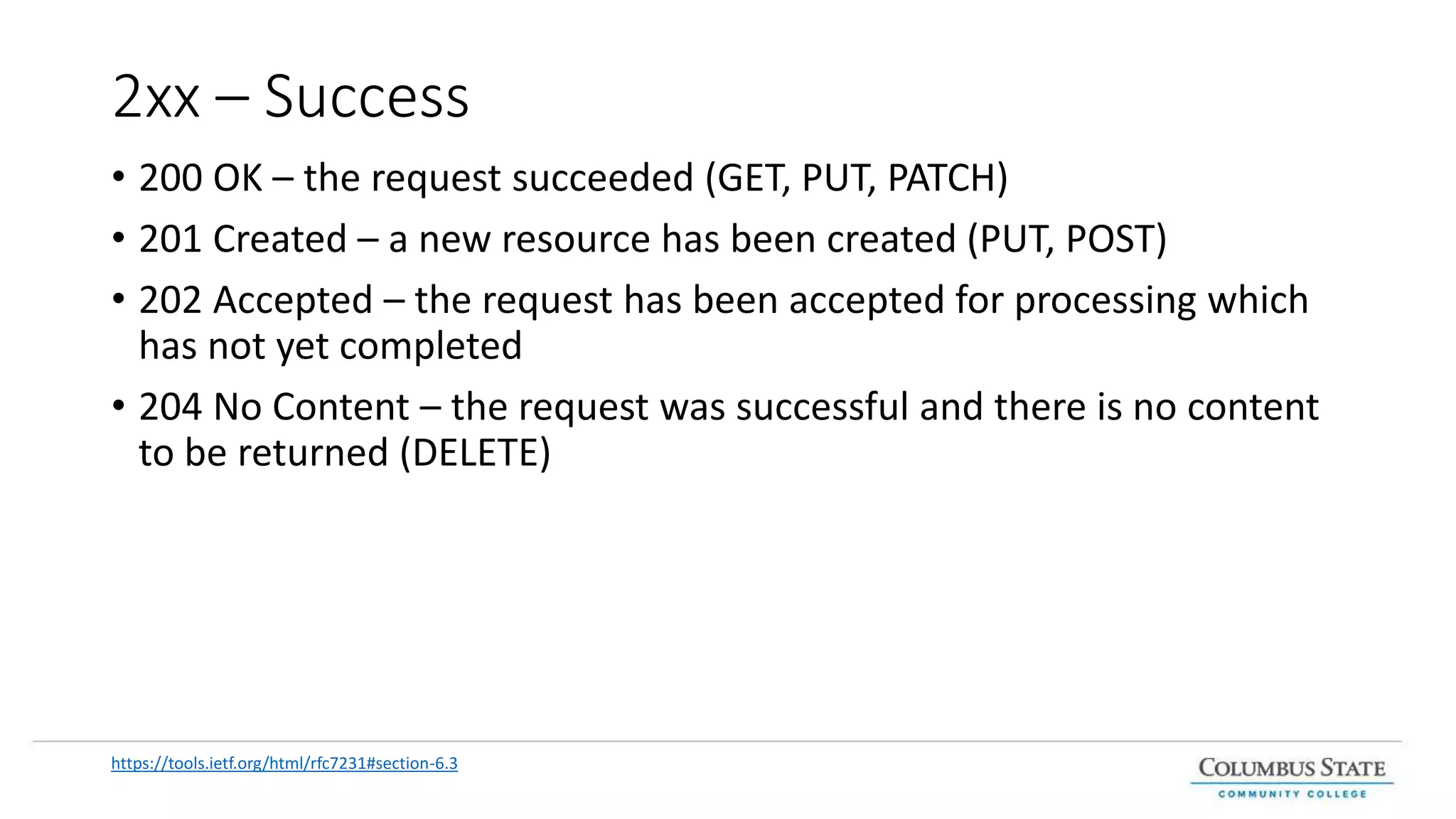
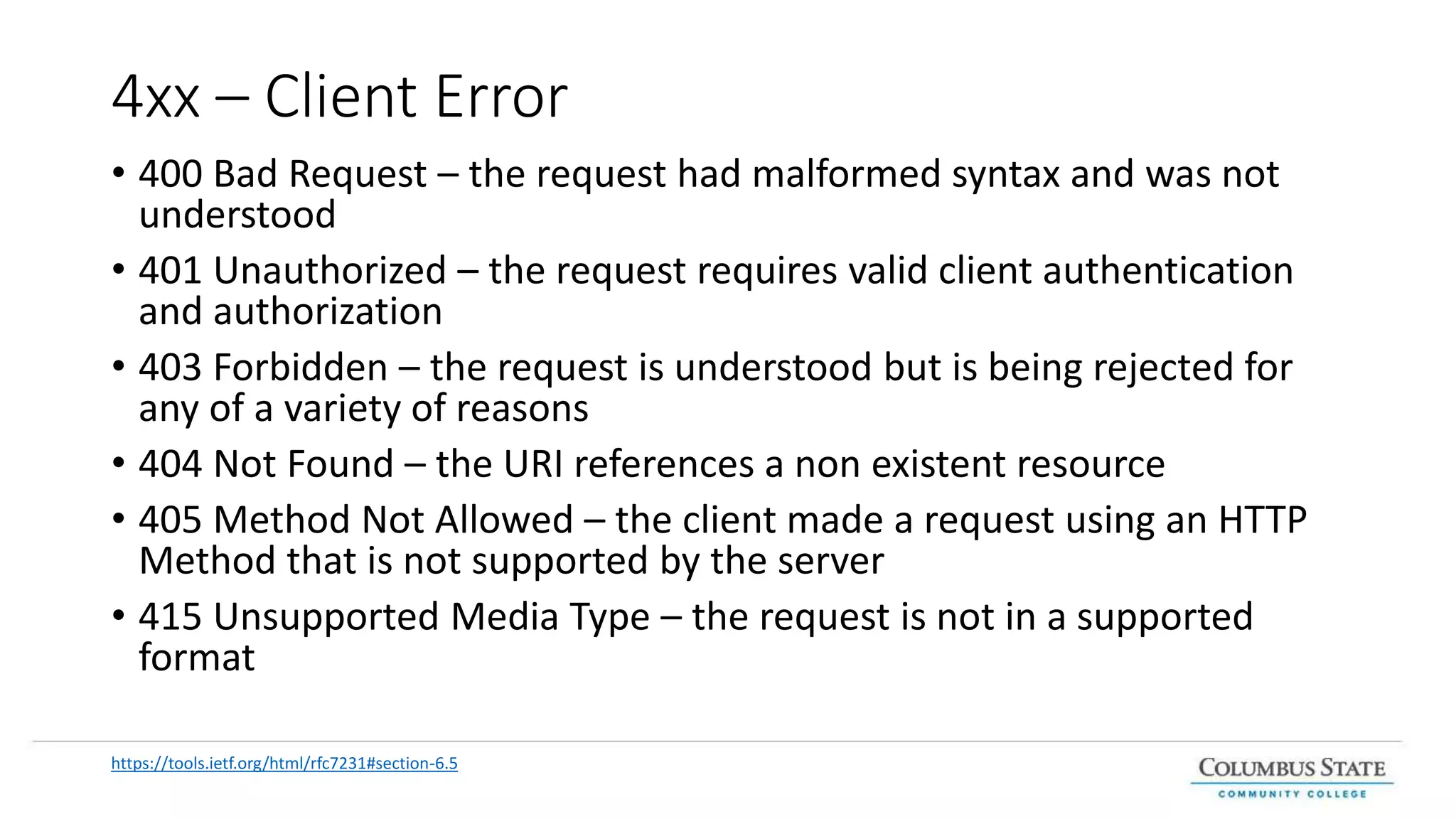
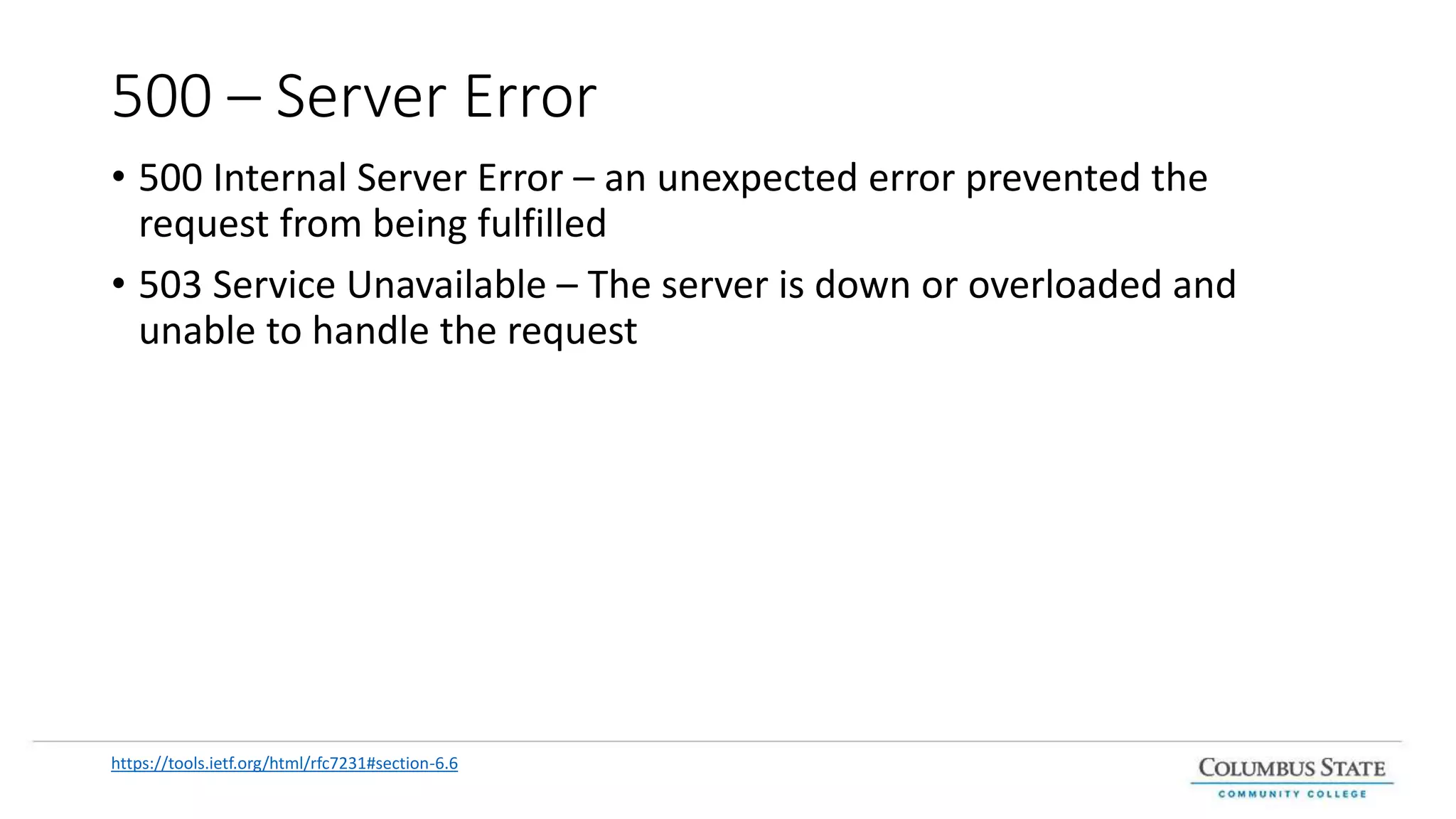
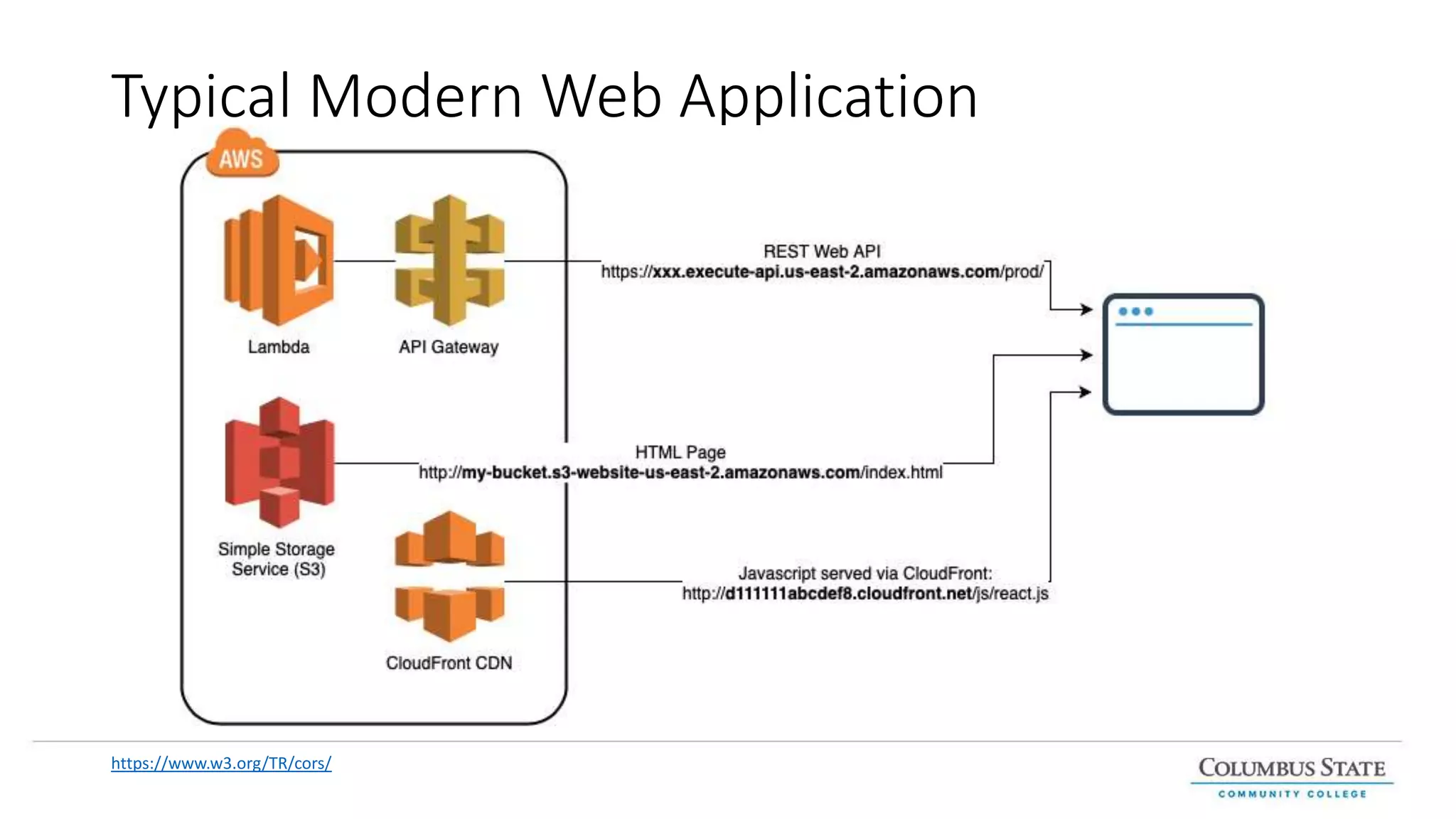
This document provides an introduction and overview of web services and RESTful APIs. It discusses the benefits of separating an application into logical layers and exposing business logic through services. It defines web services, microservices, and REST principles. It explains how RESTful resources are addressed with URIs and represented with formats like JSON. It outlines the HTTP methods GET, POST, PUT, PATCH, and DELETE and how they map to create, retrieve, update, and delete operations. It also covers SOAP and challenges it addresses compared to REST. Finally, it discusses HTTP status codes for indicating success and error responses.








![Uniform Resource Identifier (URI)
• http://www.ietf.org/rfc/rfc2396.txt
• tel:+1-816-555-1212
• mailto:John.Doe@example.com
• ftp://ftp.is.co.za/rfc/rfc1808.txt
• ldap://[2001:db8::7]/c=GB?objectClass?one
• urn:oasis:names:specification:docbook:dtd:xml:4.1.2
https://tools.ietf.org/html/rfc3986#section-1.1.2](https://image.slidesharecdn.com/rest-webservices-181222204135/75/Introduction-to-Web-Services-15-2048.jpg)