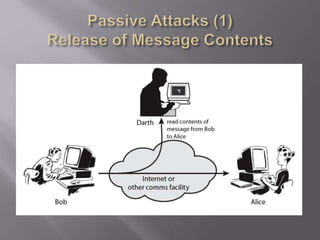
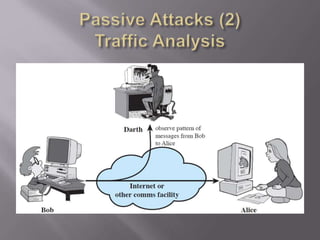
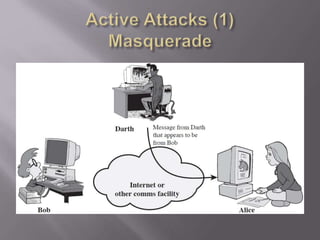
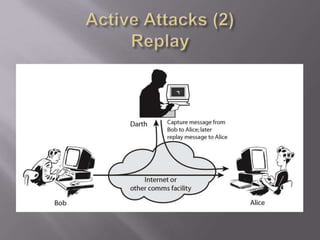
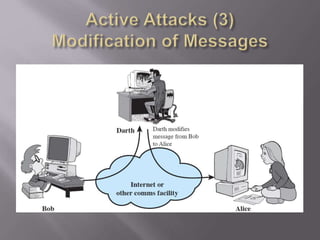
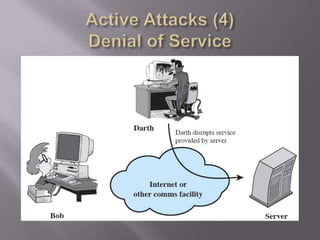
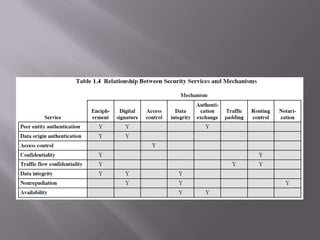
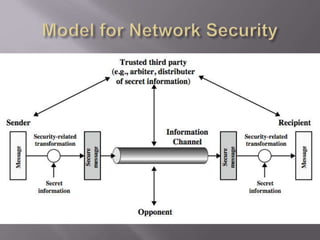
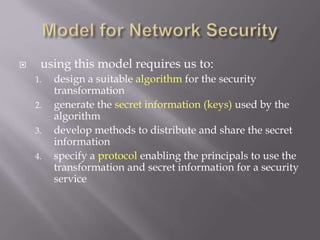
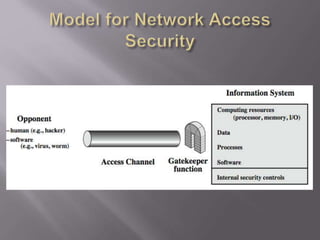
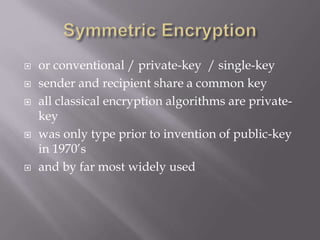
The document outlines the principles of information security, emphasizing the importance of preserving confidentiality, integrity, and availability of information systems. It describes various types of security attacks, mechanisms to counter them, and introduces cryptographic techniques as essential tools for enhancing security. Additionally, it highlights the need for regular monitoring and strategic deployment of security measures to protect against threats.

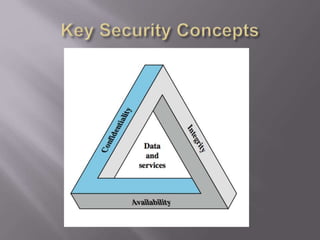
![ The protection afforded to an automated
information system in order to attain the
applicable objectives of preserving the
integrity, availability and confidentiality of
information system resources (includes
hardware, software, firmware,
information/data, and telecommunications)
[NIST 1995]](https://image.slidesharecdn.com/lecture-0102-1-240527072829-a079516d/85/Lecture-01-02-1-Information-security-introduction-ppt-2-320.jpg)