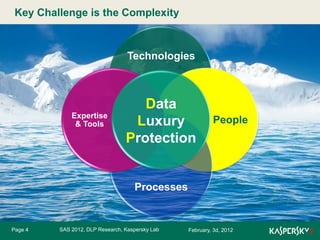
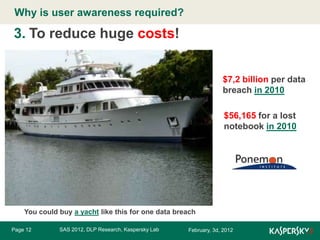
The document discusses the importance of user awareness in data loss prevention (DLP), emphasizing that humans are often the weakest link in security systems. It outlines the necessity of raising user awareness to protect against data breaches and reduce associated costs, proposing methods for effective education and management support. The authors, Valery Boronin and Vera Trubacheva from Kaspersky Lab, stress that improving user awareness is crucial for enhancing overall data security.