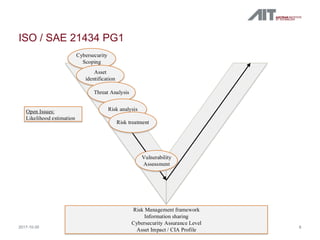
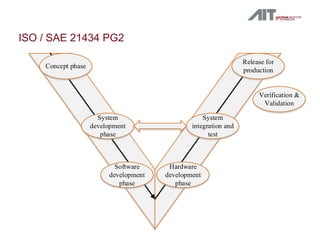
This document summarizes ISO/SAE 21434, which specifies requirements for cybersecurity risk management for road vehicles throughout their lifecycle. It defines a framework with four parts: (1) risk management, (2) product development, (3) operation/maintenance, and (4) an overview of processes and interdependencies. Each part addresses different phases like concept, design, and operation. The framework requires identifying assets, assessing vulnerabilities and threats, analyzing and treating risks, and information sharing. It applies to vehicles with electrical/electronic systems but does not prescribe specific cybersecurity technologies or solutions.