https://image.slidesharecdn.com/lico10operators-141223143703-conversion-gate02/85/Licao-10-operators-4-320.jpg)
![Arithmetic expressions
#!/bin/sh
a=10
b=20
val=`expr $a + $b`
echo "a + b : $val"
val=`expr $a - $b`
echo "a - b : $val"
val=`expr $a * $b`
echo "a * b : $val"
val=`expr $b / $a`
echo "b / a : $val"
val=`expr $b % $a`
echo "b % a : $val"
if [ $a == $b ]
then
echo "a is equal to b"
fi
if [ $a != $b ]
then
echo "a is not equal to b"
fi
Exemple](https://image.slidesharecdn.com/lico10operators-141223143703-conversion-gate02/85/Licao-10-operators-5-320.jpg)

![Arithmetic expressions
$ let X=10+2*7
$ echo $X
24
$ let Y=X+2*4
$ echo $Y
32
The let statement can be used to do mathematical functions
$ echo “$((123+20))”
143
$ VALORE=$[123+20]
$ echo “$[123*$VALORE]”
17589
arithmetic expression can be evaluated with $[expression] or $((expression))](https://image.slidesharecdn.com/lico10operators-141223143703-conversion-gate02/85/Licao-10-operators-7-320.jpg)
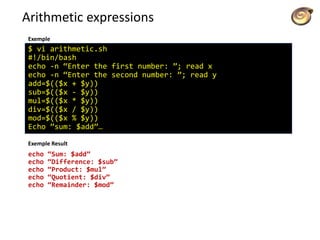
![Conditional Statements
Conditionals let us decide whether to perform an action or not this decision
is taken by evaluating an expression.
basic form:
if [ expression ];
then
statements
elif [ expression ];
then
statements
else
statements
fi
the elif (else if) and else sections are optional
Put spaces after [ and before ], and around the operators and operands.](https://image.slidesharecdn.com/lico10operators-141223143703-conversion-gate02/85/Licao-10-operators-9-320.jpg)
![Expressions
An expression can be:
• String comparison
• Numeric comparison
• File operators
• Logical operators
An expression is represented by $[expression] or $((expression))](https://image.slidesharecdn.com/lico10operators-141223143703-conversion-gate02/85/Licao-10-operators-10-320.jpg)
![Relational Operators
Number Comparisons Expression
Bourne Shell supports relational operators which are specific to numeric values
These operators do not work for string values unless their value is numeric.
For example, following operators would work to check a relation between 10 and 20 as well as in
between "10" and "20" but not in between "ten" and "twenty".
eq Check if value of two operands are equal or not, if yes then condition becomes
true. [ $a -eq $b ] is not true.
-ne If value of two operands are equal or not, if values are not equal then condition
becomes true. [ $a -ne $b ] is true.
-gt If the value of left operand is greater than the value of right operand, if yes then
condition becomes true. [ $a -gt $b ] is not true.
-lt If the value of left operand is less than the value of right operand, if yes then
condition becomes true. [ $a -lt $b ] is true.
-ge If the value of left operand is greater than or equal to the value of right operand, if
yes then condition becomes true. [ $a -ge $b ] is not true.
-le If the value of left operand is less than or equal to the value of right operand, if yes
then condition becomes true. [ $a -le $b ] is true.
Ex. variable a holds 10 and variable b holds 20 then:
All conditional expressions would be put inside square braces with one spaces around them
[ $a <= $b ] is correct , [$a <= $b] is incorrect.](https://image.slidesharecdn.com/lico10operators-141223143703-conversion-gate02/85/Licao-10-operators-11-320.jpg)
![Relational Operators
Number Comparisons Expression
Simple Table
-eq compare if two numbers are equal
-ge compare if one number is greater than or equal to a number
-le compare if one number is less than or equal to a number
-ne compare if two numbers are not equal
-gt compare if one number is greater than another number
-lt compare if one number is less than another number
[ n1 -eq n2 ] (true if n1 same as n2, else false)
[ n1 -ge n2 ] (true if n1greater then or equal to n2, else false)
[ n1 -le n2 ] (true if n1 less then or equal to n2, else false)
[ n1 -ne n2 ] (true if n1 is not same as n2, else false)
[ n1 -gt n2 ] (true if n1 greater then n2, else false)
[ n1 -lt n2 ] (true if n1 less then n2, else false)](https://image.slidesharecdn.com/lico10operators-141223143703-conversion-gate02/85/Licao-10-operators-12-320.jpg)
![Relational Operators
Number Comparisons Expression
#!/bin/sh
a=10
b=20
if [ $a -eq $b ]
then
echo "$a -eq $b : a is equal to b"
else
echo "$a -eq $b: a is not equal to b"
fi
if [ $a -ne $b ]
then
echo "$a -ne $b: a is not equal to b"
else
echo "$a -ne $b : a is equal to b"
fi
if [ $a -gt $b ]
then
echo "$a -gt $b: a is greater than b"
else
echo "$a -gt $b: a is not greater than b"
fi
if [ $a -lt $b ]
then
echo "$a -lt $b: a is less than b"
else
echo "$a -lt $b: a is not less than b"
fi
if [ $a -ge $b ]
then
echo "$a -ge $b: a is greater or equal to b"
else
echo "$a -ge $b: a is not greater or equal
to b"
fi
if [ $a -le $b ]
then
echo "$a -le $b: a is less or equal to b"
else
echo "$a -le $b: a is not less or equal to b"
fi
Exemple](https://image.slidesharecdn.com/lico10operators-141223143703-conversion-gate02/85/Licao-10-operators-13-320.jpg)

![Relational Operators
Number Comparisons Expression
Exemple
$ vi number.sh
#!/bin/bash
echo -n “Enter a number 1 < x < 10: "
read num
if [ “$num” -lt 10 ]; then
if [ “$num” -gt 1 ]; then
echo “$num*$num=$(($num*$num))”
else
echo “Wrong insertion !”
fi
else
echo “Wrong insertion again !”
fi](https://image.slidesharecdn.com/lico10operators-141223143703-conversion-gate02/85/Licao-10-operators-15-320.jpg)
![String Operators
String Comparisons Expressions
= Checks if value of two operands are equal or not, if yes then condition becomes true.
[ $a = $b ] is not true.
!= Checks if the value of two operands are equal or not, if values are not equal then
condition becomes true.
[ $a != $b ] is true.
-z Checks if the given string operand size is zero. If it is zero length then it returns true.
[ -z $a ] is not true.
-n Checks if the given string operand size is non-zero. If it is non-zero length then it
returns true.
[ -z $a ] is not false.
Str Check if str is not the empty string. If it is empty then it returns false.
[ $a ] is not false.
Ex. variable a holds “abc” and variable b holds “efg” then:](https://image.slidesharecdn.com/lico10operators-141223143703-conversion-gate02/85/Licao-10-operators-16-320.jpg)
![String Operators
String Comparisons Expressions
Simple Table
= compare if two strings are equal
!= compare if two strings are not equal
-n evaluate if string length is greater than zero
-z evaluate if string length is equal to zero
[ s1 = s2 ] (true if s1 same as s2, else false)
[ s1 != s2 ] (true if s1 not same as s2, else false)
[ s1 ] (true if s1 is not empty, else false)
[ -n s1 ] (true if s1 has a length greater then 0, else false)
[ -z s2 ] (true if s2 has a length of 0, otherwise false)](https://image.slidesharecdn.com/lico10operators-141223143703-conversion-gate02/85/Licao-10-operators-17-320.jpg)
![String Operators
String Comparisons Expressions
#!/bin/sh
a="abc"
b="efg"
if [ $a = $b ]
then
echo "$a = $b : a is equal to b"
else
echo "$a = $b: a is not equal to b"
fi
if [ $a != $b ]
then
echo "$a != $b : a is not equal to b"
else
echo "$a != $b: a is equal to b"
fi
Exemple
if [ -z $a ]
then
echo "-z $a : string length is zero"
else
echo "-z $a : string length is not zero"
fi
if [ -n $a ]
then
echo "-n $a : string length is not zero"
else
echo "-n $a : string length is zero"
fi
if [ $a ]
then
echo "$a : string is not empty"
else
echo "$a : string is empty"
fi](https://image.slidesharecdn.com/lico10operators-141223143703-conversion-gate02/85/Licao-10-operators-18-320.jpg)
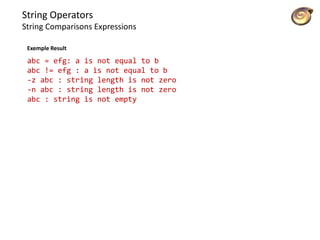
![String Operators
String Comparisons Expressions
$ vi user.sh
#!/bin/bash
echo -n “Enter your login name: "
read name
if [ “$name” = “$USER” ];
then
echo “Hello, $name. How are you today ?”
else
echo “You are not $USER, so who are you ?”
fi
Exemple](https://image.slidesharecdn.com/lico10operators-141223143703-conversion-gate02/85/Licao-10-operators-20-320.jpg)
![Boolean Operators
Logical operators Expressions
! This is logical negation.
This inverts a true condition into false and vice versa.
[ ! false ] is true.
-o This is logical OR.
If one of the operands is true then condition would be true.
[ $a -lt 20 -o $b -gt 100 ] is true.
-a This is logical AND.
If both the operands are true then condition would be true otherwise it would be false.
[ $a -lt 20 -a $b -gt 100 ] is false.
Ex. variable a holds 10 and variable b holds 20 then:](https://image.slidesharecdn.com/lico10operators-141223143703-conversion-gate02/85/Licao-10-operators-21-320.jpg)
![Boolean Operators
Logical operators Expressions
Simple Table
! negate (NOT) a logical expression
-a logically AND two logical expressions
-o logically OR two logical expressions
#!/bin/bash
echo -n “Enter a number 1 < x < 10:”
read num
if [ “$num” -gt 1 –a “$num” -lt 10 ];
then
echo “$num*$num=$(($num*$num))”
else
echo “Wrong insertion !”
fi
Exemple](https://image.slidesharecdn.com/lico10operators-141223143703-conversion-gate02/85/Licao-10-operators-22-320.jpg)
![Boolean Operators
Logical operators Expressions
a=10
b=20
if [ $a != $b ]
then
echo "$a != $b : a is not equal to b"
else
echo "$a != $b: a is equal to b"
fi
if [ $a -lt 100 -a $b -gt 15 ]
then
echo "$a -lt 100 -a $b -gt 15 : returns true"
else
echo "$a -lt 100 -a $b -gt 15 : returns false"
fi
if [ $a -lt 100 -o $b -gt 100 ]
then
echo "$a -lt 100 -o $b -gt 100 : returns true"
else
echo "$a -lt 100 -o $b -gt 100 : returns false"
fi
if [ $a -lt 5 -o $b -gt 100 ]
then
echo "$a -lt 100 -o $b -gt 100 : returns true"
else
echo "$a -lt 100 -o $b -gt 100 : returns false"
fi
Exemple](https://image.slidesharecdn.com/lico10operators-141223143703-conversion-gate02/85/Licao-10-operators-23-320.jpg)

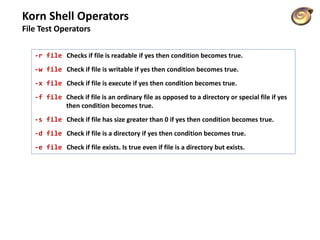
![File Test Operators
Boolean Check condition
-b file Checks if file is a block special file if yes then condition becomes true. [ -b $file ] is false
-c file Checks if file is a character special file if yes then condition becomes true. [ -b $file ] is false
-d file Check if file is a directory if yes then condition becomes true. [ -d $file ] is not true
-f file Check if file is an ordinary file as opposed to a directory or special file if yes then condition becomes true
[ -f $file ] is true
-g file Checks if file has its set group ID (SGID) bit set if yes then condition becomes true. [ -g $file ] is false
-k file Checks if file has its sticky bit set if yes then condition becomes true. [ -k $file ] is false
-p file Checks if file is a named pipe if yes then condition becomes true. [ -p $file ] is false
-t file Checks if file descriptor is open and associated with a terminal if yes then condition becomes true
[ -t $file ] is false
-u file Checks if file has its set user id (SUID) bit set if yes then condition becomes true. [ -u $file ] is false
-r file Checks if file is readable if yes then condition becomes true. [ -r $file ] is true
-w file Check if file is writable if yes then condition becomes true. [ -w $file ] is true
-x file Check if file is execute if yes then condition becomes true. [ -x $file ] is true
-s file Check if file has size greater than 0 if yes then condition becomes true. [ -s $file ] is true
-e file Check if file exists. Is true even if file is a directory but exists. [ -e $file ] is true
Ex. file holds an existing file name "test" whose size is 100 bytes and has read, write and execute permission on](https://image.slidesharecdn.com/lico10operators-141223143703-conversion-gate02/85/Licao-10-operators-25-320.jpg)
![File Test Operators
Boolean Check condition
Simple Table
-d check if path given is a directory
-f check if path given is a file
-e check if file name exists
-r check if read permission is set for file or directory
-s check if a file has a length greater than 0
-w check if write permission is set for a file or directory
-x check if execute permission is set for a file or directory
[ -d scripts ] (true if scripts is a directory, otherwise false)
[ -f scripts ] (true if scripts is a file, otherwise false)
[ -e scripts ] (true if scripts exists, otherwise false)
[ -s scripts ] (true if scripts length is greater then 0, else false)
[ -r scripts ] (true if scripts has the read permission, else false)
[ -w scripts ] (true if scripts has the write permission, else false)
[ -x scripts ] (true if scripts has the execute permission, else false)](https://image.slidesharecdn.com/lico10operators-141223143703-conversion-gate02/85/Licao-10-operators-26-320.jpg)
![File Test Operators
Boolean Check condition
#!/bin/bash
if [ -f /etc/fstab ];
then
cp /etc/fstab .
echo “Done.”
else
echo “This file does not exist.”
exit 1
fi
Exemple](https://image.slidesharecdn.com/lico10operators-141223143703-conversion-gate02/85/Licao-10-operators-27-320.jpg)

![File Test Operators
Boolean Check condition
Exemple
Assume a variable file holds an existing file name "/root/scripts/user.sh" whose size is 100
bytes and has read, write and execute permission on:
#!/bin/sh
file="/root/scripts/user.sh"
if [ -r $file ]
then
echo "File has read access"
else
echo "File does not have read access"
fi
if [ -w $file ]
then
echo "File has write permission"
else
echo "File does not have write permission"
fi
if [ -x $file ]
then
echo "File has execute permission"
else
echo "File does not have execute permission"
fi
if [ -f $file ]
then
echo "File is an ordinary file"
else
echo "This is special file"
fi
if [ -d $file ]
then
echo "File is a directory"
else
echo "This is not a directory"
fi
if [ -s $file ]
then
echo "File size is zero"
else
echo "File size is not zero"
fi
if [ -e $file ]
then
echo "File exists"
else
echo "File does not exist"
fi](https://image.slidesharecdn.com/lico10operators-141223143703-conversion-gate02/85/Licao-10-operators-29-320.jpg)

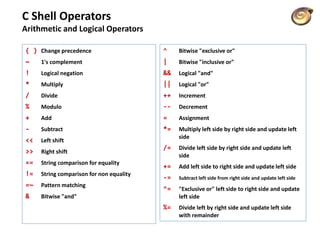


![Korn/C Shell Logical Operators
Exemple
#!/bin/bash
echo -n "Enter a number 1 < x < 10: "
read num
if [ “$number” -gt 1 ] && [ “$number” -lt 10 ];
then
echo “$num*$num=$(($num*$num))”
else
echo “Wrong insertion !”
fi](https://image.slidesharecdn.com/lico10operators-141223143703-conversion-gate02/85/Licao-10-operators-35-320.jpg)
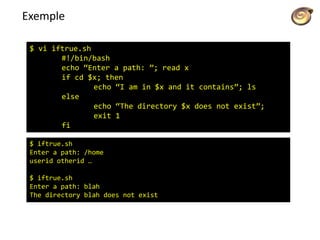

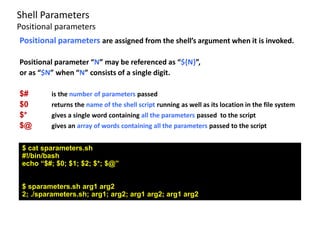
![Shell Parameters
Positional parameters
$ vi trash.sh
#!/bin/bash
if [ $# -eq 1 ];
then
if [ ! –d “$HOME/trash” ];
then
mkdir “$HOME/trash”
fi
mv $1 “$HOME/trash”
else
echo “Use: $0 filename”
exit 1
fi](https://image.slidesharecdn.com/lico10operators-141223143703-conversion-gate02/85/Licao-10-operators-39-320.jpg)