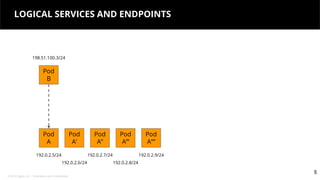
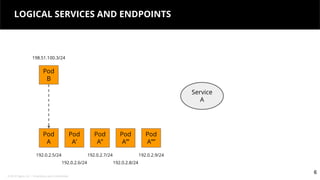
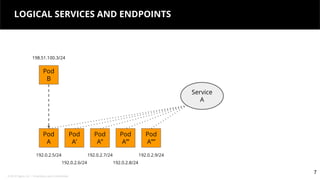
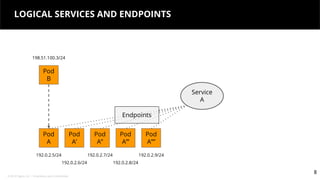
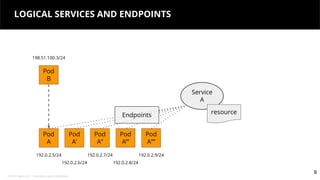
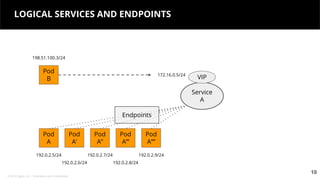
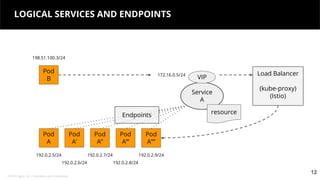
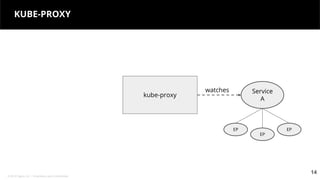
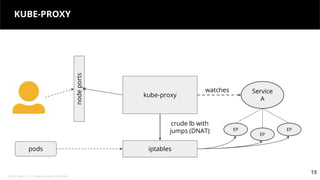
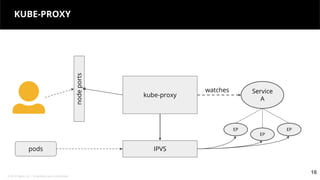
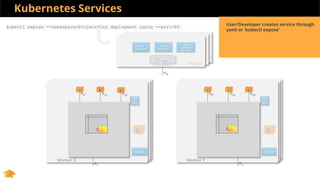
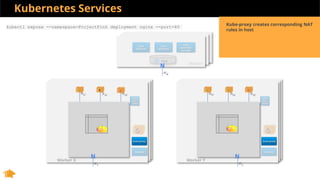
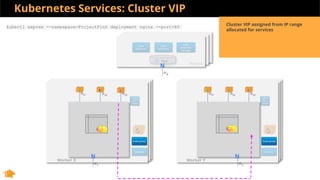
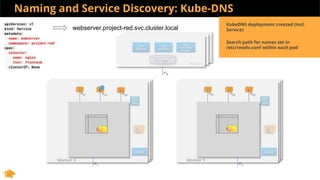
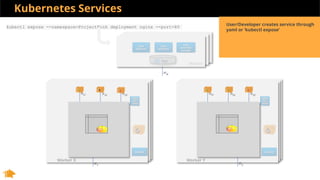
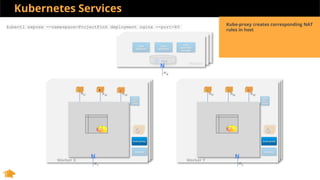
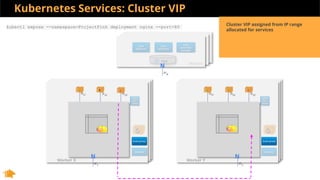
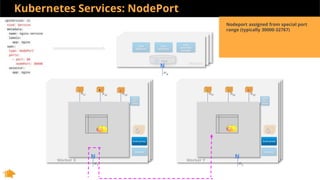
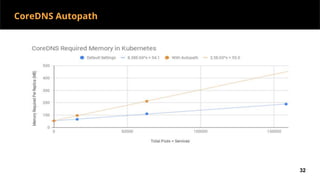
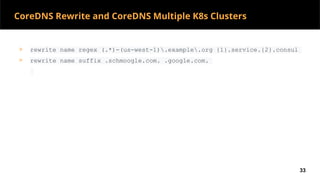
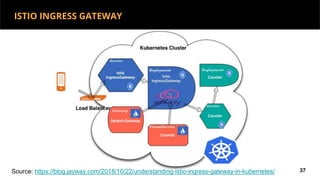
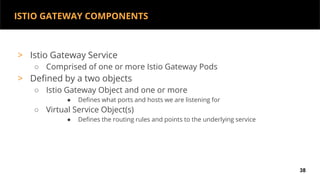
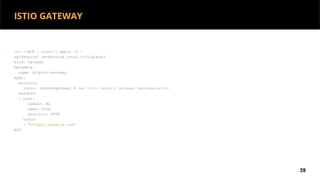
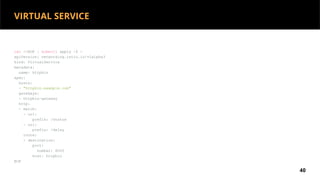
This document discusses Kubernetes services and how they provide a logical abstraction for sets of pods through concepts like services, endpoints, and the kube-proxy. It covers how Kubernetes services are implemented using kube-proxy through techniques like iptables rules or IPVS. It also discusses service discovery using Kubernetes DNS (kube-DNS or CoreDNS), and different service types like ClusterIP, NodePort, and LoadBalancer. Finally, it introduces newer projects that can enhance the Kubernetes service model like CoreDNS, ExternalDNS, MetalLB, and using the Istio ingress gateway for north-south traffic.