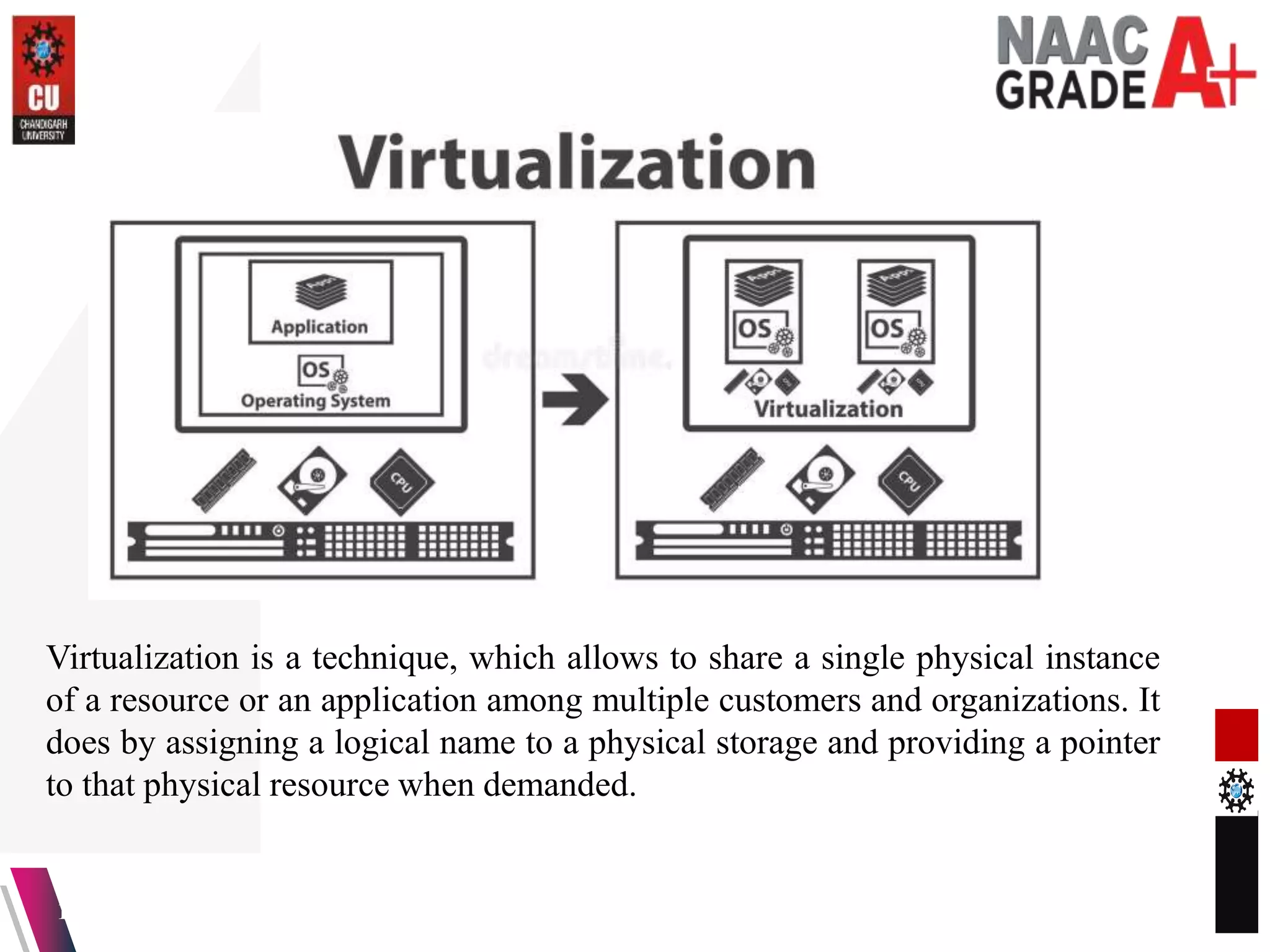
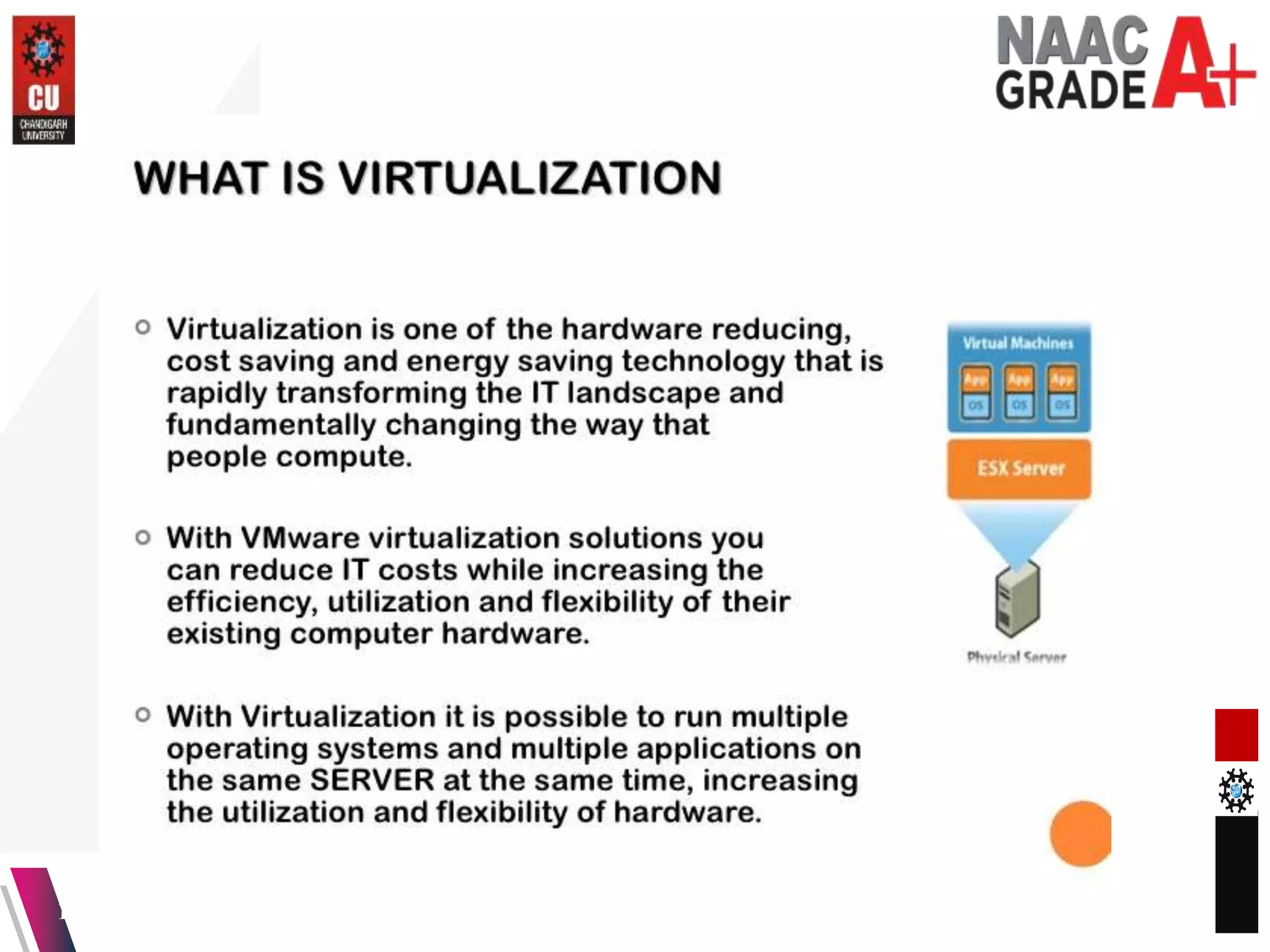
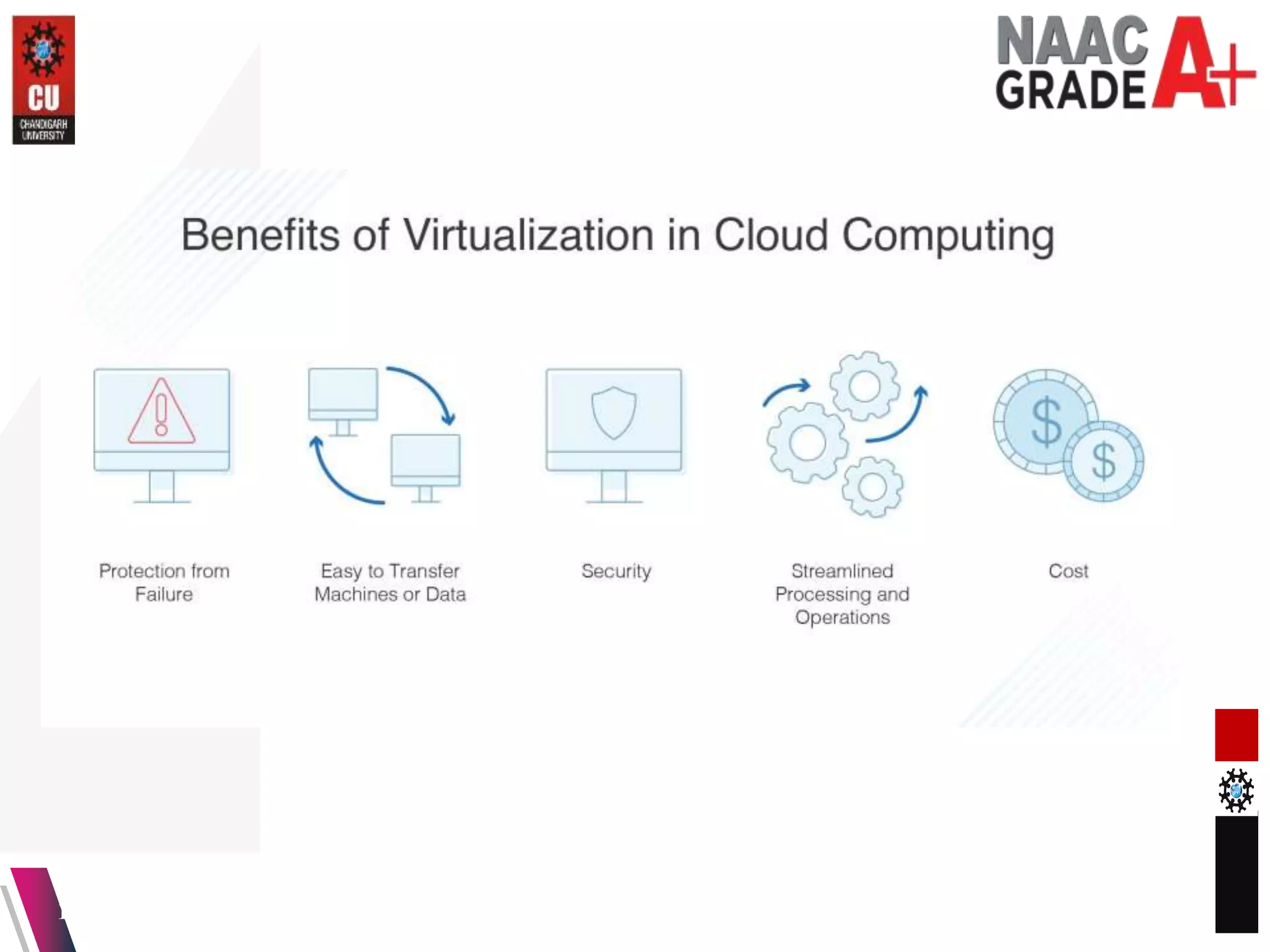
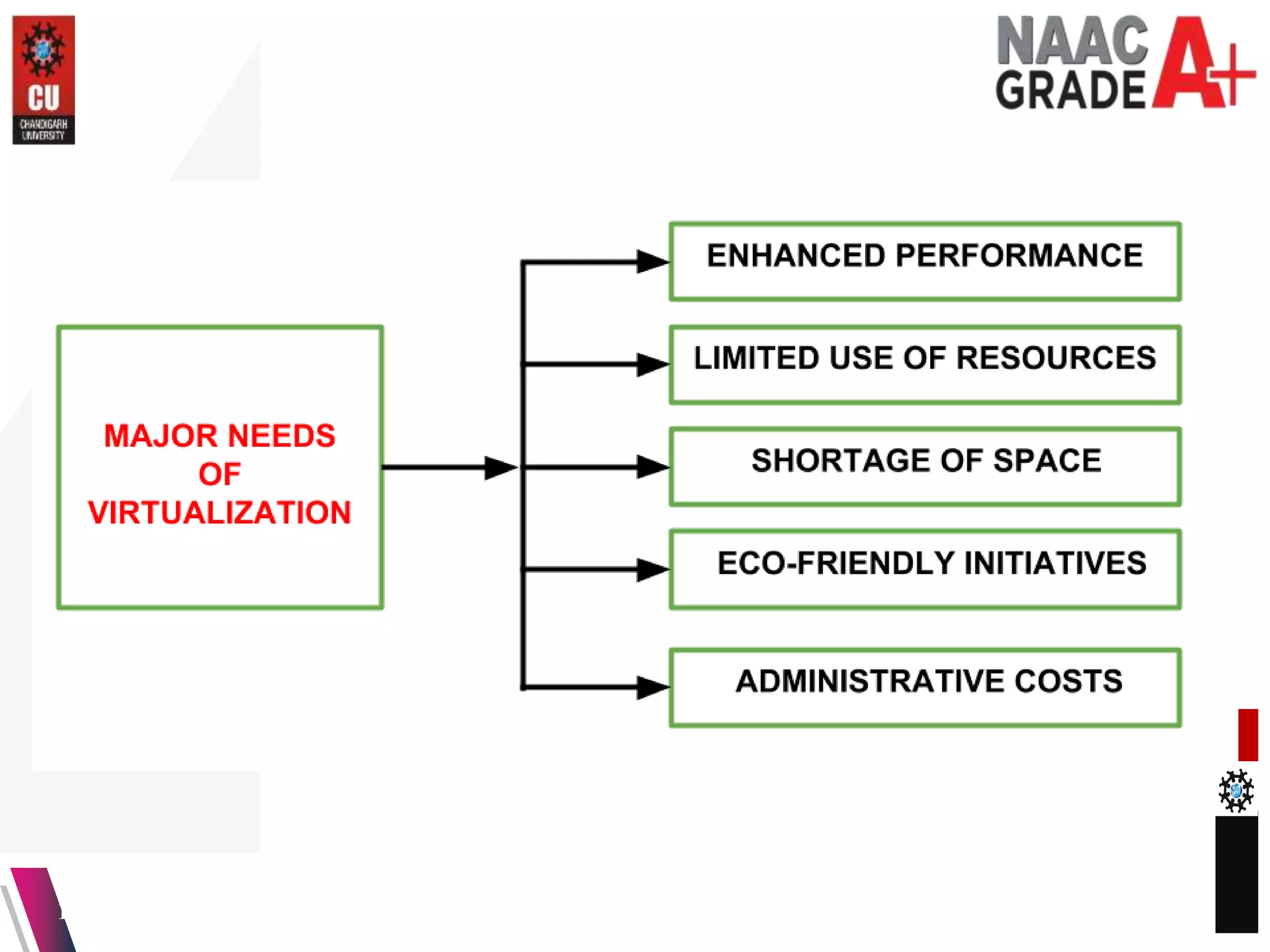
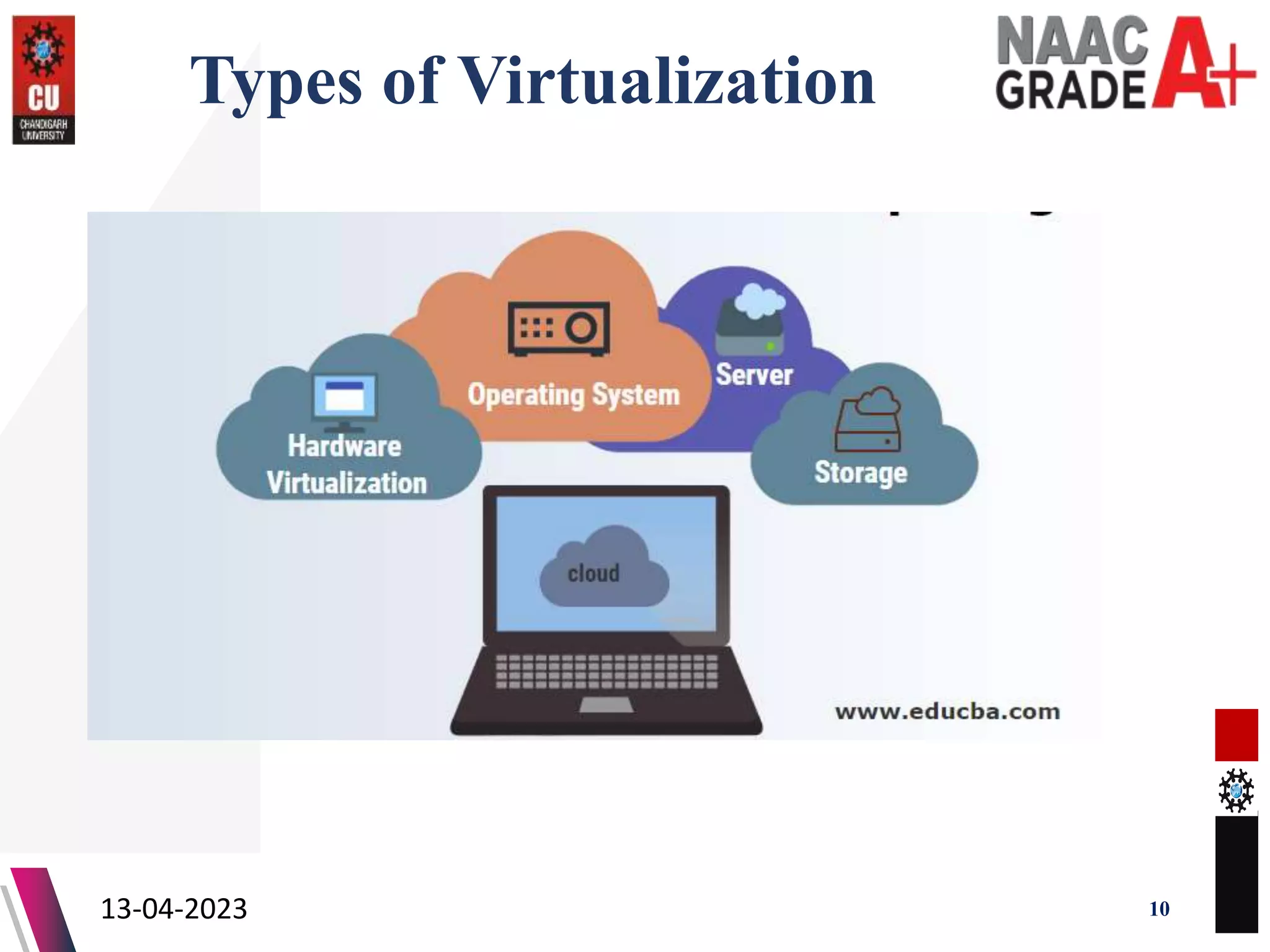
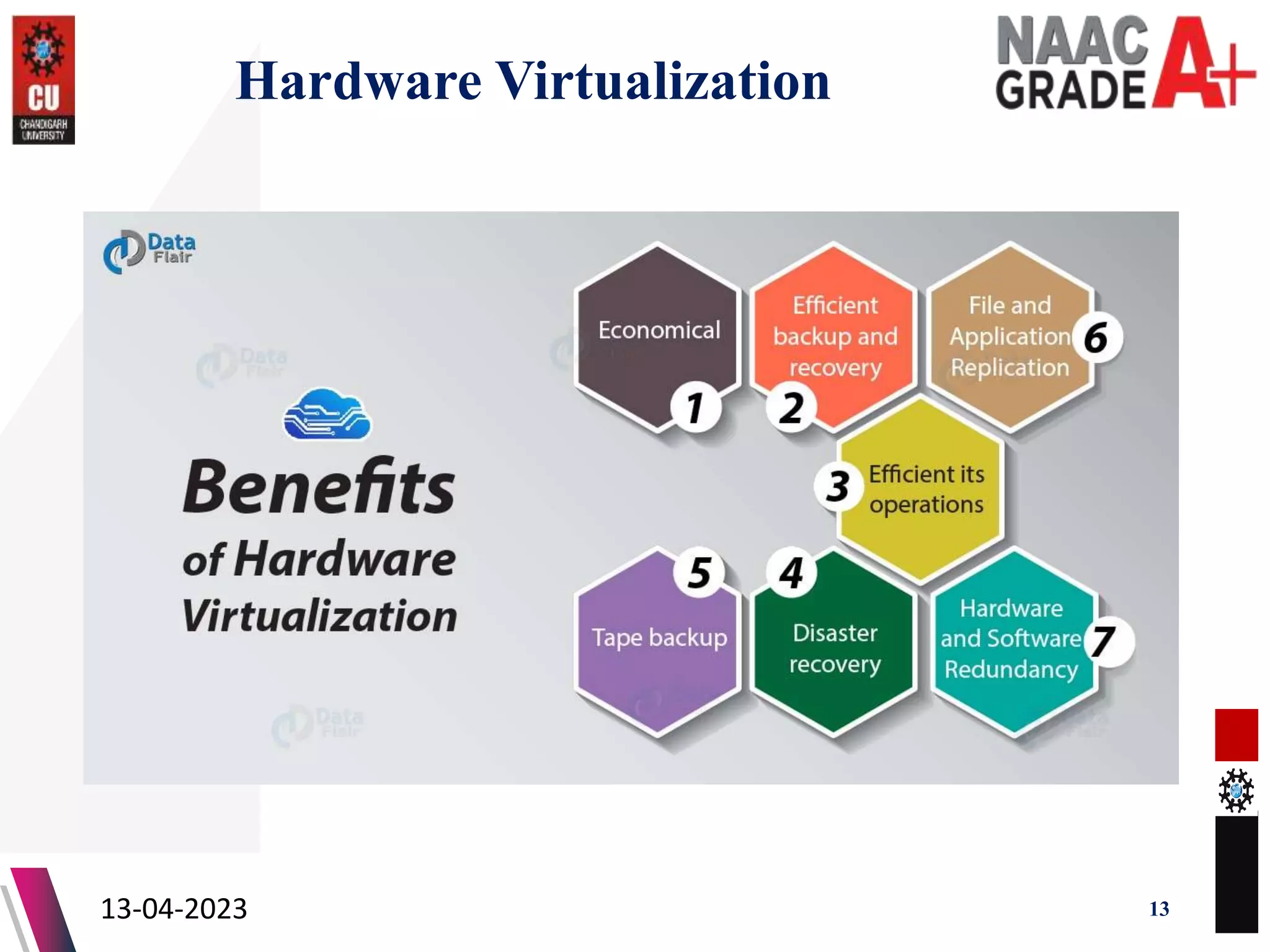
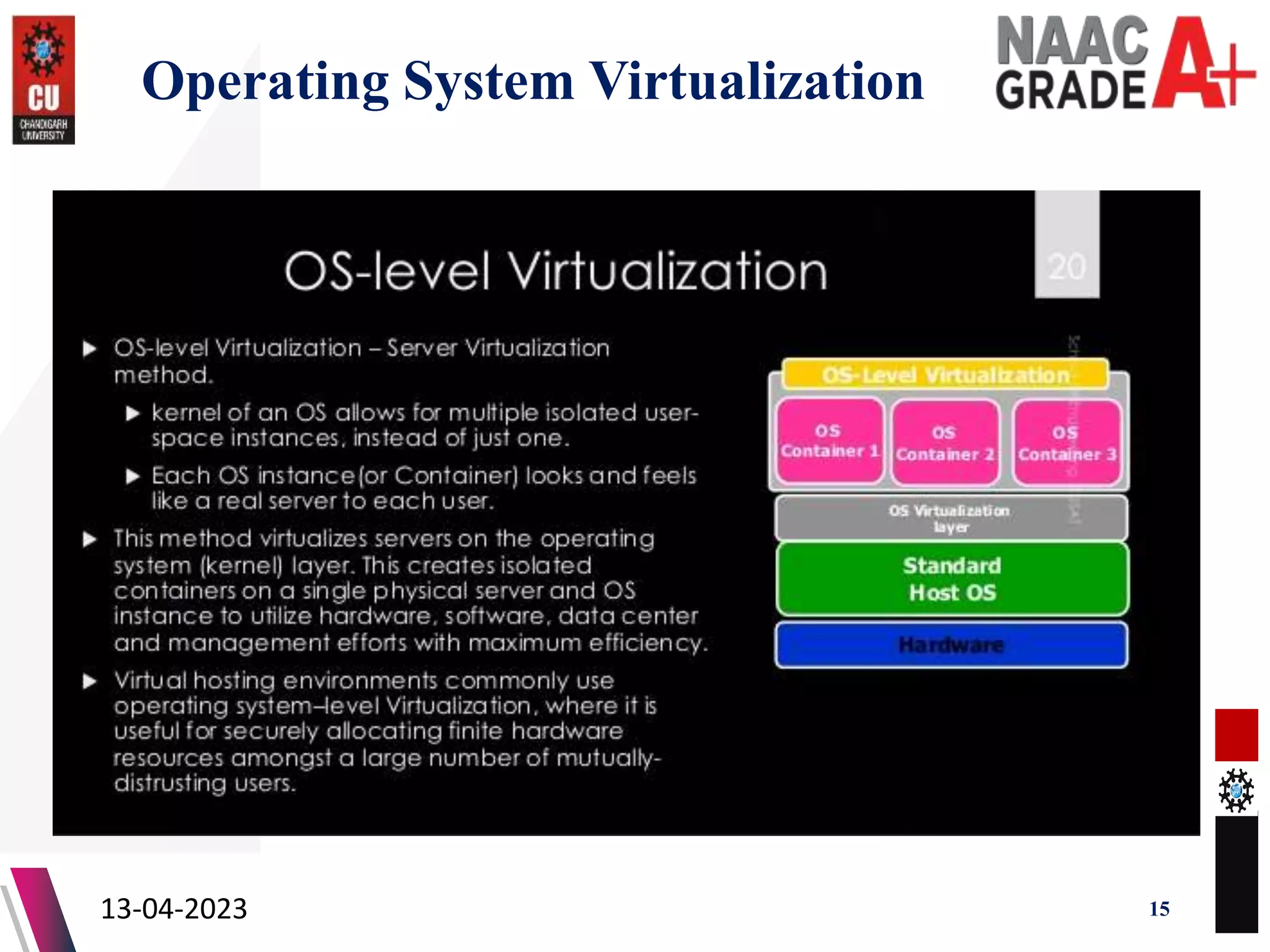
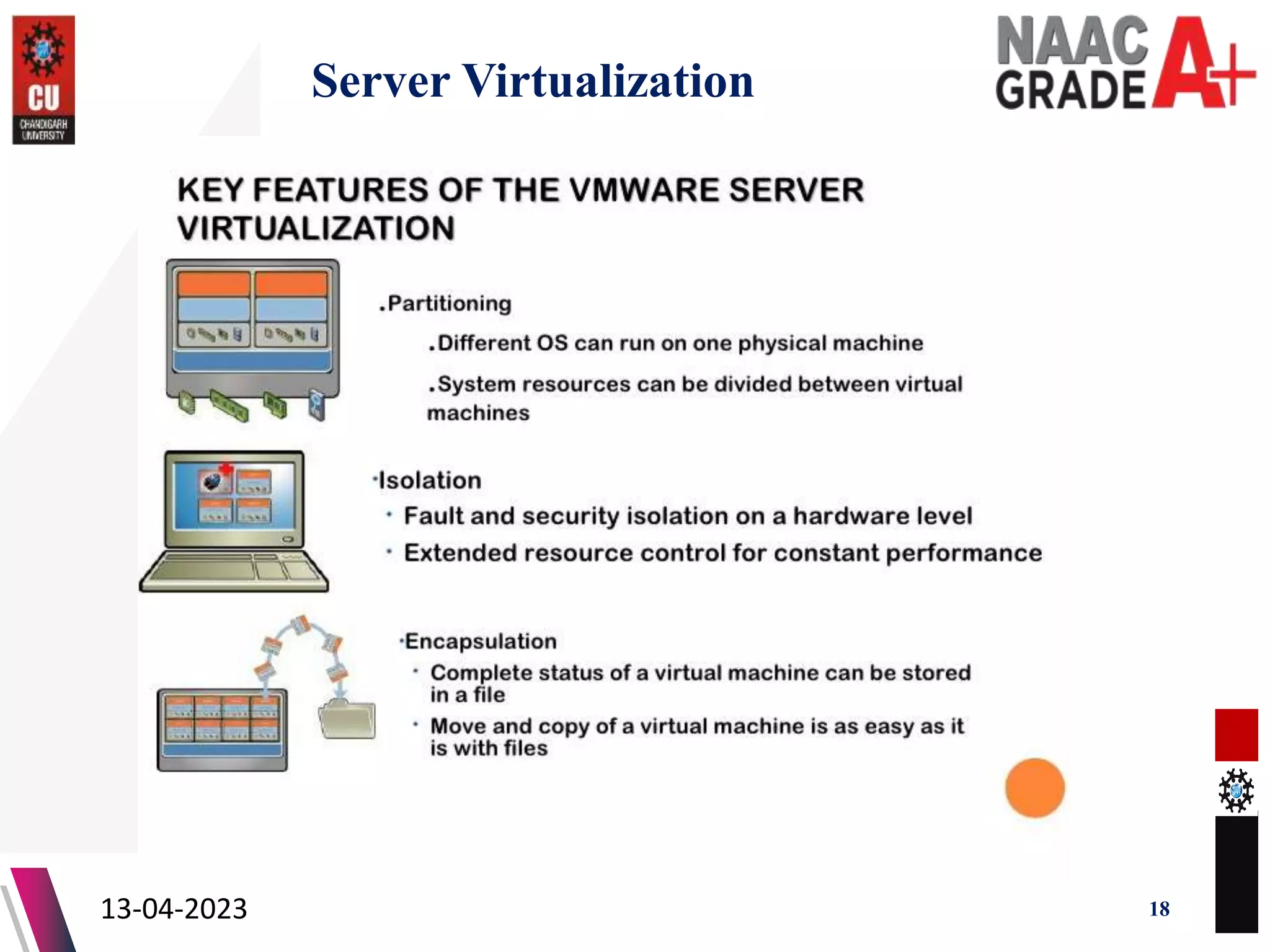
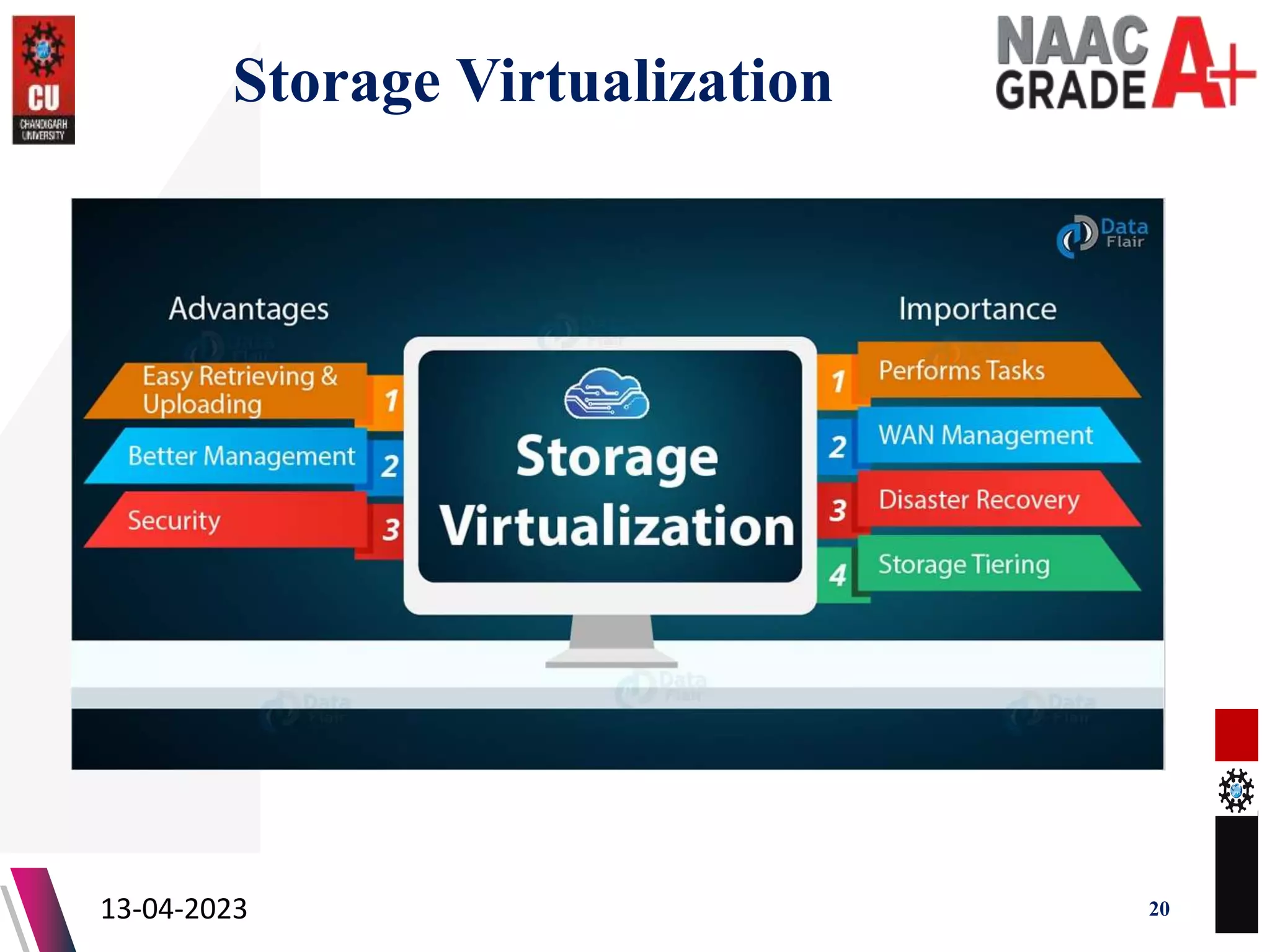
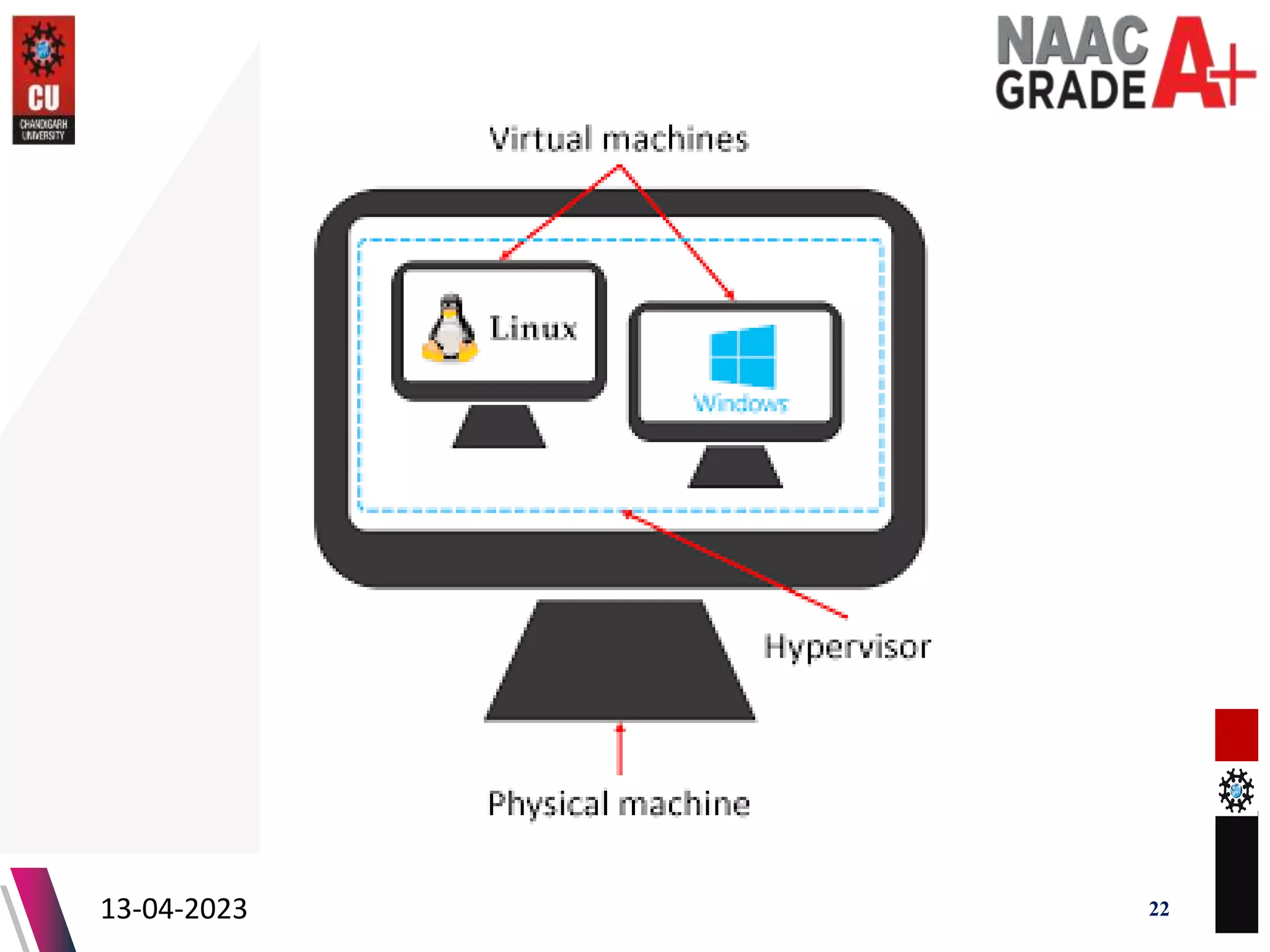
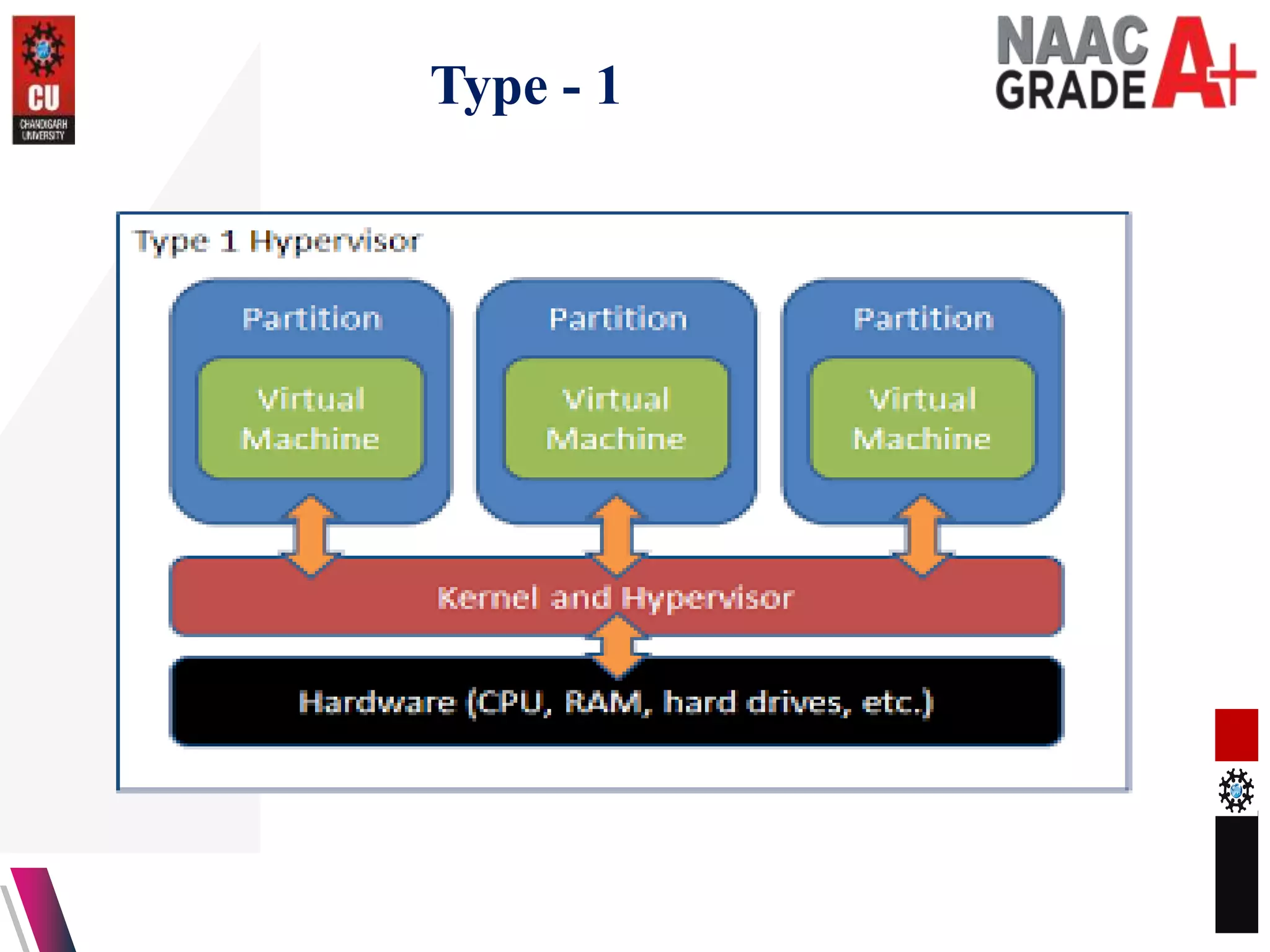
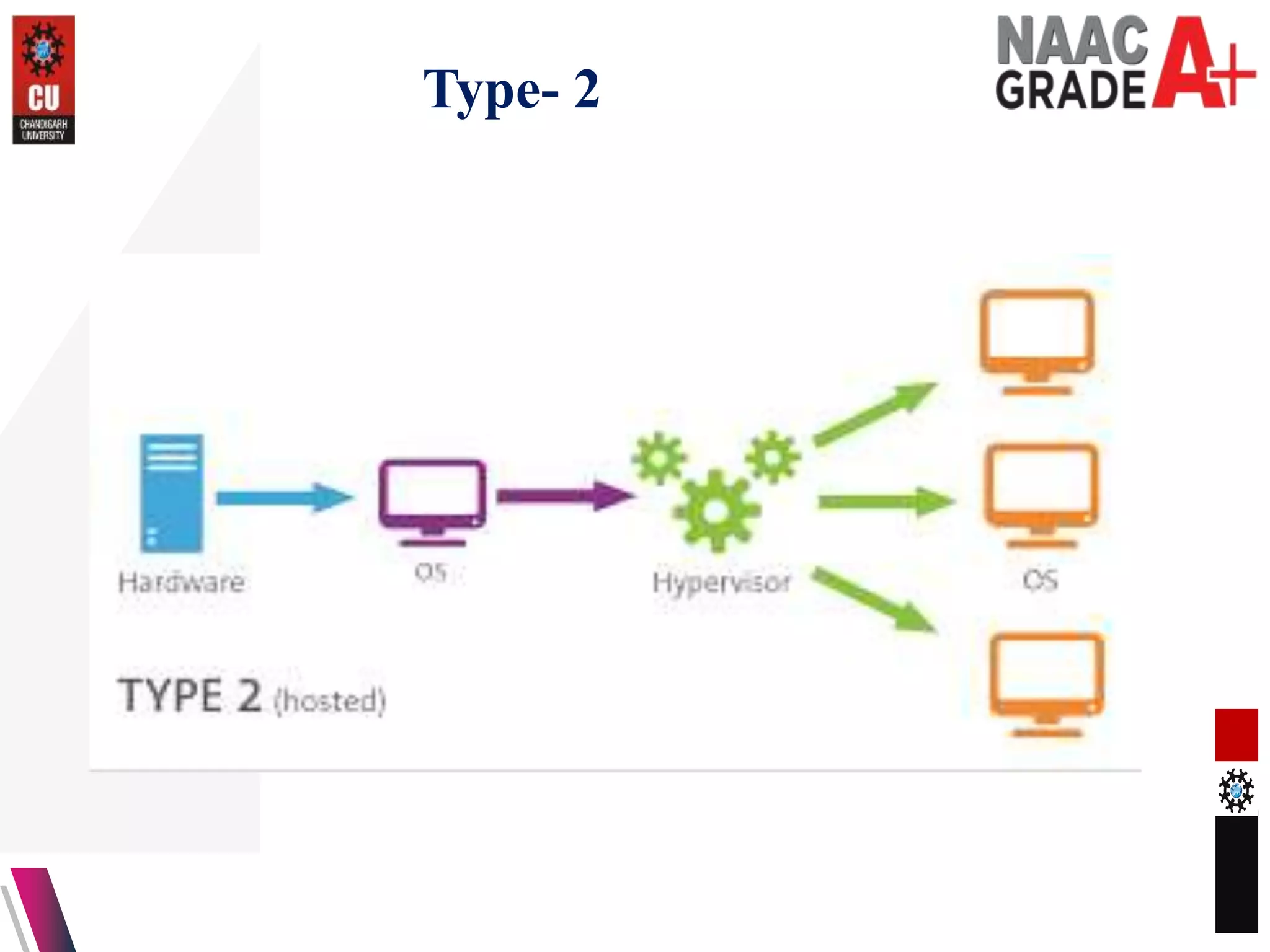
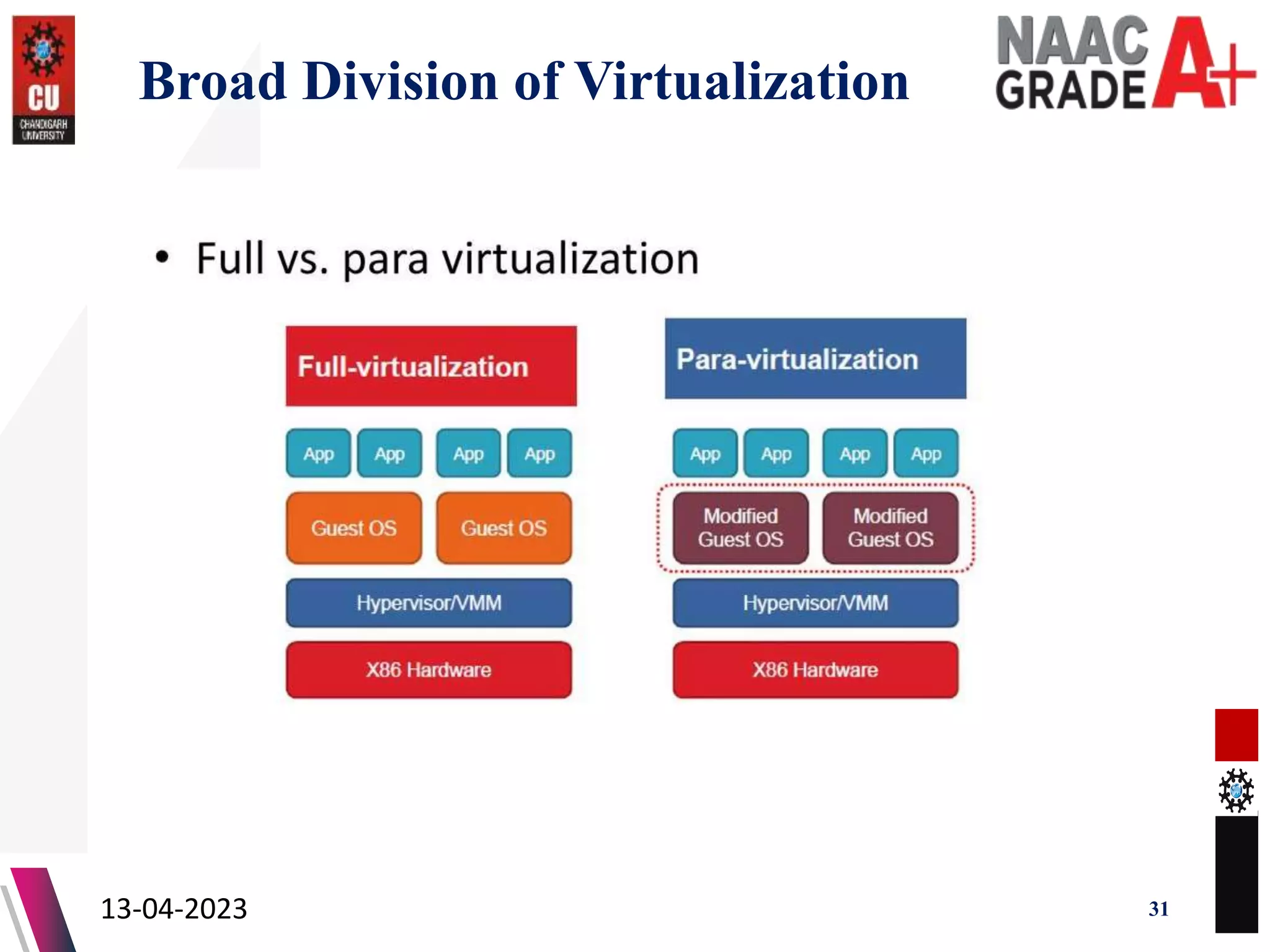
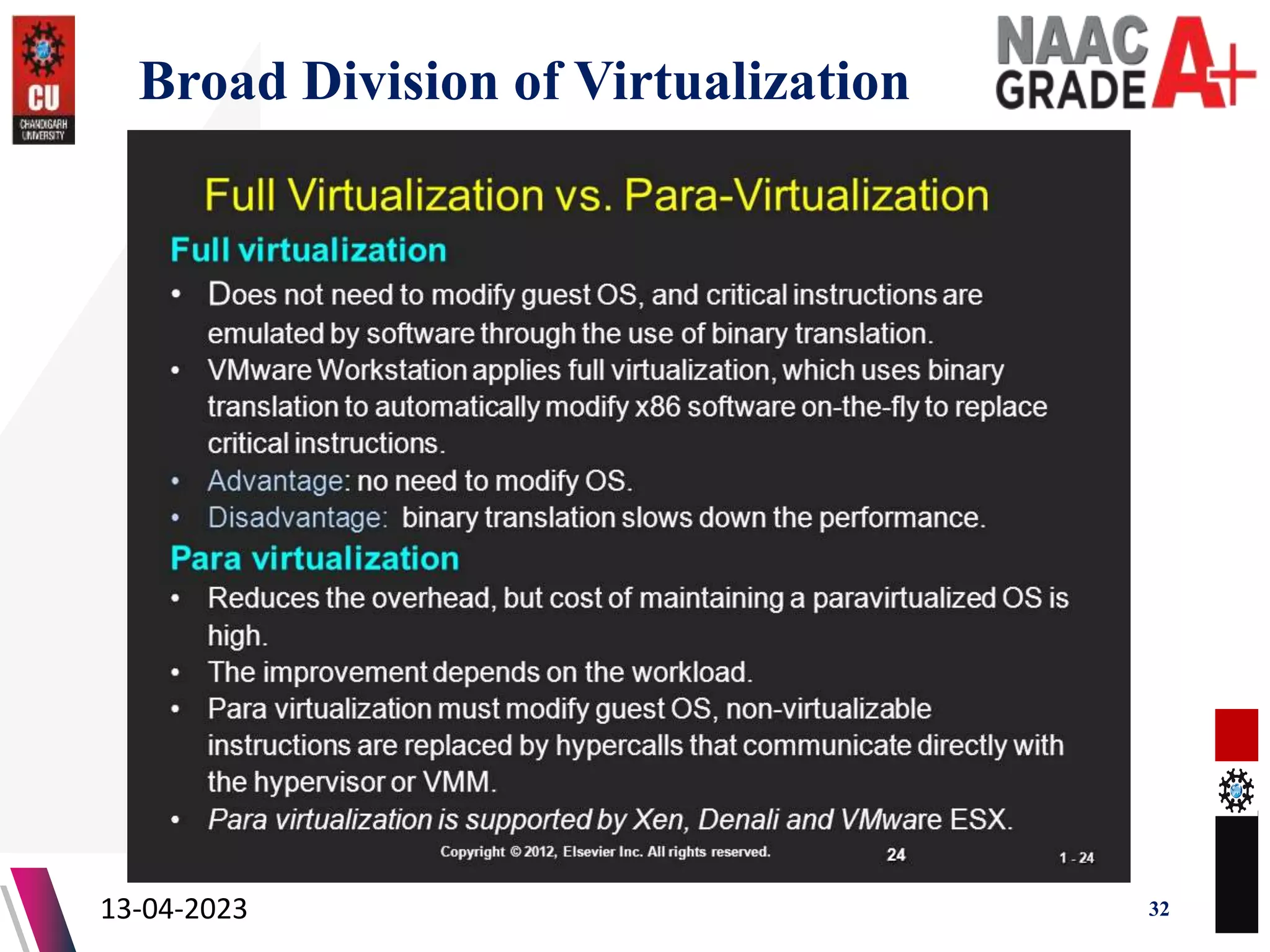
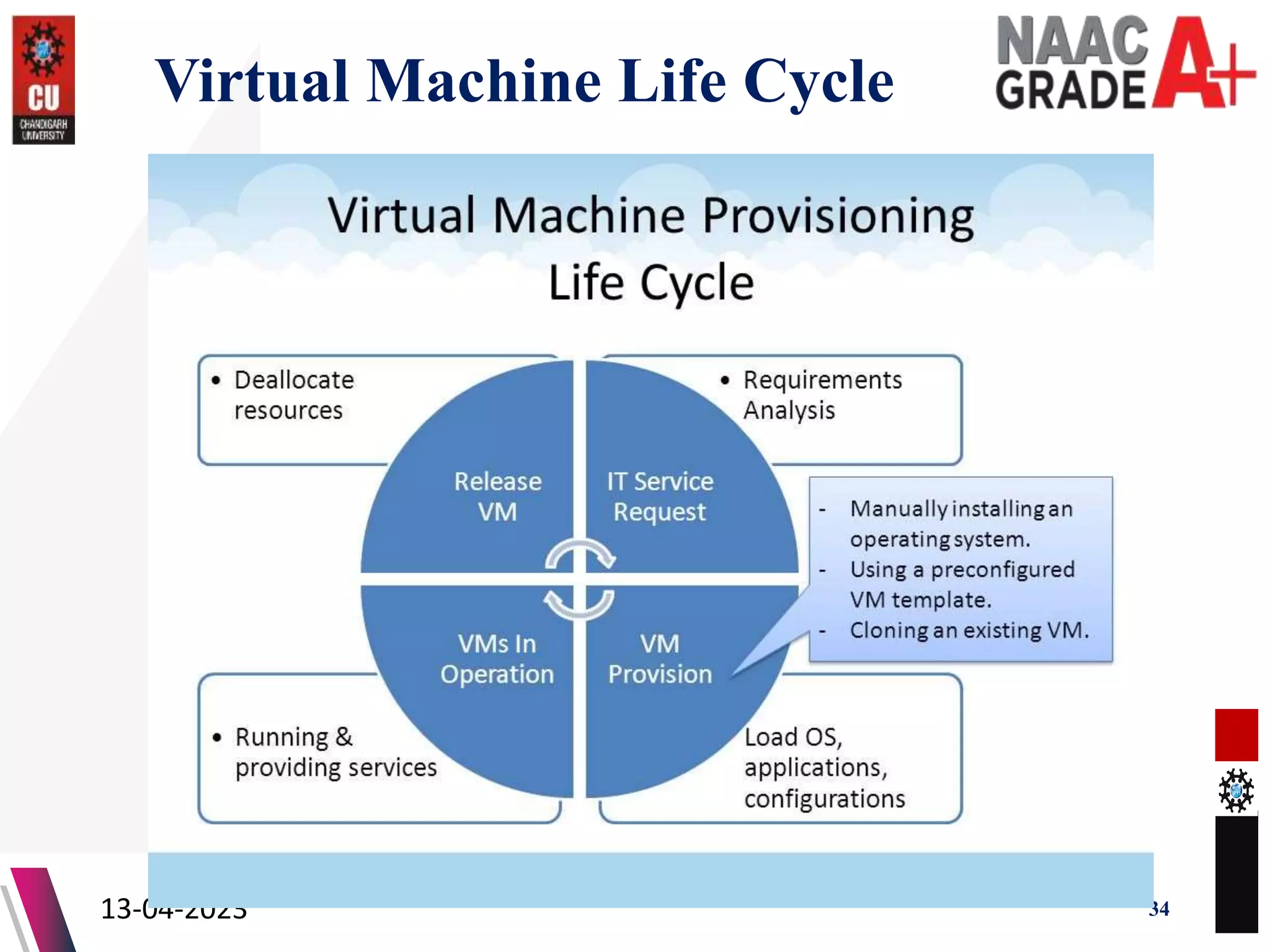
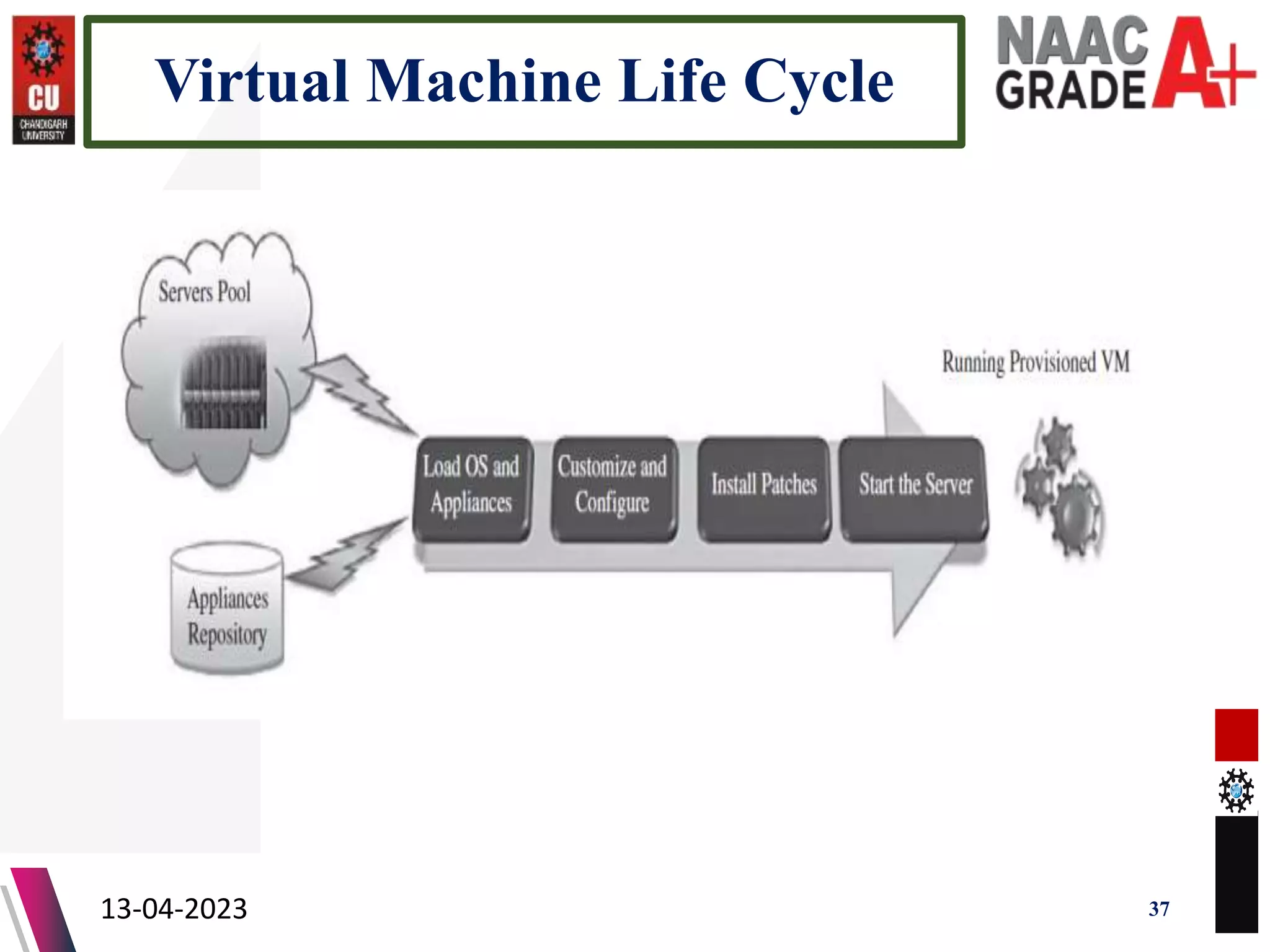
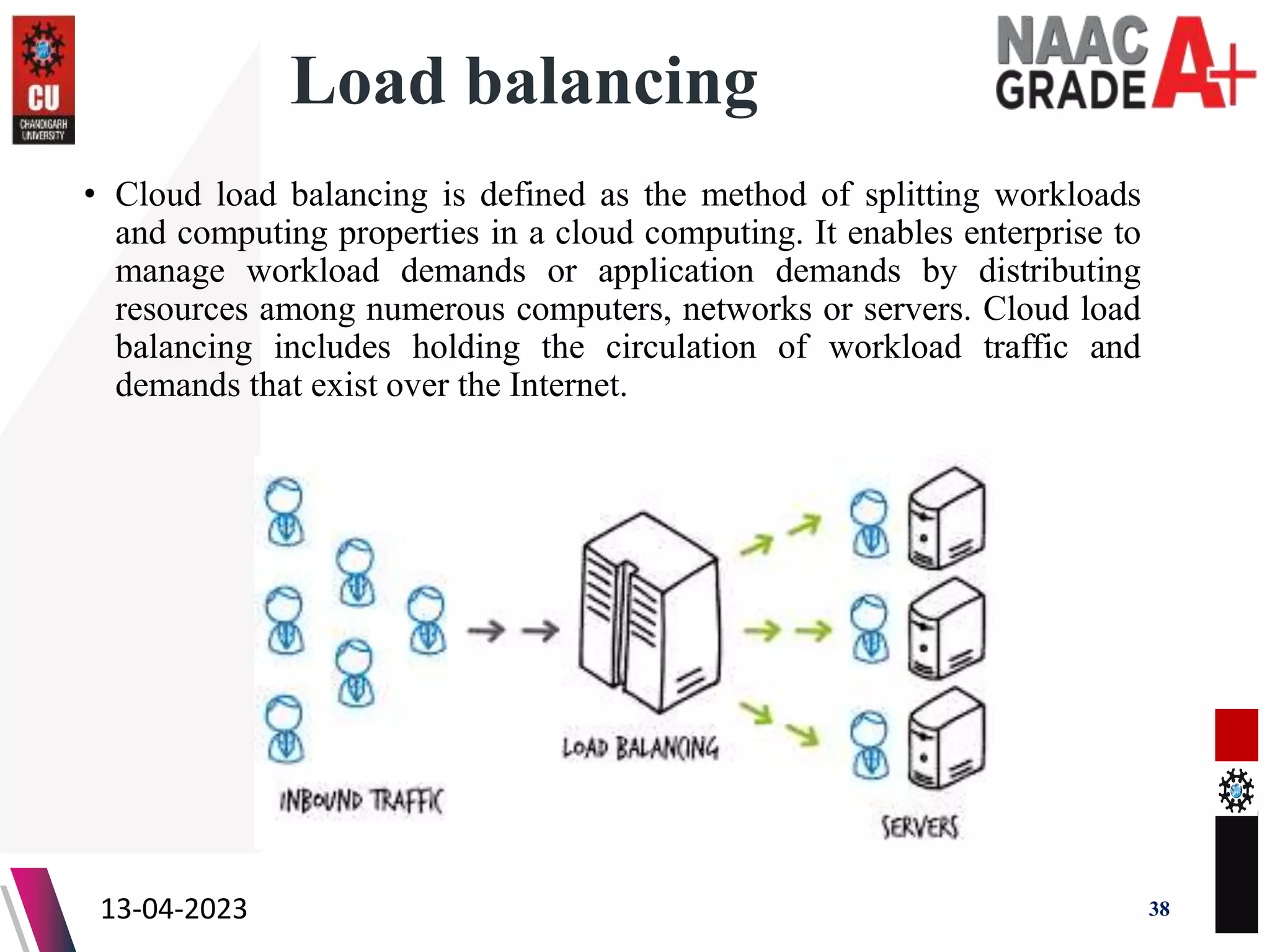
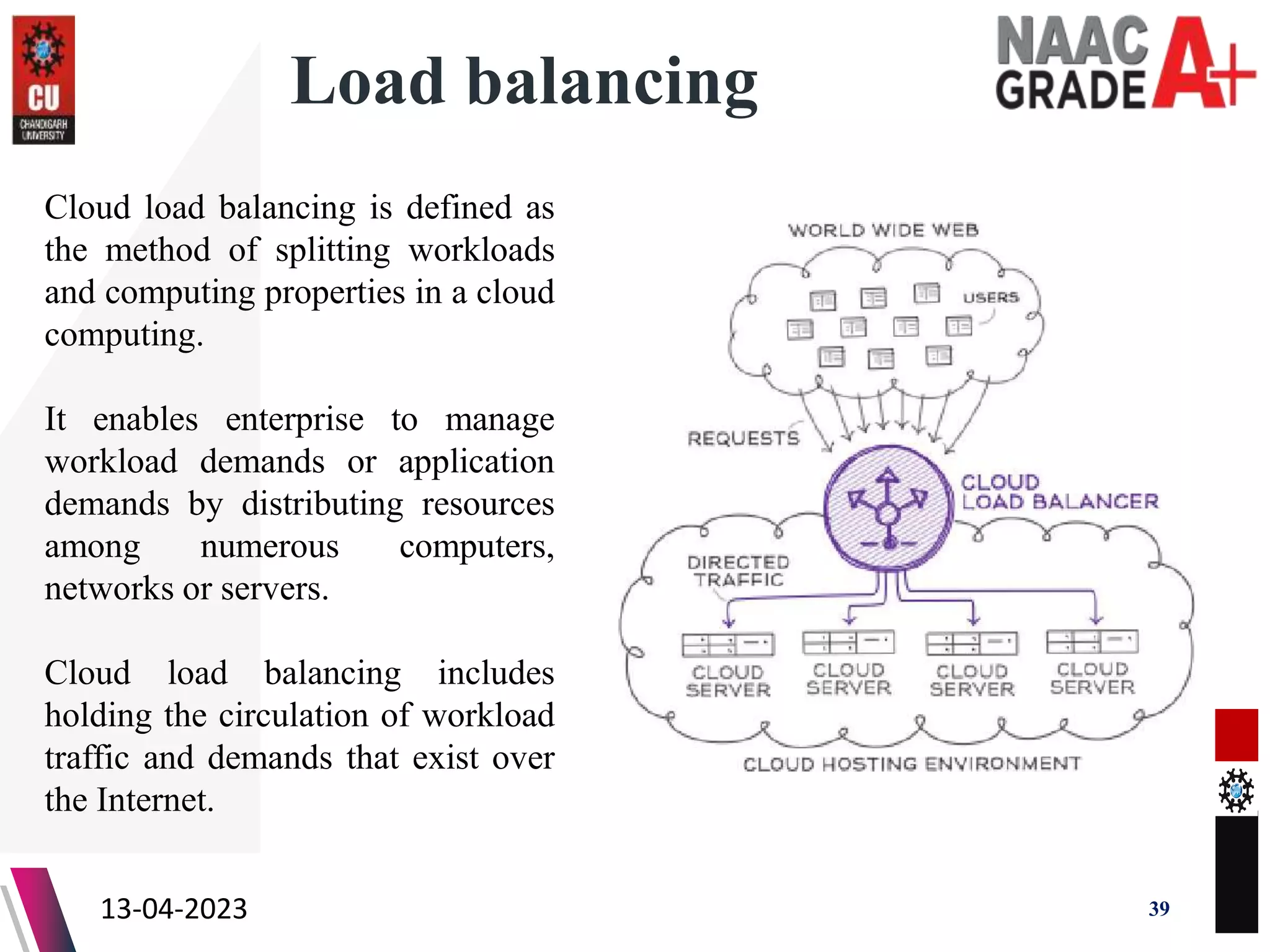
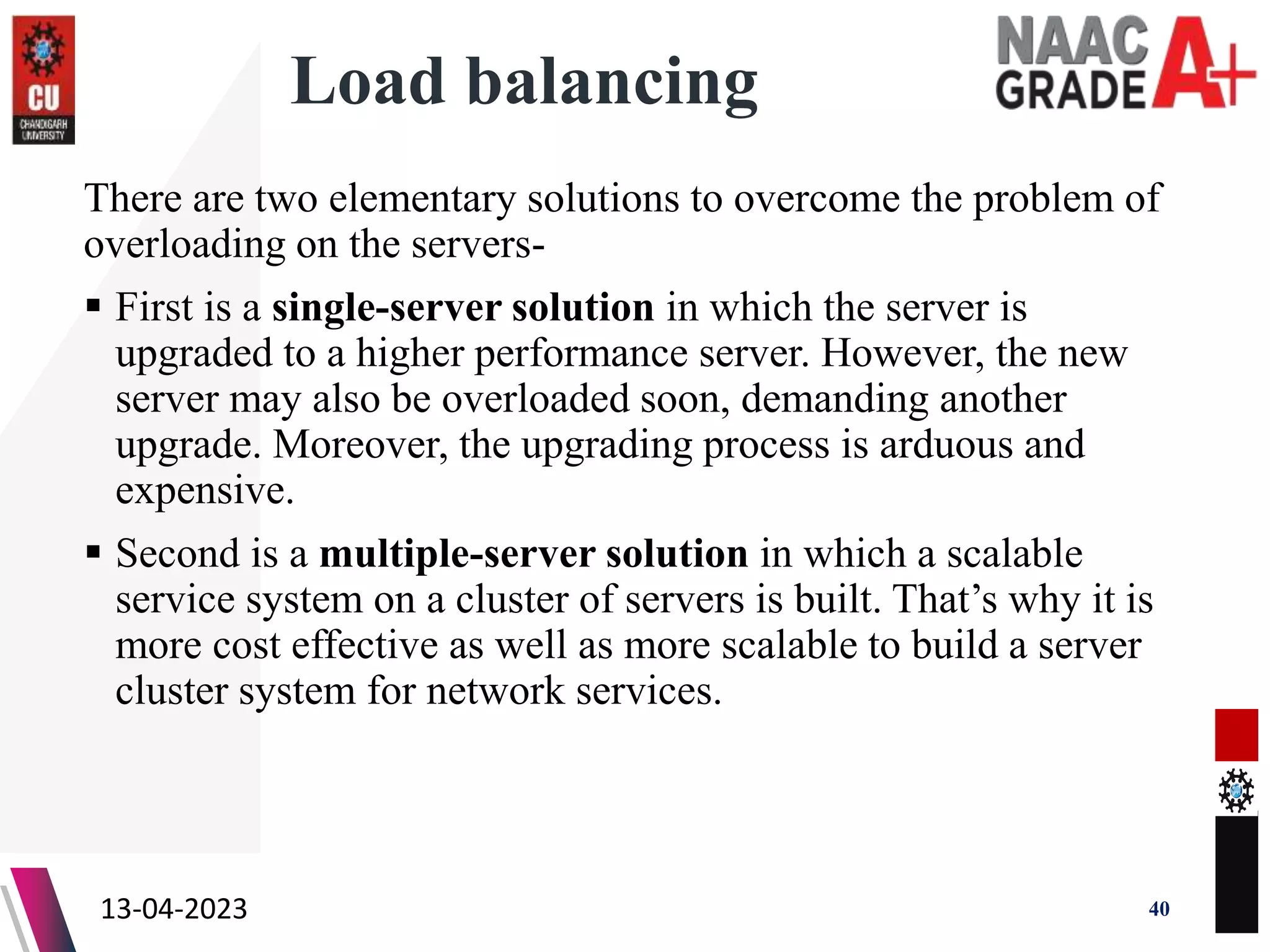
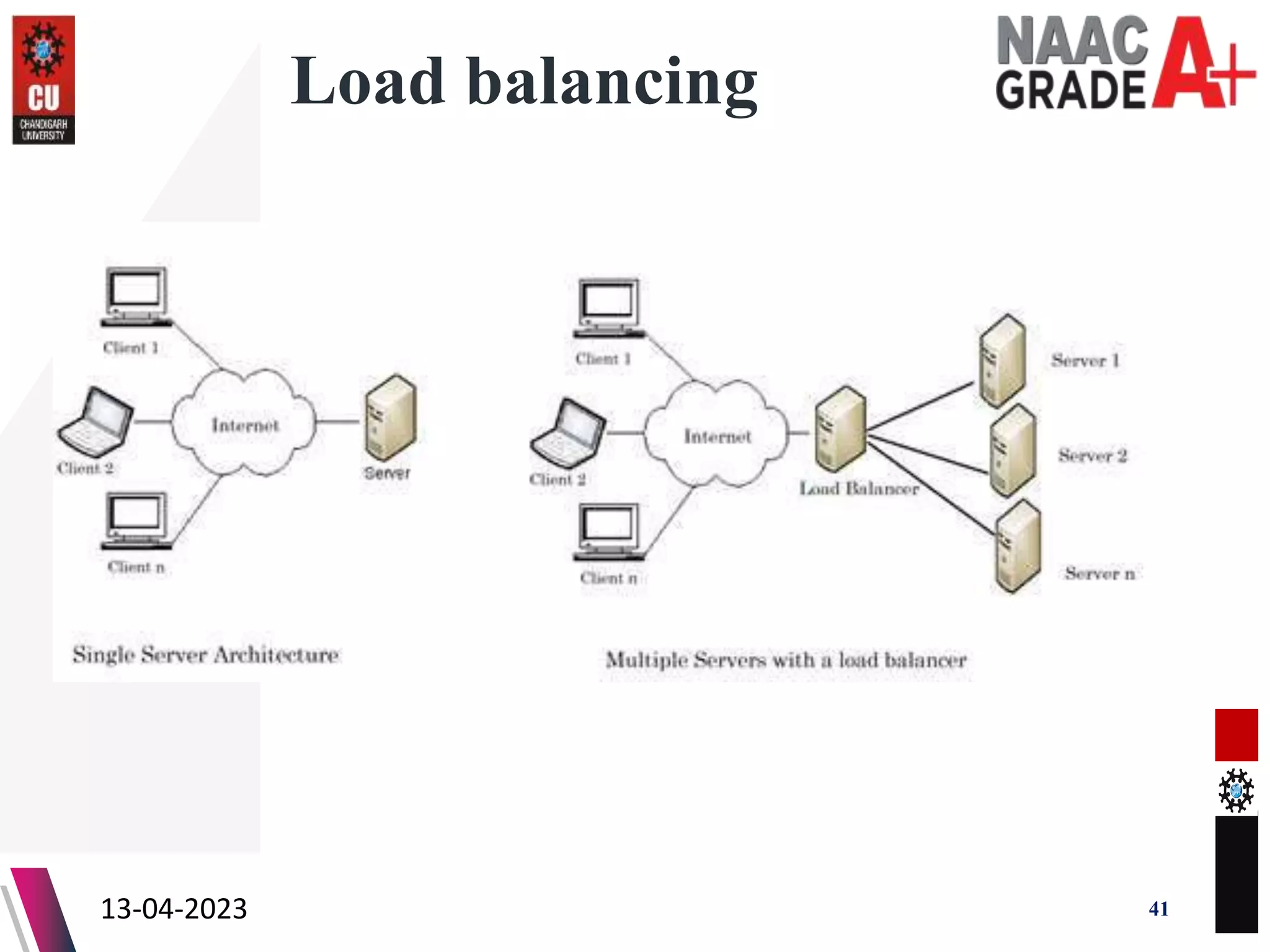
The document outlines a Master's course on Cloud Computing and Virtualization, detailing course outcomes, various types of virtualization (hardware, operating system, server, storage), and the roles of hypervisors. It also covers load balancing in cloud environments and the lifecycle of a virtual machine, including provisioning processes. Additionally, it discusses the advantages and disadvantages of virtualization and concludes with a bibliography of references.