Embed presentation
Download to read offline

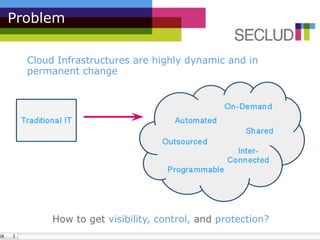



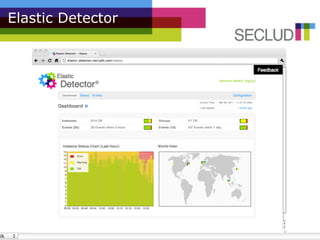
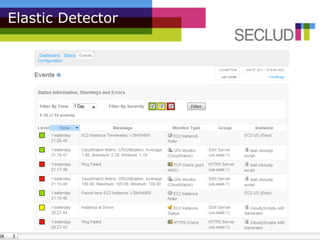
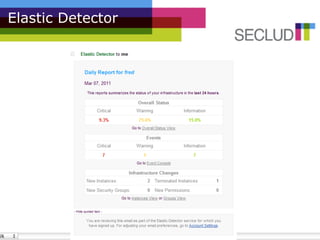



The document presents the Elastic Detector, a security solution for cloud infrastructures developed by Secludit to address issues of visibility, control, and protection in dynamic environments. Key features include auto-detection of new machines, real-time alerts, and comprehensive daily reports, all aimed at enhancing security and reducing administrative burdens. The product is in private beta as of December 2010, with an official release scheduled for March 1, 2011, and features a metered pricing model.










