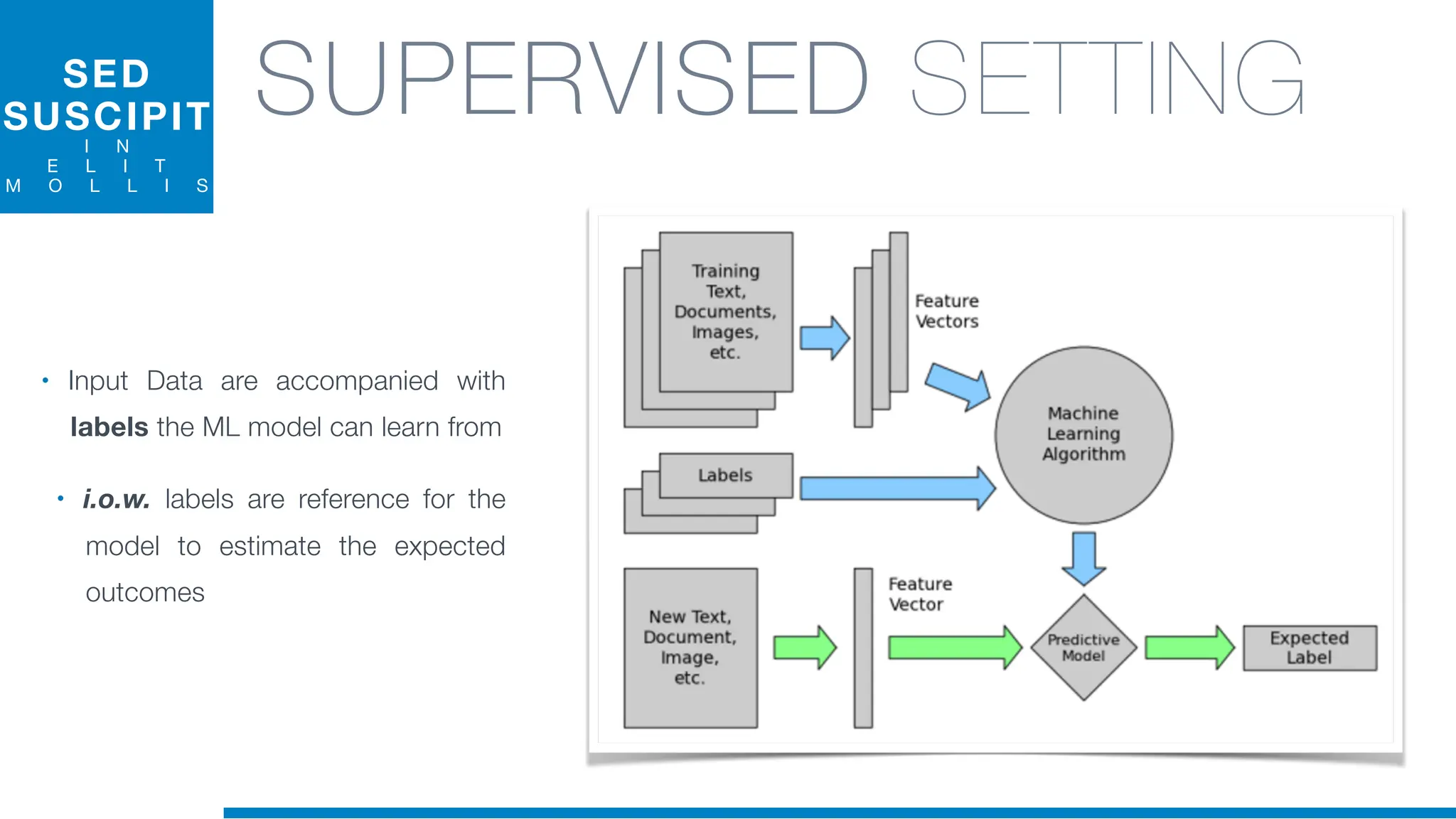
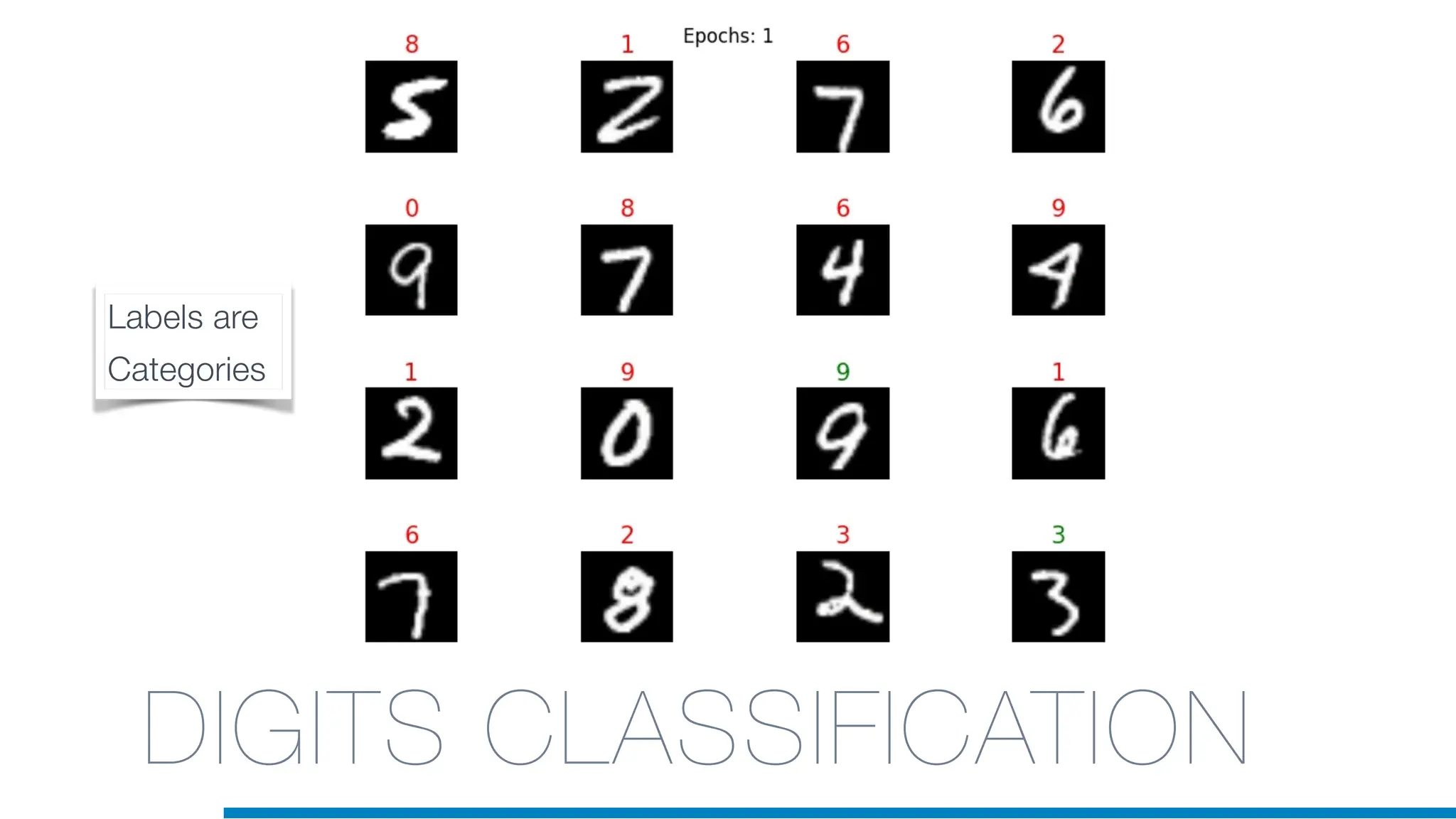
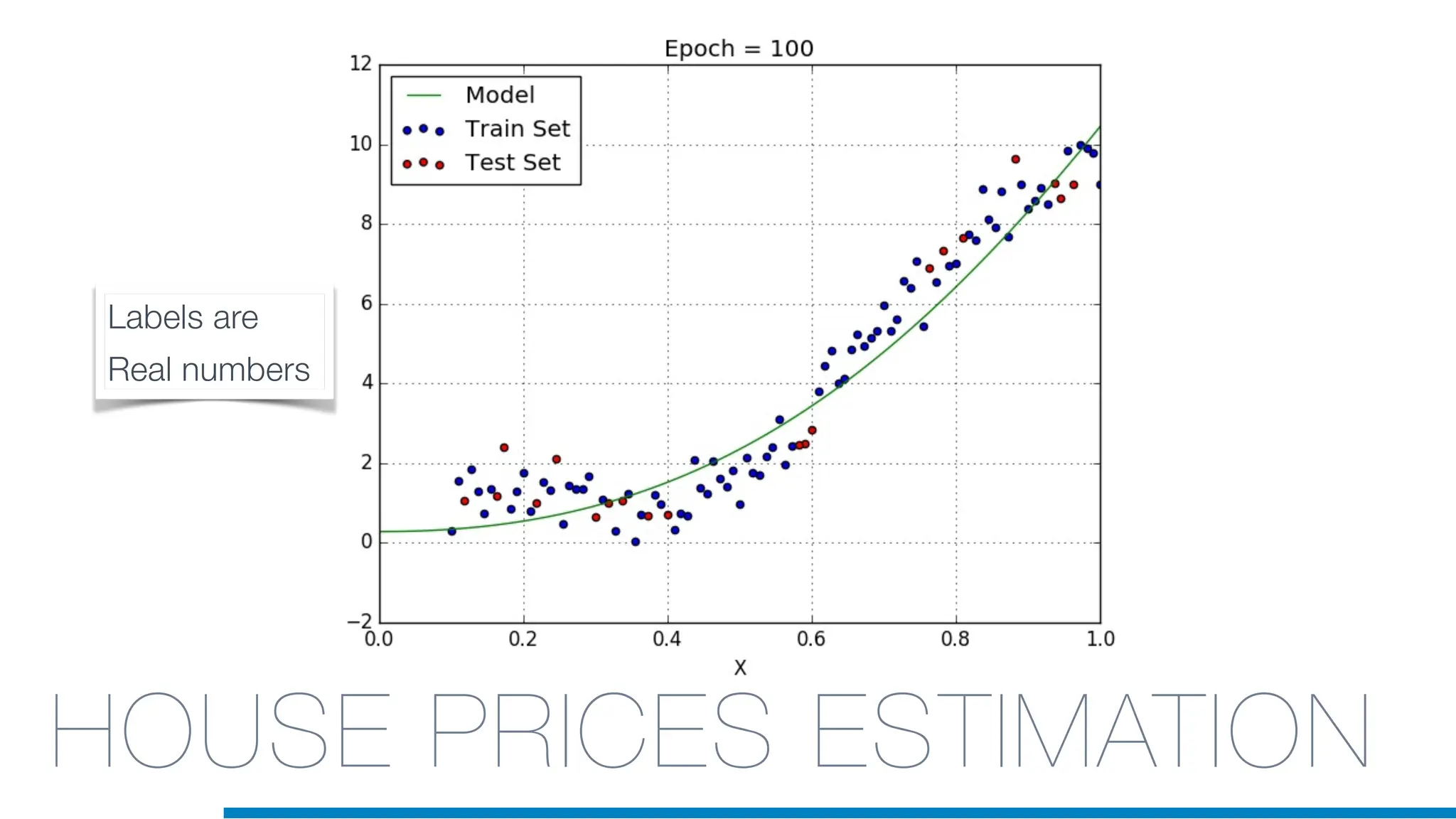
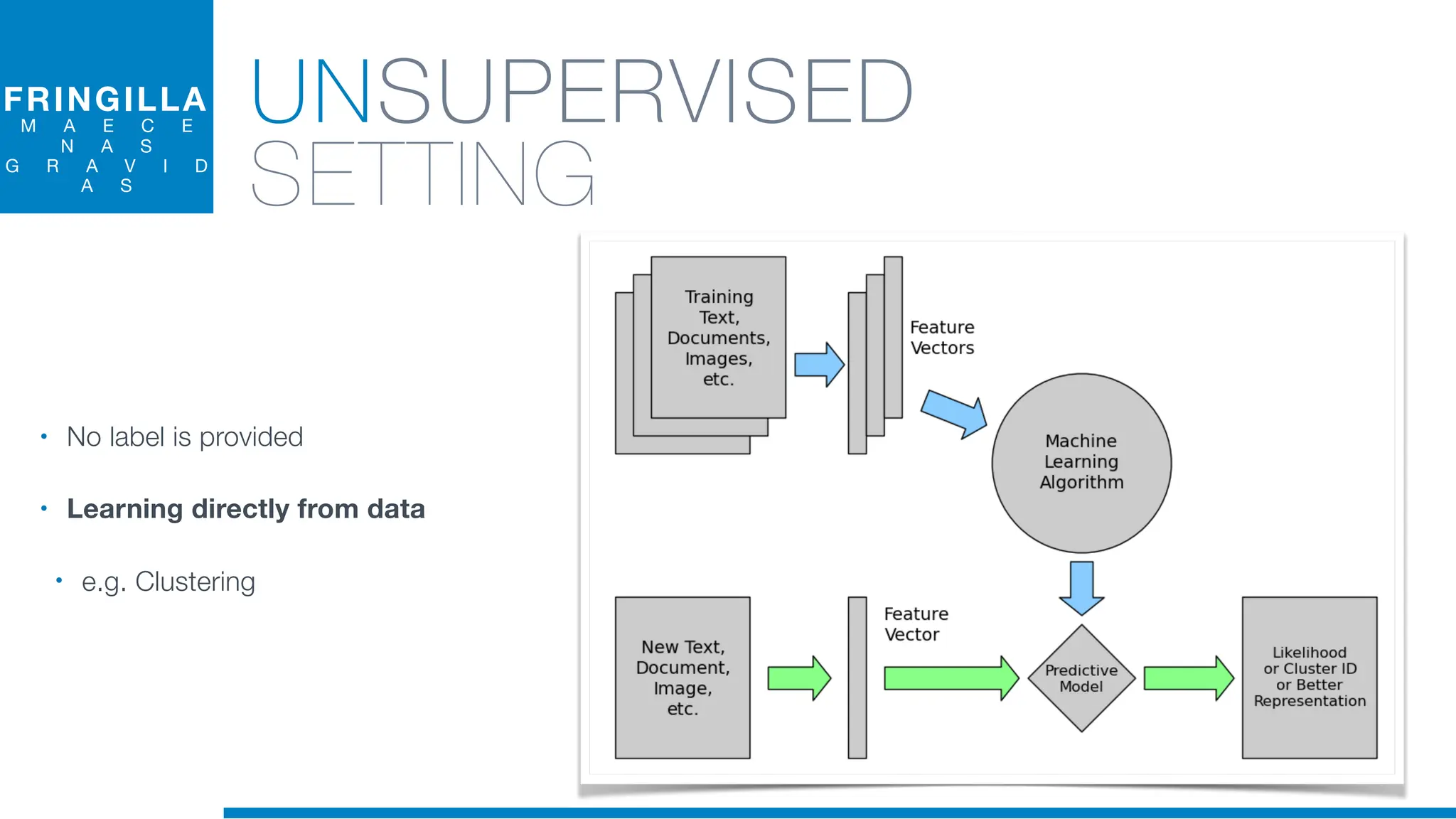
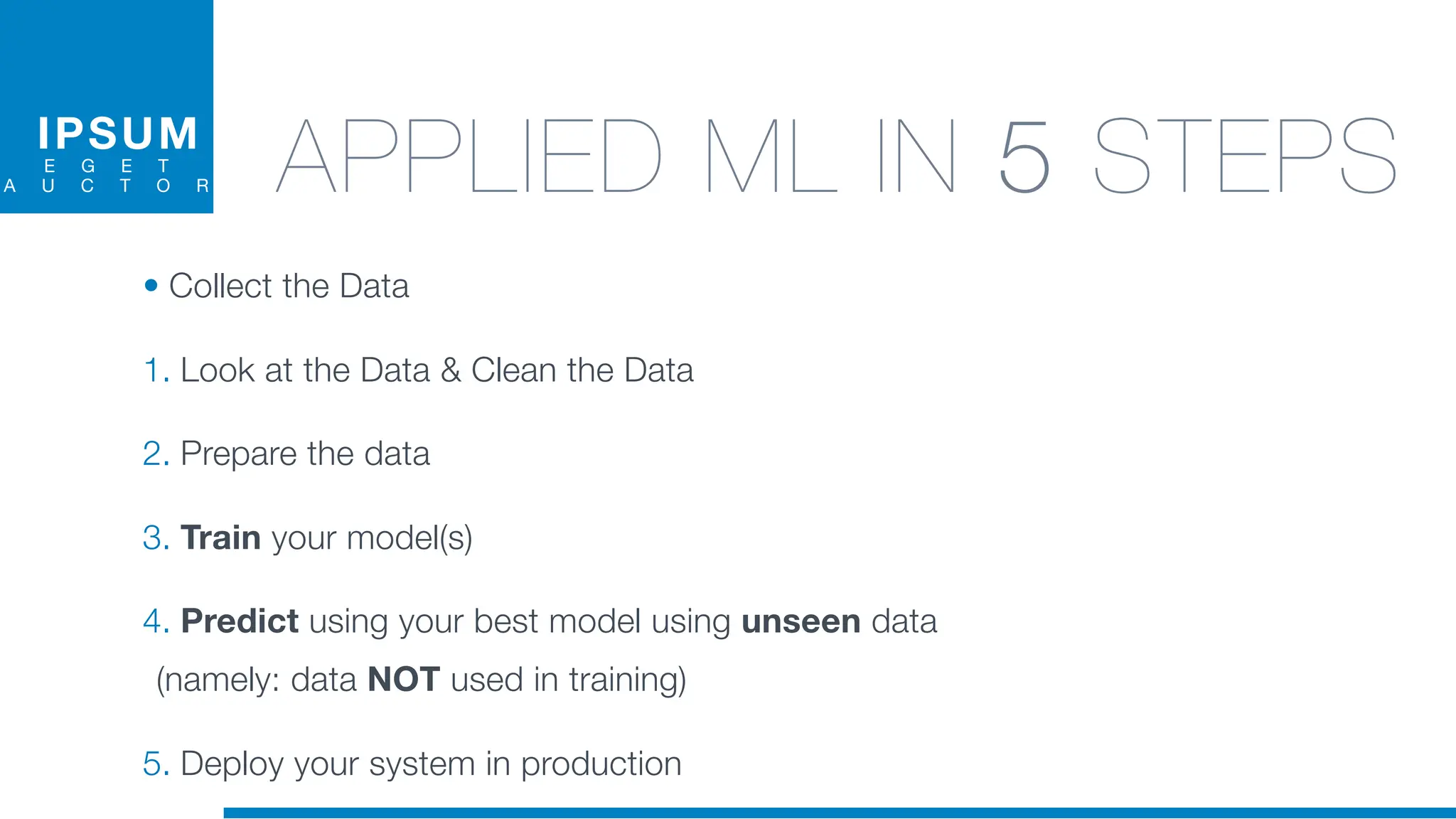
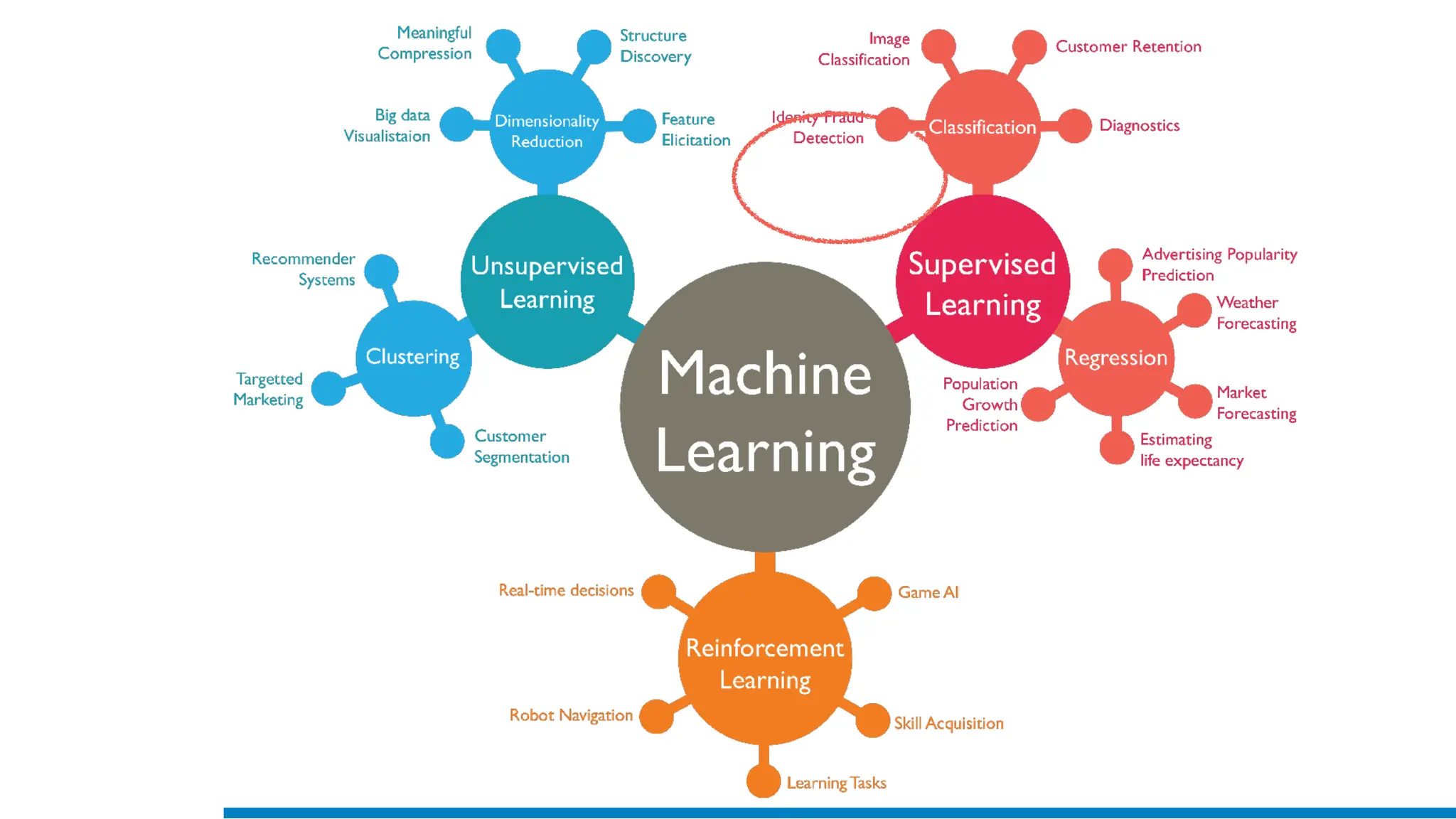
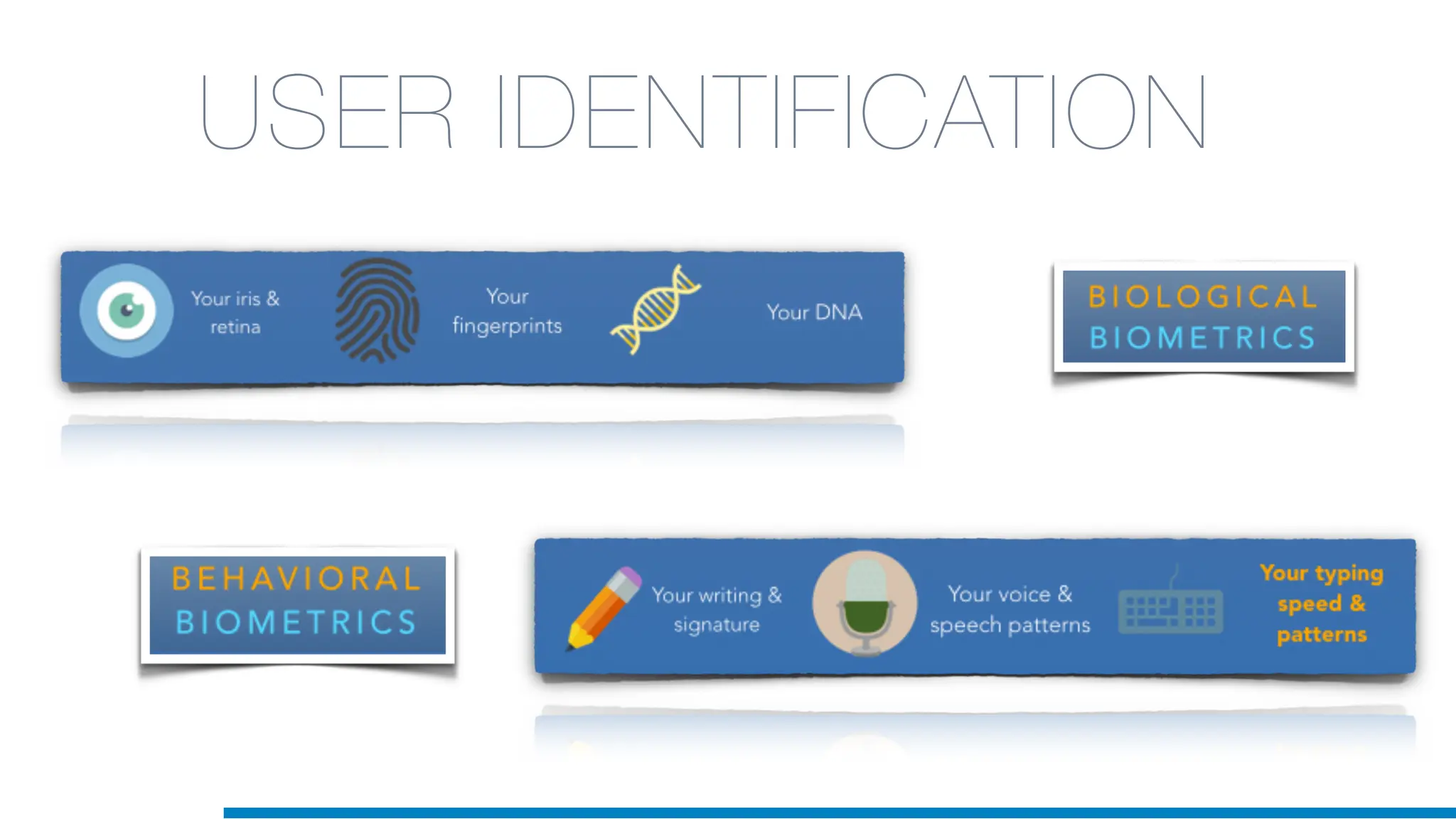
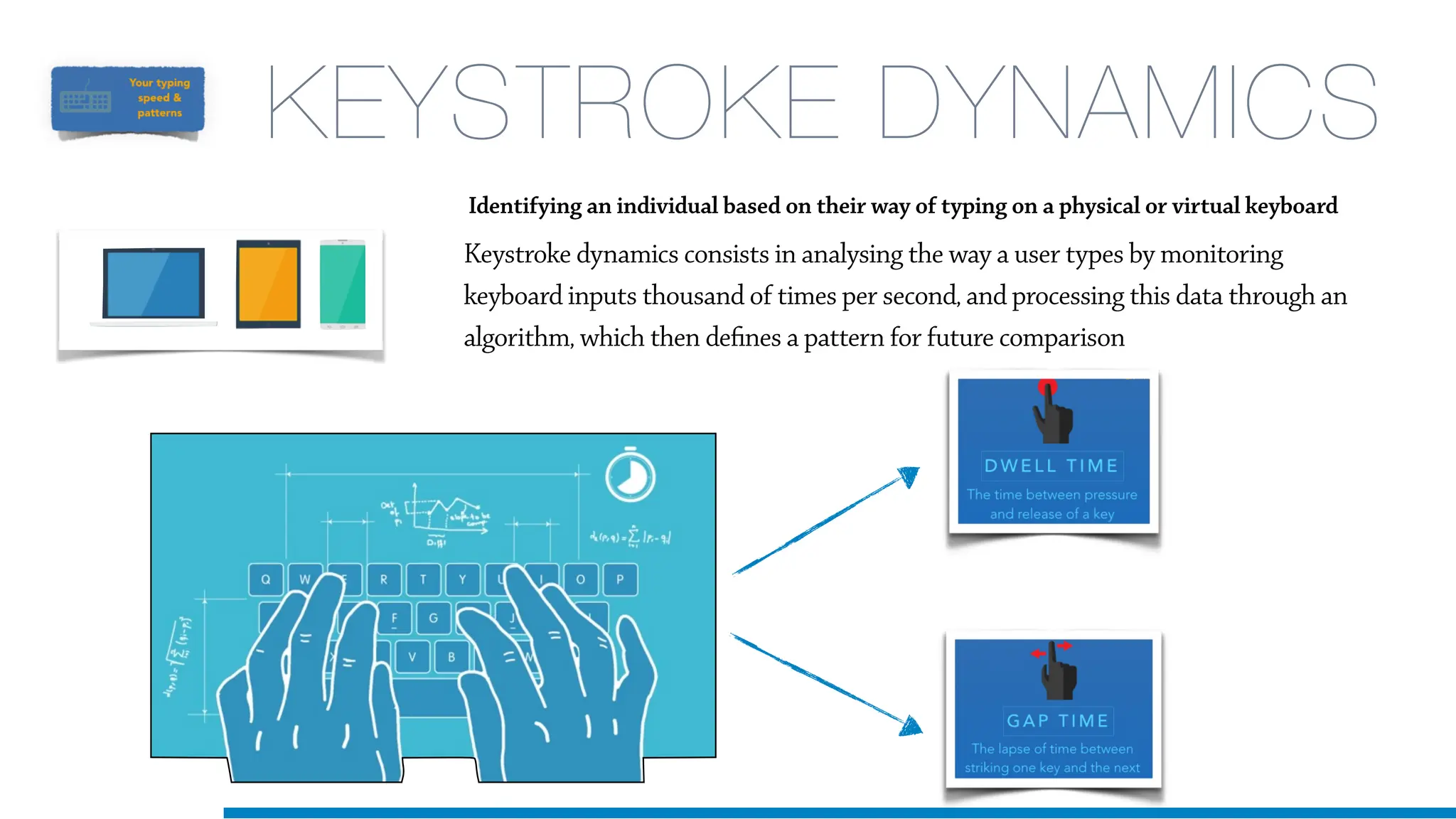
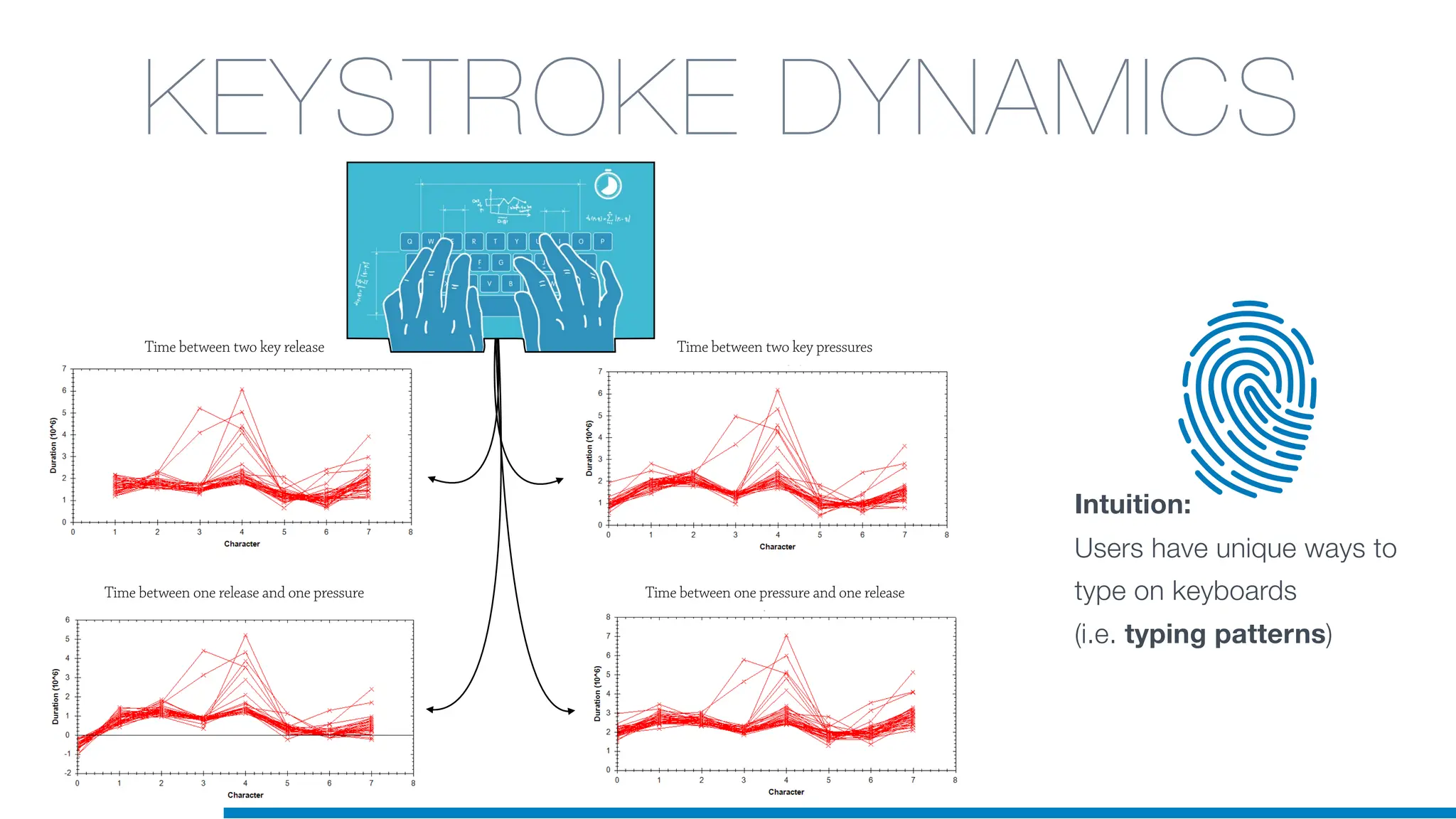
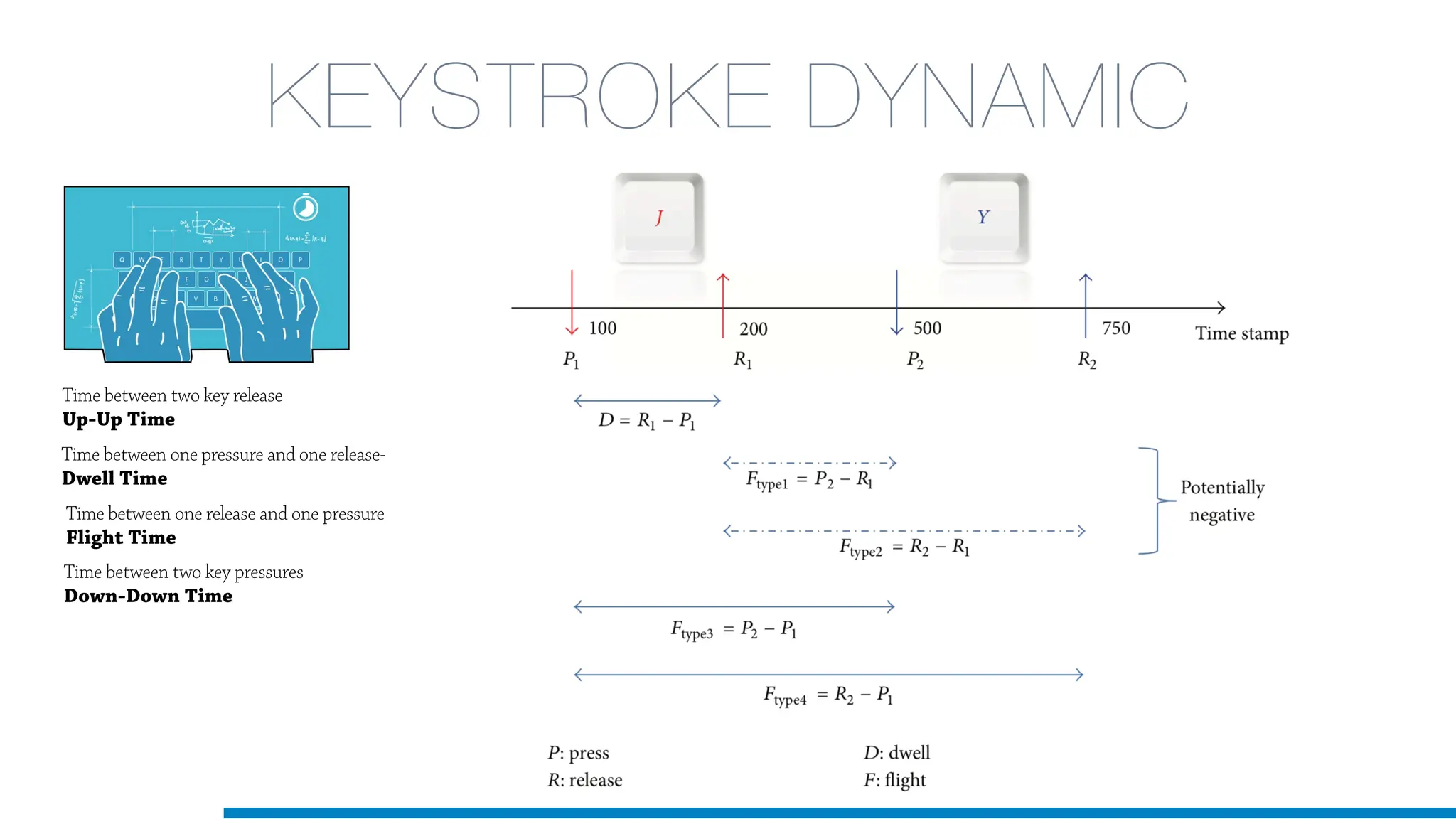
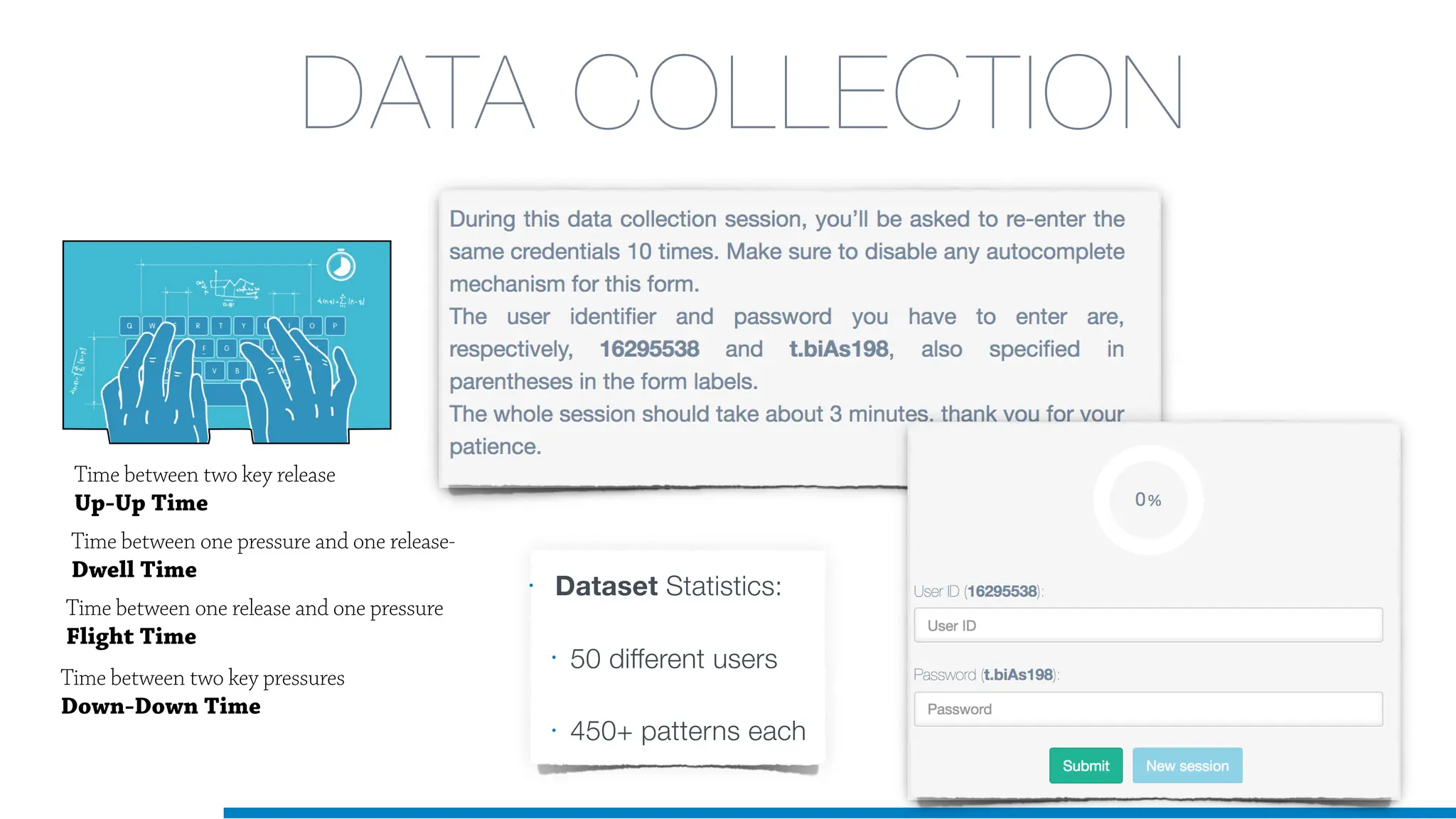
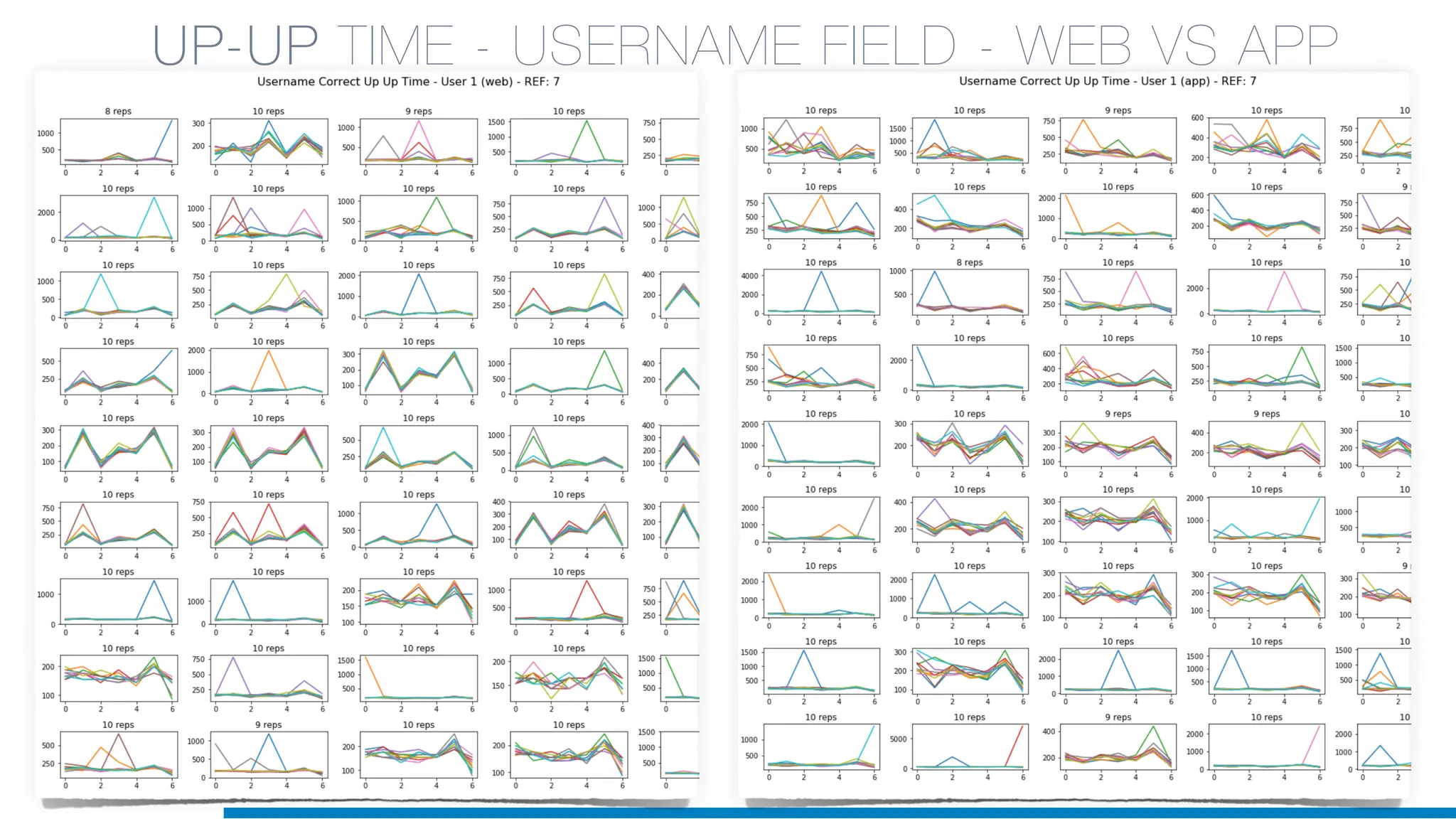
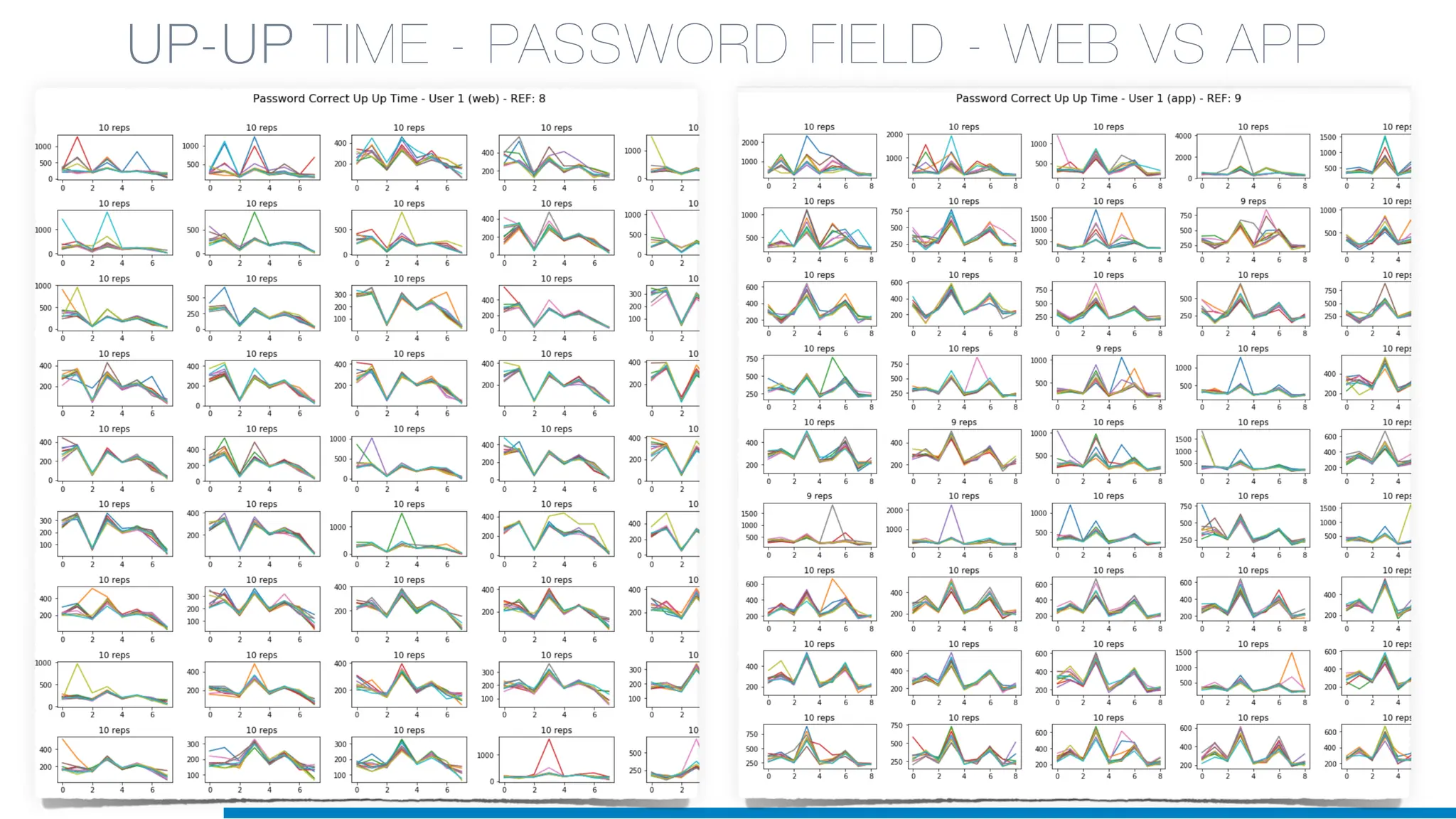
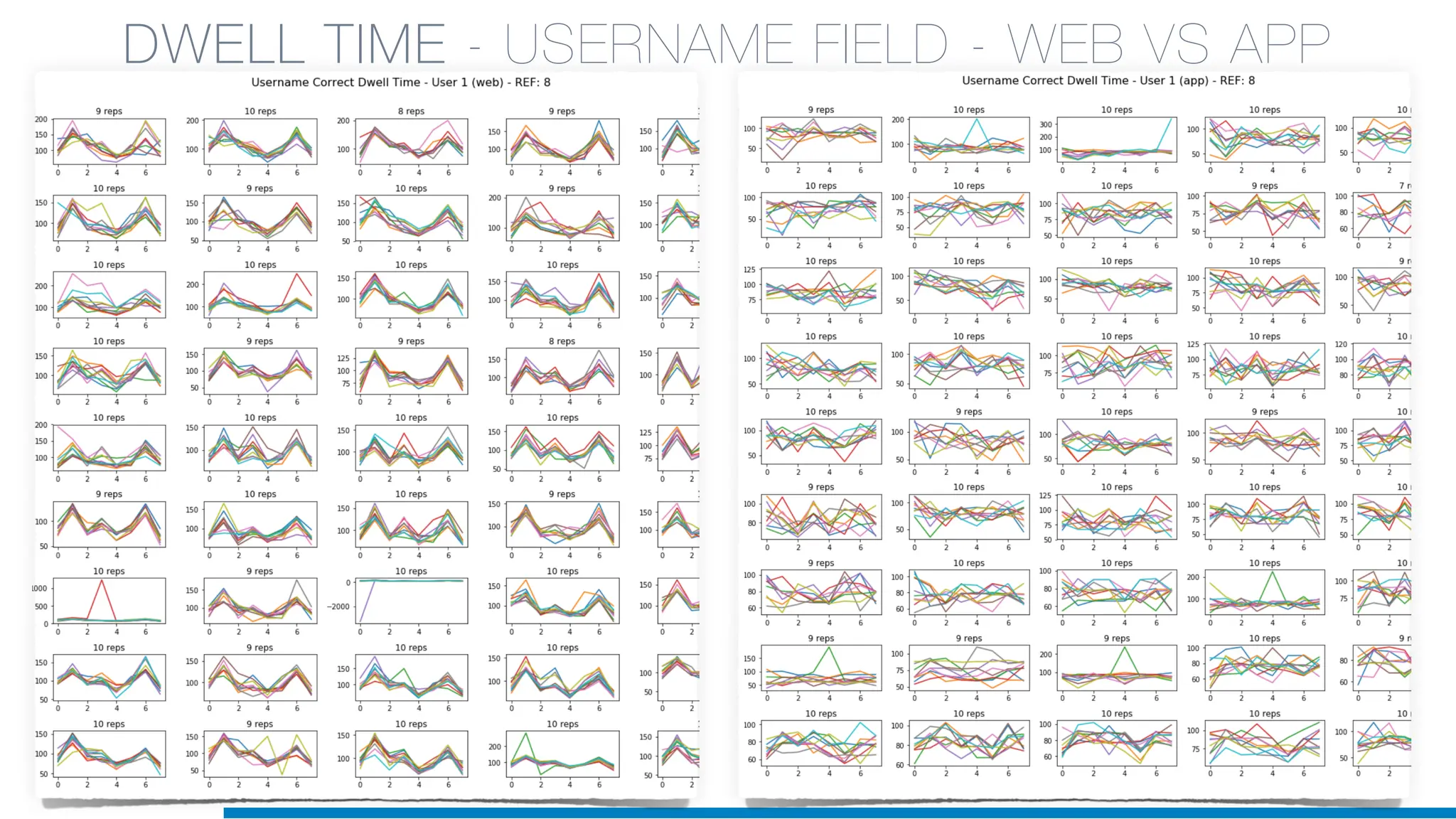
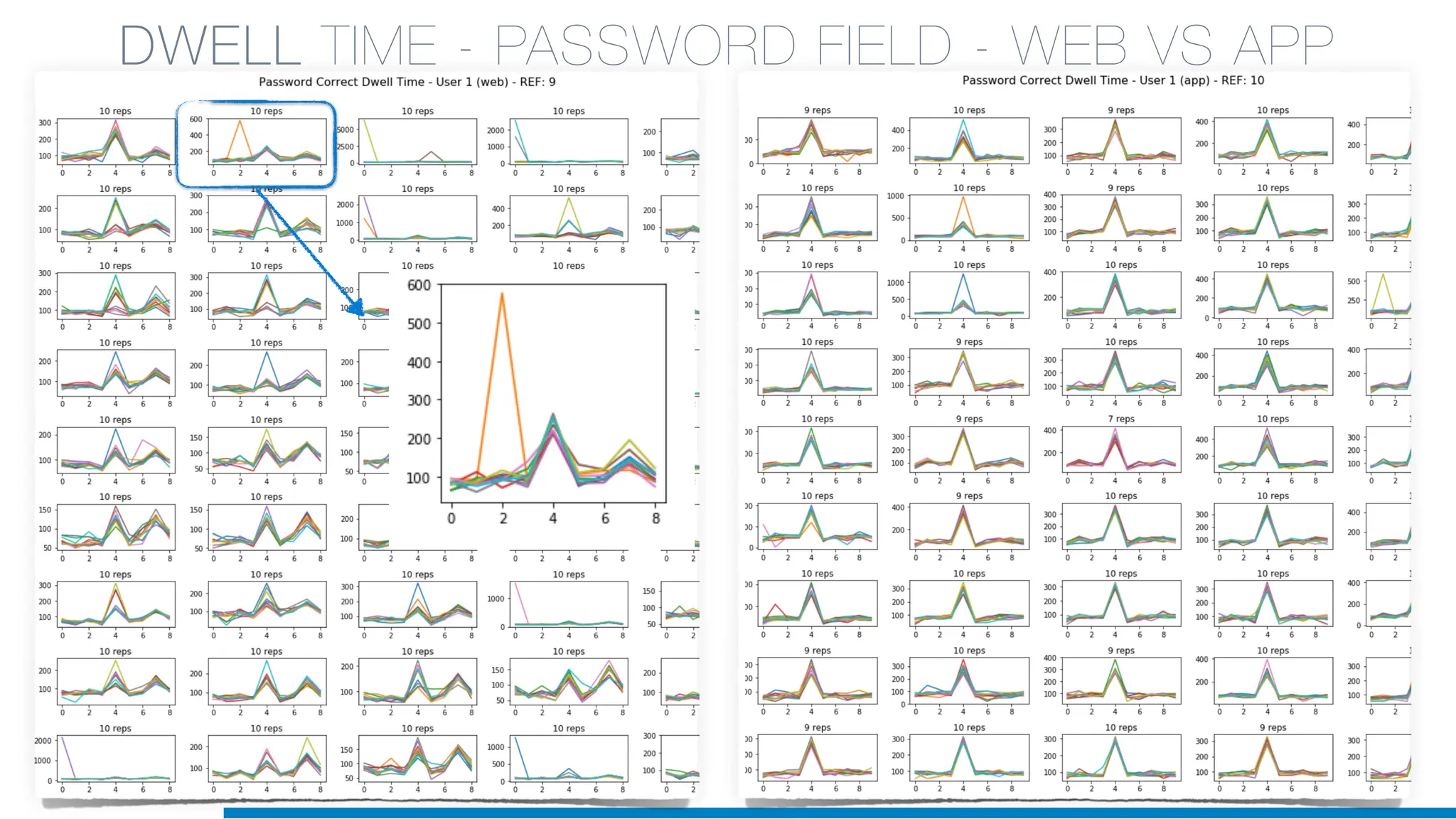
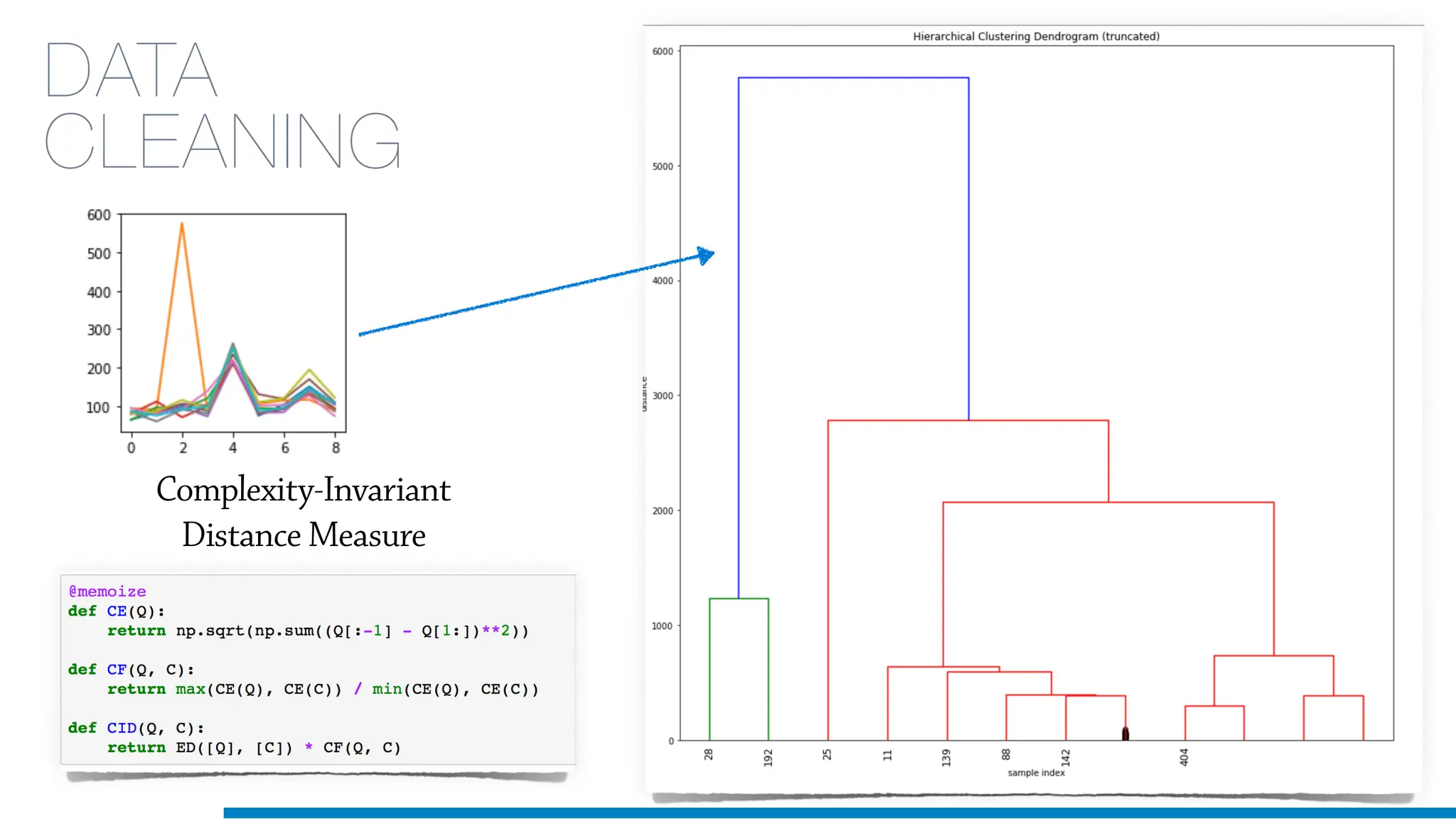
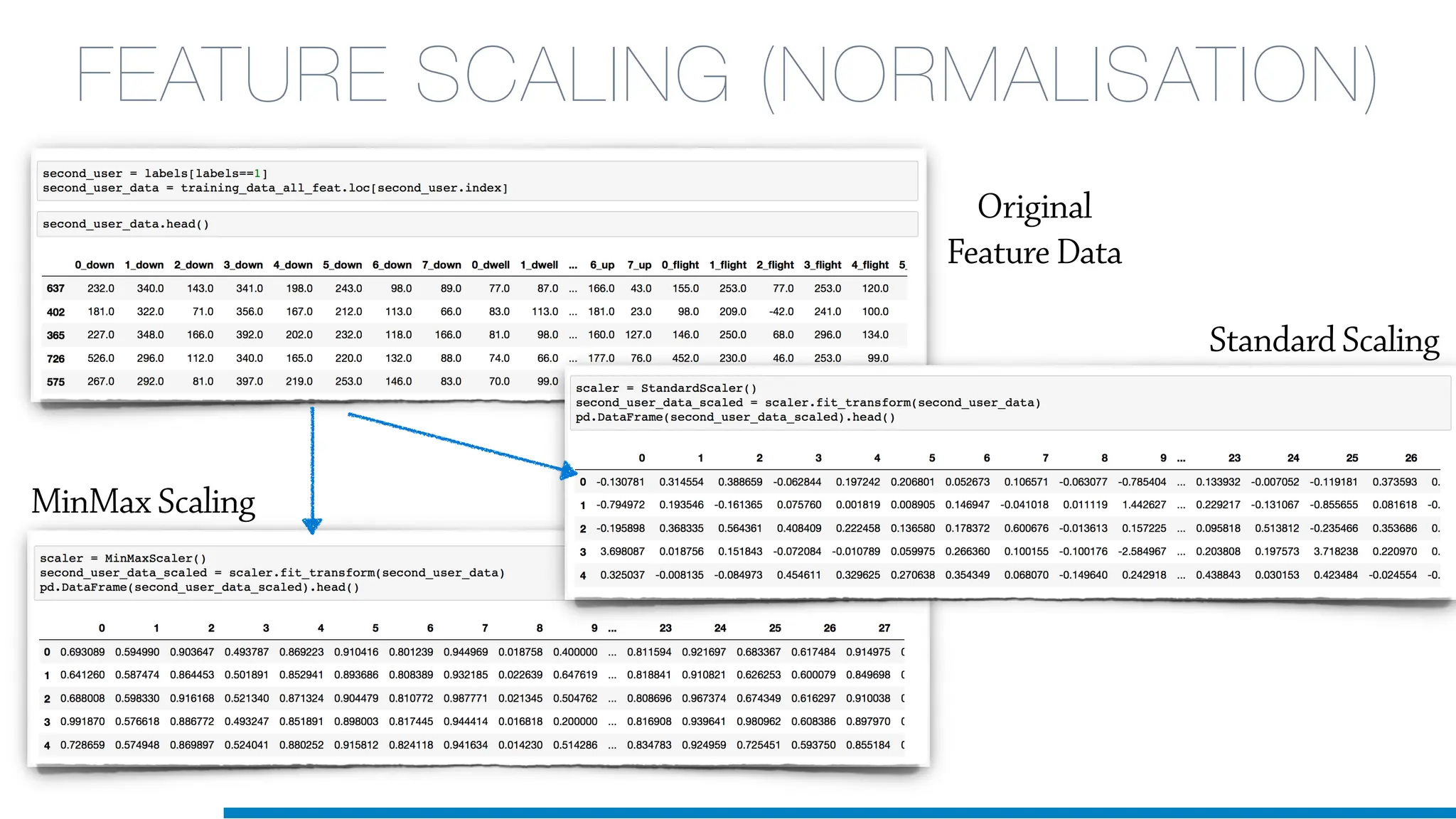
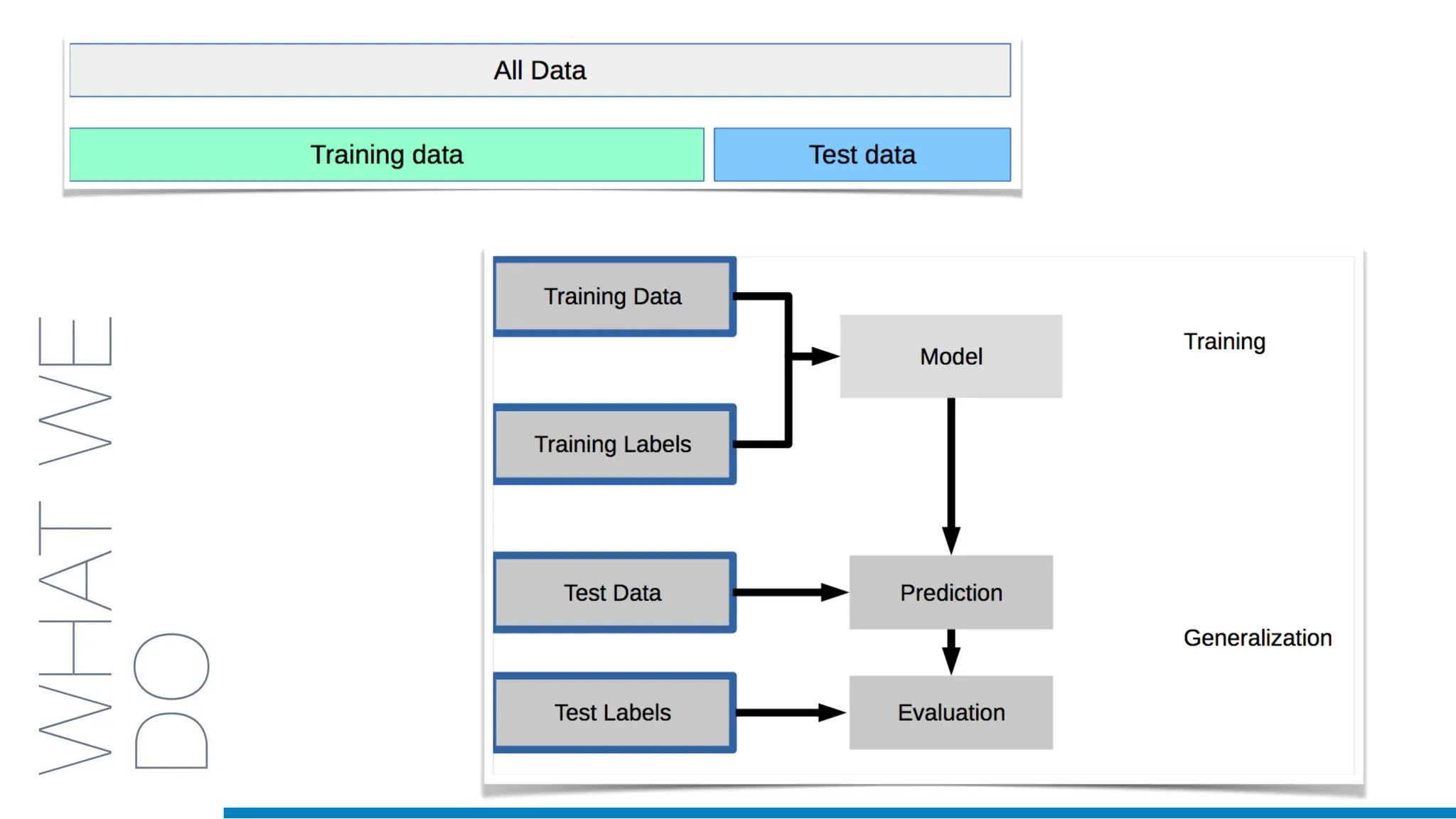
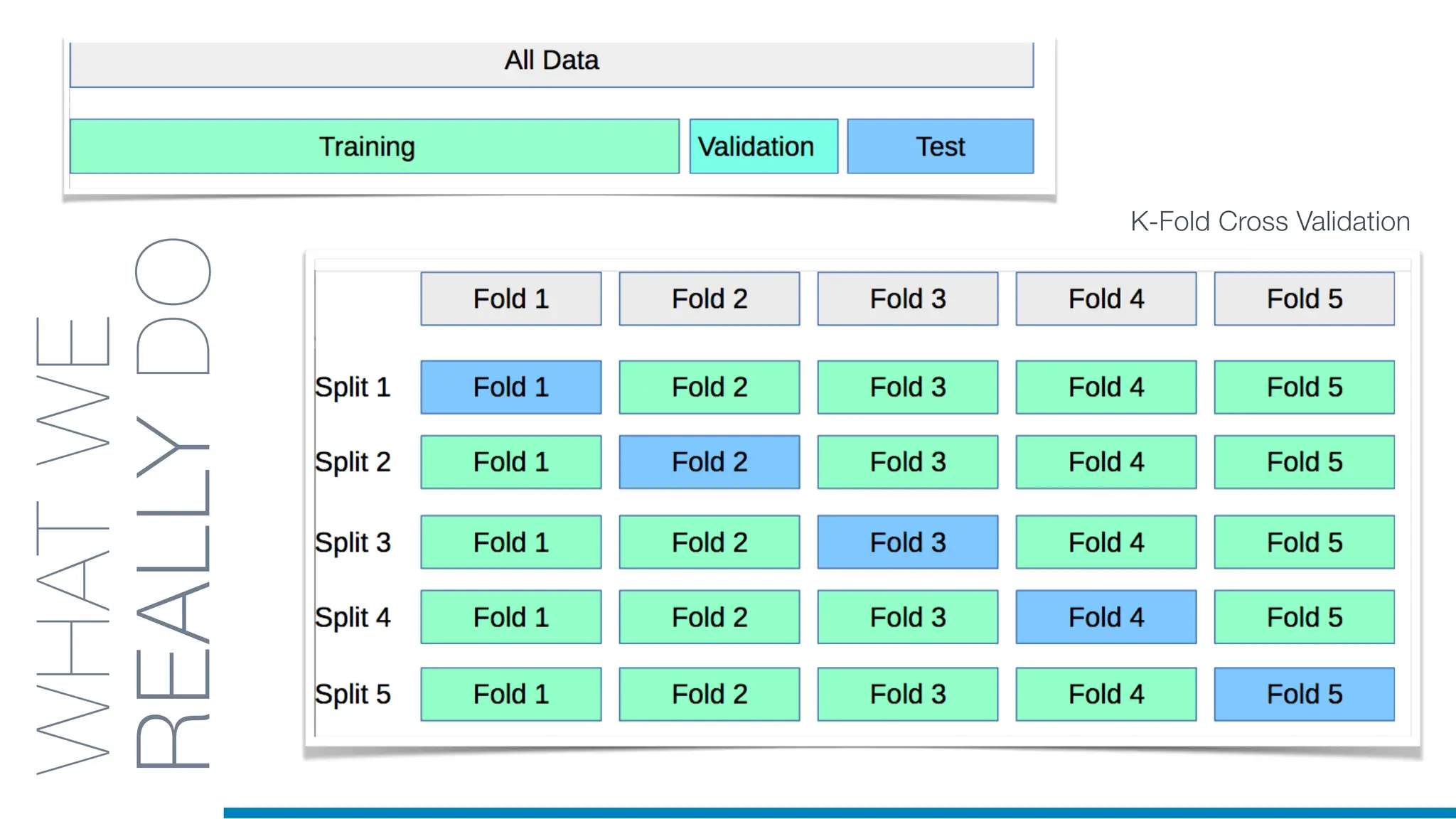
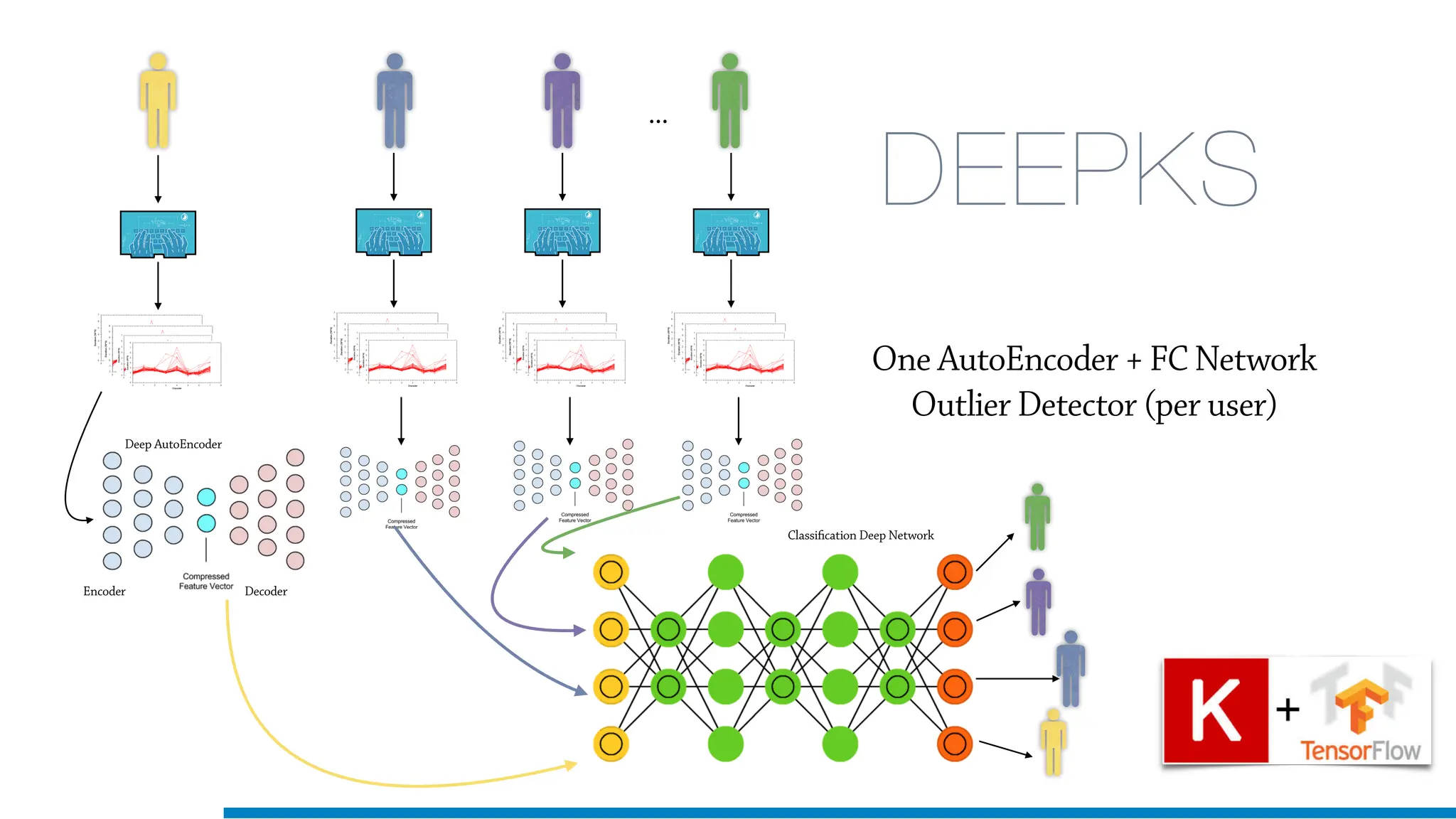
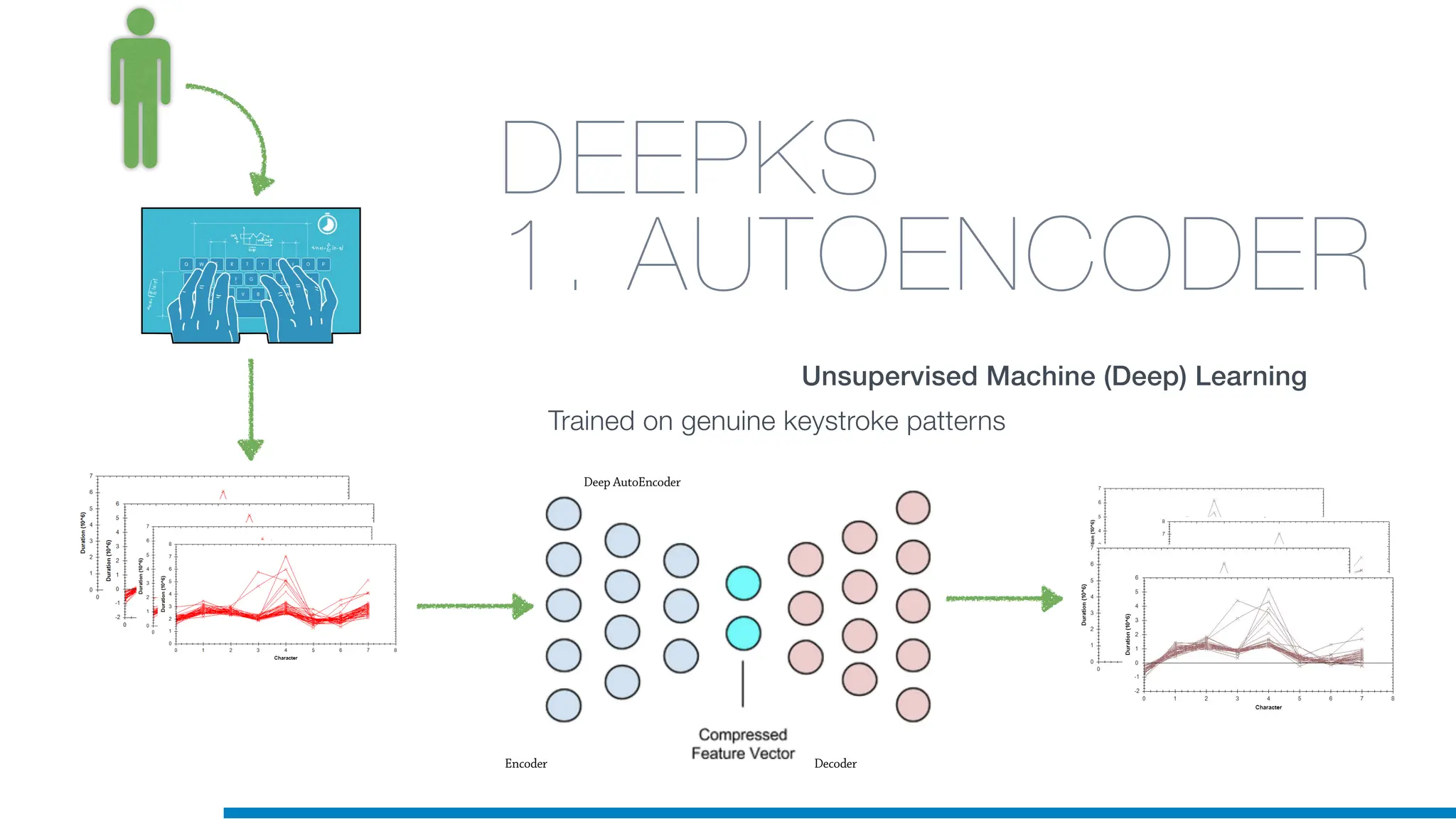
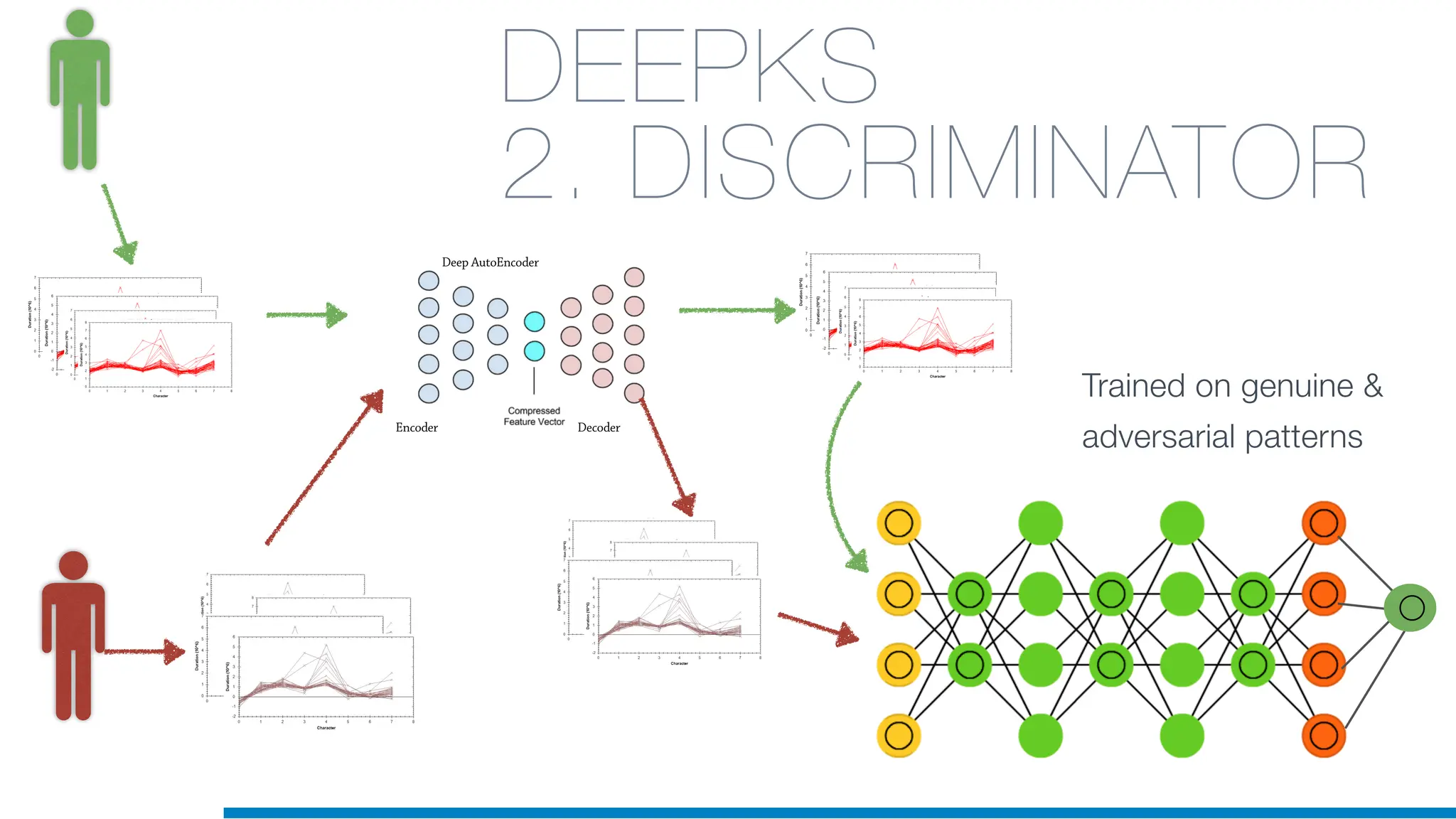
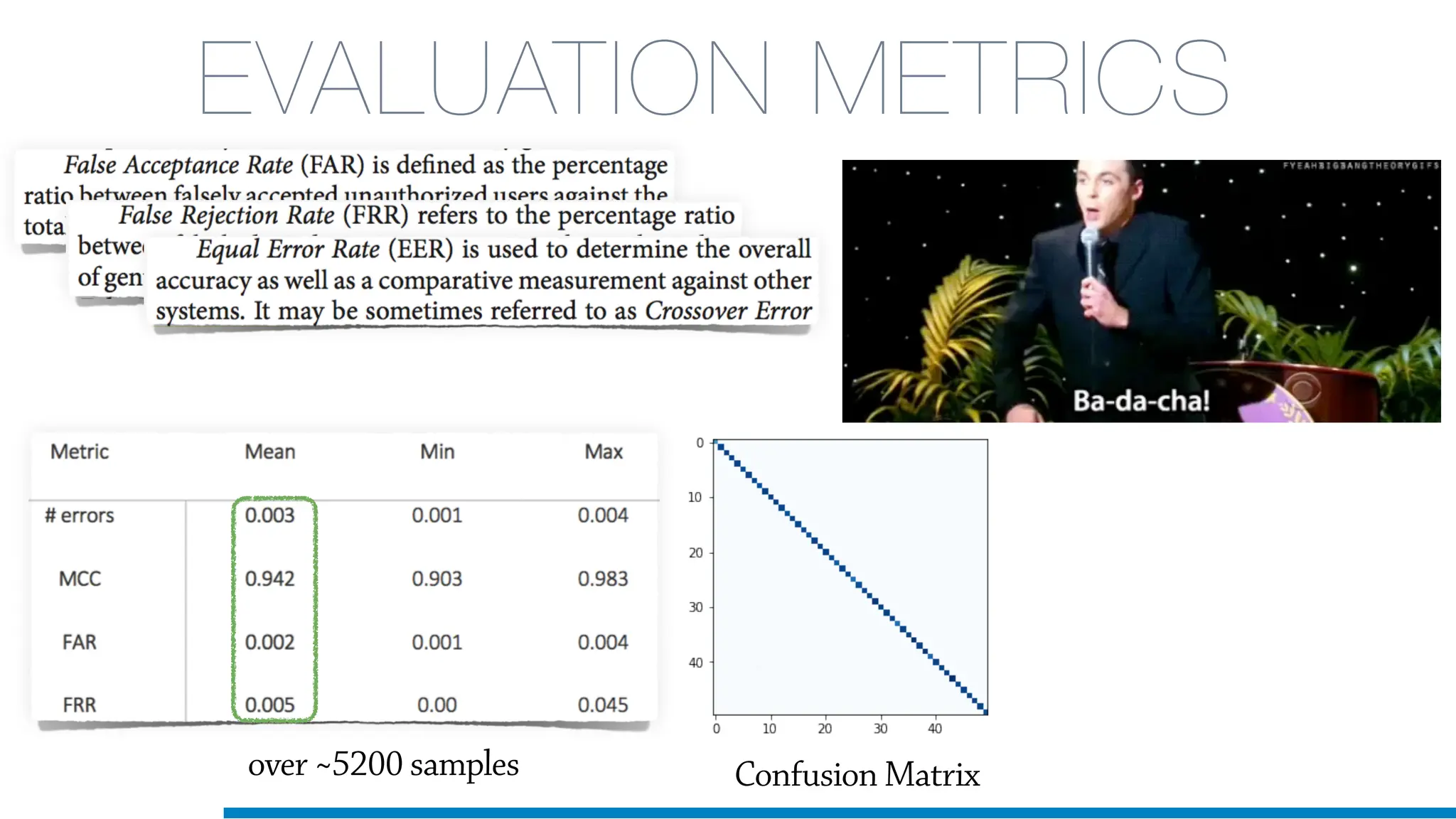
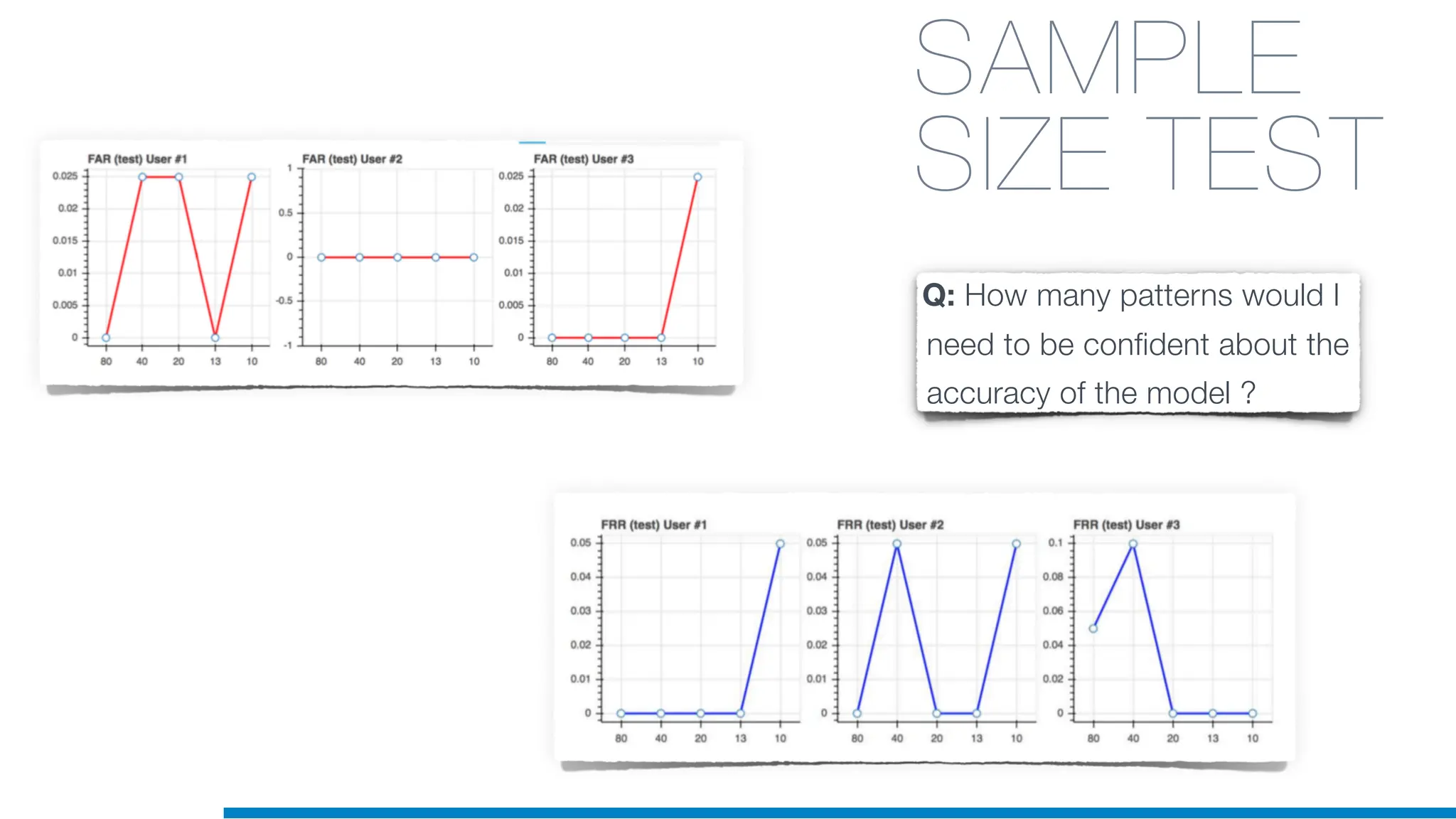
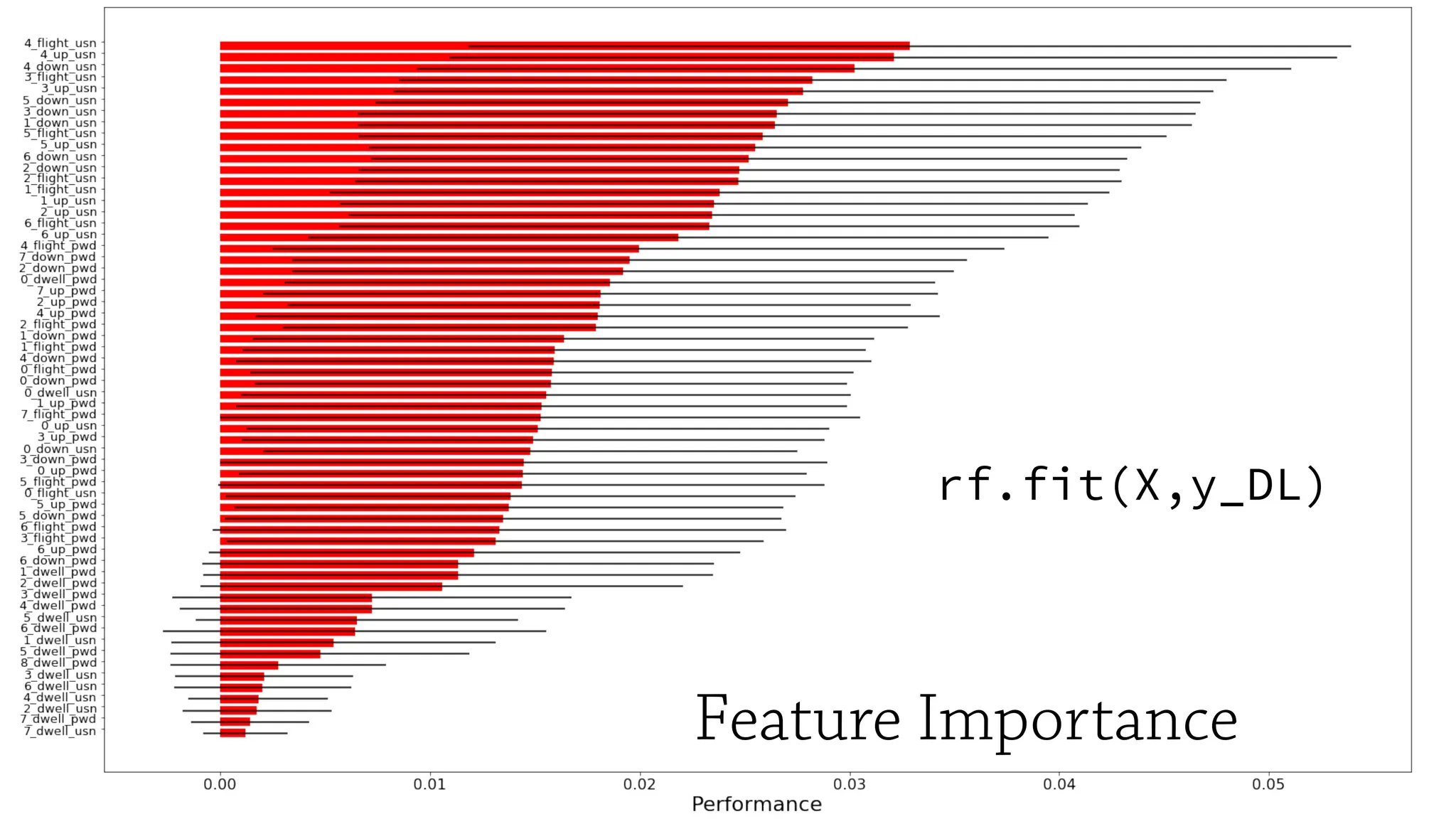
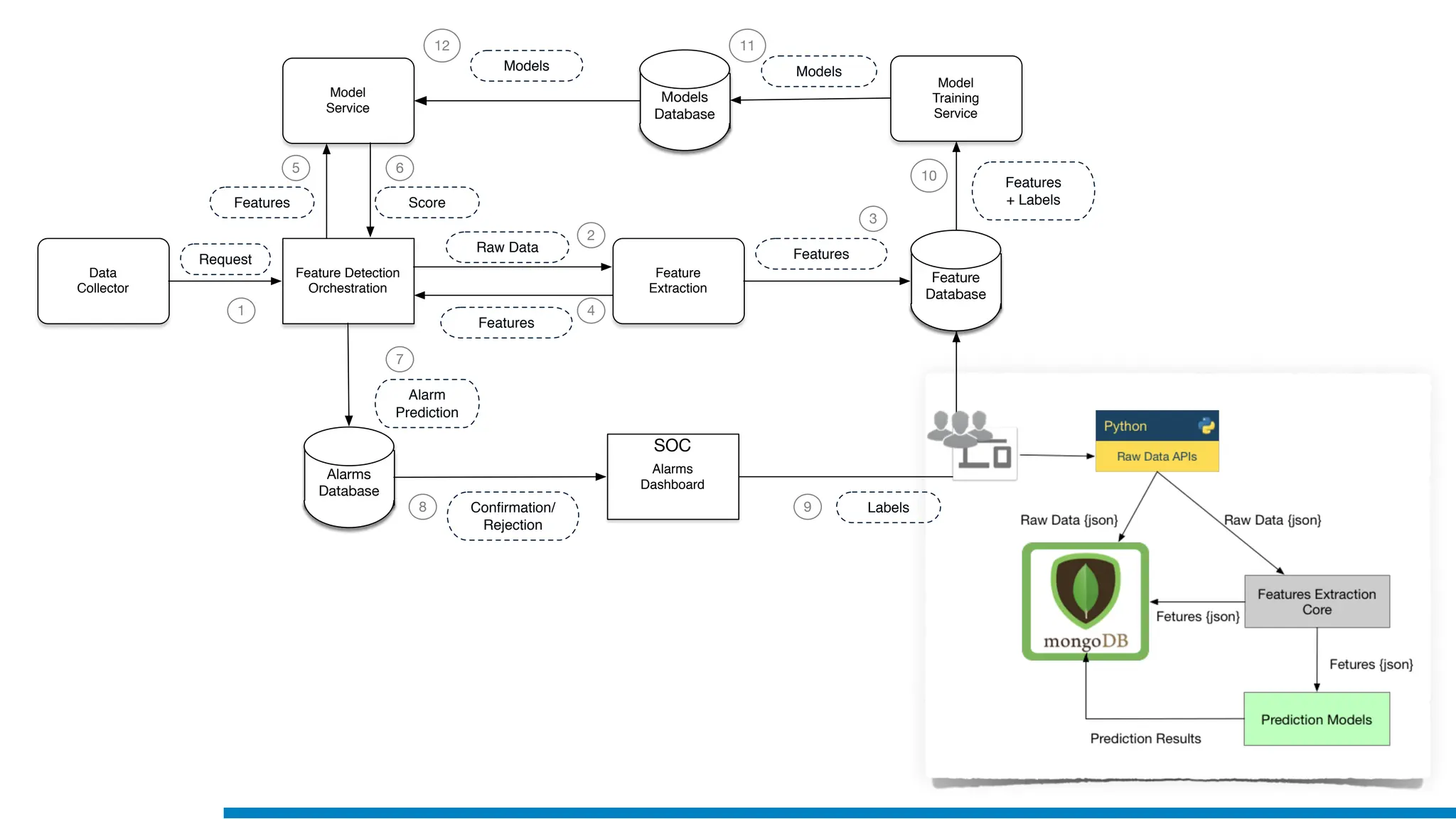
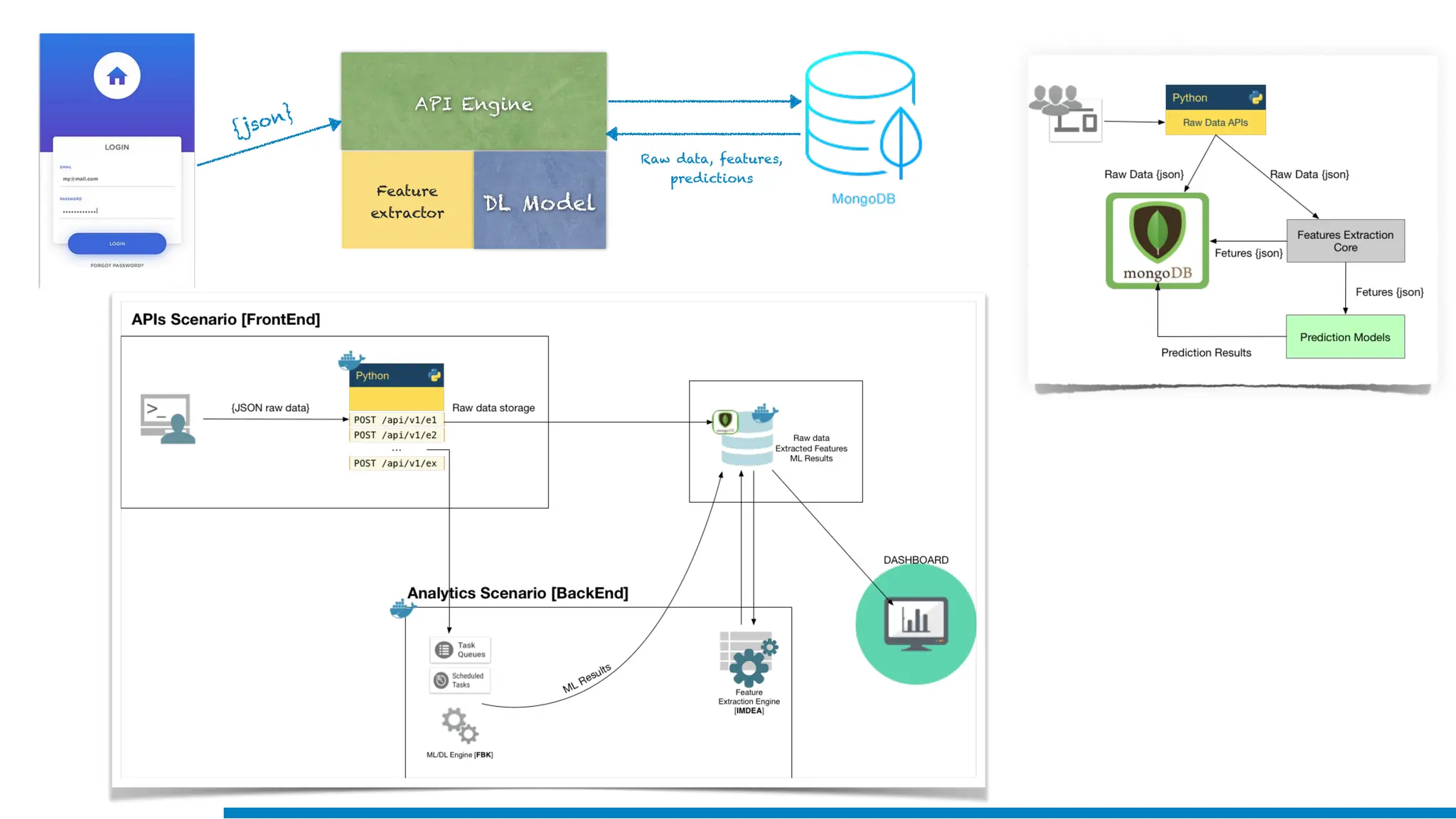
The document discusses the application of machine learning in cybersecurity, specifically focusing on keystroke dynamics for user identification. It outlines the steps for implementing applied machine learning, including data collection, preparation, model training, prediction, and deployment. Additionally, it highlights the process of analyzing typing patterns to detect anomalies for fraud prevention.