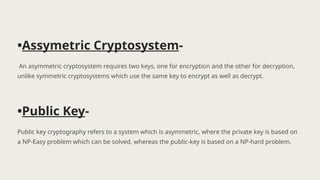
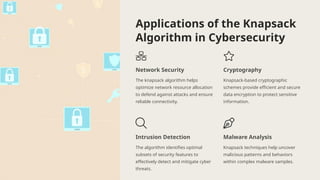
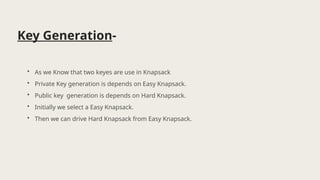
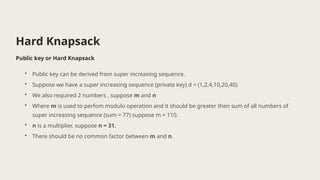
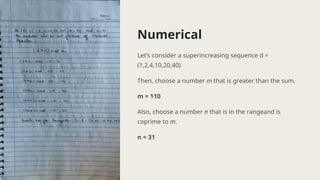
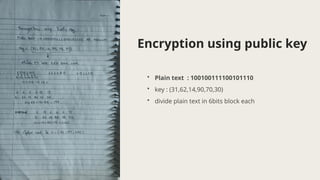
The document presents the knapsack algorithm, a public key cryptographic mechanism based on the knapsack problem, detailing its applications in cybersecurity such as network security, cryptography, and intrusion detection. It outlines the process of key generation for encryption and decryption, distinguishing between easy and hard knapsack constructions. Moreover, it discusses the algorithm's strengths and limitations regarding optimization efficiency, computational complexity, and sensitivity to data quality.