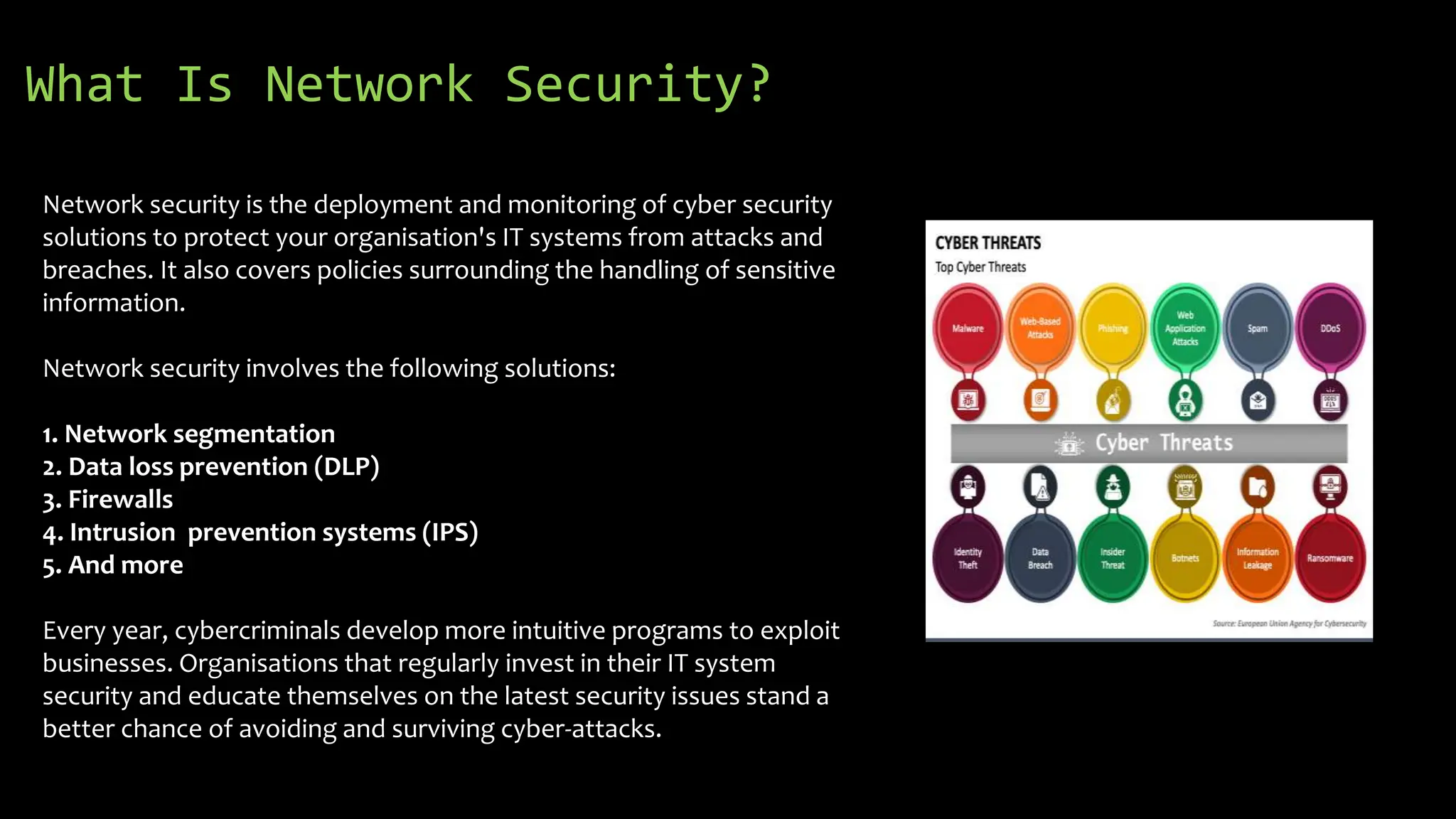
In 2022, Australians lost $72 million to cybercrime, highlighting the importance of network security for businesses of all sizes. Key threats include internal security issues, DDoS attacks, rogue software, malware, ransomware, phishing, and viruses, all of which can significantly harm operations. To protect against these threats, organizations should invest in cybersecurity training, data backups, and robust security measures, while fostering a culture of awareness among employees.