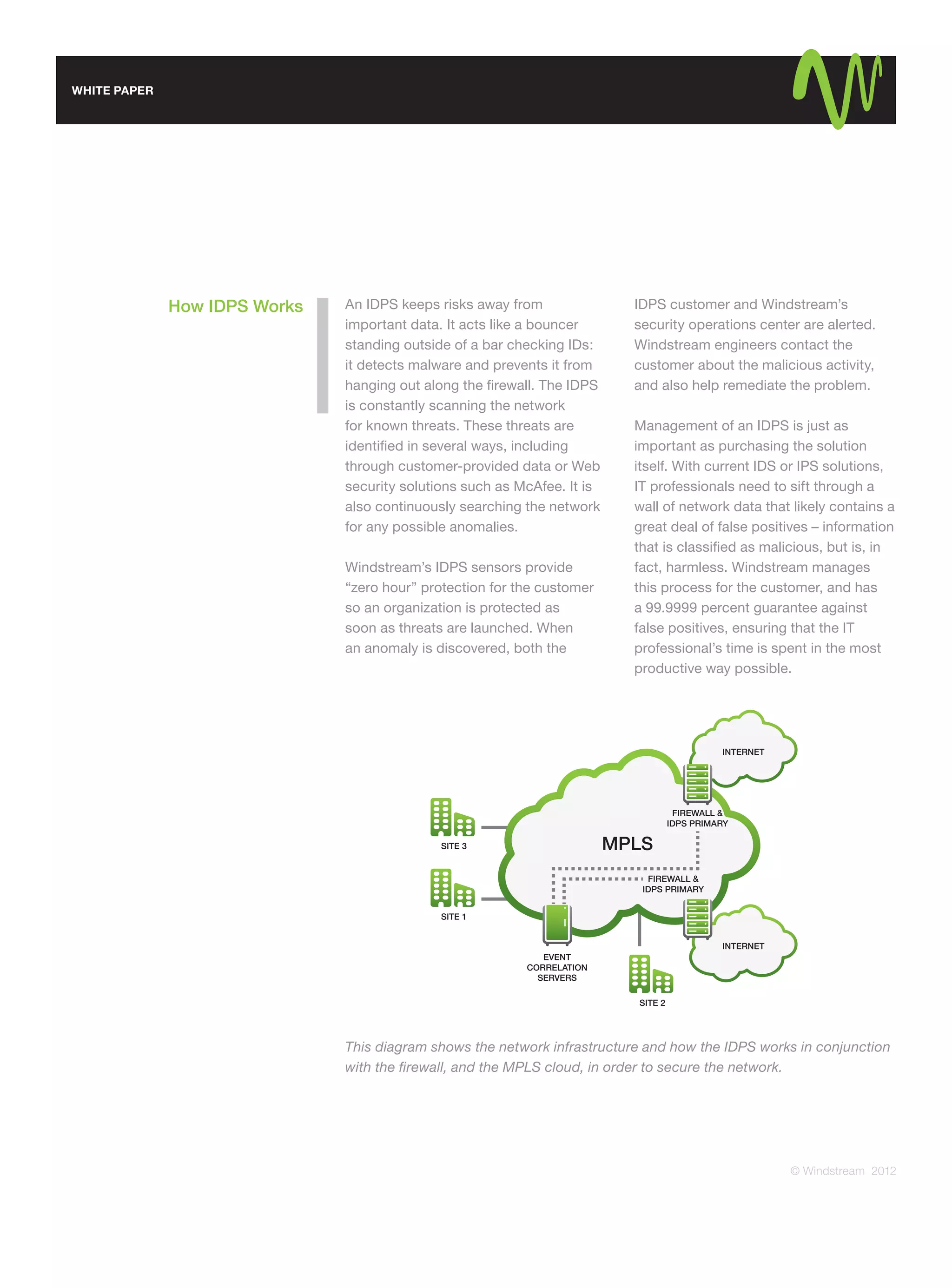
This document discusses the threats of malware to network security and argues that firewalls alone are not enough protection. It introduces intrusion detection and protection systems (IDPS) as the newest line of defense that can identify and prevent malware intrusion by examining network infrastructure. An IDPS solution scans for known threats, searches for anomalies, and actively blocks malware while allowing normal data. The document claims Windstream's IDPS requires no additional equipment, is cost-effective, and outperforms other products by minimizing risk.